Overview
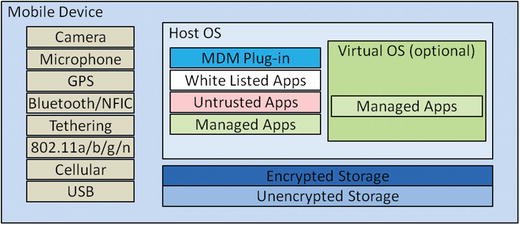
- The graphic depicts functional architecture of typical mobile devices and Bring Your Own Devices (BYODs).
- These devices impact how enterprises think about their IT.
- With multiprocessing, graphical user interface, and gigabytes of memory at our fingertips 24 hours a day, the face of IT is changing almost daily.
- These devices come in all shapes and sizes, such as notebooks, tablets, and cellular phones.
- This personal computing power arrives at a time enterprises are moving services onto the Internet and computing into the cloud.

- Frequently, personal devices are as good or better than those purchased or issued by the enterprise.
- At the same time, many people have one or more computing devices at home and want to use those devices for work.
- Enterprises need to embrace the fact that their data is going to be accessed from such devices.
- Internet-savvy employees want to use their latest and greatest devices.
- Organizations want employees to always be connected and able to be productive at home and on the road.
- Cost of equipping employees with the latest technology rapidly becomes prohibitive.
- Given that mobile devices and BYODs are here to stay, it is important to figure out how to protect enterprise data in the face of this reality.
- This chapter describes
- mobile and BYOD security challenges; and
- how an enterprise cybersecurity program should manage protection of these devices.
Topics
- Introducing Mobile and BYOD
- Challenges with Mobile and BYOD
- Legal agreements for data protection
- Personal use and personal data
- The mobile platform
- Sensors and location awareness
- Always-on and always-connected
- Multifactor authentication
- Mobile device management
- Enterprise Cybersecurity for Mobile and BYOD by Functional Area
Introducing Mobile and BYOD
- For the most part, mobile and BYOD are different types of endpoint computing devices that are not owned or managed by the enterprise.
- The National Institute of Standards and Technology (NIST) defines a mobile device as having the following characteristics :
- A small form factor
- At least one wireless network surface
- An operating system that is “not a full-fledged desktop or laptop operating system”
- Applications available through multiple methods
- Mobile devices may have characteristics that may include one or more of the following characteristics :
- Wireless personal area network, such as Bluetooth
- Wireless interfaces for voice communication, such as cellular
- Global positioning system for location
- One or more cameras or video recording devices
- Removable media storage
- From a cybersecurity perspective, mobile devices present the following concerns:
- Lack of physical security controls
- Use of untrusted mobile devices, networks, applications, and content
- Interaction with other systems
- Use of location services
- To address these mobile concerns, the US Federal CIO Council created a detailed mobile security reference architecture that describes strategies for managing such protections in the federal computing environment.
- The graphic depicts the Council’s mobile security reference architecture that accounts for the mobile and BYOD security challenges in great detail.

- If an enterprise already allows access to its resources from home computers, through Internet-connected services, cloud services, or a virtual private network (VPN), then the enterprise is already facing personal device challenges.
- Much of what people can do with mobile computing is exactly the same as what they can do with personal computers.
- Challenges of protecting the enterprise data on these devices are just as great as if the devices were within the enterprise.
- Mobile computing only makes these challenges more distressing because the data is residing on devices that are
- everywhere;
- dropped;
- stolen; and
- misplaced.
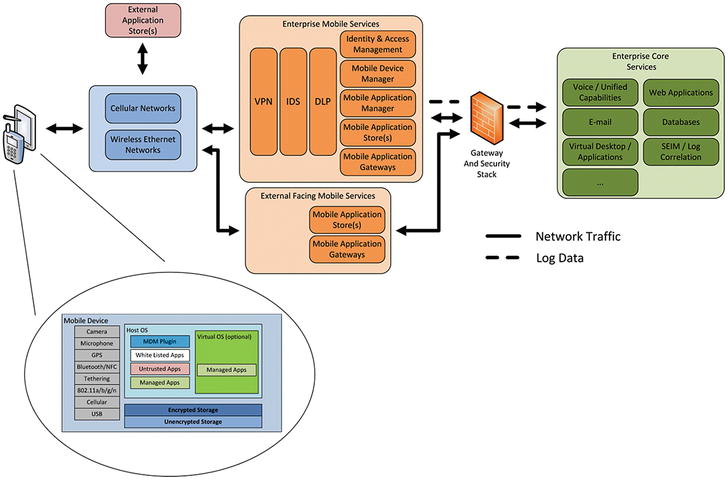
- The Federal CIO Council mobile security conceptual architecture shows the components of common mobile devices and who they might be managed by and interact with.
Challenges with Mobile and BYOD
Context
- Mobile devices and BYOD are endpoints, and there is no such thing as “perfect” endpoint security.
- An enterprise can reduce the probability that any given endpoint, server, or device gets compromised while increasing the probability that the enterprise will detect the compromised endpoint.
- Personally owned mobile and BYOD devices are not owned by the enterprise, thus increasing the probability of such devices getting compromised.
- This section describes the following factors to be considered when an enterprise plans out its mobile and BYOD strategy:
- Legal agreements for data protection
- Personal use and personal data
- The mobile platform
- Sensors and location awareness
- Always-on and always-connected
- Multifactor authentication
- Mobile device management
Legal Agreement for Data Protection
- One of the first data protection factors to consider is a legal one.
- What happens when enterprise data is stored on devices that do not belong to the enterprise?
- The enterprise needs to consider this question, not only for mobile and BYOD devices, but also in terms of home personal computers, personally owned thumb drives, portable hard drives, and recordable media such as CDs or DVDs.
- For the most part, when enterprise data is copied to non-enterprise devices, data protection agreements need to be in place with employees and contractors.
- Such agreements may be hard to enforce in practice, but are needed for legal standing to protect the data after it is copied from organizational computers.
- Agreements help the enterprise deploy data protection technologies, such as remote wipe, onto non-enterprise devices.
Personal Use and Personal Data
- Mobile and BYOD devices are going to be used for personal and business use.
- Consequently, an enterprise cannot treat them as if they belong only to the organization.
- If an enterprise deploys data protection technology on the devices, then the enterprise needs to consider potential impacts on stored personal data.
- For the most part, such deployment tends to work OK in practice.
- If a systems administrator accidently wipes an organizational device, the organization is liable for the damage and ultimately bears the cost of it.
- On the other hand, what if the action accidentally deletes someone’s personal information that is irreplaceable? What is the liability here?
- These are some of the factors that need to be considered before accidents occur so everyone’s expectations are managed.
The Mobile Platform
Strength
- Operating systems are generally designed for users not to have “root” access that would allow them to customize the operating system itself.
- Restriction makes these platforms more resistant to many types of attacks.
Challenge
- If the operating system privilege protection is defeated or if users undermine the device by “rooting” their phone, there is not as much recourse to protect the device as there is with more mature desktop operating systems.
Strength
- Mobile device vulnerabilities reflect poorly on carriers who sell these devices, so they are motived to protect devices well.
Challenge
- Carriers “turn over” mobile devices at a rapid rate and seldom provide patches or updates after the first year or so.
Strength
- Mobile devices use “App Stores” that screen applications to ensure minimal level of security protection and non-malicious behavior.
Challenge
- “App Stores” can lull users into a false sense of security.Put all of these factors together and mobile as a platform is fundamentally neither more nor less secure than the personal computers that we are all familiar with. … It’s just different …
Sensors and Location Awareness
- A significant distinction between mobile devices and desktop computing is the multitude of sensors in most mobile smartphone devices.
- Sensors include light sensors, orientation sensors, fingerprint scanners, cameras, microphones, and GPS receivers.
- It is not easy to tell or control when sensors are operating.
- It is not easy to tell or control what sensor data is being collected.
- Sensors might gain unintended access to proprietary information.
- Enterprises may not want employees to carry devices due to the possibility of sensor data being recorded—either deliberately or accidentally.
- Such data may be used against the enterprise or its employees.
- Sensors may be extremely useful; however, protecting them from potential misuse is extremely difficult.
Always-On and Always-Connected
- As opposed to PCs and desktops , many mobile devices have cellular radios that enable them to connect from almost anywhere all the time.
- Connectivity poses cybersecurity challenges, so enterprises should consider them always-on and always-connected unless the radios have been explicitly turned off using “airplane mode” or a similar feature.
- A robust mobile device sensor suite is able to transmit constantly.
- What it sees and where it is to anyone who wants to know
- Known without the device owner’s knowledge or consent
- A compromised mobile device becomes a rogue device via a public network that is always watching and listening, and could be reporting to anyone at any time.
- Since the mobile device is connected through a public network, it is not protected by network security capabilities or controls.
Multi-Factor Authentication
- Challenge
- Many strong authentication technologies (for exmaple, smart cards and USB tokens) are not directly compatible with mobile devices.
- Multifactor authentication strategies must be expanded to accommodate mobile endpoints.
- The enterprise can consider alternative form factors, such as software certificates and one-time-password (OTP) tokens.
- Challenge
- Two-factor authentication technologies often use the mobile device as the second factor.
- The enterprise needs to consider how the mobile device, being both the security token and the endpoint, affects the overall multifactor authentication.
- Frequently, if the mobile device is compromised, then the multifactor authentication will be defeated as well.
- The enterprise may need to consider alternative forms of strong authentication or compensating in other ways, such as anomaly detection or adaptive authentication.
Mobile Device Management (MDM)
- MDM software suites provide management of mobile devices and enterprise data stored on them.
- Capabilities include the following:
- Device inventory and accounting
- Malware scanning and detection
- Encrypted storage of enterprise data on device
- Protected “sandbox” for enterprise applications to run
- Secure application stores for enterprise-approved software
- Monitoring of device sensor use, including camera, microphone, and GPS
- Remote “wipe” capability if the device is lost or stolen
- An enterprise often wants theses capabilities on all its endpoints and computers, not just its mobile devices.
- For personal devices , employees may not be willing to allow their devices to be managed in this way, regardless of the potential benefits.
Enterprise Cybersecurity for Mobile and BYOD
Systems Administration
- Systems administration should be performed from enterprise-owned assets.
- Potential benefits of allowing systems administrators to perform their duties from mobile devices do not outweigh the security risks.
- If enterprise allows systems administration from unmanaged mobile or BYOD devices, it should consider the following mitigations:
- Strong authentication for Sysadmin via tokens separate from the mobile devices they use for administration
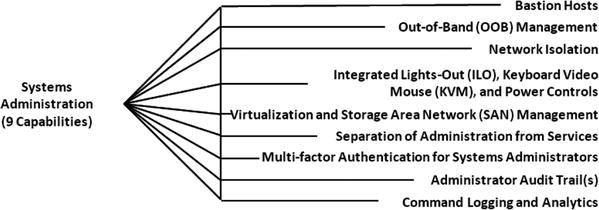
- Device recognition and fingerprinting for mobile and BYOD endpoints authorized for systems administration
- Virtual Private Networking connections for Sysadmin activities—enterprise can monitor devices
- Increased logging and auditing of Sysadmin activities for rogue activity
- Network-level anomaly detection to catch Sysadmin connections from unauthorized hosts or patterns and tools known to be malicious
Network Security
- Mobile and BYOD devices generally get their connectivity from outside the enterprise.
- Such devices are not protected by the enterprise’s network “perimeter” when accessing the Internet.
- If the devices are compromised and interacting with external command-and-control networks or botnets, the enterprise will not know.
- However, an enterprise’s network will be able to see device traffic when the traffic comes in from the Internet.
- Enterprise can look for evidence of compromise (for example, unusual connection patterns from unexpected locations).
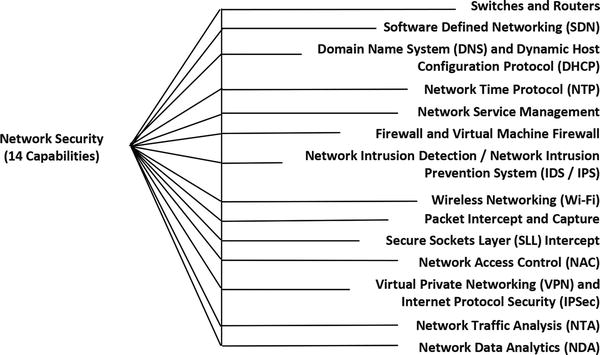
- For more privileged activities, an enterprise may want to require such devices to create a Virtual Private Network (VPN) into the enterprise network.
- Devices are treated as if they are inside of the network.
- Enterprise can see all traffic in and out of devices.
- Enterprise network defenses can monitor device network activity for malicious patterns and command-and-control traffic.
Application Security
- For specific-use cases , an enterprise may be able to leverage application security capabilities to compensate for mobile and BYOD security challenges.
- Generally, application security technologies that protect consumer-facing systems can apply just as well to enterprise users on mobile and BYOD devices.
- Some of these application security techniques and capabilities can also be used on applications that would not normally be public-facing, such as e-mail or financial systems.
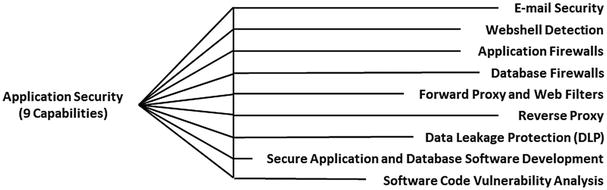
- When an enterprise considers allowing enterprise users to access these applications from unmanaged and unprotected endpoints, then available application security capabilities may be able to reduce the security risk.
- These systems can be protected from potentially anomalous activities by enterprise users on mobile or BYOD devices.
Endpoint, Server, and Device Security
- This functional area is the most impaired when users are on mobile or BYOD devices.
- With the exception of mobile device management (MDM) technologies, many enterprise tools are not applicable to personally owned computing devices.
- MDM can provide outstanding protection of enterprise apps and data while still allowing personal use of devices.
- Endpoint security software (anti-virus, firewall, and intrusion detection) may be licensed for BYOD devices.
- Remote access systems can enforce the presence of endpoint security software when machines connect to enterprise networks, reducing the probability of compromise to internal networks.

- Virtual desktops, thin clients, and “to-go” operating systems that boot from portable media provide secured, trusted endpoints for enterprise network connectivity.
- Don’t underestimate the power of policy.
- Specifies what activities and data can and cannot be performed on mobile and BYOD devices (for example, handling of removable media and encryption of data in transit or rest).
- Provides a legal basis for punitive actions when negligent behavior occurs.
Identity, Authentication, and Access Management
- Strong authentication protects accounts from being compromised even when privileged credentials are used from compromised endpoints or mobile devices.
- Even strong authentication cannot protect against session hijacking attacks where attackers wait for the users to authenticate using their credentials and then send commands through that authenticated session.
- Session hijacking can be very effective, particularly with applications such as electronic banking.

- In this functional area, the most useful protection is logging and detection.
- Enterprise logs authentication and activities and then reports this information to the user after the fact.
- Inappropriate logons and other activities can often be immediately recognized.
- Controlling access is effective by minimizing potential consequences of compromised endpoints and compromised credentials.
Data Protection and Cryptography
- This function has the most untapped potential with regard to securing personal computing devices used for enterprise purposes.
- In the future, secure elements on mobile and BYOD devices will store credit cards, payment information, and user identities in such a way that such information can be securely used over the Internet.
- Protection capabilities include the following:
- Trusted platform module (TPM) that stores device certificates to authenticate “trusted” BYOD devices
- Cryptographic tokens (smart cards or one-time-password generators) that provide strong, multifactor authentication, even from untrusted endpoints
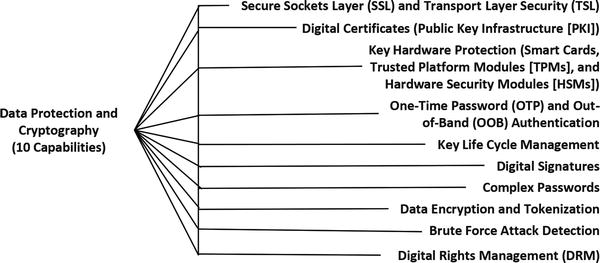
- Secure sockets layer (SSL) and transport layer security (TLS) protocols to protect from snooping when using untrusted public networks (cellular and Wi-Fi hotspots)
- This functional area is still immature, but it has tremendous potential for enterprise use of mobile and BYOD devices.
Monitoring, Vulnerability, and Patch Management
- An enterprise is not going to be able to monitor mobile or BYOD endpoints for signs of attack or intrusions.
- However, an enterprise can monitor the enterprise infrastructure for signs of compromised mobile, BYOD, or enterprise-managed endpoints.
- Endpoints will be compromised.
- Mobile and BYOD monitoring
- Internet-facing systems, including Virtual Private Network (VPN) connections, should have monitoring in place to detect unusual connection patterns.
- Internal networks should detect and identify unmanaged computing devices connecting to the network.
- Depending upon network sensitivity, such devices should be sent to guest networks or otherwise isolated from the most sensitive internal infrastructure.
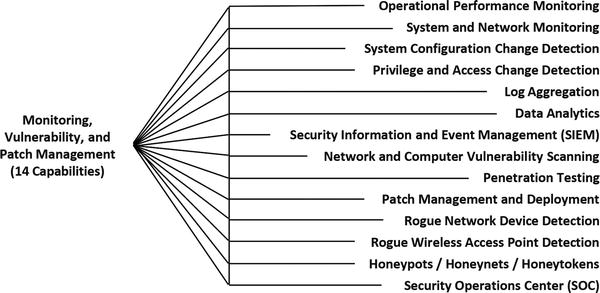
- Guest networks, even if isolated from corporate networks, should have the same level of intrusion and malware detection as any other network.
- An enterprise must make sure that when cybersecurity systems detect malware from guest, mobile, or BYOD devices, the corresponding response is fast enough to catch the devices before they leave the building.
High Availability, Disaster Recovery, and Physical Protection
- Mobile and BYOD devices frequently have little to no physical protection.
- The reality is these devices will be lost or compromised.
- Mission-critical data and processing should never reside on such devices.
- If such data does reside on the devices, strong contingency plans are needed.
- An enterprise should consider the physical security challenges for any type of personal computing device and use the same techniques and technologies to compensate for all the potential loss scenarios.
- Desktop computers are stolen from offices every now and then.
- Laptops are frequently lost or stolen.
- Personal computers and mobile devices are subject to the same situations.
- An enterprise should treat all of these possibilities as being on a continuum of physical protection challenges and use the same techniques and technologies for all these potential loss scenarios.
Incident Response
- The incident response process extends from the initial attack investigation, containment , remediation , and a post-incident IT environment with permanent security control enhancement to prevent a recurrence.
- When an enterprise introduces mobile and BYOD devices, some devices will be lost or stolen and potential data will be lost due to unencrypted media and devices.
- Enterprise incident response needs to include procedures to investigate anomalies stemming from mobile or BYOD access to corporate resources from internal networks or the Internet.

- Enterprise incident response needs to
- consider potential incident scenarios; and
- obtain adequate monitoring and logs.
- Most importantly , incident responders should be trained to understand where these devices are used and for what legitimate business purposes.
- Across the enterprise, everyone needs to be trained on mobile device security policy and safe usage considerations.
Asset Management and Supply Chain
- Since mobile and BYOD devices are frequently personally owned, they are not going to be easily accounted for in normal enterprise asset management and supply chain processes.
- To mitigate mobile and BYOD security risks,
- enterprise supplier managers should identify if there are some mobile and BYOD suppliers that are unacceptable for certain purposes;

- such information should be incorporated into policies and procedures and possibly be incorporated into and enforced by network and application controls; and
- when personal devices are trusted for higher levels of access (systems administrators), such devices should be certified for use and tracked as if they were enterprise devices.
Policy, Audit, E-Discovery, and Training
- This functional area is the most important for mobile and BYOD devices because it serves as the starting point for all other enterprise protection efforts, technical or otherwise.
- Enterprise mobile and BYOD policy should include the following:
- What business activities and data are
- Acceptable without any limitations
- Acceptable with limitations
- NOT acceptable
- Rules for protection of enterprise data stored on personal devices, at rest, in-transit, and on portable media such as thumb drives and recordable CDs or DVDs
- Guidance on investigation of known or suspected breaches of policy

- Consequences for violation of policies
- Guidance on training related to policies
- Policies should apply to everyone who may be handling such data and devices, including temporary employees, vendors, and contractors.
- When training is not practical for certain personnel (vendors and contractors), then policies can be incorporated into a “data protection agreement and end-user device policy.”
