Securing the Infrastructure
Lauren Collins, kCura Corporation
Collectively, an infrastructure consists of circuits, cabinets, cages, cabling, power, cooling, hardware, data, and traffic. Devices are placed meticulously to transmit data, to secure data, and to allow an organization to conduct business efficiently and effectively. Security is presented to protect the infrastructure, especially critical applications, and custom rules strive to restrict the susceptibilities of such structures and systems. Incidental occurrences may severely impact the business, and potentially the economy, which is the prime reason engineers architect an infrastructure to manage information securely. The nature of the business that is conducted should be considered when designing the layout of an infrastructure, where security may not always be the top priority and speed is.
Keywords
infrastructure; communication security; cryptography; network design; cipher text; secret keys; algorithms; switching; routing; backbone networks; ports; protocols
1 Communication Security Goals
Since the inception of technology, data security revolves around cryptography. Because cryptography is only as good as the ability of a person or a program, new methods are constantly implemented as technology becomes more sophisticated.
Network Design and Components
Cipher text and secret keys are transported over the network and can be harvested for analysis; furthermore they can impersonate a source or, worst case, cause a service denial. Thus, to aid encryption and complex distribution methods, a network needs to be secure and elegant. That is, the network should have applicable appliances that monitor and detect attacks, intelligence that discriminates between degradations/failures and attacks, and also a convention for vigorous countermeasure strategies to outmaneuver the attacker. Consequently, network security is a completely separate topic from data security; however, the devices chosen must complement your infrastructure.
The accumulation of advances in key technologies has enabled companies to envision the implementation of an infrastructure with no limitations. Among these advances are those in materials that underlie electronic components and optical technologies, including optical fibers. Improvements in electronic integrated circuits include both the speed at which these circuits can perform their functions and the achievable complexity that allows a single chip to perform complex tasks. Advances in signal processing techniques that use electronic circuits and software to convert information and information-carrying signals into forms suitable for transport over short or long distances arrange for data to be stored, processed, and transmitted lightning fast. Such advantages have even allowed engineers and scientists to work harder and think further out to develop new technologies to follow suit on hardware and software transformations. Significant progress is required to realize and appreciate the vision of affordable media.
New algorithms and approaches complement the speed of transport networks, coupled with complex connection and session establishment and management. Total network approaches are required to resolve effective management of a cutting-edge infrastructure solution. Large costs are associated with installation and building out of fiber networks needed to provide an objective, robust network. Networks must be scalable and support multiple types of media, including coax, fiber, copper, and wireless, using both the shared media and switched approaches. Premise access must support the multiplexing of video, voice, and data sources requiring varied quality-of-service (QoS) levels and various bandwidths.
Several backbone options and avenues are available, due mostly to the era of electronic trading. These can be comprehensively separated into time division techniques and wavelength division techniques. Determining the potential of each technology would significantly contribute to a company’s success, depending completely on the type of business involved. The time domain limits are determined by the speed of the electro-optic transducers, of the required buffer and memory, and of the switching and control logic required to manage the system. Additionally, high-speed regeneration technologies play a pivotal role in delivering benefits of time-division techniques to the system. Take long distances into consideration: Fiber properties such as loss and dispersion in the fiber limit the capabilities of the fiber span. Optical amplification, attenuators, and dispersion compensator devices can restore impairments induced by the fiber properties and allow the media to match the heat and light of the equipment chosen. Wavelength converters, wavelength filters, and wavelength division multipliers enable use of a greater capacity of the fiber. Optical regeneration techniques permit clock recovery and lead to full regeneration capabilities in the optical domain, avoiding unnecessary optical to electrical conversions.
Switching and Routing
Backbone networks require switches with tremendous capacity. Switches of this scale are not commercially available today, and much research, configuration, and testing must be done to make them perform a specific job. Total system throughputs of 15 terabits per second are possible with the latest and greatest equipment out there, and more is to come. A challenge for switching systems is to achieve systems that the access network can scale to either the amount of users or the amount of traffic being pumped through the network. Signaling systems for switch control must support a richer communication model than prior generations of switches. User channels can operate at any rate from a couple bits per second to a gig per second and beyond. Multipoint communication channels (one-to-many and many-to-many) are necessary for applications such as video and voice. This requires a signaling and control system that supports a multipoint call model, where a call may include multiple virtual circuits, each with its own individual characteristics. Certain applications place extreme demands on signaling systems.
Layer-specific functionality is now an important role of a switch. When ordering a switch, you now have to determine whether you only want layer 2 or whether layer 3 will be needed. Many switches have the capacity to install software to allow layer 3 capabilities; however, some layer 3 capabilities are tied to the hardware. The author’s favorite layer 3 function is IP multicast through Internet Group Multicast Protocol (IGMP) snooping. IGMP snooping with proxy reporting actively sifts IGMP packets in an effort to reduce the amount of load the router is carrying that provides the multicast. When a join leaves and heads to the next routers, routes are filtered so that the smallest number of information is transported. A switch warrants that the router has one point to contend with, no matter how many listeners are out there in the network. The router is only aware of the most recent member who joined the group. Since a switch creates the layer 1 connection, both virtually and physically, it is no longer required to have systems interconnected to the same hardware or at the same physical location.
Several switches will meet an organization’s needs, and several designs are available to fit in any data center or server room. Some switches, usually just in the home or small office setting, are not rackable and can be located on a desktop or server. Rack-mounted switches are intended to be used in racked environments and can range anywhere from 1 u to an entire cabinet of 42 u (u is the measurement relating to units). A chassis switch, as seen in00000000000000000 Figure 10.1, is one that has either vertical or horizontal blades that allow for hot swapping and many different, custom options. There are many switch management features:
• Bandwidth and duplex settings for circuits
• Simple Network Management Protocol (SNMP) configuration to monitor devices and perform health checks
• Message authentication code (MAC) filtering and port security
• Link aggregation for versions<Elastic Sky X interface (ESXi) 5, trunking for versions of ESXi>5
Switching over to routers (no pun intended), we find that when choosing a router it is important to understand the job the router should perform. Just as there are many protocols, there are many types of routing platforms to accomplish services at the edge, at the distribution layer, or at the core. An edge router operates at the edge of a multiprotocol switching network. In a (MPLS) domain, IP datagrams are forwarded, and routing information is used to determine which labels should accompany the datagram. The packets are then labelled accordingly, and the labeled packets are forwarded into the MPLS domain.
Similarly, an edge router can strip the label and forward the resulting packet over utilizing standard IP forwarding logic. Distribution routers can aggregate traffic from multiple-access routers and are not dependent on site location or geographical region. Often, distribution routers are responsible for enforcing quality of service (QoS) across a (WAN), so they may have considerable amounts of memory installed, multiple wide area network (WAN) interfaces, and extensive on-board data processing routines. These types of routers are also capable of providing connectivity to large groups of servers, whether it be file servers or additional external networks. Core routers operate on the Internet backbone at an organization to transmit lightning fast speeds and to forward IP packets just as fast. Routing also needs to be done at the core level, in some instances, and differs since edge routers have different features and sit at the edge of a network. Conversely, core routers can sit at the edge of a network if the engineer desires to build the infrastructure this way.
Ports and Protocols
Between the protocols User Datagram Protocol (UDP) and Transmission Control Protocol (TCP), there are 65,535 ports available for communication between devices. Among this impressive number are three classes of ports:
Understandably, not all of the ports listed in those three categories are secure. As a result, reference Table 10.1, which enumerates the most commonly used ports and the service/protocol that utilizes the port.
Table 10.1
Well-Known Port Numbers and Their Respective Service Description and Protocol.
| Port | Service/Protocol |
| 7 | Echo/TCP & UDP |
| 9 | Systat/TCP & UDP |
| 15 | Netstat/TCP & UDP |
| 20 | FTP data transfer/TCP |
| 21 | FTP control/TCP |
| 22 | SSH/TCP |
| 23 | Telnet/TCP |
| 24 | Private mail/TCP & UDP |
| 25 | SMT{/TCP |
| 39 | RLP/TCP & UDP |
| 42 | ARPA/TCP & UDP |
| 42 | Windows Internet Name Service/TCP & UCP |
| 43 | WHOIS/TCP |
| 49 | TACACS/TCP & UDP |
| 53 | DNS/TCP & UDP |
| 69 | TFTP/UDP |
| 80 | HTTP/TCP |
| 88 | Kerbos/TCP & UDP |
| 101 | NIC hostname/TCP |
| 110 | POP3/TCP |
| 115 | SFTP/TCP |
| 119 | Network News Transfer Protocol/TCP |
| 123 | NTP/UDP |
| 143 | IMAP/TCP |
| 152 | Background File Transfer Protocol/TCP & UDP |
| 156 | SQL Service/TCP & UDP |
| 161 | SNMP/UDP |
| 162 | SNMPTRAP/TCP & UDP |
| 175 | VMNET/TCP |
| 179 | BGP/TCP |
| 220 | IMAP/TCP & UDP |
| 264 | Border Gateway Multicast Protocol/TCP & UDP |
| 280 | http-mgmt/TCP & UDP |
| 389 | LDAP/TCP & UDP |
| 443 | HTTPS/TCP |
| 500 | Internet Security Assoc and Key Mgmt (ISAKMP)/UDP |
Ideally, when architecting a system, one should plan out the intent for the environment and should only configure the services necessary for the network to pass traffic and servers to perform their intended functions.
Table 10.1 reflects protocols that may be open by default, as well as some that are necessary for the intended purpose of the environment. When installing equipment in Section I, it is imperative that the engineer be aware of the ports that need to be open for each device or piece of software and, if needed, can be referenced in the device white paper. It is also essential to recognize the variation between the numerous types of attacks and the respective ports on which such attacks would be executed. It is necessary to monitor the ports that are open in an effort to detect protocols that may leave the network vulnerable. Running netstat on a workstation will allow one to view the ports that are running and that are open. In addition, running a local port scan will also portray which ports are exposed.
Many protocols may still be used during an installation where system administrators and users are not aware, and those may leave the network vulnerable. Simple Network Management Protocol (SNMP) and Domain Naming Service (DNS) were deployed years ago, yet still present security risks. SNMP can be utilized for monitoring the health of network equipment, servers, and other peripheral equipment. However, susceptibilities associated with the SNMP derive from use of SNMP v1. Although such vulnerabilities were raised years ago (about 10 years), exposures are still reported while utilizing the current version of SNMP. Liabilities allow for authentication evasion and execution of proprietary code when utilizing SNMP. The SNMP infrastructure has three components:
Where the devices are concerned, they load the agent, which in turn assembles information and forwards it to the management servers. Network management servers collect a substantial amount of significant network information and are possibly targets of attacks due to their use of SNMP v1, which is not secure. A community name is a point of security; however, it may be similar to a password. Usually, the community name is public and is not secure, nor is it changed, thus permitting information to leak out to invasions. Conversely, SNMP v2 uses Message Digest Version 5 (MD5) for authentication. The transmission can also be encrypted. SNMP v3 is used across firms as the criteria; however, a number of devices are not compatible and are left to use SNMP v1 or SNMP v2.
SNMP assists spiteful users to learn too much about a system, making password speculations easier. SNMP is often disregarded when checking for vulnerabilities due to the User Datagram Protocol (UDP) ports 161 and 162. Ensure network management servers are physically secured and secured on the network layer. Consider utilizing a segregate management subnet, protecting it by using a router with an access list. Unless the service is required, it should be shut off by default. In order to defend a network infrastructure from incidents aimed at obsolete or unfamiliar ports and/or protocols, remove any unnecessary protocols while creating access-control lists to allow traffic on defined ports. This eliminates the possibility of any obscure protocols being utilized, while minimizing the danger of an incident.
Threats
Hijacking occurs when an intruder takes control of a session between a server and the client. The communication starts when a middle-man attack adds a request to the client, resulting in the client getting kicked off the session. Meanwhile, the rogue workstation talks with the server, and the attacker intercepts the source-side packets, replacing them with fresh packets that are sent over to the destination. This type of hijacking, referred to as TCP/IP hijacking, most commonly occurs during telnet and Web sessions when security is nonexistent, or lacking, and also when session timeouts are improperly configured.
During the course of a Web session, cookies are commonly used to authenticate and track users. While the authentic session is in session, an attacker may attempt to hijack a session by loading a modified cookie in the session page. Session hijacking may also ensue when a session timeout is set to be an extended period of time; this gives an attacker a chance to hijack a session. Telnet-type plaintext connections create the ideal situation for TCP hijacking. In an instance like this, when an attacker surveys the data passing in the TCP session, the attacker can take control of the user’s session; this is yet another reason why it is called session hijacking. When a user is forced to authenticate prior to allowing transactions to occur, it helps to prevent hijacking attacks. Protection mechanisms include the use of unique sequence numbers (USNs) and Web session cookies. The more unique the cookies, the harder it is to crack and hijack. Additional preventative measures for this type of attack include the use of encrypted session keys and Secure Socket Layer (SSL) encryption.
Spoofing
Spoofing is a method of providing false identity information to gain unauthorized access. This can be achieved by modifying the source address of traffic or source of information. Spoofing seeks to bypass IP address filters by setting up a connection from a client and sourcing the packets with an IP address that is allowed through the filter. Blind spoofing occurs when the attacker only sends data and only makes assumptions of responses. Informed spoofing is when the attacker can participate in a session and can monitor the bidirectional communications. Services that can be spoofed are:
Web spoofing occurs when an attacker creates a convincing, fabricated copy of an entire Web site. The fabricated Web site will appear just as a real Web site would, and it has all the pages and links. The attacker controls the fabricated Web site so that all network traffic between the user’s browser and the site goes through the attacker. In the situation for email spoofing, a spammer or virus can forge the email packet information in an email so that it appears that the email is coming from a trusted host, a friend, or even your own email. When one leaves their email address at an Internet site, or exchange email with others, a spoofer may be able to use your email address as the sender address to blast spam. File transfer spoofing involves the FTP service, and FTP is sent in clear, plain text. The data can be intercepted by an attacker. The data can then be viewed and altered prior to sending it over to the receiver. These types of attacks are intended to pull information from a network of users to accomplish a more comprehensive attack. By setting up a filter to deny traffic originating from the Internet that shows an internal network address, using the signing capabilities of certificates on servers and clients will allow Web and email services to be more secure. Using an Internet Protocol Security (IPSEC) tunnel adds more security between critical servers and their clients by preventing these types of attacks from transpiring.
Intercepting Traffic
The man in the middle attack occurs when an attacker intercepts traffic and deceives the parties at both ends into believing they are communicating with one another. An attack like this is possible due to the nature of the three-way TCP handshake process using SYNchronize (SYN) and ACKnowledge (ACK) packets. Since TCP is a connection-oriented protocol, a three-way handshake takes place when establishing a connection and when closing the session. When a session is established, the client sends a SYN request; then the server sends an ACK (sometimes referred to as SYN-ACK-ACK), completing the connection. During this process, the attacker initiates the man-in-the-middle attack by using a program that appears to be a server to the client and appears to be a client to the server. In telnet and wireless communications, this attack is common. This is a difficult attack to perform due to physical routing matters, TCP sequencing number, and speed. Since the hacker must sniff both sides of the connection simultaneously, programs have been developed to aid the attacker in order to make man in the middle easier.
If an attack is performed on an internal network, physical access to that network is mandatory. By ensuring that access to wiring closets and switches are restricted, and that they’re behind locked doors, physical access becomes difficult. Once the physical segment of the network has been secured, services and resources may allow a system to be inserted into a session, so those will need to be protected. DNS can be compromised and used to redirect the initial request for service, providing an opportunity to execute the man-in-the-middle attack. DNS access needs to be restricted, allowing read-only access for anyone but administrators. By using encryption and security controls and protocols, organizations can prevent these types of attacks on their infrastructure.
Packet Capturing
Packets are captured by sniffing devices in a replay attack. Once the relevant information is extracted, packets are put back on the network. An attack such as this can be used to replay a bank transaction or other comparable types of data transfers in the hopes of replicating or changing activities, such as transfers or deposits. Protecting oneself against a replay attack will involve some type of timestamp associated with the packets, or time-valued nonrepeating serial numbers. Additionally, integrating secure protocols, such as IPSEC, prevents replays of data traffic while providing authentication and data encryption.
Denial of Service
When resources have been disrupted or services that a user would expect to have access to are compromised, they have experienced a denial-of-service attack. These types of attacks are executed by manipulating protocols and can occur without the need to be validated by the network. An attack will usually involve flooding the listening port on a machine with packets. The purpose is to make that workstation so busy processing the new connections that it cannot process legitimate service requests. Several tools are available on the Internet that will produce a denial-of-service attack. IT administrators use them daily to test connectivity and troubleshoot issues on their networks, whereas malicious users will use the tool to cause connectivity issues. Some examples of DoS attacks are:
• SYN flood—This attack takes advantage of the TCP three-way handshake. A source system will send a flood of synchronization (SYN) requests and will never send the final acknowledgment (ACK), creating partially open TCP sessions. Since the TCP stack waits before resetting the port, the attack overflows the destination workstation connection buffer, making it impossible to service requests from valid users.
• Ping flood—This attack attempts to block service or reduce activity on a host by sending ping requests directly to the target. Variations of these attacks include the ping of death, where the packet size is too large and the system is unable to handle the number of packets.
• Ping/Smurfing—This attack is based on the Internet Control Message Protocol (ICMP) echo reply function. The common name is ping, the command line tool utilized to invoke the function. The attacker sends ping packets to the broadcast address of a network, replacing the original source address in the ping packets with the source address of the target, causing a flood of traffic to be sent to the unsuspecting network device.
• Fraggle—This attack is similar to smurfing. The difference is that fraggle uses UDP rather than ICMP. The attacker sends spoofed UDP packets to broadcast addresses, just as the smurf attack does. These UDP packets are directed to port 7, echo, or port 19, Chargen. When connected to port 19, a character generator attack can be run. Refer to Table 10.1 for the commonly exploited ports.
• Land—This attack exploits a behavior in the operating systems of several versions of Windows, Unix, Mac, and Cisco IOS with respect to their TCP/IP stacks. The attacker spoofs a TCP/IP SYN packet to the victim system with the same source and destination IP address and the same source and destination ports. This confuses the system as it attempts to respond to the packet.
• Teardrop—This form of attack targets a known behavior of UDP in the TCP/IP stack of some operating systems. The Teardrop attack will send fragmented UDP packets to the target with odd offset values in subsequent packets. When the operating system attempts to rebuild the original packets from the fragments, the fragments overwrite each other, causing confusion. Since some operating systems cannot elegantly handle the error, the system will either crash or restart.
DoS attacks come in many flavors, shapes, and sizes. Take the first step to protect the firm from an attack: Understand the types of attacks and the nature in which they operate.
Distributed Denial of Service
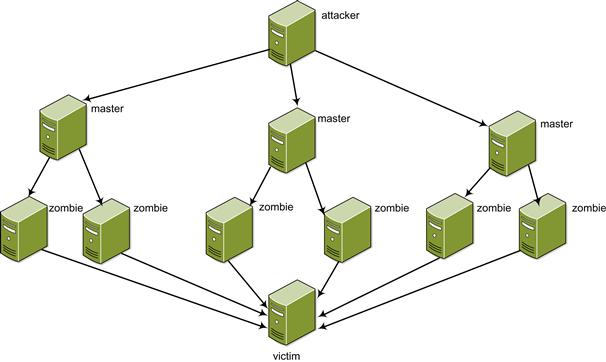
A modest expansion of denial of service can be referred to as distributed DoS attacks. Masters are computers that run the client software, where zombies will run the software. The attacker will create a master, which in turn creates a large number of zombies, or recruits. The software that runs on the zombies can launch multiple types of attacks, such as UDP or SYN flooding on a particular target. Figure 10.2 depicts a distributed DoS attack.
Although distributed DoS attacks usually come from the outside of the network to deny services, the impact of the attacks displayed inside the network should also be cogitated. Internal distributed DoS attacks allow disgruntled employees or malicious users to disrupt services without any outside influence or interaction. To help protect your network, set up filters on external routers to drop packets involved in these types of attacks. Also, set up an additional filter that denies traffic originating from the Internet but showing an internal IP address. By doing this, ping and some services are lost to test network connectivity, but this is where administrators should be on a separated network segment than users and would be on a segment where the filtering did not occur. If the operating system supports it, one can reduce the amount of time before the reset of an unfinished TCP connection. Doing so makes it harder to keep resources unavailable for extended periods of time.
Tip: In the case of a distributed DoS attack, it is best to get in touch with your service provider so that they can divert traffic or block traffic at a higher level.
ARP Poisoning
Every network card has a 48-bit address that is unique and hard-coded into the card. For network communications to occur, this hardware address must be associated with an IP address. Address resolution protocol (ARP), which operates at layer 2 (data link layer) of the Open System Interconnection (OSI) model, associates MAC addresses to IP addresses. ARP is a lower-layer protocol that is straightforward and consists of requests and replies without validation. However, this simplicity leads to a lack of security.
When using a protocol analyzer to look at traffic, you will see an ARP request and an ARP reply, which are the two fundamental parts of ARP communication. There are also reverse ARP (RARP) requests and RARP replies. Devices maintain an ARP table that contains a cache of the IP addresses and MAC addresses that the device has already correlated. The host device searches its ARP table to see whether there is a MAC address corresponding to the destination host IP address. When there is no matching entry, it broadcasts an ARP request to the entire network. The broadcast is seen by all systems, but only the device that has the corresponding information replies. However, devices can accept ARP replies before even requesting them. This type of entry is known as an unsolicited entry because the information was not explicitly requested.
Because ARP does not require any type of validation, as ARP requests are sent, the requesting devices believe that the incoming ARP replies are from the correct devices. This can allow a perpetrator to trick a device into thinking any IP is related to any MAC address. In addition, they can broadcast fake or spoofed ARP replies to an entire network and attack all computers. This is known as ARP poisoning. Simply worded, the attacker deceives a device on your network, poisoning its table associations of other devices.
ARP poisoning can lead to attacks such as denial of service, man in the middle, and MAC flooding. Denial of service and man in the middle were discussed earlier in this chapter. MAC flooding is an attack directed at network switches. This type of attack is successful because of the nature of the way all switches and bridges work. The amount of space allocated to store source addresses of packets is limited. When the table becomes full, the device can no longer learn new information and becomes flooded. As a result, the switch can be forced into a hub-like state that will broadcast all network traffic to every device in the network. Macof is a tool that floods the network with random MAC addresses. Switches may get stuck in open repeating mode, leaving the network traffic susceptible to sniffing. Nonintelligent switches do not check the sender’s identity, thereby allowing this condition to happen.
A lesser vulnerability of ARP is port stealing. Port stealing is a man-in-the-middle attack that exploits the binding between the port and the MAC address. The principle behind port stealing is that an attacker sends numerous packets with the source IP address of the victim and the destination MAC address of the attacker. This attack applies to broadcast networks built from switches. ARP traffic operates at layer 2, the data link layer of the OSI model, and is broadcast on local subnets. ARP poisoning is limited to attacks that are local, so an intruder needs either physical access to your network or control of a device on your network. To mitigate ARP poisoning on a small network, you can use static or script-based mapping for IP addresses and ARP tables. For larger networks, utilize equipment that offers port security. By doing so, one can only permit one MAC address for each physical port on the switch. In addition, you can deploy monitoring tools or an intrusion detection system (IDS) to signal when suspicious activity occurs.
DNS Poisoning
DNS poisoning enables a perpetrator to redirect traffic by changing the IP record for a specific domain, thus permitting the attacker to send legitimate traffic anywhere he chooses. This not only sends a requestor to a different Web site, but also caches this information for a short period and distributes the attack’s effect to the servers users. DNS poisoning may also be referred to as DNS cache poisoning because it affects the information that is cached.
Because all Internet requests begin with a DNS query, if the IP address is not known locally then the request is sent to a DNS server. There are two types of DNS servers: authoritative and recursive. DNS servers share information, but recursive servers maintain information in their cache. This means caching or recursive servers can answer queries for resource records even if they cannot resolve the request directly. A flaw in the resolution algorithm allows the poisoning of DNS records on a server. All an attacker has to do is delegate a false name to the domain server along with providing a false address for the server. For example, an attacker creates a hostname hackattack.gov. Next, the attacker queries your DNS server to resolve the host hackattack.gov. The DNS server resolves the name and stores the information in its cache. Until the zone expiration, any further requests for hackattack.gov do not result in lookups but are answered by the server from its cache. It is now possible for the attacker to set your DNS server as the authoritative server for the zone with the domain registrar. If the attacker conducts malicious activity, the attacker can make it appear that your DNS server is being used for those malicious activities.
DNS poisoning can result in many different implications. Domain name servers can be used for distributed DoS attacks. Malware can be downloaded to an unsuspecting user’s computer from the rogue site, and all future requests by that computer will be redirected to the fake IP address. This could be used to build an effective botnet. This method of poisoning could also allow for cross-site scripting exploits, especially since Web 2.0 capabilities allow content to be pulled from multiple Web sites simultaneously.
To minimize the effects of DNS poisoning, check the DNS setup if you are hosting your own DNS. Be sure the DNS server is not open-recursive. An open-recursive DNS server responds to any lookup request, without checking where the request originated. Disable recursive access for other networks to resolve names that are not in your zone files. Also, use different servers for authoritative and recursive lookups and require that cached information is discarded except from the com servers and the root servers. As far as users are concerned, educate them. However, it is becoming increasingly difficult to spot an issue by watching the address bar on an Internet browser. Therefore, operating system vendors are adding more protection by notifying the user that a program is attempting to change the system’s settings, thus preventing the DNS cache from being poisoned.
2 Attacks and Countermeasures
To secure a network, a firewall can be successfully implemented and utilized whether it is software or hardware based. The purpose of a firewall is to control the incoming and outgoing traffic by analyzing packets and determining whether or not a rule set will allow the traffic in or not.
Network Firewall
In Figure 10.3, the firewall is protecting the network, rather than leaving it directly exposed to the Internet. The firewall will sit in conjunction with a network device and will serve as a gateway between two networks.
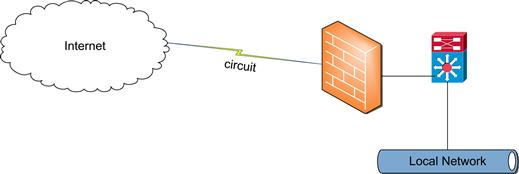
Figure 10.3 A firewall is placed between the outside world and the internal local network components.
Firewalls inspect all traffic routed between two networks to determine whether or not that traffic meets predetermined criteria. If it does, the traffic is allowed through and routed to the appropriate destination. Otherwise, the traffic is blocked. Firewalls can also manage public access to private network resources, such as host applications. Hard drive space on firewalls is becoming increasingly important since log entries can grow to be terabytes of data, depending on the amount of traffic on your network. Consider your logging setup to log every attempt to enter into and exit the network. When half the company is surfing the Internet during their lunch time, one can fathom how large the log files can grow to be. Firewalls can also filter packets specific to network types and is known as protocol filtering. Since the decision to forward or reject traffic is dependent on the protocol used, a user attempting to access a server via HTTP, FTP, or telnet will either be allowed or denied based not only on their access to the server, but also on whether the firewall allows specific protocol access to that target server.
Firewalls use two approaches: Allow all traffic unless said traffic meets a certain criteria or deny all traffic unless it meets a certain criteria. Additionally, firewalls can fit into four categories: packet filters, circuit-level gateways, application-level gateways, and stateful multilayer inspection firewalls. Packet filtering firewalls sit at the Network Layer, or the IP layer of the TCP/IP Layer. Depending on the packet criteria, the firewall can drop the packet, forward it, or send a message to the initiator. Rules can include source and destination IP address, source and destination port number, and protocol used. The advantage of packet filtering firewalls is that they are affordable and have no impact on network performance. If a higher level firewall is used, packet filtering rules will not add any overhead to the network traffic. A lower level firewall will not support many other features that an organization may desire, such as network address translation (NAT). NAT is used in many different types of companies, whether it is a trading firm or a law firm. Understanding private and public IP addressing is the first step in translating network addresses. Your internal network will communicate with internal IPs; however, if you have a client that needs to access a server on your network, giving them the internal IP on your network will not allow them access unless they’re on your virtual private network (VPN). So, translating that IP to a public IP will allow the user to access that internal server, but the firewall is the tool that gives the user outside access by translating the IP. Additionally, the firewall needs to know that 66.55.44.123 is a public IP that belongs to internal IP 10.10.10.100. How will the user access the server? If a user wants to RDP to 10.10.10.100, the firewall must give RDP access to that server. Specific ports and protocols are allowed at the firewall level, too. When implementing a firewall, one must consider the following measures:
• Determine the access denial methodology: Most recommend denying all access by default right at the start. That would have a gateway that routes no traffic and is a brick wall with no doors in it. If you prefer a solid, secure environment, this is the first step, and then you can allow access from here.
• Determine inbound access: If all of your Internet traffic originates on the LAN, a NAT router will block all inbound traffic that is not in response to requests originating from within the LAN. As mentioned in the preceding example, only the external IP address is given to a client. The internal IP addresses of hosts behind the firewall are never revealed to the outside world, which makes intrusion difficult. Most hosts are nonpublic IPs, so it would make it difficult unless the attacker was on the internal network; however, it is the best practice. Packets coming in from the Internet in response to requests from local hosts are addressed to dynamically allocate port numbers on the public side of the NAT router. These numbers change rapidly, making it nearly impossible for an intruder to make assumptions of which port number they could use. You may also want to determine which criteria can be used when a packet originates from the Internet and whether or not to allow it into the LAN. The more rigorous the rules, the more secure your network will be. Ideally, you’ll know which public IP addresses on the Internet originate inbound traffic, and by limiting inbound traffic to packets originating from specific hosts, you decrease the likelihood of hostile intrusion. Going further, earlier protocols were mentioned, and limiting communication-based off-protocol sets like HTTP or FTP adds greater security.
• Determine outbound access: When users only need access to the Internet, a proxy server may provide enough security, with access granted based off user rights. This type of firewall can be a great deal to manage since it requires manual configuration of each Web browser on every machine. Outbound protocol filtering can also be transparently achieved with packet filtering and no sacrifice on security. If you are using NAT without inbound mapping or traffic originating from the Internet, then it is possible to allow users access to all services on the Internet without compromising security. Consequently, there is a risk of employees acting irresponsibly through email or external hosts, but that is a management or HR issue and not IT.
Proxies
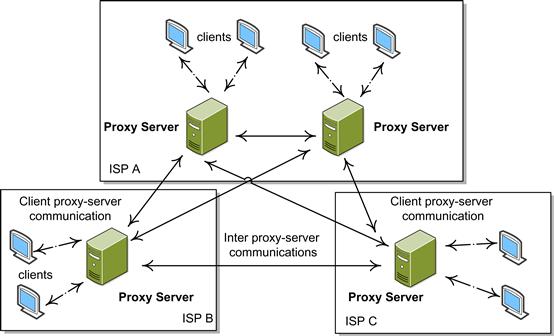
Proxy servers are capable of functioning on dedicated hardware or as software on a utility server. It acts as a transitional point of communication between two clients attempting to reach out to other servers. For example, if a client connects to a proxy server, requesting some file or connection, the proxy server will assess the request in an effort to simplify and regulate the intricacy of the communication, as shown in Figure 10.4.
Proxies can perform just as a firewall would by handling connection requests for packets coming into an application and by blocking any other packets. A proxy server can be thought of as a gateway from Network A to a certain network application, while acting as a proxy for the user on the network. When an administrator properly designs the function of a proxy, it is much more difficult for an outside attacker to access the internal network. However, an attacker may utilize a highly available system and use it as a proxy for their selfish means. This allows the proxy to deceive other machines, forcing them to think the proxy is safe and on their network, or their proxy. Utilizing internal, private IP addresses adds another layer for security; conversely, hackers could spoof the IP’s attempt to gain access and transmit packets to a network.
Proxy servers have become prevalent in the gaming community since real-time, Internet gaming surfaced. Considering how many kids and adults are into gaming, the network for real-time streaming multiplayer gaming requires a low-latency proxy server-network topology. Client-server or peer-to-peer topologies provide a variety of positive aspects and can be applied intricately, leading to their high acquiescence for computer gaming. Both models also have many disadvantages, which results in weak QoS and constrains robust gaming architectures where there are a high amount of users. As soon as the player numbers increase, client-server and peer-to-peer topologies do not scale well. Additionally, the server in a client-server framework forms a single point of failure for the entire session. While the peer-to-peer method eradicates the problem of a single point of failure, a hacked client can cheat, since acquiesced game updates are not filtered by a server instance and concealed information becomes readily available to the player.
Architecting a proxy server setup, stemming from a peer-to-peer server-network, is shown in Figure 10.5. Utilizing several interconnected proxy servers for a one-user gaming session shows each proxy server having a full view of the comprehensive game architecture. Each client communicates with a single proxy, sending user selections and obtaining updates of the game status.
Proxy servers process user actions and forward them to other proxies, manipulating multicast at the IP or application level to synchronize the disseminated game state. With regard to low-latency Internet-centered sessions, proxy servers need to be disbursed among different Internet service providers (ISPs), such that each client will connect to a proxy at its local ISP. Through testing, the author has set up the servers manually; however, testing proves that a dynamic setup of proxies falls in line with user demand and quick response times. Rather than replicating a gaming world, one could partition the approach across servers, compelling clients to exchange servers depending on their region. This approach may work well to accommodate slower flow of traffic, but it cannot be applied to the low-latency, graphic-intensive world. Pauses are annoying for users, as are noticeable server changes. Because the proxy has a wide spectrum to view the game state, best practices avoid a proxy server-network to attempt multiple reconnects during one session.
To manage replication utilizing proxy servers in a gaming infrastructure, ensure that the architecture is scalable, responsive, and consistent, simulating large amounts of data. Although trade-offs may be involved, implementing strong consistency patterns will increase the amount of inter-proxy communication. For example, proxies would order changes of the game state using timestamps or a physical clock mechanism. This would delay the transmission of acknowledgments of user actions to clients, thus reducing the responsiveness of the game. Talk about detrimental; especially when you’ve stood in line for 18 hours outside of the store, and now you’re competing with 500,000 other users during the first hour of the game. A scalable, distributed model with real-time performance can only be achieved if all the servers do not talk to each other simultaneously; nonetheless, servers must be able to share the same data at all times. To implement this architecture, only allow one process to alter specific parts of replicated data (shown in Figure 10.6). Changes must be propagated to other processes, certifying the reliability of the replicated state immediately as the message arrives. The process in Figure 10.6 can be described by following these steps: (1) user actions are transferred from clients; (2) the server checks to see if the input is authorized to block cheating before changing the state; (3) consistency for the altered part of the game state is guaranteed, and the clients receive acknowledgments for movement commands in a short amount of time; (4) informs proxies about updating position values; (5) update local copies consequently; (6)in the case of interactions, notified proxies also check whether local clients are affected, and if local clients are affected, the proxy updates the game state of its local client and informs other servers; and (7) for all state updates received from other proxy servers, each proxy evaluates which local clients are affected and informs them. The architecture presented allows for management of a distributed state, with efficient synchronization of the game state in conjunction with fast acknowledgment of user actions.
3 Summary
This chapter focused on how security is presented to protect the infrastructure. Smart grid cybersecurity must address not only deliberate attacks, such as from disgruntled employees, industrial espionage, and terrorists, but also inadvertent compromises of the information infrastructure due to user errors, equipment failures, and natural disasters.
Infrastructure Security Tasks Checklist
The primary intent of this chapter is to increase your awareness of specific technologies that secure the foundation of your infrastructure. Although this part of the chapter is called a checklist, each of the tasks in the checklist (An Agenda for Action for Implementing Infrastructure Security Tasks) requires so much elaboration that it is easy to lose the thread of organization. The guiding structure is to first summarize the major types of security vulnerabilities and mitigation techniques in general, and then traverse the OSI communication reference model layers (previously discussed) while discussing specific security considerations.
This chapter also addressed the critical cybersecurity needs in the areas of encryption key management, security requirements, testing criteria for remote upgrades, and privacy recommendations for third-party data usage. The chapter also provided foundational cybersecurity guidance, outreach, and foster collaborations in the cross-cutting issue of cybersecurity in the smart grid. Remember that a system is only as secure as its most vulnerable path, and it is difficult (if not impossible) to build a secure voice solution if the infrastructure foundation is insecure.
Finally, let’s move on to the real interactive part of this chapter: review questions/exercises, hands-on projects, case projects, and optional team case project. The answers and/or solutions by chapter can be found in the Online Instructor’s Solutions Manual.
Chapter Review Questions/Exercises
True/False
1. True or False? Since the inception of technology, data security revolves around cryptography.
2. True or False? Cipher text and secret keys are transported over the network, and can be harvested for analysis, and furthermore to impersonate a source or, in a worst case, cause a service acceptance.
3. True or False? Backbone networks require switches with tremendous capacity.
4. True or False? Between the UDP and TCP protocols, there are 5,535 ports available for communication between devices.
5. True or False? Hijacking occurs when an intruder takes control of a session between a server and the port.
Multiple Choice
1. What is a method of providing false identity information to gain unauthorized access?
2. What attack occurs when an attacker intercepts traffic and deceives the parties at both ends into believing they are communicating with one another?
3. What are captured by sniffing devices in a replay attack?
4. When resources have been disrupted or services are compromised that a user would expect to have access to, they have experienced a:
5. A modest expansion of denial of service can be referred to as:
Exercise
Problem
Which Ethernet ports require 802.1x authentication?
Hands-On Projects
Project
What 802.1x authentication mechanism should one use?
Case Projects
Problem
Do all clients support 802.1x?
Optional Team Case Project
Problem
Does 802.1x have security vulnerabilities?