Chapter 12
Making Recommendations
IN THIS CHAPTER
![]() Exploring the need for recommendations
Exploring the need for recommendations
![]() Offering ways to shore up security
Offering ways to shore up security
![]() Looking at general areas of security to strengthen
Looking at general areas of security to strengthen
![]() Showing how to defend against attacks
Showing how to defend against attacks
![]() Understanding and protecting vectors
Understanding and protecting vectors
In this chapter, I try to capture the most common issues you might encounter and recommendations you’ll likely want to make based on your tools. The chapter focuses on the tools, the report, the output, and your report findings and fuse those with best practices found in the industry today.
Most of what you find in this chapter (and in real life) is that most of the recommendations revolves around systems that are not up to date and need security and other forms of patching or misconfigurations that lead to security risks in your infrastructure, network, and applications.
This is your time to shine! You can highlight many of the items you will learn in your report, create a separate report or put a presentation together and/or give a training class or awareness seminar. All this is part of post-test assessment and recommendations that you can provide your company or clients based on your findings.
Understanding Why Recommendations Are Necessary
You may be given tasks where you just run the pen test, collect the findings, and report them. Other times, you are expected to recommend how to remediate some of the issues you’ve identified.
Before you report any recommendations, think about these key considerations:
Not all recommendations are actionable. You’ll find accepted risks (which are noted on the risk register), and you may have to have alternative solutions in place to mitigate the threat. For example, a router may need to remain exposed.
The recommendation normally would be to block access to the router. Because it needs to be accessed, hardening it with access control lists may be the viable solution in this case.
Some recommendations may not solve the problem. You may make recommendations that are industry-standard solutions that often come from the vendors, but they may not mitigate the risk.
There may be more risks hidden within the solution. This is where retesting (which I cover in the next chapter) comes into play and is a critical piece of pen testing.
Seeing How Assessments Fit into Recommendations
When you’re making recommendations, keep in mind you might need to consider information from various sources and that you might need to supply information to someone else. The latter case happens when you’re only running the test and submitting a report, but another person or team actually makes the recommendations.
Here’s where you most likely get information to build a recommendation list, if you’re responsible for this task:
- The assessments from the pen test you conducted
- The final pen test report you submitted
- Your pen test tool logs and any other artifacts you have from the test
- An existing pen test report that you need to analyze
Your first steps are to review what you have conducted and start to develop a recommendations list from your reported findings.
In Figure 12-1 is a snapshot from Nessus that highlights findings I put into a report after a pen test. If I were to create a series of recommendations from this snapshot alone, I may come up with some of the most obvious, such as reviewing the organization’s use of the Firefox web browser installed on Apple OS and whether an upgrade or a patch is needed. At this point, I’m getting the lay of the land if you will.
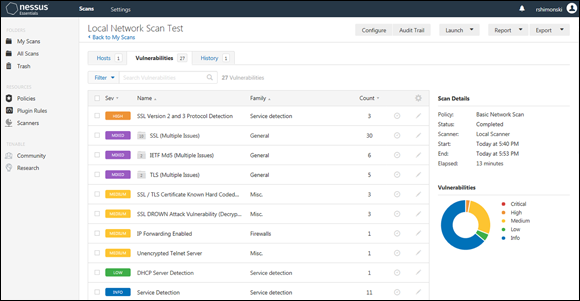
FIGURE 12-1: Reviewing Nessus for hardening tips.
These are some of the easiest assessment-based recommendations to make because you have a blueprint to follow. You should also use the priority flags from the toolset to provide a priority level to each item for your risk register.
A recommendation to make here may also expand beyond a patch or a security update. You may do some research and find that the browser itself is flawed, it is unable to be fixed (perhaps it’s not fixed by the vendor yet), and is so critical that you need to disable the use of this browser across your organization until it’s fixed.
- Do your best to suggest a reduced footprint. Reduce the amount of overhead in your technology that you may not need. For example, if you’re using Windows systems and you don’t need certain services, remove them or disable them. An example could be to turn off AutoPlay (AutoRun in older systems), which allows devices once connected to run what may be on them. AutoPlay is dangerous because anyone can plug in a USB drive with malware, which would immediately install. By turning off a service of this kind, you have reduced the attack service, reduced exposure, hardened your system, and inevitably reduced your footprint.
- Educate those who might be susceptible to providing sensitive information. Social engineering, which I discuss further in Chapter 4, is a great way for would-be hackers to coax information such as usernames and passwords out of unwitting users.
- Keep certain information on a need to know basis. People need access to information required to perform their jobs, so policies managing access should be in place.
- Become deceptive with what you provide as information. For example, you might recommend turning a default account on a system into a honeypot to identify whether possible attackers are testing the waters from inside your organization. A honeypot account looks and behaves like the real account, but it’s isolated from other systems, so no actual damage can be done if someone does hack into it.
Networks
Making recommendations to harden your network can come from the current pen test and report you conducted and completed. You may have found a series of ports open that allowed access to systems or credentials to devices that were easily cracked and accessed.
General network hardening
There are many ways to secure and harden a network:
- Use challenging password security options and block IP access from unknown sources. Doing so helps you to protect and harden against router hopping from device to device. Hackers commonly try to breach a network by router hopping. You can use Kali to check routers for access and conduct brute force password cracking until access is gained.
- Use encryption. Other attacks I covered include buffer overflows, reading routing updates that were left unencrypted, and more. Every one of these should be in your recommendations list and how they can be fixed so that the attack can’t be conducted in the future, or if you can’t block or change access, how to monitor for intrusion so you’re aware if a hack is taking place.
- Disable any services not in use. As mentioned earlier in the chapter, reducing the footprint or attack surface can minimize what a hacker has access to exploit. An example could be to remove any protocols not being used so if you are only using TCP/IP version 4, you can remove version 6. You can remove NetBIOS if you’re only using DNS for name resolution and so on.
- Use up-to-date software that is free of bugs and security issues.
- Leverage Authentication, Authorization, and Accounting (AAA) whenever possible. AAA is used as a service that allows you to monitor access into devices so you can review a log of all activities taking place.
- Authentication: Authentication handles credentials such as username and password. Without a credential set, you can’t access a system. You must authenticate to a system to use it.
- Authorization: Authorization gives you permission to do things. So, for example, your user account may belong to a group that allows you access to data.
- Accounting: Accounting is the log based on what you do once you’ve been authenticated and authorized (or not authorized) based on your activity. So, when you access the file, it appends to a log what you have done and makes inspection and tracking easier for those looking to protect services, systems, and data.
- Ensure certain attack patterns are nullified by additional security. For example, applying SSH instead of telnet so passwords that aren’t cleartext can be caught by pen test tools such as Wireshark, or further segmenting protected areas of your network with VLANs (virtual LANs) so that access can be controlled to secure services like databases you want to keep secure.
- Rely on vendors. For example, Cisco Systems (
www.cisco.com) is one of the premier vendors of network equipment and software. Cisco provides a hardening guide (as most vendors do) so that you know how to increase your security posture and allow for your systems to be in a higher state of protection then if you didn’t apply many of the suggestions they make.https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.htmlAlso, many of these same suggestions (such as using a centralized log collection) can be further used and suggested on other systems regardless of make or vendor. Some of the suggestions are best practices no matter what product you use.
Network segmentation
Networks can be laid out in many ways, but most (if not all) generally follow basic standards. You can see most of them in Figure 12-2. The figure shows the most common, which is the division of the internal and external networks (usually by the demarcation of the public or private owned vendor network) that allows you to gain or get access into and out of your internal network. Along the external edge is where most hackers attempt to penetrate because this is where you’re visible on the public Internet.
To access an internal company network, you have to use a public facing connection to then connect in from the edge into the company network to access their core. The core is commonly referred to as the high-speed center of any network that is configured.
Depending on the size of the network, you could say that most core networks at least have a distribution, or access, layer where other switches connect and wired and wireless segments connect together. Most of these segments are configured with different IP address blocks and further configured as virtual local area networks (VLANs). Segmentation (physically by device or logically by VLAN) can help you protect each portion with access lists or firewalls so you can control what people can or can’t access based on what they’re permitted to do.

FIGURE 12-2: A large network map.
Internal network
Making recommendations to secure a local internal network are fairly straightforward:
- Make sure the recommendation is correctly documented. This is true of any recommendation of any IT system or services. Documentation helps all parties better understand, respond to, secure, and operate their technology investment.
- Use IANA private IP addressing blocks and segment your network correctly. Keep critical resources on private networks or VLANs that you can use your routers or layer 3 switches as barriers by controlling access with access control lists or only routing approved segments to these private ones. This step alone helps to mitigate many hop-by-hop attacks and stop many hackers in their tracks.
- Secure the core network by only allowing traffic to traverse it. You don’t necessarily plug servers directly into it as shown in Figure 12-2. This is one reason why it was so easy to access this server because it was further segmented into the distribution layer.
Wired/wireless
A major challenge with wireless networks is that they aren’t always set up correctly. An example may be where a hacker is able to see and get a signal from a wireless access point from the external network (refer to Figure 12-2). This can be a hacker with a transmitter hacking from the parking lot with a high-powered antenna to see whether any SSIDs respond to beaconing.
If you show you can in fact gain access this way, here are a few recommendations to make:
- Turn off SSIDs to private networks so they do not advertise.
- Lower the decibel and power rating on the access point so it doesn’t transmit past the walls of the organization.
- Set up monitoring of the wireless network through controllers that allow for auditing and other AAA functions.
External
The external network is hard to secure because most times you don’t own the systems that the ISP provides. You also need to consider that you are limited in what you can secure, but this is the true power of the pen test and the pen test report. If you find that you scan the provider and edge leading into your private network (the demarcation is considered the DMZ, or demilitarized zone) where you may even host public facing systems, you can show where they need to lock down their own system or if you own them, lock down your own.
Systems
Whether you pen test and report on Windows, Linux, Unix, Apple OS, or basically any other operating system in your organization, you will find some form of vulnerability that needs to be patched, fixed, reconfigured, or examined. With the nature of changing technology, there will always be updates that cause more problems later. Most, if not all, pen test output shows operating systems that need patching or protected against some form of threat in the wild.
In general, you can apply across the board some of these common guidelines:
- Apply hardening to the base operating system. If you were considering Windows desktops (very commonly a big footprint in most organizations), you would want to consider focusing on Internet Explorer or Edge and using policies to control what it allows an end user to do.
- Include a program for patching and compliance. The program should allow all Windows desktops to be up to date with all critical security patches most of which stop elevated privileged and malware.
Lock down local administrator rights and privileges. You limit access rights for any user, admin, or anyone permitted to use the system so that they only have rights to do exactly what they need to do.
 Because default administrator accounts have access to literally everything, consider making them honeypot accounts to ensnare unsuspecting hackers looking to attempt to use them. Or disable them and give rights to the named accounts of your users and admins with logging enabled to ensure that no unnamed accounts remain in use with the power to do anything on your systems.
Because default administrator accounts have access to literally everything, consider making them honeypot accounts to ensnare unsuspecting hackers looking to attempt to use them. Or disable them and give rights to the named accounts of your users and admins with logging enabled to ensure that no unnamed accounts remain in use with the power to do anything on your systems.- Ensure the desktops use an updated antivirus program.
- Stay abreast of new features available with newer versions of operating systems. With these newer systems come updated forms of security, and you’re responsible to know about these updates and consider recommending them if you find that you were able to penetration and exploit a system because it was not available. One example of this may be the Windows 10 Attack Surface Reduction (ASR) feature that can work with your AV solution against malware.
Servers
You secure servers by hardening them using vendor recommendations. For example, if you have a Windows Server system, a large number of services specific to that vendor are available. You must consider turning all those services on or shutting them off based on what you captured during your pen test.
To generalize, if you run Unix or Windows, you want to make sure that they are both not running extraneous services (like telnet) and secure them with SSH as an example.
No matter what you pen test (and report on), when you’re making recommendations, include general or standard server recommendations and then you make those more specific. To further explain what I mean:
- A general recommendation would be to make sure all your servers are patched to the approved level by the vendor and that all current security patches are applied.
- A more specific recommendation would be to make sure that Company X shuts down and stops the DHCP server service found on a rogue Windows system that could inadvertently dole out IP addresses to unsuspecting victims.
You can follow these same recommendations for any server platform you choose to test.
Client-side
Client-side attacks are the most common because the desktop (and other desktop level devices) are the most commonly used, easily accessed, least protected and least monitored of all infrastructure components. They are the easiest to infiltrate with malware or even through social engineering.
The most common recommendations:
- Make sure client systems are patched and updated.
- Run current AV software on the clients and ensure they’re scanned daily.
- The devices should be encrypted and unusable in case of theft or if lost.
- Access to the devices should be secured through awareness training and constant reminder from IT staff.
- Disable unneeded services. As shown in Figure 12-3, one of the things you can do on server systems, client systems, and even routers and switches, is disabling unneeded services; for example, telnet.
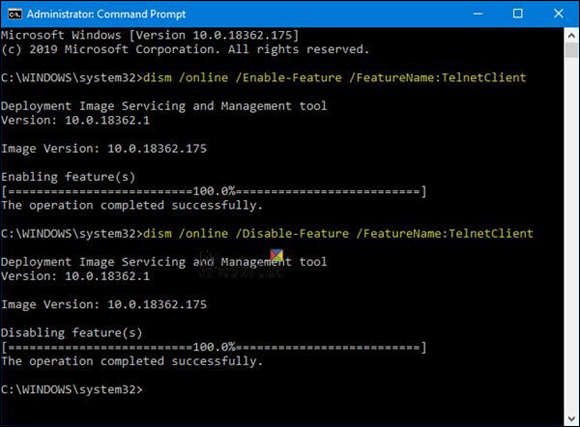
FIGURE 12-3: Disabling unneeded services, such as telnet services.
Infrastructure
General infrastructure includes storage platforms, mainframes, tape silos, and anything else that falls outside of the network and servers attached to them. You need to consider each separately and harden it accordingly.
Some examples (and suggestions) include but aren’t limited to all of these devices connect to the network that share network interfaces, ports, and protocols, use TCP/IP (or other protocol), and communicate and pass traffic back and forth. Because they do, every single one of them becomes a target to an unethical hacker or ethical hacker.
Storage systems might be considered the holy grail of data capture. Storage arrays normally host terabytes of data, the company’s databases, and other critical data that keeps many technology-driven companies alive and healthy. To launch an attack and successfully destroy, overwhelm, or subvert any of this infrastructure is an immediate win.
The recommendations are similar to what I cover for networks and systems:
- Access (and follow) vendors’ online hardening guides.
Make sure you have a working copy of your data in a redundant and resilient setup. This is where disaster recovery (DR) and business continuity planning (BCP) become a pen tester’s main suggestion to a client.
 If you have the important data backed up and available, any issues to it can be solved.
If you have the important data backed up and available, any issues to it can be solved.- Use some of the same recommendations given for network and systems. To help you secure access against it, apply access control correctly, for example, and monitor (audited) for threats.
- Encrypt data. Encryption of data both in transit and at rest can protect any data on the storage system, going to it or being requested.
Mobile
Mobile systems are increasingly hard to secure. Pen testing them is often more critical than pen testing an internal core network secured by firewalls. As I mention with client-side attack secure recommendations, earlier in this chapter, mobile fits directly into this model where all work and functions are performed on them are transported from place to place in an always-on configuration.
Mobile is normally secured by local biometric access or a password/passcode. Corporate devices face a current challenge with end users wanting to own and operate their own personal devices to access corporate resources.
Recommendations include:
- Divide the access between personal and work use with a VPN, or other secure form of app that allows your corporate resources to remain secure. It also helps to prevent the spread of malware.
Find out what is being used on employees’ devices and attempt to secure them with protective software and encryption.
Mobile pen testing can be as follows: You send an email to an end user who opens it on the Android phone (or jailbroken iPhone). This allows for an app to be installed, much like a Trojan horse. Access can be provided and from there you can launch attacks. If you know what apps are there, you secure them accordingly.
- Use a mobile management enterprise solution if your company can afford one to manage this as well.
Cloud
Assessing cloud and other forms of outsources services that connect to your corporate company can be a true challenge. The truth is, though, it’s not much different than other connectivity you may have, such as ISP connections and disaster recovery locations where you may host systems.
General Security Recommendations: All Systems
From ports and unused services to firewalls and encryption (and more), this section covers several recommendations that don’t fall specifically under networks and systems. Though general in nature, they’re still important, of course, and so I take them one by one.
Ports
One of the most common items to appear on pen test reports is ports. Closing unnecessary server ports helps if you can’t change them or readjust them. The IANA registry shows the list of commonly used and assigned ports:
https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml
It’s important to be aware of ports and how they’re used and configured. Ports are commonly how attackers and pen test access remote systems through socket connection established by a port and IP address set. The example in Figure 12-4 shows one of the ways you can secure a system by changing the default port. Another consideration is, if Server A wanted to access web services on Server B, it would have to do so by specifying the port by number and look like: 10.1.1.11:8080.
Unneeded services
Remove unneeded services from systems and audit them periodically for use. What this means is, if you find that you have the FTP service running on most of your servers but FTP is only really needed on two of them, remove the unneeded ones.
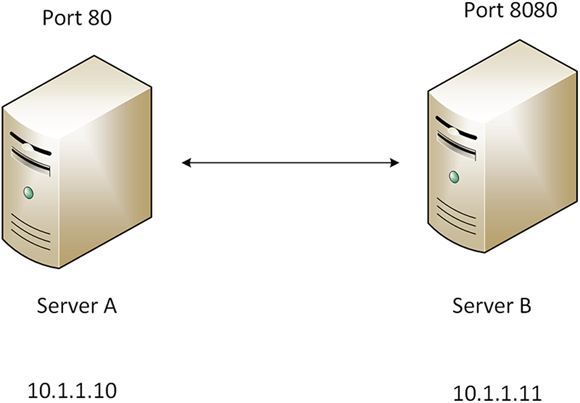
FIGURE 12-4: Changing a default port to help secure a system.
A pen test and thus the pen test report can help guide you into removing these items. Often tools such as Nmap show you what ports are running and commonly map to which services are in use. This highlights what you can shut off.
A patch schedule
Make sure that every single piece of technology in your organization is on a patch program where everything is reviewed, tested, and applied as required on a monthly basis.
Firewalls
Installing a firewall is one of the most common things that organizations do to protect their demarcation point and control access to hosts that the company may manage in their DMZ. Figure 12-5 shows how monitoring access in and out of the firewall can be helpful to an organization trying to protect their assets. You can then audit the firewall log to see what connections were attempting to gain access to a specific server. Use that information to look for possible attacks or breaches.
AV software
Today, the only thing more important than using a firewall is to make sure all your devices use an active AV program such as the one shown in Figure 12-6. AV is one of the best ways to protect endpoints, client-side devices, and mobile from being flooded with problematic malware.
FIGURE 12-5: Using a firewall allows you to monitor access in and out.
FIGURE 12-6: Antivirus software is still an effective way to protect devices from attack.
Sharing resources
Another common recommendation is to disable services by blocking ports or disable sharing of resources that are not needed within the operating system you’re hardening. For example, with Windows (and some Linux distributions), you can use SMB or SAMBA and share resources such as folder, printers, and so on. One of the ways malware propagates through a network from system to system is by riding these kinds of protocols.
In Figure 12-7, Nessus found SMB in use on the network and is recommending that you either shut it down (if possible) or configure much needed patches that disallow remote code execution.
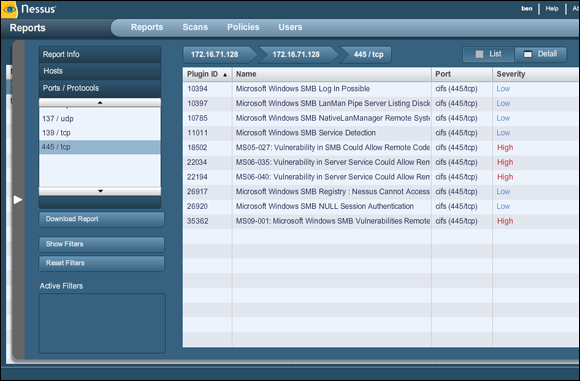
FIGURE 12-7: Finding SMB issues on the network with Nessus.
Encryption
Using encryption allows you to not worry about many of the common attacks such as eavesdropping, hijacking, data theft, and packet sniffing and capture. By using protocols, such as SSH, IPsec, and SSL/TLS, you can prevent many attacks through encryption, as shown in Figure 12-8.

FIGURE 12-8: Use encryption such as SSL.
More Recommendations
This section gives you a quick snapshot of other important recommendations that didn’t fit elsewhere in the chapter.
Segmentation and virtualization
One really important one is a different view on segmentation. You should always put more critical systems into separate parts of the network whenever possible. This doesn’t just mean network components; it also means the systems that connect to your network such as servers. This can be more easily accomplished with virtualized servers (or virtual machines) within a virtualized host.
Also consider virtualization. With the use of VMware and other technologies you can also create virtual machines (VMs) that allows you to create separate logical networks instead of physical ones, much like VLANs.
Access control
Gaining access is one of the biggest targets for hackers (and pen testers), which makes access control where you can potentially thwart incoming attacks. Some of the recommendations you can make here is to
- Use a tool for AAA, such as TACACS+ or RADIUS, which provides centralized logging and control of access.
- Use access control lists (ACLs). An ACL is a guideline that your system must follow to permit access. If a deny statement is within the list, the system blocks entry.
- Use firewalls and firewall rules. Firewalls can also monitor and log information for later review, or send alerts based on thresholds or alarms that are set to be tripped for alerting purposes. Firewall rules (very similar to ACLs) are statements that a system reviews when entry is requested and if a deny statement is used, it blocks entry based on specific criteria such as a port, IP address, hostname, or other form of identifier. The firewall can also be intelligent in that when it sees something out of the ordinary, it can send an alert to the administrator. For example if a port known for hacking is accessed on a system very rarely used, it may trigger the firewall to send an alert.
- Enforce secure password or credential usage. A set of credentials is a username and password combo, unless you’re using multifactor authentication mechanisms, biometrics, or other form of access and identity control.
- Have multifactor authentication (MFA) in use. MFA increases the difficulty of password guessing or cracking. It’s especially true with the extra factor added is something like a one-time password (or OTP) that needs to be generated and used on demand.
- Encourage strong passwords. Another consideration is to have a password policy in place for your organization that disallows the use of easy to guess passwords and makes the end users change them in a specified amount of time.
- Disable default, unnamed, or generic accounts. You want to ensure that credential sets are tied to real users who can be audited. Any default accounts can be set up as a trap (for example, a honeypot) and audited so that if you do see activity on default (and honeypot) accounts, you know someone is probing the network or attempting to.
Backups
Creating and keeping backups is vital to the health of an organization. You can’t continue operations if you lose critical data or systems with no way to access them after a disaster.
Make no mistake, a breach by hackers is in fact a disaster and your recovery or continuity policy should follow your incident response plan.
Securing logs
As a pen tester, logs are your source of most of the information you collect and a giant source for information you want to populate in your report. One of the ways hackers conduct APTs is by deleting or updating logs. By swapping, changing, moving, deleting, or altering logs, you have false information or no information about breaches.
Figure 12-9 shows a simple log from Solarwinds called Kiwi that allows me to have a router or switch send their syslog information to a separate server that I can access and review. This way, if a router or other device is rebooted, or a log is deleted or changed, I can get a copy of the log saved off the device itself. Securing logs is a very good recommendation that allows organizations a fighting chance to review and monitor activity on devices that are possibly at risk.
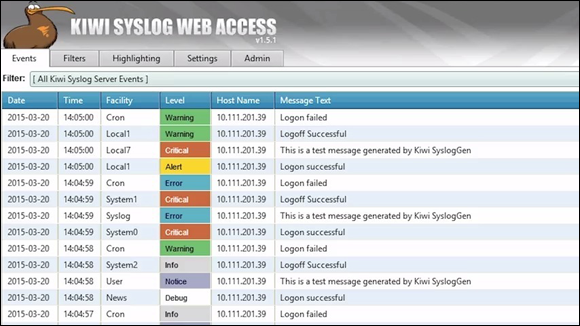
FIGURE 12-9: Saving copies of logs in case a hacker interferes.
Awareness and social engineering
I’ve said it before, but I have to say it again: The weakest link is the non-technology assets such as your line workers, desktop users, and mobile workforce. They’re human, and there’s really no way to make 100 percent certain everyone will work diligently to always consider security. This is why awareness training is a must and why it’s an ongoing effort.
- Policies: You’ll want to restrict things such as using your personal mobile device for corporate business and your corporate devices for personal business.
Consistent auditing: This can help to provide feedback on programs and how end users feel about security and their ability to withstand an attack. By pen testing them with a phishing email, you can see whether they click it and give you access. If this happens, you want to see how many end users did this through an audit and use that metric as the basis for getting more training for your workforce.
 People and skills are important to consider. The more your workforce knows about security, the more likely they will suspect an attack and do something about it if they recognize it.
People and skills are important to consider. The more your workforce knows about security, the more likely they will suspect an attack and do something about it if they recognize it.Separation of duties and a need-to-know environment: Administrators only have access to what they need, not to the entire domain in Windows (as an example). Maybe every network engineer does not need access to the core. Maybe the storage administrator should request higher level access as needed and required.
 By separating these, you can protect your assets with a higher security posture. It also helps to alleviate mistakes.
By separating these, you can protect your assets with a higher security posture. It also helps to alleviate mistakes.

 If you’re asked for recommendations, options, or solutions on security threats in an organization post pen test, be sure you’re confident in your ability to do so. Your strengths may lie in pen testing but may not rely on applying security solutions in an enterprise. For example, some solutions might require programming to fix, and maybe you aren’t a programmer. Be honest with your abilities and make sure you’re honest with the project team. This is when other consultants or experts may be brought in to help apply the security solutions needed when others can’t apply them. The role of the pen tester is to penetration test and ethically hack to find weaknesses. Another person (or team) might be responsible for securing the weaknesses. Whatever part you play in this process, you can learn from it and it will make you a better pen tester over time.
If you’re asked for recommendations, options, or solutions on security threats in an organization post pen test, be sure you’re confident in your ability to do so. Your strengths may lie in pen testing but may not rely on applying security solutions in an enterprise. For example, some solutions might require programming to fix, and maybe you aren’t a programmer. Be honest with your abilities and make sure you’re honest with the project team. This is when other consultants or experts may be brought in to help apply the security solutions needed when others can’t apply them. The role of the pen tester is to penetration test and ethically hack to find weaknesses. Another person (or team) might be responsible for securing the weaknesses. Whatever part you play in this process, you can learn from it and it will make you a better pen tester over time.