Overview
- This study guide describes effective cybersecurity that
- works against advanced cyberthreats;
- evolves over time to handle increasingly sophisticated adversaries in an increasingly interconnected world;
- is involved as a partner, coach, and scorekeeper for IT, rather than just as a naysayer standing in the way of progress; and
- works when you are faced with an adversary who is well-funded, intelligent, sophisticated, and persistent.
- Cybersecurity challenges and technologies continue to evolve quickly—attackers and defenders are not standing still.

- This study guide describes a cohesive Enterprise Cybersecurity Framework that integrates
- architecture consisting of cybersecurity capabilities organized into functional areas that make capabilities easier to track, manage, and delegate;
- cybersecurity policy designed to balance security needs against business priorities;
- programmatics involving people, budget, and technology that are allocated to day-to-day operations and projects;
- an IT life cycle aligned with IT departments responsible for strategy and architecture, engineering, and operations; and
- cybersecurity assessments that are conducted periodically to help prevent cybersecurity program obsolescence.
- The Enterprise Cybersecurity Framework is pragmatic, realistic, and designed for battling today’s cyberthreats as well as tomorrow’s next-generation cyberthreats.
Topics
- The Cyberattacks of Today
- Types of Cyberattackers
- Types of Cyberattacks
- The Steps of a Cyberintrusion
- Why Cyberintrusions Succeed
- A New Cybersecurity Mindset
- An Effective Enterprise Cybersecurity Program
The Cyberattacks of Today
Context
- Compared to today, cybersecurity used to be relatively simple.
- Major cyberthreats were viruses, worms, and Trojan horses.
- Transformation started to take place.
- Cyberattackers started getting inside enterprise networks.
- Once inside, cyberattackers operated surreptitiously:
- They took control of infected machines.
- They connected infected machines to remote command-and-control systems.
- They escalated their privileges to systems administration. …
- “We are using outdated conventional defenses to guard against cutting-edge innovative malware. We are no more prepared to do this than a 19th century army trying to defend itself against today’s weaponry.” 1
- Breaches in the News
- In 2011, RSA’s enterprise was breached, and the security keys for many of its customers were believed to have been stolen.
- In 2013, Target’s point of sale network was compromised, resulting in the loss of personal information and credit card numbers for over 40 million customers.
- In 2014, a German steel mill was affected by a hacking incident that caused one of its blast furnaces to malfunction, resulting in significant physical damage to the plant and its facilities.
- In 2015, Anthem reported its IT systems had been breached and personal information on over 80 million current and former health care network members was compromised.
- These examples are but a handful of cybersecurity breaches that are indicative of trends.
The Sony Pictures Entertainment Breach of 2014
- In November 2014, an attacker took over the employees’ computers.
- The nonfunctional computers displayed a message from the Guardian of Peace.
- By the end of the day, most computers had been completely disabled, which impacted the company’s business—or lack thereof.
- The cyberattacker published proprietary data to include salaries and personal e-mails of Sony’s senior executives.
- Key Lessons Learned
- Attackers did what cyberattackers have been able to do all along, but have chosen not to—they put the reality of the Sony hack in full view of the press and public.
- It is reasonable to assume Sony’s cyberdefenses were consistent with industry norms, but reflected what is and what is not being done at companies around the world.
- Effectiveness of the Sony hack was likely amplified by the consolidation of IT systems administration that has occurred over the past 20 years.
- A single systems administrator used to manage a handful of servers.
- Today, this same administrator may have privileged access to hundreds of systems or even thousands.
- Professional attackers, who understand how modern IT works and how it is managed, can effectively turn an enterprise’s IT infrastructure against the enterprise.
- IT infrastructures are largely designed for functionality—not security—and often lack compartmentalization to contain an attack.
- Attack underscores the fear factor that devastating cyberattacks can have on an industry or nation.
- Megatrend—As further described , such attacks are moving “down market” over time and becoming more common.
Advanced Persistent Threats
- Advanced Persistent Threat (APT) is rising as a new type of adversary.
- An APT attacker is skilled in the art of cyberattacks and leverages IT technologies effectively to breach enterprises and systematically bypass all their protections, one at a time.
- What makes APT different from earlier cyberattack types is the persistence of the attack.
- APT cyberattacks are much more focused and effective because they are under the control of an intelligent actor who has an objective to achieve.
- If their objective is to break into a company and steal corporate secrets, attackers persist until they succeed.
- If their objective is to break into a government and steal national security information, they persist to find a weakness to exploit.
- Conventional Cyberattacks
- Defenses only need to block the malware and the attacker will move on to other targets.
- Simply having defenses is no longer effective when an opportunistic attacker can exploit a single mistake.
- An APT attacker constantly adjusts the attack to get past the latest round of defenses.
- Given enough time, an APT attacker eventually gets through.
- To stop an APT attacker, the defenses have to work perfectly and be maintained perfectly.
- An APT attacker will exploit any mistake.
- APT requires a new type of defense method—one that adapts to the attack as quickly as the attack adapts to the defense.
Waves of Malware
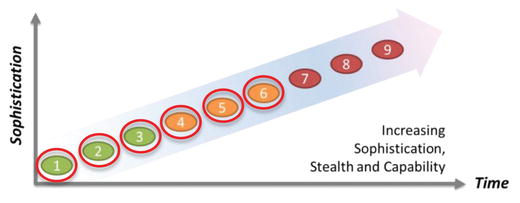
- Over the past 20 years, there have been a number of generations, or waves, of malware technologies.
- 1.Static Viruses
- a)Propagated from computer to computer via floppy disks and boot sectors of hard drives
- b)Had little impact on system operations
- a)
- 2.Network-Based Viruses
- a)Propagated across the open Internet from computer to computer, exploiting weaknesses in operating systems or configurations
- b)Were effective because computers were often directly connected to each other without firewalls or protection
- a)
- 3.Trojan Horse
- a)Propagated across the Internet via e-mail and from compromised or malicious web sites
- b)Can infect large number of victims, but does so relatively arbitrarily since it is undirected
- a)
- 4.Command and Control (C2)
- a)Allows attacker to remotely control its operation within the target enterprise
- b)Enables compromised machines to become footholds within the enterprise
- c)Allows footholds to be manipulated by the attacker
- a)
- 5.Customized
- a)Developed for a particular target
- b)Sent directly to specific targets via phishing e-mails, drive-by web sites, or downloadable applications such as mobile apps
- c)Is not not recognized by signature-based defenses since this malware is customized for each victim
- a)
- 6.Polymorphic
- a)Designed not only to take administrative control of victim networks, but also to dynamically modify itself so it can continuously evade detection and stay ahead of attempts to remediate it
- a)
- 7.Intelligent
- a)Analyzes a victim network, moves laterally within it, escalates privileges to take administrative control, and then extracts, modifies, or destroys its target data or information systems
- b)Does all its actions autonomously, without requiring human intervention or external command and control
- a)
- 8.Fully Automated, Polymorphic
- a)Combines the features of polymorphic and intelligent malware
- b)Takes control autonomously and dynamically evades detection and remediation to stay one step ahead of defenders at all times
- a)
- 9.Firmware and Supply Chain
- a)Takes fully automated, polymorphic malware to its logical conclusion by delivering malware capabilities through the supply chain, either embedded in product firmware or software products before they are shipped
- b)Is virtually undetectable
- c)Is difficult to differentiate the supply chain malware from the other features coming from the factory
- a)
- 1.
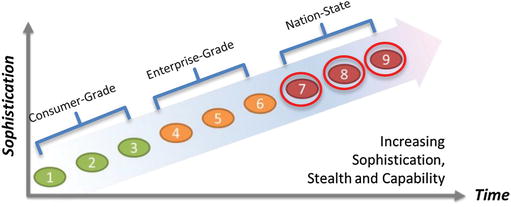
- Many people are familiar with malware waves 1, 2, and 3 because they represent the majority of consumer-grade cyberthreats, and many of the attacks are covered by the mainstream press.
- Enterprises are experiencing malware waves 4, 5, and 6 on a regular and increasing basis, but few outside of specialized cybersecurity fields understand the malware.
- Nation-state attackers use malware waves 7, 8, and 9, which require significant resources and expertise.
Types of Cyberattackers
Context
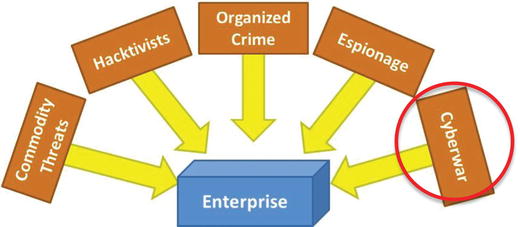
- Who are these mysterious cyberattackers hacking into systems and causing media headlines?
- Cyberattackers are people who choose to create, distribute, and use malware or other tools and techniques to do things on computers they shouldn’t be doing.
- The graphic shows five groups of cyberattackers grouped by their intent and objectives:
- Commodity Threats
- Hacktivists
- Organized Crime
- Espionage
- Cyberwar
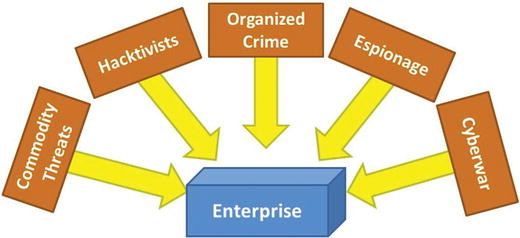
- Note: There can be significant overlap in the tools and technologies used by these groups.
Commodity Threats
- Commodity threats include random malware, viruses, Trojans, worms, botnets, and ransomware.
- Commodity threats are propagating on the Internet all the time. Commodity threats
- are undirected and opportunistic;
- may exploit cyberdefense vulnerabilities;
- do not adjust or adapt in order to work their way around protections that are in place;
- can be destructive, but limited;
- can be a starting point for more dangerous, targeted threats; and
- be stopped if defenders block the commodity threat’s attack vector, making the defenders safe.
- For other cyberattack threat categories, simply blocking the initial attack vector is only a start.
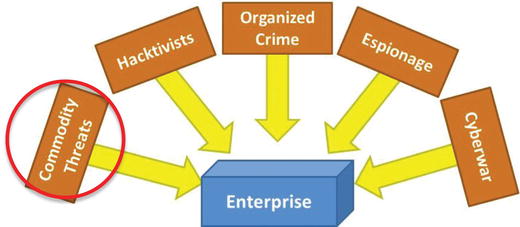
- Targeted cyberattackers
- These cyberattackers may start their efforts by going to botnet operators and purchasing access to computers and servers that are already compromised inside the target environment.
- Purchasing access can make the attackers’ initial entry into the enterprise easier and save them valuable time and money.
Hacktivists
- Activist hacking , or hacktivism, consists of targeted attacks that
- make public or political statements;
- are used against individuals, enterprises, or governments;
- seldom set out to hurt anyone or do significant physical damage;
- are simply looking to get a message out and draw attention to a cause;
- tend to use mostly commodity tools and techniques that are widely available on the Internet; and
- take advantage of vulnerabilities that are unpatched or open.
- Defenses to protect against these tools and techniques are also usually widely available.
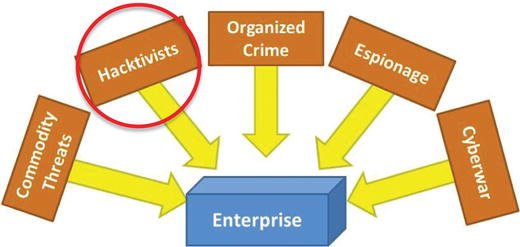
- Hacktivists will try and try again until the defenders make a mistake that allows them to accomplish their goal of bolstering their cause or embarrassing their adversaries.
Organized Crime
- Organized crime attacks are targeted attacks.
- Criminals and criminal organizations have found there is serious money to be made on the Internet.
- Easy Access
- On a global, interconnected network, the so-called good and bad neighborhoods are just a click apart.
- Criminals can reach most anyone in the world without leaving their easy chairs.
- Lack of Attribution
- It can be difficult to track down attackers, especially when they cover their tracks.
- With criminals in one country and victims in another country, national boundaries make attribution even more difficult.
- Wholesale Data
- Why steal money from one person at a time when you can rob the bank instead?
- With the consolidation of data into huge corporate databases, wholesale data theft can be relatively easy to carry out.
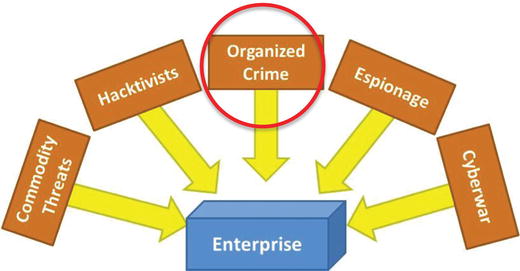
- Data theft is big business.
- Stolen credit cards or social security numbers typically sell for $1 each.
- Medical records can sell for $10 or more.
- Stealing one million records can make real money, which can be used to support an entire shadow industry willing to lend their services for a piece of the action.
- There are many ways to make money through cyberattacks:
- Business banking accounts
- Ransomware
- Payroll accounts can be relatively easy to carry out
- Direct deposits
Espionage
- What organized crimes start, espionage agents take to the next level.
- Cyberespionage is more complex than organized crime.
- It may be financially driven, but other drivers are much less forward.
- It centers on stealing trade secrets for commercial advantage or national secrets for political or military advantage.
- In the cases of international business, trade secrets and national secrets can be closely aligned.
- Secrets can include the following:
- Blueprints, formulas, or software code that is considered critical for success
- Plenty of other information such as organization charts, budgets, project schedules, and meeting minutes that are vitally useful to the competition

- Cyberespionage practitioners frequently use APT-style methods because they tend to be effective against enterprises with legacy-style cyberdefenses.
- Why hack the CEO’s laptop when, for the same amount of effort, you can get control of every laptop in the enterprise?
- Cyberespionage campaigns can be
- conducted at the nation-state level; and
- can be made up of multiple parts or phases (stepping stones).
Cyberwar
- Whereas espionage is generally focused on stealing information, the focus of cyberwar is on damaging the ability of enterprises or governments to operate in cyberspace.
- Damage can done by the following:
- Overwhelming, overloading, disabling, or destroying IT systems used by victims
- Using victim IT systems to cause physical systems to malfunction and damage themselves or their operators
- Everything is increasingly computerized and networked—the damage from cyberspace continues to increase.
- Cyberwar’s cousin is cyberterrorism. Unaffiliated individuals or terrorist organizaions use the same techniques:
- Denial of service
- Data destruction
- Control system manipulation
- Cyberwar supports national interests.
- Cyberterrorism is done for an activist agenda or for the sake of anarchy and destruction for its own sake.
- In 2007, Estonia’s Internet infrastructure (telephone, financial, and government operations) was targeted.
- The Stuxnet worm infiltrated the Iranian nuclear program and ruined nuclear centrifuges.
- The 2012 cyberattack of Saudi Aramco resulted in damaging tens of thousands of computers.
Types of Cyberattacks
Context
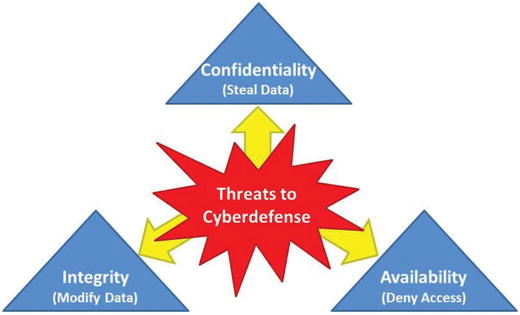
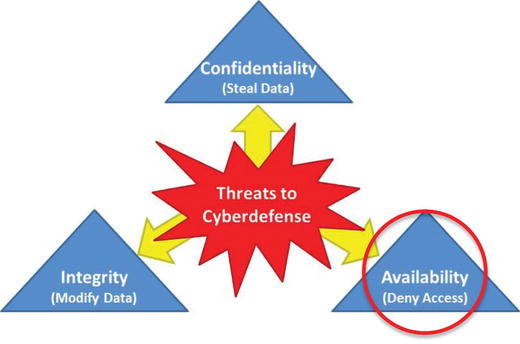
- Regardless of their objective or techniques, cyberattacks generally can do three things to an enterprise or its data.
- Cyberattacks compromise
- confidentiality by stealing data;
- integrity by modifying data; and
- availability by denying access to data, services, or systems.
- Some attacks combine two or more of the three types, but the three cyberattack types are the building blocks for most malicious cyberactivities.
- Cyberdefenses must focus on protecting confidentiality, integrity, and availability of data and the IT systems that process data.
- Following are common cyberattacks:
- Phishing / Spearsphishing
- Drive-By / Watering Hole / Malvertising
- Code Injection / Webshell
- Keylogging / Session Hijacking
- Pass-the-Hash and Pass-the-Ticket
- Credential Harvesting
- Gate-Crashing
- Malware / Botnet
- Distributed Denial-of-Service (DDoS)
- Identity Theft
- Industrial Espionage
- Pickpocket
- Bank Heist
- Ransomware
- Webnapping
- Hijacking
- Decapitation
- Sabotage
- Sniper / Laser / Smart Bomb
- Smokeout / Lockout
- Infestation / Whack-a-Mole
- Burndown
- Meltdown
- Defamation
- Graffiti
- Smokescreen / Diversion
- Fizzle
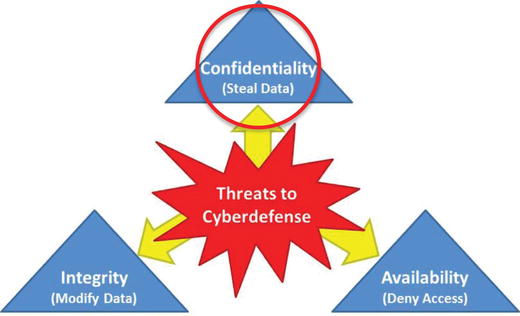
Confidentiality—Steal Data
- Confidentiality breaches steal data, sell data to the highest bidder, and often make headlines:
- Social security numbers
- Credit card numbers
- Bank account information
- Electronic health records
- Confidential corporate secrets and executive correspondence
- Breaches focus on getting access to data at-rest or in-transit locations.
- Databases
- Large pools of data
- Relatively well-protected deep inside enterprise architecture
- Backups
- Contain critical business information and customer data
- Frequently do not get much security consideration
- May be unencrypted
- Application Servers
- Front-end application servers with access to data are frequently directly connected to the Internet.
- Breaching such servers can provide access to data through applications, bypassing encryption, and other protection.
- Systems Administrators
- They are the Achilles' heel of most enterprises.
- Access to these credentials enable attackers to bypass data protection with little or no audit trail.
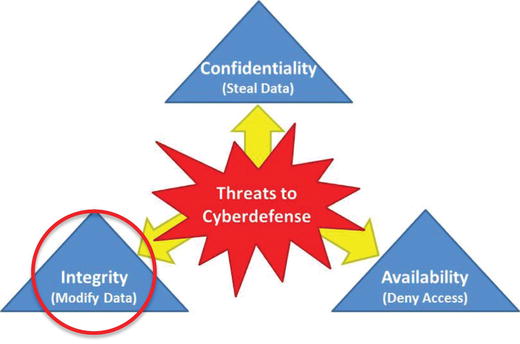
Integrity—Modify Data
- Integrity attacks involve modifying data that can result in various impacts:
- Reputational impacts if the data is public-facing such as web sites
- Financial reporting impacts, particularly for publicly traded corporations
- Losses of actual money if data is bank-routing numbers or financial command to banks handling corporate accounts
- Integrity attacks include the following:
- Hijacking
- Hijackers alter infrastructure data about Internet property (domain names, social medial identities, or registered network locations).
- Much of the Internet’s real estate is secured only by an e-mail address.
- Sarbanes-Oxley
- Unauthorized changes to financial data can have serious audit and regulatory outcomes.
- Online Banking
- Bank accounts including payroll, investments, and stock funds worth thousands or millions of dollars.
- Direct Deposits
- Vulnerable to thefts where paychecks are re-routed to attacker accounts.
- Vandalism
- Malicious actors deface web sites or other public materials with the intent of embarrassing the victim.
- Internet-facing systems can be hard to protect perfectly as a single vulnerability or configuration mistake is all an attacker needs to strike.
Availability—Deny Access to Data, Services, or Systems
- Availability attacks affect the availability of systems and deny access to the systems.
- Can be difficult to diagnose, especially if systems are impaired but not disabled
- Can cause failures by overwhelming systems and infrastructure
- Deliberate availability attacks can be grouped into three categories:
- Distributed Denial of Service (DDoS)
- Used to effectively disable services in the victim enterprise or country
- Can take significant portions of victim’s Internet capabilities offline for some time until they are mitigated
- Targeted Denial of Service
- Involves hacking into the victim’s enterprise and then disabling systems so they have to be rebuilt or recovered
- Can be time-consuming for IT personnel to recover systems and restore service, particularly if backups are affected
- Physical Destruction
- This type of availability attack Involves using cyberattacks to cause physical destruction.
- Stuxnet is a computer worm that sabotaged centrifuges used by the Iranian nuclear program.
- As more and more critical systems are computer- controlled, these types of attacks will become potentially more dangerous and destructive over time.
The Steps of a Cyberintrusion
Attack Trees and Attack Graphs
- How do cyberattacks occur?
- Hackers actually take control of computers and accounts inside of victim enterprise.
- It is helpful to work out steps required for intrusion to succeed.
- Attack Trees and Attack Graphs
- In 1999, Bruch Schneider published an article introducing a methodology for analyzing attacks, called Attack Trees.
- An attack tree begins with the objective of the cyberattack (such as stealing enterprise data).
- Then the attack tree works backward to consider the various ways the objective could be achieved and the steps involved to accomplish the objective.
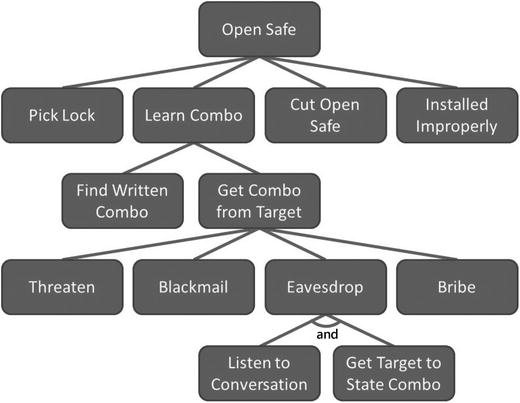
- The graphic depicts a notional attack tree Mr. Schneider analyzed for the case of trying to break into a safe.
- Each attack tree step is an opportunity to apply defenses and make the overall attack harder.
- Attack steps can trigger an alarm and cause the entire attack to be detected.
- Defenses can also add steps the attack must take before it can succeed.
- Putting money in a safe means the attackers have to figure out how to get into the safe before they can get to the money.
- Putting data into “virtual safes” can have the same effect.
- Defensive steps don’t make stealing the data impossible, as no defense is perfect, but they can make the attack significantly more difficult, time-consuming, and expensive.
- Significant academic research is ongoing using attack trees and a generalized version of attack trees called Attack Graphs.
- A graph is just like a tree , except the dependencies can loop back on themselves.
- Attack graphs have been computed for massive networks.
- Research shows how vulnerabilities interconnect and how attackers can step from one compromised computer to another until they reach their target.
- This research is of limited use.
- Attack graphs of more than a handful of machines considering more than a handful of potential vulnerabilities become incredibly complex.
- It is difficult to turn results into actionable intelligence.
Lockheed Martin Kill Chain
- What kind of graph is useful?
- Attack-tree and attack-graph methodologies provide a generalized model of the sequence of cyberintrusion activities.
- Defenders can analyze multiple options of attacker activities.
- Defenders can then focus their defenses on disrupting such options.
- The attack tree can be generalized into a model that is simpler to analyze, but powerful in terms of providing specific, actionable results.
- When simplified, the attack tree gets reduced down to a sequence.
- The sequence has many labels, including Kill Chain, Attack Life Cycle, and Attack Sequence.
- In 2011, several researchers from Lockheed Martin published a paper2 that analyzed Advanced Persistent Threat (APT) attack campaigns.
- Attackers followed a sequence of seven steps; defenders could apply defenses at each step to attempt to thwart the attack.

Lockheed Martin Kill Chain

- 1.Reconnaissance
- a)Research, identify , and select targets.
- b)Crawl Internet web sites such as conference proceedings, mailing lists for e-mail addresses, social media sites, and so on.
- a)
- 2.Weaponization
- a)Attackers couple a remote access Trojan with an exploit into a deliverable payload, typically by means of an automated tool (weaponizer).
- b)Adobe Portable Document Format (PDF) and Microsoft Office documents often serve as the weaponized vehicle.
- a)
- 3.Delivery
- a)Delivery denotes the transmission of the weapon to the targeted environment.
- b)Lockheed Martin Computer Incident Response Team reported for the years 2004–2010, the three most prevalent delivery vectors for APT weaponized payloads were e-mail attachments, web sites, and USB removable media.
- a)
- 4.Exploitation
- a)After the weapon is delivered to the victim host, exploitation triggers the intruder’s code.
- b)Exploitation often targets an application or operating system vulnerability, but it can also target the users or leverage an operating system feature that auto-executes code.

- a)
- 5.Installation
- a)Installation of a remote access Trojan or back door on the victim system allows the adversary to maintain persistence inside the environment.
- a)
- 6.Command and Control (C2)
- a)Typically, compromised hosts must beacon outbound to an Internet controller server to establish a C2 channel.
- b)APT malware typically requires manual interaction rather than activity conducted automatically. Once the C2 channel is established, intruders have “hands-on-the-keyboard” access inside the target environment.
- a)
- 7.Actions on Objectives
- a)After progressing through the first six steps, intruders take actions to achieve the objectives.
- b)The typical objective is data exfiltration—collecting, encrypting, and extracting information from the target environment; violations of data integrity or data availability are also potential objectives.
- c)Alternatively, intruders may use the initial victim box as a “hop point” to compromise additional systems and move laterally inside the network.
- a)
Mandiant Attack Life Cycle
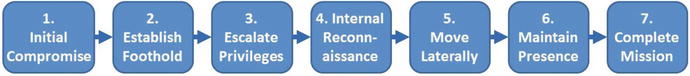
- The Mandiant Attack Life Cycle contains seven steps that start at the initial compromise.
- The process breaks out the steps of accomplishing the mission in greater detail than the Lockheed Martin Kill Chain.
- Mandiant believes China used such techniques to spy on governments and corporations in the United States and elsewhere.
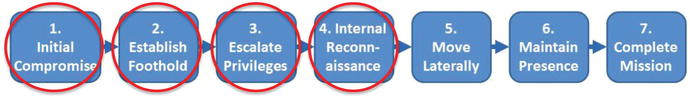
- 1.Initial Compromise
- a)This step represents the methods intruders use to penetrate a target organization.
- b)APT intruders frequently target individual users or look for technical vulnerabilities in public-facing infrastructure.
- a)
- 2.Establish Foothold
- a)By establishing a foothold , APT threat groups can access and control one or more victim computers from outside the network via back doors.
- b)Back doors give the APT groups basic access to a system, typically through a command shell or graphical user interface.
- a)
- 3.Escalate Privileges
- a)This step involves acquiring administrative access to resources within the victim environment.
- b)Administrative access can be obtained through usernames and passwords, Public Key Infrastructure (PKI) certificates, Virtual Private Networking (VPN) connectivity, or control of systems administration computers.
- a)
- 4.Internal Reconnaissance
- a)Attackers collect information about the victim environment.
- b)Data of interest may take different forms, most commonly consists of documents, the contents of user e-mail accounts, or databases.
- c)Attackers may use custom scripts to automate the process of reconnaissance and identification of data of interest.
- a)
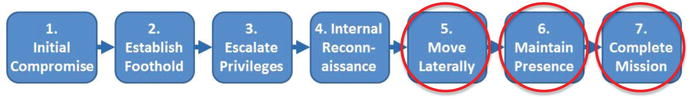
- 5.Move Laterally
- a)In most cases, the systems intruders initially compromise do not contain the data they want.
- b)Moving laterally within a network to other computers is necessary for mission success.
- c)APT groups leverage compromised user credentials or pass-the-hash tools (that steal user credentials) to gain access to additional victim computers and devices.
- a)
- 6.Maintain Presence
- a)Intruders take actions to ensure continued control over key systems in the network environment from outside the network.
- b)They may install different families of malware on multiple computers and use a variety of command and control addresses.
- c)Different malware families provide redundancy and make it difficult to identify and remove all intruder access points.
- a)
- 7.Complete Mission
- a)The APT intrusion goal typically is to steal data (for example, intellectual property, business contracts or negotiations, policy papers, and internal memoranda).
- b)Once APT groups find files of interest on compromised systems, they often pack them into archive files before exfiltrating them.
- c)A variety of methods are used to transfer files out of the victim network, including file transfer protocol (FTP), file sharing tools, and web upload sites.
- a)
Enterprise Cybersecurity Attack Sequence
- Based on the authors’ experience building and operating defenses against real-world APT actors, they adopted a simplified version of the attack sequence process they call the Enterprise Cybersecurity Attack Sequence.
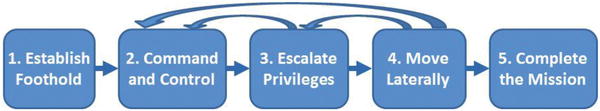
- This attack sequence is derived from the preceding work and simplifies it somewhat to align more closely with how and where defensive capabilities are often deployed in enterprise defenses.
- Initial attacker access and footholds are almost impossible to prevent completely.
- The attack sequence includes iterative cycles among steps 2, 3, and 4, as attackers move around the target enterprise in search of their objective.
- During steps 2, 3, and 4, attackers often generate considerable telemetry activity that can be used to detect their presence and repel their attacks before those attacks can succeed.
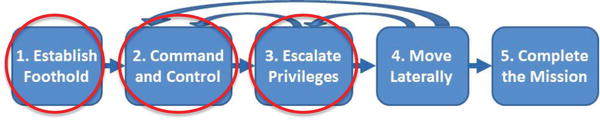
- 1.Establish Foothold
- a)Attackers can accomplish this activity by exploiting vulnerabilities in servers and applications, compromising end-user workstations, or buying access through criminally operated botnet networks.
- b)Footholds can consist of a compromised server, endpoint computer, mobile device, or simply a user account with access into the victim enterprise network.
- a)
- 2.Command and Control
- a)Attackers establish remote command and control capabilities so they can manually run commands in the target environment.
- b)These connections can be made via inbound connections to Internet-facing servers, outbound connections from internal endpoints, or various forms of protocol tunneling, including encrypted connections.
- a)
- 3.Escalate Privileges
- a)Attackers gain control of user accounts with the privileges needed to accomplish the attack objective.
- b)In environments with username and password authentication for systems administrators, this activity can be trivially easy to accomplish.
- c)In more complex environments, this activity may take more time as attackers must identify and circumvent multiple layers of protections around the privileges the attackers want.
- a)
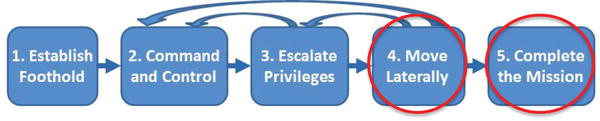
- 4.Move Laterally
- a)While escalating privileges , attackers may also move laterally from computer to computer.
- b)This movement can involve transiting network zones, bypassing firewalls, compromising machines, and stealing credentials.
- c)Lateral movement may then feed back into multiple rounds of privilege escalation and command-and-control establishment.
- d)In complex environments, this cyclical process may take weeks or months to get from the starting point to the ultimate objective.
- a)
- 5.Complete the Mission
- a)Once the objective has been accessed, the attackers can complete their mission.
- b)If the objective is to steal data, attackers will bundle the data up and exfiltrate it.
- c)If the objective is to modify data, attackers will make the desired changes or initiate the desired transactions.
- d)If the objective is to damage availability, attackers will disable the targeted systems.
- e)At the end of this step , attackers may cover their tracks.
- a)
Why Cyberintrusions Succeed
Context
- Successful attacker cyberintrusions require the following:
- Successfully performing multiple steps
- Defeating potential defenses and defensive technologies
- Why are cyberintrusions successful?
- No single or simple answer exists.
- A number of factors, when taken together, is making it harder for cybersecurity defenses to succeed.
- Factors impacting enterprises’ abilities to protect themselves include the following:
- The Explosion in Connectivity
- Consolidation of Enterprise IT
- Defeat of Preventive Controls
- Failure of Detective Controls
- Compliance over Capability
- The Gap in Cybersecurity Effectiveness
The Explosion in Connectivity
- Network connectivity (Internet connectivity in particular) has exploded over the last twenty years.
- Enterprises were fairly simple.
- A perimeter, a network, and a data center containing servers
- Desktop computers accessing those services from within a closed network
- Today, the architecture is complex.
- Mobile devices, cloud services using federated credentials
- Corporate infrastructures operated by third-party providers
- Network complexity has exploded.
- Everything is interconnected in a myriad of ways.
- With the rise of mobile, cloud, and the “Internet of things,” everything is connected.
- Complex and sophisticated devices are vulnerable to countless glitches, bugs, and exploits that can turn them from useful appliances into malicious tools.
- In an all-connected world, the functionality is amazing, but the security challenges are daunting.
- Managing, protecting, and defending this complexity are extremely difficult, if not impossible.
Consolidation of Enterprise IT
- Twenty years ago, highly-trained and experienced administrators performed IT functions.
- Today the functions are scripted and automated.
- Administrators can now manage ten or a hundred times as many computers rather than a relatively few computers.
- Enterprise data centers can now contain thousands or tens of thousands of computers vs. a hundred servers.
- Opportunities for mistakes and glitches have grown significantly.
- Modern data centers with cloud services, virtual networking, virtual storage, and virtual computing add to the protection challenge.
- Layers of virtualization and abstraction add complexity.
- Specialized administration areas are difficult to understand, troubleshoot, and protect.
- Legacy data centers had a server administrator who was the one point of contact for server and services protection.
- In a virtualized environment, successful server administration depends on multiple administrators for network, storage, virtualization, servers, and applications.
- Achieving proper configurations across all layers of the computing environment is difficult and complex, and it requires collaboration.
- If attackers get control of the IT power that is in the hands of a small number of people, they can use the enterprise’s own tools against itself.
Defeat of Protective Controls/Failure of Detective Controls
- Before discussing the Defeat of Protective Controls and the Failure of Detective Controls , it is important to understand the types of cybersecurity controls used to mitigate enterprise risks.
- Cybersecurity controls help reduce confidentiality , integrity , or availability risks by
- reducing risk probability;
- reducing risk impact;
- detecting occurrences of risk incidents;
- collecting evidence to support security evaluations and incident investigations; and
- providing validation that risks are being mitigated adequately.
- Cybersecurity control types include the following:
- Preventive Controls
- Block the threat and prevent incidents from occurring altogether
- Detective Controls
- Detect when the threat has transpired
- Generates alerts that can then be acted upon
- Forensic Controls
- Collect records of activities related to the threat
- Can be used to produce artifacts to support the following:
- The operation of detective controls
- Investigations of incidents
- Audits of controls to verify their operation and effectiveness
- Audit Controls
- Investigate the following:
- Presence of the threat
- Incidents associated with the threat
- Operation of controls that mitigate the risk
Defeat of Preventive Controls
- Much of cybersecurity has involved blocking undesired activities and preventing them from executing.
- The preventive approach sounds good in principle, but it has its limitations.
- Establishing preventive controls is like putting up a network of fences and then assuming the fences are working as designed without ever checking them.
- Advanced attackers have consistently succeeded in defeating or working around preventive controls to accomplish their objectives.
- Preventive controls are riddled with vulnerabilities , holes, bugs, and poor configurations.
- Enterprises must assume preventive controls will, at best, only slow down an attacker.
- Eventually, even the strongest preventive controls may be defeated by a skilled and patient attacker.
- Does the above commentary mean preventive controls have failed altogether? Of course not!
- However, it does mean such controls have limits—successful cyberdefense needs more than prevention!
Failure of Detective Controls
- Detective controls are supposed to raise alerts or alarms when malicious activity occurs in their vicinity, based on recognizing known patterns of malicious behavior or software.
- Systemic detective control failures involve (1) lack of incident detection and (2) overloading cybersecurity personnel with potential incident alarms, most of which are false alarms or simply noise.
- First, in many cases, detection is not even happening.
- Most IT systems can log activity, but the activity is often in the form of cryptic text files or event codes that require significant expertise to decipher.
- Consequently, many enterprises have little to no visibility of activity taking place within their systems.
- Enterprises must integrate these logs, correlate across them, and then use the data to alert on activity patterns that are or may be malicious.
- Second, even when enterprises have set up their systems to alert them on potentially malicious behavior, it is easy to become buried in alerts.
- With terabytes of data and thousands of servers, there can be hundreds or thousands or even millions of events per day calling for investigation.
- In practice, a cyber analyst can thoroughly investigate perhaps a dozen events in a single day.
- When people become overwhelmed with data, the enterprise is just as blind as it was when it had nothing.
Compliance over Capability
- Ironically, many of the companies involved in credit card breaches had been recently certified as complying with the Payment Card Industry Digital Security Standards (PCI_DSS).
- Given this situation, it appears compliance certification against established standards does not necessarily correlate with breach resistance.
- First, standards must necessarily focus on the presence or absence of technologies or controls, but it is hard for standards to specify the level of resistance of those technologies or controls to deliberate attack by skilled attackers.
- We can ask if a firewall is present or if network traffic is being filtered, but how do we expand compliance specifications to determine if the firewall is properly configured to stop a deliberate attack?
- The cybersecurity industry is still relatively immature compared to other industries with regard to the establishment of repeatable and auditable standards for effectiveness.
- Second, the requirement for standards compliance can take enterprise resources away from “real cybersecurity.”
- Compliance standards incentivize leadership to focus on checking the box to meet standards and receive certification vs. modeling cybersecurity threats and building effective defenses.
- Once an enterprise is certified as compliant, it can then fall back on the compliance certification if something goes wrong, shielding itself from liability or accusations of negligence.
- Evidence suggests compliance frameworks are not having their intended effect and may need to be upgraded to correlate better with cyberdefense effectiveness against real-world cyberattack scenarios.
The Gap in Cybersecurity Effectiveness
- The graphic suggests that perhaps cyberattacks are improving faster than cyberdefenses, resulting in a gap in effectiveness.
- Unfortunately, gradually improving cyberdefenses may be losing ground over time.
- Modern cybersecurity architecture consists, in part, of secured networks, firewall protections, and anti-virus on endpoints.
- Modern cybersecurity architecture does not seem to be holding up well against cyberattacks.
- Maintaining the defenses of ten years ago is an increasingly daunting task given the
- complexity of devices;
- exploding size of IT architectures;
- interconnections among partners, vendors, and customers;

- bring-your-own-device (BYOD); and
- cloud services.
- Meanwhile, cyberattackers and the technologies they use are only getting better.
- As cyberdefenses are upgraded, attackers continue to find and exploit gaps and vulnerabilities.
- The result is a consistent arms race between attackers and defenders.
- It may be time to embrace a new cybersecurity mindset.
A New Cybersecurity Mindset
- Determined attackers will eventually penetrate any and all defenses.
- Intelligent attackers will adjust their attacks to work around the defenses they encounter.
- Therefore, defenders must not place all of their focus on attempting to stop the attacker because stopping a determined attacker is impossible.
- Enterprise defenses must value delay and detection.
- An attack that is detected can be stopped, while an attack that is not detected will progress until it eventually succeeds.
- Defenders can usually stop a discovered attack before the attack accomplishes its objective.
- Defenses must be architected to create defensible areas where detection can occur after attacks begin but before they succeed.
- Active defenders monitor and patrol these areas to find attacker activities.
- Defenders analyze attacker activities to understand what attackers are doing, where they are coming from, and so on.
- Defenders repel attacks after they are detected but before they can succeed.
- Defenders improve defenses to make future attacks more difficult.
- Analogy—How Protection Is Performed in the Physical World
- It is impossible to perfectly protect physical assets from harm or theft.
- Physical protection is designed to detect and delay attacks until authorities can arrive.
- Locks, gates, alarms, cameras, guards, and authorities all work together as a system to provide “good enough” protection.
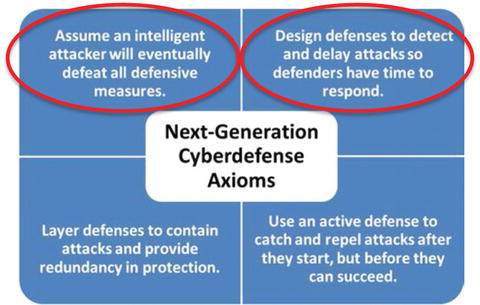
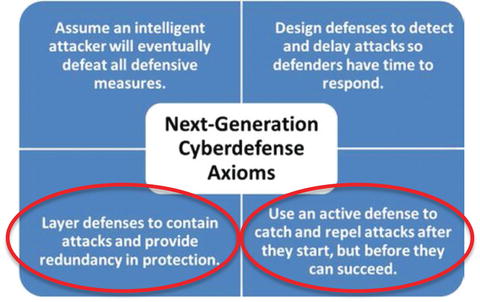
- The graphic delineates four next- generation cyberdefense axioms that can help cyberdefenders be more effective against intelligent attackers.
- 1.Assume an intelligent attacker will eventually defeat all defensive measures.
- a)An intelligent attacker is not going to walk into defenses as they are designed.
- b)An attacker is going to seek to find the easiest, fastest, and potentially cheapest attack.
- c)Enterprises must look at themselves from the attacker’s perspective and design defenses accordingly.
- a)
- 2.Design defenses to detect and delay attacks so defenders have time to respond.
- a)Prevention will inevitably fail or be defeated.
- b)When preventive controls fail or are defeated, defenses should detect the attack and delay attackers long enough for defenders to respond.
- c)Detection must be designed to catch real attacks and not overload defenders with noise from false positives.
- a)
- 3.Layer defenses to contain attacks and provide redundancy in protection.
- a)Design defenses so initial incursions, particularly in Internet-facing systems such as web servers or endpoints, can be detected when they first occur.
- b)Have additional layers of protection around the databases, file servers, and security infrastructures the attackers are really targeting.
- c)For the most critical information assets, ensure defenders have multiple opportunities to detect and respond to attacks before the attacks can succeed, and test those defense regularly.
- a)
- 4.Use an active defense to catch and repel attacks after they start, but before they can succeed.
- a)Active defense involves real people who monitor IT systems and respond to intrusions when they occur.
- b)The incident response team must diagnose attacks and repel them before the attackers can achieve their objectives.
- c)When attacks are not being detected, defense teams should be actively hunting for signs of attacker activity and seeking to improve prevention, detection, and response capabilities .
- a)
- Cybersecurity professionals
- need to achieve partial security, rather than doing everything perfectly all the time; and
- must work with the business to implement enterprise defenses that are effective relative to the business’s activities.
An Effective Enterprise Cybersecurity Program
- How is this new cybersecurity mindset turned into an effective enterprise cybersecurity program?
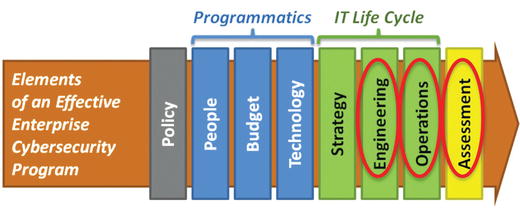
- Enterprises must pause and consider what the elements of an enterprise cybersecurity program are—policy, programmatics, IT life cycle, and assessments.
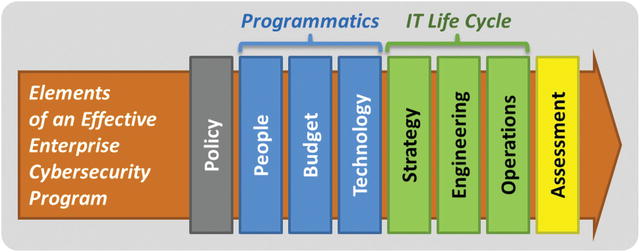
- Not only do these elements need to be coordinated, but they also need to be integrated to work well together.
- For an enterprise cybersecurity program to be effective, all elements must
- be part of a common roadmap
- be well-coordinated; and
- work effectively together.
- Otherwise, critical cybersecurity pieces fall into the gaps and are missed.
- Having the right policy is a necessary start.
- However, if the technology to implement the policy is not deployed, then the policy will not be effective.
- Having the right technology deployed is great.
- However, if the operational processes are not in place to operate and maintain the technology after deployment, then the technology will not be effective.
- If the enterprise cannot constantly assess its status and cybersecurity effectiveness to keep up with rapidly changing threats, then the program is going to fall quickly behind.
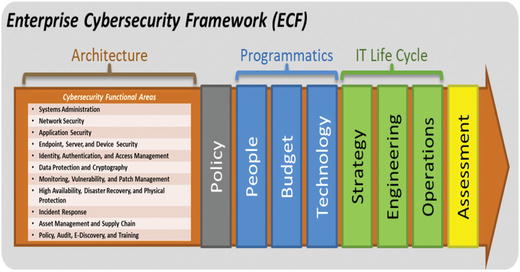
- The graphic depicts the necessary elements needed for an effective enterprise cybersecurity program.
- 1.Policy
- a)Staffing, budget, technology, and operations must trace to written policy that directs what is to be protected and to what degree as well as what the consequences are for violations.
- b)This traceability is the foundation of the entire cybersecurity program.
- c)Policy includes standards, guidelines, procedures, and baselines for the entire enterprise.
- a)
- 2.People
- a)This element organizes the people responsible for cybersecurity.
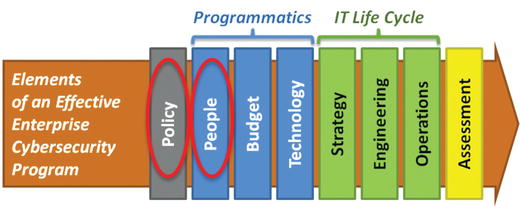
- b)These people may report to different departments of IT, operations, cybersecurity, compliance, or internal audit.
- c)People must be carefully organized so their authority, responsibility, and expertise are all in harmony with each other.
- d)Organizational lines of authority and responsibility must be carefully considered, along with organizational interfaces where departments must collaborate.
- a)
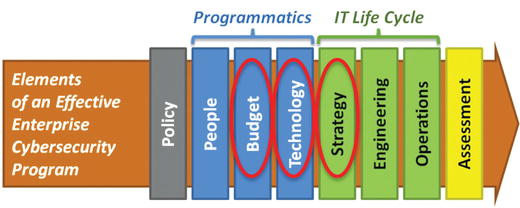
- 3.Budget
- a)Allocation of resources to pay for deploying, operating, and maintaining the cybersecurity technologies and operational processes making up the enterprise cybersecurity program must be well thought out.
- b)The amount of money allocated to each cybersecurity item must be adequate for the functional area to be effective.
- a)
- 4.Technology
- a)The size, complexity, and speed of modern IT dictate that cybersecurity cannot be accomplished manually.
- b)Cybersecurity technologies protect the enterprise by providing for prevention, detection, logging, response, and audit capabilities.
- c)The right technologies, well deployed and properly maintained, are essential to success.
- a)
- 5.Strategy
- a)Effective strategy ensures the technologies are well coordinated so they work together as integrated systems.
- b)Integration applies both to (1) cybersecurity technologies themselves and (2) cybersecurity technologies being well coordinated with the whole of the IT enterprise.
- c)Strategic disconnects can render technologies ineffective, impair enterprise productivity, or dramatically increase operational costs.
- a)
- 6.Engineering
- a)Proper engineering ensures technologies are (1) properly selected to meet requirements, (2) configured and deployed, and (3) supported so they continue to meet initial and new requirements over their life cycles.
- b)It also ensures deployed systems are “fit for purpose” and “fit for use” for as long as they are needed and used.
- a)
- 7.Operations
- a)Security technologies must be operated to stay effective.
- b)Other security operational processes such as policy exception management must also be performed.
- c)If cybersecurity is not maintained on an ongoing basis, it will become ineffective over time.
- a)
- 8.Assessment
- a)Assessment tools evaluate the effectiveness of the enterprise’s risk mitigations , cybersecurity capabilities, and operational processes.
- b)Assessment includes (1) reporting status against legal, regulatory, and compliance requirements , and (2) ensuring enterprise cybersecurity measures up to the requirements of thwarting real-world cyber adversaries.
- a)
Rest of Study Guide
- The remainder of this study guide presents a new Enterprise Cybersecurity Framework for managing a cohesive enterprise cybersecurity program in a well-coordinated and integrated manner.
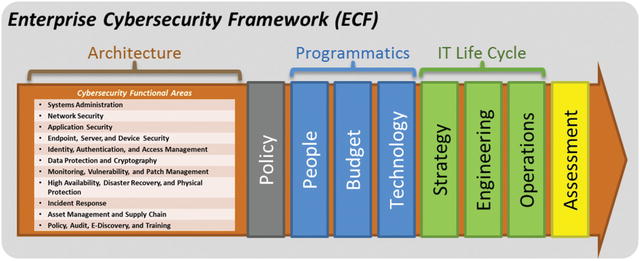
- The Enterprise Cybersecurity Framework is field-tested and field-proven for managing cyberdefenses against the most dangerous nation-state attackers.
- Enterprise cybersecurity is organized into functional areas.
- Functional areas are then used to delegate and coordinate policy, programmatics, IT life cycle, and assessments in a coherent fashion.
- Cybersecurity leadership can spend less time on integration and more time on strategy.
- Practitioners can build a cyberdefense that is flexible, cost-effective, comprehensive, and, above all, effective against today’s modern cyberthreats and tomorrow’s envisioned cyberthreats.
Footnotes
2
Eric M. Hugchins, Michael J. Cloppert, and Rohan M. Amin, Ph.D., “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains,” www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf, 2011
3
Mandiant, “APT: Exposing One of China’s Cyber Espionage Units,” http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf, 2013