Chapter 8
Subvert (Controls Bypass)
IN THIS CHAPTER
![]() Stopping subvert attacks with antivirus software
Stopping subvert attacks with antivirus software
![]() Simulating subvert attacks with Nmap
Simulating subvert attacks with Nmap
![]() Discovering the vectors hackers use in subvert attacks
Discovering the vectors hackers use in subvert attacks
![]() Exploring ways hackers bypass controls
Exploring ways hackers bypass controls
The definition of subvert is to undermine and get within control. In the realm of IT security, this means you get within and beyond controls or control points that are meant to secure access. Subvert attacks bring their own intense brand of nastiness to the security equation.
Advanced persistent threats (APTs) are the holy grail of hacker attacks where an attacker can infiltrate, gain what they need, and then move to exfiltration undetected with the goods. There are other attacks that are less advanced such as bypassing controls such as an access list without being caught or logging into a system undetected to access data. Some malware can also be introduced to elevate privileges of accounts that can then be used to bypass other security controls.
In this chapter, I discuss these and other forms of subvert attacks.
Toolkit Fundamentals
In this section, I show you the tools for conducting a pen test to simulate subvert attacks, which are attacks that get past security controls. Tools such as Kali, Nmap (which I discuss further in an upcoming section), Wireshark, and others can be used to scan for vulnerabilities in your systems. As with so many attacks, subvert attacks can be difficult to track. To mitigate the risks and the attacks, I recommend going outside your pen test toolkit.
Antivirus software and other tools
Many subvert attacks originate from malware. Because of this, the best tool you have in your arsenal is antivirus software platforms used in your enterprise. I focus the final section of this chapter on how attackers thwart your security by getting around your AV tool.
Nmap
There is no better tool used to probe, map, and identify holes and ways through them than Nmap. Nessus, Metasploit, and even Kali offer many tools to perform this function, but Nmap itself is the go-to for this type of attack.
Using Nmap to simulate subvert attacks
Here are some reasons why Nmap helps to simulate subvert attacks:
- Nmap is customizable and can be script driven. You can set up scripts to execute based on the programming you create to launch attacks.
- Nmap does exactly what is needed to scan, probe, map and identify weaknesses especially needed for a subvert attack.
- You can conduct varying levels of attacks from low to high intensity. This allows for a very quick pen test scan of your weaknesses, all the way to very involved highly intense and robust scanning that can help to really show you over time what problems exist.
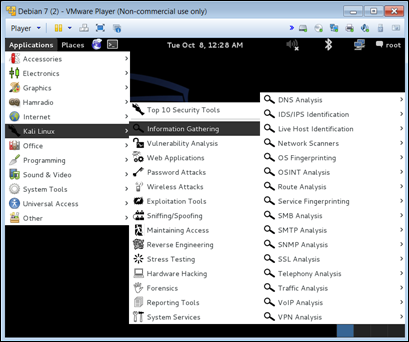
FIGURE 8-1: Kali’s Information Gathering menu can help you perform subvert and stealth-based attacks.
Putting Nmap to work
As shown in Figure 8-2, I have launched an attack against a router/routing device scan. My goal is to identify all devices on a subnet by scanning hosts and trying to identify them and map them. This also allows me to build a list of vulnerabilities that I may be able to exploit.
Running a scan against a host may be captured by security devices, which will show the IP address of origination (your IP address). Many times, these attacks are leveraged from spoofed addresses or hosts that have been hijacked and owned by the hacker — usually through malware such as a Trojan horse — so they aren’t caught.
In this example, I am choosing an intense scan, which generates the most output for my report, because:
- I am not on a production network.
- I am limiting my scan to one host at a time as I am aware of the network topology.
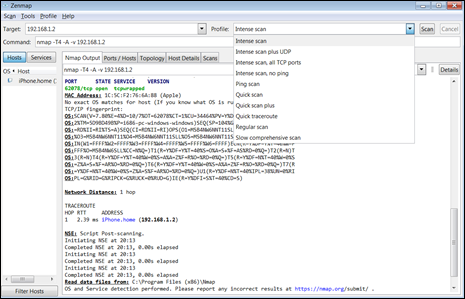
FIGURE 8-2: Using Nmap to launch an attack against a router/routing device scan.
As shown in Figure 8-3, this intense scan is mapping the vulnerabilities through a series of test scans looking for open ports and other penetration points. The main penetration test I am launching right at this point is a SYN Stealth Scan, which is designed to use SYN packets at a host or hosts in hopes of receiving an acknowledgment from a host in the form of an ACK packet.
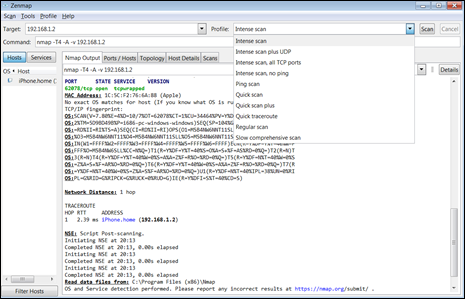
FIGURE 8-3: Conducting a SYN scan to identify open ports.
Figure 8-4 shows the SYN Stealth Scan identifying a host and a possible host that responded, which is the source of my next attack. Other identifiable information was found (see Figure 8-5), which includes the MAC address of the device being scanned and distance by network hop.
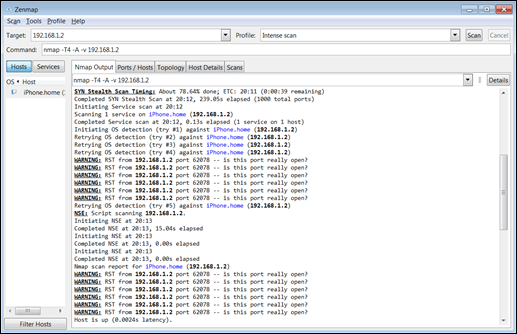
FIGURE 8-4: Identifying possible hosts and ports.
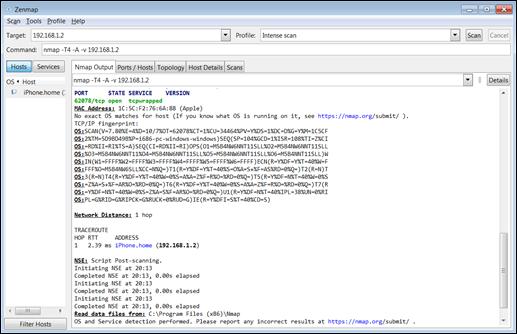
FIGURE 8-5: Learning the MAC address of the scanned device and distance by network hop.
You can do so much more with Nmap, and it’s a must for this next series of subvert attacks I cover.
Attack Vectors
To help explain attack vectors, Figure 8-6 shows that regardless of whether an attack originates from inside or outside your protected network, the concepts are the same. I am going to conduct a pen test to first see if I can probe your network. I may do this from a spoofed address or I may launch an attack from a Trojan installed on a machine that a victim may not be aware of.
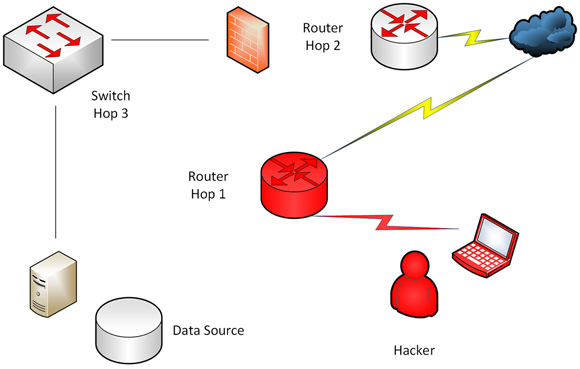
FIGURE 8-6: Internal and external subvert attacks operate under the same concepts.
In this attack vector, the hacker (in this case, me) is looking to gain access and do so undetected. By infiltrating the network step by step (or hop by hop), I can begin sneaking my way inside to collect information from valuable data sources. Here’s how I did it:
The first hop will be through a router I scanned with Nmap and found that it was vulnerable due to a weak password.
By conducting a password crack, I am inside the first hop and ready to attempt to gain access to the next hop. Once in this router, I am able to conduct a series of next steps to find more information: I can look at the routing table, the MAC address table, ARP cache, and other non-proprietary features to learn where to go next.
I can look at the router’s configuration file and see how it is configured. For example, if I see that there is a port connected to another network with an IP address and subnet mask associated for only four valid hosts to include the network and broadcast identifiers, I can assume that if the one configured IP address is 10.1.1.2, perhaps the next one across the wide area network (WAN) link may be 10.1.1.3. I can quickly ping or attempt to telnet to the next hop to see.
Proprietary systems such as Cisco brand routers also use other protocols and services such as CDP (Cisco Discovery Protocol), which allows for the building of a database of neighbors that can be accessed by running the
show CDP neighborscommand as another example on how to get information on adjacent hosts.- I can attempt to access router hop 2 and do the same procedure as hop 1.
I then attempt to get to hop 3, which is a switch that also accepts telnet as an option.
I also list a firewall host between the router and the switch, but this may signify an access control list (ACL) that disallows traffic or attempts and may not be an actual separate firewall device.
If the router or any other device is misconfigured and allows connections through, I am able to get to the third hop.
Once I am able to maintain a connection in the third hop, I may be able to run a ping sweep from the switch device or look at the MAC table to see what may be connected. Inside I find a Linux host that I find interesting because it too accepts connections from telnet and allows me to quickly password crack and gain access to the system.
Here I can then look through the system and see whether it hosts any internal data I can use, or I can remain dormant to see whether there are other secrets elsewhere at another time.
Although this is a simplified explanation of a pen attack with a lot of misconfigurations and protocols that should be disabled and more secure versions used (such as SSH instead of telnet), it does not mean that this attack is unachievable. Believe it or not, this exact hack is still being conducted today.
What it should teach you as a pen tester is that the attack vector and path taken would be the same no matter what types of attacks were used or attempted. If a piece of malware was inside your network and a hacker can control the host it is attached to, they would conduct this exact series of attacks.
Phishing
One of the main options for a hacker is to gain access to a host computer through phishing, which is a technical version of social engineering. You are using an email hoax or information to entice someone to do something (such as click a link), which can lead to click bait or clickjacking attacks that install software on your machine to gain access to it. That machine then becomes part of the hacker toolkit to gain access to your systems.
As a pen tester, you need to attempt this same attack on your internal users to see whether they are smart or trained well enough to know to not click a phishing attempt. If they're presented with something that looks fishy (pun intended), do the users know what they can do to thwart what might be a possible attack?
The clickjacking attack is very similar. The hacker tricks a victim to click something they perceive to be something else. The victim clicks, for example, a link they think is legitimate, and the hacker can gain access or control that system.
It’s kind of like a standard carjacking but with click bait instead. An attacker is going to trick you into giving something up by making you provide it through trickery.
How this relates to subvert attacks and stealth ops is that the victim becomes part of the attacker’s hack. When victims allow themselves to be fooled, they become part of the path or vector of the attack the hacker is launching. You should be comfortable with constructing a fake link that redirects to another page or site (informing the user they have been fooled) from a real-looking address and provide materials for them to review on how to identify these types of attacks in an educational way.
Spoofing
Spoofing is the way an attacker disguises their identity and remains hidden. If I launch an attack from Nmap and need to hide my identity, I can either do it from a hacked source or directly from the tool itself.
As an example, when you launch Nmap, you can use the –S option, which spoofs your source address into whatever address you would like to choose. Other ways to spoof are pretty well documented online based on the tools you choose, but because Nmap is the focus here, attempt to add the –S <ip_address> information and use Wireshark on the receiving host to see the spoof attack. To conduct a spoofing attack, such as Man in The Middle (MiTM) or other subvert attacks, see Chapter 5.
Another example of spoofing would be when a hacker makes an email look legitimate to the recipient. But it’s easily seen as a spoof through the email header, where the fake address is usually listed. This kind of spoof happens to people all the time — they get an email from their email provider (or so they think) saying that their account has been compromised and they need to log into their account to fix it. When they do, they give the attacker their username and password.
Malware
In this section, I shine a light on the inner workings of how an attacker uses AV software and malware to get into your system. It should be no wonder (or mistake) that the best way to get in undetected is through malware. The original vector I describe earlier in this chapter, in the “Attack Vectors” section, going hop from hop leaves a huge footprint in the sand. You can get caught at any point in that path.
As you move from system to system you may be caught by other tools and logs. As well, you need to clean and sanitize hop from hop to eliminate being seen, which sometimes means wiping logs that can identify you. It all depends on how much security an enterprise uses and has deployed. For any company with much to lose (and much to gain for a hacker), it seems likely that they will have much of this security gear deployed.
Using malware to find a way in
Malware is one of the best ways in, so using this to your advantage can reap many rewards. Obviously by running tools such as Nessus and other vulnerability assessors, you will find what systems are unpatched, are vulnerable, and have more holes than Swiss cheese. This doesn’t mean that it covers all vectors. Just because you patch a system doesn’t mean it’s safe from attack.
If a system gets malware on it that disables the protection from a host level as shown in Figure 8-7, you may not see it until it’s too late. For example, this version of Symantec Endpoint Protection (SEP) has been disabled, causing it to allow malware to pass due. It requires updates due to a long disable period. If you don’t see it on the host system or whoever is managing it didn’t fix it, malware could have slipped by. You can also cause it to fail manually by locally accessing the host.
In Figure 8-8, the only way to re-enable and fix your AV is by either having it done remotely at the management console or if you fix it yourself locally at the local workstation.
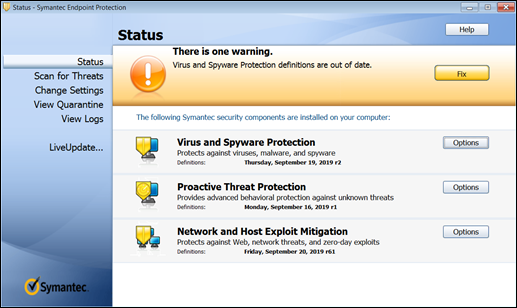
FIGURE 8-7: Host-based AV software indicates there’s an issue requiring attention.

FIGURE 8-8: Updating and fixing your AV.
Bypassing AV software
AV bypass is common and one way to get through your host-based defenses. Local firewalls are passed in the same fashion. Once this happens, malware, viruses, worms, Trojan horses, backdoor/rootkits and other nasty pieces of code will enter and allow for further attacks remotely. The attacks can happen locally, too; raised privileges or escalated privileges on the host machine allows more access than the user may have had previously.
APTs are commonly done by using a variety of methods such as infiltration through code, by accessing via pen tests tools, malware, programs, and other means. Once you gain access, you can expect the following to take place from the hacker and you as the ethical hacker should take each step and ensure that you are secure:
Gain initial access (infiltration).
This is the first step in the APT attack and can happen from many of the methods I list throughout this chapter. You should re-enact them to ensure your systems are safe and your end users are educated.
Once access is established and can be maintained, work to protect that access and keep it a secret.
This is done through stealth ops and by maintaining those operations by any means possible.
Now that access is secure and secret, start attempting to move around, gaining more access, and identifying data or targets to access.
This is done by continuing to run tests, access other devices, find targets, penetrate them, all while remaining secret and secure.
Complete the APT by exfiltration of data and information.
Do so while remaining inside or by getting out with the data and without getting caught.

 Other tools in your toolkit include (but aren’t limited to) Kali, Nmap, Wireshark, AV management consoles, router and firewall logs, and others. For subvert attacks the focus will be on probing and mapping to find an entry point. Once an entry point is found, there needs to be movement within the network and then finding a way to stay hidden.
Other tools in your toolkit include (but aren’t limited to) Kali, Nmap, Wireshark, AV management consoles, router and firewall logs, and others. For subvert attacks the focus will be on probing and mapping to find an entry point. Once an entry point is found, there needs to be movement within the network and then finding a way to stay hidden. Kali has Nmap and several other mapping tools within its toolset. Open Kali and navigate to the Information Gathering menu (see
Kali has Nmap and several other mapping tools within its toolset. Open Kali and navigate to the Information Gathering menu (see  Remember that Nmap is a scanning tool and will probe and test your systems. If you’re using this on a production network, it could create issues or set off alarms. Make sure you have permission to launch this tool prior to doing so.
Remember that Nmap is a scanning tool and will probe and test your systems. If you’re using this on a production network, it could create issues or set off alarms. Make sure you have permission to launch this tool prior to doing so.