Appendix G. Measures from Lifecycle Activities, Security Resources, and Software Assurance Principles
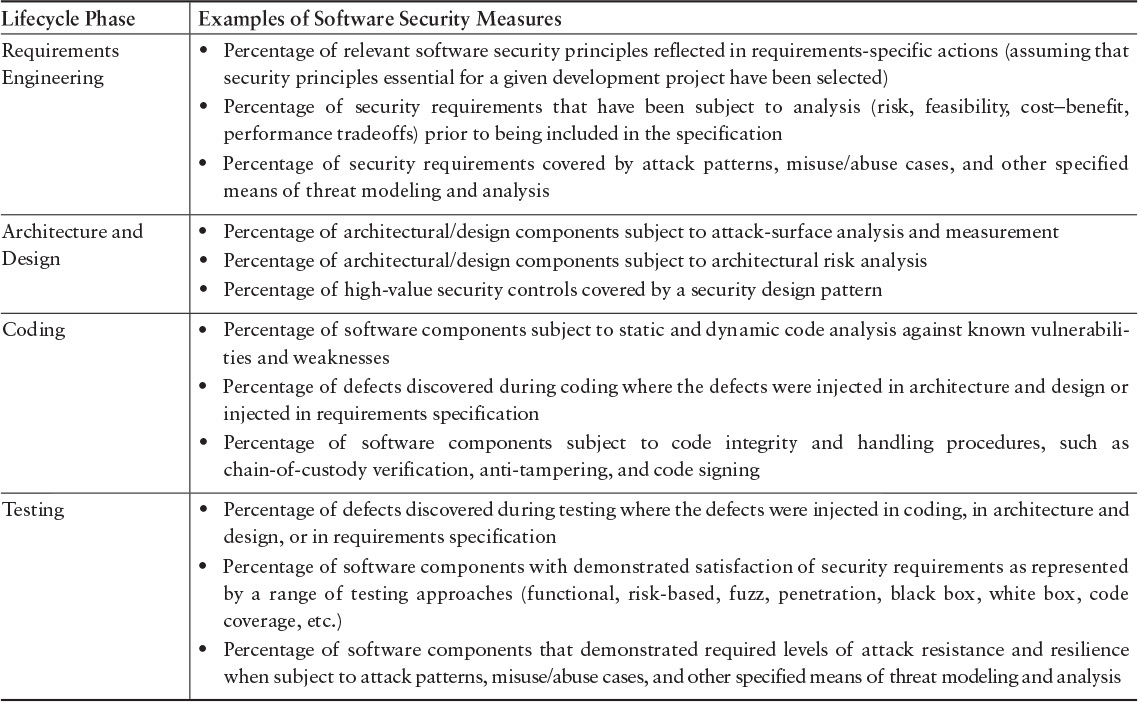
Measures are selected to provide justification that the steps performed to build a software system or product sufficiently address software assurance. Sampling from each lifecycle phase is one approach to determine that expectations are being met. Table G.1 provides examples for these measurements. Interviews with resources responsible for addressing security can provide evidence and example questions to solicit useful data are listed in Table G.2.
1. From Integrated Measurement and Analysis Framework for Software Security [Alberts 2010].
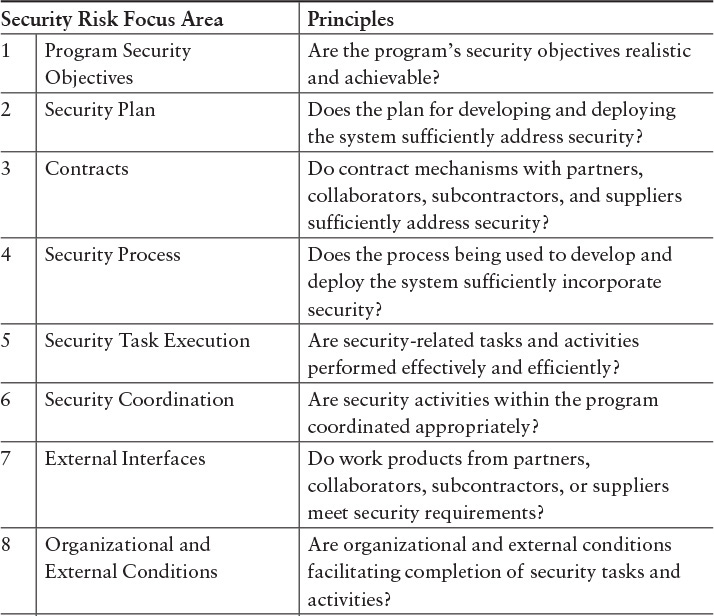
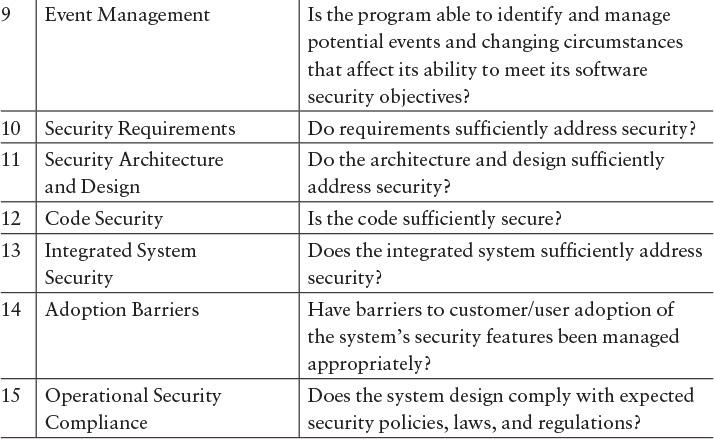
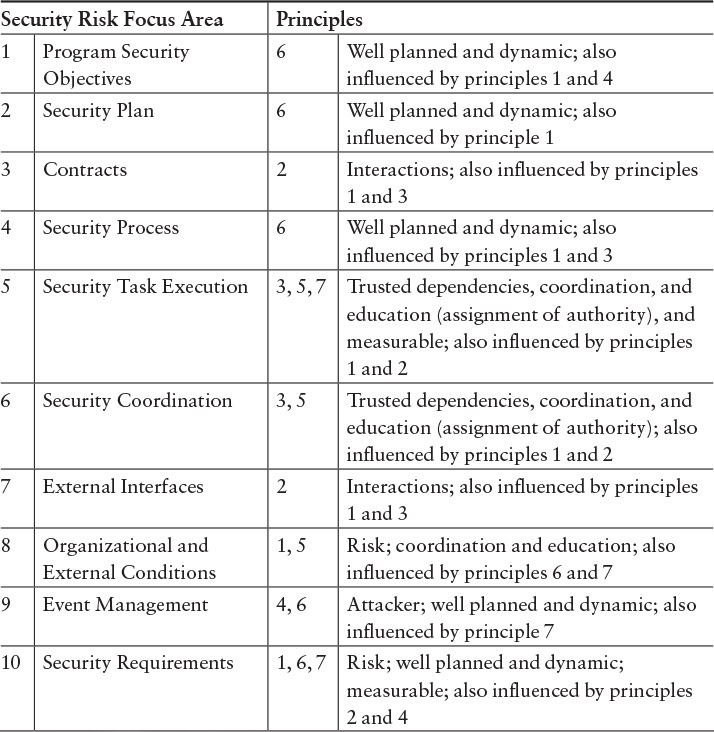
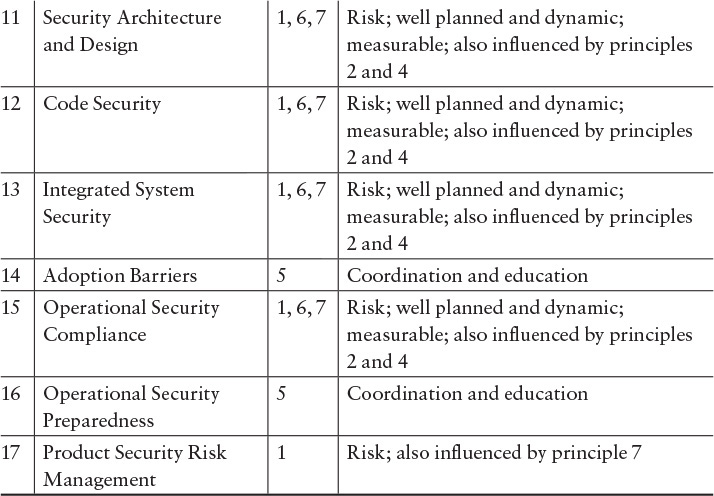
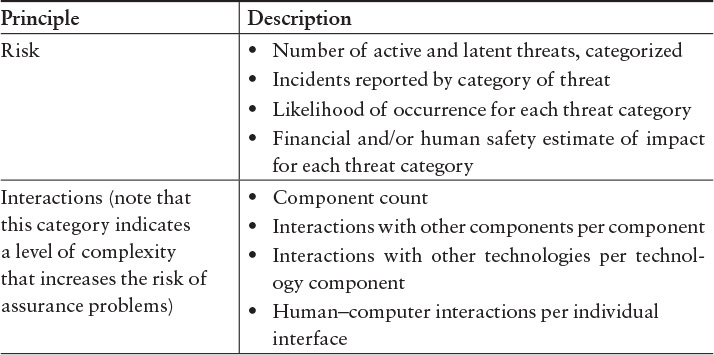
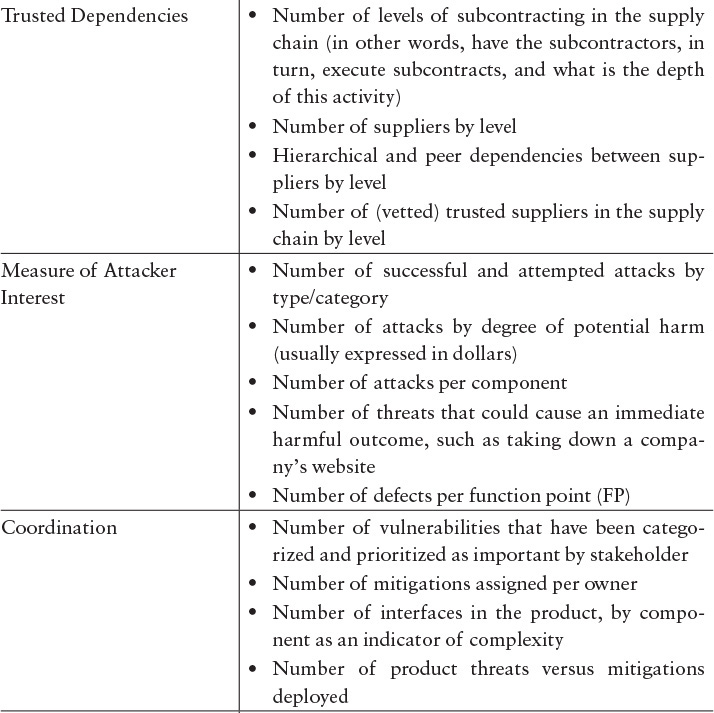
Confirmation that the principles for software assurance are appropriately addressed through security activities in the lifecycle can be verified using Table G.3. In addition, the principles can indicate measures that could be collected to provide evidence that a lifecycle is appropriately addressing software assurance (Table G.4).
2. From “Principles and Measurement Models for Software Assurance” [Mead 2013b].
3. From Common Weakness Enumeration: A Community-Developed Dictionary of Software Weakness Types [MITRE 2014].
Alberts, Christopher J.; Allen, Julia H.; & Stoddard, Robert W. Integrated Measurement and Analysis Framework for Software Security. CMU/SEI-2010-TN-025. Software Engineering Institute, Carnegie Mellon University. 2010. http://resources.sei.cmu.edu/library/asset-view.cfm?AssetID=9369
Mead, Nancy R.; Shoemaker, Dan; & Woody, Carol. Principles and Measurement Models for Software Assurance. International Journal of Secure Software Engineering. Volume 4. Number 1. April 2013.
MITRE. Common Weakness Enumeration: A community-developed dictionary of software weakness types. June 9, 2016 [accessed]. http://cwe.mitre.org/.