Biometrics
Luther Martin, Voltage Security
This chapter explains why designing biometric systems is actually a very difficult problem. The problem has been made to look easier than it actually is by the way that the technology has been portrayed in movies and on television. Biometric systems are typically depicted as being easy to use and secure, whereas encryption that would actually take billions of years of supercomputer time to defeat is often depicted as being easily bypassed with minimal effort. This portrayal of biometric systems may have increased expectations well past what current technologies can actually deliver, and it is important to understand the limitations of existing biometric technologies and to have realistic expectations of the security that such systems can provide in the real world.
Keywords
biometrics; biometric systems; biometric data; standards; biometric system architecture; subsystem; data capture; fingerprint; signal processing; reference; template
Biometrics is the analysis of biological observations and phenomena. People routinely use biometrics to recognize other people, commonly using the shape of a face or the sound of a voice to do so. Biometrics can also be used to create automated ways of recognizing a person based on her physiological or behavioral characteristics. Using biometrics as the basis of technologies that can be used to recognize people is not a new idea; there is evidence that fingerprints were used to sign official contracts in China as early as AD 700 and may have been used by ancient Babylonian scribes to sign cuneiform tablets as early as 2000 BC.1 In both of these cases, a fingerprint was pressed in clay to form a distinctive mark that could characterize a particular person. It is likely that the sophistication of the techniques used to analyze biometric data has increased over the past 4000 years, but the principles have remained essentially the same.
Using biometrics in security applications is certainly appealing. Determining a person’s identity through the presence of a physical object such as a key or access card has the problem that the physical token can be lost or stolen. Shared secrets such as passwords can be forgotten. Determining a person’s identity using biometrics seems an attractive alternative. It allows an identity to be determined directly from characteristics of the person. It is generally impossible for people to lose or forget their biometric data, so many of the problems that other means of verifying an identity are essentially eliminated if biometrics can be used in this role.
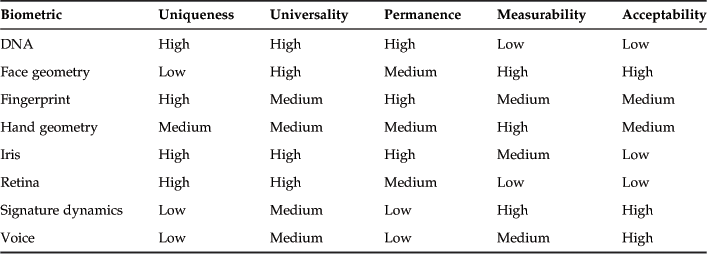
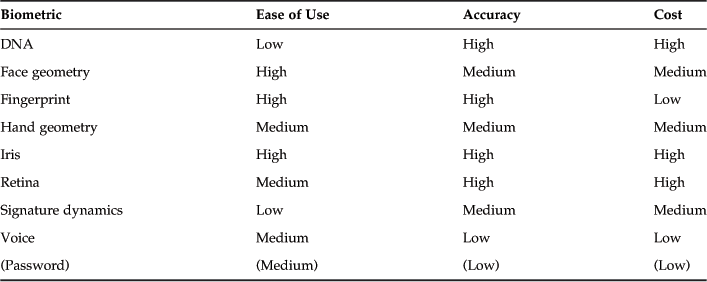
Not all biometric data is suitable for use in security applications, however. To be useful, such biometric data should be as unique as possible (uniqueness), should occur in as many people as possible (universality), should stay relatively constant over time (permanence), and should be able to be measured easily (measurability) and without causing undue inconvenience or distress to a user (acceptability). Examples of technologies that seem to meet these criteria to varying degrees are those that recognize a person based on his DNA, geometry of his face, fingerprints, hand geometry, iris pattern, retina pattern, handwriting, or voice. Many others are also possible. Not all biometrics are equally suited for use in security applications. Table 6.1 compares the properties of selected biometric technologies, rating each property as high, medium, or low. This table shows that there is no “best” biometric for security applications. Though this is true, each biometric has a set of uses for which its particular properties make it more attractive than the alternatives.
Biometrics systems can be used as a means of authenticating a user. When they are used in this way, a user presents his biometric data along with his identity, and the biometric system decides whether or not the biometric data presented is correct for that identity. Biometrics used as a method of authentication can be very useful, but authentication systems based on biometrics also have very different properties from other authentication technologies, and these differences should be understood before biometrics are used as part of an information security system.
Systems based on biometrics can also be used as a means of identification. When they are used in this way, captured biometric data is compared to entries in a database, and the biometric system determines whether or not the biometric data presented matches any of these existing entries. When biometrics are used for identification, they have a property that many other identification systems do not have. In particular, biometrics do not always require the active participation of a subject. While a user always needs to enter her password when the password is used to authenticate her, it is possible to capture biometric data without the user’s active involvement, perhaps even without her knowledge. This lets data be used in ways that other systems cannot. It is possible to automatically capture images of customers in a bank, for example, and to use the images to help identify people who are known to commit check fraud. Or it is possible to automatically capture images of airline passengers in an airport and use the images to help identify suspicious travelers.
The use of biometrics for identification also has the potential to pose serious privacy issues. The interests of governments and individual citizens are often at odds. Law enforcement agencies might want to be able to track the movements of certain people, and the automated use of biometrics for identification can certainly support this goal. On the other hand, it is unlikely that most people would approve of law enforcement having a database that contains detailed information about their travels. Similarly, tax authorities might want to track all business dealings to ensure that they collect all the revenue they are due, but it seems unlikely that most people would approve of government agencies having a database that tracks all merchants they have had dealings with, even if no purchases were made. Using some biometrics may also inherently provide access to much more information that is needed to just identify a person. DNA, for example, can used to identify people, but it can also be used to determine information about genetic conditions that are irrelevant to the identification process. But if a user needs to provide a DNA sample as a means of identification, the same DNA sample could be used to determine genetic information that the user might rather have kept private.
Designing biometric systems has been dubbed a “grand challenge” by researchers,2 indicating that a significant level of research will be required before it will be possible for real systems to approach the performance that is expected of the technology, but one that also has the possibility for broad scientific and economic impact when technology finally reaches that level. So, although biometric systems are useful today, we should expect to see them become even more useful in the future and for the technology to eventually become fairly commonly used.
1 Relevant Standards
The American National Standard (ANS) X9.84, “Biometric Information Management and Security for the Financial Services Industry,” is one of the leading standards that provide an overview of biometrics and their use in information security systems. It is a good high-level discussion of biometric systems, and the description of the technology in this chapter roughly follows the framework defined by this standard. This standard is particularly useful to system architects and others concerned with a high-level view of security systems. On the other hand, this standard does not provide many details of how to implement such systems.
There are also several international (ISO/IEC) standards that cover the details of biometric systems with more detail than ANS X9.84 does. These are listed in Table 6.2. These standards provide a good basis for implementing biometric systems and may be useful to both engineers and others who need to build a biometric system, and others who need the additional level of detail that ANS X9.84 does not provide. Many other ISO/IEC standards for biometric systems are currently under development that address other aspects of such systems, and in the next few years it is likely that the number of these standards that have been finalized will at least double from the number that are listed here. The JTC 1/SC 37 technical committee of the ISO is responsible for the development of these standards.
Table 6.2
Current ISO/I EC Standards for Biometric Systems.
| Standard | Title |
| ISO/IEC 19784-1:2006 | Information technology – Biometric Application Programming Interface – Part 1: BioAPI Specification |
| ISO/IEC 19784-2:2007 | Information technology – Biometric Application Programming Interface – Part 2: Biometric Archive Function Provider Interface |
| ISO/IEC 19785-1:2006 | Information technology – Common Biometric Exchange Formats Framework (CBEFF) – Part 1: Data Element Specification |
| ISO/IEC 19785-2:2006 | Information technology – Common Biometric Exchange Formats Framework (CBEFF) – Part 2: Procedures for the Operation of the Biometric Registration Authority |
| ISO/IEC 19794-1:2006 | Information technology – Biometric data interchange format – Part 1: Framework |
| ISO/IEC 19794-2:2005 | Information technology – Biometric data interchange format – Part 2: Finger minutiae data |
| ISO/IEC 19794-3:2006 | Information technology – Biometric data interchange format – Part 3: Finger pattern spectral data |
| ISO/IEC 19794-4:2005 | Information technology – Biometric data interchange format – Part 4: Finger image data |
| ISO/IEC 19794-5:2005 | Information technology – Biometric data interchange format – Part 5: Face image data |
| ISO/IEC 19794-6:2005 | Information technology – Biometric data interchange format – Part 6: Iris image data |
| ISO/IEC 19794-7:2006 | Information technology – Biometric data interchange format – Part 7: Signature/sign time series data |
| ISO/IEC 19794-8:2006 | Information technology – Biometric data interchange format – Part 8: Finger pattern skeletal data |
| ISO/IEC 19794-9:2007 | Information technology – Biometric data interchange format – Part 9: Vascular image data |
| ISO/IEC 19795-1:2006 | Information technology – Biometric performance testing and reporting – Part 1: Principles and framework |
| ISO/IEC 19795-2:2007 | Information technology – Biometric performance testing and reporting – Part 2: testing methodologies for technology and scenario evaluation |
| ISO/IEC 24709.1: 2007 | BioAPI Conformance Testing – Part 1: Methods and Procedures |
| ISO/IEC 24709.2: 2007 | BioAPI Conformance Testing – Part 2: Test Assertions for Biometric Service Providers |
2 Biometric System Architecture
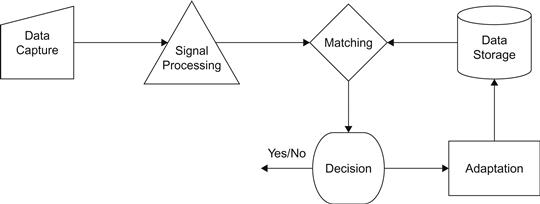
All biometric systems have a number of common subsystems. These are the following:
An additional subsystem, the adaptation subsystem, may be present in some biometric systems but not others.
Data Capture
A data capture subsystem collects captured biometric data from a user. To do this, it performs a measurement of some sort and creates machine-readable data from it. This could be an image of a fingerprint, a signal from a microphone, or readings from a special pen that takes measurements while it is being used. In each case, the captured biometric data usually needs to be processed in some way before it can be used in a decision algorithm. It is extremely rare for a biometric system to make a decision using an image of a fingerprint, for example. Instead, features that make fingerprints different from other fingerprints are extracted from such an image in the signal processing subsystem, and these features are then used in the matching subsystem. The symbol that is used to indicate a data capture subsystem is shown in Figure 6.1.
The performance of a data capture subsystem is greatly affected by the characteristics of the sensor that it uses. A signal processing subsystem may work very well with one type of sensor, but much less well with another type. Even if identical sensors are used in each data capture subsystem, the calibration of the sensors may need to be consistent to ensure the collection of data that works well in other subsystems.
Environmental conditions can also significantly affect the operation of a data capture subsystem. Dirty sensors can result in images of fingerprints that are distorted or incomplete. Background noise can result in the collection of a data that makes it difficult for the signal processing subsystem to identify the features of a voice signal. Lighting can also affect any biometric data that is collected as an image so that an image collected against a gray background might not work as well as an image collected against a white background.
Because environmental conditions affect the quality and usefulness of captured biometric data, they also affect the performance of all the subsystems that rely on it. This means that it is essential to carry out all testing of biometric systems under conditions that duplicate the conditions under which the system will normally operate (see checklist, “An Agenda For Action For Biometrics Testing”). Just because a biometric system performs well in a testing laboratory when operated by well-trained users does not mean that it will perform well in real-world conditions. Because the data capture subsystem is typically the only one with which users directly interact, it is also the one that may require training of users to ensure that it provides useful data to the other subsystems.
Signal Processing
A signal processing subsystem takes the captured biometric data from a data capture subsystem and transforms the data into a form suitable for use in the matching subsystem. This transformed data is called a reference, or a template if it is stored in a data storage subsystem. A template is a type of reference, and it represents the average value that we expect to see for a particular user.
A signal processing subsystem may also analyze the quality of captured biometric data and reject data that is not of high enough quality. An image of a fingerprint that is not oriented correctly might be rejected, or a sample of speech that was collected with too much background noise might be rejected. The symbol that is used to indicate a signal processing subsystem is shown in Figure 6.2.
If the captured biometric data is not rejected, the signal processing subsystem then transforms the captured biometric data into a reference. In the case of fingerprints, for example, the signal processing subsystem may extract features such as the locations of branches and endpoints of the ridges that comprise a fingerprint. A biometric system that uses the speech of users to characterize them might convert the speech signal into frequency components using a Fourier transform and then look for patterns in the frequency components that uniquely characterize a particular speaker. A biometric that uses an image of a person’s face might first look for large features such as the eyes, nose, and mouth and then look for distinctive features such as eyebrows or parts of the nose relative to the large ones, to uniquely identify a particular user. In any case, the output of the signal processing subsystem is the transformed data that comprises a reference. Although a reference contains information that has been extracted from captured biometric data, it may be possible to recover the captured biometric data, or a good approximation to it, from a template.3
Note that though several standards exist that define the format of biometric references for many technologies, these standards do not describe how references are obtained from captured biometric data. This means that there is still room for vendor innovation while remaining in compliance with existing standards.
Matching
A matching subsystem receives a reference from a signal processing subsystem and then compares the reference with a template from a data storage subsystem. The output of the matching subsystem is a numeric value called a comparison score that indicates how closely the two match.
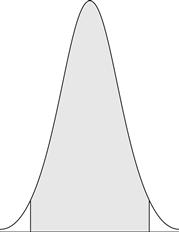
Random variations occur in a data capture subsystem when it is used. This means that the reference created from the captured data is different each time, even for the same user. This makes the comparison score created for a particular user different each time they use the system, with random variations occurring around some average value. This concept is shown in Figure 6.3, in which the distribution of comparison scores that are calculated from repeated captures of biometric data from a single user are random. Such random data tend to be close to an average value every time that they are calculated from captured biometric data but not exactly the average value.
This is much like the case we get in other situations where observed data has a random component. Suppose that we flip a fair coin 100 times and count how many times the result “heads” appears. We expect to see this result an average of 50 times, but this average value actually occurs fairly rarely; exactly 50 out of 100 flips coming up heads happen less than 8% of the time. On the other hand, the number of heads will usually be not too far from the average value of 50, with the number being between 40 and 60 more than 95% of the time. Similarly, with biometrics, captured data will probably be close, but not identical, to an average value, and it will also not be too different from the average value.
The comparison score calculated by a matching subsystem is passed to a decision subsystem, where it is used to make a decision about the identity of the person who was the source of the biometric data. The symbol that is used to indicate a matching subsystem is shown in Figure 6.4.
Data Storage
A data storage subsystem stores templates that are used by the matching subsystem. The symbol that is used to indicate a data storage subsystem is shown in Figure 6.5.
A database is one obvious candidate for a place to store templates, but it is possible to store a template on a portable data storage device such as a chip card or a smart card. The relative strengths and weaknesses of different ways of doing this are discussed in the section on security considerations.
Decision
A decision subsystem takes a comparison score that is the output of a matching subsystem and returns a binary yes or no decision from it. This decision indicates whether or not the matching subsystem made a comparison which resulted in a match or not. The value yes is returned if the comparison was probably a match; the value no is returned is the comparison was probably not a match. The symbol that is used to indicate a decision subsystem is shown in Figure 6.6.
To make a yes or no decision, a decision subsystem compares a comparison score with a parameter called a threshold. The threshold value represents a measure of how good a comparison needs to be to be considered a match. If the comparison score is less than or equal to the threshold value then the decision subsystem returns the value yes. If the comparison score is greater than the threshold, it returns the value no. Comparison scores that will result in a yes or no response from a decision subsystem are shown in Figure 6.7. Comparison scores in the gray area of this illustration are close to the average value and result in a yes, whereas comparison scores that are outside the gray area are too far from the average value and result in a no. In Figure 6.7, the threshold value defines how far the gray area extends from the central average value. If the threshold is decreased, the size of the gray area will get narrower and decrease in size so that fewer comparison scores result in a yes answer. If the threshold is increased, the gray area will get wider and increase in size so that more comparison scores result in a yes answer.
Errors may occur in any decision subsystem. There are two general types of errors that can occur. In one case, a decision subsystem makes the incorrect decision of no instead of yes. In this case, a user is indeed who she claims to be, but large random errors occur in the data capture subsystem and cause her to be incorrectly rejected. This type of error might result in the legitimate user Alice inaccurately failing to authenticate as herself.
This class of error is known as a type-1 error by statisticians,4 a term that would almost certainly be a contender for an award for the least meaningful terminology ever invented if such an award existed. It was once called false rejection by biometrics researchers and vendors, a term that has more recently been replaced by the term false nonmatch. One way in which the accuracy of biometric systems is now typically quantified is by their false nonmatch rate (FNMR), a value that estimates the probability of the biometric system making a type-1 error in its decision subsystem.
In the second case, a decision subsystem incorrectly returns a yes instead of a no. In this case, random errors occur that let a user be erroneously recognized as a different user. This might happen if the user Alice tries to authenticate as the user Bob, for example. This class of error is known as a type-2 error by statisticians.5 It was once called false acceptance by biometrics researchers and vendors, a term that has been more recently been replaced by the term false match. This leads to quantifying the accuracy of biometrics by their false match rate (FMR), a value that estimates the probability of the biometric system making a type-2 error.
For a particular biometric technology, it is impossible to simultaneously reduce both the FNMR and the FMR, although improving the technology does make it possible to do this. If the parameters used in a matching subsystem are changed so that the FNMR decreases, the FMR rate must increase; if the parameters used in a matching subsystem are changed so that the FMR decreases, the FNMR must increase. This relationship follows from the nature of the statistical tests that are performed by the decision subsystem and is not limited to just biometric systems. Any system that makes a decision based on statistical data will have the same property. The reason for this is shown in Figures 6.8 and 6.9.
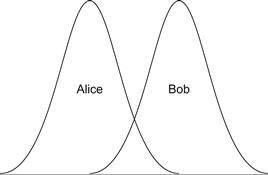
Suppose that we have two users of a biometric system: Alice and Bob, whose comparison scores are distributed as shown in Figure 6.8. Note that the distributions of these values overlap so that in the area where they overlap, the comparison score could have come from either Alice or Bob, but we cannot tell which. If the average values that we expect for Alice and Bob are far enough apart, the chances of this happening may get extremely low, but even in such cases it is possible to have large enough errors creep into the data capture step to make even the rarest of errors possible.
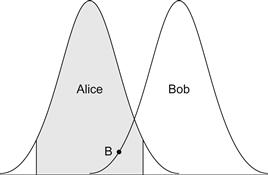
Figure 6.9 shows how a false match can occur. Suppose that Bob uses our hypothetical biometric system but claims to be Alice when he does this, and the output of the matching subsystem is the point B that is shown in Figure 6.9. Because this point is close enough to the average that we expect from biometric data from Alice, the decision subsystem will erroneously decide that the biometric data that Bob presented is good enough to authenticate him as Alice. This is a false match, and it contributes to the FMR of the system.
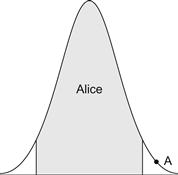
Figure 6.10 shows how a false nonmatch can occur. Suppose that Alice uses our hypothetical biometric system and the output of the matching subsystem is the point A that is shown in Figure 6.10. Because this point is too far from the average that we expect when Alice uses the system, it is more likely to have come from someone else other than from Alice, and the decision subsystem will erroneously decide that the biometric data that Alice presented is probably not hers. This is a false nonmatch, and it contributes to the FNMR of the system.
Because the FNMR and FMR are related, the most meaningful way to represent the accuracy of a biometric system is probably by showing the relationship between the two error rates. The relationship between the two is known by the term receiver operating characteristic, or ROC, a term that originated in the study of the sensitivity of radio receivers as their operating parameters change. Figure 6.11 shows an ROC curve for a hypothetical biometric. Such an ROC curve assumes that the only way in which the error rates are changed is by changing the threshold value that is used in the decision subsystem. Note that this ROC curve indicates that when the FMR increases the FNMR decreases, and vice versa.
By adjusting the threshold that a decision subsystem uses it is possible to make the FMR very low while allowing the FNMR to get very high or to allow the FMR to get very high while making the FNMR very low. Between these two extreme cases lies the case where the FMR and the FNMR are the same. This point is sometimes the equal error rate (EER) or crossover error rate (CER) and is often used to simplify the discussions of error rates for biometric systems.
Though using a single value does indeed make it easier to compare the performance of different biometric systems, it can also be somewhat misleading. In high-security applications like those used by government or military organizations, keeping unauthorized users out may be much more important than the inconvenience caused by a high FNMR. In consumer applications, like ATMs, it may be more important to keep the FNMR low. This can help avoid the anger and accompanying support costs of dealing with customers who are incorrectly denied access to their accounts. In such situations, a low FNMR may be more important than the higher security that a higher FMR would provide. The error rates that are acceptable are strongly dependent on how the technology is being used, so be wary of trying to understand the performance of a biometric system by only considering the CER.
There is no theoretical way to accurately estimate the FMR and FNMR of biometric systems, so all estimates of these error rates need to be made from empirical data. Because testing can be expensive, the sample sizes used in such testing are often relatively small, so the results may not be representative of larger and more general populations. This is further complicated by the fact that some of the error rates that such testing attempts to estimate are fairly low. This means that human error from mislabeling data or other mistakes that occur during testing may make a bigger contribution to the measured error rates than the errors caused by a decision subsystem. It may be possible to create a biometric system that makes an error roughly only one time in 1 million operations, for example, but it is unrealistic to expect such high accuracy from the people who handle the data in an experiment that tries to estimate such an error rate. And because there are no standardized sample sizes and test conditions for estimating these error rates, there can be a wide range of reliability of error rate estimates. In one study,5 a biometric system that performed well in a laboratory setting when used by trained users ended up correctly identifying enrolled users only 51% of the time when it was tested in a pilot project under real-world conditions, perhaps inviting an unenviable comparison with a system that recognizes a person by his ability to flip a coin and have it come up heads. Because of these effects, estimates of error rates should be viewed with a healthy amount of skepticism, particularly when extremely low rates are claimed.
Adaptation
Some biometric data changes over time. This may result in matches with a template becoming worse and worse over time, which will increase the FNMR of a biometric system. One way to avoid the potential difficulties associated with having users eventually becoming unrecognizable is to update their template after a successful authentication. This process is called adaptation, and it is done by an optional part of a biometric system called an adaptation subsystem. If an adaptation subsystem is present, the symbol shown in Figure 6.12 is used to indicate it.
3 Using Biometric Systems
There are three main operations that a biometric system can perform. These are the following.
• Enrollment. During this operation, a biometric system creates a template that is used in later authentication and identification operations. This template, along with an associated identity, is stored in a data storage subsystem.
• Authentication. During this operation, a biometric system collects captured biometric data and a claimed identity and determines whether or not the captured biometric data matches the template stored for that identity. Although the term authentication is almost universally used in the information security industry for this operation, the term verification is often used by biometrics vendors and researchers to describe this.
• Identification. During this operation, a biometric system collects captured biometric data and attempts to find a match against any of the templates stored in a data storage subsystem.
Enrollment
Before a user can use a biometric system for either authentication or identification, a data storage subsystem needs to contain a template for the user. The process of initializing a biometric system with such a template is called enrollment, and it is the source of another error rate that can limit the usefulness of biometric systems. The interaction of the subsystems of a biometric system when enrolling a user is shown in Figure 6.13.
In the first step of enrollment, a user presents his biometric data to a data capture subsystem. The captured biometric data is then converted into a reference by a signal processing subsystem. This reference is then stored in a data storage subsystem, at which point it becomes a template. Such a template is typically calculated from several captures of biometric data to ensure that it reflects an accurate average value. An optional step includes using a matching subsystem to ensure that the user is not already enrolled.
The inherent nature of some captured biometric data as well as the randomness of captured biometric data can cause the enrollment process to fail. Some people have biometrics that are far enough outside the normal range of such data that they cause a signal processing subsystem to fail when it attempts to convert their captured data into a reference. The same types of random errors that contribute to the FMR and FNMR are also present in the enrollment process, and can be sometimes be enough to turn captured biometric data that would normally be within the range that the signal processing subsystem can handle into data that is outside this range. In some cases, it may even be impossible to collect some types of biometric data from some users, like the case where missing hands make it impossible to collect data on the geometry of the missing hands.
The probability of a user failing in the enrollment process is used to calculate the failure to enroll rate (FER). Almost any biometric can fail sometimes, either temporarily or permanently. Dry air or sticky fingers can cause fingerprints to temporarily change. A cold can cause a voice to temporarily become hoarse. A broken arm can temporarily change the way a person writes his signature. Cataracts can permanently make retina patterns impossible to capture. Some skin diseases can even permanently change fingerprints.
A useful biometric system should have a low FER, but because all such systems have a nonzero value for this rate, it is likely that there will always be some users that cannot be enrolled in any particular biometric system, and a typical FER for a biometric system may be in the range of 1% to 5%. For this reason, biometric systems are often more useful as an additional means of authentication in multifactor authentication system instead of the single method used.
Authentication
After a user is enrolled in a biometric system, the system can be used to authenticate this user. The interaction of the subsystems of a biometric system when used to authenticate a user is shown in Figure 6.14.
To use a biometric system for authentication, a user first presents both a claimed identity and his biometric data to a data capture subsystem. The captured biometric data is then passed to a signal processing subsystem where features of the captured data are extracted and converted into a reference. A matching subsystem then compares this reference to a template from a data storage subsystem for the claimed identity and produces a comparison score. This comparison score is then passed to a decision subsystem, which produces a yes or no decision that reflects whether or not the biometric data agrees with the template stored for the claimed identity. The result of the authentication operation is the value returned by the decision subsystem.
A false match that occurs during authentication will allow one user to successfully authenticate as another user. So if Bob claims to be Alice and a false match occurs, he will be authenticated as Alice. A false nonmatch during authentication will incorrectly deny a user access. So if Bob attempts to authenticate as himself, he will be incorrectly denied assess if a false nonmatch occurs.
Because biometric data may change over time, an adaptation subsystem may update the stored template for a user after they have authenticated to the biometric system. If this is done, it will reduce the number or times that users will need to go through the enrollment process again when their biometric data changes enough to increase their FNMR rate to an unacceptable level.
Identification
A biometric system can be used to identify a user that has already enrolled in the system. The interaction of the subsystems of a biometric system when used for identification is shown in Figure 6.15.
To use a biometric system for identification, a user presents his biometric data to a data capture subsystem. The captured biometric data is then passed to a signal processing subsystem where features of the captured data are extracted and converted into a reference. A matching subsystem then compares this reference to each of the templates stored in a data storage subsystem and produces a comparison score. Each of these comparison scores are passed to a decision subsystem, which produces a yes or no decision that reflects whether or not the reference is a good match for each template. If a yes decision is reached, then the identity associated with the template is returned for the identification operation. It is possible for this process to return more that one identity. This may or may not be useful, depending on the application. If a yes decision is not reached for any of the templates in a data storage subsystem, then a response that indicates that no match was found is returned for the identification operation.
A false match that occurs during identification will incorrectly identify a user as another enrolled user. So if Bob uses a biometric system for identification, he might be incorrectly identified as Alice if a false match occurs. Because there are typically many comparisons done when a biometric system is used for identification, the FMR can increase dramatically because there is an opportunity for a false match with every comparison. Suppose that for a single comparison we have an FMR of ε1 and that εn represents the FMR for n comparisons. These two error rates are related by εn=1 – (1 – ε1)n. If n·ε1 ![]() 1. then we have that εn≈n · ε1. This means that for a small FMR, the FMR is increased by a factor equal to the number of enrolled users when a system is used for identification instead of authentication. So an FMR of 10−6 when a system is used for authentication will be increased to approximately 10−3 if the identification is done by comparing to 1000 templates. A false nonmatch during identification will fail to identify an enrolled user as one who is enrolled in the system. So Bob might be incorrectly rejected, even though he is actually an enrolled user.
1. then we have that εn≈n · ε1. This means that for a small FMR, the FMR is increased by a factor equal to the number of enrolled users when a system is used for identification instead of authentication. So an FMR of 10−6 when a system is used for authentication will be increased to approximately 10−3 if the identification is done by comparing to 1000 templates. A false nonmatch during identification will fail to identify an enrolled user as one who is enrolled in the system. So Bob might be incorrectly rejected, even though he is actually an enrolled user.
4 Security Considerations
Biometric systems differ from most other authentication or identification technologies in several ways, and these differences should be understood by anyone considering using such systems as part of an information security architecture. Biometric data is not secret, or at least it is not very secret. Fingerprints, for example, are not very secret because so-called latent fingerprints are left almost everywhere. On the other hand, reconstructing enough of a fingerprint from latent fingerprints to fool a biometric system is actually very difficult because latent fingerprints are typically of poor quality and incomplete. Because biometric data is not very secret, it may be useful to verify that captured biometric data is fresh instead of being replayed. There are technologies available that make it more difficult for an adversary to present fake biometric data to a biometric system for this very purpose. The technology exists to distinguish between a living finger and a manufactured copy, for example. Such technologies are not foolproof and can themselves be circumvented by clever attackers. This means that they just make it more difficult for an adversary to defeat a biometric system, but not impossible.
It is relatively easy to require users to frequently change their passwords and to enforce the expiration of cryptographic keys after their lifetime has passed, but many types of biometric data last for a long time, and it is essentially impossible to force users to change their biometric data. So when biometric data is compromised in some way, it is not possible to reissue new biometric data to the affected users. For that reason, it may be useful to both plan for alternate forms of authentication or identification in addition to a biometric system and to not rely on a single biometric system being useful for long periods of time.
Biometrics used for authentication may have much lower levels of security than other authentication technologies. This, plus the fact there is usually a non-zero FER for any biometric system, means that biometric systems may be more useful as an additional means of authentication than as a technology that can work alone. Types of authentication technology can be divided into three general categories or “factors”:
• Something that a user knows, such as a password or PIN
• Something that a user has, such as a key or access card
• Something that a user is or does, which is exactly the definition of a biometric
To be considered a multifactor authentication system, a system must use means from more than one of these categories to authenticate a user so that a system that uses two independent password-based systems for authentication does not qualify as a multifactor authentication system, whereas one that uses a password plus a biometric does. There is a commonly held perception that multifactor authentication is inherently more secure than authentication based on only a single factor, but this is not true. The concepts of strong authentication, in which an attacker has a small chance of bypassing the means of authentication, and multifactor authentication are totally independent. It is possible to have strong authentication based on only one factor. It is also possible to have weak authentication based on multiple authentication factors. So, including a biometric system as part of a multifactor authentication system should be done for reasons other than to simply use more than a single authentication factor. It may be more secure to use a password plus a PIN for authentication than to use a password plus a biometric, for example, even though both the password and PIN are the same type of authentication factor.
Error Rates
The usual understanding of biometric systems assumes that the FMR and FNMR of a biometric system are due to random errors that occur in a data capture subsystem. In particular, this assumes that the biometrics that are used in these systems are actually essentially unique. The existing market for celebrity lookalikes demonstrates that enough similarities exist in some physical features to justify the concern that similarities also exist in the more subtle characteristics that biometric systems use.
We assume, for example, that fingerprints are unique enough to identify a person without any ambiguity. This may indeed be true,6 but there has been little careful research that demonstrates that this is actually the case. The largest empirical study of the uniqueness of fingerprints used only 50,000 fingerprints, a sample that could have come from as few as 5000 people, and has been criticized by experts for its careless use of statistics.7 This is an area that deserves a closer look by researchers, but the expense of large-scale investigations probably means that they will probably never be carried out, leaving the uniqueness of biometrics an assumption that underlies the use of the technology for security applications. Note that other parts of information security also rely on assumptions that may never be proved. The security provided by all public-key cryptographic algorithms, for example, assumes that certain computational problems are intractable, but there are currently no proofs that this is actually the case.
The chances that the biometrics used in security systems will be found to be not unique enough for use in such systems is probably remote, but it certainly could happen. One easy way to prepare for this possibility is to use more than one biometric to characterize users. In such multi-modal systems, if one of the biometrics used is found to be weak, the others can still provide adequate strength. On the other hand, multi-modal systems have the additional drawback of being more expensive that a system that uses a single biometric.
Note that a given error rate can have many different sources. An error rate of 10% could be caused by an entire population having an error rate of 10%, or it could be caused by 90% of a population having an error rate of zero and 10% of the population having an error rate of 100%. The usability of the system is very different in each of these cases. In one case, all users are equally inconvenienced, but in the other case, some users are essentially unable to use the system at all. So understanding how errors are distributed can be important in understanding how biometric systems can be used. If a biometric system is used to control access to a sensitive facility, for example, it may not be very useful in this role if some of the people who need entry to the facility are unlucky enough to have a 100% FNMR. Studies have suggested that error rates are not uniformly distributed in some populations, but they are not quite as bad as the worst case. The nonuniform distribution of error rates that is observed in biometric systems is often called Doddington’s Zoo and is named after the researcher who first noticed this phenomenon and the colorful names that he gave to the classes of users who made different contributions to the observed error rates.
Doddington’s Zoo
Based on his experience testing biometric systems, George Doddington divided people into four categories: sheep, goats, lambs, and wolves.8 Sheep are easily recognized by a biometric system and comprise most of the population. Goats are particularly unsuccessful at being recognized. They have chronically high FNMRs, usually because their biometric is outside the range that a particular system recognizes. Goats can be particularly troublesome if a biometric system is used for access control, where it is critical that all users be reliably accepted. Lambs are exceptionally vulnerable to impersonation, so they contribute to the FMR. Wolves are exceptionally good false matchers and they also make a significant contribution to the FMR.
Doddington’s goats can also cause another problem. Because their biometric pattern is outside the range that a particular biometric system expects, they may be unable to enroll in such a system and thus be major contributors to the FER of the system.
Note that users that may be sheep for one biometric may turn out to be goats for another, and so on. Because of this it is probably impossible to know in advance how error rates are distributed for a particular biometric system, it is almost always necessary to test such systems thoroughly before deploying them on a wide scale.
Birthday Attacks
Suppose that we have n users enrolled in a biometric system. This biometric system maps arbitrary inputs into n+1 states that represent deciding on a match with one of the n users plus the additional “none of the above” user that represents the option of deciding on a match with none of the n enrolled users. From this point of view, this biometric system acts like a hash function so might try to use well-known facts about hash functions to understand the limits that this property puts on error rates. In particular, errors caused by the FMR of a biometric system look like a collision in this hash function, which happens when two different input values to a hash function result in the same output from the hash function. For this reason, we might think that the same “birthday attack” that can find collisions for a hash function can also increase the FMR of a biometric system. The reason for this is as follows.
For a hash function that maps inputs into m different message digests, the probability of finding at least one collision, a case where different inputs map to the same message digest, after calculating n message digests is approximately 1 – e−n2/2m.9 Considering birthdays as a hash function that maps people into one of 365 possible birthdays, this tells us that the probability of two or more people having the same birthday in a group of only 23 people is approximately 1 – e−232/2·365≈0.52. This means that there is greater that a 50% chance of finding two people with the same birthday in a group of only 23 people, a result that is often counter to people’s intuition. Using a biometric system is much like a hash function in that it maps biometric data into the templates in the data storage subsystem that it has a good match for, and collisions in this hash function cause a false match. Therefore, the FMR may increase as more users are added to the system, and if it does, we might expect the FMR rate to increase in the same way that the chances of a collision in a hash function do. This might cause false matches at a higher rate that we might expect, just like the chances of finding matching birthdays does.
In practice, however, this phenomenon is essentially not observed. This may be due to the nonuniform distribution in error rates of Doddingon’s Zoo. If the threshold used in a decision subsystem is adjusted to create a particular FMR, it may be limited by the properties of Doddington’s lambs. This may leave the sheep that comprise the majority of the user population with enough room to add additional users without getting too close to other sheep.
ANS X9.84 requires that the FMR for biometric systems provide at least the level of security provided by a four-digit PIN, which equates to an FMR of no greater than 10−4 and recommends that they provide an FMR of no more than 10−5. In addition, this standard requires that the corresponding FNMR be no greater than 10−2 at the FMR selected for use. These error rates may be too ambitious for some existing technologies, but it is certainly possible to attain these error rates with some technologies.
On the other hand, these error rates compare very unfavorably with other authentication technologies. For example, an FMR of 10−4 is roughly the same as the probability of randomly guessing a four-digit PIN, a three-character password, or a 13-bit cryptographic key. And although few people would find three-character passwords or 13-bit cryptographic keys acceptable, they might have to accept an FMR of 10−4 from a biometric system because of the limitations of affordable current technologies. Table 6.3 summarizes how the security provided by various FMRs compares to both the security provided by all-numeric PINs and passwords that use only case-independent letters.
Comparing Technologies
There are many different biometrics that are used in currently available biometric systems. Each of these competing technologies tries to be better than the alternatives in some way, perhaps being easier to use, more accurate, or cheaper to operate. Because there are so many technologies available, however, it should come as no surprise that there is no single “best” technology for use in biometric systems. Almost any biometric system that is available is probably the best solution for some problem, and it is impossible to list all of the cases where each technology is the best without a very careful analysis of each authentication or identification problem. So any attempt to make a simple comparison between the competing technologies will be inherently inaccurate. Despite this, Table 6.4 attempts to make such a high-level comparison. In this table, the ease of use, accuracy and cost are rated as high, medium, or low.
Using DNA as a biometric provides an example of the difficulty involved in making such a rough classification. The accuracy of DNA testing is limited by the fairly large number of identical twins that are present in the overall population, but in cases other than distinguishing identical twins it is very accurate. So if identical twins need to be distinguished, it may not be the best solution. By slightly abusing the usual understanding of what a biometric is, it is even possible to think of passwords as a biometric that is based purely on behavioral characteristics, along with the FMR, FNMR, and FER rates that come with their use, but they are certainly outside the commonly understood meaning of the term. Even if they are not covered by the usual definition of a biometric, passwords are fairly well understood, so they provide a point of reference for comparing against the relative strengths of biometrics that are commonly used in security systems. The accuracy of passwords here is meant to be that of passwords that users select for their own use instead of being randomly generated. Such passwords are typically much weaker than their length indicates because of the structure that people need to make passwords easy to remember. This means that the chances of guessing a typical eight-character case-insensitive password is actually much greater than the 26−8 that we would expect for strong passwords. Studies of the randomness in English words have estimated that there is approximately one bit of randomness per letter.10 If we conservatively double this to estimate that there are approximately two bits of randomness per letter in a typical user-selected password, we get the estimate that an eight-character password probably provides only about 16 bits of randomness, which is close to the security provided by a biometric system with an FMR of 10−5. This means that the security of passwords as used in practice is often probably comparable to that attainable by biometric systems, perhaps even less if weak passwords are used.
Storage of Templates
One obvious way to store the templates used in a biometric system is in a database. This can be a good solution, and the security provided by the database may be adequate to protect the templates that it stores. In other cases, it may be more useful for a user to carry his template with him on some sort of portable data storage device and to provide that template to a matching subsystem along with his biometric data. Portable, credit-card-sized data storage devices are often used for this purpose. There are three general types of such cards that are used in this way, and each has a different set of security considerations that are relevant to it.
In one case, a memory card with unencrypted data storage can be used to store a template. This is the least expensive option, but also the least secure. Such a memory card can be read by anyone who finds it and can easily be duplicated, although it may be impossible for anyone other that the authorized user to use it. Nonbiometric data stored on such a card may also be compromised when a card is lost.
In principle, a nonauthorized user can use such a card to make a card that lets them authenticate as an authorized user. This can be done as follows. Suppose that Eve, a nonauthorized user, gets the memory card that stores the template for the authorized user Alice. Eve may be able to use Alice’s card to make a card that is identical in every way to Alice’s card but that has Eve’s template in place of Alice’s. Then when Eve uses this card to authenticate, she uses her biometric data, which then gets compared to her template on the card and gets her authenticated as the user Alice. Note that doing this relies on a fairly unsecured implementation.
A case that is more secure and also more expensive is a memory card in which data storage is encrypted. The contents of such a card can still be read by anyone who finds it and can easily be duplicated, but it is infeasible for an unauthorized user to decrypt and use the data on the card, which may also include any nonbiometric data on the card. Encrypting the data storage also makes it impractical for an unauthorized user to make a card that will let them authenticate as an authorized user. Though it may be possible to simply replace one template with another if the template is stored unencrypted on a memory card, carrying out the same attack on a memory card that stores data encrypted requires being able to create a valid encrypted template, which is just as difficult as defeating the encryption.
The most secure as well as the most expensive case is where a smart card with cryptographic capabilities is used to store a template. The data stored on such a smart card can only be read and decrypted by trusted applications, so that it is infeasible for anyone who finds a lost smart card to read data from it or to copy it. This makes it infeasible for unauthorized users to use a smart card to create a way to authenticate as an authorized user. It also protects any nonbiometric data that might be stored on the card.
5 Summary
Using biometric systems as the basis for security technologies for authentication or identification is currently feasible. Each biometric has properties that may make it useful in some situations but not others, and security systems based on biometrics have the same property. This means that there is no single “best” biometric for such use and that each biometric technology has an application where it is superior to the alternatives.
There is still a great deal of research that needs to be done in the field, but existing technologies have progressed to the point that security systems based on biometrics are now a viable way to perform authentication or identification of users, although the properties of biometrics also make them more attractive as part of a multifactor authentication system instead of the single means that is used.
Finally, let’s move on to the real interactive part of this Chapter: review questions/exercises, hands-on projects, case projects and optional team case project. The answers and/or solutions by chapter can be found in the Online Instructor’s Solutions Manual.
Chapter Review Questions/Exercises
True/False
1. True or False? Biometrics is the analysis of biological observations and phenomena. People routinely use biometrics to recognize other people, commonly using the shape of a face or the sound of a voice to do so.
2. True or False? Not all biometric systems have a number of common subsystems.
3. True or False? A data subsystem collects captured biometric data from a user.
4. True or False? A signal processing subsystem takes the captured biometric data from a data subsystem and transforms the data into a form suitable for use in the matching subsystem.
5. True or False? A matching subsystem receives a reference from a signal processing subsystem and then compares a template from a data storage subsystem.
Multiple Choice
1. What subsystem stores templates that are used by the matching subsystem?
2. What subsystem takes a comparison score that is the output of a matching subsystem and returns a binary yes or no decision from it?
A. Network attached storage (NAS)
3. One way to avoid the potential difficulties associated with having users eventually becoming unrecognizable is to update their template after a successful authentication. This process is called:
4. During what operation, does a biometric system create a template that is used in later authentication and identification operations?
5. During what operation, does a biometric system collect captured biometric data and a claimed identity and determines whether or not the captured biometric data matches the template stored for that identity?
Exercise
Problem
How are biometrics collected?
Hands-On Projects
Project
What are biometric templates?
Optional Team Case Project
Problem
Why are there so many different biometric modalilties?
1R. Heindl, System und Praxis der Daktyloskopie und der sonstigen technischen Methoden der Kriminalopolizei, De Gruyter, 1922.
2A. Jain, et al., “Biometrics: A grand challenge,” Proceedings of the 17th International Conference on Pattern Recognition, Cambridge, UK, August 2004, pp. 935–942.
3M. Martinez-Diaz, et al., “Hill-climbing and brute-force attacks on biometric systems: A case study in match-on-card fingerprint verification,” Proceedings of the 40th IEEE International Carahan Conference on Security Technology, Lexington, October 2006, pp. 151–159.
4J. Neyman and E. Pearson, “On the use and interpretation of certain test criteria for purposes of statistical inference: Part I,” Biometrika, Vol. 20 A, No. 1–2, pp. 175–240, July 1928.
5S. King, H. Harrelson and G. Tran, “Testing iris and face recognition in a personnel identification application,” 2002 Biometric Consortium Conference, February 2002.
6S. Pankanti, S. Prabhakar and A. Jain, “On the individuality of fingerprints,” IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 24, No. 8, pp. 1010–1025, August 2002.
7S. Cole, Suspect Identities: A History of Fingerprinting and Criminal Identification, Harvard University Press, 2002.
8G. Doddington, et al., “Sheep, goats, lambs and wolves: A statistical analysis of speaker performance in the NIST 1998 speaker recognition evaluation,” Proceedings of the Fifth International Conference on Spoken Language Processing, Sydney, Australia, November–December, 1998, pp. 1351–1354.
9D. Knuth, The Art of Computer Programming, Volume 2: Sorting and Searching, Addison-Wesley, 1973.
10C. Shannon, “Prediction and entropy of printed english,” Bell System Technical Journal, Vol. 30, pp. 50–64, January 1951.