CHAPTER
Protocol Tunneling |
4 |
INFORMATION IN THIS CHAPTER
• How Protocol Tunneling Works
• Dangers of Protocol Tunneling
• Defending against Protocol Tunneling
• The Future of Protocol Tunneling
You’re at work and bored as usual. You decide to take some time off from monitoring network security alerts to download some music. You hop on the Internet, download a peer-to-peer (P2P) file-sharing program, and install it on your company laptop. Nice. Now you’re ready to download.
Your first few searches don’t seem to work, and soon you’ve figured out why. At the bottom of the window is a little icon that indicates that the file-sharing program has detected a firewall. You are being blocked by your company’s Internet policies. The software needs port 45114 open, but it is closed. A little experimentation reveals that the company is blocking traffic on most ports. It’s frustrating; it is like they don’t want you downloading. Worse, the thought occurs to you that they might even monitor your Internet use.
Fortunately, you know about protocol tunneling. After a few minutes you’ve created an encrypted connection between your laptop and your home computer. Now all the P2P traffic goes through the tunnel to your computer, and then out to the Internet. Others on the P2P network can connect to your home computer and their traffic is encrypted and sent to your work laptop. Soon you are listening to music and silently laughing at the information technology (IT) department’s feeble attempts to block you. If you’ve configured everything “correctly,” others can download files from your hard drive, just as you can from theirs. This might include your music files, your tax return, your company’s host lists, or the information on the latest bid your company is planning to submit.
It now appears that a defense contractor in Bethesda, Maryland, had just such a file-sharing program installed on one of their machines. The machine also contained sensitive data: in this case, blueprints for Marine One, the helicopter that transports the President of the United States. File-sharing programs are all about sharing, and the blueprints and other information now appear to have been downloaded to a site in Iran, according to officials at Tiversa, Inc., a company that monitors P2P networks for sensitive data.A This was not a unique event.B
This particular incident may not have been a protocol-tunneling incident per se, but it does illustrate the risks. Protocol tunneling can allow employees to inadvertently subvert your company’s security policies. Worse, it can allow insiders or attackers to explicitly subvert your security policies to exfiltrate data, or establish a command and control channel for further hacking.
Unlike most of the other subjects in this text, there is nothing inherently dangerous about protocol tunneling. Sometimes it is a good thing, and sometimes it is essential for maintaining security. If your company requires you to use a virtual private network (VPN) to connect, they are requiring you to use protocol tunneling. Protocol tunneling is an essential enabling technology, but it can enable both good and bad Internet behavior.
EPIC FAIL |
Of course, you’re careful about file-sharing software and would never inadvertently share your tax return, old love letters, or your Star Trek fan script. You have nothing to worry about, right? |
Maybe. But others may have your information, too, and might not be so careful. On July 9, 2008, The Washington Post reported on an investment firm employee who decided to install and run the LimeWireC file-sharing program. When he or she did this, he or she inadvertently shared out his or her firm’s files to the world. This information included names, social security numbers, and dates of birth for about 2,000 of the firm’s clients. Among these clients was Supreme Court Justice Stephen Breyer.D |
HOW PROTOCOL TUNNELING WORKS
Simply put, protocol tunneling (or just tunneling) is using one communication protocol, say the Hypertext Transfer Protocol (HTTP) that allows the Web to function, to transmit data in another protocol, say for a P2P network.
Protocol tunneling relies on the simple fact that a communications medium that allows you to transmit information of some kind can be exploited to transmit any kind of information (though perhaps at a greatly reduced rate).
We can illustrate this with the following example. Suppose you are offered money for sensitive information from your company. Security is tight, and no electronic media can leave the site, but you do have access to a customer-facing support site set up by your company to answer customer support questions. Perfect! You wait for a customer to post a complicated question about configuration. Your reply includes a series of screenshots that show how to do the configuration. The site is monitored, but there is nothing wrong with your message. In fact, going the extra mile with the screenshots earns you an “attaboy” from your supervisor. Encoded within the screenshots is the sensitive data. You’ve just used the Internet, a blog, and digital steganography, concealment of a secret message in such a way that the existence of the secret message is itself hidden, to exfiltrate data. Software to do this encoding is readily available and easy to use.E
In general, protocol tunneling of arbitrary data through a firewall requires just three elements:
• Access to a computer inside the firewall.
• Access to a computer outside the firewall.
• A communication channel that connects the two.
If an employee or an attacker has these three items, protocol tunneling can be used to transmit data and bypass a firewall.
NOTE
Are you running Microsoft Windows Vista? It has protocol tunneling built in.
The Internet Protocol (IP) controls how data is transferred on the Internet. At present, most Internet traffic uses the IPv4 version of this protocol. IPv6 is the designated successor to IPv4, but adoption is progressing slowly because of legacy equipment and software.
If you want to use IPv6, but are sitting behind an IPv4 router, what are you to do? Well, why not tunnel IPv6 over IPv4? That’s precisely what the Teredo software that is part of Windows Vista does. This software is enabled by default.
Is this a problem? Unless your network security devices and software are Teredo-aware, this can effectively bypass them, creating a security risk. James Hoagland of Symantec wrote a paper on just this subject in 2006: “The Teredo Protocol: Tunneling Past Network Security and Other Security Implications.” F
Teredo can be disabled as follows. Open the Windows Control panel and click on system and maintenance. Click on Device manager. In the device manager, select Show Hidden Devices from the View menu. Now expand the Network Adapters node in the device list. You should see Teredo Tunneling Pseudo Interface in the list. Right-click this entry and select Disable. Also disable the 6to4 Adapter in the list.
It is probably a good idea to restart the computer after this change.
The Great Firewall
China’s Golden Shield project, widely known to the rest of the world as the Great Firewall of China, is an attempt to control access to the Internet by various methods, including blocking certain Internet addresses, blocking or redirecting specific hosts and domains, URL filtering, and even packet filtering.G Despite these efforts, there are still unblocked communications channels (or nothing would get through). This has spawned a cottage industry of tools for bypassing the Great Firewall. Some of these include the following.
• The Gollum “browser” uses advanced Web technology to allow access to the English language Wikipedia from within China.H
• Freegate and UltraSurf are anti-censorship tools that use P2P-like protocol tunnel network to transmit data.I
Setting Up a Channel with SSH
One of the most common protocol tunnels to establish is a secure shell (SSH) tunnel. This uses the SSH tool to create an encrypted tunnel between two computers. The channel encrypts and decrypts any data sent, and any information may be sent through the channel. This allows setting up secure versions of otherwise insecure connections, such as mail, File Transfer Protocol, and remote desktop. It can also be used to bypass a firewall.
Suppose you’ve discovered that you can’t access some service from work (bittorrent, instant messaging, or perhaps your favorite “graphics” site). Or perhaps you don’t like having your Internet browsing monitored. Sure, you spend most of your time at work on social networking sites arguing about whether Kirk or Picard was the best captain of the Enterprise, but that’s not your boss’ business, now is it? You decide to use SSH to create a secure tunnel, bypass the company firewall and packet monitoring system, and cloak your traffic.
Recall what is needed for protocol tunneling. You have access to your machine at work (inside the firewall), but you need access to a machine outside the firewall. There are a few possibilities.
• You can get an SSH account on an SSH provider. There are many Internet service providers (ISPs) that offer SSH accounts, at varying prices. A quick visit to Google at the time of writing turned up several sites with plans under $10 per month.J
• You might have an SSH-enabled account already. If you are a student, or if you have an alumnus account at a college, you may have an account on the school’s machines.
• You might have an always-on Internet connection at home. If so, great! You completely control a machine outside the firewall. The trick is getting to it. If your ISP gives you a different IP address every time you connect, you can use a dynamic domain name system (DNS) service to assign your machine an Internet accessible name.K
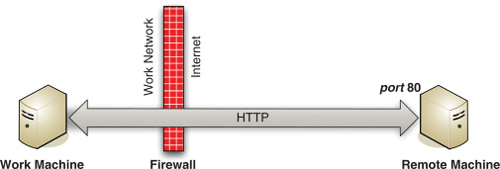
Let’s assume you want to create a tunnel for browsing the Web. Figure 4.1 illustrates the usual way of connecting to a Web site. Your machine makes a connection through the company firewall to port 80 (or port 443 for HTTPS) on the remote machine. Because your traffic passes “in the clear” through the firewall, your company IT department can monitor, or restrict, your Internet use.
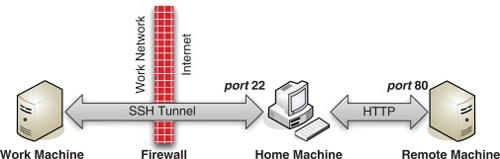
Let’s suppose your home machine is accessible as home.dynamic.example. Even better, you can get to it from work via HTTP and SSH, both of which are commonly allowed through firewalls. The desired situation is illustrated in Figure 4.2. Now only encrypted SSH traffic passes through the company firewall, to your home machine’s SSH port, port 22. Your home machine acts as a proxy, and makes a connection on your behalf with the remote machine, on port 80. Traffic again passes in both directions, but only “in the clear” between your home machine and the remote machine. Your company IT department sees only the encrypted traffic.
You will pay a penalty for this in terms of bandwidth. First, your home machine probably doesn’t have the same bandwidth as your company machine or the remote machine, so it slows down the traffic. You can possibly overcome this by leasing an SSH account from an ISP. Second, there is overhead associated with encrypting and decrypting the traffic on your work machine and your home machine, though this is small. Finally, your outgoing traffic must include both the SSH protocol traffic and your tunneled HTTP traffic. Overall, however, you will probably find this quite acceptable.
FIGURE 4.1
Usual HTTP Connection
FIGURE 4.2
Tunneling HTTP over SSH
Configuring SSH
Now that you’ve planned your tunnel, your next step is to download and install SSH software on both your work machine and your home machine. You have choices. There are both commercialL and open-source implementations.M PuTTYN is a SSH client commonly used on Windows machines. It is also common to install OpenSSH under Cygwin,O a UNIX-like environment for Windows.
Okay, you’ve downloaded and installed the OpenSSH server on your home machine. Sadly, you are not able to install software on your work machine. No problem. You only need to run the client, and you can probably run it as a regular user. Let’s assume your work machine is a Windows machine, and you plan to use PuTTY on it. You can just download the putty.exe executable, and run it locally.
Next, you need to set up a tunnel. Modern SSH clients support the SOCKSP protocol, an Internet proxy protocol. All you really need to know is that the SSH client software on your machine is going to send your Web requests to your home machine, which will forward them on to the correct host, just as you want.
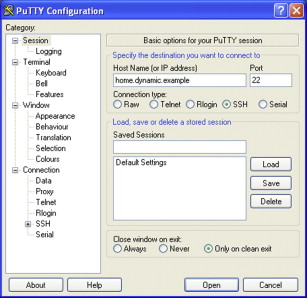
Double-click the putty.exe you downloaded earlier to start PuTTY. The PuTTY configuration dialog will open. Enter the remote host name in Host Name (Figure 4.3). If you have changed the port used by SSH (more on that in a bit), then you should set the correct port here; otherwise leave it at 22, which is the default for SSH. Do not click Open yet!
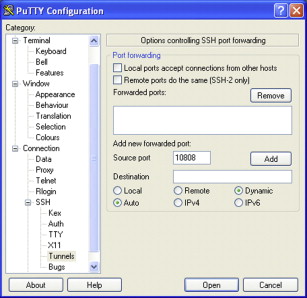
Expand SSH on the left, and then select Tunnels. You need to choose a port on your local machine that is not otherwise being used. Values above 10,000 are a fairly safe bet. Let’s say you choose 10808. Enter the port number and select Dynamic in the radio buttons. Leave the Destination field empty, and click Add. The text D10808 will appear in the list of tunnels (Figure 4.4).
FIGURE 4.3
PuTTY Configuration Dialog
FIGURE 4.4
Tunnel Configured in PuTTY
Now you are ready to connect to the remote machine that will do the proxying. Switch back to Session at the top left of the dialog, verify the host name, and click Open. Log in to your home computer. You’ve established the tunnel.
Configuring the Browser
Having the tunnel and using the tunnel are different things. By default the software on your work computer is not going to use the tunnel; you need to tell it to use it. This section will discuss the Firefox browser, as it is available on many different platforms.
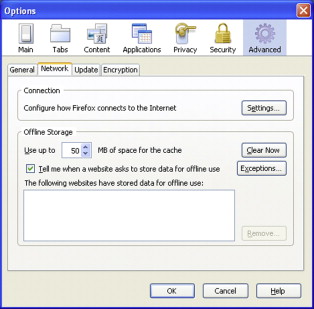
You need to tell Firefox to use port 10808 as a SOCKS v5 proxy. This is considerably easier than it sounds. From the Tools menu select Options. The Options dialog will appear. Select Advanced at the top of the dialog (Figure 4.5).
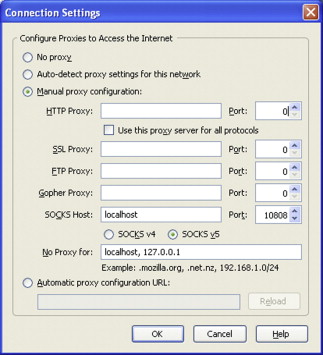
Click Settings to open the network settings dialog. This is where you will add the information about the proxy. Select manual proxy configuration and enter local-host as the SOCKS Host and 10808 as the port and click OK (Figure 4.6).
Now you can browse the Web. Firefox will transmit Web requests to port 10808, where SSH will intercept them, encrypt them, and forward them to your home machine. Your home machine will then decrypt the traffic and forward the request on to the correct host.
You can verify that this is all working correctly. There are several services on the Internet that report back your IP address, such as whatismyipaddress.com. Point your browser to one of these; you should get back the IP address of your home machine. If you do, everything is working correctly.
Tunneling DNS
There is one minor item of importance. You don’t want your boss to see your Internet traffic, and now it is encrypted: so far, so good. However, when your work computer needs to connect to a remote host, it must first look up the host name to get an IP address. The protocol used for this is called the domain name service, or DNS. Right now every DNS query is being sent “in the clear,” so everyone can see where you are browsing, even if they can’t see what you are doing.
FIGURE 4.5
Firefox Advanced Options
FIGURE 4.6
Configuring a Proxy Server in Firefox
Don’t worry, you can tunnel the DNS Protocol, too, and it is easy. In the location bar of Firefox enter the text about:config and hit Enter. You’ll get a scary warning about voiding your warranty, but keep in mind that Firefox comes with no warranty, so click the button to continue.
This page lists many different configuration options that are supported by the browser. We only want to change one: network.proxy.socks_remote_dns. Find this option and double-click it. The setting should change to true. This tells Firefox to send DNS queries to the proxy, so they get encrypted and sent over the SSH tunnel along with all other traffic.
TIP
DNS is itself a protocol; why can’t we tunnel our traffic over DNS? That’s precisely what OzymanDNS, written by Dan Kaminsky, does.Q
In hotels, airports, and other places you may encounter unencrypted public wireless Internet (WiFi). These services typically block your connection to remote hosts unless you pay a fee, but also often allow DNS queries to succeed. By tunneling your traffic over DNS, you can bypass these restrictions. The process to do this is well documented on the Web.R
Potential Problems
The first problem is that your Internet traffic now looks very suspicious. Your machine never generates any Web traffic, but generates a lot of SSH traffic destined for just one host. In reality, you probably don’t need to use the proxy for certain kinds of browsing. You can configure Firefox to enable the proxy for certain sites, but not for others. Now you will generate normal Web traffic, with an occasional SSH connection. To do this, install the FoxyProxy Firefox extension.S This will make it easy to enable and disable the proxy, and also to automatically switch for certain URLs.
Another problem is that you are generating SSH traffic destined for your home machine. The folks in IT might start to suspect you are running an SSH tunnel. One way to make this harder to detect is to change the port from the default 22 to 443. Port 443 is the port used by HTTPS, the encrypted version of the HTTP protocol. Because the traffic to port 443 is usually encrypted, your SSH traffic will look much more normal. To do this, you need to modify the port for the SSH server on your home machine, and then specify it when you start the tunnel on your work machine. To change the port, edit the SSH configuration file. For OpenSSH on Linux this is typically found in/etc/ssh/sshd_config. Edit or add the entry for Port and set it to 443. Then restart the SSH server (or just restart the machine).
Corkscrew and SSH over HTTPS
Suppose that your company has realized that someone, possibly you, may exploit SSH to create covert tunnels. They’ve proactively shut down port 22, and perhaps even installed software to detect SSH. All traffic to the outside world now goes through a proxy server, so you cannot open an arbitrary port. What are you going to do now?
Why not tunnel SSH through the proxy? After all, the proxy exists to let you get to the outside. If it all sounds too complicated, then good news: there are freely available tools to help you set this up. CorkscrewT and ProxytunnelU both focus on creating an HTTPS tunnel to allow SSH through a proxy server.
SSH over HTTP
If you can use HTTP to transmit hockey scores, wedding photos, e-mail attachments, PDF documents, and Joe Satriani’s “It’s So Good,” then why not SSH? If you can create an SSH tunnel over HTTP, then you can go ahead and create other tunnels over SSH just as before. Even HTTP. Yes, you are going to pay a price in bandwidth, but computers and corporate networks are fast, and getting faster all the time.
It may seem a bit surreal to tunnel HTTP over SSH that is in turn tunneled over HTTP, but that is just what the httptunnelV tool is for. You run an httptunnel server on your home machine and an httptunnel client on your work machine.
Automation
By now you are probably starting to complain about the dizzying technical details. “SSH? HTTPS? Acronyms? Aw...can’t someone else do all this?” Yes, of course they can. There are turn key solutions to this problem, so let’s have a look at some of them.
The Onion Router (Tor)W is an open-source implementation of “onion routing,” in which several layers of encryption are added to messages. As the messages are passed along the network, each layer of encryption is removed to determine where to send the message next, until it emerges “in the clear” at an endpoint. The primary purpose of Tor is anonymity.
On the subject of anonymity, the Swedish company Relakks runs proxy servers that allow you to tunnel your Web and other Internet traffic anonymously.X
Recall httptunnel? If you visited the Web page and read some of the documentation, you might be wondering if someone can’t make things simpler. Sure they can. There is a commercial HTTP tunnel client called, interestingly enough, HTTPTunnelClient.Y
DANGERS OF PROTOCOL TUNNELING
Protocol tunneling can explicitly bypass security restrictions. In that sense it poses a serious challenge to network security. Further, when coupled with encryption techniques like steganography it becomes nearly impossible to eliminate. The primary dangers posed by protocol tunneling are data exfiltration, hijacking, and enabling direct attacks.
WARNING
“Deep packet inspection,” where security devices and software inspect the packets to determine what their payload really is, can detect many common forms of protocol tunneling. Of course, it is still possible to “leak” information out. Steganography is the practice of transmitting information in such a way that only the sender and recipient know that there was a transmission at all. Typically the hidden message is embedded in another, typical and unremarkable, message.
It is possible to use steganography to tunnel a protocol over otherwise typical transmissions. One can queue up the data to transmit, wait for outgoing messages, and transmit the tunneled traffic over this otherwise normal traffic. Deep packet inspection will determine this to be expected traffic.Z
You should be aware of protocol steganography, as it represents a serious threat for data exfiltration that is not adequately addressed by current technologies.
Data exfiltration is the most obvious malicious application of protocol tunneling. An insider can use protocol tunneling to transmit confidential information outside the company. A tunnel, once configured and established, can serve as a back door, or reverse-connect proxy, allowing subsequent intrusion.
Creating a tunnel entails other risks as well, even if the intent of the tunnel is not malicious. The tunnel can be hijacked, allowing an intruder to compromise security. In the incident described at the beginning of this chapter, the P2P protocol was exploited to gain unauthorized access to confidential information. Older versions of the SSH protocol are subject to hijacking by a kind of man-in-the-middle attack (the subject of Chapter 6, “Man-in-the-Middle”) called SSH injection. Nearly all protocols used on the Internet allow bidirectional data transfer; if people can use the tunnel to get out, others may use it to get in.
Finally, a tunnel may be created simply to enable other malicious technologies. Chapter 1, “Denial of Service,” explains how networks of compromised machines (“botnets”) can be managed using Internet relay chat (IRC), a simple communications protocol. Tunneling IRC over another protocol makes it more difficult to detect these botnets.
Every communications channel can be exploited to create a tunnel. Even one of the simplest Internet protocols, the ICMP echo/reply, also known as ping, can be exploited to create a tunnel.AA Many Windows machines set their clocks using a protocol known as Network Time Protocol (NTP). A single NTP packet contains four 64-bit timestamp fields, or 32 bytes total. Even though 32 bytes per packet is not a lot of bandwidth, if the message to be sent is small or suitably compressed an NTP tunnel may be sufficient.
DEFENDING AGAINST PROTOCOL TUNNELING
Employees may create protocol tunnels to overcome company network policies, with no malicious intent in mind. However, when the tunnels created bypass the company firewall and network restrictions, they effectively negate a significant part of the network security plan. Whether a tunnel is created explicitly for data exfiltration, or just to enable an Internet radio station, the possibility of an intruder using the tunnel for malicious purposes exists.
As long as you allow access to a communications channel to the outside world, protocol tunneling will be possible. Defenses against this attack therefore tend to fall into one of two categories:
• taking actions to make protocol tunneling harder or less efficient, or
• detecting protocol tunnels.
Preventing Protocol Tunneling
If you decide you must make every effort to guard against protocol tunneling, the first step is to close down every unnecessary port (a good idea, anyway). This restricts the channels available to create tunnels. As we have seen, this does not make protocol tunneling impossible, but it does make it harder and may make it easier to detect.
Another strategy is to limit the allowable payload. For example, ICMP tunneling can be overcome by restricting the payload of the packets. If bandwidth is not an issue, however, any allowable variation in payload can be exploited.
An application-level gateway (ALG) can be used to augment your firewall and provide application-level filtering and control of traffic. ALGs understand a variety of protocols, from bittorrent to instant messaging, and can perform deep packet inspection, where packets are scanned to determine their purpose and information content. Because of this, an ALG can act as a kind of proxy for the application level traffic. There are a variety of ALG solutions on the market, with a wide range of functionality.BB
Open-source solutions exist, as well. Squid is a caching proxy server that also supports content filtering via access control lists (ACL).CC Dante is an implementation of the SOCKS protocol that allows for logging, bandwidth control to limit access to nonwork sites, and for implementing quality-of-service (QoS) restrictions, giving preference to certain traffic or denying other traffic.DD The redirection server rinetd is widely available, simple to configure, and can be used to redirect, deny, and log network traffic.EE
In extreme cases you may opt to block outgoing SSH and HTTPS traffic. This eliminates encrypted traffic and the common routes for tunneled traffic. This is not a perfect solution, as it is possible to tunnel SSH over other protocols, but it reduces the available bandwidth and makes tunneling more challenging.
If HTTPS is essential, you can throttle the traffic back. This reduces the bandwidth available for tunneling SSH. Normal HTTPS traffic can still go through, but since tunneled traffic requires more bandwidth it increases the time required for large-scale data exfiltration, improving the odds you will detect it through network monitoring.
Detecting Protocol Tunneling
Since protocol tunneling is possible whenever you allow traffic in and out of your network, you also need to consider a detection strategy.
Monitor your network. Intrusion-detection and intrusion-prevention systems (IDS/IPS) can be used to detect suspicious traffic. A very common IDS is Snort,FF described more fully in the Chapter 1, “Denial of Service.” This can be combined with other network monitoring software, including SANCP, a network logging and auditing tool, and Sguil, a real-time network event monitor available for most platforms.GG
Netfilter is a packet filtering framework for Linux.HH This can be combined with the L7-filters to classify packets according to protocol (HTTP, bittorrent, Kazaa, etc.), and even to detect certain kinds of protocol tunnels.II
THE FUTURE OF PROTOCOL TUNNELING
Attacks on network infrastructure are becoming both more focused and more financially motivated. Modern attacks may focus on extortion or espionage, rather than on simply gaining access. As financial incentives increase, so does the risk of data exfiltration by a trusted insider. Worse, employees may carry laptops home and, even though they may not have confidential information on their machines, at work they may access confidential sites and information. Malware on a compromised employee laptop can later be used to create a protocol tunnel to allow attackers into the laptop when it is connected to the company network.
The means to create protocol tunnels are becoming both more sophisticated (e.g., SSH over HTTP) and easier to deploy. The reliance on common of-the-shelf software and solutions for easily creating and managing protocol tunnels is troubling for the following reason: the user may not fully understand the implications of what they are doing. If an attacker determines that particular protocol tunneling software is being used, they may acquire the software themselves and reverse-engineer it to find vulnerabilities (or just wait for a published vulnerability to exploit). The pace of vulnerability detection and exploit far outstrips patching of software, especially on machines like laptops that are not always on, and which move around to a variety of untrusted networks.
Fortunately, the ability to detect unauthorized tunnels is improving as well. Data occupies space. The amount of space per unit of data may vary, but bits do correspond to something physical: space on a DVD, a data thumb, printed pages, or a signal on a wire. This is the basic idea of bandwidth. If you have to transmit one protocol over another protocol, even Transmission Control Protocol over IP, then you pay a penalty in overhead. This idea can potentially be exploited to detect covert channels.JJ
Researchers at the University of California at San Diego have been developing a system called Glavlit to vet all information before it is allowed to leave the network to prevent data exfiltration by either overt or covert channels.KK The idea is that the only data allowed to travel out of the network is preauthorized data. Information that is to be sent out of the network is first sent to a warden that employs some mechanism to determine whether to allow or deny the transmission. Although this approach guarantees that data leaving the network has been vetted, it cannot guarantee that sensitive data is not exfiltrated using steganographic or other cloaking techniques. If the data to be transmitted is small, it can even be encoded in the delay between transmissions, or in time stamps of transmitted data. Despite this, Glavlit looks like a promising technology to prevent bulk data exfiltration.
Other approaches rely on detecting suspicious traffic using statistical methods. Tunnel Hunter uses statistical fingerprinting and profiling techniques to detect covert tunnels with high accuracy.LL Driving down the bandwidth of a covert channel does not necessarily help avoid detection with this approach. Instead, one should drive up the volume of legitimate (or legitimate looking) traffic in relation to the covert payload.
SUMMARY
Data exfiltration by protocol tunneling is a serious concern, and by its very nature protocol tunneling is impossible to perfectly defeat. This chapter explained how protocol tunneling is used, and detailed some of the methods for defense against this attack. You should have an understanding of why protocol tunneling is difficult to completely prevent, but also have understand basic steps you can take to protect against protocol tunneling.
Awww.wpxi.com/news/19377076/detail.html
BFor another example of data exfiltration using P2P network software, see the article “Army Special Forces Document Leaked On P2P Network,” in SC Magazine. At the time of writing, this was available online from www.scmagazineus.com/Army-Special-Forces-document-leaked-on-P2P-network/article/151309/.
Dwww.washingtonpost.com/wp-dyn/content/article/2008/07/08/AR2008070802997.html
EBitCrypt is one open-source steganographic tool for hiding information in images. The information is first encrypted and then the encrypted message is hidden in an image. At the time of writing, BitCrypt is available for free from http://bitcrypt.moshe-szweizer.com/.
FThe paper is available from Symantec’s Web site: www.symantec.com/.
GOn May 20, 2008, the U.S. Senate Judiciary Committee held a hearing titled “Global Internet Freedom: Corporate Responsibility and the Rule of Law” that discusses both Internet censorship and the technologies that are used to bypass it. At the time of writing the webcast and transcripts are available from http://judiciary.senate.gov/. In particular, Dr. Shiyu Zhou discussed China’s Golden Shield project and the role of U.S. companies operating in China.
IFreegate: www.dit-inc.us/freegate/. UltraSurf: www.ultrareach.com/.
JThe site www.red-pill.eu/freeunix.shtml lists (at the time of writing) several free shell providers, including http://freeshell.org/ and www.grex.org/.
KAgain, a quick trip to Google reveals several free dynamic DNS services. DHIS (www.dhis.org/) and DynDNS (http://www.dyndns.com/www.dyndns.com/) both provide free dynamic DNS services.
LSee SSH Communications Security Croporation, http://ssh.com/.
MSee OpenSSH, http://openssh.com/.
Nhttp://chiark.greenend.org.uk/~sgtatham/putty/.
Phttp://tools.ietf.org/html/rfc1928
SFirefox extensions can be found at https://addons.mozilla.org/en-US/firefox/.
Uhttp://proxytunnel.sourceforge.net/
Vwww.nocrew.org/software/httptunnel.html
ZThis approach is explored in the paper “Syntax and Semantics-Preserving Application-Layer Protocol Steganography,” by Norka Lucena, James Pease, Payman Yadollahpour, and Steve Chapin, in Lecture Notes in Computer Science, volume 3200/2005, Springer, Berlin, 2005.
AASee Ping Tunnel, www.cs.uit.no/~daniels/PingTunnel/.
BBSome examples are the following: BalaBit IT Security (www.balabit.com/) sells Zorp, a “perimeter defense” tool for implementing application level network policies, including quality-of-service (QoS). Cisco (www.cisco.com/) includes an ALG in IOS, the operating system for much of their hardware. AEP Networks (www.aepnetworks.com/) produces SmartGate, a ALG solution.
DDDante is an open-source application with a variety of free and commercial modules to modify its functionality. It can be obtained from Inferno Nettverk, A/S (www.inet.no/dante).
EEwww.boutell.com/rinetd/index.html
GGhttp://sguil.sourceforge.net/
II“L7” refers to the application layer in the OSI network layer model. The L7-filters can be found at http://l7-filter.sourceforge.net/.
JJAnnarita Giani et al. used this idea to define the covertness of a channel as the difference between the capacity of the channel and the transmission rate. A very low transmission rate for a high-capacity tunnel provides fewer opportunities to observe transmission. See their paper “Data Exfiltration and Covert Channels,” in Proceedings of the SPIE Defense and Security Symposium, Orlando, Florida, April 2006.
KKNabil Schear, Carmelo Kintana, Qing Zhang, and Amin Vahdat, “Glavlit: Preventing Exfiltration at Wire Speed.” Proceedings of the 5th ACM Workshop on Hot Topics in Networks (HotNets-V), November 2006.
LLSee MD, et al., “Detection of Encrypted Tunnels Across Network Boundaries,” in Proceedings of the IEEE International Conference on Communications (ICC), Beijing, May 2008.