THE OBJECTIVE OF THIS CHAPTER IS TO ACQUAINT THE READER WITH THE FOLLOWING CONCEPTS:
Defining governance and IT governance
Identifying who is responsible for implementing governance
The fiduciary responsibility and security requirements that every organization must exercise to protect assets and information
Defining the executive strategy, direction, and objectives
Accepted management practices that are in use to optimize allocation of available resources
How management establishes adequate internal controls for the IT organization
What management needs to do to protect the critical dependencies of information systems in economic transactions
How an organization demonstrates that it has exercised the best available management options to protect itself
Using business process reengineering to fix missing and nonworking processes

To be successful, management must define a strategy and provide for effective corporate governance. Strategy is defined as "an adaptation of behavior or structure with an elaborate and systematic plan of action." Another more specific definition of strategy is "to create a fundamental change in the way the organization conducts business." Obviously the second definition indicates that there are only a handful of people with that much authority. Corporate governance is often defined as "ethical behavior of corporate executives toward shareholders and the stakeholders to maximize the return of a financial investment." To clarify who is responsible for corporate governance, we could use this definition: "to lead by position or authority."
Three high-level management objectives to be verified by the auditor are as follows:
A strategic alignment between IT and the enterprise objectives (formal strategy). Proper planning is required to deploy resources in the right place for the right reason. Management is always responsible for getting it done (corporate governance, preventive controls).
A process of monitoring assurance practices for executive management. The senior executives need to understand what is actually occurring in the organization (staying involved by using detective controls).
An intervention as required to stop, modify, or fix failures as they occur (corrective action). Everyone has some kind of problem. Management should be working to resolve the issue immediately rather than covering it up by hiding the truth.
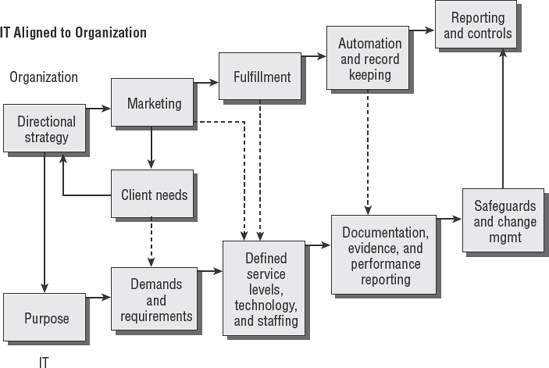
Each organization needs to develop their directional strategy. What direction should the business take to fulfill its goals? The strategy selected progresses to focus on client needs and how to fulfill that market. Critical success factors are selected. Marketing initiatives are designed to generate revenue with plans for fulfillment to the buyer. Figure 3.1 demonstrates the path of organizational requirements in conjunction with the IT requirements.
The revenue process entails a significant amount of administrative overhead and record keeping. The expectation in every business is to make money and not be hampered by a particular technology nor tied to a particular vendor.
The IT department is looking for a clearly stated purpose that IT is expected to fulfill. The department looks at the demands and requirements necessary to be successful. A structured service-level agreement can be generated with this data, complete with staffing and technology growth plans.
Technology plans have to fulfill a business objective. For instance, take Amazon.com. This very successful bookseller isn't necessarily hung up on using Microsoft Windows, Macintosh, or Unix. What the executives want to know is that all the money is processed and the product arrives on time to fulfill their customers' expectations. Systems management and auditing on the back end will verify that all their bookkeeping and internal controls are functioning effectively. In an industry leading move, Amazon added same-day shipping as a $5 option on select stock for customers geographically located in vicinity of the Amazon warehouses. The bookseller downloaded the daily courier route schedules, and then compares the pickup and delivery schedule to the buyer's address. Orders placed in the morning can arrive the same afternoon in select major cities. A same day delivery option is automatically added to the shopping cart for eligible purchases. Amazon demonstrates excellent integration of the business and IT strategy.
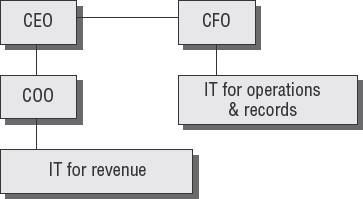
The top side of this diagram is motivated by gains in revenue. Executives take calculated risks to exploit new opportunities for their business to make more money. Conversely, IT is expected to prevent service failures that hurt revenue. IT may also be expected to focus on activities that enable revenue and concurrent activities to prevent loss based on risk management planning. This can make it difficult to determine which problem or goal is the priority. Auditors can gain insight by looking into the IT reporting structure. IT functions reporting to the chief operating officer (COO) are services that generate revenue. IT functions reporting to the chief financial officer (CFO) are internal functions of reporting and processing controls. Refer to Figure 3.2.
The principal mechanism for ensuring IT alignment is to implement an IT steering committee.
Most organizations use an IT strategy committee or IT steering committee. An IT steering committee is used to convey the current business requirements from business executives to the IT executive. The name of the committee is not as important as the function that it performs; a committee may perform more than one function. An IT steering committee may possibly be the same committee used for the purpose of a business continuity steering committee, but with a slightly different charter (focus). What's important is that the job of steering operations to business requirements is occurring.
Steering committees should have a formal charter designating the participation of each member. This charter grants responsibility and authority in a concept similar to an audit charter. An absence of a steering committee charter would indicate a lack of formal controls—a condition warranting management oversight review.
The steering committee is also discussed in Chapter 5, "Life Cycle Management."
Note
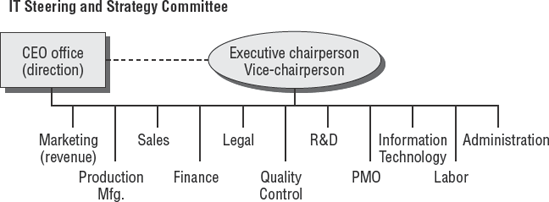
The steering (or strategy) committee is made up of quite a few individuals. Each individual is required to have the authority to act on behalf of their department. These members are vice president–level or higher in the organization so they can help align the IT efforts to specific business requirements. Figure 3.3 shows the basic organizational structure of the steering committee.
The committee is managed by an executive chairperson. The CEO is expected to provide directional guidance in person or via a representative, such as the COO, to identify targeted sources of revenue. Each member of the committee is expected to participate in focus discussions concerning business issues. On occasion, the committee may invite trusted observers or presenters to the meeting to increase awareness of a particular area.
After the business objectives are identified, the next step is to determine the business objectives for IT to fulfill. The steering committee sticks to high-level objectives rather than dictating technical detail.
Let's look at the representation necessary on the steering committee:
- Marketing
Marketing should be represented on the steering committee. The purpose of all marketing is to attract buyers for the organization's product or service. Even if the organization builds the world's finest product, it will not matter unless a steady stream of buyers make a purchase.
- Manufacturing/Software Development
The input from manufacturing or software development is required to align production efforts to sales efforts.
- Sales
The sales function is to convert interested prospects from marketing campaigns into closed sales. Sales executives are interested in using technology to facilitate more sales. The cooperation of manufacturing and technology is necessary to assist the sales effort.
- Finance
Financial guidance and budgeting skills are essential to optimize the organization's investment. Obtaining funding approval for projects would be difficult without the cooperation of the finance comptroller.
- Legal
The executive from the legal department should ensure compliance to the law. Qualified legal counsel advises management in areas of uncertainty. Expert legal counsel should help protect the company from excessive liability or undue risk as a result of a control failure.
- Quality Control
The quality process provides consistency in operations, manufacturing, and risk mitigation. A well-run quality process is a major contributor to the organization's survival. Failures in quality control can damage market image or lead to liability problems.
- Research and Development (R&D)
The Research and Development staff is constantly working on creating new products and improving existing products. The R&D effort is focused on developing products that will generate revenue six months to two years in the future.
Note
Depending on the organization, R&D may be suspended during times of financial shortfall. The planned R&D budget would be applied to projects with a faster return or to pay past-due obligations.
- Project and Program Management
The head of the Project Management Office, if one exists, should be on the committee to advise members on current and proposed projects. Ideas presented by customers may require changes, causing the need for new projects to modify existing programs. Change is required to be successful in business. Remember that projects are temporary, while programs are ongoing for multiple years or even perpetual.
- Business Continuity
The head of business continuity planning should always be in attendance. This person may possess the title of continuity manager or program manager and have the authority of a vice president or major director. This person's job is to assess impact or help exploit opportunities presented in support of the organizational strategy. It's important not to sacrifice continuity in favor of shortsighted decisions.
- Information Technology
The chief information officer (CIO) or vice president of IT listens to business ideas and objectives raised by committee members. This person acts as a liaison to facilitate the involvement of IT. The IT member may delegate planning and research activities to members of the IT organization.
- Human Resources
The management of personnel grows more complex each week. Compliance with federal labor standards is mandatory. International organizations require special assistance that is beyond the expertise of most non-HR executives. Noncompliance can carry stiff penalties.
- Labor Management
An executive representative from any labor organization, such as a labor union, may need to be involved in decisions concerning labor. This can be a touchy subject depending on the organization.
- Administration
Office administration functions include bookkeeping, record keeping, and the processing of paperwork. Every executive would be handicapped without an administrative assistant.
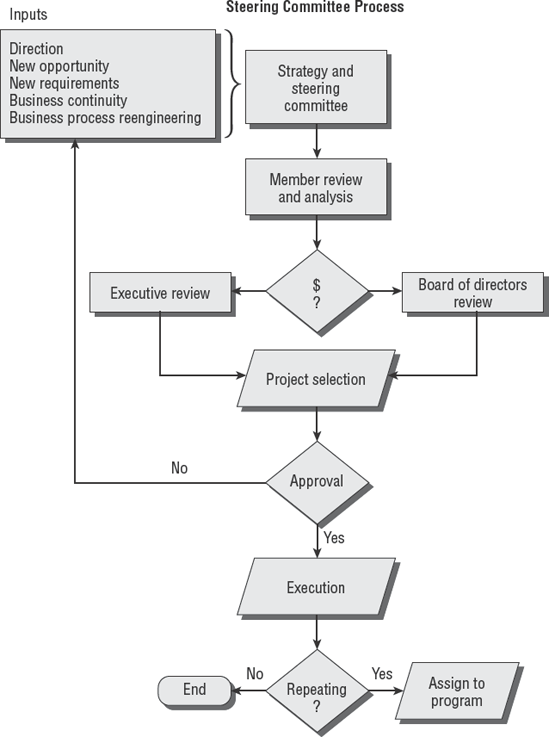
The steering committee reviews ideas and opportunities to make recommendations. Those recommendations go to the board of directors for review. If the idea receives preliminary approval, resources are allocated for project planning. The steering committee executives perform a final review of comparing the total cost and benefit to determine whether the project is a "go" or "no-go."
If a go decision is reached, the organization specifies details, charters the project, allocates funds, commits resources, and moves the plan into execution. If the project is scheduled to be a repeating event, the project is assigned to program status. Otherwise, it is managed as a project with fixed time duration, and the assigned project team members will disband after project completion.
Figure 3.4 is a flowchart of the IT steering process.
In strategic planning, plans generally run in a time frame of three to five years. A tactical plan is going to be carried out over six months to a year and it may go into two years. Daily plans are no more than steps in the tactical plan. When an organization projects three to five years, it is really developing a strategy. This strategy can be to run a streamlined low-cost airline operation like Southwest Airlines, offer the best market reach like eBay, provide competitive rate marketing like Progressive insurance, or use the shipping model of FedEx to assure your package is absolutely positively delivered overnight.
Table 3.1 compares strategic plans, long-term plans, and operational plans.
Table 3.1. Differences between Strategic, Long-Term, and Operational Plans
Item | |||
|---|---|---|---|
Time frame | 3 years + | 1–3 years | 1 year or less |
Question | What business are we in? Should we expand or contract? | What are the major business components? What should we concentrate on now? What products and services are planned? | What specific tasks must be done to meet the long-term plan? |
General broad statement of what business the company is in | Financial goals Market opportunities Management organization Next review period | Assumptions for the period Changes needing to be made Production times Responsibilities Budget |
Now that we have discussed the definition of strategic planning, it is time to get specific about the content of the executive strategy.
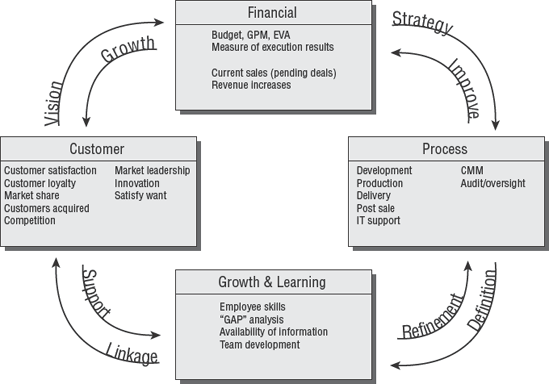
To set forth a strategic goal without proper planning and meaningful definitions would be both negligent and reckless. One of the most powerful executive planning tools available is the balanced scorecard (BSC). The BSC is a strategic methodology designed for senior executives.
Originally, the balanced scorecard was designed in a university environment to be used by business executives for reporting metrics. A very smart person once said, "the product's actual use will be invented at the customer site," meaning you can build what you want, but the customer will determine how it's used to solve their problem. It turns out that the most successful executives are using the BSC to define internal cause-effect relationships of smaller plans that run their business, not just to report metrics as originally conceived.
The scorecard approach converts organizational objectives of customer perception, business processes, employee growth and learning, and financial goals into a series of defined actions. We typically call these actions either projects or programs, but the BSC doesn't care. The BSC refers to projects and programs as initiatives (what you are doing).
Three years ago, after a less-than-successful board meeting, I set a personal goal to learn how to apply the BSC tool. I searched all websites in the first 200 Google results and read every book available from Barnes & Noble. Plenty of people claimed knowledge of the BSC, yet consistently failed to demonstrate how the inner details actually worked. Frankly, none provided enough direction to make it work. I fell into the same trap as everyone else. It takes special training with firsthand experience to receive the benefits that this type of advanced planning tool offers. ISACA just wants you to know it exists. I teach my students in our seminars how to use it, exceeding the exam study requirement. So this section is my short brochure-level introduction on how it works. I use BSC constantly each week and stand behind all my statements with supporting evidence.
When properly implemented, the scorecard concept enforces better alignment by defining details of strategic business objectives. Overused terms such as world class and customer driven are broken down into low-level definitions that the staff can actually implement. Using the scorecard should eliminate activities of little or no strategic value.
The scorecard methodology is common outside the IT environment. Information technology can benefit from using the balanced scorecard if it is implemented by the CEO or CFO. To be effective, the scorecard must be driven from the top down.
Table 3.2 illustrates the four scorecard perspectives and matching emphasis area of the BSC methodology. For example, the finance perspective will place emphasis on cost control and company profits.
Table 3.2. Balanced Scorecard Methodology
Perspective | Emphasis |
|---|---|
Customer | What is our market image? What makes us different? How should the organization appear to the customer? Why would a client want to do business with us? |
Business process | What is our mission? How can we create a genuine competitive advantage? What are our critical success factors? What are the key performance indicators? |
Financial | What are the financial goals? What are the shareholder goals? Are we a cash cow or a pioneer? |
Growth and learning | What information do we need to beat our competition? What are the organization's growth plans? How will we keep or obtain the knowledge and workers necessary to support the organization's plans? |
A smaller number of organizations are successful at using the balanced scorecard approach, while many fail. Upon investigation, several of the failing executives referred to BSC as old news. It did not take long to discover that these executives had a lack of BSC training, misunderstood the objective, and possessed little BSC experience. Let's investigate why this occurs.
The advantages and disadvantages of using the scorecard methodology are as follows:
- Scorecard advantages
It promotes a focus on the specific if-then linkage between different objectives and their budgets. The goal is direct support of organizational objectives. If you change funding or strategy on a linked initiative (project or program), the effect can be seen rippling through the scorecard. We are actually using the BSC to create well-defined articulated strategies.
All the initiatives (project or programs) are linked into a complete process flow that ignores departments and traditional boundaries. Never again will strategy be determined in one meeting and budget determined somewhere else.
When fully implemented, none of the departments will have their own budget to spend. The result is project-based, program-based staffing. It does not matter whether the department function is internal or external.
Each department pledges its level of support to a defined strategy initiative. The corresponding budget money is issued to the department, provided it is meeting its delivery goals. No support of the linked project means no money, no people, and no job. This blocks waste and personal agendas.
Each employee works from a personal scorecard created by cascading the BSC down into specific execution tasks. The combined effect of the personal scorecards will achieve their department's objective. Achievement of the departmental objectives will help fulfill the organizational objectives.
- Scorecard disadvantages
The scorecard requires a careful selection of initiatives by the CEO or CFO. It is reported in executive trade journals that metrics derived from a committee will consistently fail. Interestingly, observations indicate that executives unwilling to adapt to the scorecard methodology may lack a genuine interest in being a team player or may possess more interest in building their own empire within the organization. Politics can kill the BSC unless the sponsor eliminates the people creating political conflict.
The balanced scorecard can contain whatever you need to define. It is flexible in having three, four, or five perspectives depending on what your executives decide is needed. The typical approach of four perspectives is shown in Figure 3.5. Notice how the different initiatives are linked into a complete process.
There are several secrets involved in making the scorecard generate true results. Using a BSC will most likely take beginners at least 20–30 failed attempts, which end in frustration, before it begins to show a glimmer of success. Keep trying; the benefits will far outweigh the effort. Each failed attempt is simply an indicator of an existing relationship problem or definition problem. Problems need to be fixed one by one before you can build an effective linkage. Often this includes retreating a few steps to adapt for changes as they are discovered. That's part of the magic in using BSC. The strategy becomes more defined with each pass, forcing each problem to be fixed before it can effectively function inside the overall strategy plan.
Every planning exercise brings more clarity as you roll the linkages forward and backward to fine-tune the details. It's like using algebra to solve a problem and then using calculus to prove you actually did solve the problem by returning to zero. Now the strategy works forward and backward, with excellent definitions exploding all the details into specific action items. Initiatives (projects or programs) are now selected, scoped, and funded based on which ones generate the highest return on investment (ROI).
What if your project or program doesn't generate revenue? Simply put, it would be linked with a function that is generating revenue and used to calculate the combined operating costs. For example, security costs in a bank are coupled with the profits the bank generates. The final ROI estimate is used to decide whether that area of the business is expanded or shut down. What if you make more money from brokering mortgages? You may switch from being a full-service bank into focusing on mortgages. The final goal is to find the highest-earning ROI and quit wasting resources on marginal or losing activities.
Executives at AMR operate American Airlines and Sabre reservations as two separate companies. One reporter asked which one they would sell if necessary. The response was that American Airlines' business need created Sabre, yet they would keep Sabre, selling the airline if that day ever came. Sabre's reservation system is a better ROI.
The balanced scorecard fundamentally changes how employees prioritize and report their work. Activities and projects are selected on the basis of the value created under established metrics. This also results in a change in how the employee is evaluated. It is essential that management and staff receive proper training prior to implementation. Just remember, without full buy-in at all levels, the balanced scorecard is likely to fail.
The IT balanced scorecard should be a subset of the organization's overall balanced scorecard. When properly implemented, the scorecard methodology supports the highest-level business objectives.
As a CISA, you need to understand how the balanced scorecard can be applied specifically to information technology. ISACA describes the scorecard by using three layers that incorporate the more common four perspectives (customer, business process, financial, and growth and learning). The three layers for IT scoring according to ISACA are as follows:
- Mission
Develop opportunities for future needs. Become the preferred supplier of IT systems to the organization. Obtain funding from the business for IT investments. Deliver effective and cost-efficient IT services. Often the mission statement sounds like an advertising slogan. In reality, the mission statement should be less of a political statement and more specific in definition. Therefore, each mission statement needs supporting details contained in the strategy definition. The goal of the BSC is to convert vague mission statements into clear-cut action items that the staff can understand and then implement.
- Strategy
Attain IT control objectives. Obtain control over IT expenses. Deliver business value through IT projects. Provide ongoing IT training and education. Support R&D to develop superior IT applications. All these sound great, but they need significantly more detail before they can be implemented. Using the BSC can help define the lower-level initiatives necessary to make the mission functional. Far too many executives fail to provide a well-defined, articulate strategy. A definition is needed that maps detailed cross-coordination rolling across departmental boundaries.
- Metrics
Develop and implement meaningful IT metrics based on critical success factors and key performance indicators. We'll cover more in metrics in Chapter 6, "IT Service Delivery."
Tip
The balanced scorecard method is a wonderful tool for the auditor to gain invaluable insight into the organization. A simple BSC exercise will uncover the organization's critical path while illuminating its ROI dependencies.
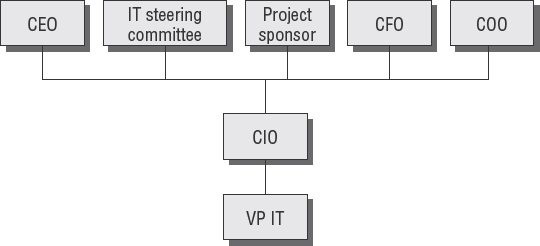
Executive management selects an IT strategy to fulfill their business objectives. The strategy should be approved from the top down. The strategy is then formalized into a policy and communicated throughout the organization. Figure 3.6 shows the executives involved at the strategy level (in policy making).
You should assume that the executives have already gone through the process of gathering requirements. Their strategy may be to insource or to outsource. However, one of their most important questions is to determine how the strategy will be funded. Each of the following methods of funding bears unique advantages and disadvantages:
- Shared cost
It is common for the bulk of IT costs to be allocated as a shared cost across all members of the organization. This method is relatively easy for the finance department to implement. Unfortunately, it may lead to user dissatisfaction. Some users and their managers may feel that they are paying for a service that is not received.
- Charge-back
Individual departments receive a direct charge for system use. This is designed to be a pay-as-you-go style of accounting for IT expenses. Charge-back schemes are quite effective if properly implemented. Mainframe charge-back schemes are particularly effective for usage billing.
- Sponsor pays
This last type can present a significant challenge to IT governance. The project sponsor pays all the bills. In exchange, the sponsor may demand more authority over decisions. This method is notorious for creating shadow support organizations. Shadow organizations indicate willful distrust between executives. Usually the basis of shadow groups is a self-centered agenda that creates a design contributing toward a functional failure. Additional conflicts usually occur with IT management in disputes over budget responsibilities, not implementing all the proper controls, lack of effective monitoring, and improper reporting of failures. The best way to solve the conflict is by fully enforcing separation of duties.
Executive management has the responsibility of setting goals. Each goal should be supported with a defined set of objectives. A strategy should be in place to achieve those objectives. The next step is to specify a policy to communicate management's desires to the subordinates.
Every policy should be designed to define a high-level course of action. The purpose of the policy is to inform interested parties of a chosen solution. A well-designed policy is based on a statement by management of the policy's importance. The statement explains how this particular policy supports a business objective. The policy is signed by the most senior person available to prove authorization.
We discussed the role of policies, standards, and procedures in Chapter 1, "Secrets of a Successful IS Auditor." Table 3.3 should serve as a memory refresher concerning the role of policies, standards, and procedures.
Successful policies are issued from the top down to all subordinates. The policy may designate a department director to create a standard in support of the policy. The final procedures are generated from the workers at the bottom of the hierarchy. Common procedures are intended to be implemented from the bottom up. The procedure is a lower-level person's response in support of the executive's policy.
Policies are designed to inform interested parties about a particular situation. The policy may be advisory, regulatory, or informational:
- Advisory policy
An advisory policy explains the condition to be prevented by the policy and provides notice as to the consequences of failure. The interested party may be an employee. The subject could be acceptable use of the Internet. In the Internet example, the advisory mandate is to either comply or be fired.
- Regulatory policy
The term regulatory indicates that this policy is mandated by some type of law. All organizations under the jurisdiction of the regulation are expected to comply. Failure to comply will result in criminal liability.
- Informational policy
Informational policies inform the public of the organization's operating policies. Examples include the customer privacy policy, the customer refund policy, and the customer exchange policy.
Note
IS auditors should be aware that undefined policies indicate a lack of control.
After the strategy is selected and the goals are set and the policy is created, it's time to begin the planning process. In planning, the strategy is broken down into useable definitions to move it closer to reality.
IT strategy plans must be created to aid the organization in the fulfillment of long- and short-term business objectives. Each IT plan should correlate to a specific organizational goal. The business goal may be to improve customer contact management, expand e-commerce services, or improve operating speed with better software integration. The supporting IT plan could define implementation and support for a new Customer Relationship Management (CRM) system. IT's role is that of a requirements facilitator and custodian. The true strategic value will be determined in the minds of the business executives. There should be a concern if IT's influence is overriding other non-IT business objectives. The IT strategy will be composed of plans for data, software applications, technology, personnel, and facilities.
IT data plans are created in support of the organization's intended use of the data. An example is the creation of a new customer survey system, database marketing system, or financial record-keeping system. The key is to determine what data you really need and how you will protect it. This is accomplished by implementing an information classification program with administrative policies and procedures. Well-run businesses and governments have been doing this for hundreds of years to explain how each piece of data should be handled. After the intended use of the data is recognized, the next step is to define the application to manipulate the data.
Computer software applications are actually methods of accomplishing work. Therefore, a software management plan is necessary to define the type of work to be performed. A consumer bank may be in the same industry as a debt collection company, for example. However, both organizations use different software applications. Computer software applications need to be tailored to fit the client's needs.
Note
Computer software is not an advantage if the competitor uses the same software, unless the implementation is unique and highly customized.
It is possible to gain a competitive advantage by using a different product than the competitor uses. The advantage is attaining a higher level of business integration and/or lower operating costs. The cost argument is the very reason why some software applications use open source MySQL for the database rather than Oracle. Both are fine products. The cost difference may allow for a significant investment in specialized customization by a guru to build highly integrated software, which can create a competitive advantage with a lower overall operating cost. The resulting integrated software may perform a unique function that the competitor will have difficulty obtaining because of required knowledge, lead time needed, or additional capital investment. Cost avoidance can be a competitive advantage. The application risk is that the integration does not occur or the intended application usage is flawed.
Computer application software represents a substantial investment in capital. Computer software creates business risks that must be managed. The risks include process failure, increased operating risk, ineffective results, waste of capital resources, lost time, and increased operating cost for the same effective output.
Technology plans address an organization's technical environment by indicating the types of hardware and software that will be used. Unfortunately, some organizations start with the hardware technology first and attempt to force the data and application requirements into their desired technology. Putting the technology plans first may hinder the results.
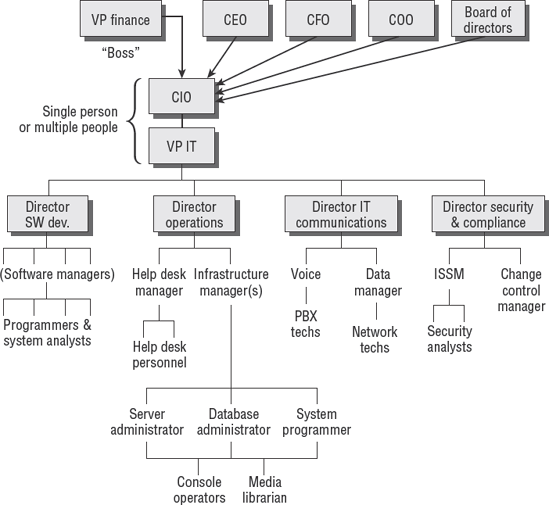
The IT organizational structure needs to be designed to support the business strategy. Information technology is usually regarded as a function of internal administration. This would place IT under the head of internal controls (the CFO, VP of finance, or the comptroller). Figure 3.7 illustrates a typical IT organization. We will discuss the individual positions as we proceed through this chapter.
Tip
Figure 3.7 can serve as a roadmap if you're unsure about the authority of positions we discuss in this chapter.
Finally, the strategy needs to incorporate a facilities plan. Where will the data applications and technology reside? Who will manage the environment? The final decision will be based on the desires of management. These desires can include increased control, insourcing, outsourcing, or a hybrid combination.
Knowing what to do is a challenge for all auditors. Discussions were occurring on this subject long ago in the old Electronic Data Processing (EDP) audit association, before it was renamed ISACA. One of the goals of every association is to add value by improving the performance of its members. ISACA has definitely delivered on this goal. The definitive framework for IS auditing is called the Control Objectives for Information and related Technology, also known as CObIT.
This framework contains a complete set of strategies, processes, and procedures necessary for executives to lead the IT organization. CObIT is now in its fourth edition. Within the supporting manuals, you will find the guidance provided in their audit toolkit invaluable. CObIT is protected under copyright, so it's a good idea not to lose your CISA certification by doing something stupid like having a bootleg copy.
The audit guideline section contains more than enough questions necessary for a first-class audit. It covers the entire spectrum from executive strategy down to device settings. BSC properly combined with CObIT would make a phenomenal audit practice.
Now let's get back to the auditing plan. We have discussed strategy, so the next step is to figure out the work location.
The next step is to identify sourcing locations. The sourcing decision may be based on the operating cost for particular geographic locations. Operating cost is a combined factor of facilities, labor, regulations, and available resources. Organizations may choose to perform functions onsite, in their facility. Alternatively, there may be an advantage to performing functions offsite, at other offices or with an outside vendor. This is a common practice for customer support, employee payroll, and manufacturing. Cheap labor may influence management's decision to move the location offshore, to another country.
Note
Three popular offshore locations include China, India, and Russia. The expected benefits include cheaper labor or lower standards for environmental compliance. The effective cost of steel, concrete, and materials to construct an office is approximately the same worldwide.
Performing functions offshore introduces both opportunities and burdens. The opportunities include a potentially lower production cost. There is also an advantage for an organization to operate 24 hours a day in order to lower turnaround times. Consider the effect when the day shift identifies a problem and the night shift in another country fixes it before the day shift returns in the morning.
Disadvantages include the potential loss of control or the disclosure of proprietary intellectual property. In some countries, the culture, language, or level of education presents unique challenges.
Cultural examples of potential conflicts include India's caste system and Africa's ongoing tribal wars. Another example is the attitudes in some societies toward a woman in an authoritative role.
The world is growing smaller as transportation and communication services improve. Many of the old cultural barriers have been reduced by the global economy. This global economy also has increased the number of competitors in the fierce battle for revenue. An organization at one time worried only about servicing clients in a small number of local time zones. Now customers depend on businesses 24 hours a day, worldwide.
Most administrative and technical support functions can be performed from alternate locations. Some of the services that could be fulfilled from remote locations include the following:
Accounting and bookkeeping
Accounts payable (AP) and accounts receivable (AR)
Data entry and transcription
Live telephone support (including IT, customer service, order taking)
Legal and medical records management and processing
Human resources and benefits administration
Creative advertising production
Printing
Software development
Systems administration
In the following section, you will look at the various types of sourcing methods, what factors go into choosing a sourcing method, and why it is important for you as an IS auditor to be familiar with them.
The decision of location is usually based on the cost of operation, market pressures, or a centralization versus decentralization strategy. Management may choose to hire personnel by using a combination of insourcing and outsourcing. Services provided by internal staff are referred to as in-house (insourced). Services provided by an external vendor are referred to as outsourced. The insourced versus outsourced decision may be based on a case-by-case or project-by-project requirement.
On occasion, an opportunity may present itself that exceeds the capability of the existing service provider. Hybrid sourcing models may be effective under a joint venture or to provide additional capability. The hybrid model combines insourcing and outsourcing on a function-by-function basis.
The advantage of outsourcing is that someone else may be able to perform the work better or cheaper, or frankly may know how to do something others don't. Insourcing provides more control. The hybrid method retains control in selected areas and uses the outsource contractor for collateral work. Outsourcing may allow the client to focus on what they do best, their core revenue generator. A potential disadvantage is losing control under the contract. Maybe the methods used by a subcontractor will cost less because they are cutting corners that, if known, a company might find unacceptable.
The basic decision may result from an executive thinking about the following:
Is this something that the organization wants to do in-house?
Is this something the company should outsource?
Is there an advantage to sending this offshore?
Is the organization bringing it back from offshore?
Will local processing be a competitive advantage?
Is the location here, in this building, or is it in another building?
Businesses may encounter a variety of globalization issues, including international regulation, local laws, tribal rivalries, or cultural class or caste systems. As an organization begins to look at opportunities for global outsourcing, they have to keep in mind the controls and the total costs related to that decision.
A business looks for inexpensive operating facilities with a high-quality labor pool willing to work for lower wages. If the business is going to decide whether to outsource, it needs to look at all the practices and strategies that are in place.
A business can run into problems over the differences in legal regulations between governments. Additional concerns can arise in different currency exchange rates and government taxation methods. Some of these requirements may indicate that foreign outsourcing would not provide any advantage.
Competitive advantage should be a factor in the sourcing decision. For example, American Apparel manufactures clothing exclusively inside the United States and pays better-than-average wages for their industry. Their advantage is a shorter cycle time from market idea to delivery and sale in their stores. American Apparel touts a one-day turnaround from a finished idea. Their competition has to contend with manufacturing and shipping delays measured in months.
In the last few years, Russia and the Baltic states have benefited from increased popularity, as companies reconsider India or choose to outsource for the first time. Increasing operating costs and U.S. consumer rejection are troublesome to companies outsourcing to India. The cost of real estate in India is skyrocketing. China is reeling backward after a virtual tidal wave of product recalls. Additional reasons cited for Russian sourcing include a more convenient proximity to Western Europe, more positive consumer attitudes of acceptance, a well-educated population, financial savings in real estate prices, and the competitive low cost of labor.
When dealing with outsourcing issues, companies need to be aware that what might be legal in one country might not be legal in another. Examples include the European Union (EU) privacy laws, which are much stricter than those of the United States, or the shortfall of intellectual-property laws in China, which frankly don't exist. In China the attitude is that if someone has a copy, they own it. This is where business management needs to understand: How does that country or culture see it?
As a primitive example, just compare the religious holidays and lifestyles that different countries observe. For example, the flow of harmony in the office is considered upset in Japan if everyone does not go to lunch at the exact same time, and return within a couple of minutes of one another. In Mexico, the lunch hour is two hours and often includes drinking alcohol followed by a siesta (nap). It is not uncommon for employees to drink alcohol during the office lunch hour in the United Kingdom (referred to as having a few pints or getting pissed over a few drinks).
While management plans their labor strategy, there should be a provision ensuring continuity of operations for both in-house and outsourced activities.
The biggest downside of outsourcing is liability. Outsourcing permits an organization to reassign the tasks to be performed but not the liability. It's not possible to transfer the actual liability for failure. Insurance may help cover some of the expenses but not the damage to your reputation, the cancelled sales, or the costs of defending a lawsuit.
Consider the situation of Value Jet airlines. A subcontractor violated cargo-loading procedures when it placed a hazardous container in the cargo bay. The container exploded, causing the airplane to crash. A massive media circus was spawned by the event. Value Jet held their subcontractor liable. The public held Value Jet responsible. The public didn't pick the subcontractor; Value Jet did. Value Jet was expected to spend extra time and money to supervise the subcontractor. The airline folded.
Let's consider the long-term effects of the following well-publicized examples of food contamination:
Recently, problems surfaced in many well-known brands of canned pet food. A supplier of ingredients shipped tainted flour, which led to the death of many beloved family pets. Other pet owners reported paying expensive medical bills for emergency care by veterinarians. Retailers trashed their entire inventories of canned pet food and asked for refunds to cover the losses. Pet owners are pursuing lawsuits against the brand for the harm to their pets and their own emotional strain.
ConAgra is involved in legal battles over a bad batch of ingredients used in Peter Pan peanut butter. One lawyer is advertising on television to "keep the jar and call attorney Loncar," thus promoting possible monetary awards for the consumer to sue ConAgra. Wal-Mart sold the same ConAgra peanut butter under its own house brand.
Several products manufactured in China are now banned from the United States and other countries because of unacceptable chemicals in foods or illegal hormones used to grow vegetables and fish.
Outsourcing does not relieve the company's responsibility to test products or services for compliance. In fact, the outsourcer should be trusted less and tested more. The auditor is always interested in how the process of governing all outsourced services is handled.
It's interesting how some vendors can perform the task cheaper than in-house. Unfortunately, the cost and benefit structure might not be telling the whole story. Outsourcing is frequently an option when the organization
Is unable to get the right result
Considers the process is too much work
Fails to define their actual needs
As time goes by, it may be discovered that the outsource provider is taking unacceptable shortcuts or charging higher prices than expected. Additional issues to consider include turnaround time plus increased costs of supervision necessary to maintain the desired results.
Note
Heartland Payment Systems moved their processing back in-house after years of outsourcing. Their service provider was identified as the bottleneck slowing responses for customers and creating other delays in distributing information within Heartland. Management realized that the service provider was limiting their ability to compete in their market. Bringing their processing back in-house saved $3 million and enabled them to deliver next-day funding. Heartland is now able to respond faster to customers, thus winning new business. —Source: Information Week," 20 Great Ideas"
We have discussed strategy and sourcing. Next, we'll discuss the performance of the executives in delivering results.
The executive staff is subject to review by the audit committee. As you recall, it is this committee's job to challenge the assumptions and assurances in the organization. The audit committee is expected to provide management oversight and allow executives the opportunity to discuss confidential issues about the business. An effective audit committee will advise individual executives with an opinion for possible solutions to internal problems.
Independent auditors are hired by the audit committee to provide an impartial (independent) opinion as to the status of internal controls. Audit committees are frequently the client of external audit engagements.
As an IS auditor, you need to find evidence of management governing IT and the enterprise. The composition and performance of the steering committee could be a powerful source of evidence. You may be able to review the plans and meeting minutes from the committee. The auditor's goal is to assess the performance of the CEO and executive management in developing and leading a successful strategy based on business objectives.
By using tactical management, an organization selects a maneuver or technique that will render a better result. The goal of tactical management is to manage the return on investment for information systems. The successful manager will need to establish a requirement for the collection of performance metrics. The performance metrics are used to determine whether the results are improving or deteriorating against a baseline. The same metrics are used to demonstrate management success to the executives and stakeholders.
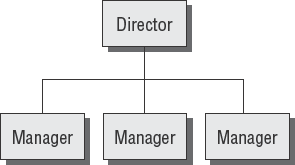
Figure 3.8 illustrates the tactical level in the organizational chart.
Individuals at the tactical level should be providing support to the strategic objectives. The majority of planning work accomplished at the director level is tactical in nature. Strategic plans are handed down from top management. The director level is expected to fulfill the strategic goals by providing solutions without the authority to make changes in other areas of the organizational structure. A director's authority outside of their own department is limited to requesting and negotiating.
Every IS organization has a number of functions that it should implement to fulfill its strategic plan, its tactical plan, and its daily plan. An auditor looks at any industry-standard benchmarks for performance optimization that have been adopted. Several are available, including the National Institute of Standards and Technology's controls matrix and the Federal Information Security Management Act (FISMA). In addition, the organization may use an organizational planning maturity model such as the Organizational Project Management Maturity Model (OPM3) by the Project Management Institute.
It is possible that the organization benchmarks its business continuity plans and disaster plans after the public domain version of the Business Continuity Maturity Model (BCMM). The organization may have an information assurance program and be using the ISO 27002 or Capability Maturity Model (CMM).
The value of benchmarking is to determine the organization's position and progress as compared to a recognized reference. There are several competitive advantages to benchmarking, the first of which is the ability to attract respect and more-favorable terms from stakeholders. Every IS organization has an issue regarding financial management.
The question comes up, what does IS pay for?
What does the department pay for?
What does the project pay for?
Individual departments may be operating a shadow IT group funded by department budgets. This condition usually indicates some type of failure to align to the business objectives in the strategic plan.
All levels of management are responsible for providing leadership. Good leaders generate better performance from individual employees. To manage is to create an unnatural result. If the same result would naturally occur by itself, then you are not managing it. The objective of management is to get a better result. Every organization needs to plan for how to collect continuous evidence of performance. The minimum requirements of good management include the following:
Performance reporting
General record keeping
Safeguards and implementation details of controls
The auditor needs to review a variety of documents, including the organization's strategic plan, policies, IT plans, and operating procedures. These include plans for training, system mitigation, system certification, disaster recovery, continuity, and the inevitability of change. As an auditor, you will need input from people besides IT management to ensure alignment with the enterprise objectives.
Performance review refers to the identification of a target to be monitored, tracked, and assigned to a responsible party, and the resolution of any open issues.
Existing systems require a regular review to determine the ongoing level of compliance to internal controls and the next steps to take.
The Capability Maturity Model (CMM) is a method for evaluating and measuring the maturity of processes in organizations. A rating scale from 0 to 5 is used. A score of zero indicates that nothing is occurring. Level 1 maturity indicates that the initial activity was successful and may later progress up to level 5, when the activity is statistically controlled for continuous improvement. The CMM rating scale was developed by the Software Engineering Institute at Carnegie Mellon University and has been widely used for rating business process capabilities.
Note
The Capability Maturity Model is also discussed in Chapter 5.
Levels of the CMM are as follows:
- Level 0 = Nothing yet
The level of zero is implied in the CMM but may not be noticed. This is important when evaluating process maturity. Missing processes and controls without evidence will be rated as zero. Many individuals assume that all controls are present when, in fact, some may be missing. A process or control must have occurred in order to reach a level of maturity (1–5).
- Level 1 = Initial
Processes are unique and chaotic. The organization does not have a stable environment. Success is based on individual competencies and heroics. This level often produces products and services that work. However, output may exceed the available resources or be dependent on specific individuals. At level 1, people have the most freedom and flexibility to make their own decisions.
- Level 2 = Repeatable
Processes are repeatable. The organization uses project management to track projects. The project status is communicated by using milestones with a defined work breakdown structure. The basic standards, processes, descriptions, and procedures are documented.
- Level 3 = Defined
Processes are well documented and understood. Level 3 is more mature and better defined than level 2. Processes have objectives, measurements, improvement procedures, and standards. The results in level 3 are predictable by qualitative measure.
- Level 4 = Managed
Management can use precise measurement criteria to control the processes and identify ways to adjust the results. Processes at level 4 are predictable by quantitative measure.
- Level 5 = Optimized
This is the highest level, with continuous improvement of processes. Objectives for improvement are defined and continually revised to reflect business needs and objectives. Products at CMM level 5 have been so well defined that they are effectively converted into a commodity.
Level 5 is the ideal maturity for the maximum level of control in outsourcing. It allows the company to switch to using less-skilled people who are told what to do, pay less, and demand unquestionable authority. People have the least authority with the fewest decisions at level 5.
Note
CObIT version 4.1 uses the CMM approach to rate auditee performance by the maturity of their control environment.
Figure 3.9 shows the five maturity levels of the CMM in a lateral view.
Frankly, attaining higher levels in the maturity model increases the likelihood that internal controls are successful. A higher CMM grade indicates a definition of maturity with a higher degree of control.
Consider the typical hooks in an outsource contract. The buyer is hooked to it, and so the following questions should be asked:
Did the client give away resources, intellectual-property knowledge, or procedures of value that will not be recoverable?
Has the client given away highly qualified personnel who will no longer be in-house?
What will a contract change cost, if desired?
Can the contract be cancelled?
If a decision is made to cancel, what will it take to get the replacement function online?
This should be enough information for the prospective CISA. Let's take a look at two other sources of governance models. The first is the U.S. National Institute of Standards and Technology.
The U.S. government has set forth standards for engineering, weights and measures, and even computer processing. Management of the standards is assigned to the National Institute of Standards and Technology (NIST). The NIST standards for information technology management are mandatory for government agencies and optional for nongovernmental organizations. Many of the IT best practices were derived from NIST.
The U.S. government passed new internal control regulations under FISMA to unify the former Federal Information Processing Standards (FIPS). The U.S. internal control rating requirements for compliance are posted on the NIST website under the heading for special reports (http://csrc.nist.gov). NIST is an excellent resource with governance models that implement the CMM. Now let's look at an international standard.
Not to be outdone by the United States, the British government enacted their own security standard for government systems in 1995. The standard for British information security is British Standard 7799-1 (BS-7799 part 1). This uses similar internal controls for governance of IS systems. The ISO ratified the BS-7799-1 framework as ISO standard 17799. It then renamed 17799 as ISO standard 27002. ISO 27002 contains numerous points that are identical to the U.S. standards and work in concert. The ISO 27002 is actually functioning quite well as the executive summary for implementing the U.S. NIST 800-53 standard.
Just a reminder: ISO standards are protected by international copyright. Each country sells a single-user copy for the equivalent of $1 U.S. per page. That's how ISO gets funding. CISAs should not have bootleg copies under any condition. Besides the illegal issues, it violates your certification. Remember, the person who turns you in will usually get amnesty.
With so much attention on internal controls, the most important step an organization can take is the first—to implement controls. Any one of these best practices models should already be implemented.
We have already discussed the basics of quality management in Chapter 2, "Audit Process." Every organization should have processes in place to ensure that people are taking steps to do the right job at the right time. Quality management is a pervasive requirement.
Note
We will discuss quality further in Chapter 5.
In Chapter 1, we discussed a few basics of project management and the defined project management processes. Every organization should be following a well-defined project management methodology. Larger organizations will implement a Project Management Office (PMO). The PMO is composed of project managers for the organization. Their function is to manage the larger or more-critical projects.
As a CISA, you should recall that each project will have at least four distinct phases. Recall that the Project Management Institute defines five phases of project management: Initiating, Planning, Executing, Monitoring and Controlling, and Closing. However, PMI considers the process of getting a sponsor as the phase of project initiation. Most employees will never be involved in the Initiating phase. Therefore, ISACA wants the IS auditor to understand the four common phases of Planning, Executing (scheduling), Monitoring and Controlling, and Closing.
Now let's look at risk management in IT governance.
Risks occur at all levels. There are strategic risks, tactical risks, operational risks, and inherent risks. We have discussed these definitions in Chapters 1 and 2. Now let's look at one of the more common risk management formulas.
The first step in risk management is to calculate how much a single loss event would cost. This formula multiplies an asset value (expressed in dollars) by the percentage of loss for a particular event. For example, the percentage of loss of a stolen purse is likely to be 100 percent. In that example, the loss would be 100 percent of purse value. The loss due to data-entry errors may be equal to .007 percent of labor cost. This first formula is expressed as follows:

The single loss expectancy can be multiplied by the number of related events that are likely to occur for the year. The final result would be the estimated annual loss, as shown in the following formula:
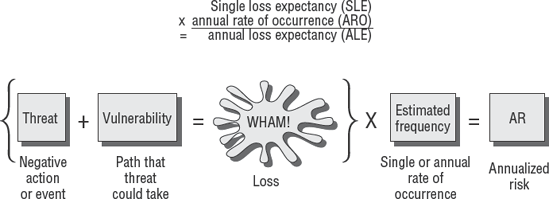
Risk management should be pervasive in all areas of business, including the IT department. As you might recall, we covered risk management previously in Chapter 2. The choices are to avoid, mitigate, transfer, accept, or eliminate the risk, and the goal is to reduce the level of risk.
When developing a risk management program, the auditor wants to find evidence that the risk management function has been implemented with an established purpose—in other words, that someone has been assigned responsibility, and risk management is a formal ongoing process, not just a review by lawyers.
Risks can involve many areas of the business. Impacts can be direct or indirect, but in either case will damage the organization's position, capital, or future opportunities. Typical assets include the organization's customer list, general information (which could be information about marketing or development), data, files, hardware, and software. Assets could also include the facility, a particular document, or services rendered. The risks, or threats, could be terror acts, malicious fraud, executing the wrong procedure, theft, or failure of controls.
It's interesting that criminals do not look at vulnerabilities the same way as an upstanding individual. To a criminal mind, a window becomes an entry or exit point to a building with the aid of a brick.
Risk management operates at a variety of levels: Management at the strategic level focuses on whether going forward with a particular strategy over a period of years is a good idea. Management could be at a project level—is the project on track? Or it could be at a daily or hourly or by-the-minute operational level to ensure that personnel are doing what they are supposed to do. Frankly, most major disasters are caused by a domino effect of a tiny failure multiplying into multiple failures that become catastrophic.
Overall, situations of high risk—where high loss, high consequence, or high impact is possible—require a method to ensure that the problem receives adequate consideration and the appropriate level of effort to prevent an unfortunate outcome. It is extremely common for IT staff to execute poor change control when dealing with interruptions, failures, theft, fraud, or just general risk while under pressure.
Determining the requirements related to hiring or terminating outsourced personnel can be challenging. Several companies have discovered way too late that certain organizations in the European Union have some rather stout requirements for expatriation and repatriation. The company may be liable for future employee benefits and the individual's cost of relocation. The requirements could also include severance plans that provide advance pay of up to about a year, the company's purchase of the former employee's home because that person did not have time to sell it, and payment of medical expenses for six months to a year. These requirements can make a huge difference if a company is planning changes such as layoffs or is trying to determine whether hiring a contractor is a good idea.
Every organization communicates sensitive data over delicate communication lines, which are not necessarily secure. In fact, every government has mandates to conduct surveillance for foreign intelligence in order to provide trade advantages for their citizens. News articles indicate that government organizations from competing countries are attempting to bring foreign technology to domestic organizations. It's the old game of economic espionage and political advantage. Data security is the number one concern when planning for communication crossing the border. We refer to this as transborder communication. One of the challenges is determining whether the data is legal or regulated across the border. The next concern may be that infrastructure issues impede delivery or quality of service from a geographically remote location.
Note
France was the first country to implement an organized system of spying on foreign nationals, beginning in the fourteenth century. The United States was one of the later countries to follow this initiative. Surveillance is mandated in the United States under the Foreign Intelligence Surveillance Act of 1978 (USC Title 50 Chapter 36, FISA).
IT governance is founded on the implementation of formal policies and standards. Each standard is supported by a matching procedure. The purpose of IT governance is to ensure that the risks are properly managed by mitigation, avoidance, or transfer. Let's review a short list of the policies required to address issues faced by IT governance:
- Intellectual property
The term intellectual property refers to data and knowledge that is not commonly known. This information possesses a commercial value. The IS auditor should understand how the organization is attempting to protect its intellectual property. There is no method for registering a trade secret. The owner has to undertake all control measures necessary to keep it secret. The rights of intellectual property can be destroyed by a failure of the organization to take preemptive action.
- Data integrity
What mechanisms have been put in place to ensure data integrity? Does the organization have input controls? How is the data validated for accuracy? Are the systems formally reviewed in a certification and accreditation process? What level of security management and access controls are present? Internal controls for data integrity are required by most industries and government regulation. The goal of data integrity is to ensure that data is accurate and safely stored.
- Backup and restoration
What are the plans and procedures for data backup and restoration? The number one issue in IT is loss of data due to faulty backup. The failures can be procedural or technical.
- Security management
Without security controls, ensuring data integrity is impossible. Internal controls prevent unauthorized modifications. SOX and FISMA mandate strong security controls.
- Mandatory versus discretionary controls
Every control is based on the human implementation. The organization needs to clearly identify its management directives for implementation of controls. Every control will be one of two fundamental types:
- Mandatory control
This is the strongest type of control. The implementation may be administrative or technical. A mandatory control is designed to force compliance without exception. Mandatory controls are managed from a centralized authority.
- Discretionary control
The weakest type of control is discretionary. In a discretionary control, the user or delegated person of authority determines what is acceptable.
- Monitoring
The IT systems should be monitored throughout the entire life cycle and in daily operations. The monitoring process provides valuable metrics necessary to compare alignment to business objectives. The purpose of governance is to lead. It would be impossible to lead without understanding ongoing conditions. Monitoring may prove that the organization is well run or a ticking time bomb. Without monitoring, determining whether an incident needs attention would be impossible.
- Incident response
A response is required for skilled individuals to deal with technical problems or the failure of internal controls. An incident may be major or minor depending on the cir cumstances. It is necessary to have an established policy, standard, and procedure for handling the incident response. At the beginning of an incident, it is impossible to accurately foretell the full impact of possible consequences. An incident response team should be in place to investigate suspicious situations. Care and diligence is necessary because it may later be determined that the initial response area is a crime scene. The mishandling of evidence could lead to forfeiture of the organization's damage claims. Unproven allegations against an individual or organization will frequently result in financial liability by the accuser.
Note
We discuss the details of monitoring and incident response in Chapter 6.
IT governance is conjoined with requirements to properly manage people. Good management is founded on human resource management that is well defined, fair, and consistent. Let's take a look at a few of the HR-related policies that affect IT management:
- Hiring
What are the organization's policies for selecting the best candidate? How should the interview process be handled? Quality management is required during the hiring process to ensure that the organization is in compliance with equal opportunity standards.
- Termination
Personnel may be terminated via either friendly or unfriendly procedures. The requirements for layoffs are relatively clear. What are the procedures for terminating personnel over extended periods of time? A special procedure may be necessary in the case of an upcoming personal retirement. A different procedure may apply to an employee who will be returning as a contractor on the same project. A hostile termination could stem from workplace violence, a criminal act, fraud, or a dispute with other personnel.
- Employee contracts
Many organizations use employee contracts to specify terms of employment. This technique is typically in effect in states with a Right to Work law. Right to Work laws are primarily about union versus nonunion employment—that people have a right to decide whether they want to be part of a union, that union membership can't be a condition of employment. The use of employment contracts is invaluable for identifying the ownership of new discoveries. The employment contract details that the individual is performing work for hire, to the benefit of the employer organization.
- Confidentiality agreement
A standard practice is for employees and contractors to sign a confidentiality agreement. The purpose is to ensure that strategic, tactical, and operational details are not divulged outside the organization. Operating without a confidentiality agreement is usually a significant risk.
- Noncompetition agreement
The employer may implement a noncompete agreement to prevent the employee from working for a competitor until after a specific period of time. The terms of this type of agreement may be successful as long as they are not overly restrictive for the amount of money paid to the employee.
- Ethics statements
The organization should provide a statement of what is acceptable and unacceptable behavior. The best method for preventing a problem is to explain to an individual what actions are acceptable. Unacceptable behavior includes any activities for personal gain at the expense of the organization.
- Performance evaluation
A standardized process should be in place for reviewing an employee's performance. Each employee in the same basic role should be judged by their manager on defined criteria, pertinent to their organizational role. A quarterly or annual review is customary. More-progressive organizations may conduct reviews on a weekly or monthly basis. The morale of hard-working employees is damaged if the boss fails to notice their good work. The results of each review fall under HR record retention requirements for several years.
- Promotion policy
What is the organization's promotion policy? Is it based on job performance, education, or something else? The organization is required to demonstrate a fair and objective promotion policy in order to meet equal opportunity compliance.
- Work schedule
Work schedules and vacation schedules should be clearly defined. In some financial organizations, the vacation schedule is implemented as a detective control. An individual is forced to take vacations in one- or two-week increments. During their absence, another individual performs that job, and a discovery audit may take place to ensure that no irregular or illegal acts have been committed by the employee.
- Corrective counseling
What are the organization's policies for corrective counseling after poor performance from the employee? Care must be taken to prevent discrimination. An improper termination can create a financial liability. An employee may collect monetary damages if able to prove wrongful termination.
These are just a few of the many policies and procedures necessary to manage human resources. The IS auditor should be concerned about activities that increase the organization's level of risk. This includes Human Resources activities.
All computer systems need to be managed through their entire life cycle. Each system will go through a series of phases starting with a feasibility study. Next, requirements are generated and followed by system design. Systems are tested for integrity, and their fitness of use is determined. The life cycle continues into system implementation. After successful implementation, the system can migrate into production use. Each year of production, the system should undergo a review. The annual post implementation review focuses on the system's present condition compared to the more current requirements. A system may be upgraded to the new requirements or retired. This is just a summary.
The CISA is interested in understanding how the organization manages each phase of this process. Evidence should be obtained to support the auditor's conclusions.
Note
We cover the system life cycle in more depth in Chapter 5.
Information technology systems are so pervasive today that most organizations would cease to operate if their computers were unavailable. IT governance requires continuity planning for systems and data. Any disruption to operations could have far-reaching effects. Members of the media can be merciless in their quest to report an interesting story. The damage to an organization's reputation and brand can be fatal. ISACA wants every CISA to be aware of the need for continuity planning. We have expanded coverage of business continuity in Chapter 8, "Business Continuity and Disaster Recovery."
Adequate insurance is the minimum response for asset protection. This is a corrective administrative control. There are issues concerning insurance including the cost versus actual benefits received. Insurance does not replace lost market share, nor damage from unauthorized disclosure of confidential information. Acts of god, war, and terrorism are exempt from coverage in most insurance policies. Proper risk management reduces the organization's exposure. Risk reduction efforts, combined with insurance, are a good practice.
Note
Normally, the term self-insurance implies a level of protection that does not exist. Self-insurance means the organization is accepting the risk with full liability for any consequences.
The CISA should be aware that there is a difference between real insurance and self-insurance.
Performance management serves to inform executives and stakeholders as to the progress of current activities. A fair and objective scoring system should be used. Scores may be based on a current service-level agreement. Another method is to use key performance indicators (KPIs), which tend to represent a historical average of monitored events. Unfortunately, a key performance indicator may indicate a failing score too late to implement a change. A perfect example of a KPI is the high-school report card. By the time the score is reported, the target child may not be eligible to graduate.
A process should exist to report the performance of IT budgets and noncompliant activities. Executive management should encourage the reporting of issues without punishing the messenger. Some effort is necessary to ensure the accurate and timely flow of information upward to the executives. False information can be very damaging.
Instead of just having a qualitative assessment of good or bad, or high, medium, or low, this should be an accounting exercise using a quantitative measure. It could be semi quantitative, using a ranking scale similar to scoring in a school: 70 to 79 is a C, 80 to 89 is a B, 90 to 100 represents an A, and then percentages such as A– or A+. This technique will convert a subjective decision into a more objective review. The Capability Maturity Model is very effective for communicating performance metrics.
Figure 3.10 shows a brief glimpse of the CMM used to report metrics.
When an organization decides to consider outsourcing, one of the concerns is that the organization may lose the visibility necessary to effectively operate the processes. The outsource contract should require a right to audit the service provider. Occasionally the response is that they cannot be audited by everyone because they do not have the time or the money, but will give you a copy of the SAS-70 service provider's audit report, which is a standard audit format.
Unfortunately, the report may be insufficient to management needs, because the report is probably vetted and groomed to ensure it states the level of information the service provider wants to convey, not necessarily what may be observed during your own audit.
Our suggestion is that if a company is considering outsourcing, the auditor could ask, "Why not run a controls audit and an SLA audit using the client's auditor, or a full audit before signing the contract?" The goal is to determine whether the service provider is fulfilling their entire obligation before signing a contract. Why risk the time and money to sign a contract while silently hoping and praying that the requirements are met?
Tip
An excellent idea is to implement a business process review before outsourcing.
One of the principles in business that remains constant is the need to improve your processes and procedures. Most trade magazines today contain discussions of the detailed planning necessary for implementing change in an organization. The concept of change must be accepted as a fundamental principle. Terms such as business evolution and continuous improvement ricochet around the room in business meetings. It's a fact that organizations which fail to change are destined to perish.
As a CISA, you must be prepared to investigate whether process changes within the organization are accounted for with proper documentation. All internal control frameworks require that management be held responsible for safeguarding all the assets belonging to their organization. Management is also responsible for increasing revenue. Let's discuss why business process reengineering (BPR) review is important.
Tip
Every IS auditor is required to choose sides. An IS auditor's independence would be compromised by participating in a nonaudit role on the BPR project. You can't audit your own work. If an IS auditor has participated in the design of systems, processes, or procedures as part of the BPR team, that auditor is required to refuse the audit of those functional areas. Therefore, it's common to have two sets of auditors during BPR projects. One set works on the BPR team to help steer the project, and auditors from a second firm perform verification audits. Cha-ching!
Times change. People change. Needs change. It is said that change is the only constant in life. BPR is used to improve process performance by removing, combining, or replacing steps that are no longer important.
BPR is concerned with reducing costs of the existing process while increasing performance. BPR includes three major areas for improvement:
- Business efficiency
Efficiency will increase as the proficiency of workers increases as they gain experience. In the very beginning, work is slow with multiple test inspections to ensure that results will be acceptable. Workers will progress through the learning curve. With more experience, the workers' technique will become more refined. Eventually, the number of inspections may be reduced after the quality becomes consistent.
- Improved techniques
New improvements in the existing techniques will be discovered with more experience. An updated technique may eliminate previous steps that become unnecessary because of higher consistency. Improved methods and advances in technology can change how a process is performed. Several steps may be combined into a single step; eliminating the unnecessary steps increases efficiency. It may be necessary to add extra steps in the process if quality begins to decline.
- New requirements
New requirements may be added in response to a regulation, business need, or customer. The existing business process will be reworked to comply with the updated requirements.
BPR activities are performed as a unique project. The BPR project will design a new process or improve existing processes to replace the outdated, inefficient processes.
Note
You may want to refer to Chapter 1 for a quick refresher on project management.
Every good methodology specifies a basic vision to illustrate its strategy, and recommends standards to follow and procedures to use. There is more than one version of the BPR methodology available for businesses. For clarity, we are going to focus on the views representative of ISACA and the CObIT framework of management guidelines. These are considered an excellent resource in the industry.
The key to governance is for management to take responsibility as the leader for implementing change, while establishing an adequate system of internal control. This would include implementing a culture of continuous monitoring to fuel continuous improvement. There is a saying: "You can't fix what you can't prove." It would be ridiculous to charge off on a whim under the guise of BPR without supporting evidence. Yet some companies do it all the time. BPR is often coupled with an enterprise resource planning (ERP) implementation. It would be a reckless misuse of company resources to switch to a particular ERP system just because it sounds cool, makes you look important, or aids your political agenda because it's the same system used at a former employer.
Consider for a moment that many of us are members of the general public. Stock-holding investors are on the outside of the business without full knowledge of the internal processes. We expect you as the auditor to investigate the supporting evidence and tell us whether management is making good, solid decisions based on intelligent facts. We hold you, the auditor, responsible for telling the truth. Please keep this fiduciary responsibility in mind when working on BPR-related projects.
It is a commonly held belief that there is a fine line between genius and insanity. The secret is to know which side of the line you're on. The latter is beyond the scope of this book, so let's focus on the genius side. True genius is grounded in a logical progression of intelligent thought.
History is loaded with the names of famous people regarded as the inspired genius in their fields. One characteristic is pervasive: Every great accomplishment was based on lessons learned from careful observations. These observations provided the facts necessary to fuel a progression of ideas into an intelligent hypothesis. The next step was to determine an objective method for testing the hypothesis. Useful metrics were created to help measure results. If the hypothesis failed, it was back to the drawing board to check their work and revise their ideas. Each test simulation yielded additional data to steer their thoughts.
Even Leonardo da Vinci's ideas were considered wild hallucinations until it was realized he had collected evidence indicating a crystal-clear thought process involving observation, hypothesis, and testing.
All BPR projects are intended to be strategic in nature. We are going to change the way the business operates. Service organizations and manufacturers need a mechanism to support their evolution. Continuous improvement is necessary to survive the challenges of increasing competition with the constant pressure of rising costs. Any change to a running business introduces new magnitudes of risk. Thin profit margins leave little tolerance for bad ideas or inadequate implementation. Proper reengineering will involve comprehensive changes affecting the design structure of management, people in support roles, information systems, and operating policies.
One of the auditor's duties is to impress upon management that controls are necessary. You may need to correct their view that controls appear to slow the process by explaining how controls are necessary to offset the risks that would be difficult to manage or to measure. The most damaging risks are those whose likelihood or effect you cannot calculate. Repeated answers of "I don't know" may indicate that you're on the wrong side of the genius-insanity line.
Let's instill a few guiding principles for your BPR activities. The purpose is to lend a structure to support the innovative thinking necessary for you to be successful. Reengineering projects are founded on specific situations and require creative ideas to generate the appropriate solution. Let's look at three possible approaches:
- Think big
This is an unconstrained top-down approach. The focus is on determining how the organization's strategy can be implemented without being restrained by existing processes. Many of the details in the current processes are ignored. All emphasis is placed on the future process to be (end state). Ideas are generated to answer the question, what will it ultimately be? This is consistent with the step change philosophy presented by authors Michael Hammer and James Champy in Reengineering the Corporation (Collins, 2006). Donald Trump is famous for using this approach because people naturally want to be involved in big projects. Tom Peters illustrates the power of thinking big in his fabulous book Re-imagine! (Dorling Kindersley, 2006). The risk is bigger and so are the rewards.
- Incremental
This is a bottom-up approach that models existing processes to gain deeper understanding. Metrics are created and compared to identify what can be changed to streamline the process. The focus is on making incremental changes to the current process by identifying opportunities for improvement. The downside of the bottom-up approach is the tendency for BPR teams to spend too much time documenting the current process. By focusing so hard on the current process, their innovative thoughts and ideas are stifled. Overall gains are small because creative genius is lost. This tends to fit the stereotype of detail-oriented accountants spending too much time counting the beans while ignoring the potential that could be realized by exploiting a broader strategy.
- Hybrid approach
The most practical application is a mixed approach. Planning begins with a top-down view of the big-picture strategy. Bottom-up research is performed to understand the current functionality and define the processes in use. The process starts by grading what you have as good, average and poor (GAP). Then comparing it to what you want. This GAP analysis is used to identify the differences between what is getting done and what needs to occur. The GAP will provide valuable insight for determining the best transition path. This will result in an initial recommendation that may require relatively small changes to remove bottlenecks. Alternatively, it could yield a series of more-complex projects, thus charting a course that places the organization ahead of its competitors. This is a noble route that the auditor is advised to undertake.
To be competent in BPR requires a working knowledge of auditing standards and the control frameworks such as CObIT. The competent auditor must possess the following skills before undertaking a BPR project:
Up-to-date information systems auditing skills
Specialized CISA audit standard knowledge
Specialized knowledge of the company processes and procedures
Specialized knowledge of the functional area being audited
General management knowledge and skills
Interpersonal "people" skills
The IS auditor can make an important contribution to their knowledge of internal controls and systems. Frequently the auditor will have to reengineer their own skills and audit approach to deal with the radical changes created by BPR. When auditing BPR, the CISA complements the other auditors on the BPR team who will be representing the special needs of finance and regulatory compliance.
ISACA expects every CISA to understand the operating techniques used in BPR projects. There are some conflicting viewpoints by different BPR experts; however, most of the suggested techniques include the following:
Revising the logical order of individual processes to simplify the process of improving overall quality
Reviewing a logical diagram of an existing process to determine whether multiple jobs can be combined into fewer steps
Giving workers additional authority to make operational decisions while maintaining an acceptable level of control
Eliminating superfluous or overlapping processes
Standardizing processes, procedures, methods, products, and tools across the organization
Using the most effective controls to ensure governance
Converting manual processes into automated methods
Establishing parallel processes for business continuity
BPR projects should be undertaken only when the business value can be demonstrated. Three simple methods to demonstrate business value are to increase capability, to reduce operating cost, or to obtain compliance with a new requirement. The BPR project may commence after the steering committee has reviewed the ROI evidence, agreed with the scope, and granted formal approval to proceed.
ISACA cites six basic steps in their general approach to BPR. These six steps are simply an extension of Shewhart's Plan-Do-Check-Act model for managing projects:
- Envision
Visualize a need (envision). Develop an estimate of the ROI created by the proposed change. Elaborate on the benefit with a preliminary project plan to gain sponsorship from the organization. The plan should define the areas to be reviewed and clarify the desired result at the end of the project (aka end state objective). The deliverables of the envision phase include the following:
Project champion working with the steering committee to gain top management approval
Brief description of project scope, goals, and objectives
Description of the specific deliverables from this project
With a preliminary charter to evidence management's approval, the project may proceed into the initiation phase.
- Initiate
This phase involves setting BPR goals with the sponsor. Focus on planning the collection of detailed evidence necessary to build the subsequent BPR plan for redesigning the process. Deliverables in the initiation phase include the following:
Identifying internal and external requirements (project specifications)
Business case explaining why this project makes sense (justification) and the estimated return on investment compared to the total cost (net ROI)
Formal project plan with budget, schedule, staffing plan, procurement plan, deliverables, and project risk analysis
Level of authority the BPR project manager will hold and the composition of any support committee or task force that will be required
From the profit and loss (P&L) statement, identify the item line number that money will be debited from to pay for this project and identify the specific P&L line number that the financial return will later appear under (to provide strict monitoring of the ROI performance)
Formal project charter signed by the sponsors
It's important to realize that some BPR projects will proceed to their planned conclusion and others may be halted because of insufficient evidence. After a plan is formally approved, the BPR project may proceed to the diagnostic phase.
- Diagnose
Document existing processes. Now it's time to see what is working and identify the source of each requirement. Each process step is reviewed to calculate the value it creates. The goal of the diagnostic phase is to gain a better understanding of existing processes. The data collected in the diagnostic phase forms the basis of all planning decisions:
Detailed documentation of the existing process
Performance measurement of individual steps in the process
Evidence of specific process steps that add customer value
Identification of process steps that don't add value
Definition of attributes that create value and quality
Put in the extra effort to do a good job of collecting and analyzing the evidence. All future assumptions will be based on evidence from the diagnostic phase.
- Redesign
Using the evidence from the diagnostic phase, it's time to develop the new process. This will take several planning iterations to ensure that the strategic objectives are met. The formal redesign plans will be reviewed by sponsors and stakeholders. A final plan will be presented to the steering committee for approval. Here's an example of deliverables from the redesign phase.
Comparison of the envisioned objective to actual specifications
Analysis of alternatives (AoA)
Prototyping and testing of the redesigned process
Formal documentation of the final design
The project will need formal approval to proceed into the reconstruction phase. Otherwise, the redesign is halted pending further scrutiny while comparing the proposed design with available evidence. Insufficient evidence warrants halting the project.
- Reconstruct
With formal approval received, it's time to begin the implementation phase. The current processes are deconstructed and reassembled according to the plan. Reconstruction may be in the form of a parallel process, modular changes, or complete transition. Each method presents a unique risk and reward opportunity. Deliverables from this phase include the following:
Conversion plan with dependencies in time sequence
Change control management
Execution of conversion plan with progress monitoring
Training of users and support personnel
Pilot implementation to ensure a smooth migration
Formal approval by the sponsor.
The reconstructed process must be formally approved by management to witness their consent for fitness of use. IT governance dictates that executive management shall be held responsible for any failures and receive recognition for exceptional results. System performance will be evaluated again after entering production use.
- Evaluate (post evaluation)
The reconstructed process is monitored to ensure that it works and is producing the strategic value as forecast in the original justification.
Comparison of original forecast to actual performance
Identification of lessons learned
Total quality management plan to maintain the new process
A method of continuous improvement is implemented to track the original goals against actual process performance. Annual reevaluation is needed to adapt new requirements or new opportunities.
These steps are easier to practice if you can relate them to something meaningful. Let's compare the BPR process steps with similar objectives in PMI project management and System Development Life Cycle (SDLC). An excellent way to get buy-in is to communicate by relating BPR steps to other methodologies already in use. Table 3.4 provides an illustration of the objectives in common.
Table 3.4. Comparison of Common Objectives
BPR Process Areas | PMI Project Management Phases | System Development Life Cycle (SDLC) | Objectives in Common |
|---|---|---|---|
Envision | Initiating | Feasibility | Determine scope, get a strong sponsor, target a process, set goals |
Initiate | Requirements definition | Obtain stakeholder buy-in, Identify external customer needs | |
Diagnose | Planning | Identify process attributes, possible benchmarks, activities, resources, roles, cost estimates, and communication needs | |
Redesign | System design | Devise solutions and alternatives through brainstorming and creative techniques | |
Executing | Development | Build prototypes to test the new design | |
Reconstruct | Implementation | Install IT systems, train users and support staff, begin transition | |
Managing and Controlling | Post implementation | Monitor and review the new process to see whether goals were attained | |
Closing | Document lessons learned, archive files, assign the process to a quality program (TQM). |
Now we need to clarify the role of information systems in the BPR effort. Just how does IS help make this project successful?
ISACA has identified four distinct roles to be delivered by information systems within the BPR projects. IT is a key supplier of tools necessary for the business to be successful. The four roles of IS are as follows:
Enable the new processes by improving automation.
Provide IT project management tools to help analyze the process and defined requirements.
Provide IT support for collaboration tools, teleconferencing, and specialized software supporting the business users.
Help business unit managers to integrate their business process with ERP systems. This may include integrating business partners through online transaction processing.
When looking at changes to business processes or when implementing these changes, the CISA should consider the use of the following tools to help define and document the processes being changed:
- Process maps
Diagram business processes by using flowcharts, influence diagrams, and fish-bone diagrams to assist in the definition and documentation of the process.
- Risk assessment
Look at the process by using the preceding risk categories as well as other categories. External risk and organizational risk should be assessed. Tools for risk identification, such as interviewing experts, brainstorming, holding risk identification roundtable sessions, and using the Delphi technique, should be considered. The Delphi technique uses a blind interaction of ideas between members of a group. Each member provides suggestions without knowledge of the suggestions by other participants. The exercise continues until a consensus is reached. We covered some of the other methods of performing a risk assessment in Chapter 2.
- Benchmarking
Compare your process to another process that is the same or similar.
- Roles and responsibilities
Define and document who is responsible for what process or what portions of the process. Many times the auditor will discover through interviews that several people know a portion of the process but no one knows the whole process.
- Tasks and activities
Define tasks and activities in conjunction with defining roles and responsibilities. The purpose is to define who performs what work and how it affects the overall process. The results may be documented in a work breakdown structure (WBS). All the tasks in the project are grouped into related work packages. Each task is assigned with its predecessor and successor dependencies identified. The list of tasks is referred to as the WBS.
- Process controls and data process restrictions
Document the current process with clearly defined checkpoints and/or checklists to ensure that the entire process is being performed. Define the data available for the process. This includes defining contributory sources and defining all data available from the process being considered for review.
Now it's time to discuss the types of planning tools available for BPR projects.
High-quality data can be assembled into information that will create significant power. Several planning tools and techniques have been developed to capture the data. We need good tools to combine this data into meaningful information. Let's look at a few of the available options:
Traditional project management such as PMI
Analysis tools such as Critical Path Method (CPM) or PERT charting
Presentation using graphical flowcharts (process flow diagrams) with decision trees
Manual process of setting goals, and performing root cause analysis and risk analysis
The right tools will harness the power necessary for your BPR project to be successful. Let's start with the manual process of setting goals through benchmarking. Later we will discuss the manual process of risk analysis in the BIA project.
Benchmarking is the process of comparing performance data (aka metrics). It can be used to evaluate business processes that are under consideration for reengineering. Performance data may be obtained by using a self-assessment or by auditing for compliance against a standard (reference standard). Evidence captured during the diagnostic phase is considered the key to identifying areas for performance improvement and documenting obstacles. ISACA offers the following general guidelines for performing benchmarks:
- Plan
Identify the critical processes and create measurement techniques to grade the processes.
- Research
Use information about the process and collect regular data (samples) to build a baseline for comparison. Consider input from your customers and use analogous data from other industries.
- Observe
Gather internal data and external data from a benchmark partner to aid the comparison results. Benchmark data can also be compared against published standards.
- Analyze
Look for root cause-effect relationships and other dependencies in the process. Use predefined tools and procedures to collate the data collected from all available sources.
- Adapt
Translate the findings into hypotheses of how these findings will help or hurt strategic business goals. Design a pilot test to prove or disprove the hypotheses.
- Improve
Implement a prototype of the new processes. Study the impact and note any unexpected results. Revise the process by using controlled change management. Measure the process results again. Use preestablished procedures such as total quality management for continuous improvement.
The benchmarking process is a valuable first step toward self-improvement. Figure 3.11 illustrates the benchmarking process.
Another excellent tool is the Business Impact Analysis (BIA). This would be more involved than benchmarking, yet a properly executed BIA will yield extremely valuable information.
The Business Impact Analysis (BIA) is a discovery process. Its purpose is to uncover the inner workings of any process. The BIA will answer questions about actual procedures, shortcuts, workarounds, and the types of failure that may occur. Armed with this knowledge, it is possible to assess priorities.
Part of the BIA is to determine what the process does, who performs the process, and what the output is. The BIA also determines the value of the process output to the organization. The BIA interviewer will ask key managers and key workers a series of questions to discover the low-level details of current processes. Some sample BIA questions that might be asked of key personnel in a BPR process review include the following:
What processes do you perform?
Who do you perform these actions for?
What tools, equipment, and systems do you use?
What request, event, or system provides an indication for you to start work on the subject (input)?
Get/show examples of the work the person performs (processes). Do multiple processes exist? If so, be sure to document each process for later review.
Who is the key vendor and the alternate vendor?
What is the time sensitivity of the process?
What is the basic priority of the process?
Where do you record your work (output)?
Who uses the output of your process next, and who depends on your output?
What happens if the process is
not used?
not available?
not performed?
not accepted?
What other methods could you use to accomplish the process? Are there workarounds or alternate processes that might already exist?
Would the alternate procedure really work?
How can you test it, or has it already been tested?
Who else knows this process and could do this in a crisis?
Who is the ultimate customer for this process?
How much revenue does this process create or support?
Is documentation on this process readily available?
Is documentation on the technical requirements for the process readily available?
Are there previous audit reports about this process that can be examined?
What is the projected lifetime of this process? Will the process continue to be used, or is this process being made obsolete by a future process or projected change in business?
Questions 17 and 21 provide key information for determining the true value of the process. Determining how much revenue the process creates or supports helps define its true value to the enterprise. Another measurement for value is to determine how long the process will remain in use.
For example, an organization can afford to spend $50,000 to reengineer a shipping process if they intend to use the process in perpetuity. The cost savings or cost avoidance saved each year will be used to pay for this effort. Processes expected to end within one year will need to be carefully evaluated to determine whether the payback is worth the effort. Practical advice suggests that processes selected for reengineering should have a lifetime in excess of one year, or be nonworking processes, to provide enough return value for the time and effort expended to reengineer them.
Proper planning of the process reengineering project requires documentation of the process to be modified. If the process has been correctly documented with all outputs and all interrelated activities, the chances of having "leftover parts" is minimized.
Radical improvements are not possible without increased risk. BPR projects are known to have a high rate of failure. Risks associated with changing an existing process must be identified. The ISACA Audit Standards, Guidelines, and Procedures identify several risk areas to consider when planning a BPR project. The risks can be broken down into three broad areas of design risks, implementation risks, and operational risks:
- Design risks
A good design can improve profitability while satisfying customers. Conversely, a design failure would spell doom to any BPR project. It would be reckless to undertake new projects without dedicated resources capable of committing the time and attention necessary to develop a quality solution. Often this type of detailed planning may consume more money and time than is available from key personnel. ISACA wants all CISA candidates to recognize the risks that may occur in the BPR design:
- Sponsorship risks
C-level management is not supportive of the effort. Insufficient commitment from the top is just as bad as having the wrong person leading the project. Poor communication is also a major problem.
- Scope risks
The BPR project must be related to the vision and the specifications of the strategic plan. Serious problems will arise if the scope is improperly defined. It's a design failure if politically sacred processes and existing jobs are excluded from the scope of change.
- Skill risks
Absence of radical "out of the box" thinking will create a failure by dismissing new ideas that should have been explored. Thinking big is the most effective way to achieve the highest return on investment. Participants without broad spatial skills will experience serious difficulty because the project vision is beyond their ability to define an effective action plan.
- Political risk
Sabotage is always possible from people fearing a loss of power or resistance to change. Uncontrolled rumors lead to fear and subversion of the concept. People will resist change unless the benefits are well understood and accepted.
- Implementation risks
The implementation risks represent another source of potential failures that could occur during the BPR project. The most common implementation risks include the following:
- Leadership risks
C-level executives may fail to provide enough support for the project to be successful. Leadership failures include disputes over ownership and project scope. Management changes during the BPR project may signal wavering needs that may cause the loss of momentum. Strong sponsors will provide money, time, and resources while serving as project champions with their political support.
- Technical risks
Complexity may overtake the definition of scope. The required capability may be beyond that of prepackaged software. Custom functions and design may exceed IT's creative capability or available time. Delays in implementation could signal that the complexity of scope was underestimated. If the key issues are not fully identified, disputes will arise about the definitions of deliverables, which leads to scope changes during implementation.
- Transition risks
The loss of key personnel may create a loss of focus during implementation. Personnel may feel burned out because of workload or their perception that the project is not worth the effort. Reward and recognition are necessary during transition to prevent the project from losing momentum.
- Scope risks
Improperly defined project scope will produce excessive costs with schedule overruns (variance from schedule). Poor planning may neglect the human resource requirements, which will lead team members to feel that the magnitude of effort is overwhelming. The reaction will cause a narrowing of the scope during implementation, which usually leads to a failure of the original BPR objectives.
- Operation/rollout risks
It's still possible for the BPR project to fail after careful planning. Common failures during production implementation include negative attitudes and technical flaws. These problems manifest in the form of management risks, technical risks, and cultural risks:
- Management risks
Strong respected leadership is required to resolve power struggles over ownership. Communication problems must be cured to prevent resistance and sabotage. Executive sponsors need to provide sufficient training to prevent an unsuccessful implementation.
- Technical risks
Nothing kills a rollout faster than insufficient support. Inadequate testing leads to operational problems caused by software problems. Data integrity problems represent a root problem capable of escalating into user dissatisfaction. Perceptions of a flawed system will undermine everyone's confidence.
- Cultural risks
Resistance in the organization is a result of failing to achieve user buy-in. Resistance will increase to erode the benefits. Effective training is often successful in solving user problems. Dysfunctional behavior will increase unless the new benefits are well understood and achieved.
BPR projects require the use all the principles found in project management. It is advisable to consider project management as the framework for your BPR project. Many of the PMI processes, mentioned in Chapter 1 will be utilized to manage the project inputs, tools (techniques), and outputs necessary for the project to be successful. By following a recognized standard, the project manager can prevent most of the errors and common omissions inherent in almost any project.
Let's discuss some practical ground rules for BPR projects:
Don't fix an existing process unless it's broken.
Calculate the ROI before investing any resources.
Make sure you fully understand the process before you try to fix it.
Make sure you don't have any "leftovers" after reengineering the process. All the original components should be reused, modified, or formally retired.
The following points illustrate how each of these ground rules applies to planning a BPR project.
The return on investment is usually very small unless the existing process is already broken. Small improvements can be gained at lower cost by using the normal change control process. There is no need to implement a BPR project unless dramatic changes are required. The highest return on your investment will be realized by collective brainstorming to fix a missing or broken process.
There is never enough money for all the proposed projects. Opportunity is synonymous with the availability of resources. Businesses must change and evolve to remain competitive. It would be both reckless and negligent to charge off on a new project without having first calculated the potential return on your investment. So ask, "What will we actually get back for our money?" Resources should be spent using the principles of highest and best use, also known as portfolio management.
If you only had $10,000, what is the best use of that money? Where should you invest your thoughts and time? You may consider only those ideas that have a profound or life-changing effect rather than just prepaying some outstanding bills. For example, is the money best spent on a minor system upgrade or by investing in additional staff training? Choose the solution that best improves your bottom-line profits. Don't waste money on something with no return or a low return.
Even if the process is suspected to be faulty, it's important to have proper evidence before making any changes. The fastest way to failure is to start making changes based on incorrect assumptions.
The BIA is an efficient method for collecting high-quality data. The BIA process involves interviewing subject matter experts to determine what the process does and tracing the root sources of process specifications. A well-run BIA will uncover a complete blueprint of the entire process flow in sequence with influential dependencies and some of the known alternative methods to accomplish the desired results. BIAs are frequently used in organizational acquisitions, divestitures, business continuity planning, and business process reengineering. The value of the BIA is the ability to make decisions factoring in all of the low-level details indicating over reliance, untapped capacity, and alternative sources with the potential to increase net revenue.
Everything in the current process exists for a reason. This is why it's necessary to discover the specifications for inputs, actions, and outputs of the process before making any changes. Some specifications will be new, whereas others may be eligible for retirement. Each specification needs to be thoroughly investigated, no matter how small. The purpose and relationship of every specification needs to be considered before you can determine its disposition.
At one particular organization, the inventory manager misunderstood the reason why the factory needed to warehouse more than 100,000 product labels. It turned out that the label was a custom-made warning label that cost almost nothing if ordered in very large quantities. The labels had a moderate delay from ordering until shipping to the factory. It turned out to be an extremely serious violation of government law if the product shipped without the required warning label. In fact, it was better to halt production than to ship without the mandated warning label.
Every hour spent in research and planning should be focused on tracing the most current specifications. Each specification will either be reused, modified, or formally retired.
The BPR selection process looks for areas with the greatest return on investment. The needs of each organization are unique. Executive governance dictates that the executives must define unique selection criteria and a selection process. Each process under consideration for reengineering must be evaluated and generally fits into one of the following categories:
Nonworking process
Marginal process
Working process
Excluded process
In addition to these categories, the overall value needs to be considered in the equation. Is there a reasonable ROI for reengineering each process under consideration? Using a report in the format of Table 3.5 is helpful for organizing the discussion of investment, return, and priority.
Note
You should remember that your goal during BPR is to ensure that the organization is properly managing the entire process.
Let's summarize each of these categories with a little more detail:
- Nonworking process
Some elements of the process are simply not working. It may be a manual or an automated process that can't deliver to the expectations of the user. This is an ideal target for process reengineering. Nonworking processes are usually the highest priority if their business value can be justified. Priority will be based on the anticipated financial return that the process can generate.
- Marginal process
This type of process seems to work yet fails to generate any tangible benefit. Something about the design may be preventing it from generating its full potential. It may be a control issue or design failing to deliver to a specific need. The output of the process needs to be closely reviewed to determine what need it was intended to solve and whether there is any value created by reengineering it. Otherwise, the process might be discontinued.
- Working process
This process is currently in use and generating some type of meaningful benefit. It should have existing documentation of how the process works and its related specifications. Working processes are expected to have a support staff and the necessary controls to achieve compliance with their business objective.
- Excluded process
An excluded process might be exempt from BPR because of its special nature or limited frequency of use. Politics is never a valid reason for exclusion. A process nearing retirement may be excluded because BPR would not generate any increase in value.
Without excellent leadership, the BPR project can become a convoluted mess. Even the simplest of objectives may wander aimlessly into failure. We want to take a few minutes to diagnose some of the more common BPR problems you may encounter as an auditor:
- Problem: Reengineered process resembles the existing process
Compare the process to its current objectives and specifications. It will not be identical unless the initiation and diagnostic phases were compromised. If the diagnostic phase was objective, the best solution is to rethink the redesign by using a higher-level approach. Too much emphasis was placed on duplicating the attributes of the old process if the redesign occurred at too low a level or protected a politically sacred area. Approach it again with a "think big" philosophy.
- Problem: Business process does not fit all the customers
Unserved customers may be outside the target market. Analyze the intended audience to determine whether it represents your most profitable clients. If so, there is no problem in the BPR design. Use the Pareto principle (aka 80/20 rule) to evaluate the net revenue created by the unserved customers. Stick to those clients who generate the highest return in net profits. Times change; everyone else may not be your target customer.
- Problem: Implementation of the new process is stalled or slowing
Failure to implement indicates problems in reconstruction or political blocking. Implementing a smaller pilot project may work to smoke out the problem. Extra effort may be needed to resell the concept and to train the users. A strong leader is usually willing to remove political obstacles (or the person obstructing progress) as long as the effectiveness of the new process has been proven.
- Problem: New process is not performing as expected or generates hidden incompatibilities
Business processes have informal relationships that may have been missed during BPR planning. Perform a stakeholder analysis to identify missing stakeholders or underrepresented dependencies. The problem can be rooted in leadership failure during initiation, inadequate diagnosis, missed material specifications, or poor planning during reconstruction. This is a frequent problem found in outsourcing arrangements after the impact of total costs are calculated. It may occur during initial implementation or post evaluation.
Note
Additional information on business process reengineering can be found under the BPR guideline G-26 in the ISACA Audit Standards, Guidelines, and Procedures.
Tactical management involves the departmental director and manager. Tactical performance reporting should occur during weekly and monthly status meetings with senior-level executives. Tactical performance is frequently included during a regular audit.
As an IS auditor, you will be interested in learning the scope and extent of project management methodologies in use. Your interest will include gaining an understanding of the management tools in use and application of management controls. Tactical management should be using a change control process that exercises advance planning, risk management, and due diligence. The auditor should seek materially relevant evidence demonstrating management's efforts in support of the strategic objectives. The auditor's opinion should include a determination of the effective level of IT integration with various stages of project management. Is tactical management well integrated with measurable performance?
We start the discussion of operations management with a simple definition. An operation is a procedure to set forth or produce a desired result.
The objective of operations management is to promote consistency with an effective response to the user requests. Operations management represents support for issues faced in day-to-day business. The operations support is sometimes referred to as firefighting or user support. This section briefly covers the IT goals and operations management.
Every organization faces the challenges of sustaining operations. You will investigate whether the IT staff has the capability to sustain current operations. Three areas of interest are immediately identifiable. The auditor should seek evidence to discover whether the following three sustaining factors are met:
Adequate staffing
Written procedures
Level of staff integration
It would be practically impossible to sustain regular operations without documented procedures executed by an adequate number of well-trained IT staff members. The staff members must be able to interact and communicate effectively inside the IT organization and with the business organization. To ensure these objectives, each member of the IT team will need to have specified roles and responsibilities.
Performance of all operations should be tracked and reported by using metrics developed for the user's needs. These metrics should be based on best practices of NIST, COSO, ISACA's CObIT, and other industry standards. It is the responsibility of tactical management to develop the metrics. Operations management is required to report the detail necessary to generate a score.
Note
Chapter 6 covers operations and metrics in more detail.
Change control is an organized process for making sure that the best possible decision is reached. The reality is that any change introduces new variables. A person can execute a minor change that does what it intended, but then also has unintended consequences such as disabling or invalidating a previous control setting or a processing method. So change control must be a methodical process.
The change process should be evidenced by supporting policies and procedures. One employer, for example, had a policy that changes would occur only on Tuesdays and Thursdays in the evening. Users were required to provide their work-acceptance test procedures along with a competent user from their department. The user would run their own tests to prove whether the evening change had an impact. Positive impacts were desired. Negative impacts signaled the need to rerun the intended change procedure or restore the system to its earlier condition. Management allowed changes over the weekend if the requirement was so broad as to exceed an 8-hour window. Their preference was to avoid scheduling changes that would result in the next workday being on Monday. Problems occurring on Monday tend to set a negative tone for the entire week.
Internal auditors should be involved in change control meetings. The visibility and experience of the internal auditor present a valuable opportunity for the client. An internal audit should review requested changes to ensure that each change complies with the best practices of change management. You can bet that the staff will become more alert when they realize that the internal auditors are watching.
The auditor will need to evaluate whether the organization has provided effective daily support in accordance with the IS strategy. What is IT expected to deliver? Taking that into consideration, what are the issues considering fulfillment and capacity to supply this need? There should be a systematic decomposition of how each business objective is translated down into specific needs, which are fulfilled by specific tasks. If there is no stated requirement in a business objective, there should be no specific need, only a request. The IT alignment concept is to dedicate all efforts toward bona fide goals identified in the business strategy, not requests.
The auditor's job is to ensure that proper controls are in place and are appropriate to the unique risks of each source and location.
In this chapter, we have reviewed the authority levels in the organization and controls used for IT governance. A short definition of IT governance is to effectively lead and monitor performance of the information technology investment. IT governance exists at three levels: strategic, tactical, and operational management. Top executives are responsible for providing the strategic guidance with policies and decisions to define objectives; department directors provide tactical management with standards and plans for their subordinates. The operational functions and procedures are controlled by the managers with execution by staff workers.
- Know how to evaluate the performance and effectiveness of the IT governance structure.
Does IT support the organizational objectives? You will investigate how the IT management decisions are made. After a decision is reached, it is important to understand how the directions are communicated to ensure that the decision supports the desired outcome. Does evidence indicate that management is leading the activities necessary to fulfill the business strategy?
- Understand that the organizational structure must be designed to support the business strategy and objectives.
Does the client have a well-documented organizational chart with accurate job descriptions? How does the client handle problem reports, user complaints, and staff member concerns? Is there a mechanism for management oversight?
- Be aware that the IT policy, standards, and procedures must be developed under the supervision of management.
A formal process should exist to ensure that each policy is in support of legal requirements and fulfills a business objective. You need to understand how the client determines policies and standards. Who approves the adoption and implementation? Do the policies and standards directly support the business strategy? Do the standards and procedures support the resulting IT strategy?
- Know that management is responsible for ensuring compliance with policies and standards.
Operating procedures must be developed to promote compliance and consistency. Have policies, standards, and procedures been formally implemented? How does management monitor compliance? How are violations detected, corrected, and prevented?
- Understand that risk management practices should be in use at all times.
Risk management applies to decisions concerning vendors, operational support, and projects. Is an effective risk management practice in use? Does the evidence show that risks are properly managed?
- Know that quality management requires the use of generally accepted IT standards.
A benchmarking process should be in use, with a control framework such as CObIT, ISO 17799, COSO control framework, and the OECD security guidelines. A maturity model such as CMM should be in use to show progress or regression in regard to internal controls.
- Understand that IT performance and IT vendors should be tracked by using key performance indicators.
The goal of IT governance is to align IT resources to support the business strategy. The role of IT is to solve support problems faced by business users. The IT steering committee is designed to identify business support issues to be resolved by IT. Key performance indicators are based on business needs and used to determine the IT return on investment.
Which of the following would be included in an IS strategic plan?
Brochures for future hardware purchases
At least a six-month list of goals from the IT manager
Target dates for development projects
Plans and directives from senior non-IT managers
What is the primary purpose of the IT steering committee?
Make technical recommendations
Identify business issues and objectives
Review vendor contracts
Specify the IT organizational structure
Which of the following functions should be separated from the others if segregation of duties cannot be achieved in an automated system?
Origination
Authorization
Correction
Reprocessing
The Software Engineering Institute's Capability Maturity Model (CMM) is best described by which of the following statements?
Measurement of resources necessary to ensure a reduction in coding defects
Documentation of accomplishments achieved during program development
Relationship of application performance to the user's stated requirement
Baseline of the current progress or regression
What would be the area of greatest interest during an audit of a business process reengineering (BPR) project?
The steering committee approves sufficient controls for fraud detection.
Planning methods include Program Evaluation Review Technique (PERT).
Risk management planning with alignment of the project to business objectives.
Vendor participation including documentation, installation assistance, and training.
If separation of duties cannot be achieved, which of the following is an acceptable alternative?
Compensating controls.
Mandatory hiring of additional personnel.
Change control review board.
Separation of duties is required.
What is the correct sequence for benchmark processes in business process reengineering (BPR) projects?
Plan, research, observe, analyze, adapt, improve
Research, test, plan, adapt, analyze, improve
Plan, observe, analyze, improve, test
Observe, research, analyze, adapt, plan, implement
Which of the following statements is true concerning the steering committee?
Steering committee membership is composed of directors from each department.
The steering committee focuses the agenda on IT issues.
Absence of a formal charter indicates a lack of controls.
The steering committee conducts formal management oversight reviews.
What is the primary purpose for running a lights-out data center?
Save electricity
Reduce risk
Improve security
Reduce personnel expense
The Capability Maturity Model (CMM) contains five levels of achievement. Which of the following answers contains three of the levels in proper sequence?
Initial, Managed, Repeatable
Initial, Managed, Defined
Defined, Managed, Optimized
Managed, Defined, Repeatable
Segregation of duties may not be practical in a small environment. A single employee may be performing the combined functions of server operator and application programmer. The IS auditor should recommend controls for which of the following?
Automated logging of changes made to development libraries
Hiring additional technical staff to force segregation of duties
Procedures to verify that only approved program changes are implemented
Automated controls to prevent the operator logon ID from making program modifications
Which of the following is the best example of mandatory controls?
User account permissions
Corporate guidelines
Acceptable use policy
Government regulation
What is the objective of incident response?
Ensure that the problem is reviewed by appropriate personnel using an established procedure to protect evidence.
Reduce the impact of a virus outbreak without inconveniencing users.
Provide an immediate estimate as to the consequence or impact of the damage.
Fix the user's problem as quickly as possible. The final resolution should be reported to the help desk.
An IS auditor is auditing the controls related to employee termination. Which of the following is the most important aspect to be reviewed?
Company staff members are notified about the termination.
All login accounts of the employee are terminated.
The details of the employee have been removed from active payroll files.
Company property provided to the employee has been returned.
Which of the following is not true concerning the process of terminating personnel?
The company must follow HR termination procedures.
Any company property in possession of the employee must be returned.
The employee must be allowed to copy any personal files from their computer.
The employee's recent history of login account activity should be reviewed in the audit log.
Which of the following represents the best explanation of the balanced scorecard?
Provides IT benchmarking against standards
Ensures that the IT strategy supports the business strategy
Measures IT help desk performance
Specifies procedures for equal opportunity employment
What is the primary business purpose behind business process reengineering (BPR)?
Eliminate jobs
Reduce steps to improve business efficiency
Change management direction
Increase stockholder value
Which of the following business process reengineering (BPR) risks are likely to occur during the design phase?
Transition risk, skill risk, financial risk
Management risk, technical risk, HR risk
Technical risk, detection risk, audit risk
Scope risk, skill risk, political risk
Which of the following answers contains the steps for business process reengineering (BPR) in proper sequence?
Diagnose, envision, redesign, reconstruct
Evaluate, envision, redesign, reconstruct, review
Envision, initiate, diagnose, redesign, reconstruct, evaluate
Initiate, evaluate, diagnose, reconstruct, review
What is the purpose of job descriptions and the change control review board?
Provide optimum allocation of IT resources
Eliminate disputes over who has the authority
Identify the hierarchy of personnel seniority
Provide guidance to the IT steering committee
What is the primary purpose of employee contracts?
Define the relationship as work for hire
Prevent individuals from ever working for competitors
Enforce the requirement to join a union
Specify the terms of employee benefits
What is the simple definition of strategy?
Ethical behavior of the executive management team to follow an iterative process of development
Using best practices in a uniform application
Implementing standards and procedures in a multilayered approach to accomplish the business requirements
Fundamental change in the way we do business
Which of the following is a governance problem that may occur when projects are funded under the "sponsor pays" method?
Deliverables are determined by the sponsor.
The definition of quality may be insufficient.
The sponsor may not implement the proper controls.
The sponsor may not have enough funding.
Which of the following is not a reason cited in the text that the balanced scorecard (BSC) could fail?
Politics of losing the department budget
Top management provides full support
Lack of BSC training and awareness
Empire building by the department head
Which of the following is not true concerning mandatory access controls?
Someone in authority determines what is acceptable.
The controls are implemented by using technical methods.
They are administrative controls.
They are administered from a central authority.
Which of these strategies is used in business process reengineering with an incremental approach?
Bottom-up
End-state
Unconstrained
Top-down
Shadow organization refers to two groups performing similar functions under different departments. What does the presence of a shadow organization indicate?
Sponsor pays
Actual usage billing
Charge-back
Budgeted cost
Which type of charge-back scheme is notorious for violating separation of duties or for attempting to exceed authority?
Sponsor pays
Actual usage billing
Charge-back
Budgeted cost
What is the advantage of using PERT analysis during projects for business process reengineering (BPR)?
It charts a detailed sequence of individual activities.
It is a critical path methodology.
It is used to perform root cause analysis
It enables the use of decision tree reporting
Which one of these is not a good reason for an organization to decide to reverse its outsourcing decision and bring the work back to be performed in-house?
Realizing a loss of control
Recognizing added delays in the overall delivery of service to their customers
Recognizing added expense after considering the total cost of long-distance supervision and price to make changes
Wanting to copy a competitor without doing the hard research
Which statement about the Capability Maturity Model is not true?
Level 3 provides quantitative measurement of the process output.
Level 3 processes have published objectives, measurements, and standards that are in effect across departmental boundaries.
Level 5 provides maximum control in outsourcing because the definition of requirements is very specific.
Level 5 maturity converts a product into a commodity and allows a company to pay less and demand unquestionable adherence to management's authority.
Which of the following statements has the best correlation to the definition of strategy?
Defines the supporting techniques to be used in support of the business objective
Defines the necessary procedures to accomplish the goal
Defines guidelines to follow in a recipe for success
Defines what business we are in for the next three years
Why is change control considered a governance issue?
It forces separation of duties to ensure that at least two people agree with the decision.
Change control increases the number of people employed and therefore provides a valuable economic advantage.
It allows management to hire less-skilled personnel and still get the same results.
Proper implementation of governance saves money by reducing the need for change control.
Which of the following is not considered a control failure?
Using a policy which lacks a detective mechanism to identify violations
Modifying an ineffective procedure outside of change control
Testing to discover how many policy violations have occurred
Implementing a policy or standard without consequences of failure
Which of the following is likely to be the most common method of IT control used in business?
Mandatory
Discretionary
Executive order
Preventive
D. The IS strategy must support business objectives from senior managers in other departments of the business. The IT plans should be designed to support the strategic business plans of the organization.
B. The purpose of the steering committee is to bring the awareness of business issues and objectives to IT management. An effective steering committee will focus on the service level necessary to support the business strategy.
B. Authorization should be separate from all other activities. A second person should review changes before implementation. Authorization will be granted if the change is warranted and the level of risk is acceptable.
D. The Capability Maturity Model provides a baseline measurement of process maturity. The CMM begins with no process defined and progresses through five phases of documentation and controls. The fifth phase represents the highest level of maturity.
C. The steering committee provides guidance to IT concerning business objectives. A risk management plan must be in use for every BPR project. The purpose of risk management is to determine whether the project can actually fulfill a business objective. The second part of risk management is to determine whether the organization will be able to complete the project and generate the desired results.
A. Compensating controls may be used when separation of duties cannot be achieved. Compensating controls include supervisory review, audit trails, exception reporting, and job rotation. An auditor would recognize that the lack of separation of duties is a control failure unless compensating controls are in place. Lack of compensating controls is also control failure.
A. The business process reengineering sequence is to plan for change, research possible implications, observe the current process, analyze potential opportunities for improvement and verify key performance indicators, adapt to the new/updated process, and work to improve the results.
C. The steering committee should be authorized by a formal charter. The lack of a steering committee indicates that IT is not governed by formal alignment to business objectives. The technology investment is not properly managed as an investment portfolio should be managed. The purpose of the steering committee is to convey business issues that IT should consider and objectives to fulfill. Membership of individuals on the steering committee should be formally designated.
B. The primary purpose of a lights-out operation is to reduce the personnel risk and environmental risk. Errors can be eliminated by separating equipment from the support IT personnel. Environmental risk is reduced by eliminating contamination from liquids, food particles, and debris. Maintenance and support personnel enter the lights-out operation for a short duration to perform any required functions.
C. The five levels of achievement in the Capability Maturity Model (CMM) are level 1 Initial, level 2 Repeatable, level 3 Defined, level 4 Managed, and level 5 Optimized.
C. Procedures should be implemented to ensure that only approved program changes are implemented. The purpose of separation of duties is to prevent intentional or unintentional errors. A logical separation of duties may exist if a single person performs two job roles. The ultimate objective is to ensure that a second person has reviewed and approved a change before it is implemented.
D. A government regulation is a mandatory control that forces compliance. Mandatory controls are the strongest type of control. Permission is explicit or it must be denied.
A. Incident response is intended to ensure that the problem is reviewed by appropriate personnel. Personnel should be properly trained and should execute an established procedure to document the condition, protect evidence, and resolve the problem. During the incident response, the problem will be analyzed to determine whether it was malicious or unintentional.
B. The former employee's access to information systems should be terminated immediately. The accepted practice is to terminate access while the employee is being informed of the termination in the HR department.
C. Employee access should be disabled upon termination from the organization. All of the other statements are true.
B. The balanced scorecard is used in management to ensure that all projects and activities are in direct support of the organization's strategy and objectives. The IT balanced scorecard is a subset of the organization's overall scorecard.
B. The purpose of BPR is to improve efficiency by reducing unnecessary steps or to implement improved techniques. Business process reengineering may be implemented to reduce operating costs or to achieve compliance with requirements.
D. The primary risks during the BPR design phase are improper scope, lack of necessary skills, political resistance, and a failure by management to support the project.
C. According to ISACA, the general steps in business process reengineering are to envision the need, initiate the project, diagnose the existing process, redesign the process, use change management to reconstruct the organization in transition, and evaluate the results.
A. Job descriptions specify the roles of each individual to ensure proper allocation of personnel. The change control review board ensures that changes and related activities are properly managed.
A. Employee contracts provide evidence of the work relationship: that the employee is providing "work for hire" to the company. All of the employee's discoveries and development become the intellectual property of the employer.
D. Strategy is best defined as a fundamental change in the way we do business. Strategy is the highest level of management and frequently a noble goal or idea. Standards provide a reference point for mid-level objectives. Procedures (aka best practices) are a low-level cookbook recipe for achieving a standard with repeatable performance.
C. The auditor needs to recognize that the sponsor may attempt to exceed their authority or fail to implement proper controls. Project scope should be controlled and verified to include separation of duties with preventative, detective, and corrective controls. It would be a failure in governance to allow a project to occur otherwise.
B. Using the balanced scorecard helps executives create a linked strategy to unite the activities of each department. Department budgets no longer exist. Funding and people are allocated in a strong-matrix style of project management. Departments get funding based on their share of the work supported in each project. Employees work from a personal scorecard, which has been created out of the project's work breakdown structure (WBS). This eliminates empire building and ensures that only the most valuable tasks receive any resources. Employees are graded on how many of the tasks are performed properly. Full support of top management is required for the balanced scorecard to work.
A. Mandatory controls are the strongest type of controls. They can be implemented by using both administrative and technical methods. Mandatory controls are centrally managed. There is no way to increase access except by formal promotion of access by the central authority. With discretionary controls, we allow someone to decide.
A. The incremental approach uses bottom-up modeling of the existing process. Overall gains tend to be small because this method focuses so hard on current processes. All the other choices represent a think-big (top down) approach without limitations. Top-down looks at what it could be, not what it is (end-state).
C. Shadow organizations indicate an integration failure caused by executive distrust or similar conflict. This creates additional conflict with inefficiencies of scale. Problems include conflicting strategies, and the sponsor violating separation of duties or exceeding their normal authority. Shadow organizations are known for duplication of effort, creating a high combined cost to the organization.
A. Sponsor pays is notorious for problems of exceeding authority, violating separation of duties, and failing to implement all the governance controls. Sponsors tend to pay for only what they want. Exceptionally good sponsors consider everyone's need ahead of their own agenda.
B. PERT analysis shows the critical path to illustrate the minimum specific tasks necessary to complete the project's objective. The CPM technique is a valuable tool for demonstrating what must be accomplished versus what was requested. High-dependency tasks get performed, while low-dependency tasks may be cancelled from the project.
D. Poor leaders may be playing the copycat game of making decisions without sufficient formal research (not using BPR). Decisions shall be made using supporting evidence, including total cost analysis of the combined overall impact, not just the function under consideration. Several organizations have realized that outsourcing was a poor choice after learning that it slowed their ability to deliver to the customer. Unique customer service, efficiency with better integration, and total delivery time to the customer are competitive advantages.
A. Qualitative measurement occurs at level 3, and quantitative measurement is at level 4. Level 5 effectively converts the product into a commodity with the intent to squeeze out every last percentile of improvement. All workers are expected to just do what they are told and have no authority. At level 5, the company has the most control and may decide to outsource with lower-paid workers.
D. Strategy defines the primary business we are in for the next three to five years. Using this information, the business can develop or adopt supporting standards and then create low-level procedures to accomplish the strategic objective.
A. Change control is a foundation of good governance. The purpose is to reduce questionable decisions. Benefits of change control include no longer wasting resources on low-profit tasks and preventing failure by reducing the risk (risk mitigation).
C. All of the available options except testing indicate that a control failure was present. The minimum effective control must include a preventative, detective, and corrective action.
B. Discretionary control is usually the choice in business. Its weakness is that someone decides rather than uses a formal centralized authority. Auditors should investigate how decisions are made and who makes each decision. This is usually a good place to look for control failures.