 Appendix C. Memory Tables
by Troy McMillan
CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2nd Edition
Appendix C. Memory Tables
by Troy McMillan
CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide, 2nd Edition
- Cover Page
- Title Page
- Copyright Page
- Contents at a Glance
- Table of Contents
- About the Author
- Dedication
- Acknowledgments
- About the Technical Reviewers
- We Want to Hear from You!
- Reader Services
- Introduction
- Chapter 1. The Importance of Threat Data and Intelligence
- Chapter 2. Utilizing Threat Intelligence to Support Organizational Security
- Chapter 3. Vulnerability Management Activities
- Chapter 4. Analyzing Assessment Output
- “Do I Know This Already?” Quiz
- Foundation Topics
- Web Application Scanner
- Infrastructure Vulnerability Scanner
- Software Assessment Tools and Techniques
- Enumeration
- Wireless Assessment Tools
- Cloud Infrastructure Assessment Tools
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 5. Threats and Vulnerabilities Associated with Specialized Technology
- “Do I Know This Already?” Quiz
- Foundation Topics
- Mobile
- Internet of Things (IoT)
- Embedded Systems
- Real-Time Operating System (RTOS)
- System-on-Chip (SoC)
- Field Programmable Gate Array (FPGA)
- Physical Access Control
- Building Automation Systems
- Vehicles and Drones
- Workflow and Process Automation Systems
- Incident Command System (ICS)
- Supervisory Control and Data Acquisition (SCADA)
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 6. Threats and Vulnerabilities Associated with Operating in the Cloud
- “Do I Know This Already?” Quiz
- Foundation Topics
- Cloud Deployment Models
- Cloud Service Models
- Function as a Service (FaaS)/Serverless Architecture
- Infrastructure as Code (IaC)
- Insecure Application Programming Interface (API)
- Improper Key Management
- Unprotected Storage
- Logging and Monitoring
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 7. Implementing Controls to Mitigate Attacks and Software Vulnerabilities
- Chapter 8. Security Solutions for Infrastructure Management
- “Do I Know This Already?” Quiz
- Foundation Topics
- Cloud vs. On-premises
- Asset Management
- Segmentation
- Network Architecture
- Change Management
- Virtualization
- Containerization
- Identity and Access Management
- Cloud Access Security Broker (CASB)
- Honeypot
- Monitoring and Logging
- Encryption
- Certificate Management
- Active Defense
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 9. Software Assurance Best Practices
- “Do I Know This Already?” Quiz
- Foundation Topics
- Platforms
- Software Development Life Cycle (SDLC) Integration
- DevSecOps
- Software Assessment Methods
- Secure Coding Best Practices
- Static Analysis Tools
- Dynamic Analysis Tools
- Formal Methods for Verification of Critical Software
- Service-Oriented Architecture
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 10. Hardware Assurance Best Practices
- “Do I Know This Already?” Quiz
- Foundation Topics
- Hardware Root of Trust
- eFuse
- Unified Extensible Firmware Interface (UEFI)
- Trusted Foundry
- Secure Processing
- Anti-Tamper
- Self-Encrypting Drives
- Trusted Firmware Updates
- Measured Boot and Attestation
- Bus Encryption
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 11. Analyzing Data as Part of Security Monitoring Activities
- Chapter 12. Implementing Configuration Changes to Existing Controls to Improve Security
- “Do I Know This Already?” Quiz
- Foundation Topics
- Permissions
- Whitelisting and Blacklisting
- Firewall
- Intrusion Prevention System (IPS) Rules
- Data Loss Prevention (DLP)
- Endpoint Detection and Response (EDR)
- Network Access Control (NAC)
- Sinkholing
- Malware Signatures
- Sandboxing
- Port Security
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 13. The Importance of Proactive Threat Hunting
- “Do I Know This Already?” Quiz
- Foundation Topics
- Establishing a Hypothesis
- Profiling Threat Actors and Activities
- Threat Hunting Tactics
- Reducing the Attack Surface Area
- Bundling Critical Assets
- Attack Vectors
- Integrated Intelligence
- Improving Detection Capabilities
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 14. Automation Concepts and Technologies
- “Do I Know This Already?” Quiz
- Foundation Topics
- Workflow Orchestration
- Scripting
- Application Programming Interface (API) Integration
- Automated Malware Signature Creation
- Data Enrichment
- Threat Feed Combination
- Machine Learning
- Use of Automation Protocols and Standards
- Continuous Integration
- Continuous Deployment/Delivery
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 15. The Incident Response Process
- Chapter 16. Applying the Appropriate Incident Response Procedure
- Chapter 17. Analyzing Potential Indicators of Compromise
- Chapter 18. Utilizing Basic Digital Forensics Techniques
- Chapter 19. The Importance of Data Privacy and Protection
- Chapter 20. Applying Security Concepts in Support of Organizational Risk Mitigation
- “Do I Know This Already?” Quiz
- Foundation Topics
- Business Impact Analysis
- Risk Identification Process
- Risk Calculation
- Communication of Risk Factors
- Risk Prioritization
- Systems Assessment
- Documented Compensating Controls
- Training and Exercises
- Supply Chain Assessment
- Exam Preparation Tasks
- Review All Key Topics
- Define Key Terms
- Review Questions
- Chapter 21. The Importance of Frameworks, Policies, Procedures, and Controls
- Chapter 22. Final Preparation
- Appendix A. Answers to the "Do I Know This Already?" Quizzes and Review Questions
- Appendix B. CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide Exam Updates
- Glossary of Key Terms
- Appendix C. Memory Tables
- Appendix D. Memory Tables Answer Key
- Appendix E. Study Planner [This content is currently in development.]
Appendix C. Memory Tables
Chapter 3
Table 3-2 Server-Based vs. Agent-Based Scanning

Chapter 8
Table 8-2 Advantages and Disadvantages of SSL/TLS

Table 8-3 Examples of Logging Configuration Settings
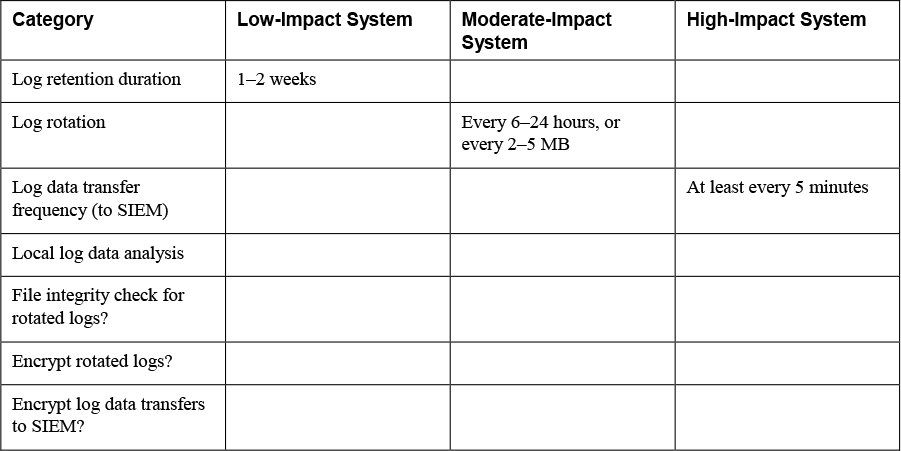
Table 8-4 Symmetric Algorithm Strengths and Weaknesses

Table 8-5 Symmetric Algorithms Key Facts

Table 8-6 Asymmetric Algorithm Strengths and Weaknesses

Table 8-7 Applying Cryptography

Chapter 9
Table 9-2 Comparing Black-Box, Gray-Box, and White-Box Testing
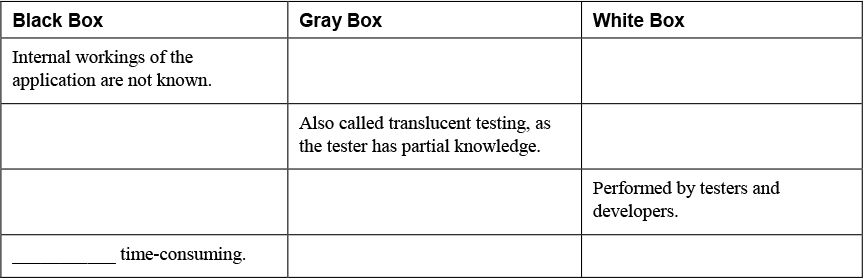
Table 9-3 Authentication Protocols

Table 9-4 RADIUS and TACACs+

Chapter 11
Table 11-3 SFC Switches

Chapter 12
Table 12-2 Advantages and Disadvantages of NGFWs

Table 12-3 Pros and Cons of Firewall Types

Table 12-4 RADIUS vs. TACACS+

Chapter 15
Table 15-2 Control Objectives of PCI DSS

Chapter 21
Table 21-3 SABSA Framework Matrix

Table 21-8 SOC Report Comparison Chart

-
No Comment
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.