Chapter 7
Destroy (Malware)
IN THIS CHAPTER
![]() Stopping destroy attacks with antivirus software
Stopping destroy attacks with antivirus software
![]() Using Nessus to track down malware in your enterprise
Using Nessus to track down malware in your enterprise
![]() Exploring various types of malware: worms, spyware, Trojan horses, and more
Exploring various types of malware: worms, spyware, Trojan horses, and more
![]() Staying ahead of ransomware
Staying ahead of ransomware
The next series of attacks I cover revolves around the destruction of targets or the destruction of the resources provided by targets. The previous chapters in this part cover attacks that are meant to confuse, obfuscate, distract, overwhelm, or disrupt, and maybe even remain completely undetected. But in this chapter, I cover the types of attacks meant to simply destroy a company’s assets for the purpose of revenge, leverage, gain, or in some cases, for the challenge (or for fun).
Destroy attacks can cost a company a lot of time and money to recover from. You can recover from a destroy attack if you’re running a backup program, but your real loss is time. The time it takes to recover the system, data, or resource can be lengthy. If you’re running a disaster recovery solution, you could try to move your clients over to another working system, but not all companies have this up and running or have it running in a confident state.
In this chapter I focus on what toolkit tools you need to identify when you’re experiencing a destroy type attack, and also whether your systems are vulnerable to that kind of attack.
Toolkit Fundamentals
In this section, I show you the tools for conducting a pen test to simulate malware attacks, which are attacks that cause destruction.
Antivirus software and other tools
Tools such as Kali, Nessus (which I discuss further in the following section), Wireshark, and others can be used to scan for vulnerabilities in your systems, so that you can mitigate the risks and the attacks.
Destruction attacks — like all attacks — are hard to identify, so don’t limit yourself to your pen test toolkit. You might also want to monitor antivirus (AV) management consoles, firewall logs, routers in the network (to see inbound and outbound traffic patterns), and other tools such as Burp Suite (see Chapter 5) and Metasploit (see Chapter 4).
Nessus
I discuss Nessus in previous chapters, but the focus in this chapter is using it to scan for vulnerabilities that find:
- Issues with outdated virus software
- Malware in the enterprise
- Other threats that can destroy assets and resources in your network and systems
Figure 7-1 shows different types of scans available by default in Nessus. For example, you might want to run a patch audit to see what systems are vulnerable to being manipulated by exposed code that needs to be fixed by the vendor.
Exposed code refers to software (firmware, operating systems, applications, apps, and so on) that exist that isn’t secure when released. Because of this fact, the code needs to be updated, fixed, or even replaced from time to time.

FIGURE 7-1: Nessus offers various scan types for pen testing destroy attacks.
Normal procedure for most enterprises is to have a patch window or patch cycle (which perhaps opens monthly) to fix all systems impacted by known issues. The patch window can take priority status for issues — identified during pen testing — that point to a known bug or security threat that needs to be patched immediately.
You would run a scan from Nessus that scans a subnet and identifies all hosts that could be vulnerable to known threats. Using Nessus in this fashion (see Figure 7-2) helps you generate a report showing hosts that have malware and or the possibility of being threatened because of known vulnerabilities the tool identifies.
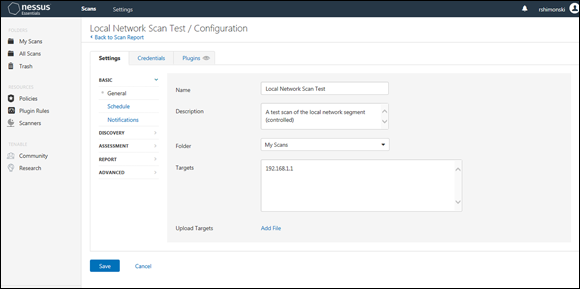
FIGURE 7-2: Looking for hosts that are vulnerable to known threats.
A pen tester could use these types of ethical hacks and attacks to penetrate systems that are exploitable or vulnerable. When conducting these attacks, you need to make sure that you understand (and report to those you’re doing the test for) that you could cause irreversible damage that may only be fixable by restoration or backup.
You could also simulate the attack to probe in a way that you could see whether unpatched systems exploitable by malware are vulnerable.
The attack vector for your hacker can be internal and external. Figure 7-3 shows a typical external vector attack in which the goal would be to inject and destroy a host or database:
- The database is the target.
- The goal of the attacker is to launch an attack penetrating the firewall in a web application and injecting a script.
- The injected script systematically deletes tables from the database host it’s connected to in the backend.

FIGURE 7-3: A typical external vector attack with the goal of destroying a database.
This example shows a very simple design in which the attacker destroys assets using a script that could have been delivered in a variety of ways:
- From a Trojan horse application inserted on a host inside the network.
- Sent in an email with an attached virus (malware) that spreads perhaps like a worm that caused attacks against the database that could corrupt it.
- Someone walking into the data center, getting on a console, and deleting files.
- Conducted remotely from a trusted (but potentially disgruntled) user from the safety of their home over VPN.
Malware
Malware (or malicious software) is the most common form of vulnerability faced by almost every single organization that uses technology today. This is a global issue and it doesn’t discriminate in any way. If you’re connected to a network and use its resources, it’s likely you have at one time in your life come across some form of malware — be it viruses, worms, or Trojan horses.
Types of malware include but are not limited to:
- Virus: A simple program created to replicate itself to other computers, systems, and programs when it’s executed. The most common theme with a virus is that it needs to be executed to be harmful, so it’s usually followed by some form of trickery to get someone to execute it. This trickery can be in the form of phishing, social engineering, click baiting, and so on.
- Worm: A worm is similar to a virus and a bad form of malware in that it is self-replicating. The worm uses holes in your security that it can piggyback on to replicate.
Trojan horse: In ancient Greek mythology, the Trojan horse was used to trick those who thought it to be a gift to accept it and bring it into their fortified protected area (through their gates), unknowing that within it was a great many soldiers ready to do battle. This is why this piece of malware is called a Trojan horse. It misleads you into thinking it is something you want or need, but in the background contains a piece of malware causes you harm.
A Trojan horse (sometimes just simply referred to as a Trojan) is devastating to those who install it because it essentially can spy on you (capture your passwords/credentials), activate and use your machine (to launch attacks), and other things, too, such as leave a backdoor open to your enterprise systems from the host it has occupied.
- Spyware: Spyware does exactly what it says; it spies on you and your activities while lying dormant on your system. It can collect information and send it to those who might find value in the collected data sent by the malware.
- Zero day: A zero day is simply a piece of code that has an exploit that has yet to be identified. It’s ripe for the picking by hackers if they find it before you do. It’s one of the hardest attacks to prevent. Zero days can come from failed coding by a vendor or a purposeful code exploit or malware. Either way — the zero day event is because no one knows about it yet.
- Logic bomb: The logic bomb is malware code set to activate based on a set of criteria taking place. For example, as the payload, a bomb could be to delete a bunch of files on your local computer at a certain time, a certain key stroke, or a certain click, which would be the logic that activates it.
Ransomware: Covered in more detail in the next section, this type of malware happens to be one of the most devastating. It feels worse than the others because you’re left to interact with the hacker — who has caused you this problem and who is demanding a ransom for the release of your property.
Ransomware is a destroy attack with a timer. If you fail to pay the ransom, the encrypted data is held hostage forever and you can’t use it thus leaving it in a devastated state. Anyone who doesn’t have reliable and timely backups is left helpless.
Ransomware
Ransomware is its own brand of evil. Those who create it and distribute it are some of the worst of the bunch because this is a script kiddie paradise. The elite hackers who created the tool in the first place have left a tool like WannaCry (one of the most common ransomware attacks) to those who can use it to extort good people out of money. There are others, like Petya. Regardless of how many variants exist, they all do the same basic function: Encrypt your data so you’re unable to use it, and then make you pay a large amount of money to decrypt it.
Figure 7-4 shows an example of WannaCry and how the attack is conducted. The end user in your organization could have visited a website with the tool on it and downloaded it thinking it was something they needed. They get a nasty surprise when they find out what they actually downloaded: an encryption tool on their system that can conduct an attack when activated.
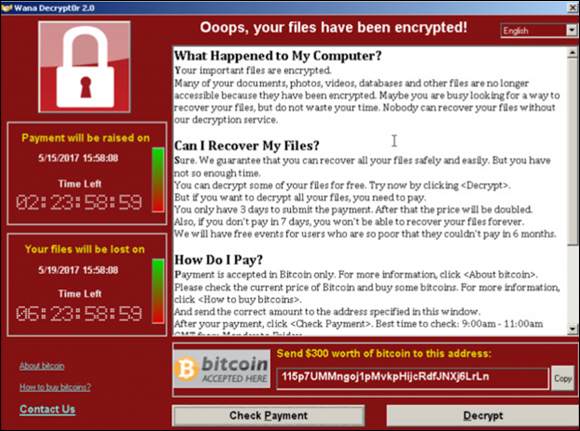
FIGURE 7-4: An example of a ransomware attack.
The question to ask yourself is: How do I test systems and infrastructure to make sure I am secure against malware attacks?
The answer is: Conduct assessments with pen test tools and other tools appropriate to the company’s enterprise management and monitoring system, identify if any issues exist, determine where those issues could cause problems, and finally mitigate the risk before the hacks and attacks take place in the first place.
This is similar to what you would do to protect against any type of attack, but in the case of malware, I recommend first putting on the security analyst hat. You must make sure your company has a great enterprise management and monitoring tool such as antivirus (AV) software deployed across the enterprise to protect all endpoints from attack. Endpoints can be any device such as a laptop, computer, mobile device, or tablet.
Figure 7-5 shows an example of the most commonly used tool to prevent malware attacks, which is endpoint protection through an AV tool. Although this is the most common and helpful, it doesn’t completely solve the problem.
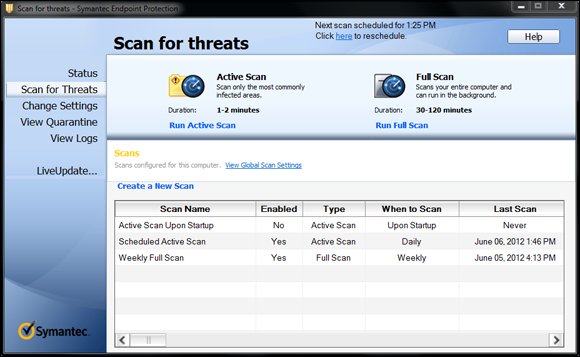
FIGURE 7-5: An example of AV endpoint protection.
Additionally, you must do the following:
- Ensure the AV tool is managed and maintained. This means that the tool itself is updated with all the latest scanning information required to stay on top of the latest threats.
- Secure the endpoints. Every endpoint in your enterprise that runs some form of software (or firmware) is susceptible to malware. Pen testing can come to the rescue, of course, by helping you to identify all the endpoints and which are vulnerable.
By running the tools I cover in this chapter (and in Chapter 8, where I cover subvert attacks, another attack against AV), you’ll notice that simple assessments identify many of your systems as susceptible to attack. Why? Because hackers work night and day to uncover holes in the software itself and write code attacks to expose the holes they find. The vendors then write code (hotfixes, service packs, and patches) for you to download and install on the machine to protect it. Running a pen test will tell you that 15 percent of your workstations aren’t running the latest patches. You can then download and install them to protect your systems.
Running pen tests, using good AV software, finding risks and fixing them all provides a good level of protection applied to your enterprise. But you can’t consider this to be how you fully protect against malware. You must remain diligent in your testing because there is a constant effort underway to undermine security to get this bad code through your door. Social engineering is the best way for hackers to get in and get someone to click something and download it. You can pen test this by educating your end users. If an educated end user knows not to click something, then they can avoid activating malware. Does it stop all of it? No, but it will limit attacks significantly.
Other Types of Destroy Attacks
Other destroy attacks aren’t very fancy but just as brutal as the code-based ones. Although they may not have a fancy name, many manual attacks can destroy assets all the same. In these attacks, the vectors are just as difficult to determine as the malware-based ones (which can come from anywhere — email, weblink, and so on). Attacks that thwart physical access, the vector is as simple as a person leaving their computer open, which means someone else can sit down and go to work.
The damage an attacker can do would essentially be sabotage, which can take various forms, to cause a destroy-based attack:
- Mass deletion of files
- The insertion of a virus or malware
- The intentional corruption of data
- The insertion of a payload
- The changing of settings or injecting errors
- An injection overload to corrupt
Hackers look for these attacks because they are easy, require far less time and resources, and are the ones that leave little to no trail other than what security cameras might pick up.

 Destruction of resources can always be fixed if you have an active backup. If the source data/code is destroyed or if some data is lost in transit, and you don’t have a backup, it will be lost forever. Make sure to back up data, systems, software, firmware, and access to all of this, and so on. If virtual snapshots of data/systems and VM (virtual machine) hosts are all being taken and performed, you will have a great path to restoring your service very quickly if you need to.
Destruction of resources can always be fixed if you have an active backup. If the source data/code is destroyed or if some data is lost in transit, and you don’t have a backup, it will be lost forever. Make sure to back up data, systems, software, firmware, and access to all of this, and so on. If virtual snapshots of data/systems and VM (virtual machine) hosts are all being taken and performed, you will have a great path to restoring your service very quickly if you need to. By looking at NAC (network access control) software from vendors such as Forescout, you will have a better chance at finding, exposing, and protecting against destroy-style attacks. NAC denies (and quarantines) systems that come online in your network with any malware present or not meeting the expectations of the policies set forth by the administrators. They are placed on a protected network segment and addressed (possibly fixed or repaired) prior to being allowed to participate on the network.
By looking at NAC (network access control) software from vendors such as Forescout, you will have a better chance at finding, exposing, and protecting against destroy-style attacks. NAC denies (and quarantines) systems that come online in your network with any malware present or not meeting the expectations of the policies set forth by the administrators. They are placed on a protected network segment and addressed (possibly fixed or repaired) prior to being allowed to participate on the network.