Fundamentals of Cryptography
Scott R. Ellis, EnCE, RCA, RCIA, kCura Corporation
This chapter discusses how information security is the discipline that provides protection of information from intrusion and accidental or incidental loss. It also provides a framework for the protection of information from unauthorized use, copying, distribution, or destruction of data. Cryptography plays a key role in supporting the protection of captured data from prying eyes. It does nothing to actually protect the encrypted data from being intercepted.
Keywords
cryptography; encryption; privacy; physical security; logical security; ranking; risk; protocols; audits; confidentiality; integrity; availability; block ciphers; algorithms; cryptographic standards
1 Assuring Privacy with Encryption
Encryption provides a secure layer, at the storage byte level, under which information can be secured from prying eyes (see checklist: An Agenda for Action for Implementing Encryption and Other Information Security Functions). Data, or “plaintext” as it is called in cryptography, is rendered into cipher text through a ciphering process. Most importantly, encryption protects stored data. Files such as database data files, spreadsheets, documents, and reports can contain critical information—information which, if lost, could cause damage to:
Ultimately, the loss of enough data, especially were it due to incompetence, could be a business-ending event. Inadvertent disclosure of data, especially personally identifiable data, can mean financial liabilities and the need for restitution to injured parties.
Ensuring that files are encrypted in storage, everywhere, allows the files to be protected in the event of a breach of physical security. Should a hacker gain access to a system, database encryption will prevent her from accessing the database files. Whole-disk encryption will prevent her from accessing drive shares and pulling excel spreadsheets.
The past decade has seen additional liabilities and exposures of sensitive data in the form of lost backup tapes, lost laptops, and recycled computers that were not destroyed, encrypted, or wiped. After a third-party courier service lost a box of backup tapes, Bank of New York Mellon Corp. officials implemented a policy to encrypt data on all storage devices. Furthermore, they said they would limit the type and amount of confidential client data stored on tape backups. It took two losses of unencrypted data before the policy was launched.
Unfortunately, far too many companies wait for disaster to strike before they begin to think about all of the things they really need to do to ensure, or at least substantially mitigate, their risk of data loss. There are three primary reasons why industry executives are reticent to implement encryption:
1. The cost of doing it—the complexity of setting it up
2. Their feeling that it can’t happen to them
3. The fear of data loss due to key loss—an inability to decrypt the data
The cost of implementing an encryption policy pales in comparison to the cost of a data loss due to a breach, or due to release of data simply because Joe Smith left his laptop on the train. In an interesting, real-life situation, the author of this chapter did, in fact, once find a small box of hard drives in a bag on a train. The drives were labeled backup01, backup02, and backup03. Fortunately, the box had a CDW Computer Centers, Inc. shipping label that identified a client number. After reaching out to a friend at the computer company on the label, who contacted the owner (a large university library), a reunion was arranged. The kindness and responsibility of strangers cannot serve, however, as a failsafe. If anything, the loss of ALL the backup data was narrowly averted. According to the library executive, the backup drives held everything. She also promised that the policy would be changing immediately.
Encryption also introduces an additional level of difficulty in the event of corruption. Certain segments of the drive, if they become corrupted, can make retrieval of the data more challenging. This necessitates the storage, offsite, of secure, unencrypted backups. This may seem contrary to the purpose of this chapter, but consider that:
a. The data must be delivered to the unencrypted DR site encrypted.
b. Access to the unencrypted backup site should be manned access only with biometric access controls and no Internet or network connectivity.
c. As physical security and controls increase, the need for encryption decreases.
Such a high level of security allows the data to be under a much higher degree of control than the data in production data centers. A regular program of data movement, refreshing, and redundancy checks should be in place to ensure against data corruption. Placing data on a disk is no guarantee that two years later (if the disk has sat idle) the data will be coherent. Data can become corrupt just sitting on a disk.
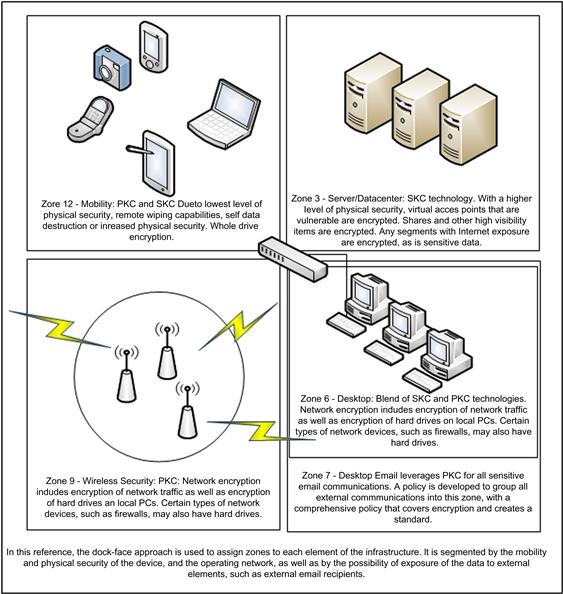
Organizations should consider and design a program that understands and includes recipient and sender environments, and ensures that data encryption and decryption are as seamless and unintrusive as possible. In Figure 13.1, a clock-face approach to security balances the need for physical security against the need for encryption. Observe how, as the network segment approaches the 12th hour, everything is encrypted.
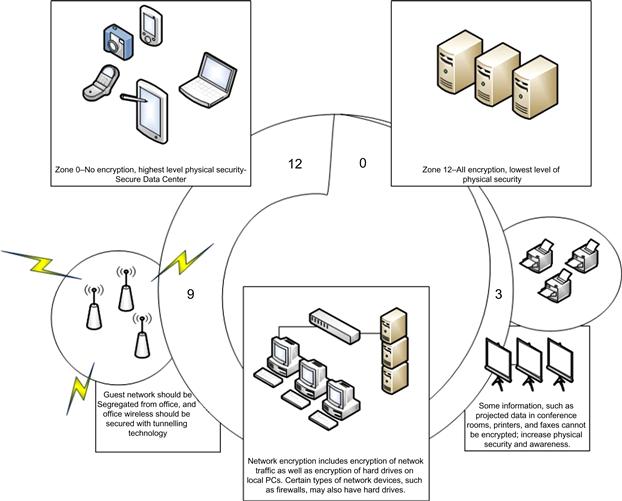
Figure 13.1 In a clock-face model, the most physically secure enterprise segments are at the zero hour, with the possibility of imminent attack or loss increasing up to the 12th hour. Note that the crescent line indicates increasing risk of loss, as well as a decrease in physical security.
This model only inserts five categories of devices and activities. Each “hour” could conceivably have its own protocols. The analogy of “hour” is used by this author simply to explain and set forth this model as one plausible way of making it easier to think about security, and thus categorize applications based on the activity or on the type of encryption required.
Physical Versus Logical Security
In this clock-face model, the level of physical security decreases the need for encryption security. Physical and data security are applicable to each of the items shown in this diagram. For some items, such as digital cameras, security can get complicated. GPS locators and remote wiping are available for many personal devices, but digital cameras, for example, do not have any sort of a mechanism for encrypting their memory cards.
Consider ranking things in order of “Needs no encryption” to “Must be encrypted.” As mentioned previously, the security requirement for encryption decreases as physical security increases. For example, a computer, sealed in cement and sunk to the bottom of the Mariana trench needs not be encrypted. Cell phones and laptops, on the other hand, should be. Create a panel of advisors to assist with the ranking. Depending on the workplace and the industry, the threat level of various areas could vary. Moving items from one position on the clock face to a lower number effectively diminishes the immediate need for encryption. This can be accomplished by increasing physical security. For example, whether a PC in an office is more deserving of encryption than a data center that is hooked into the Internet and has lots of virtual traffic through it may be dependent on other factors. Increasing the security in the office may effectively reduce the need for encryption to a level beneath that of the data center.
Deciding which area is more likely to be attacked first requires some decision making—decisions that may, down the road, turn out to be wrong. Planning the implementation requires a healthy imagination, not a paranoid one. Too much paranoia can bog down the project, but a healthy dose of possible, real-life scenarios and a little imagination can make planning both enjoyable and effective. See the sidebar, Using Imagination to Effectively Plan, for an example scenario cooked up by the author with one of his coauthors.
As shown in Figure 13.1, devices can (generally) be ordered by Highest Concern for Encryption and least physical security to Least Concern for Encryption and highest physical security:
• Cell phones, PDAs, memory sticks, USB drives, tablets
• Data Center Web farm (financial data)
• DR site (of course, in a failover, encryption protocols should be activated)
Most organizations will need to take into account their own strategy. This allows for deployment of a planned implementation of encryption in an orderly and risk-biased way.
The Confidentiality, Integrity, and Availability (CIA) Model and Beyond
CIA, or confidentiality, integrity, and availability, is a model for establishing security and risk. It dovetails into the clock-face model presented herein in that CIA provides the litmus tests needed for assessing into which zone things must be placed.
Confidentiality
To the degree that some information must be made available only to a certain group of people, this determines the level of restriction needed. Unauthorized access to information must be prevented. In areas of the network where information transmissions are uncontrolled and breach the perimeter, encryption of confidential data must occur.
This is especially true of wireless networks. Frequently, wireless networks are set up with weak, flawed, or no security.
Integrity
Information should never be transmitted in ways that may disturb the integrity of the files or data. Unauthorized personnel should not be able to destroy or alter data. Hash values for files should be stored and transmitted with the file and accessed programmatically for validation.
Availability
Information that is so locked down that it is nearly inaccessible reduces the efficiency of operations. Information should be readily accessible to those who are authorized to view it.
Cryptographic Standards and Protocols: Block Ciphers—Approved Algorithms
Block ciphers utilize mathematical formulas that, when operated in cryptography, are called algorithms, and different flavors of algorithms are called ciphers. Block ciphers are a type of algorithm that converts plaintext into cypher text. They are called “block” ciphers because they work by enciphering a preset size of text at a time. Three well-known block ciphers are AES, Triple DES, and Skipjack.
AES
AES, published in FIPS 197 in February 2001, replaced DES. The government reviewed several different algorithms, but ultimately chose the Rijndael encryption algorithm to serve as a FIPS-approved symmetric encryption algorithm. The primary consideration here is that, by virtue of publishing under FIPS, the government created a standard whereby the U.S. government organizations (and others) may protect sensitive information.
Federal agencies also review the Office of Management and Budget (OMB) guidance, which suggests that AES is a standard that will be secure for 20 to 30 years. Furthermore, the OMB guidance warns agencies that the loss of cryptographic keys presents a risk to the availability of information needed to accomplish critical mission tasks and objectives.3
In today’s world of extremely complex communication systems, the need for a full understanding of security, which includes a detailed understanding of the business itself first, has never been more apparent. The ability to protect and secure information depends entirely on the ability of those doing the protecting to understand the business. It cannot be solely dependent on the mathematical strengths of the encryption algorithm or the ability of someone to classify certain information. Likewise, you cannot count on the classification of the material to always be an accurate predictor of which encryption algorithm to use. Flexibility MUST be built into the system. There MUST be a way for the governing organization to stop, look, and listen. Many factors must be considered in choosing an algorithm and process for encryption, and these factors may, of course, change over time. An inflexible policy risks failure. The following factors are most relevant:
• How well the implementation of the algorithm will perform in specific software, firmware, or hardware configurations;
• The ability to develop a functional key management system, or of the algorithm to mesh with an existing solution;
• The fragility of the of the information to be protected; and/or
• Any requirements to interoperate, globally, where encryption algorithm restrictions may exist.
Considered in total, these requirements demand the implementation of a flexible implementation and policy that mixes the best of breed software with best practices derived from the individual business requirements.4
2 Summary
Ultimately, the best encryption protocol would be completely seamless, effective, and transparent. A seamless encryption utility would provide, across the enterprise, a single-console approach to management. Phones, PDAs, hard drives, servers, network communications, and the like, all could be added to the encryption layer with the drag of a mouse. An effective algorithm is one that is not just unbreakable in the near foreseeable future, but rather, is simply unbreakable. A transparent system would provide encryption services without any observation by the user. They would not know, nor would they have reason to know, that their emails are encrypted using PKC technology. Unfortunately, modern information technology has not been able to provide any sort of all-encompassing program for managing secure communications. In the meantime, it is up to information technologists to cobble together a best of breed solution that protects and secures information simultaneously.
Finally, let’s move on to the real interactive part of this chapter: review questions/exercises, hands-on projects, case projects, and optional team case project. The answers and/or solutions by chapter can be found in the Online Instructor’s Solutions Manual.
Chapter Review Questions/Exercises
True/False
1. True or False? Encryption provides an insecure layer, at the storage byte level, under which information can be secured from prying eyes.
2. True or False? Ultimately, the gain of enough data, especially were it due to incompetence, could be a business-ending event.
3. True or False? Ensuring that files are encrypted in storage everywhere allows the files to be protected in the event of a breach of physical security.
4. True or False? The cost of implementing an encryption policy pales in comparison to the cost of a data loss due to a breach or to release of data simply because Joe Smith left his laptop on the train. In an interesting, real-life situation, the author of this chapter did, in fact, once find a small box of hard drives in a bag on a train.
5. True or False? Encryption also introduces additional levels of difficulty in the event of corruption.
Multiple Choice
1. The data must be delivered to the following unencrypted DR site:
2. Which unencrypted backup site should be manned accessed with only biometric access controls and no Internet or network connectivity?
3. As physical security and controls increase, the need for encryption does which one of the following:
4. Who or what should consider and design a program that understands and includes recipient and sender environments, and ensures that data encryption and decryption are as seamless and unintrusive as possible?
5. Deciding which area is more likely to be attacked first requires some __________decisions that may, down the road, turn out to be wrong.
Exercise
Problem
What are the cryptographic module specification types?
Hands-On Projects
Project
What is cryptographic key management?
Case Projects
Problem
What types of self-tests must the cryptographic module perform?
Optional Team Case Project
Problem
What is the minimum information required in a cryptographic module security policy?
2.The diagram in Figure 13.2 represents the author’s viewpoint of how encryption might be deployed across a network that he just imagined in his head. The purpose of this is to create a model, a framework of sorts, that can be copied and adjusted as needed. It is meant to start a conversation, not end one.
3.http://csrc.nist.gov/drivers/documents/ombencryption-guidance.pdf.
4.Additional information regarding the use of AES can be found in CNSS Policy No. 15, Fact Sheet No. 1 National Policy on the Use of the AES to Protect National Security Systems and National Security Information, June 2003.