Terms you’ll need to understand:
✓ | Spyware |
✓ | End user license agreement (EULA) |
✓ | Antivirus software |
✓ | Windows Defender |
✓ | Windows Firewall |
✓ | Stateful firewall |
✓ | Packet filter |
✓ | Port |
Techniques/concepts you’ll need to master:
✓ | List the symptoms of a system infected with spyware. |
✓ | Configure a computer to resist spyware. |
✓ | Given a computer with spyware, use Windows Defender to remove the spyware. |
✓ | Use Software Explorer to configure items not loaded during startup. |
✓ | Configure and use Windows Firewall to protect your computer from unauthorized access. |
In today’s world, users often need to share data with other users. This chapter focuses on sharing files so those users can access files from a Windows Vista computer over the network and how to control such access so that it remains secure. Because these files will access the files over the network, this chapter also discusses how to configure Windows Vista to connect to the network.
A common threat to computers that can cause problems similar to a virus is spyware. Spyware (including adware) programs are more like Trojan horse viruses. Some machines are infected with spyware when it is bundled with other software, often without the user’s knowledge, or is slipped into the fine print of an end user license agreement (EULA). A EULA is a type of license used for most software, and represents a legal contract between the manufacturer or the author and the end user of an application. The EULA details how the software can and cannot be used and any restrictions that the manufacturer imposes. Spyware can also be picked up by simply visiting various websites, where they are often hidden as ActiveX controls.
After it has been installed, spyware can monitor user activity on the Internet and transmit information such as e-mail addresses, passwords, and credit card numbers without the user’s knowledge. This information can be used for advertising or marketing purposes, to send the information to other parties, or to use the information for illegal purposes. Spyware can do the following:
Generate annoying pop-ups
Monitor keystrokes
Scan files on the hard drive
Snoop other applications such as chat programs or word processors
Install other spyware programs
Read cookies
Change the default home page on the web browsers other links or default pages
Open your computer to be accessed by others
Exam Alert
It is important that you know the symptoms of spyware so that when presented with a troubleshooting question you will know what steps to take next.
Spyware can also use network bandwidth and computer memory and can lead to system crashes or general system instability.
To reduce your chance of being affected by spyware, you should do the following:
Use a good antivirus package such as Norton Antivirus, McAfee Viruscan, or Microsoft Windows Live OneCare.
Use spyware-detecting and -removal programs such as Windows Defender if it is not included in the antivirus software.
Be sure that your machine has all security patches and fixes loaded.
Install software only from sources and websites you trust.
Be careful about what software you install on your system. Be sure to read the EULA for any piece of shareware or file-sharing package you plan to install.
Keep your web browser security settings to Medium or higher.
Install or enable a personal firewall such as the one included in Windows Vista.
Use pop-up blockers.
Windows Defender, included with Windows Vista, helps users detect and remove known spyware and other potentially unwanted software. Windows Defender protects your computer with automated and real-time scanning and software removal.
Because spyware and other potentially unwanted software can try to install itself on your computer any time you connect to the Internet or when you install some programs, it is recommended that you have Windows Defender running whenever you use your computer.
Windows Defender offers three ways to help keep spyware and other potentially unwanted software from infecting your computer:
Real-time protection. Running in the background, Windows Defender alerts you when spyware or potentially unwanted software attempts to install itself or to run on your computer. It also alerts you when programs attempt to change important Windows settings.
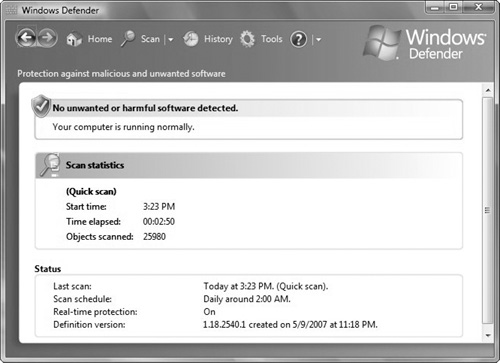
Scanning options. You can use Windows Defender to actively scan your disks for spyware and other potentially unwanted software that might be installed on your computer and to automatically remove any malicious software that is detected during a scan (see Figure 7.1). Windows Defender can be set up to scan automatically according to a schedule or manually.
SpyNet community. The online Microsoft SpyNet community helps you see how other people respond to software that has not yet been classified for risks.
You can also use Windows Defender to constantly monitor your system to offer real-time protection. The real-time protection uses nine security agents to monitor the critical areas of your computer that spyware may attack. Then, an agent detects potential spyware activity, it stops the activity, and raises an alert. The agents include the following:
Microsoft Internet Explorer Configuration. Monitors browser security settings so that they do not get changed by spyware.
Internet Explorer Downloads. Monitors files and applications that work within Internet Explorer, such as ActiveX controls and software installation applications to make sure spyware is not being installed with the files and applications.
Internet Explorer Add-Ons (Browser Helper Objects). Monitors browser applications that automatically run when you start Internet Explorer to make sure that these programs are not spyware.
Auto Start. Monitors applications that start when Windows starts to verify that these applications are not spyware.
System Configuration. Monitors Windows hardware and security settings to make sure they do not get changed by spyware.
Services and Drivers. Monitors services and drivers to make sure that spyware does not use them to access the computer.
Windows Add-Ons. Monitors add-on applications, also known as software utilities, that integrate with Windows.
Application Execution. Monitors applications to make sure that spyware does not use software application vulnerabilities to access a computer.
Application Registration (API Hooks). Monitors files and tools in the operating system to make sure that they do not open up applications or other files that contain spyware.
When you choose automatic scanning, you can choose the type of scan that you would like to perform:
Quick Scan. Checks areas on a hard disk that spyware is most likely to infect.
Full Scan. Checks all critical areas, all files, the registry, and all currently running applications.
Custom Scan. Allows you to scan specific drives and folders.
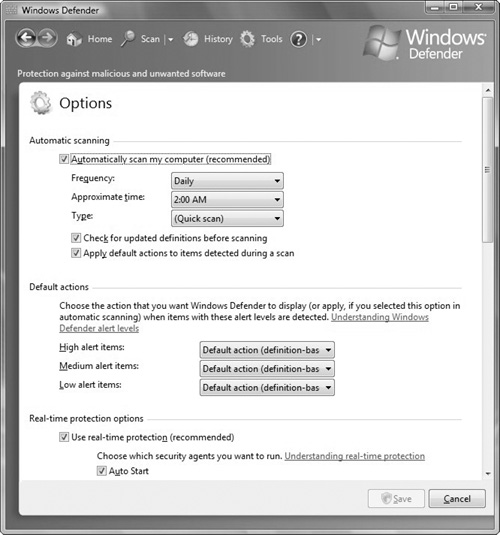
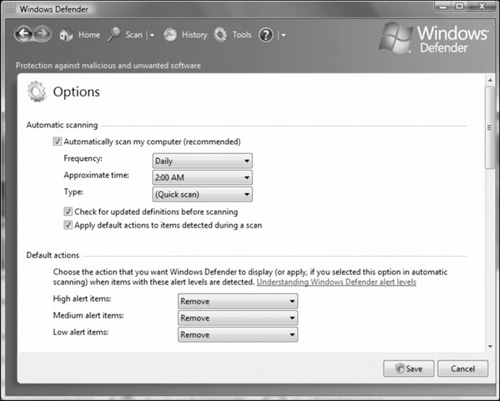
When you perform a scan, you can configure what Windows Defender will do when it identifies unwanted software (see Figure 7.2). The actions include the following:
Ignore. Windows Defender does not take any action, and the next scan will detect the item again.
Quarantine. Windows Defender places identified unwanted software in quarantine, which allows you to determine whether it is spyware.
Remove. Windows Defender removes the item from the system.
Always Allow. Windows Defender will not take any action and will stop detecting the item in future scans.
To prevent Windows Defender from automatically taking the recommended action, such as quarantining or removing software, you need to clear the Apply Default Actions to Items Detected During a Scan option. As a result, Windows Defender will recommend an action to take for detected malicious software.
Similar to antivirus software, Windows Defender uses a definition database that lists and details the characteristics of known spyware. When software is identified as spyware, it removes the software. Like antivirus software, the definition database becomes out of data as new spyware is introduced. Therefore, you must update the database regularly for it to be effective.
To help keep your system from being compromised, Windows Defender will scan all startup items, including those specified in the following registry key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
Exam Alert
You can use Windows Defender to view which items load during startup and easily disable any programs that you don’t recognize.
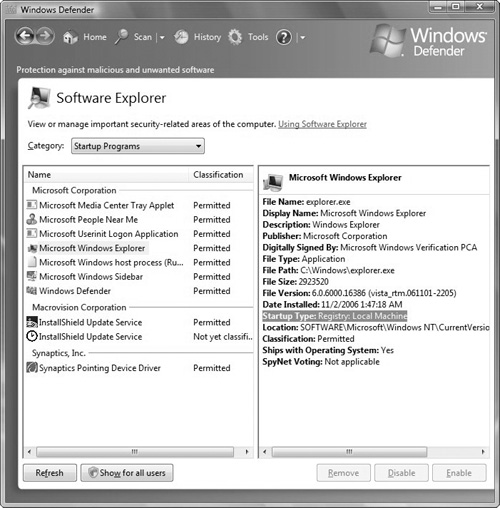
To view all programs that are set to run at startup, click the Tools button, and then click the Software Explorer option to view all programs that are set to run at startup (see Figure 7.3). This enables you to view several categories of software, including what is running at that time and what is set to run at startup. For each application set to run at startup, there is additional information, including the startup type, so you can identify the mechanism used to start it, such as the registry.
By deleting the correct program in Windows Defender, you prevent the program from starting whenever Windows starts. Therefore, you should open Windows Defender and remove any unfamiliar programs whose startup type is set to Registry: Local Machine.
Windows Defender in Windows Vista automatically blocks all startup items that require administrator privileges to run. Because this feature is related to the User Account Control (UAC) functionality in Windows Vista, and requires the user to manually run each of these startup items each time he logs in, if you cannot get an update to the software that allows a startup item to run without being an administrator, you need to disable UAC altogether.
Exam Alert
Windows Defender automatically blocks all startup items that require administrator privileges.
To turn Windows Defender on or off, follow these steps:
Open Windows Defender by clicking the Start button, All Programs, and then clicking Windows Defender.
Click Tools, Options.
Under Administrator options, select or clear the Use Windows Defender check box, and then click Save. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
To turn Windows Defender real-time protection on or off, follow these steps:
Open Windows Defender by clicking the Start button, All Programs, and then clicking Windows Defender.
Click Tools, Options.
Under Real-time Protection options, select the Use Real-Time Protection (Recommended) check box.
Select the options you want. To help protect your privacy and your computer, we recommend that you select all real-time protection options.
Under Choose If Windows Defender Should Notify You About, select the options you want, and then click Save. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
If you trust software that Windows Defender has detected, you can stop Windows Defender from alerting you to risks that the software might pose to your privacy or your computer. To stop being alerted, you need to add the software to the Windows Defender allowed list. If you decide that you want to monitor the software again later, you can remove it from the Windows Defender allowed list at any time.
To add an item to the allowed list, follow these steps:
The next time Windows Defender alerts you about the software, on the Action menu in the Alert dialog box, click Always Allow.
If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
To remove an item from the allowed list, follow these steps:
Open Windows Defender by clicking the Start button, All Programs, and then clicking Windows Defender.
Click Tools, Allowed Items.
Select the item that you want to monitor again, and then click Remove From List.
If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
Because most computers are connected to the Internet through dialup, broadband (such as Digital Subscriber Line [DSL] or cable modems), or through a local area network, computers are vulnerable to attack or unauthorized access. To help protect your system, you should have a firewall between you and the outside world that will monitor all traffic going in and out and prevent such access.
Windows Firewall is a packet filter and stateful host-based firewall that allows or blocks network traffic according to the configuration. A packet filter protects the computer by using an access control list (ACL), which specifies which packets are allowed through the firewall based on IP address and protocol (specifically the port number). A stateful firewall monitors the state of active connections and uses the information gained to determine which network packets are allowed through the firewall. Typically, if the user starts communicating with an outside computer, it will remember the conversation and allow the appropriate packets back in. If an outside computer tries to start communicating with a computer protected by a stateful firewall, those packets will automatically be dropped unless it was granted by the ACL.
Exam Alert
Remember that any program or service that needs to communicate on a network must be able to pass through a firewall. This includes file sharing.
The rules that can be defined include the following:
Inbound rules. Prevents other computers from making an unsolicited or unexpected connection to your computer from other computers making an unsolicited connection to it.
Outbound rules. Prevents your computer from making unsolicited connections to other computers.
Connection-specific rules. Allows you to create and apply custom rules based on a specific connection.
Compared to Windows Firewall introduced with Windows XP SP2, the Windows Firewall used in Windows Vista has been improved. Some of the improvements are as follows:
IPv6 connection filtering.
Outbound packet filtering.
Rules can be configured for individual services chosen from a list without needing to specify the full path filename.
Internet Protocol Security (IPSec) is fully integrated with Windows Firewall to make sure there is not a conflict between IPSec and firewall settings.
Capability to have separate firewall profiles when computers communicating on a Windows domain are connected to the Internet (public) or private network.
Windows Firewall is on by default. When Windows Firewall is on, most programs are blocked from communicating through the firewall. If you want to unblock a program, you can add it to the Exceptions list (on the Exceptions tab). For example, you might not be able to send photos in an instant message until you add the instant messaging program to the Exceptions list.
To turn on or off Windows Firewall, follow these steps:
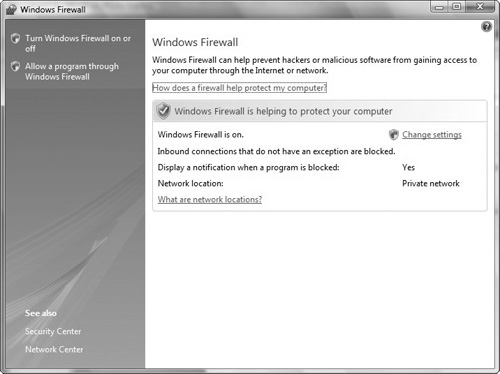
Open Windows Firewall by clicking the Start button, Control Panel, Security, and then clicking Windows Firewall.
Click Turn Windows Firewall on or off shown in the left pane (see Figure 7.4). If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
Click On (recommended) or Off (not recommended), and then click OK (see Figure 7.5).
If you want the firewall to block everything, including the programs selected on the Exceptions tab, select the Block All Incoming Connections check box (which blocks all unsolicited attempts to connect to your computer). Use this setting when you need maximum protection for your computer, such as when you connect to a public network in a hotel or airport, or when a computer worm is spreading over the Internet. With this setting, you are not notified when Windows Firewall blocks programs, and programs on the Exceptions list are ignored.
The Windows Firewall Settings interface has three tabs:
General. Allows you to turn Windows Firewall on and off and temporarily block all incoming connections.
Exceptions. Allows you to specify which programs and services are allowed through the firewall or not. Of course, you should never create an exception for a program when you are unsure of the functionality of that program.
Advanced. Allows you to select which network interfaces that Windows Firewall will protect.
To configure programs as exceptions, follow these steps:
Open Windows Firewall by clicking the Start button, Control Panel, Security, and then clicking Windows Firewall.
Click Allow a Program Through Windows Firewall. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
In the Windows Firewall dialog box, select the Exceptions tab, and then click Add Program.
In the Add a Program dialog box, select the program in the Programs list or click Browse to use the Browse dialog box to find the program.
By default, any computer, including those on the Internet, can access this program remotely. To restrict access further, click Change Scope.
Click OK three times to close all open dialog boxes.
To open a port in Windows Firewall, follow these steps:
Open Windows Firewall by clicking the Start button, Control Panel, Security, and then click Windows Firewall.
Click Allow a Program Through Windows Firewall. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
Click Add Port.
In the Name box, enter a name that will help you remember what the port is used for.
In the Port Number box, enter the port number.
Click TCP or UDP, depending on the protocol.
By default, any computer, including those on the Internet, can access this program remotely. To change scope for the port, click Change Scope, and then click the option that you want to use. (Scope refers to the set of computers that can use this port opening.)
Click OK two times to close all open dialog boxes.
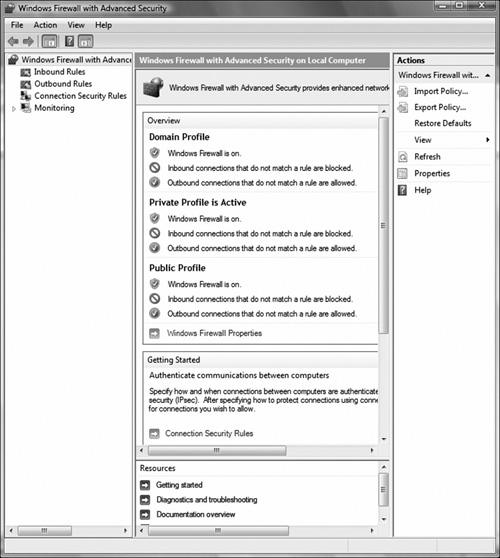
The new Windows Firewall with Advanced Security is a Microsoft Management Console (MMC) snap-in that provides more advanced options for IT professionals. With this firewall, you can set up and view detailed inbound and outbound rules and integrate with IPSec. To access the Windows Firewall with Advanced Security, follow these steps:
Open Administrative Tools by clicking the Start button, Control Panel, System and Maintenance, and then click Administrative Tools.
Double-click Windows Firewall with Advanced Security. If you are prompted for an administrator password or confirmation, enter the password or provide confirmation.
Of course, you must be a member of the Administrators group or the Network Operators group to use Windows Firewall with Advanced Security.
The Windows Firewall with Advanced Security management console enables you to configure the following (see Figure 7.6):
Inbound rules. Windows Firewall will block all unsolicited incoming traffic unless allowed by a rule.
Outbound rules. Windows Firewall will allow all outbound traffic unless blocked by a rule.
Connection security rules. Forces two computers to authenticate to each other and to secure or encrypt data using IPSec.
Monitoring. Display information about current firewall rules, connection security rules, and security associations.
You create inbound rules to control access to your computer from the network. Inbound rules can prevent the following:
Unwanted software being copied to your computer
Unknown or unsolicited access to data on your computer
Unwanted configuration of your computer
To configure advanced properties for a rule using the Windows Firewall with Advanced Security, follow these steps:
Right-click the name of the inbound rule, and click Properties.
From the Properties dialog box for an inbound rule, configure settings on the following tabs:
General. The rule’s name, the program to which the rule applies, and the rule’s action (allow all connections, allow only secure connections, or block).
Programs and Services. The programs or services to which the rule applies.
Users and Computers. If the rule allows only secure connections, you can specify which computer accounts are allowed to make the connection.
Protocols and Ports. The rule’s IP protocol, source and destination TCP or UDP ports, and ICMP or ICMPv6 settings.
Scope. The rule’s source and destination addresses.
Advanced. The profiles or types of interfaces to which the rule applies.
You can also use the Windows Firewall with Advanced Security to create outbound rules to control access to network resources from your computer. Outbound rules can prevent the following:
Programs including malware from accessing network resources without your knowledge
Programs including malware from downloading software without your knowledge
Users downloading software without your knowledge
Because the Internet is inherently insecure, businesses still need to preserve the privacy of data travelling over the network. IPSec creates a standard platform to develop secure networks and electronic tunnels between two machines. The two machines are known as endpoints. After the tunnel has been defined and both endpoints agree on the same parameters, the data will be encrypted on one end, encapsulated in a packet, and sent to the other endpoint (where the data is decrypted).
In Windows XP and Windows Server 2003, you configure the Windows Firewall and IPSec separately. Unfortunately, because both can block or allow incoming traffic, it is possible that the firewall and IPSec rules can conflict with each other. In Windows Vista, Windows Firewall with Advanced Security provides a single, simplified interface for managing both firewall filters and IPSec rules.
Windows Firewall with Advanced Security uses authentication rules to define IPSec policies. No authentication rules are defined by default. To create a new authentication rule, follow these steps:
In Windows Firewall with Advanced Security, select the Computer Connection Security node.
Right-click the Computer Connection Security node in the console tree, and then click New Rule to start the New Connection Security Rule Wizard.
From the Rule Type page of the New Authentication Rule Wizard, you can select the following:
Isolation. Used to specify that computers are isolated from other computers based on membership in a common Active Directory domain or current health status. You must specify when you want authentication to occur (for example, for incoming or outgoing traffic and whether you want to require or only request protection), the authentication method for protected traffic, and a name for the rule.
Authentication exemption. Used to specify computers that do not have to authenticate or protect traffic by their IP addresses.
Server to server. Used to specify traffic protection between specific computers, typically servers. You must specify the set of endpoints that will exchange protected traffic by IP address, when you want authentication to occur, the authentication method for protected traffic, and a name for the rule.
Tunnel. Used to specify traffic protection that is tunneled, typically used when sending packets across the Internet between two security gateway computers. You must specify the tunnel endpoints by IP address, the authentication method, and a name for the rule.
Custom. Used to create a rule that does not specify a protection behavior. You would select this option when you want to manually configure a rule, perhaps based on advanced properties that cannot be configured through the pages of the New Authentication Rule Wizard. You must specify a name for the rule.
To configure advanced properties for the rule, follow these steps:
Right-click the name of the rule, and then click Properties.
From the Properties dialog box for a rule, you can configure settings on the following tabs:
General. The rule’s name and description and whether the rule is enabled.
Computers. The set of computers, by IP address, for which traffic is protected.
Authentication. When you want authentication for traffic protection to occur (for example, for incoming or outgoing traffic and whether you want to require or only request protection) and the authentication method for protected traffic.
Advanced. The profiles and types of interfaces to which the rule applies and IPSec tunneling behavior.
Answer D is correct. Spyware cannot physically damage a computer. It can, however, capture information as you type, change the default home page, generate pop-up windows, and slow your machine. Therefore, answers A, B, C, and E are incorrect. | |
Answer D is correct. When you know that a program is not spyware, click Always Allow so that it stops thinking the software is spyware. Answer A is incorrect because you don’t want to ignore the other programs. Answer B is incorrect because parental controls do not function on domains. Answer C could be a correct answer, but when taking Microsoft exams where you are to choose the best answer, answer B is a better answer. | |
Answer D is correct. If you use Software Explorer, you can remove any program that executes during startup. Many spyware programs, including those that change home pages, load themselves automatically during startup. Therefore, you should remove any programs that you don’t recognize. Answer A is incorrect because not all programs will be shown in the Add/Remove Programs. Answer B is incorrect because there is no indication it is communicating with the outside world, and using the firewall would not stop the spyware program from changing the home page. Answer C is incorrect because changing the security level would do nothing because the spyware program is already on the machine. | |
Answer D is correct. Because the computer is slow even after reboot, the spyware program must load every time the computer is rebooted. Therefore, it has to be loaded during startup. Answer A is incorrect because spyware is not typically loaded as a service. Answer B is not the best answer because most startup programs are specified in the registry, not the startup folder. Answer C is incorrect because if you stop the program using Task Manager, the program will still reload when you restart the computer. | |
Answer A is correct. Quick Scan will check all places that you normally would find spyware, including those that execute during startup. Answer B is incorrect because a Fast Scan does not exist. Answer C is incorrect because a Full Scan is much more thorough but takes much longer. Answer D is incorrect because you would then need to manually specify where to search for spyware. | |
Answer C is correct. By default, all suspected spyware will be removed. If you uncheck the Apply Default Actions to Items During a Scan, it will prompt you for each item on what action to take. Answer A is incorrect because there is no default recommended option. Answer B is incorrect because the same actions will be taken. A Full Scan checks all drives instead of checking where spyware is typically found. Answer D is incorrect because checking for updates is important to keep updated, but it will not change Windows Defender from automatically removing any spyware that it finds. | |
Answer B is correct. If you want full control of the firewall, you would use the Windows Firewall with Advanced Security. By using the Windows Firewall with Advanced Security, you can enable and configure firewall rules depending on its connection. Answer A is incorrect because you only want it enabled for private connection (home). Answer C is incorrect because if you use the Windows Firewall settings in the Control Panel, it will open up file sharing for all connections. Answer D is incorrect also because it would be for all incoming connections. | |
Answer A is correct. Because you want the PAY.EXE to communicate through the firewall, you can use an exception, where you can specify that PAY.EXE can communicate out port 8787. Answer B is incorrect because you want to specify that only PAY.EXE can communicate through port 8787, not any other programs. Answer C is incorrect because you don’t want the PAY.EXE to communicate through any other port. Answer D is incorrect because the PAY.EXE is not a program that executes during startup. | |
Answer D is correct. IPSec, short for IP Security, is a protocol that encrypts data packets sent over the network. Answer A is incorrect because the AES is an encryption scheme used to encrypt data. Answer B is incorrect because stateful firewall is used to keep track of all conversations going through a firewall so that it determine which outside packets can come into the network. Answer C is incorrect because EFS is used to encrypt files and folders on an NTFS volume. | |
Answer A is correct. Windows Firewall is configured to block packets, including accessed shared folders. Answer B, C, and D are incorrect because you do not need to configure any of these to allow communications. |
Mitch Tulloch, Tony Northrup, Jerry Honeycutt, Ed Wilson, Ralph Ramos, and the Windows Vista Team, Windows Vista Resource Kit (Pro - Resource Kit) (Redmond, Washington: Microsoft Press, 2007).
William R. Stanek, Introducing Microsoft Windows Vista (Redmond, Washington: Microsoft Press, 2006).
For more information about Windows Defender, visit http://www.microsoft.com/athome/security/spyware/software/default.mspx.