Terms you’ll need to understand:
✓ | Internet Explorer |
✓ | Add-on |
✓ | Phishing |
✓ | Protected mode |
✓ | Cookie |
✓ | ActiveX controls |
✓ | Dynamic Security |
✓ | RSS Feeds |
Techniques/concepts you’ll need to master:
✓ | Demonstrate how to zoom in and out within Internet Explorer |
✓ | Configure common Internet Explorer options |
✓ | Configure Internet Explorer security |
✓ | Enable Protected mode in Internet Explorer |
✓ | Configure RSS feeds for Internet Explorer |
A web browser is the client program or software that you run on your local machine to gain access to a web server. It receives commands, interprets the commands, and displays the results. It is strictly a user-interface/document presentation tool. It knows nothing about the application it is attached to, and only knows how to take the information from the server and present it to the user. It also able to capture data entry made into a form and gets the information back to the server for processing. Because these browsers are used to search and access web pages on the Internet and can be used by an organization’s website or provide interface to a program, you need to understand how to configure, customize, and troubleshoot browser issues.
By far, Microsoft Internet Explorer (IE) is the most common browser available (because it comes with every version of Windows). Windows Vista includes IE 7.0, which has new functionality while reducing online risks.
Compared to older versions of IE, the most obvious difference is its redesigned streamlined interface, which is simpler and less cluttered. As a result, IE 7.0 maximizes the space available for displaying web pages. In addition to a simpler interface, IE 7.0 introduced tabs that enable you to open multiple web pages in a single browser window. If you have a lot of tabs, you can use Quick Tabs to easily switch between open tabs.
Other features in IE 7.0 include the following:
The new Instant Search box lets you search the web from the address bar. You can also search using different search providers to get better results.
IE now lets you delete your temporary files, cookies, web page history, saved passwords, and form information from one place. Delete selected categories, or everything at once.
Click the Favorites Center button to open the Favorites Center to manage favorites, feeds, and history in one place.
Printing now scales web pages to fit the paper you’re using. Print Preview gives more control when printing, with manual scaling and an accurate view of what you’re about to print.
By subscribing to a feed, you can get updated content, such as breaking news or your favorite blog, without having to visit the website.
The Zoom feature lets you enlarge or reduce text, images, and some controls. IE Zoom lets you enlarge or reduce the view of a web page. Unlike changing font size, Zoom enlarges or reduces everything on the page, including text and images. You can zoom from 10 percent to 1,000 percent.
To zoom a web page, follow these steps:
On the bottom right of the IE screen, click the arrow to the right of the Change Zoom Level button.
Do one of the following:
To go to a predefined zoom level, click the percentage of enlargement or reduction you want.
To specify a custom level, click Custom. In the Percentage Zoom box, enter a zoom value, and then click OK.
If you have a mouse with a wheel, hold down the Ctrl key, and then scroll the wheel to zoom in or out. If you click the Change Zoom Level button, it will cycle through 100%, 125%, and 150%, giving you a quick enlargement of the web page. From the keyboard, you can increase or decrease the zoom value in 10 percent increments. To zoom in, press Ctrl + the plus sign key (Ctrl++). To zoom out, press Ctrl + the hyphen (Ctrl+-). To restore the zoom to 100 percent, press Ctrl+0.
Most of the configuration options for IE are accessed by starting IE, clicking the Tools button, and selecting Internet Options. It can also be accessed from the Internet Options applet in the Control Panel. The Internet Options dialog box has several tabs, including General, Security, Privacy, Content, Connections, Programs, and Advanced (see Figure 8.1).
At the top of the General tab, you can configure the home page or the default page that is loaded when you start IE. This enables you to have your favorite search engine, news, website, portal, or an organization’s internal website load automatically when you start IE. By going to a web page and then clicking the Use Current button, you make the page that is currently being displayed your home page. You can also configure it to show a blank page. Of course, to make the change go into effect, you have to click the Apply or OK button.
Some organizations may configure the organization’s home page as the default home page so that users cannot make changes to IE using group policies. Other times, if you experience an unexpected change in the home page, it was most likely caused by visiting a particular website (usually you have to click Yes to change the website, but that is not always the case), installing a program that changes the IE home page, or being infected by a virus or spyware.
Below the home page, you will find the section to configure browsing history, including how IE uses temporary Internet files, which are used as a disk cache for Internet browsing. When you visit a website, parts of the web page (such as pictures, sound, and video files) are copied on the system as a temporary Internet file so that on future visits to that site, it will load faster. If you click the Settings button, you can configure the browser to check for newer versions of the saved page on every visit, every time you start IE, automatically, or never. If you need to force IE to reload a fresh web page, you can hold down on the Shift key while you click Refresh, or press Shift+F5. You can also click the View Files button to view the temporary Internet files.
You can determine how much disk space you want to use as a cache and where the folder is located that stores the temporary files. If you click View Files, you will open the folder that stores the temporary files so that you can inspect them directly.
History specifies the number of days that IE should keep track of your viewed pages in the History list. IE creates shortcuts to pages you viewed in this and previous browsing sessions. If you are low on disk space, you might want to decrease the number. You can also clear your history from here.
The AutoComplete feature remembers previous entries that you made for web addresses, forms, and passwords. When you type information in one of these fields, AutoComplete suggests possible matches. These matches can include folder and program names you type into the address bar; the matches can also include search queries, stock quotes, or other information that you type in forms on web pages. To use AutoComplete, start typing the information in the address bar, in a field on a web page, or in a box for a username or password. If you have typed a similar entry before, AutoComplete lists possible matches as you type. If a suggestion in the list matches what you want to enter in that field, click the suggestion. If no suggestion matches what you are typing, continue typing.
To select AutoComplete settings in IE, click Tools, Internet Options. On the Content tab, click AutoComplete. You can specify whether you want to use AutoComplete for web addresses, forms, usernames, and passwords. You can also clear the history of previous AutoComplete entries. When typing information in web forms, and when typing passwords, you can remove an item from the list of suggestions by clicking the item and then pressing the Delete key.
If you click the Advanced options, you can configure a wide range of configuration options, including disabling script debugging, enabling Folder view for FTP sites, enabling personalized favorites menu, notifying when downloads are complete, enabling automatic image resizing, and playing sounds and videos in web pages. It also has several security features such as emptying temporary Internet files when the browser is closed, enabling Profile Assisting, using Secure Sockets Layer (SSL) 2.0 or 3.0 (needed to connect to secure web pages as indicated by https://), warning about invalid site certificates, and warning if a form is being redirected (see Figure 8.2).
To make IE more powerful and more flexible and by adding additional functionality, IE has the capability to use add-ons and scripting languages. A plug-in is a software module that adds a specific feature or service to the browser to display or play different types of audio or video messages. The most common plug-ins are Shockwave, RealMedia (RealAudio and RealVideo), and Adobe Reader (used to read Portable Document Format [PDF]).
In an effort to make browsing more functional, web developers create and enable active content. Active content uses small executable or script code that is executed and shown within the client’s web browser. Unfortunately, like a Trojan horse virus, this feature is an added security risk; some scripts could be used to perform harmful actions on a client machine. Some of the most popular types of active content are VBScript, JavaScript, and ActiveX components.
To view current add-ons, follow these steps:
Click the Tools button, Manage Add-Ons, Enable or Disable Add-Ons.
In the Show box, select one of the following options:
To display a complete list of the add-ons that reside on your computer, click Add-Ons That Have Been Used by Internet Explorer.
To display only those add-ons that were needed for the current web page or a recently viewed web page, click Add-Ons Currently Loaded in Internet Explorer.
To display add-ons that were preapproved by Microsoft, your computer manufacturer, or a service provider, click Add-Ons That Run Without Requiring Permission.
To display only 32-bit ActiveX controls, click Downloaded ActiveX Controls (32-bit).
When you run an add-on for the first time, IE will ask permission, which should notify you if a website is secretly trying to run malicious code. IE has a list of preapproved add-ons that have been checked and digitally signed. The add-on list can come from Microsoft, your computer manufacturer, your Internet service provider (if you are using a private branded version of IE), or your corporation’s network administrator. These add-ons in this list are run without displaying the permissions dialog.
Add-ons are typically fine to use, but sometimes they force IE to shut down unexpectedly. This can happen if the add-on was created for an earlier version of IE or has a programming error. When you encounter a problematic add-on, you can disable it or report it to Microsoft. If disabling add-ons doesn’t solve the problem, try resetting IE back to its default settings.
To permanently disable add-ons, follow these steps:
Click the Tools button, Manage Add-Ons, Enable or Disable Add-Ons.
In the Show list, click Add-Ons That Have Been Used by Internet Explorer to display all add-ons.
Click the add-on you want to disable, and then click Disable. Repeat for every add-on you want to disable.
When you have finished, click OK.
To reenable an add-on, follow these steps:
Click the Tools button, Manage Add-Ons, Enable or Disable Add-Ons.
In the Show list, click Add-Ons That Have Been Used by Internet Explorer to display all add-ons.
Click the add-on you want to enable, and then click Enable. Repeat for every add-on you want to enable.
When you have finished, click OK.
To temporarily disable all add-ons, follow these steps:
Click the Start button, All Programs.
Click Accessories.
Click System Tools.
Click Internet Explorer (No Add-ons).
You can delete only ActiveX controls that you have downloaded and installed. You cannot delete ActiveX controls that were preinstalled or add-ons of any kind, but you can disable them. To delete an ActiveX control that you have installed, use the Remove Programs tool in the Windows Control Panel, as follows:
IE offers a number of features to help protect your security and privacy when you browse the web, including the following:
Phishing Filter. Helps protect you from online phishing attacks, fraud, and spoofed websites.
Protected mode. Helps protect you from websites that try to save files or install programs on your computer.
Pop-up Blocker. Helps block most pop-up windows.
Add-on Manager. Lets you disable or enable web browser add-ons and delete unwanted ActiveX controls.
Notification. Notifies you when a website is trying to download files or software to your computer.
Digital signatures. Tells you who published a file and whether it has been altered since it was digitally signed.
128-bit secure (SSL) connection for using secure websites. Helps IE create an encrypted connection with websites such as banks and online stores.
A cookie is a message given to a web browser by a web server, and is typically stored in a text file on the PC’s hard drive. The message is then sent back to the server each time the browser requests a page from the server. The main purpose of cookies is to identify users and possibly prepare customized web pages for the user. When you enter a website using cookies, you may be asked to fill out a form providing some information as your name and interests. This information is packaged into a cookie and sent to your web browser, which stores it for later use. The next time you go the same website, your browser will send the cookie to the web server. The server can use this information to present you with custom web pages. So, for example, instead of seeing just a generic welcome page, you might see a welcome page with your name on it.
Among other things, cookies are used to keep track of what a person buys, personalize online ordering, personalize a website, store a person’s profile, store IDs, and provide support to older web browsers that do not support host header names. A cookie cannot be used to get data from your hard drive, get your e-mail addresses, or steal sensitive information about you.
From the General tab, you can delete the cookies that are stored on your hard drive. By clicking the Privacy tab, you can determine how much of your personal information can be accessed by websites and whether a website can save cookies on your computer by adjusting the tab slider on the privacy scale.
To view privacy settings, select the Privacy tab on the Internet Options dialog box. To adjust your privacy settings, adjust the tab slider to a new position on the privacy scale. A description of the privacy settings that you select displays on the right side of the tab slider. The default level is Medium; it is recommended to configure Medium or higher. You can also override the default for cookies in each security zone. In addition, you can override certain settings (automatic cookie handling and session cookies) by clicking the Advanced button, or you can allow or block cookies from individual websites by clicking the Edit button.
Many websites provide privacy statements that you can view. A site’s privacy policy tells you what kind of information the site collects and stores and what it does with the information. Information that you should be mostly concerned with is how the websites uses personally identifiable information such as your name, e-mail addresses, address, and telephone number. Websites also might provide a Platform for Privacy Preferences (P3P) privacy policy, which can be used by browsers to filter cookie transactions on the basis of the cookie’s content and purpose. To view the privacy report, open the View menu and click Privacy Report. To view a site’s privacy statement, select the website and click the Summary button.
To help manage IE security when visiting sites, IE divides the network connection into four content types:
Internet zone. Anything that is not assigned to any other zone and anything that is not on your computer, or your organization’s network (intranet). The default security level of the Internet zone is Medium.
Local intranet zone. Computers that are part of the organization’s network (intranet) that do not require a proxy server, as defined by the system administrator. These include sites specified on the Connections’ tab, network, paths such as \computernamefoldername, and local intranet sites such as http://internal. You can add sites to this zone. The default security level for the local intranet zone is Medium=Low, which means IE will allow all cookies from websites in this zone to be saved on your computer and read by the website that created them.
Trusted sites zone. Contains trusted sites that you believe you can download or run files from without damaging your computer or data or that you consider are not a security risk. You can assign sites to this zone. The default security level for the trusted sites zone is Low, which means IE will allow all cookies from websites in this zone to be saved on your computer and read by the website that created them.
Restricted sites zone. Contains sites that you do not trust and from which downloading or running files may damage your computer or data, or you just consider them a security risk. You can assign sites to this zone. The default security level for the restricted sites zone is High, which means IE will block all cookies from websites in this zone.
For each of the web content zones, there is a default security level. The security levels available in IE are as follows:
High. Excludes any content that can damage your computer.
Medium. Warns you before running potentially damaging content.
Low. Does not warn you before running potentially damaging content.
Custom. A security setting of your own design. Use this level to customize the behavior and Active Data Object (ADO) and Remote Data Services (RDS) objects in a specific zone.
Whenever you access a website, IE checks the security settings for zone of the website. To tell which zones the current web page falls into, you look at the right side of the IE status bar. Besides adjusting the zones or assigning the zones or assigning a website to a zone, you can also customize settings for a zone by importing a privacy settings file from a certificate authority.
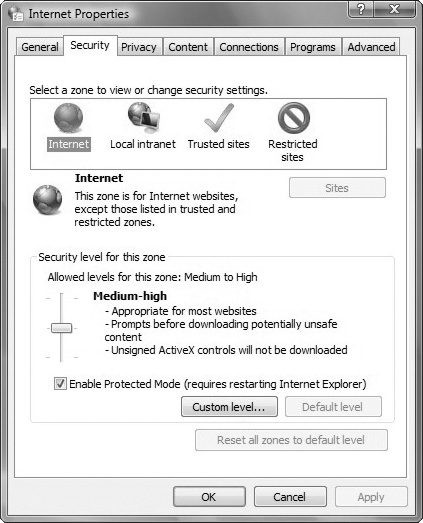
To modify the security level for a web content zone, follow these steps:
Click the Tools button, Internet Options.
In the Internet Options dialog box, on the Security tab, click the zone on which you want to set the security level.
Drag the slider to set the security level to High, Medium, or Low. IE describes each option to help you decide which level to choose. You are prompted to confirm any reduction in security level. You can also choose the Custom Level button for more detailed control (see Figure 8.3).
Click OK to close the Internet Options dialog box.
Software publisher certificates (third-party digital certificates) are used to validate software code such as Java or ActiveX controls or plug-ins. Depending on the security settings for a zone, when software code is accessed from a website, you will automatically download the software code, disable the software code, or prompt to download the software code via a security warning. If you open the Tools menu and select Internet Options, select the Security tab, and click the Custom Level button, you can select to enable, disable, or prompt to download ActiveX controls (signed and unsigned) and scripting of Java applets.
To view the certificates for IE, open the Internet Options dialog box, click the Content tab, and then click the Certificates button. To see list of certificates, click the appropriate certificates. From here, you can also import and export individual certificates.
Dynamic Security options for IE 7.0 offer multiple security features to defend your computer against malware and data theft. The Security status bar keeps you notified of the website security and privacy settings by using color-coded notifications next to the address bar. Some of these features are as follows:
Address bar turns green to indicate that a website is bearing new High Assurance certificates, indicating the site owner has completed extensive identity verification checks.
Phishing Filter notifications, certificate names, and the gold padlock icon are now also adjacent to the address bar for better visibility.
Certificate and privacy detail information can easily be displayed with a single click in the Security status bar.
The address bar is displayed to the user for every window, whether it’s a pop-up or standard window, which helps to block malicious sites from emulating trusted sites.
To help protect you against phishing sites, IE warns you when visiting potential or known fraudulent sites and blocks the site if appropriate. The opt-in filter is updated several times per hour with the latest security information from Microsoft and several industry partners.
International Domain Name Anti-Spoofing notifies you when visually similar characters in the URL are not expressed in the same language.
To protect your system even further, IE includes the following features:
ActiveX opt-in. Disables nearly all pre-installed ActiveX controls to prevent potentially vulnerable controls from being exposed to attack. You can easily enable or disable ActiveX controls as needed through the Information Bar and the Add-on Manager.
Cross-domain barriers. Limit scripts on web pages from interacting with content from other domains or windows. This enhanced safeguard will help to protect against malicious software by limiting the potential for malicious websites to manipulate flaws in other websites or cause you to download undesired content or software.
If IE is still using its original settings, you’ll see the Information bar in the following circumstances:
If a website tries to install an ActiveX control on your computer or run an ActiveX control in an unsafe manner
If a website tries to open a pop-up window
If a website tries to download a file to your computer
If a website tries to run active content on your computer
If your security settings are below recommended levels
If you access an intranet web page, but have not turned on intranet address checking
If you started IE with add-ons disabled
If you need to install an updated ActiveX control or add-on program
If the web page address can be displayed with native language letters or symbols, but you don’t have the language installed
When you see a message in the information bar, click the message to see more information or to take action.
To stop the information bar from blocking file and software downloads, follow these steps:
Click to open IE.
Click the Tools button, Internet Options.
Click the Security tab, and then click Custom Level.
Do one or both of the following:
To turn off the information bar for file downloads, scroll to the Downloads section of the list, and then, under Automatic Prompting for File Downloads, click Enable.
To turn off the information bar for ActiveX controls, scroll to the ActiveX Controls and Plug-Ins section of the list, and then, under Automatic Prompting for ActiveX Controls, click Enable.
Click OK, click Yes to confirm that you want to make the change, and then click OK again.
Table 8.1 lists some of the more common messages that might appear in the information bar, along with a description of what each message means.
Table 8.1. Information Bar Messages
Message | What It Means |
|---|---|
To help protect your security, Internet Explorer stopped this site from installing an ActiveX control on your computer. Click here for options. | The web page tried to install an ActiveX control, and IE blocked it. If you want to install the ActiveX control and you trust the publisher of the ActiveX control, right-click the information and select Install Software. |
Pop-up blocked. To see this pop-up or additional options click here. | Pop-up Blocker has blocked a pop-up window. You can turn Pop-up Blocker off or allow pop-ups temporarily by clicking the information bar. |
This website is using a scripted window to ask you for information. If you trust this website, click here to allow scripted windows. | IE has blocked a website that tried to display a separate window such as a logon screen in an attempt to gather confidential information. If you trust the website, click the information bar and click select Temporarily Allow Scripted Windows or Allow Websites to Prompt for Information Using the Scripted Windows customer security setting. |
To help protect your security, Internet Explorer blocked this site from downloading files to your computer. Click here for options. | A web page tried to download a file that you might not have requested. If you want to download the file, click the information bar, and then click Download File. |
Your security settings do not allow websites to use ActiveX controls installed on your computer. This page may not display correctly. Click here for options. | The website tried to install an ActiveX control, but your security settings did not allow it. This is usually caused when a website is listed in the restricted site list. If you trust the site, remove the site from the restricted site zone. If the problem still exists, try adding the site to the trusted sites list. To access the trusted sites, click the Tools button and select Internet Options. Then select the Security tab, select Trusted Sites, and click the Sites button. |
Internet Explorer has blocked this site from using an ActiveX control in an unsafe manner. As a result, this page may not display correctly. | A website tried to access an ActiveX control on your computer without your permission. |
IE’s Protected mode is a feature that makes it more difficult for malicious software to be installed on your computer. In addition, it allows users to install wanted software when they are logged on as a standard user rather than an administrator. Protected mode is turned on by default, and an icon appears on the status bar to let you know that it’s running. When you try to install software, Protected mode will warn you when web pages try to install software or if a software program runs outside of Protected mode. If you trust the program and want to allow it to run on any website, select the Always Allow Websites to Use This Program to Open Web Content check box.
Exam Alert
Protected mode makes it more difficult for malicious software to be installed on your machine.
Note
As mentioned in Chapter 3, “Using Windows Vista,” Windows Vista offers parental controls to help keep children safer online (by allowing parents to control browsing behavior). A child’s browsing session can even be examined by a parent afterward, and cannot be removed without the parent’s permission. Parental controls can be configured from the User Accounts and Family Safety section of the Control Panel.
RSS, short for RDF Site Summary or Rich Site Summary, is an Extended Markup Language (XML) format for syndicating web content. A website that wants to allow other sites to publish some of its content creates an RSS document and registers the document with an RSS publisher. A user that can read RSS-distributed content can use the content on a different site. Syndicated content includes such data as news feeds, events listings, news stories, headlines, project updates, and excerpts from discussion forums or even corporate information.
A feed can have the same content as a web page, but it’s often formatted differently. When you subscribe, IE automatically checks the website and downloads new content so that you can see what is new since you last visited the feed.
To indicate whether a web page has a feed, the Feeds button will change color, letting you know that feeds are available on the web page. To subscribe to a feed, follow these steps:
Open IE.
Go to the website that has the feed you want to subscribe to.
Click the Feeds button to discover feeds on the web page.
Click a feed (if more than one is available). If only one feed is available, you will go directly to that page.
Click the Subscribe to This Feed button, and then click Subscribe to This Feed.
Type a name for the feed and select the folder to create the feed in.
Click Subscribe.
To view feeds, go to the Feed tab in the Favorites Center. To view your feeds, click the Favorites Center button, and then click Feeds. You can also use other programs such as e-mail clients such as Microsoft Outlook and Windows Sidebar to read the feeds set up with IE.
To reset IE settings and to help troubleshoot problems, you can remove all changes that have been made to IE since it was installed, without deleting your favorites or feeds. To reset IE, follow these steps:
Close all IE or Windows Explorer windows.
Click to open IE.
Click the Tools button, Internet Options.
Click the Advanced tab, and then click Reset.
Click Reset.
When you have finished, click Close, and then click OK.
Close IE and reopen it for the changes to take effect.
You can also restore the options in the Advanced tab of the Internet Options dialog box by clicking the Restore Advanced Settings button on the Advanced tab.
Answer D is correct. To reset IE to its original settings, you have to open Internet Options, select the Security tab, and click Reset. Answer A is incorrect because reinstalling IE does not generally overwrite the settings that are already configured. Answer B is incorrect because resetting zones will affect only information specified in the security zones. Answer C is incorrect because this will only reset the advanced options. | |
Answer E is correct. To delete saved passwords in IE, you must delete the browsing history. Answers A, B, and C are incorrect because these methods will not affect any saved passwords. Answer D is incorrect because passwords are not affected by the advanced settings. | |
Answer D is correct. To prevent passwords from beings stored, you have to configure the AutoComplete feature. Answer A, B, and C do not affect AutoComplete and passwords. Answer E is used to delete saved passwords. | |
Answer D is correct. When you have trouble seeing an image, you can use the Zoom feature. Answers A and B are incorrect because they affect all programs. Answer C is incorrect because decreasing the zoom makes the image smaller. | |
Answer D is correct. Protected mode helps protect you from websites that try to save files or install programs on your computer. Answer A is incorrect because disabling all ActiveX components may disable functionality that you might use for other websites. Answer B is incorrect because the Phishing Filter is used to stop users from being tricked into fake sites that emulate corporate sites in an attempt to steal confidential information. Answer C is incorrect because it was never stated what level the website is. Therefore, changing the level may or may not affect the controls. | |
Answer C is correct. When you click some links, the link is supposed to open a separate window. If you have a pop-up blocker set up, the site might be blocked. Answer A is incorrect because add-ons are designed to run within a website, not as a stand-alone application. Anwer B is incorrect because adding a URL to a trusted site might have some effect on functionality but it would not allow or disallow the entire window for opening. Answers D and E are incorrect because none of these affect whether a website opens. | |
Answer B is correct. Some sites are created to look like other sites and are used to lure people to divulge confidential information. Because these sites are “fishing” for information, these sites are referred to as phishing. Answer A is incorrect because Protected mode tries to secure the IE by securing other files. Answer C is incorrect because Junk Mail Filter is used in e-mail. Answer D is incorrect because there is no such thing as Fake Site Filter. | |
Answer C is correct. RSS feeds are used to get automatic updates and notifications when a website posts something new. Answer A is incorrect because auto updates are used to automatically update Windows security patches and fixes. Answer B is incorrect because dynamic updates provide application and device compatibility updates, driver updates, and emergency fixes for setup or security issues (when you run Windows Setup). Answer D is incorrect because closing IE and restarting it will open up the home page again. It will not notify when other websites get updated. |
Mitch Tulloch, Tony Northrup, Jerry Honeycutt, Ed Wilson, Ralph Ramos, and the Windows Vista Team, Windows Vista Resource Kit (Pro. Resource Kit) (Redmond, Washington: Microsoft Press, 2007).
William R. Stanek, Introducing Microsoft Windows Vista (Redmond, Washington: Microsoft Press, 2006).
For more information about Internet Explorer, visit http://www.microsoft.com/windows/products/winfamily/ie/default.mspx.