Using Software to Generate Reports
Nearly all commercial forensic software produces a report for the beginning of your documentation. Let’s look at a sample report from Paraben’s Case Agent Companion. To save space, most of the bookmarks have been deleted, but this will give you a general idea of what a generated report looks like.
Case #234—Acme Accounting Copyright Piracy Summary
Header
Agent: Customs Cyber Center
Examiner: D. Brown
Notes
Subject: Software Evidence
Body: The bookmarked files are part of a program that is used to generate software labels.
Author: D. Brown
Created: Fri Sep 10 13:42:28 GMT-07:00 2004
Modified: Sat Sep 11 06:16:35 GMT-07:00 2004
Analysis Logs
1. A laboratory computer was prepared by the investigator using licensed copies of Windows 2000 Professional, AccessData’s FTK version 1.43, and WinHex version 10.45 SR-2.
2. The FTK evidence files from the desktop computer were copied to the laboratory computer’s hard drive.
3. A new FTK case file was opened, and the suspect computer’s evidence files were examined using FTK.
a. Deleted files were recovered by FTK.
b. File data, including filenames, dates and times, physical and logical size, and complete path, were recorded.
c. Keyword text searches were conducted based on information provided by the investigator. All hits were reviewed.
d. Graphics files were opened and viewed.
e. HTML files were opened and viewed.
f. Data files were opened and viewed; four password-protected and encrypted files were located.
g. Unallocated space and slack space were searched.
h. Files of interest were copied from the FTK evidence file to a compact disk.
4. Unallocated clusters were copied from the FTK evidence file to a clean hard drive, which had been wiped to U.S. Department of Defense recommendations (DoD 5200.28-STD). FTK was then used to carve images from unallocated space. The carved images were extracted from FTK, opened, and viewed, and subsequently verified using WinHex. A total of 3,592 images were extracted.
5. AccessData’s Password Recovery Toolkit was run on the files, and passwords were recovered for the password-protected files. The files were opened using the passwords and then viewed.
Bookmarks
Images Excluded
Contraband Images Included
Full Text Excluded
nero.exe
Description:
Name = nero.exe
Path = C:Program FilesAheadNero
Created = Sun Dec 16 13:40:06 GMT-07:00 2001
Modified = Wed Feb 20 10:53:58 GMT-07:00 2002
Last Accessed = Sun Apr. 11 13:40:06 GMT-07:00 2004
Size Actual = 18421
Size Allocated = 18421
PFS Type = 10000709
MD5 Hash = fc3031a83d9d82add69ab5df15a0d338
Cluster Map = []
Incident Counter = 0
Deleted = false
Encrypted = false
FOCH Hit = false
Volume = Volume0
System = Windows 2000
Author: D. Brown
Created: Fri Sep 10 13:49:23 GMT-07:00 2004
Modified: Fri Sep 10 13:49:23 GMT-07:00 2004
NeroCmd.exe
Description:
Name = NeroCmd.exe
Path = C:Program FilesAheadNero
Created = Sun Dec 16 13:40:06 GMT-07:00 2001
Modified = Wed Feb 20 10:53:58 GMT-07:00 2002
Last Accessed = Sun Apr. 11 13:40:06 GMT-07:00 2004
Size Actual = 71266
Size Allocated = 71266
PFS Type = 10000708
MD5 Hash = fe45230445a0b16fb0c3b483b21aa0c5
Cluster Map = []
Incident Counter = 0
Deleted = false
Encrypted = false
FOCH Hit = false
Volume = Volume0
System = Windows 2000
Author: D. Brown
Created: Fri Sep 10 13:49:23 GMT-07:00 2004
Summary
The analysis of the desktop computer recovered 265 files of evidentiary value or investigative interest. The recovered files included: 90 document files including documents containing the suspect’s name and personal information; text in the files included names of customer who had purchased the software, their methods of payment, and shipping information. Text describing the counterfeit software and pricing structure was also found. Fifty-seven graphics files, including high-resolution image files of software labels and packaging materials, certificates of authenticity, registration cards, and copies of checks made out to Knockoff.
Most graphic files were scanned, including:
- Eighty-three HTML files including Hotmail and Yahoo e-mail inquiries about the software including e-mails between the suspect and customers (including the concerned citizen who reported his inability to register the software he had purchased).
- Thirty-one graphics files carved from unallocated space depicting copies of checks.
- Four password-protected and encrypted files.
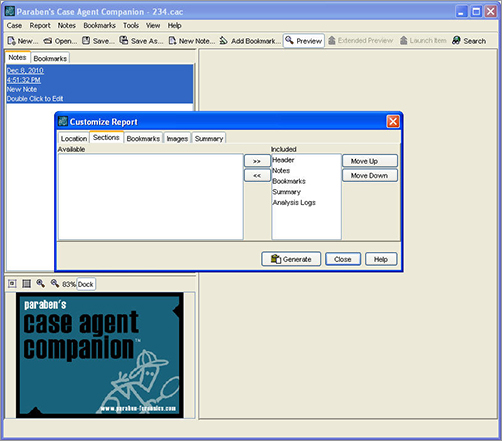
The software allows you to add or remove sections and sort them to suit your needs, as shown in Figure 9-6.
Figure 9-6: Customizing a report in Paraben’s Case Agent Companion
Whether you choose to use a reporting method similar to one demonstrated here, or create your own, your report should document facts so that they may be easily understood. The goals of the report are to accurately recount the details of the case in an understandable format while including all required information to explain your findings and withstand legal examination.
