Chapter 8. Summary and Plan for Improvements in Cyber Security Engineering Performance
8.1 Introduction
The following topics exhibit varying levels of maturity and use differing terminology, but they all play a role in building assured systems:
Effective cyber security engineering requires the integration of security into the software acquisition and development lifecycle. For engineering to address security effectively, requirements that establish the target goal for security must be in place. Risk management must include identification of possible threats and vulnerabilities within the system, along with ways to accept or address them. There will always be cyber security risk, but an engineer needs to be able to plan for the ways in which a system should avoid as well as recognize, resist, and recover from an attack.
Mechanisms that ensure correctness and compliance can be excellent tools if they are applied by teams and individuals with cyber security expertise and linked to appropriate and complete cyber security requirements.
Throughout this book, we have provided ways in which practitioners, managers, faculty, and students can address cyber security engineering throughout the lifecycle. In addition, we provide mechanisms for addressing each of the key principles introduced in Chapter 1, “Cyber Security Engineering: Lifecycle Assurance of Systems and Software”: risk, trusted dependencies, interactions, attacker, coordination and education, well planned and dynamic, and measurable. Risk considerations should be part of each decision made throughout the lifecycle, and cyber security risk modeling can be addressed using methodologies such as the Security Risk Assurance Methodology (SERA) discussed in Chapter 2, “Risk Analysis—Identifying and Prioritizing Needs.” Interactions among the technologies that support a mission must be monitored and managed for effective cyber security. Just because technology elements can be connected does not mean they should be, and effective cyber security engineering supports appropriate choices.
The various chapters provide support for the underlying principles. Developing an understanding of mission risk (see Chapter 2) and addressing cyber security engineering (see Chapters 2 and 7, “Special Topics in Cyber Security Engineering”) provide mechanisms for addressing this area of concern. Means for defining, evaluating, and managing dependencies; linking integration choices with protection needs; and mechanisms for managing interactions are provided (see Chapter 3, “Secure Software Development Management and Organizational Models”). Education underlies all of our work and is specifically part of the basis for Chapters 3, 4, “Engineering Competencies,” and 5, “Performing Gap Analysis.” Planning is discussed throughout but forms an integral part of methods discussed in Chapters 3, 4, and 5. Measurement is the focus of Chapter 6, “Metrics.” Attacker considerations are proposed throughout but most specifically when developing requirements that drive technology choices early in the lifecycle. The A-SQUARE methodology introduced in Chapter 7 is particularly valuable in supporting the development of good security requirements during acquisition.
It’s not enough to write about cyber security engineering, however. We want to see good cyber security engineering models and methods put into practice. We recognize that each organization or project may be at a different point when it comes to improvement plans. Some organizations are already doing a lot in terms of implementing cyber security engineering strategy. Others may just be starting to think about it. Either way, the material presented in this book can help in developing a new cyber security engineering strategy or refining an existing one. As noted earlier, for purchasers of this book, we are providing free access to our online course: Software Assurance for Executives. This course provides an excellent overview of software assurance topics for busy managers and executives. To obtain access to Software Assurance for Executives, please send an email to:
RE: SwA Executive Course
In addition, the resources on our accompanying website, and the reference material we have provided all will contribute to developing a strategy.
Website for Cyber Security Engineering http://www.cert.org/cybersecurity-engineering/
The order of the chapters provides the suggested order of implementation of a cyber security engineering strategy and program:
• Risk analysis (Chapter 2)—The first step toward lifecycle assurance, cyber security risk analysis can be performed using techniques such as the Mission Risk Diagnostic (MRD) and SERA.
• Organizational competencies (Chapter 3)—Next comes the identification and development of competencies that support management (this includes the organization’s ability to address cyber security).
• Engineering competencies (Chapter 4)—Identification and development of competencies from an engineering perspective form the next step.
• Methods (Chapter 5)—Models can be used for benchmarking cyber security capabilities and performing gap analysis; the SEI’s Software Assurance Competency Model and the Building Security In Maturity Model (BSIMM) are two examples.
• Measurement (Chapter 6)—Measurement involves the methods and mechanisms needed not only to evaluate cyber security but to properly balance it with other operational needs such as performance and reliability.
• Special topics (Chapter 7)—Topics such as governance and other organizational and engineering capabilities may be needed to provide a well-planned and dynamic approach to cyber security engineering.
8.2 Getting Started on an Improvement Plan
In Chapter 3, we discussed maturity levels that we developed for use in our earlier work [Allen 2008]. In this chapter, we show how these maturity levels can be used to categorize the approaches presented in this book:
• L1—The approach provides guidance for how to think about a topic for which there is no proven or widely accepted approach. The intent of the area is to raise awareness and aid the reader in thinking about the problem and candidate solutions. The area may also describe promising research results that may have been demonstrated in a constrained setting.
• L2—The approach describes practices that are in early pilot use and that demonstrate some successful results.
• L3—The approach describes practices that have been successfully deployed (i.e., they are mature) but are in limited use in industry or government organizations. They may be more broadly deployed in a particular market sector.
• L4—The approach describes practices that have been successfully deployed and are in widespread use. Readers can start using these practices today with confidence. Experience reports and case studies are typically available.
When an organization is developing an improvement plan, the maturity levels can help assess whether to play it safe with approaches at higher maturity levels or whether to take the risk of using less mature approaches. For a less mature approach, say at maturity level 1 or 2, we suggest initially trying the approach on a less critical pilot project rather than adopting it across the organization. Tables 8.1 through 8.6 show the approaches presented in each chapter and their maturity levels.

Table 8.1 Risk Analysis (Chapter 2)
Table 8.3 Engineering Competencies (Chapter 4)
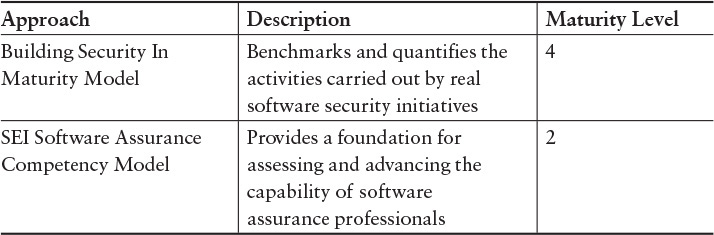
Table 8.4 Gap Analysis (Chapter 5)

Table 8.5 Metrics (Chapter 6)
8.3 Summary
The choice is not whether to develop a cyber security engineering strategy but rather when and how to implement it. In our connected world, it is vital for organizations and projects to come up with their own tailored plans to address cyber security engineering. As professionals, each of us should have our own plan to improve our cyber security engineering competencies. This book, along with the associated website, executive overview course, and reference material, provide you with the tools to get started.






