Terms you’ll need to understand:
✓ | TCP/IP |
✓ | IP address |
✓ | IPv4 |
✓ | IPv6 |
✓ | Subnet mask |
✓ | Default gateway |
✓ | Domain Name System (DNS) |
✓ | HOSTS file |
✓ | LMHOSTS file |
✓ | Windows Internet Name Service (WINS) |
✓ | The ping command |
✓ | the ipconfig command |
✓ | Wireless network |
✓ | Ad hoc mode |
✓ | Infrastructure mode |
✓ | 802.11 standard |
✓ | Wireless Equivalency Protection (WEP) |
✓ | Wi-Fi Protected Access (WPA) |
✓ | Wi-Fi Protected Access Version 2 (WPA2) |
✓ | Temporal Key Integrity Protocol (TKIP) |
✓ | Advanced Encryption Standard (AES) |
✓ | Service set identifier (SSID) |
✓ | Dial-up connection |
✓ | Broadband connection |
✓ | Virtual private network (VPN) |
✓ | Internet service provider (ISP) |
Techniques/concepts you’ll need to master:
✓ | Compare and differentiate IPv4 addressing and IPv6 addressing. |
✓ | List the private addresses used in an IPv4 addressing scheme. |
✓ | Configure a Windows Vista computer to use a giving IP address (IPv4 and IPv6), subnet mask, default gateway, and DNS server. |
✓ | Given a network connectivity problem, troubleshoot and correct the problem. |
✓ | Given a laptop running Windows Vista, connect the computer to a wireless network. |
✓ | Compare and differentiate between WEP, WPA-personal, WPA-enterprise, WPA2-personal, and WPA2-enterprise. |
✓ | Connect a computer running Windows Vista to an ISP using dial-up. |
✓ | Connect a computer running Windows Vista to a broadband connection such as DSL or cable modem. |
✓ | Connect a computer running Windows Vista to a network using a VPN. |
A network is two or more computers connected to share resources such as files or printers. To function, a network requires a service to share (such as file or print sharing) and access a common medium or pathway. Today, most computers connect to a wired network using an Ethernet adapter, which in turn connects to a switch or set of switches via a twisted-pair cable, or the computers connect to a wireless network using a wireless adapter to connect to a wireless switch. To bring it all together, protocols give the entire system common communication rules. Today, virtually all networks use TCP/IP protocol suite, the same protocol on which the Internet runs.
TCP/IP (Transmission Control Protocol/Internet Protocol) is an industry suite of protocols on which the Internet is based. It is supported by most versions of Windows (including Windows NT, Windows 9x, Windows 2000, Windows XP, Windows Server 2003, and Windows Vista) and virtually all modern operating systems.
The lowest protocol within the TCP/IP suite is the Internet Protocol (IP), which is primarily responsible for addressing and routing packets between hosts. Each connection on a TCP/IP address is called a host (a computer or other network device that is connected to a TCP/IP network) and is assigned a unique IP address. A host is any network interface, including each network’s interface cards or a network printer that connects directly onto the network. When you send or receive data, the data is divided into little chunks called packets. Each of these packets contains both the sender’s TCP/IP address and the receiver’s TCP/IP address.
Windows Vista supports both IPv4 and IPv6 through a dual-IP-layer architecture and enables both by default. This architecture enables you to tunnel IPv6 traffic across an IPv4 network in addition to IPv4 traffic across an IPv6 network.
The traditional version of the IP protocol is version 4: IPv4. Each connection on a TCP/IP address (logical address) is assigned a unique IP address. The format of the IP address is four 8-bit numbers (octet) divided by periods (.). Each number can be 0 to 255. For example, a TCP/IP address could be 131.107.3.1 or 2.0.0.1.
IP addresses are manually assigned and configured (static IP addresses) or dynamically assigned and configured by a Dynamic Host Configuration Protocol (DHCP) server (dynamic IP addresses). Because the address is used to identify the computer, no two connections can use the same IP address. Otherwise, one or both of the computers would not be able to communicate, and will usually see a message stating “IP address conflict.”
The TCP/IP address is broken down into a network number and a host number. The network number identifies the entire network, and the host number identifies the computer or connection on the specified network.
Usually when defining the TCP/IP for a network connection, IT managers also specify a subnet mask. A subnet mask is used to define which address bits describe the network number and which address bits describe the host address. Similar to the IP address, the format of the subnet mask is four 8-bit numbers (octet) divided by periods (.). Each number can be 0 to 255. For example, a subnet mask could be 255.0.0.0, 255.255.255.0, or 255.255.240.0.
For example, if you have an address of 15.2.3.6 and you define a subnet mask of 255.255.255.0, 15.2.3.0 defines the network address where every computer on that network must begin with 15.2.3. Then, each computer must have a unique host number, making the entire address unique. Because the first three octets are defined as the network ID, the last octet defines the host ID. Therefore, the one host (and only one host) would have a host ID of 0.0.0.6 located on the 15.2.3.0 network.
If an individual network is connected to another network and users must communicate with any computers on the other network, they must also define the default gateway, which specifies the local address of the router. If the default gateway is not specified, users will not be able to communicate with computers on other networks. If the LAN is connected to more than two networks, users must specify only one gateway, because when a data packet is sent, the gateway will first determine whether the data packet needs to go to a local computer or onto another network. If the data packet is meant to be sent to a computer on another network, the gateway forwards the data packet to the router. The router then determines the best direction that the data packet must go to reach its destination.
If you are connected to the Internet, you need a default gateway. Because the default gateway address is an address of a host, it also is a four 8-bit number (octet) divided by periods (.). Each number can be 0 to 255. Because it must be connected on the same network as the host, it must also have the same network address as the host address.
Because TCP/IP addresses are scarce for the Internet (based on the IPv4 and its 32-bit addresses), a series of addresses has been reserved to be used by the private networks. These addresses can be used by many organizations because these addresses are not seen from outside of the local network. The addresses are as follows:
10.x.x.x (1 Class A address range)
172.16.x.x to 172.31.x.x (16 Class B address ranges)
192.168.0.x and 192.168.255.x (256 Class C address ranges)
To enable these addresses to connect to the Internet, you use a router that supports Network Address Translation (NAT), also known as IP masquerading, which translates between the internal private addresses and the public Internet addresses.
Since the TCP/IP protocol and the Internet became popular, the Internet has grown and continues to grow at an exponential rate. Eventually, the Internet will run out of network numbers. Therefore, a new IP protocol called IPv6 is replacing IPv4.
IPv6 provides a number of benefits for TCP/IP-based networking connectivity, including the following:
Larger address space. The 128-bit address space for IPv6 potentially provides every device on the Internet with a globally unique address.
Efficient routing. The IPv6 network packet supports hierarchical routing infrastructures, which enables it to be more efficient routing than IPv4.
Straightforward configuration. IPv6 can use both Dynamic Host Configuration Protocol for IPv6 (DHCPv6) and local routers for automatic IP configuration.
Enhanced security. The IPv6 standard provides better protection against address and port scanning attacks, and all IPv6 implementations support IPSec for protection of IPv6 traffic.
IPv4 is based on 32-bit addresses (four 8-bit octets), which allows a little more than 4 billion hosts. IPv6 uses 128 bits for the addresses, which can have up to 3.4 x 1038 hosts. Thus, IPv6 can handle all of today’s IP-based machines and allow for future growth while handling IP addresses for mobile devices such as personal digital assistants (PDAs) and cell phones.
An IPv6 address is usually divided into groups of 16 bits, written as 4 hex digits. Hex digits include 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F. The groups are separated by colons (:). Here is an example of an IPv6 address:
FE80:0000:0000:0000:02A0:D2EF:FEA5:E9F5
Similar to IPv4, the IPv6 addresses are split in two parts, bits that identify the network and bits that define the host address. Different from IPv4, IPv6 has a fixed prefix that contains specific routing and subnet information. The first 64 bits (four groups of four hex digits) define the network address and the second 64 bits define the host address. For our FE80:0000:0000:0000:02A0:D2EF:FEA5:E9F5 address, FE80:0000:0000:0000 defines the network bits, and 02A0:D2EF:FEA5:E9F5 defines the host bits.
Exam Alert
If you need to assign a computer directly to the Internet, you need to configure the computer with an IPv6 address that is equivalent to a public IPv4 address, and is a global unicast IPv6. Global unicast IPv6 addresses are globally routable and can be reached from the Internet. These addresses are usually assigned by your ISP or network administrator. For more information on IPv6 addresses and how they are assigned, look at the Exam Cram Exam 70-642 Windows Server 2008 Configuring Network Infrastructure.
Most users will find the IPv4 and IPv6 addresses difficult to remember when communicating with other computers. Instead, a user specifies a recognizable name, and the name is translated into an address. For example, when a user opens Internet Explorer and specifies http://www.microsoft.com, the www.microsoft.com is translated into an IP address. The web page is then accessed from the server using the translated IP addresses.
Fully qualified domain names (FQDNs), sometimes referred to as just domain names, are used to identify computers on a TCP/IP network. Examples include the following:
server1.acme.com
One way to translate the FQDN to the IP address is to use a Domain Name System (DNS) server. DNS is a distributed database (database is contained in multiple servers) that contains the host name and IP address information for all domains on the Internet. For every domain, a single authoritative name server contains all DNS-related information about the domain. When you configure IP, you must specify the address of a DNS server so that you can use the Internet or log on to a Windows Active Directory domain.
Besides the DNS server, a HOSTS file on each machine can also be used to translate domain/host names to IP addresses. The disadvantage of using HOSTS files is that you must add entries on every machine.
Note
Another naming scheme used on TCP/IP networks is the NetBIOS names (such as that used to identify share names for file and printers, \COMPUTERNAMESHARENAME). To translate NetBIOS names to IP addresses, you use a Windows Internet Name Service (WINS) server or the LMHOSTS files.
On Windows machines, the HOSTS and LMHOSTS files are located in the C:WindowsSystem32driversetc folder.
If you try to access a network resource by name rather than IP address and the device cannot be found, it is most likely a problem with the DNS server/HOSTS file or the WINS server/LMHOSTS file. Either the servers cannot be contacted, or the servers or files have the wrong address associated with the name. The failure of these servers or files can also affect network applications that need to access various services or resources.
To configure the IP configuration in Windows Vista, follow these steps:
Open the Control Panel.
While in Category view, click Network and Internet, click Network and Sharing Center, and then click Manage Network Connection.
Right-click the connection that you want to change, and then click Properties. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
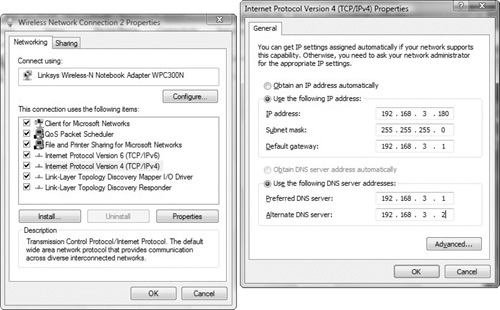
Click the Networking tab. Under This Connection Uses the Following Items, click either Internet Protocol Version 4 (TCP/IPv4) or Internet Protocol Version 6 (TCP/IPv6), and then click Properties.
To specify IPv4 IP address settings, do one of the following:
To obtain IP settings automatically from a DHCP server, click Obtain an IP Address Automatically, and then click OK.
To specify an IP address, click Use the Following IP Address, and then, in the IP Address, Subnet Mask, and Default Gateway boxes, enter the IP address settings.
To specify IPv6 IP address settings, do one of the following:
To obtain IP settings automatically, click Obtain an IPv6 Address Automatically, and then click OK.
To specify an IP address, click Use the Following IPv6 Address, and then, in the IPv6 Address, Subnet Prefix Length, and Default Gateway boxes, enter the IP address settings.
Windows Vista provides the capability to configure alternate IP address settings to support connecting to different networks. Although static IP addresses can be used with workstations, most workstations use dynamic or alternate IP addressing, or both. You configure dynamic and alternate addressing by completing the following steps:
Click Start, and then click Network. In Network Explorer, click Network and Sharing Center on the toolbar.
In the Network and Sharing Center, click Manage Network Connections.
In Network Connections, right-click the connection you want to work with, and then select Properties.
In the Local Area Connection Status dialog box, click Properties. This displays the Local Area Connection Properties dialog box.
Double-click Internet Protocol Version 6 (TCP/IPv6) or Internet Protocol Version 4 (TCP/IPv4), as appropriate for the type of IP address you want to configure.
Select Obtain an IPv6 Address Automatically or Obtain an IP Address Automatically, as appropriate for the type of IP address you are configuring. If desired, select Obtain DNS Server Address Automatically. Or, select Use the Following DNS Server Addresses and then enter a preferred and alternate DNS server address in the text boxes provided.
When you use dynamic IPv4 addressing with desktop computers, you should configure an automatic alternate address. To use this configuration, on the Alternate Configuration tab, select Automatic Private IP Address (APIPA). Click OK twice, click Close, and then skip the remaining steps.
When you use dynamic IPv4 addressing with mobile computers, you might want to configure the alternate address manually. To use this configuration, on the Alternate Configuration tab, select User Configured. Then, in the IP Address text box, enter the IP address you want to use. The IP address that you assign to the computer should be a private IP address, and it must not be in use anywhere else when the settings are applied.
With dynamic IPv4 addressing, complete the alternate configuration by entering a subnet mask, default gateway, DNS, and WINS settings. When you have finished, click OK twice, and then click Close.
To specify DNS server address settings for IPv4 and IPv6, do one of the following:
To obtain a DNS server address automatically, click Obtain DNS Server Address Automatically, and then click OK.
To specify a DNS server address, click Use the Following DNS Server Addresses, and then, in the Preferred DNS server and Alternate DNS server boxes, type the addresses of the primary and secondary DNS servers.
You can use several utilities to test and troubleshoot the TCP/IP network.
If you experience network connectivity problems while using Windows Vista, you can use Window Network Diagnostics to start the troubleshooting process. If there is a problem, Windows Network Diagnostics analyzes the problem and, if possible, presents a solution or a list of possible causes.
Windows Network Diagnostics may be able to complete the solution automatically or may require the user to perform steps in the resolution process.
If Windows Network Diagnostics cannot resolve the problem, you should follow a logical troubleshooting process using tools available in Windows Vista. Table 4.1 lists some of these tools.
Table 4.1. Troubleshooting Tools
Tool | Description |
|---|---|
The ipconfig command displays current TCP/IP configuration.
| |
By using the Internet Control Message Protocol (ICMP) protocol, the ping command verifies connections to a remote computer by verifying configurations and testing IP connectivity. | |
The tracert command traces the route that a packet takes to a destination and displays the series of IP routers that are used in delivering packets to the destination. If the packets are unable to be delivered to the destination, the tracert command displays the last router that successfully forwarded the packet. The tracert command also uses ICMP. | |
The nslookup command displays information that you can use to diagnose your DNS infrastructure. You can use nslookup to confirm connection to the DNS server and the existence of required records. |
A typical troubleshooting process follows:
Check local IP configuration (ipconfig).
Use the ping command to gather more information on the extent of the problem:
Ping the loopback address (127.0.0.1).
Ping the local IP address.
Ping the remote gateway.
Ping the remote computer.
Identify each hop (router) between two systems using the tracert command.
Verify DNS configuration using the nslookup command.
Using ipconfig with the /all switch will show you the IP configuration of the computer. If the IP address is invalid, communication may fail. If the subnet mask is incorrect, the computer will have an incorrect network ID, and therefore communication may fail, especially to remote subnets. If the default gateway is incorrect or missing, the computer will not be able to communicate with remote subnets. If the DNS server is incorrect or missing, the computer may not be able to resolve names, and communication may fail.
If the computer is set to accept a DHCP server and one does not respond, the computer will use automatic private IP addressing, which generates an IP address in the form of 169.254.xxx.xxx and the subnet mask of 255.255.0.0. After the computer generates the address, it broadcasts this address until it can find a DHCP server. When you have an automatic private IP address, you can communicate with computers only on the same network/subnet that have an automatic private IP address.
If you can successfully ping the IP address but not the name, name resolution is failing. If you successfully ping the computer name but the response does not resolve the FQDN name, resolution has not used DNS. This means a process such as broadcasts or WINS has been used to resolve the name, and applications that require DNS may fail. A “Request timed out” message indicates that there is a known route to the destination computer but one or more computers or routers along the path, including the source and destination, are not configured correctly. “Destination host unreachable” indicates that the system cannot find a route to the destination system and therefore does not know where to send the packet on the next hop.
A quickly advancing field in networking is wireless technology. Today’s computers can have a wireless network adapter to connect to other computers or to a wireless access point, which in turn allows the users to connect to the Internet or the rest of the internal network. Today’s wireless adapters include PC cards for notebooks, Peripheral Component Interconnect (PCI) cards for desktops, and universal serial bus (USB) devices (which can be used with notebooks or desktops).
Wireless adapters can run in one of two operating modes:
Ad hoc. Wireless adapter connects directly to other computers with wireless adapters.
Infrastructure. Wireless adapter connects to an access point (AP).
The most widely used wireless network adapters and APs are based on the Institute of Electrical and Electronics Engineers (IEEE) 802.11 specification, as shown in Table 4.2. Most wireless networks used by companies are 802.11b 802.11g, or 802.11n networks. Wireless devices that are based on this specification can be Wi-Fi Certified to show they have been thoroughly tested for performance and compatibility.
Table 4.2. Popular Wireless Standards
Wireless Standard | 802.11a | 802.11b | 802.11g | 802.11n |
|---|---|---|---|---|
Speed | Up to 54 Mbps | Up to 11 Mbps | Up to 54 Mbps | Up to 240 Mbps |
Transmission frequency | 5 GHz | 2.4 GHz | 2.4 GHz | 2.4 GHz |
Effective indoor range | Approximately 25 to 75 feet | Approximately 100 to 150 feet | Approximately 100 to 150 feet | Approximately 300 to 450 feet |
Compatibility | Incompatible with 802.11b and 802.11g. | 802.11b wireless devices can interoperate with 802.11g devices (at 11 Mbps); 802.11g wireless adapters can operate with 802.11b APs (at 11 Mbps). | 802.11g wireless devices can operate with 802.11b devices (at 11 Mbps). | 80.2.11n devices can interoperate with 802.11b and 802.11g devices. |
Because a wireless network signal can be captured by anyone within the range of the antennas, it is easy for someone to intercept the wireless signals that are being broadcast. Therefore, it is always recommended that you use some form of encryption.
The most basic wireless encryption scheme is Wireless Equivalency Protection (WEP). With WEP, you encrypt data using 40-bit, 128-bit, 152-bit, or higher private key encryption. With WEP, all data is encrypted using a symmetric key derived from the WEP key or password before it is transmitted, and any computer that wants to read the data must be able to decrypt it using the key. However, it is easy for someone with a little knowledge or experience to break the shared key because it doesn’t change automatically over time. Therefore, it is recommended to use a higher form of wireless encryption than WEP.
Today, it is recommended to use Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access Version 2 (WPA2). WPA was adopted by the Wi-Fi Alliance as an interim standard prior to the ratification of 802.11i. WPA2 is based on the official 802.11i standard and is fully backward compatible with WPA.
WPA provides strong data encryption via Temporal Key Integrity Protocol (TKIP), whereas WPA2 provides enhanced data encryption via Advanced Encryption Standard (AES), which meets the Federal Information Processing Standard (FIPS) 140-2 requirement of some government agencies. To help prevent someone from hacking the key, WPA and WPA2 rotate the keys and change the way keys are derived.
WPA-compatible and WPA2-compatible devices can operate in Personal or Enterprise mode:
Personal mode provides authentication via a preshared key or password.
Enterprise mode provides authentication using IEEE 802.1X and Extensible Authentication Protocol (EAP).
In Personal mode, WPA or WPA2 uses a preshared encryption key rather than a changing encryption key. The preshared encryption key is programmed into the AP and all wireless devices, which is used as a starting point to mathematically generate session keys. The session keys are then changed regularly so that the same session key is never used twice. Because the key rotation is automatic, key management is handled in the background.
In Enterprise mode, wireless devices have two sets of keys: session keys and group keys. Session keys are unique to each association between an AP and a wireless client. They are used to create a private virtual port between the AP and the client. Group keys are shared among all clients connected to the same AP. Both sets of keys are generated dynamically and are rotated to help safeguard the integrity of keys over time. The encryption key can be supplied through a certificate or smart card.
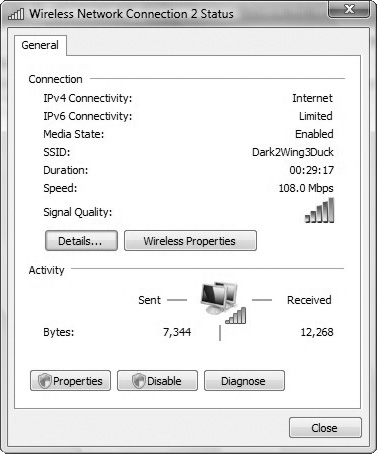
If you click View Status for the wireless connection, you’ll see a status dialog box. You can use the Wireless Network Connection Status dialog box to check the status of the connection and to maintain the connection, in much the same way as you can for other types of connections. You’ll also see the duration and speed of the connection (see Figure 4.2).
Any wireless AP broadcasting within range should be available to a computer with a wireless adapter. By default, Windows Vista is set to allow you to configure the network settings that should be used. This enables you to configure different authentication, encryption, and communication options as necessary.
If you haven’t previously connected to a wireless network, you can create a connection for the network by completing the following steps:
Click Start, and then click Network. In Network Explorer, click Network and Sharing Center on the toolbar.
In the Network and Sharing Center, click Set Up a Connection or Network. This starts the Set Up a Connection or Network Wizard.
Select Manually Connect to a Wireless Network, and then click Next.
Enter information about the wireless network to which you want to connect. Your network administrator should have this information.
In the Network Name box, enter the network name, also referred to as the network’s service set identifier (SSID).
Use the Security Type selection list to select the type of security being used. The encryption type is then filled in automatically for you.
With WEP and WPA-Personal, you must enter the required security key or password phrase in the Security Key/Passphrase box.
By default, the connection is started automatically whenever the user logs on. If you also want the computer to connect to the network regardless of whether it can be reached, such as when the computer is out of range of the wireless base, select Connect Even if the Network Is Not Broadcasting.
Click Next to connect to the wireless network using the settings you’ve entered.
If you have multiple computers that need to be configured to connect to a wireless network, you can use a USB flash drive to carry the configuration from computer to computer. To save the USB information to a USB drive, follow these steps:
Click the Start button, and select the Control Panel.
Click Network and Internet, click Network and Sharing Center, and then, in the left pane, click Add a Wireless Device.
Follow the steps in the wizard to save your wireless network settings to the USB flash drive.
To add a wireless computer running Windows Vista by using a USB flash drive, follow these steps:
Log on to the computer.
Plug the USB flash drive into a USB port on the computer.
For a computer running Windows Vista, in the AutoPlay dialog box, click Wireless Network Setup Wizard.
You might be prompted to restart the computer. If you’re previously connected to a wireless network, you can easily connect to it or disconnect from it by completing the following steps:
Click Start, and then click Network. In Network Explorer, click Network and Sharing Center on the toolbar.
In the Network and Sharing Center, click Connect to a Network. By default, all available networks are listed by name, status, and signal strength (see Figure 4.3). If a network that should be available isn’t listed, try clicking the Refresh button.
Moving the cursor over a wireless network entry displays a message box that provides the network name, signal strength, security type, radio type (the wireless standard supported), and the link‘s security ID.
You can now connect to or disconnect from wireless networks. To connect to a wireless network, click the network, and then click Connect. To disconnect from a wireless network, click the network, and then click Disconnect. Confirm the action by clicking Disconnect again.
You can manage wireless networks using Manage Wireless Networks. To access Manage Wireless Networks, follow these steps:
Click Start, and then click Network. In Network Explorer, click Network and Sharing Center on the toolbar.
In the Network and Sharing Center, click Manage Wireless Networks.
Manage Wireless Networks lists wireless networks in the order in which the computer should try to use the available networks. The network listed at the top of the list is tried before any others. If the computer fails to establish a connection over this network, the next network in the list is tried, and so on.
To change the preference order of a network, click it, and then use the Move Up or Move Down buttons to set the order in which the computer should try to use the network. As necessary, click Add to create a new wireless network that will be added to the wireless networks list, or select an existing network and click Remove to delete a listed wireless network.
As a Windows Vista Technology Specialist, you may be expected to support users in remote locations, including at their homes. Remote connections connect individuals or groups to a network from a remote location. Windows Vista supports the following remote connections:
Dial-up
Broadband
Virtual private network (VPN)
A dial-up connection is a nonpermanent point-to-point connection typically using a modem and a phone line to connect to
A modem pool at an Internet service provider (ISP) so that the computer can connect to the Internet.
A modem pool on an internal network (such as work) to access network resources such as e-mail and data files.
Analog modems use dedicated telephone lines to connect users to the internal network at speeds up to 33.6 kilobits per second (kbps). Digital modems use channels of an ISDN line to connect users to the internal network at speeds up to 56 kbps. Communication is controlled by a remote access server (RAS), which authenticates the login ID and password and authorizes the user to connect to the Internet or internal network.
If you are using a modem, you need to configure dialing rules so that the modem knows how the phone lines are accessed, what the caller’s area code is, and what additional features should be used when dialing connections. Sets of dialing rules are saved as dialing locations in the Phone and Modem Options tool.
To view and set the default dialing location, follow these steps:
Click Start, and then click Control Panel. In the Control Panel, click Hardware and Sound.
In the Hardware and Sound dialog box, click Set Up Dialing Rules under Phone and Modem Options. The first time you start this tool, you’ll see the Location Information dialog box.
Specify the country/region you are in, the area code (or city code), a number to access an outside line, and whether the phone uses tone dialing or pulse dialing.
After you configure an initial location and click OK, you‘ll see the Phone and Modem Options dialog box. To create a dial-up Internet connection to an ISP, follow these steps:
Click Start, and then click Connect To. Then click Set Up a Connection or Network to start the Connect to a Network Wizard.
To make a dial-up connection to an ISP, select Set Up a Dial-Up Connection, and then click Next.
Enter the phone number to dial for this connection using the Dial-Up Phone Number text box.
Enter the account information, including the username and password.
In the Connection Name field, enter the name for the connection, such as Service Provider. Keep in mind that the name should be fewer than 50 characters, but should be descriptive.
If you want (although not recommended), you can check the Remember This Password check box.
If you want the connection to be available to all users of the computer, select Allow Other People to Use This Connection.
Click Create to create the dial-up connection, and then click Close.
Dial-up uses a telephone line to establish connections between two modems. To establish a dial-up connection, follow these steps:
Click Start, and then click Connect To. In the Connect to a Network dialog box, click the dial-up connection you want to use, and then click Connect.
Confirm that the username is correct, and enter the password for the account if it doesn’t already appear.
To use the username and password whenever you attempt to establish this connection, select Save This User Name and Password for the Following Users, and then select Me Only. To use the username and password when any user attempts to establish this connection, select Save This User Name and Password for the Following Users, and then select Anyone Who Uses This Computer.
The Dial drop-down list shows the number that will be dialed. The primary number is selected by default. To choose an alternate number, click the drop-down list, and then select the number you want to use.
Click Dial. When the modem connects to the ISP or office network, you’ll see a connection speed. The connection speed is negotiated on a per-call basis and depends on the maximum speed of the calling modem and the modem being called, the compression algorithms available, and the quality of the connection.
Today, many connections are broadband connections, typically using a cable or Digital Subscriber Line (DSL) connection. Because these connections are always on, you don’t need to set up dial-up rules or locations, and you don’t have to worry about ISP access numbers. Most broadband providers give users a router or modem, which users need to connect to the service provider. In most scenarios, a network adapter on the user’s computer is used to connect to the router or modem. In this configuration, the necessary connection is established over the local area network (LAN) rather than a specific broadband connection. Therefore, it is the local area connection that must be properly configured to gain access to the Internet. You won’t need to create a broadband connection.
You can, however, create a specific broadband connection if needed. In some cases, you need to do this to set specific configuration options required by the ISP, such as secure authentication, or you might want to use this technique to set the username and password required by the broadband provider.
Virtual private networking (VPN) is the creation of secured, point-to-point connections across a private network or a public network such as the Internet. A virtual private networking client uses special TCP/IP-based protocols, called tunneling protocols, to make a virtual call to a virtual port on a virtual private networking service. Encryption technology is used to secure the communication channel.
Windows Vista supports VPN tunnels that use Point-to-Point Tunneling Protocol (PPTP) for tunneling and Microsoft Point-to-Point Encryption (MPPE) for encryption. In addition, Windows Vista also supports VPN tunnels that use Layer 2 Tunneling Protocol (L2TP) for tunneling and IP security (IPSec) for encryption. The VPN client authenticates to the remote-access server, at which time they negotiate the tunneling and encryption technologies.
VPNs are used to establish secure communications channels over an existing dial-up or broadband connection. You must know the IP address or FQDN of the remote-access server to which you are connecting. If the necessary connection is available and you know the host information, you can create the connection by following these steps:
Click Start, and then click Connect To. Click Set Up a Connection or Network to start the Set Up a Connection or Network Wizard.
To make a VPN connection, scroll down, select Connect to a Workplace, and then click Next.
Select No, Create a New Connection, and then click Next.
The user will need to establish a connection to the Internet—via either dial-up or broadband—before attempting to use the VPN. Therefore, click Use My Internet Connection (VPN). On the Before You Connect page, select the previously created connection to use, and then click Next. This connection can be a dial-up or broadband connection.
Enter the IP address or FQDN of the computer to which you are connecting, such as 131.5.27.14 or www.external.acme.com. In most cases, this is the remote-access server you’ve configured for the office network.
Enter a name for the connection in the Destination Name field.
If the computer is configured to use a smart card for authentication, select Use a Smart Card.
If you want the connection to be available to all users of the computer, select Allow Other People to Use This Connection. This option is best when you plan to assign the connection through Group Policy and have not provided user logon information. Click Next.
A user is prompted by default for her name and password when she makes a connection. If you’re creating a connection for an individual user and don’t want the user to be prompted for logon information, you can enter the username and password in the fields provided.
If you want to ensure that password will be remembered, you can select Remember This Password. If you don’t select Remember This Password, the user is prompted for the password.
Specify the logon domain in the Domain field, and then click Connect. Of course, to connect to a VPN connection, you must first be connected to the dial-up or broadband connection specified previously.
Answer B is correct. To renew IPv4, you have to use the ipconfig /renew command. Answer A is incorrect because the ipconfig command without any options will only display basic IP configuration information. Answer C is incorrect because the /renew6 option will renew IPv6 IP addresses. Answer D is incorrect because the /release_and_renew option does not exist. Answer E is incorrect because the /registerdns option is how to get the computer to register itself with the DNS server. | |
Answer E is correct. To flush local cached DNS information, you use the ipconfig /flushdns command. Answer A is incorrect because the ipconfig command without any options will only display basic IP configuration information. Answer B is incorrect because the /renew option will renew the IPv4 IP addresses. Answer C is incorrect because the /renew6 option will renew IPv6 IP addresses. Answer D is incorrect because the /registerdns option is how to get the computer to register itself with the DNS server. | |
Answer C is correct. The two commands that will show network connectivity to another computer are the ping command and the tracert command. Answer A is incorrect because the ipconfig command without any options will only display basic IP configuration information. Answer B is incorrect because the arp command is used to view and manage IP address-to-MAC address mappings. The traceroute command would be found on UNIX and Linux machines. Windows machines use tracert. | |
Answer B is correct. To show all IP configuration information, you must use the ipconfig /all command. Answer A is incorrect because the ipconfig command without any options will only display basic IP configuration information. Answer C is incorrect because the arp command is used to view and manage IP address-to-MAC address mappings. Answer D and E are commands used to test network connectivity. | |
Answer A is correct. According to this output, the address assigned to the computer is 169.254.3.103, which is an automatic private IP address. Automatic private IP addresses are assigned to Windows computers when they cannot find a DHCP server to get an address from. Automatic private IP addresses begin with 169.254. Answer B is incorrect because although a gateway address might be needed to communicate with computers on another network, the gateway was not assigned because it could not find a DHCP server. Answer C is incorrect because the subnet mask was assigned because it could not find a DHCP server. Answer D is incorrect because the problem does not describe any kind of name-resolution problem. | |
Answer D is correct. If you have a name resolution, the problem has to be with a DNS or WINS server, or you have incorrect entries in your HOSTS or LMHOST files. Answer A is incorrect because if you can ping it by address, you have network connectivity to the server. So, it does not matter whether the server is on the same subnet or a different subnet. Answer B is incorrect because you cannot block access to a computer by name but keep access by address. Answer C is incorrect because if the DHCP client service was not on, you would not be able to get any address from a DHCP server and not able to connect to the network. | |
Answer A is correct. In corporations, most networks use 802.11b or 802.11a networks. Because 802.11a is not compatible with 802.11b/g, it is most likely the problem. Answer B is incorrect because 802.11b and 802.11g can operate at lower speeds. Answer C is incorrect because although having the wrong SSID will cause problems, the SSID does not expire. Answer D is incorrect because most networks will have DHCP service to assign IP addresses. | |
Answer B is correct. You can save the information to a USB device and then use that device to copy the configuration to each computer. Answer A is incorrect because although this would work, it would require a lot more administrative effort. Answer C is incorrect because these computers do not have wired network cards to connect to a shared drive. Answer D is incorrect because copying the network settings would also require a lot more administrative effort. | |
Answer D is correct. If you want an address to be available from the Internet and be the same address for both IPv4 and IPv6, it must have a global address that can be seen on the Internet. Answer A is incorrect because private addresses cannot be used on the public network such as the Internet. Answer B is incorrect because it has to be a single address assigned to a single computer, not a multicast that is used to broadcast to multiple addresses at the same time. Answer C is incorrect because a local address cannot be seen on the outside. | |
Answer D is correct. Because this person is traveling between two sites, the user needs to have a local address on each site. Therefore, you should let the local DHCP server hand out the addresses when she connects to each network. Answer A is incorrect because she can connect to one network. Therefore, the driver is working fine. Answer B is incorrect because this means that you are putting this computer directly on the Internet. Answer C is incorrect because running a Troubleshooting Wizard could be a lengthy process (when the solution is, in fact, simple). | |
Answer D is correct. WPA uses Temporal Key Integrity Protocol (TKIP), and Enterprise does not require a security key or passphrase. Instead, a certificate or similar technology is used to provide the initial key. Answer A is incorrect because WEP does not use TKIP and requires a key to be supplied. Answer B is incorrect because Personal means that you have to enter a security key or passphrase. Answers C and E are incorrect because they use AES rather than TKIP. | |
Answer A is correct. To connect to the office over the Internet, you need to set up a VPN connection. The correct order to set up a VPN connection is as follows:
Answer B is incorrect because you do not click Manage Network Connections from the Start menu. Answer C is incorrect because to set up a VPN, you do not open a network connection’s interface. Answer D is incorrect because you do not choose VPN; instead, you choose Connect to a Workplace. |
Mitch Tulloch, Tony Northrup, Jerry Honeycutt, Ed Wilson, Ralph Ramos, and the Windows Vista Team, Windows Vista Resource Kit (Pro - Resource Kit) (Redmond, Washington: Microsoft Press, 2007).
William R. Stanek, Introducing Microsoft Windows Vista (Redmond, Washington: Microsoft Press, 2006).
Patrick Regan, Working with Windows 2000 and 2003 (Upper Saddle River, New Jersey: Prentice Hall, 2004).
Patrick Regan, Wide Area Networks (Upper Saddle River, New Jersey: Prentice Hall, 2004).
3Com, “Understanding IP Addressing: Everything You Ever Wanted to Know,” white paper located at http://www.3com.com/other/pdfs/infra/corpinfo/en_US/501302.pdf.