Using Technology to Manage Information
![]() Distinguish between data and information, and discuss information systems.
Distinguish between data and information, and discuss information systems.
![]() List the components and types of information systems.
List the components and types of information systems.
![]() Discuss computer hardware and software.
Discuss computer hardware and software.
![]() Describe computer networks.
Describe computer networks.
![]() Discuss the security and ethical issues affecting information systems.
Discuss the security and ethical issues affecting information systems.
![]() Explain disaster recovery and backup.
Explain disaster recovery and backup.
![]() Review information systems trends.
Review information systems trends.
Evernote Raises Note Taking to a Profitable Art
If you've ever forgotten something—a deadline, the name of a restaurant, an idea—and worse, couldn't remember how to retrieve it, a software start-up called Evernote has a solution for you.
Evernote is a software app for desktops, laptops, and smart phones that lets users store “notes”—typed or handwritten jottings, Web clips, voice memos, receipts, photos, and other data and images—and easily find them. Evernote stores each user's data in the cloud, but in searchable (and rigorously backed-up) storage that lets you find whatever you've forgotten, using any Internet-connected device, by looking up information associated with it, like when and where you were when you recorded it, who you were with, what you were eating, or any other tag you've attached to it. You can create separate “notebooks” to file your data, and—although the platform isn't intended as a social network—you can also share your notes with others.
Evernote of the future may even help you “remember” things you might not have even known, like your grandmother's birthday, or sense your mood and suggest a restaurant when you appear to be hungry. To do this will require a whole new computing approach, and as the CEO says, “A computer should at least anticipate what you want, when you're happy or unhappy with something or you're frustrated…. That's incredibly difficult—but it's fun to work on.”1
Overview
Today, virtually all business functions—from human resources to production to supply chain management—rely on information systems. This chapter explores how organizations use technology to manage an important resource: information. The chapter begins by differentiating between information and data and then defines an information system. The components of information systems are presented, and two major types of information systems are described. Because of their importance to organizations, the chapter discusses databases, the heart of all information systems. Then the chapter looks at the computer hardware and software that drive information systems. Today, specialized networks make information access and transmission function smoothly, so the chapter examines different types of telecommunications and computer networks to see how start-ups like Evernote are applying them for competitive advantage. The chapter then turns to a discussion of the ethical and security issues affecting information systems, followed by a description of how organizations plan for, and recover from, information system disasters. A review of the current trends in information systems concludes the chapter.
 Data, Information, and Information Systems
Data, Information, and Information Systems
Daily, in organizations around the world, businesspeople ask themselves questions like these:
- How is our product doing in Dallas? Are sales to our target audience growing, declining, or staying static?
- Is the rising price of gas affecting our distribution costs?
- Are we winning the battle for market share?
data raw facts and figures that may or may not be relevant to a business decision.
information knowledge gained from processing data.
An effective information system can help answer these and many other questions. Data refers to raw facts and figures that may or may not be relevant to a business decision. For example, the U.S. Census might report the average home price in a particular neighborhood. And while this datum might be interesting, it is probably not very useful to someone living across the country. On the other hand, data on home prices in your own neighborhood are clearly more valuable. Information—the knowledge gained from processing the facts and figures of raw data about home prices—would be useful for would-be buyers and sellers of these properties. So, although businesspeople need to gather data about the demographics of a target market or the specifications of a certain product, the data are useless unless they are transformed into relevant information that can be used to make a competitive decision.
information system organized method for collecting, storing, and communicating past, present, and projected information on internal operations and external intelligence.
chief information officer (CIO) executive responsible for managing a firm's information system and related computer technologies.
An information system is an organized method for collecting, storing, and communicating past, present, and projected business information. Most information systems today use computer and telecommunications technology to handle the enormous volumes of information generated by large companies. A large organization typically assigns responsibility for directing its information systems and related operations to an executive called the chief information officer (CIO). Often, the CIO reports directly to the firm's chief executive officer (CEO). An effective CIO will understand and harness technology so that the company can communicate internally and externally in one seamless operation. But small companies rely just as much on information systems as do large ones, even if they do not employ a manager assigned to this area on a full-time basis.
Information systems can be tailored to assist many business functions and departments—from marketing and manufacturing to finance and accounting. They can manage the overwhelming flood of information by organizing data in a logical and accessible manner. Through the system, a company can monitor all components of its operations and business strategy, identifying problems and opportunities. Information systems gather data from inside and outside the organization, then process the data to produce information that is relevant to all aspects of the organization. Processing steps could involve storing data for later use, classifying and analyzing them, and retrieving them easily when needed.
Quick Review
![]() What is the difference between data and information?
What is the difference between data and information?
![]() What is an information system?
What is an information system?
 Components and Types of Information Systems
Components and Types of Information Systems
The definition of information system in the previous section does not specifically mention the use of computers or technology. In fact, information systems have been around since the beginning of civilization but, by today's standards, they were very low tech. Think about your college or university's library. At one time the library probably had card catalog files to help you find information. Those files were information systems because they stored data about books and periodicals on 3- by 5-inch index cards.
computer-based information system information system that relies on computer and related technologies to store information electronically in an organized, accessible manner.
Today, however, when businesspeople think about an information system, they are most likely thinking about a computer-based information system. Such systems rely on computer and related technologies to store information electronically in an organized, accessible manner. So, instead of card catalogs, your college library uses a computerized information system that allows users to search through library holdings much faster and easier.
Computer-based information systems consist of four components and technologies:
- computer hardware
- computer software
- telecommunications and computer networks
- data resource management.
Computer hardware consists of machines that range from supercomputers to smart phones. It also includes the input, output, and storage devices needed to support computing machines. Software includes operating systems, such as Microsoft's Windows 8 or Linux, and applications programs, such as Adobe Acrobat or Oracle's PeopleSoft Enterprise applications. Telecommunications and computer networks encompass the hardware and software needed to provide wired or wireless voice and data communications. This includes support for external networks such as the Internet and private internal networks. Data resource management involves developing and maintaining an organization's databases so that decision makers are able to access the information they need in a timely manner.

Libraries typically use a computer-based information system made up of computer hardware linked to the library's network and a database containing information on the books in the library. Specialized software allows users to access the database.
In the case of your institution's library, the computer-based information system is generally made up of computer hardware, such as monitors and keyboards, which are linked to the library's network and a database containing information on the library's holdings. Specialized software allows users to access the database. In addition, the library's network is likely also connected to a larger private network and the Internet. This connection gives users remote access to the library's database, as well as access to other computerized databases such as LexisNexis.
DATABASES
database centralized integrated collection of data resources.
The heart of any information system is its database, a centralized integrated collection of data resources. A company designs its databases to meet particular information processing and retrieval needs of its workforce. Businesses obtain databases in many ways. They can hire a staff person to build them on site, hire an outside source to do so, or buy packaged database programs from specialized vendors, such as Oracle. A database serves as an electronic filing cabinet, capable of storing massive amounts of data and retrieving it within seconds.
Decision makers can also look up online data. Online systems give access to enormous amounts of government data, such as economic data from the Bureau of Labor Statistics and the Department of Commerce. One of the largest online databases is that of the U.S. Census Bureau. The census of population, conducted every ten years, collects data on more than 120 million households across the United States. Another source of free information is company Web sites. Interested parties can visit firms' home pages to look for information about customers, suppliers, and competitors. Trade associations and academic institutions also maintain Web sites with information on topics of interest.
TYPES OF INFORMATION SYSTEMS
Many different types of information systems exist. In general, however, information systems fall into two broad categories: operational support systems and management support systems.
operational support system information system designed to produce a variety of information on an organization's activities for both internal and external users.
- An operational support system is designed to produce a variety of information on an organization's activities for both internal and external users. Examples of operational support systems include transaction processing systems and process control systems.
transaction processing system operational support system that records and processes data from business transactions.
- A transaction processing system records and processes data from business transactions. For example, major retailers use point-of-sale systems, which link electronic cash registers to the retailer's computer centers. Sales data are transmitted from cash registers to the computer center either immediately or at regular intervals.
process control system operational support system designed to monitor and control physical processes.
- A process control system monitors and controls physical processes. A steel mill, for instance, may have electronic sensors linked to a computer system monitoring the entire production process. The system makes necessary changes and alerts operators to potential problems.

The complex process of airline maintenance is critical to passenger safety.
MANAGEMENT SUPPORT SYSTEMS
management support system information system designed to provide support for effective decision making.
management information system (MIS) information system designed to produce reports for managers and other personnel.
An information system designed to provide support for effective decision making is classified as a management support system. Several different types of management support systems are available. A management information system (MIS) is designed to produce reports for managers and other personnel.
decision support system (DSS) system that provides direct support to businesspeople during the decision-making process.
A decision support system (DSS) gives direct support to businesspeople during the decision-making process. For instance, a marketing manager might use a decision support system to analyze the impact on sales and profits of a product price change.
executive support system (ESS) system that allows senior executives to access the firm's primary databases, often by touching the computer screen, pointing and clicking a mouse, or using voice recognition.
An executive support system (ESS) lets senior executives access the firm's primary databases, often by touching the computer screen, pointing and clicking a mouse, or using voice recognition. The typical ESS allows users to choose from many kinds of data, such as the firm's financial statements and sales figures for the company or industry. If they wish, managers can start by looking at summaries and then access more detailed information when needed.
expert system computer program that imitates human thinking through complicated sets of “if-then” rules.
Finally, an expert system is a computer program that imitates human thinking through complicated sets of “if-then” rules. The system applies human knowledge in a specific subject area to solve a problem. Expert systems are used for a variety of business purposes: determining credit limits for credit card applicants, monitoring machinery in a plant to predict potential problems or breakdowns, making mortgage loans, and determining optimal plant layouts. They are typically developed by capturing the knowledge of recognized experts in a field, whether within a business itself or outside it.
Quick Review
![]() List the four components of a computer-based information system.
List the four components of a computer-based information system.
![]() What is a database?
What is a database?
![]() Name the two general types of information systems and give an example of each.
Name the two general types of information systems and give an example of each.
 Computer Hardware and Software
Computer Hardware and Software
It may be hard to believe, but only a few decades ago computers were considered exotic curiosities, used only for very specialized applications and understood by only a few people. The first commercial computer, UNIVAC I, was sold to the U.S. Census Bureau in the early 1950s. It cost $1 million, took up most of a room, and could perform about 2,000 calculations per second.2 The invention of transistors and then integrated circuits (microchips) quickly led to smaller and more powerful devices. By the 1980s, computers could routinely perform several million calculations per second. Now, computers perform billions of calculations per second, and some fit in the palm of your hand.
When the first personal computers were introduced in the late 1970s and early 1980s, the idea of a computer on every desk, or in every home, seemed farfetched. Today they have become indispensable to both businesses and households. Not only have computers become much more powerful and faster over the past 25 years, they are less expensive as well. IBM's first personal computer (PC), introduced in 1981, cost well over $5,000 fully configured. Today, the typical PC sells for under $800.
TYPES OF COMPUTER HARDWARE
hardware all tangible elements of a computer system.
Hardware consists of all tangible elements of a computer system—the input devices, the components that store and process data and perform required calculations, and the output devices that present the results to information users. Input devices allow users to enter data and commands for processing, storage, and output. The most common input devices are the keyboard and mouse. Storage and processing components consist of the hard drive as well as various other storage components, including DVD drives and flash memory devices. Flash memory devices are becoming increasingly popular because they are small and can hold large amounts of data. Some, called thumb drives, can even fit on a keychain. To gain access to the data they hold, users just plug them into an unused USB (universal serial bus) port, standard on today's computers. Output devices, such as monitors and printers, are the hardware elements that transmit or display documents and other results of a computer system's work.
Different types of computers incorporate widely varying memory capacities and processing speeds. These differences define four broad classifications: mainframe computers, midrange systems, personal computers, and handheld devices. A mainframe computer is the largest type of computer system with the most extensive storage capacity and the fastest processing speeds. Especially powerful mainframes called supercomputers can handle extremely rapid, complex calculations involving thousands of variables, such as weather modeling and forecasting.3
The TITAN Supercomputer at Oak Ridge National Laboratory is the fastest computer on earth, performing 20,000 trillion calculations per second.
server a dedicated computer that provides services to other computers on a network.
Midrange systems consist of high-end network servers and other types of computers that can handle large-scale processing needs. They are less powerful than mainframe computers but more powerful than most personal computers. A server is a dedicated computer that provides services to other computers on a network. Many Internet-related functions at organizations are handled by servers. File servers, gaming servers, print servers, and database servers are but a few of the applications of these types of computers. They are also commonly employed in process control systems, computer-aided manufacturing (CAM), and computer-aided design (CAD).
Personal computers are everywhere today—in homes, businesses, schools, nonprofit organizations, and government agencies. According to recent estimates of PC ownership, more than two-thirds of American households have at least one personal computer. Personal computers have earned increasing popularity because of their ever-expanding capability to handle many of the functions that large mainframes performed only a few decades ago. Most desktop computers are linked to networks, such as the Internet.
Desktop computers were once the standard PC seen in offices and homes. And while millions of people still use desktop computers, laptop computers (including notebooks and netbooks) now account for more than half of all PCs sold. The increasing popularity of these computers can be explained by their improved displays, faster processing speeds, the ability to handle more intense graphics, larger storage capacities, and more durable designs. Their most obvious advantage is portability. Laptops are thinner and lighter than ever before. Business owners, managers, salespeople, and students all benefit from the constant innovation of the laptop.
Handheld devices such as smart phones are even smaller. Smart phones like the iPhone, Android, and BlackJack combine a phone with the Internet. Because of their ever-increasing capacity to surf the Internet, open and edit documents, send and receive messages, make calls, and more, sales of smart phones are rapidly outpacing traditional cell phones.
Two other devices—tablets and e-readers—are also making inroads in business. Besides Apple, Dell, Hewlett Packard, Motorola, and Samsung have all entered the tablet market with serious intentions and constant innovations designed to make them standard business tools. E-readers such as the Amazon Kindle and the Barnes & Noble Nook continue to expand their capacities as well—and will likely find their way into the business market before long.4
In addition to smart phones, specialized handheld devices are used in a variety of businesses for different applications. Some restaurants, for example, have small wireless devices that allow servers to swipe a credit card and print out a receipt right at the customer's table. Drivers for UPS and FedEx use special handheld scanning devices to track package deliveries and accept delivery signatures. The driver scans each package as it is delivered, and the information is transmitted to the delivery firm's network. Within a few seconds, using an Internet connection, a sender can obtain the delivery information and even see a facsimile of the recipient's signature.
COMPUTER SOFTWARE
software all the programs, routines, and computer languages that control a computer and tell it how to operate.
Software includes all of the programs, routines, and computer languages that control a computer and tell it how to operate. The software that controls the basic workings of a computer system is its operating system. More than 80 percent of personal computers use a version of Microsoft's popular Windows operating system. Personal computers made by Apple use the Mac operating system. Most handheld devices use other operating systems, such as Garnet or Windows Phone. The Droid and iPhone models have their own operating systems. Other operating systems include Unix, which runs on many midrange computer systems, and Linux, which runs on both PCs and midrange systems.

Although smart phones can boost productivity, some people overuse or even misuse them.
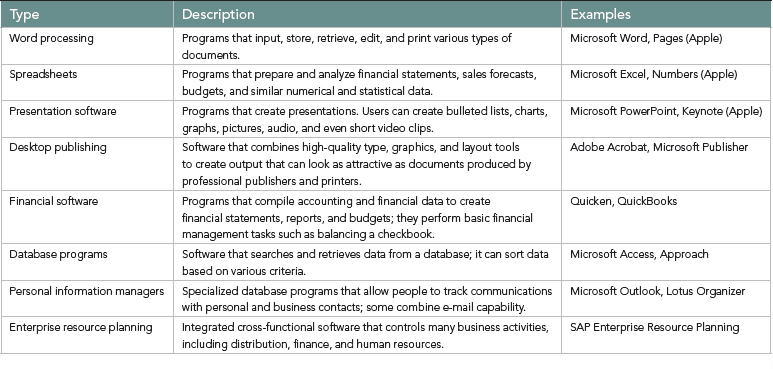
A program that performs the specific tasks that the user wants to carry out—such as writing a letter or looking up data—is called application software. Examples of application software include Adobe Acrobat, Microsoft PowerPoint, and Quicken. TABLE 14.1 lists the major categories of application software. Most application programs are currently stored on individual computers. The future of applications software is constantly changing. Some believe much of it will eventually become Web-based, with the programs themselves stored in the “cloud,” on Internet-connected servers. Others disagree, arguing that most computer users will not want to rely on an Internet connection to perform tasks such as preparing a spreadsheet using Microsoft Excel.
Quick Review
![]() List two input and two output devices.
List two input and two output devices.
![]() What accounts for the increasing popularity of notebook computers?
What accounts for the increasing popularity of notebook computers?
![]() What is software? List the two categories of software.
What is software? List the two categories of software.
 Computer Networks
Computer Networks
As mentioned earlier, virtually all computers today are linked to networks. In fact, if your computer has Internet access, you're linked to a network. Local area networks and wide area networks allow businesses to communicate, transmit and print documents, and share data. These networks, however, require businesses to install special equipment and connections between office sites. But Internet technology has also been applied to internal company communications and business tasks, tapping a ready-made network. Among these new Internet-based applications are intranets, virtual private networks (VPNs), and voice over Internet protocol (VoIP). Each has contributed to the effectiveness and speed of business processes, so we discuss them next.
LOCAL AREA NETWORKS AND WIDE AREA NETWORKS
local area network (LAN) computer network that connects machines within limited areas, such as a building or several nearby buildings.
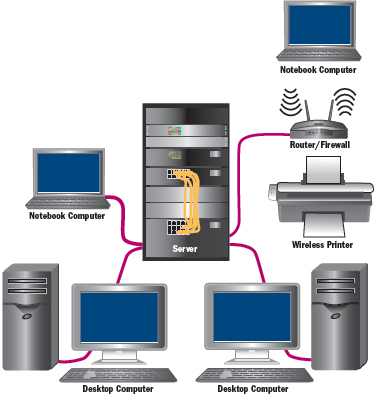
Most organizations connect their offices and buildings by creating a local area network (LAN), a computer network that connects machines within limited areas, such as a building or several nearby buildings. LANs are useful because they link computers and allow them to share printers, documents, and information and provide access to the Internet. FIGURE 14.1 shows what a small business computer network might look like.
wide area network (WAN) ties larger geographical regions together by using telephone lines and microwave and satellite transmission.
A wide area network (WAN) ties larger geographical regions together by using telephone lines and microwave and satellite transmission. One familiar WAN is long-distance telephone service. Companies such as AT&T and Verizon provide WAN services to businesses and consumers. Firms also use WANs to conduct their own operations. Typically, companies link their own network systems to outside communications equipment and services for transmission across long distances.
WIRELESS LOCAL NETWORKS
WiFi wireless network that connects various devices and allows them to communicate with one another through radio waves.
A wireless network allows computers, printers, and other devices to be connected without the hassle of stringing cables in traditional office settings. The current standard for wireless networks is called WiFi. WiFi—short for wireless fidelity—is a wireless network that connects various devices and allows them to communicate with one another through radio waves. Any PC with a WiFi receptor can connect with the Internet at so-called hot spots—locations with a wireless router and a high-speed Internet modem. Hundreds of thousands of hot spots exist worldwide today, in such places as airports, libraries, and coffee shops. Examples include Panera Bread's 1,500 bakery-cafes in the United States and Kansai International Airport in Osaka, Japan. Some locations provide free access, while others charge a fee.
Many believe that the successor to WiFi will be Wi-Max. Unlike WiFi's relatively limited geographic coverage area—generally around 300 feet—a single Wi-Max access point can provide coverage over many miles. In addition, cell phone service providers, such as Sprint Nextel and AT&T, offer broadband network cards for notebook PCs. These devices allow users to access the provider's mobile broadband network from virtually any location where cell phone reception is available.
INTRANETS
intranet computer network that is similar to the Internet but limits access to authorized users.
firewall limits data transfers to certain locations and logs system use so that managers can identify attempts to log on with invalid passwords and other threats to a system's security.
A broad approach to sharing information in an organization is to establish a company network patterned after the Internet. Such a network is called an intranet. Intranets are similar to the Internet, but they limit access to employees or other authorized users. An intranet blocks outsiders without valid passwords from entering its network by incorporating both software and hardware known as a firewall. Firewalls limit data transfers to certain locations and log system use so that managers can identify attempts to log on with invalid passwords and other threats to a system's security. Highly sophisticated packages immediately alert system administrators about suspicious activities and permit authorized personnel to use smart cards to connect from remote terminals.

WiFi connections are often called hot spots—locations with a wireless router and a high-speed Internet modem. Hundreds of thousands of hot spots worldwide are found airports, libraries, and restaurants.
Intranets solve the problem of linking different types of computers. Like the Internet, intranets can integrate computers running all kinds of operating systems. In addition, intranets are relatively easy and inexpensive to set up because most businesses already have some of the required hardware and software. For instance, a small business can simply purchase a DSL router and a few cables and create an intranet using phone jacks and internal phone lines. All the business's computers will be linked with each other and with the Internet.
VIRTUAL PRIVATE NETWORKS
virtual private network (VPN) secure connection between two points on the Internet.
To gain increased security for Internet communications, companies often turn to a virtual private network (VPN), a secure connection between two points on the Internet. VPNs use firewalls and programs that encapsulate data to make them more secure during transit. Loosely defined, a VPN can include a range of networking technologies, from secure Internet connections to private networks from service providers like IBM. A VPN is cheaper for a company to use than leasing several of its own lines. It can also take months to install a leased line in some parts of the world, but a new user can be added to a VPN in a day. Because a VPN uses the Internet, it can be wired, wireless, or a combination of the two.
Advanced Systems Group (ASG) is a provider of data storage and management services. As the company expanded and opened branch offices, its own security became a concern. ASG turned to Check Point, which created a secure VPN connecting ASG's home office and five branch offices. The VPN allows ASG to add new sites and new remote users automatically.5
VoIP
VoIP alternative version of telecommunication service using the Internet.
VoIP—which stands for Voice over Internet Protocol—is an alternative to traditional telecommunication services. The VoIP telephone is not connected to a traditional phone jack but rather to a personal computer with any type of broadband connection. Special software transmits phone conversations over the Internet rather than through telephone lines. A VoIP user dials the phone as usual, and can make and receive calls to and from those with traditional telephone connections (landline or wireless).
A growing number of consumers and businesses have embraced VoIP, mainly due to its cost savings and extra features. As technology continues to advance, demand for the service has increased. Several wireless companies, including AT&T, Verizon, and Vonage, permit VoIP on smart phones. Google integrates its Google Voice over VoIP. The various VoIP providers are working together with the goal of creating VoIP standards that would, among other things, permit seamless roaming worldwide, 911 calls, and ensure communications in natural disasters.6
Quick Review
![]() What is a LAN?
What is a LAN?
![]() Explain the differences between an intranet and a VPN.
Explain the differences between an intranet and a VPN.
![]() How does VoIP work?
How does VoIP work?
 Security and Ethical Issues Affecting Information Systems
Security and Ethical Issues Affecting Information Systems
Numerous security and ethical issues affect information systems. As information systems become increasingly important business assets, they also become progressively harder and more expensive to replace. Damage to information systems or theft of data can have disastrous consequences. When computers are connected to a network, a problem at any individual computer can affect the entire network. Two of the major security threats are e-crime and so-called malware.
E-CRIME
Computers provide efficient ways for employees to share information, but they may also allow people with more malicious intentions to access information. Or they may allow pranksters—who have no motive other than to see whether they can hack into a system—to gain access to private information. Common e-crimes involve stealing or altering data in several ways:
- Employees or outsiders may change or invent data to produce inaccurate or misleading information.
- Employees or outsiders may modify computer programs to create false information or illegal transactions or to insert viruses.
- Unauthorized people can access computer systems for their own benefit or knowledge or just to see if they can get in.
Information system administrators implement two basic protections against computer crime: they try to prevent access to their systems by unauthorized users and the viewing of data by unauthorized system users. The simplest method of preventing access requires authorized users to enter passwords. The company may also install firewalls, described earlier. To prevent system users from reading sensitive information, the company may use encryption software, which encodes, or scrambles, messages. To read encrypted messages, users must use an electronic key to convert them to regular text. But as fast as software developers invent new and more elaborate protective measures, hackers seem to break through their defenses. Thus, security is an ongoing battle.
Consumers with credit cards are particularly at risk from hackers. Recently Global Payments, a payments processing company used by major credit card companies, announced that consumer credit and debit card information may have been compromised.7 When a customer swipes a credit or debit card, the data are sent to a payment processor like Global Payments, which then forwards the transaction information to credit card companies like Visa and MasterCard.
As the size of computer hardware diminishes, it becomes increasingly vulnerable to theft. Handheld devices, for instance, can easily vanish with a pickpocket or purse snatcher. Many notebook computers and handheld devices contain special security software or passwords that make it difficult for a thief or any unauthorized person to access the data stored in the computer's memory. Notebook users should consider having such safeguards on their computers.
COMPUTER VIRUSES, WORMS, TROJAN HORSES, AND SPYWARE
malware any malicious software program designed to infect computer systems.
Viruses, worms, Trojan horses, and spyware, collectively referred to as malware, are malicious software programs designed to infect computer systems. These programs can destroy data, steal sensitive information, and even render information systems inoperable. Recently, malware was discovered in advertisements on major sites such as Yahoo, Fox, and Google as well as the New York Times and WhitePages.com. Malware attacks cost consumers and businesses billions of dollars annually. And malware is proliferating: according to a recent estimate, malware occurrences have exceeded 75 million.8
virus program that secretly attaches itself to other programs (called hosts) and changes them or destroys data.
Computer viruses are programs that secretly attach themselves to other programs (called hosts) and change them or destroy data. Viruses can be programmed to become active immediately or to remain dormant for a period of time, after which the infections suddenly activate themselves and cause problems. A virus can reproduce by copying itself onto other programs stored in the same drive. It spreads as users install infected software on their systems or exchange files with others, usually by exchanging e-mail, accessing electronic bulletin boards, trading disks, or downloading programs or data from unknown sources on the Internet.
worm small piece of software that exploits a security hole in a network to replicate itself.
A worm is a small piece of software that exploits a security hole in a network to replicate itself. A copy of the worm scans the network for another machine that has a specific security hole. It copies itself to the new machine using the security hole and then starts replicating from there as well. Unlike viruses, worms don't need host programs to damage computer systems.

Like their biological counterparts, computer viruses can infect their hosts, replicate quickly, and go on to infect many more computers.
botnet a network of PCs that have been infected with one or more data-stealing viruses.
A botnet is a network of PCs that have been infected with one or more data-stealing viruses. Computer criminals tie the infected computers into a network, often without the owners being aware of it, and sell the botnet on the black market. They or others use the botnet to commit identity theft, sell fake pharmaceuticals, buy blocks of concert tickets for scalping, and attack the Internet itself. Thousands of botnets are active today, creating huge profits for the botnet creators.
Grum is an interesting case in point. At one time, Grum was thought to be responsible for about 17 percent of the world's e-mail spam. In mid-2012, a consortium of computer security companies working with Internet service providers around the world, removed the Grum computer servers from the Internet. For a time it appeared that Grum was out of business. However, computer security experts have seen some recent e-mail traffic, suggesting that Grum might not be so “dead” after all.9
Trojan horse program that claims to do one thing but in reality does something else, usually something malicious.
A Trojan horse is a program that claims to do one thing but in reality does something else, usually something malicious. For example, a Trojan horse might claim, and even appear, to be a game. When an unsuspecting user clicks on the Trojan horse to launch it, the program might erase the hard drive or steal any personal data stored on the computer.
spyware software that secretly gathers user information through the user's Internet connection without his or her knowledge, usually for advertising purposes.
Spyware is software that secretly gathers user information through the user's Internet connection without his or her knowledge, usually for advertising purposes. Spyware applications are typically bundled with other programs downloaded from the Internet. Once installed, the spyware monitors user activity on the Internet and transmits that information in the background to someone else.
Attacks by malware are not limited to computers and computer networks. Users of smart phones have reported a sharp increase in viruses, worms, and other forms of malware. Recently, a Trojan horse known as Nickispy, masquerading as a Google+ app, managed to infiltrate smart phones. By reverse-engineering the malware, technology experts were able to unravel how it ended up on smart phones and eliminate the threat.10
As viruses, worms, botnets, and Trojan horses become more complex, the technology to fight them must increase in sophistication as well. The simplest way to protect against computer viruses is to install one of the many available antivirus software programs, such as Norton AntiVirus and McAfee VirusScan. These programs, which also protect against worms and some Trojan horses, continuously monitor systems for viruses and automatically eliminate any they spot. Users should regularly update them by downloading the latest virus definitions. In addition, computer users should also install and regularly update antispyware programs because many Trojan horses are forms of spyware.
INFORMATION SYSTEMS AND ETHICS
Not surprisingly, the scope and power of today's information systems raise a number of ethical issues and concerns. These affect both employees and organizations. For instance, it is not uncommon for organizations to have specific ethical standards and policies regarding the use of information systems by employees and vendors. These standards include obligations to protect system security and the privacy and confidentiality of data. Policies also may cover the personal use of computers and related technologies, both hardware and software, by employees.
Ethical issues also involve organizational use of information systems. Organizations have an obligation to protect the privacy and confidentiality of data about employees and customers. Employment records contain sensitive personal information, such as bank account numbers, which, if not protected, could lead to identity theft. Another ethical issue is the use of computer technology to monitor employees while they are working.
Quick Review
![]() Explain computer hacking.
Explain computer hacking.
![]() What is malware?
What is malware?
![]() How does a computer virus operate?
How does a computer virus operate?
 Disaster Recovery and Backup
Disaster Recovery and Backup
Natural disasters, power failures, equipment malfunctions, software glitches, human error, and terrorist attacks can disrupt even the most sophisticated computer information systems. While these problems can cost businesses and other organizations billions of dollars, even more serious consequences can occur. For example, one study found that 93 percent of firms that lost their data centers for ten days or more went bankrupt within one year.11
FalconStor provides data backup applications and sophisticated disaster recovery solutions for businesses worldwide. The firm's services extend well beyond data replication because organizations that have suffered a major loss have needs well beyond replicating their data. FalconStor's software solutions permit them to access their applications, restart operations, and return to serving customers.12
Disaster recovery planning—deciding how to prevent system failures and continue operations if computer systems fail—is a critical function of all organizations. Disaster prevention programs can avoid some of these costly problems. The most basic precaution is routinely backing up software and data—at the organizational and individual levels. However, the organization's data center cannot be the sole repository of critical data because a single location is vulnerable to threats from both natural and human-caused disasters. Consequently, off-site data backup is a necessity, whether in a separate physical location or online. Companies that perform online backups store the encrypted data in secure facilities that in turn have their own backups. The initial backup may take a day or more, but subsequent ones take far less time because they involve only new or modified files.
Quick Review
![]() To what types of disasters are information systems vulnerable?
To what types of disasters are information systems vulnerable?
![]() What is disaster recovery planning, and how does it work?
What is disaster recovery planning, and how does it work?
 Information System Trends
Information System Trends
Computer information systems are constantly—and rapidly—evolving. To keep their information systems up to date, firms must continually keep abreast of changes in technology. Some of the most significant trends in information systems today include the changing face of the workforce, the increased use of application service providers, on-demand computing, and cloud and grid computing.
THE DISTRIBUTED WORKFORCE
As discussed in earlier chapters, many companies rely more and more on a distributed workforce—employees who no longer work in traditional offices but rather in what are called virtual offices, including at home. Information technology makes a distributed workforce possible. Computers, networks, and other components of information systems allow workers to do their jobs effectively almost anywhere. For instance, none of JetBlue's reservations agents work in offices; they all work at home, connected to the airline's information system. Today, most employers have a policy regarding employees' remote access to their firm's network.
APPLICATION SERVICE PROVIDERS
application service provider (ASP) outside supplier that provides both the computers and the application support for managing an information system.
As with other business functions, many firms find it makes sense to outsource at least some of their information technology function. Because of the increasing cost and complexity of obtaining and maintaining information systems, many firms hire an application service provider (ASP), an outside supplier that provides both the computers and the application support for managing an information system. An ASP can simplify complex software for its customers so that it is easier for them to manage and use. When an ASP relationship is successful, the buyer can then devote more time and resources to its core businesses instead of struggling to manage its information systems. Other benefits include stretching the firm's technology dollar farther and giving smaller companies more competitive information power. Even large companies turn to ASPs to manage some or all of their information systems. Microsoft outsourced much of its internal information technology services to Infosys Technology to save money and streamline, simplify, and support its services.13

Recent technological advances in data storage and cloud computing allow people to work on their laptops, tablets, or smart phones from anywhere in the world.
A company that decides to use an ASP should check the background and references of a firm before hiring it to manage critical systems. In addition, customers should try to ensure that the service provider has strong security measures to block computer hackers or other unauthorized access to the data, that its data centers are running reliably, and that adequate data and applications backups are maintained.
ON-DEMAND, CLOUD, AND GRID COMPUTING
on-demand computing an organization's rental of software time from application providers, paying only for software usage.
Another recent trend is on-demand computing, also called utility computing. Instead of purchasing and maintaining expensive software, firms essentially rent the software time from application providers and pay only for software usage, similar to purchasing electricity from a utility.
cloud computing a type of information delivery under which powerful servers store applications software and databases for users to access on the Web.
Cloud computing uses powerful servers to store applications software and databases. Users access the software and databases via the Web using anything from a PC to a smart phone. The software as a service (SaaS) movement is an example of cloud computing.
Quick Review
![]() What is an application service provider?
What is an application service provider?
![]() Explain on-demand computing.
Explain on-demand computing.
What's Ahead?
This is the first of two chapters devoted to managing technology and information. The next chapter, “Understanding Accounting and Financial Statements,” focuses on accounting, financial information, and financing reporting. Accounting is the process of measuring, interpreting, and communicating financial information to enable people inside and outside the firm to make informed decisions. The chapter describes the functions of accounting and role of accountants; the steps in the accounting cycle; the types, functions, and components of financial statements; and the role of budgets in an organization.
Weekly Updates spark classroom debate around current events that apply to your business course topics. http://www.wileybusinessupdates.com
NOTES
1. Company Web site, http://evernote.com, accessed May 15, 2013; Mary Branscombe, “Good Software Should Be at Least as Smart as Your Dog,” Techradar, May 1, 2013, http://www.techradar.com; Neil McIntosh, “At Le Web, Visions of Not-So-Social Future,” TechEurope blog, December 8, 2011, http://blogs.wsj.com.
2. Museum Web site, “Timeline of Computer History,” http://www.computerhistory.org, accessed May 15, 2013.
3. Isha Suri, “Meet the Titan Super Computer and the World's Fastest Storage System,” Silicon Angle, April 19, 2013, http://siliconangle.com.
4. Paul Lamkin, “Top 10 Tablets for Business,” Techradar, accessed January 20, 2013, http://www.techradar.com.
5. Company Web site, http://www.virtual.com, accessed May 15, 2013.
6. Paul Barbagallo, “Views Vary on FCC Role as Regulator in All0-IP World,” Bloomberg BNA, January 30, 2013, http://www.bna.com; Leena Rao, “Google Voice Founder Sets His Sights on VoIP Once Again,” Techcrunch, March 7, 2012, http://techcrunch.com; Charles Schelle, “Update: Verizon VoIP Phone Outage Resolved,” SarasotaPatch, February 25, 2012, http://sarasota.patch.com.
7. Julianne Pepitone and Leigh Remizowski, “‘Massive’ Credit Card Data Breach Involves All Major Brands,” CNNMoney, March 31, 2012, http://money.cnn.com.
8. Kelly Jackson Higgins, “Mobile Malware on the Move, McAfee Report Says,” Dark Reading, February 21, 2012, http://www.darkreading.com.
9. “Avast Says Grum Botnet Is Back from the Dead,” IT Security Pro, May 24, 2013, http://itsecuritypro.co.uk; Brian Krebs, “Who's behind the World's Largest Spam Botnet?” Krebs on Security, February 1, 2012, http://krebsonsecurity.com.
10. Ken Dilanian, “Chinese Nickispy Malware Targets Smartphones,” Sydney Morning Herald, February 26, 2012, http://www.smh.com.au.
11. Company Web site, “Data Loss Statistics,” http://www.bostoncomputing.net, accessed May 15, 2013.
12. Company Web site, “FalconStor Provides Data Migration Technology for Dell Services Offering,” press release, March 6, 2012, http://www.falconstor.com.
13. Company Web site, http://www.infosys.com, accessed May 15, 2013.
CHAPTER FOURTEEN: REVIEW
Summary of Learning Objectives
![]() Distinguish between data and information, and discuss information systems.
Distinguish between data and information, and discuss information systems.
It is important for businesspeople to know the difference between data and information. Data are raw facts and figures that may or may not be relevant to a business decision. Information is knowledge gained from processing those facts and figures. An information system is an organized method for collecting, storing, and communicating past, present, and projected information on internal operations and external intelligence. Most information systems today use computer and telecommunications technology.
data raw facts and figures that may or may not be relevant to a business decision.
information knowledge gained from processing data.
information system organized method for collecting, storing, and communicating past, present, and projected information on internal operations and external intelligence.
chief information officer (CIO) executive responsible for managing a firm's information system and related computer technologies.
![]() List the components and types of information systems.
List the components and types of information systems.
When people think about information systems today, they're generally thinking about computer-based systems, which rely on computers and related technologies. Computer-based information systems have four components:
- Computer hardware
- Software
- Telecommunications and computer networks
- Data resource management
The heart of an information system is its database, a centralized integrated collection of data resources. Information systems fall into two broad categories: operational support systems and management support systems.
- Operational support systems are designed to produce a variety of information for users. Examples include transaction processing systems and process control systems.
- Management support systems are those designed to support effective decision making. They include management information systems, decision support systems, executive support systems, and expert systems.
computer-based information system information system that relies on computer and related technologies to store information electronically in an organized, accessible manner.
database centralized integrated collection of data resources.
operational support system information system designed to produce a variety of information on an organizations activities for both internal and external users.
transaction processing system operational support system that records and processes data from business transactions.
process control system operational support system designed to monitor and control physical processes.
management support system information system designed to provide support for effective decision making.
management information system (MIS) information system designed to produce reports for managers and other personnel.
decision support system (DSS) system that provides direct support to businesspeople during the decision-making process.
executive support system (ESS) system that allows senior executives to access the firm's primary databases, often by touching the computer screen, pointing and clicking a mouse, or using voice recognition.
expert system computer program that imitates human thinking through complicated sets of “if-then” rules.
![]() Discuss computer hardware and software.
Discuss computer hardware and software.
Hardware consists of all tangible elements of a computer system, including input and output devices. Major categories of computers include mainframes, supercomputers, midrange systems, personal computers (PCs), and handheld devices.
Computer software provides the instructions that tell the hardware what to do. The software that controls the basic workings of the computer is its operating system. Other programs, called application software, perform specific tasks that users want to complete.
hardware all tangible elements of a computer system.
server a dedicated computer that provides services to other computers on a network.
software all the programs, routines, and computer languages that control a computer and tell it how to operate.
![]() Describe computer networks.
Describe computer networks.
Local area networks connect computers within a limited area. Wide area networks tie together larger geographical regions by using telephone lines, microwave, or satellite transmission. A wireless network allows computers to communicate through radio waves. Intranets allow employees to share information on a ready-made company network. Access to an intranet is restricted to authorized users and is protected by a firewall. A virtual private networks (VPN) provides a secure Internet connection between two or more points. VoIP—voice over Internet protocol—uses a personal computer running special software and a broadband Internet connection to make and receive telephone calls over the Internet rather than over traditional telephone networks.
local area network (LAN) computer network that connects machines within limited areas, such as a building or several nearby buildings.
wide area network (WAN) ties larger geographical regions together by using telephone lines and microwave and satellite transmission.
WiFi wireless network that connects various devices and allows them to communicate with one another through radio waves.
intranet computer network that is similar to the Internet but limits access to authorized users.
firewall limits data transfers to certain locations and logs system use so that managers can identify attempts to log on with invalid passwords and other threats to a system's security.
virtual private network (VPN) secure connection between two points on the Internet.
VoIP alternative version of telecommunication service using the Internet.
![]() Discuss the security and ethical issues affecting information systems.
Discuss the security and ethical issues affecting information systems.
Numerous security and ethical issues affect information systems. Two of the main security threats are e-crime and malware. E-crimes range from hacking—unauthorized penetration of an information system—to the theft of hardware. Malware is any malicious software program designed to infect computer systems. Examples include viruses, worms, botnets, Trojan horses, and spyware.
Ethical issues affecting information systems include the proper use of the systems by authorized users. Organizations also have an obligation to employees, vendors, and customers to protect the security and confidentiality of the data stored in information systems.
malware any malicious software program designed to infect computer systems.
virus program that secretly attaches itself to other programs (called hosts) and changes them or destroys data.
worm small piece of software that exploits a security hole in a network to replicate itself.
botnet a network of PCs that has been infected with one or more data-stealing viruses.
Trojan horse program that claims to do one thing but in reality does something else, usually something malicious.
spyware software that secretly gathers user information through the user's Internet connection without his or her knowledge, usually for advertising purposes.
![]() Explain disaster recovery and backup.
Explain disaster recovery and backup.
Information system disasters, whether through human error or due to natural causes, can cost businesses billions of dollars. The consequences of a disaster can be minimized by routinely backing up software and data, both at an organizational level and at an individual level. Organizations should back up critical data at an off-site location. Some firms may also want to invest in extra hardware and software sites, which can be accessed during emergencies.
![]() Review information systems trends.
Review information systems trends.
Information systems are continually and rapidly evolving. Some of the most significant trends are the increasing demands of the distributed workforce, the increased use of application service providers, on-demand computing, and grid computing. Many people now work in virtual offices, including at home; information technology makes this possible. Application service providers allow organizations to outsource most of their IT functions. Rather than buying and maintaining expensive software, on-demand computing offers users the option of renting software time from outside vendors and paying only for their usage. Grid computing consists of a network of smaller computers running special software creating a virtual mainframe or even supercomputer.
application service provider (ASP) outside supplier that provides both the computers and the application support for managing an information system.
on-demand computing an organization's rental of software time from application providers, paying only for software usage.
cloud computing a type of information delivery under which powerful servers store applications software and databases for users to access on the Web.
Quick Review
LO1
![]() What is the difference between data and information?
What is the difference between data and information?
![]() What is an information system?
What is an information system?
LO2
![]() List the four components of a computer-based information system.
List the four components of a computer-based information system.
![]() What is a database?
What is a database?
![]() Name the two general types of information systems and give an example of each.
Name the two general types of information systems and give an example of each.
LO3
![]() List two input and two output devices.
List two input and two output devices.
![]() What accounts for the increasing popularity of notebook computers?
What accounts for the increasing popularity of notebook computers?
![]() What is software? List the two categories of software.
What is software? List the two categories of software.
LO4
![]() What is a LAN?
What is a LAN?
![]() Explain the differences between an intranet and a VPN.
Explain the differences between an intranet and a VPN.
![]() How does VoIP work?
How does VoIP work?
LO5
![]() Explain computer hacking.
Explain computer hacking.
![]() What is malware?
What is malware?
![]() How does a computer virus operate?
How does a computer virus operate?
LO6
![]() To what types of disasters are information systems vulnerable?
To what types of disasters are information systems vulnerable?
![]() What is disaster recovery planning, and how does it work?
What is disaster recovery planning, and how does it work?
LO7
![]() What is an application service provider?
What is an application service provider?
![]() Explain on-demand computing.
Explain on-demand computing.