Overview
- This chapter discusses several things related to auditing and assessing an enterprise’s cybersecurity program.
- How auditing is used to evaluate enterprise cybersecurity
- How audits should be used to drive the cybersecurity control design process
- How enterprise cybersecurity can be systematically evaluated using four levels of assessment detail
- How deficiency tracking is an integral component of any formal auditing or assessment process
- Audits and assessments can be conducted by internal or external assessors.
- Can be risk-based, threat-based, framework-based, or control-based
- Should be a formal part of a successful enterprise cybersecurity program
- Without periodic and objective assessment, the cybersecurity program will eventually suffer due to the atrophy that naturally occurs over time.
Topics
- Cybersecurity Auditing Methodology
- Cybersecurity Audit Types
- “Audit First” Design Methodology
- Enterprise Cybersecurity Assessments
- Audit Deficiency Management
Cybersecurity Auditing Methodology
Context
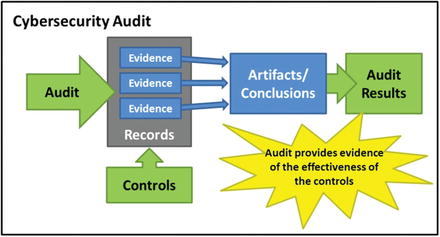
- What is a cybersecurity audit?“An audit is a process whereby a person checks an automated system or operational process to ensure that it is operating properly.”
- The graphic depicts a cybersecurity audit process.
- Analyzing the records generated by the system or process
- Collecting evidence of proper operation from those records
- Compiling evidence into artifacts to support the audit
- Compiling artifacts and conclusions into audit results
- Audit results document what was done during the audit and what was found from the audit, including identified deficiencies and their eventual remediation.
- Auditing Methodology Topics
- The Challenge of Proving Negatives
- Cybersecurity Audit Objectives
- Cybersecurity Audit Plans
- Audit Evidence Collection
- Audit Artifacts
- Audit Results
- Deficiency Tracking and Remediation
- Reporting and Records Retention
- The Challenge of Proving Negatives
- The goal of the auditor is to collect evidence that proves nothing bad or unexpected occurred during the audit period.
- Inductive reasoning suggests it is not possible to prove the absence of something.
- If malicious or negligent activity generates records , then those records can be searched for evidence of such malicious or negligent activity, or its absence.
- If auditors collect evidence of something not taking place, then such evidence gives a basis for reasonably concluding that it may not exist.
- How thorough does the checking need to be?
- Financial records may require checking every transaction because fraud may be only in a single record.
- Other records may only require spot-checking.
- Generally, audits collect evidence from available records to indicate the proper operation of security controls.
- Cybersecurity Audit Objectives
- The cybersecurity audit planning process starts with audit objectives that can be phrased in terms of a sentence.
- I want my audit to indicate that__is occurring; or
- I want my audit to indicate that__is NOT occurring.
- Example audit objectives:
- I want my audit to indicate that my web servers are functioning properly and serving up the correct pages.
- I want my audit to indicate that attackers are NOT abusing my systems administrator accounts.
- I want my audi t to indicate that my IT systems are compliant with Sarbanes-Oxley regulations.
- I want my audit to indicate that my confidential customer data is not being inappropriately accessed.
- Cybersecurity Audit Plans
- The graphic depicts a cybersecurity audit process that identifies what evidence is helpful to prove the audit objective.
- Desired evidence must be compared to what evidence is available from IT systems’ audit trails and logs, or manual processes’ records.
- The cybersecurity audit planning process includes the following activities:
- 1.Auditor analyzes the audit objective to understand what information is needed to satisfy the objective(s).
- 2.Auditor determines the desired evidence that supports the audit objective(s).
- 3.Auditor analyzes the available records to see what logs and information are available for analysis.
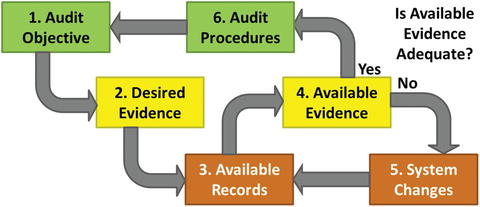
- 4.The available evidence comes from the available records. The auditor analyzes the available evidence to determine if it will be adequate for satisfying the audit objective(s).
- 5.If the available evidence is not adequate, system changes (automated or manual) may need to be made to increase or change the available logs and evidence.
- 6.Finally, the auditor constructs audit procedures to analyze the available evidence in order to satisfy the audit objective(s).
- 1.
- Audit Evidence Collection
- Specifies what records are to be analyzed
- Specifies the processes for analyzing the records
- Defines key information such as record sources, points of contact, and sample sizes
- Specifies sample sizes and statistical analysis methods to be used
- Audit Artifacts
- Answer the “because” question regarding the audit We believe systems administrator accounts are not being compromised BECAUSE we looked at systems administrator activity for 50% of the administrators over a two-week period and did not find any anomalies.
- Make up the data behind the second half of the above sentence (that is, after BECAUSE)
- Are copied out of logs and then stored with the audit and are subject to the data retention rules that apply to the rest of the audit
- Audit Results
- Are compiled together for reporting to management and must be actionable
- Identify what was audited and the findings, including deficiencies to be remediated
- Are summarized to management in terms of their business impact or level of concern
- Contain enough supporting information to be used by security practitioners to respond to and remediate the deficiencies
- Deficiency Tracking and Remediation
- May be outside the audit process , but should be formally tracked and reported to management
- May be deferred for specific deficiencies that are not cost-effective to remediate; such deficiencies should be treated as enterprise risks
- Reporting and Records Retention
- Should include the audit report and supporting artifacts
- Should comply with regulatory requirements per regulation or independent auditors, or retained like other business and financial records
- May not make sense to report on deficiency remediation as part of original audit since it can take weeks or months to complete after the original audit is completed and reported
- Regularly scheduled audits should brief deficiency remediation at the start of the next regularly scheduled audit
Cybersecurity Audit Types
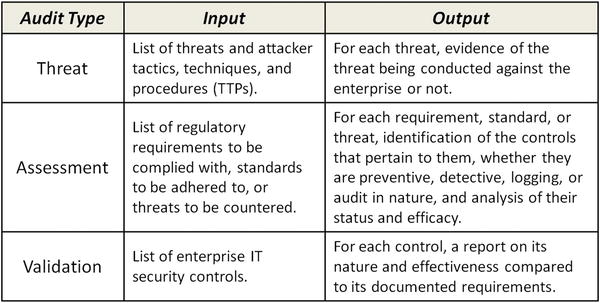
- The graphic depicts three common cybersecurity audit types:
- A threat audit (also known as hunting) analyzes cyberthreats and then audits for evidence that those threats are occurring in the IT environment.
- Looks for evidence of the threat targeting the confidentiality, integrity, or availability of enterprise’s IT systems and data
- Actively searches (hunts) for intruder and attacker activities using latest intelligence on intruder/attacker tactics, techniques, and procedures (TTP)
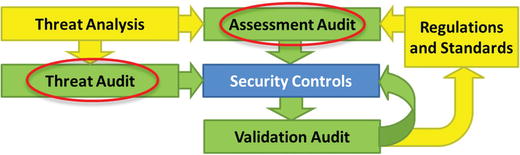
- An assessment audi t involves analyzing a set of requirements and assessing the cybersecurity controls pertaining to those requirements.
- Generally conducted against regulatory requirements, external standards, or industry frameworks, or in regard to defenses against specific cybersecurity threats
- Determines if controls are countering threats or complying with regulations or standards
- Identifies which controls are countering the threats or complying with regulations or standards
- Evaluates the effectiveness of those controls in satisfying requirement or countering the threat
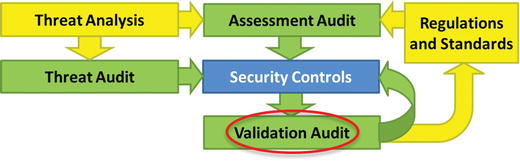
- A validation audit , unlike the other two audits, starts with the enterprise security controls and evaluates each control’s effectiveness compared to its design and documented requirements.
- Evaluates if those controls are actually performing effectively
- Is used to improve cybersecurity control operation and design
- Can also be mapped back to external regulations or standards to demonstrate compliance
- Cybersecurity audits should follow a consistent methodology starting with audit objectives and ending with an audit report.
- Defining cybersecurity audit methodology can be non-trivial, especially for a complex cybersecurity environment.
- This table summarizes the three types of cybersecurity audits in terms of their inputs and outputs.
- Different audit types can be combined into a single audit activity.
“Audit First” Design Methodology
Context
- When designing cybersecurity defenses, security practitioners may jump straight to preventive controls vs. audit, forensic, or detective controls.
- Preventive controls
- Can be cheap to operate
- Use exciting “new” technology
- Enable practitioners to make definitive statements about security
- We have blocked that behavior.
- They won’t be able to do that.
- Often introduce new vulnerabilities and dependencies on other IT systems that may be poorly understood
- Enterprise cybersecurity is NOT a point solution or collection of point solutions.
- Smart attackers target preventive control vulnerabilities and dependencies to defeat controls.
- A preventive-control-first approach results in a set of complex interdependencies that are often poorly understood, yet represent the foundation of the enterprise’s security.
- Unfortunately, enterprise cybersecurity can end up simply being security by obscurity until an attacker comes along and figures out how to bypass everything.
- Security practitioners can address this reality by thinking about preventive controls last instead of first.
- The graphic depicts the “Audit First” Design Methodology for thinking about preventive controls last, after considering other control types.

- Start with a threat analysis and then design controls to counter those threats.
- Simply stated, let security audits help drive the design of the enterprise’s cyberdefenses.
- Threat Analysis
- Used to determine the enterprise’s various security scopes1
- Identifies CIA threats to the enterprise’s data and IT systems in terms of threat impacts and indicators
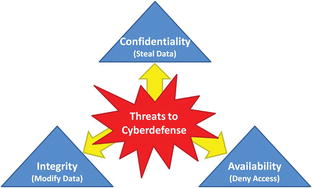
- Considers the threats that are most likely and most dangerous or a combination of both (Not every single possible threat with such consideration is overwhelming.)
- Prioritizes threats and risks just as an enterprise does with physical security considerations by addressing the greatest risks first
- Audit Controls
- After the threat analysis, the next step is to design threat audit controls that search for threat activities
- If an enterprise’s concern is loss of confidentiality, the security team might ask the following questions:
- How would the enterprise manually search the IT systems to identify that a confidentiality breach has occurred?
- What evident would the attacker leave?
- If an enterprise’s concern is loss of integrity, the team might ask:
- What evidence would be left when data was changed inappropriately?
- How would the enterprise investigate a data change incident to prove that data has been changed?
- If an enterprise’s concern is loss of availability, the team could ask:
- How would the enterprise differentiate an availability loss due to system failure from one caused by a malicious attack?
- Forensic Controls
- Forensic investigation involves analyzing logs, files, and sometimes program code to understand attacker activities and methods.
- When conducting a threat audit, an enterprise generally
- discovers little of the information needed to find confidentiality, integrity, or availability breaches against its systems;
- gains insight regarding the information it needs to collect to protect itself using, in part, forensic controls; and
- discovers the forensic controls effort may require significant upgrades to IT systems.
- Many real-world environments are deficient in logging the right data.
- It is important to resist the temptation to log everything; collect the information necessary to investigate likely attacks or support actual investigations.
- Data logging should extend across all of the 11 enterprise cybersecurity functional areas.
- Detective Controls
- Effective logging , when in place, can be used to find attacker activity and help design detective controls that alert on suspected attacker activity.
- If controls generate lots of false positives, they are not useful.
- Alerts that are constantly ignored are of little use.
- Detection does not need to be perfect to be effective.
- A security information and event management (SIEM) system or big data logging may be helpful to do cross-correlation and enable more sophisticated alerting.
- The goal is to ensure the most dangerous attacks trigger an alert when an attack occurs.
- For example, firewalls alerting on internal port scans, versus scans originating from the Internet
- Detective controls tend to have a small impact on business operations and can be deployed (or removed) aggressively vs. preventive controls.
- When combined with forensic controls, detective controls give enterprise ability to know when the attacks occur and stop them.
- Preventive Controls
- Block undesired activities and prevent them from occurring
- Are often considered primary controls to the detriment of audit, forensic, and detective controls
- Are generally the most disruptive to business to emplace and operate
- Each control requires a process for getting access or bypassing the block when required by the enterprise (for example, firewall exception and access management process)
- Characteristics of useful preventive controls include
- blocking behaviors that would be noisy with detection alone, reducing investigation costs;
- deploying or operating controls that do not cost too much, particularly in terms of business disruption caused by the block;
- not introducing significant new vulnerabilities; and
- blocking attacks and detecting attacks in progress.
- Letting Audits Drive Control Design
- Helps enterprise design controls to effectively detect attacker activities while reducing the disruption to business operations
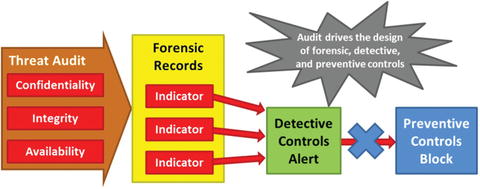
- Identifies the most likely threats to enterprise IT confidentiality, integrity, or availability via Threat Audit
- Searches for attacks that have occurred and collects the necessary supporting evidence
- Identifies what forensic records are needed to log incidents and Indicators of Compromise (IOCs)
- Creates detective and then preventive controls
Enterprise Cybersecurity Assessments
Context
- An enterprise cybersecurity program organized into functional areas lends itself to an assessment methodology that can be executed at different levels of detail.
- The remainder of this section describes how to do a multi-level enterprise cybersecurity assessment organized around the cybersecurity functional areas.
- Level 1 Assessment: Focus on Risk Mitigations
- Analyzes the risks to the enterprise and the threats against the confidentiality, integrity, and availability of IT systems and data; identifies the most likely and most dangerous threat vectors
- Examines attack sequences for those threats and enterprise defensive capabilities to disrupt, detect, delay, and defeat those attacks
- Level 2 Assessment: Focus on Functional Areas
- Evaluates the 11 enterprise cybersecurity functional areas , as well as security operations, at a high level
- Quickly identifies the functional areas that are most likely to be exploited
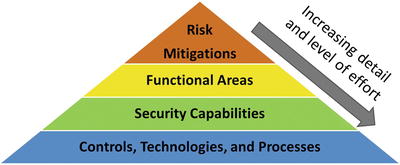
- Level 3 Assessment: Focus on Security Capabilities
- Assesses in detail 113 enterprise cybersecurity capabilities and 17 operational processes (described in this study guide)
- Aggregates results into overall enterprise cybersecurity assessment that can be used to prioritize areas for improvement
- Level 4 Assessment: Focus on Controls, Technologies , and Processes
- Assesses the controls, technologies, and manual processes that deliver the enterprise’s cybersecurity capabilities
- Identifies specific recommendations for tuning, adjustments, or remediation to improve their operational effectiveness
- Assessments (internal or external) should be performed within the security scopes identified in the cybersecurity planning process.
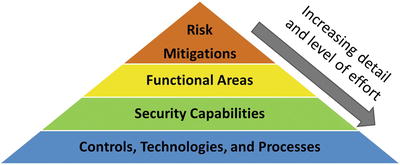
- This top-down assessment approach differs from control-based cybersecurity assessments.
- It looks at cybersecurity functional areas and capabilities rather than focusing on the individual controls.
- It provides remediation and prioritization guidance rather than producing results containing dozens or hundreds of recommendations with little guidance on how to manage remediation.
- It finds the forest for the trees by organizing results into 11 cybersecurity functional areas for remediation delegation.
- Quantitative methods can be used to calculate assessment scores and can be combined into various measurement indices to indicate the entire enterprise’s cybersecurity effectiveness.

Level 1 Assessment: Focus on Risk Mitigations
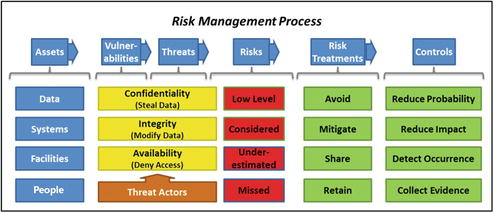
- This assessment starts with the risk management process to identify threats to the security scope and then considers those threats in terms of their attack sequence steps.
- Level 1 Assessment Activities include
- identifying threats and business impacts on confidentially, integrity, and availability;
- identifying the most likely and most dangerous threats to the security scope;
- analyzing the threats to understand the attack sequences that attackers would follow;
- assessing security controls that log, detect, or block those attack sequences in terms of their ability to reduce the probability or impact of attacks completing each step of the attack sequence; and
- if possible, investigating security control logs to see if attacks have occurred or are occurring and may be escaping detection.
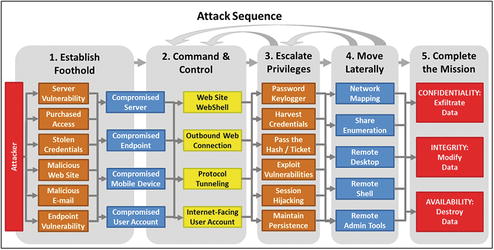
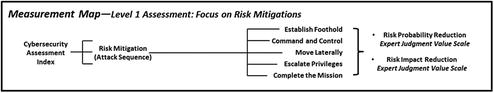
- Level 1 Assessment Outputs include the following:
- List of highest-level risks and threats
- Documentation of attack sequences
- Security controls that apply to attack sequences
- Assessment score
Level 2 Assessment: Focus on Functional Areas
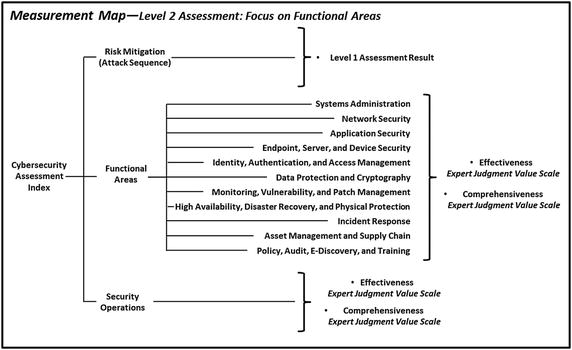
- Level 2 Assessment builds upon Level 1 Assessment and considers the following:
- Level 1 risk mitigations
- Cybersecurity posture of functional areas
- Operational process (that is, Security Operations)
- Level 2 Assessment Activities include
- using Level 1 Assessment to identify security scopes and evaluate risk mitigations against the enterprise cybersecurity attack sequence;
- evaluating functional areas and security operations in terms of effectiveness and comprehensiveness for each security scope;
- capturing evaluated results for all the functional areas and security operations (strongest to weakest);
- identifying how to improve by considering people, organization, budgets, processes , technologies , and capabilities for weakest areas; and
- considering overall security posture compared to the security requirements of the scope.
- Level 2 Assessment Outputs include
- an evaluation of each functional area and an identification of the weakest functional areas.
Level 3 Assessment: Focus on Security Capabilities
- Level 3 Assessment goes into greater detail by considering the individual capabilities within each functional area, as well as by examining each of the 17 operational processes.
- For each capability and operational process, this assessment evaluates their maturity and utilization.
- This assessment can be used to develop action plans to improve specific functional areas.
- There is an excellent balance of assessment efforts vs. actionable results.
- Level 3 Assessment Activities include
- using Level 1 Assessment to identify security scopes and evaluate risk mitigations against the enterprise cybersecurity attack sequence; and
- identifying the functional areas to be evaluated and corresponding cybersecurity capabilities.
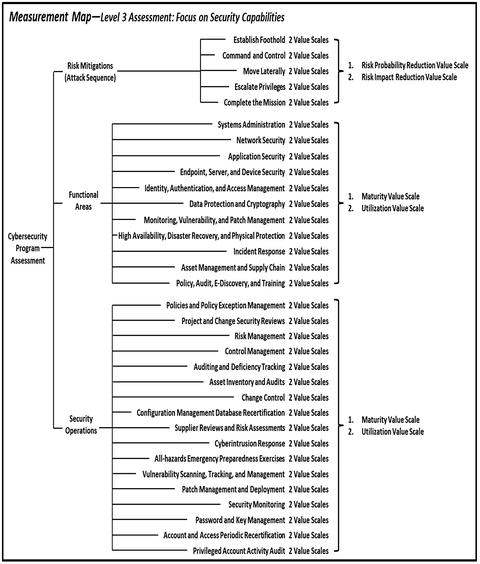
- For a complete assessment, all capabilities in all functional areas should be evaluated, in addition to all operational processes.
- For each functional area’s capabilities, security teams examine the technologies and processes that deliver the capability to evaluate the cybersecurity’s maturity (how well it works) and utilization (how consistently it is being used).
- This functional area capability examination evaluates how well the capability delivers security to the enterprise.
- For each operational process, assessors analyze its maturity (how well it works) and utilization (how consistently it is being used).
- This operational process examination evaluates how well the operational process helps the enterprise operate its cybersecurity.
- Level 3 Assessment Outputs include the following:
- Functional area maturity and utilization
- Operational process maturity and utilization
- Strongest and weakest capabilities and operational processes
- Action plans for improving functional areas and operational processes
- It is important to note there is not a perfect correlation between the presence of capabilities and a functional area’s overall security effectiveness.
- A functional area can be effective without having all the cybersecurity capabilities.
- A functional area can have many of its cybersecurity capabilities present and utilized; however, if they are not configured properly, they can be ineffective or neutralized by a deliberate attacker.
Level 4 Assessment: Focus on Controls, Technologies, and Processes
- Level 4 Assessment focuses on the following:
- Controls (preventive, detective, forensic, and audit)
- Technologies
- Supporting processes
- Can be limited to a single functional area or even just a set of cybersecurity capabilities, their supporting technologies and process, or the security controls they support
- Can be useful when evaluating deficient functional areas in order to identify tuning opportunities and cost-effective capability improvements
- Level 4 Assessment Activities include
- identifying the functional areas, capabilities that are of interest, and the supporting controls, technologies, and processes;
- examining them to identify issues with their effectiveness, configuration, or operation; and
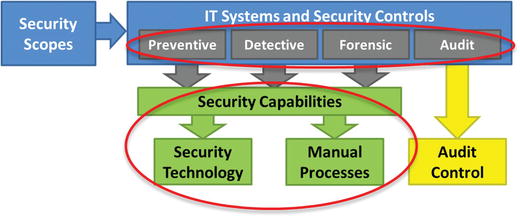
- aggregating resulting recommendations into comprehensive change proposals for updating controls, technologies, or processes to make them more effective.
- Level 4 Assessment Outputs include
- specific recommendations to improve the effectiveness of each control, technology, or process that was considered; and
- recommendations that are technology-specific and actionable.
Audit Deficiency Management
- Deficiencies and deficiency tracking are important components of the auditing process and must not be shortchanged or ignored just because the audit is over.
- What is a deficiency?
- A situation where a capability, process, technology, or control does not function as it was designed and documented
- Indication that overall enterprise security is not as effective as one would expect upon a simple review of documentation
- Revelation when actual performance of capabilities, processes, or technologies is not what was expected when they were tested
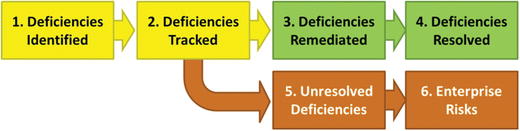
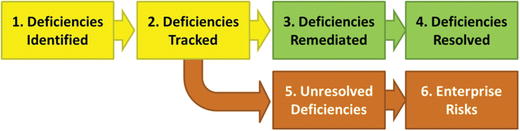
- Deficiencies
- Important because they undermine, or even completely nullify, the enterprise security that should be present through the various controls and capabilities
- The fine print that needs to be appended to any discussion of the business value of the security controls and capabilities found to be deficient
- The graphic depicts a deficiency tracking process.
- When deficiencies are identified, a simple process can be followed to track and resolve them.
- With tracking, follow-up, and timely remediation, an enterprise can benefit from the value of the overall audit process.
- An enterprise does not have to remediate all deficiencies, but an enterprise shouldn’t simply ignore them either.
- Enterprise should formally track deficiencies as part of its overall risk management process so that deficiencies do not slip through the cracks.
- Audit Deficiency Management Activities include
- identifying the deficiencies through an audit or formal testing;
- recognizing that capability, process, technology, or control is not as effective as it should be and must be considered in the context of overall enterprise risk.
- tracking identified deficiencies until they are disposed—employees departing, laptops getting lost, or other routine changes should not result in the deficiency list being lost;
- remediating deficiencies so things get back to working as expected;
- documenting remediated and resolved deficiencies;
- considering deficiencies (for example, > 1-year old) unresolved unless there is an enterprise-approved mitigation plan and documenting these deficiencies for future audits (for instance, 75% effective, which may be acceptable); and
- Audit Deficiency Management Outputs include
- identified deficiencies,
- remediated and resolved deficiencies,
- no resolved deficiencies; and
- patterns of repeat deficiencies and remediation
- In general, whether audits are regularly scheduled control validations, externally performed assessments, or internal threat audits, it is critical the audit findings, deficiencies, and recommendations be tracked through to completion.
- Enterprises benefit from the audit process with tracking, follow-up, and timely remediation.
Footnotes
1
Security scopes group together assets and controls around a shared business impact caused by a common set of threats against confidentiality, integrity, or availability (CIA).
