Chapter 3
Network Security Concepts
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
What is the current state of cybersecurity and vectors of data loss?
What tools do threat actors use to exploit networks?
What are the types of malware?
What are common network attacks?
How are IP vulnerabilities exploited by threat actors?
How are TCP and UDP vulnerabilities exploited by threat actors?
How are IP services exploited by threat actors?
What are the best practices for protecting a network?
What are the common cryptographic processes used to protect data in transit?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
denial-of-service (DoS) attack page 96
state-sponsored hacker page 100
network penetration testing page 102
man-in-the-middle (MITM) attack page 105
reconnaissance attack page 109
distributed denial of service (DDoS) page 116
command and control (CnC) page 116
amplification and reflection attack page 118
address spoofing attack page 118
access control list (ACL) page 118
TCP session hijacking page 126
DNS open resolver attack page 131
DNS domain shadowing attack page 131
defense-in-depth approach page 138
intrusion detection system (IDS) page 140
intrusion prevention system (IPS) page 140
Cisco Adaptive Security Appliance (ASA) page 140
Cisco Email Security Appliance (ESA) page 142
Cisco Web Security Appliance (WSA) page 142
Message Digest version 5 (MD5) page 144
Secure Hash Algorithm (SHA) page 144
origin authentication page 144
hash message authentication code (HMAC) page 144
symmetric encryption algorithm page 150
Introduction
Perhaps you’ve heard one of the hundreds of news stories about data security breaches within a large corporation or even a government. Was your credit card number exposed by a breach? Or perhaps your private health information? Would you like to know how to prevent these data breaches? The field of network security is growing every day. This chapter provides details about the types of cybercrime and the many ways we have to fight back against cybercriminals. Let’s get started!
Ethical Hacking Statement (3.0.3)
This chapter introduces tools and techniques used by cybercriminals to demonstrate various types of attacks. Unauthorized access to data, computer, and network systems is a crime in many jurisdictions and often is accompanied by severe consequences, regardless of the perpetrator’s motivations. It is your responsibility, as the user of this material, to be cognizant of and compliant with computer use laws.
Current State of Cybersecurity (3.1)
Network breaches are now routinely reported in the media. Many of them involve high-profile organizations, celebrities, and governments. How were these attacks conducted, and what were the threat actors looking for? This section describes the current state of cybersecurity and vectors of data loss.
Current State of Affairs (3.1.1)
Cybercriminals now have the expertise and tools necessary to disrupt critical infrastructure and systems. Their tools and techniques continue to evolve.
Cybercriminals are taking malware to unprecedented levels of sophistication and impact. They are becoming more adept at using stealth and evasion techniques to hide their activity. In addition, cybercriminals are exploiting undefended gaps in security.
Network security breaches can disrupt e-commerce, cause the loss of business data, threaten people’s privacy, and compromise the integrity of information. Corporate breaches can result in lost revenue, theft of intellectual property, and lawsuits, and they can even threaten public safety.
Maintaining a secure network ensures the safety of network users and protects commercial interests. Organizations need individuals who can recognize the speed and scale at which adversaries are amassing and refining their cyber weaponry. All users should be aware of the security terms in Table 3-1.
Table 3-1 Common Security Terms
Security Terms |
Description |
An asset is anything of value to an organization, including people, equipment, resources, and data. |
|
A vulnerability is a weakness in a system, or its design, that could be exploited by a threat. |
|
A threat is a potential danger to a company’s assets, data, or network functionality. |
|
An exploit is a mechanism that takes advantage of a vulnerability. |
|
Mitigation refers to the countermeasures that reduce the likelihood or severity of a potential threat or risk. Network security involves multiple mitigation techniques. |
|
Risk is the likelihood of a threat to exploit the vulnerability of an asset, with the aim of negatively affecting an organization. Risk is measured using the probability of the occurrence of an event and its consequences. |
Assets must be identified and protected. Vulnerabilities must be addressed before they become threats and are exploited. Mitigation techniques are required before, during, and after an attack.
Vectors of Network Attacks (3.1.2)
An attack vector is a path by which a threat actor can gain access to a server, host, or network. Attack vectors originate from inside or outside a corporate network, as shown in Figure 3-1. For example, threat actors may target a network through the internet to disrupt network operations and create a denial-of-service (DoS) attack.
An internal user, such as an employee, can accidentally or intentionally:
Steal and copy confidential data to removable media, email, messaging software, and other media.
Compromise internal servers or network infrastructure devices.
Disconnect a critical network connection and cause a network outage.
Connect an infected USB drive to a corporate computer system.
Internal threats have the potential to cause greater damage than external threats because internal users have direct access to the building and its infrastructure devices. Employees may also have knowledge of the corporate network, its resources, and its confidential data.
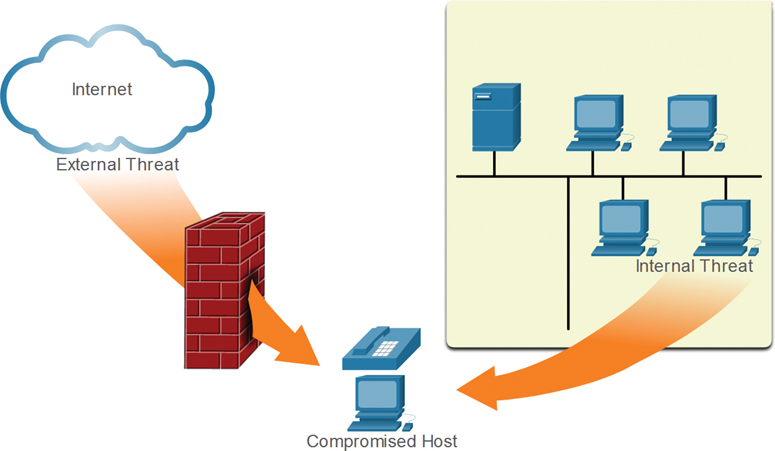
Figure 3-1 External and Internal Attack Vectors
Note
A DoS attack occurs when a network device or application is incapacitated and no longer capable of supporting requests from legitimate users.
Network security professionals must implement tools and apply techniques for mitigating both external and internal threats.
Data Loss (3.1.3)
Data is likely to be an organization’s most valuable asset. Organizational data can include research and development data, sales data, financial data, human resource and legal data, employee data, contractor data, and customer data.
Data loss or data exfiltration occurs when data is intentionally or unintentionally lost, stolen, or leaked to the outside world. The data loss can result in:
Brand damage and loss of reputation
Loss of competitive advantage
Loss of customers
Loss of revenue
Litigation/legal action resulting in fines and civil penalties
Significant cost and effort to notify affected parties and recover from the breach
Table 3-2 lists common data loss vectors.
Table 3-2 Data Loss Vectors
Data Loss Vector |
Description |
Email/social networking |
Intercepted email or IM messages could be captured and reveal confidential information. |
Unencrypted devices |
If the data is not stored using an encryption algorithm, then the thief can retrieve valuable confidential data. |
Cloud storage devices |
Sensitive data can be lost if access to the cloud is compromised due to weak security settings. |
Removable media |
One risk is that an employee could perform an unauthorized transfer of data to a USB drive. Another risk is that a USB drive containing valuable corporate data could be lost. |
Hard copy |
Confidential data should be shredded when no longer required. |
Improper access control |
Passwords or weak passwords which have been compromised can provide a threat actor with easy access to corporate data. |
Network security professionals must protect the organization’s data. Various data loss prevention (DLP) controls must be implemented to combine strategic, operational, and tactical measures.
Check Your Understanding—Current State of Cybersecurity (3.1.4)

Refer to the online course to complete this activity.
Threat Actors (3.2)
This section describes the threat actors.
The Hacker (3.2.1)
In the previous section, you took a high-level look at the current landscape of cybersecurity, including the types of threats and vulnerabilities that plague all network administrators and architects. In this section, you will learn more details about particular types of threat actors.
Hacker is a common term used to describe a threat actor. Originally the term referred to someone who was a skilled computer expert such as a programmer and a hack was a clever solution. The term later evolved into what we know of it today.
As shown in Table 3-3, the terms white hat hacker, black hat hacker, and gray hat hacker are often used to describe types of hackers.
Table 3-3 Hacker Types
Hacker Type |
Description |
White hat hackers |
|
Gray hat hackers |
|
Black hat hackers |
|
Note
In this book, we do not use the term hacker outside of this chapter. Instead, we use the term threat actor. The term threat actor includes hackers, and it also refers to any other device, person, group, or nation-state that is, intentionally or unintentionally, the source of an attack.
Evolution of Hackers (3.2.2)
Hacking started in the 1960s with phone freaking, or phreaking, which refers to using audio frequencies to manipulate phone systems. At that time, telephone switches used various tones to indicate different functions. Early hackers realized that by mimicking a tone using a whistle, they could exploit the phone switches to make free long-distance calls.
In the mid-1980s, computer dialup modems were used to connect computers to networks. Hackers wrote “war dialing” programs that dialed each telephone number in a given area, in search of computers. When a computer was found, password-cracking programs were used to gain access.
Table 3-4 lists some modern hacking terms and a brief description of each.
Table 3-4 Common Hacking Terms
Hacking Term |
Description |
|
|
|
|
|
|
Cybercriminals |
|
|
Cyber Criminals (3.2.3)
It is estimated that cybercriminals steal billions of dollars from consumers and businesses. Cybercriminals operate in an underground economy where they buy, sell, and trade attack toolkits, zero-day exploit code, botnet services, banking Trojans, keyloggers, and much more. They also buy and sell the private information and intellectual property they steal. Cybercriminals target small businesses and consumers, as well as large enterprises and entire industries.
Hacktivists (3.2.4)
Two examples of hacktivist groups are Anonymous and the Syrian Electronic Army. Although most hacktivist groups are not well organized, they can cause significant problems for governments and businesses. Hacktivists tend to rely on fairly basic, freely available tools.
State-Sponsored Hackers (3.2.5)
State-sponsored hackers create advanced, customized attack code, often using previously undiscovered software vulnerabilities called zero-day vulnerabilities. An example of a state-sponsored attack is the use of the Stuxnet malware to damage Iran’s nuclear enrichment capabilities.
Check Your Understanding—Threat Actors (3.2.6)

Refer to the online course to complete this activity.
Threat Actor Tools (3.3)
What do threat actors use to carry out their nefarious deeds?
This section introduces some of the tools that threat actors use to attack networks.
Video—Threat Actor Tools (3.3.1)

Refer to the online course to view this video.
Introduction to Attack Tools (3.3.2)
To exploit a vulnerability, a threat actor must have a technique or tool. Over the years, attack tools have become more sophisticated and highly automated. These new tools require less technical knowledge to implement than did some of the older tools.
Figures 3-2 and 3-3 demonstrate the relationship between the sophistication of attack tools and the technical knowledge required to use them in 1985 and now.

Figure 3-2 Sophistication of Attack Tools vs. Technical Knowledge (1985)

Figure 3-3 Sophistication of Attack Tools vs. Technical Knowledge (Now)
Evolution of Security Tools (3.3.3)
Ethical hacking involves using many different types of tools to test a network and keep its data secure. To validate the security of a network and its systems, many network penetration testing tools have been developed. Unfortunately, many of these tools can be used by black hat hackers for exploitation.
Black hat hackers have also created many hacking tools. These tools are created explicitly for nefarious reasons. White hat hackers must also know how to use these tools when performing network penetration tests.
Table 3-5 highlights categories of common penetration testing tools. Notice how some tools are used by white hats and black hats. Keep in mind that the list is not exhaustive as new tools are always being developed.
Table 3-5 Penetration Testing Tools
Penetration Testing Tool Category |
Description |
Password crackers |
|
Wireless hacking tools |
|
Network scanning and hacking tools |
|
Packet crafting tools |
|
Packet sniffers |
|
Rootkit detectors |
|
Fuzzers to search vulnerabilities |
|
Forensic tools |
|
Debuggers |
|
Hacking operating systems |
|
Encryption tools |
|
Vulnerability exploitation tools |
|
Vulnerability scanners |
|
Note
Many of these tools are UNIX or Linux based; therefore, a security professional should have a strong UNIX and Linux background.
Attack Types (3.3.4)
Threat actors can use the previously mentioned attack tools or a combination of tools to create attacks. Table 3-6 lists some common types of attacks. However, this list of attacks is not exhaustive as new attack vulnerabilities are constantly being discovered.
Table 3-6 Attack Types
Attack Type |
Description |
Eavesdropping attack |
|
Data modification attack |
|
IP address spoofing attack |
|
Password-based attacks |
|
Denial-of-service (DoS) attack |
|
|
|
Compromised-key attack |
|
Sniffer attack |
|
Check Your Understanding—Threat Actor Tools (3.3.5)

Refer to the online course to complete this activity.
Malware (3.4)
How do threat actors get victims to enable their attacks? They trick them into installing malicious code (malware). Malware is software that is designed to exploit a target host. There are many different types of malware, including viruses, worms, Trojan horses, ransomware, spyware, adware, and scareware.
This section describes the various types of malware used by threat actors.
Overview of Malware (3.4.1)
Now that you know about the tools that hackers use, this section introduces you to different types of malware that hackers use to gain access to end devices.
End devices are particularly prone to malware attacks. It is important to know about malware because threat actors rely on users to install malware to help exploit security gaps.
The primary vulnerabilities for end-user workstations are virus, worm, and Trojan Horse attacks:
A worm executes arbitrary code and installs copies of itself in the memory of the infected computer. The main purpose of a worm is to automatically replicate itself and spread across the network from system to system.
A virus is malicious software that executes a specific, unwanted, and often harmful function on a computer.
A Trojan horse is a non-self-replicating type of malware. It often contains malicious code that is designed to look like something else, such as a legitimate application or file. When an infected application or file is downloaded and opened, the Trojan horse can attack the end device from within.
Viruses and Trojan Horses (3.4.2)
The most common type of computer malware is a virus. Viruses require human action to propagate and infect other computers. For example, a virus can infect a computer when a victim opens an email attachment, opens a file on a USB drive, or downloads a file.
The virus hides by attaching itself to computer code, software, or documents on the computer. When opened, the virus executes and infects the computer.
Viruses can
Alter, corrupt, delete files, or erase entire drives
Cause computer booting issues and corrupt applications
Capture and send sensitive information to threat actors
Access and use email accounts to spread themselves
Lay dormant until summoned by the threat actor
Modern viruses are developed for specific intents, such as those listed in Table 3-7.
Table 3-7 Types of Viruses
Types of Viruses |
Description |
Boot sector virus |
Attacks the boot sector, file partition table, or file system. |
Firmware virus |
Attacks the device firmware. |
Macro virus |
Uses the macro feature in Microsoft Office or other applications maliciously. |
Program virus |
Inserts itself in another executable program. |
Script virus |
Attacks the OS interpreter, which is used to execute scripts. |
Threat actors use Trojan horses to compromise hosts. A Trojan horse is a program that looks useful but that carries malicious code. Trojan horses are often provided with free online programs such as computer games. Unsuspecting users download and install the game and get the Trojan horse, too.
As described in Table 3-8, there are several types of Trojan horses.
Table 3-8 Types of Trojan Horses
Type of Trojan Horse |
Description |
Remote access |
Enables unauthorized remote access. |
Data sending |
Provides the threat actor with sensitive data, such as passwords. |
Destructive |
Corrupts or deletes files. |
Proxy |
Uses the victim’s computer as the source device to launch attacks and perform other illegal activities. |
FTP |
Enables unauthorized file transfer services on end devices. |
Security software disabler |
Stops antivirus programs or firewalls from functioning. |
Denial of service (DoS) |
Slows or halts network activity. |
Keylogger |
Actively attempts to steal confidential information, such as credit card numbers, by recording keystrokes entered into a web form. |
Other Types of Malware (3.4.3)
Viruses and Trojan horses are only two types of malware that threat actors use. There are many other types of malware that have been designed for specific purposes. Table 3-9 describes some of the many different types of malware.
Table 3-9 Other Types of Malware
Type of Malware |
Description |
Adware |
|
|
|
Rootkit |
|
Spyware |
|
Worm |
|
Check Your Understanding—Malware (3.4.4)

Refer to the online course to complete this activity.
Common Network Attacks (3.5)
Networks are targets. A threat actor who gains administrative access to a corporate network infrastructure can steal data, delete data, and disrupt network availability. Threat actors commonly use three types of network attacks to achieve their objectives, as discussed in this section.
Overview of Network Attacks (3.5.1)
As you have learned, there are many types of malware that hackers can use. But these are not the only ways that they can attack a network or even an organization.
When malware is delivered and installed, the payload can be used to cause a variety of network-related attacks.
To mitigate attacks, it is useful to understand the types of attacks. By categorizing network attacks, it is possible to address types of attacks rather than individual attacks.
Networks are susceptible to the following types of attacks:
DoS attacks
Video—Reconnaissance Attacks (3.5.2)

Refer to the online course to view this video.
Reconnaissance Attacks (3.5.3)
Reconnaissance is information gathering. It is analogous to a thief surveying a neighborhood by going door-to-door, pretending to sell something but actually looking for vulnerable homes to break into, such as unoccupied residences, residences with easy-to-open doors or windows, and residences without security systems or security cameras.
Threat actors use reconnaissance (or recon) attacks to do unauthorized discovery and mapping of systems, services, or vulnerabilities. Recon attacks precede access attacks or DoS attacks.
Some of the techniques used by malicious threat actors to conduct reconnaissance attacks are described in Table 3-10.
Table 3-10 Reconnaissance Attack Techniques
Technique |
Description |
Perform an information query of a target |
|
Initiate a ping sweep of the target network |
|
Initiate a port scan of active IP addresses |
|
Run vulnerability scanners |
|
Run exploitation tools |
|
Video—Access and Social Engineering Attacks (3.5.4)

Refer to the online course to view this video.
Access Attacks (3.5.5)
Access attacks exploit known vulnerabilities in authentication services, FTP services, and web services. The purpose of these types of attacks is to gain entry to web accounts, confidential databases, and other sensitive information.
Threat actors use access attacks on network devices and computers to retrieve data, gain access, or escalate access privileges to administrator status. These are the two main types of access attacks:
Password attack: In a password attack, the threat actor attempts to discover critical system passwords using various methods. Password attacks are very common and can be launched using a variety of password cracking tools.
Spoofing attack: In a spoofing attack, the threat actor device attempts to pose as another device by falsifying data. Common spoofing attacks include IP spoofing, MAC spoofing, and DHCP spoofing. These spoofing attacks are discussed in more detail later in this chapter.
Other access attacks include
Trust exploitations
Port redirections
Man-in-the-middle attacks
Buffer overflow attacks
Trust Exploitation Example
In a trust exploitation attack, a threat actor uses unauthorized privileges to gain access to a system, possibly compromising the target. Figure 3-4 shows an example of a trust exploitation.
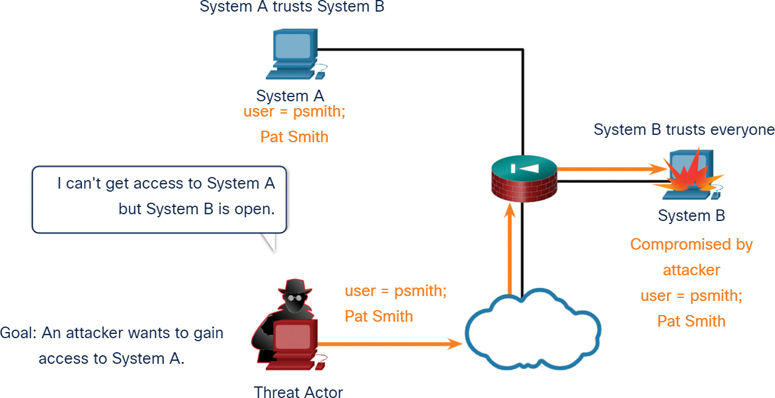
Figure 3-4 Trust Exploitation Example
Port Redirection Example
In a port redirection attack, a threat actor uses a compromised system as a base for attacks against other targets. The example in Figure 3-5 shows a threat actor using SSH (port 22) to connect to a compromised Host A. Host A is trusted by Host B and, therefore, the threat actor can use Telnet (port 23) to access it.
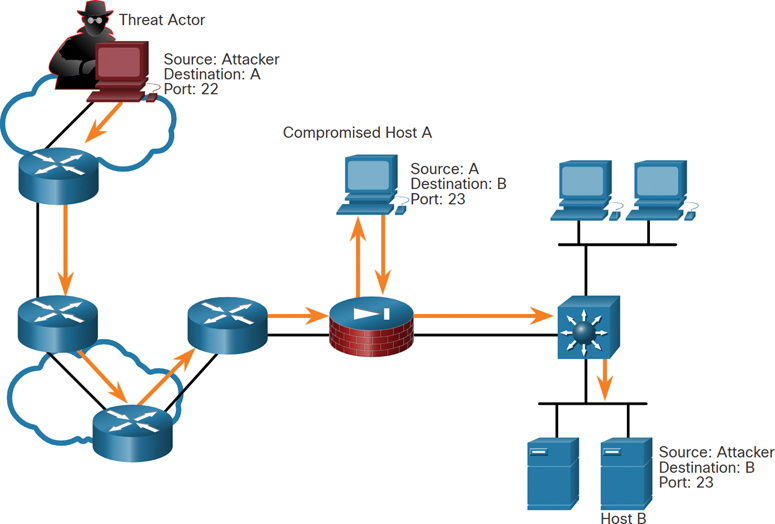
Figure 3-5 Port Redirection Example
Man-in-the-Middle Attack Example
In a man-in-the-middle attack, the threat actor is positioned in between two legitimate entities in order to read or modify the data that passes between the two parties. Figure 3-6 shows an example of a man-in-the-middle attack.
Buffer Overflow Attack
In a buffer overflow attack, the threat actor exploits the buffer memory and overwhelms it with unexpected values. This usually renders the system inoperable, creating a DoS attack. Figure 3-7 shows a threat actor sending many packets to the victim in an attempt to overflow the victim’s buffer.
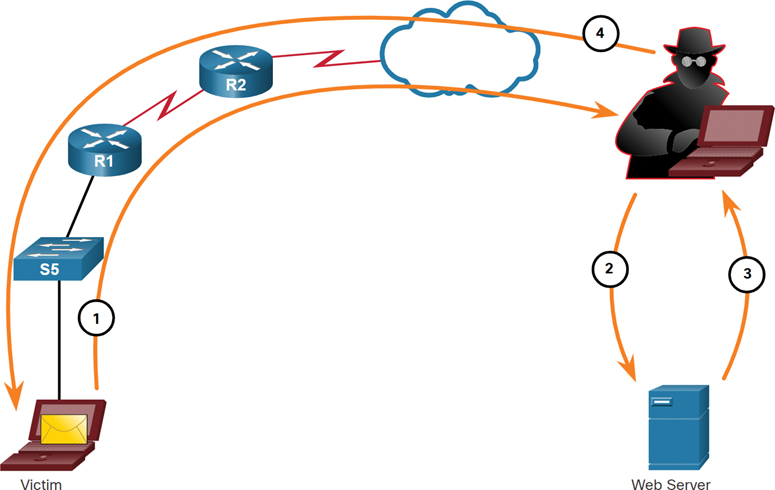
Figure 3-6 Man-in-the-Middle Attack Example

Figure 3-7 Buffer Overflow Attack
Social Engineering Attacks (3.5.6)
Social engineering is an access attack that attempts to manipulate individuals into performing actions or divulging confidential information. Some social engineering techniques are performed in person, and others occur over the telephone or internet.
Social engineers often rely on people’s willingness to be helpful. They also prey on people’s weaknesses. For example, a threat actor could call an authorized employee with an urgent problem that requires immediate network access. The threat actor could appeal to the employee’s vanity, invoke authority using name-dropping techniques, or appeal to the employee’s greed.
Information about social engineering techniques is shown in Table 3-11.
Table 3-11 Social Engineering Attacks
Social Engineering Attack |
Description |
Pretexting |
A threat actor pretends to need personal or financial data to confirm the identity of the recipient. |
A threat actor sends fraudulent email disguised as being from a legitimate, trusted source to trick the recipient into installing malware on a device or into sharing personal or financial information. |
|
Spear phishing |
A threat actor creates a targeted phishing attack tailored for a specific individual or organization. |
Also known as junk mail, spam is unsolicited email that often contains harmful links, malware, or deceptive content. |
|
Something for something |
Sometimes called Quid pro quo, this is an attack in which a threat actor requests personal information from a party in exchange for something such as a gift. |
Baiting |
A threat actor leaves a malware-infected flash drive in a public location. A victim finds the drive and inserts it into a laptop, unintentionally installing malware. |
Impersonation |
In this type of attack, a threat actor pretends to be someone else in order to gain the trust of a victim. |
Tailgating |
A threat actor quickly follows an authorized person into a secure location to gain access to a secure area. |
Shoulder surfing |
A threat actor inconspicuously looks over someone’s shoulder to steal passwords or other information. |
Dumpster diving |
A threat actor rummages through trash bins to discover confidential documents. |
The Social Engineering Toolkit (SET) was designed to help white hat hackers and other network security professionals create social engineering attacks to test their own networks.
Enterprises must educate their users about the risks of social engineering and develop strategies to validate identities over the phone, via email, and in person.
The following are recommended practices that should be followed by all users:
Never give your username and password credentials to anyone.
Never leave your username and password credentials where they can easily be found.
Never open emails from untrusted sources.
Never release work-related information on social media sites.
Never reuse work-related passwords.
Always lock or sign out of your computer when leaving it unattended.
Always report suspicious individuals.
Always destroy confidential information according to organization policy.
Lab—Social Engineering (3.5.7)
![]()
In this lab, you will research examples of social engineering and identify ways to recognize and prevent it.
Video—Denial of Service Attacks (3.5.8)

Refer to the online course to view this video.
DoS and DDoS Attacks (3.5.9)
A denial-of-service (DoS) attack creates some sort of interruption of network services to users, devices, or applications. There are two major types of DoS attacks:
Overwhelming quantity of traffic: The threat actor sends an enormous quantity of data at a rate that the network, host, or application cannot handle. This causes transmission and response times to slow down. It can also crash a device or service.
Maliciously formatted packets: The threat actor sends a maliciously formatted packet to a host or an application, and the receiver is unable to handle it. This causes the receiving device to run very slowly or crash.
DoS Attack
DoS attacks are a major risk because they interrupt communication and cause significant loss of time and money. These attacks are relatively simple to conduct, even by an unskilled threat actor.
Figure 3-8 shows an example of a DoS attack.
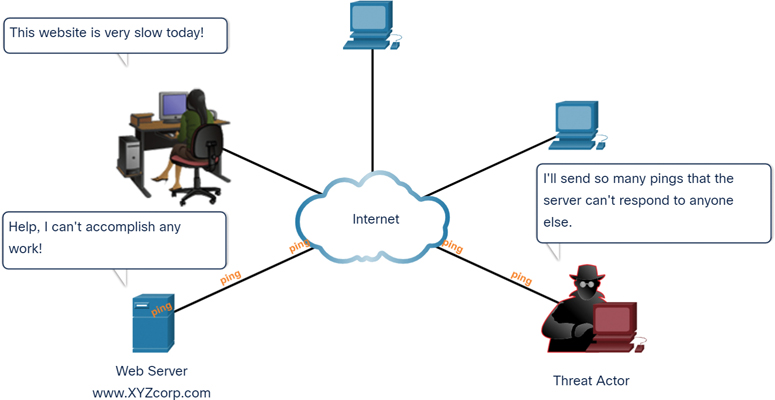
Figure 3-8 DoS Attack Example
DDoS Attack
A distributed denial-of-service (DDoS) attack is similar to a DoS attack, but it originates from multiple, coordinated sources. For example, a threat actor builds a network of infected hosts, known as zombies. The threat actor uses a command and control (CnC) system to send control messages to the zombies. The zombies constantly scan and infect more hosts with bot malware. The bot malware is designed to infect a host, making it a zombie that can communicate with the CnC system. The collection of zombies is called a botnet. Eventually, the threat actor instructs the CnC system to make the botnet of zombies carry out a DDoS attack.
Figure 3-9 shows an example of a DDoS attack.

Figure 3-9 DDoS Attack Example
Check Your Understanding—Common Network Attacks (3.5.10)

Refer to the online course to complete this activity.
IP Vulnerabilities and Threats (3.6)
Internet Protocol (IP) and Internet Control Message Protocol (ICMP) are required for network communication. Computers and networks use IP to provide the addressing for local and remote network reachability, and they use ICMP to provide messaging services for IP. However, threat actors have discovered IP and ICMP vulnerabilities that they exploit to leverage their attacks.
This section explains how IP vulnerabilities are exploited by threat actors.
Video—Common IP and ICMP Attacks (3.6.1)

Refer to the online course to view this video.
IPv4 and IPv6 (3.6.2)
IP does not validate whether a packet actually came from the source IP address contained in the packet. For this reason, threat actors can send packets using a spoofed source IP address. Threat actors can also tamper with the other fields in the IP header to carry out their attacks. Security analysts must therefore understand the different fields in both the IPv4 and IPv6 headers.
Some of the most common IP-related attacks are described in Table 3-12.
Table 3-12 IP Attacks
IP Attack Techniques |
Description |
Threat actors use ICMP echo packets (pings) to discover subnets and hosts on a protected network, to generate DoS flood attacks, and to alter host routing tables. |
|
Threat actors attempt to prevent legitimate users from accessing information or services by using DoS and DDoS attacks. |
|
Threat actors spoof the source IP address in an IP packet to perform blind spoofing or non-blind spoofing. |
|
Man-in-the-middle (MITM) attacks |
Threat actors position themselves between a source and destination to transparently monitor, capture, and control the communication. They could eavesdrop by inspecting captured packets or alter packets and forward them to their original destination. |
Session hijacking |
Threat actors gain access to the physical network and then use an MITM attack to hijack a session. |
ICMP Attacks (3.6.3)
Threat actors use ICMP for reconnaissance and scanning attacks. They can launch information-gathering attacks to map out a network topology, discover which hosts are active (reachable), identify the host operating system (OS fingerprinting), and determine the state of a firewall. Threat actors also use ICMP for DoS attacks.
Note
ICMP for IPv4 (ICMPv4) and ICMP for IPv6 (ICMPv6) are susceptible to similar types of attacks.
Networks should have strict ICMP access control list (ACL) filtering at the network edge to avoid ICMP probing from the internet. Security analysts should be able to detect ICMP-related attacks by looking at captured traffic and log files. In the case of large networks, security devices such as firewalls and intrusion detection systems (IDSs) detect such attacks and send alerts to the security analysts.
Common ICMP messages of interest to threat actors are listed in Table 3-13.
Table 3-13 ICMP Messages as Attack Vectors
ICMP Messages Used by Hackers |
Description |
ICMP echo request and echo reply |
Used to perform host verification and DoS attacks. |
ICMP unreachable |
Used to perform network reconnaissance and scanning attacks. |
ICMP mask reply |
Used to map an internal IP network. |
ICMP redirects |
Used to lure a target host into sending all traffic through a compromised device and create an MITM attack. |
ICMP router discovery |
Used to inject bogus route entries into the routing table of a target host. |
Video—Amplification, Reflection, and Spoofing Attacks (3.6.4)

Refer to the online course to view this video.
Amplification and Reflection Attacks (3.6.5)
Threat actors often use amplification and reflection techniques to create DoS attacks. The example in Figure 3-10 illustrates how an amplification and reflection technique called a Smurf attack is used to overwhelm a target host.
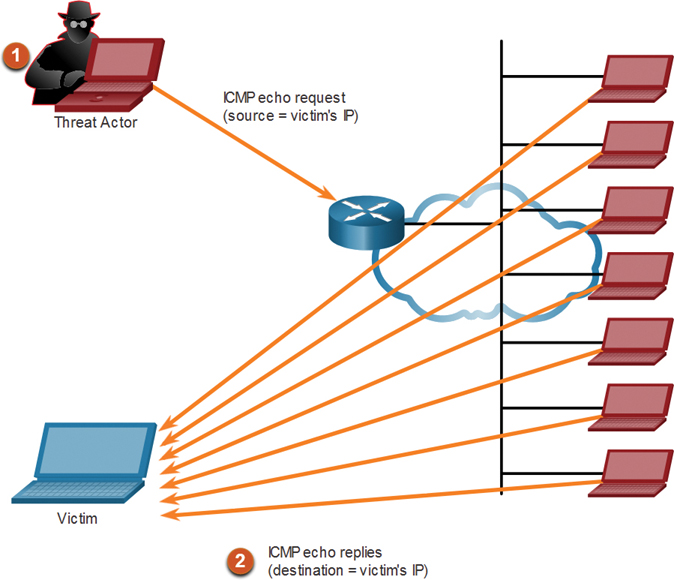
Figure 3-10 Amplification and Reflection Example
In the figure:
Amplification: The threat actor forwards ICMP echo request messages to many hosts. These messages contain the source IP address of the victim.
Reflection: These hosts all reply to the spoofed IP address of the victim to overwhelm it.
Note
Newer forms of amplification and reflection attacks such as DNS-based reflection and amplification attacks and Network Time Protocol (NTP) amplification attacks are now being used.
Threat actors also use resource exhaustion attacks. These attacks consume the resources of a target host to either crash it or consume the resources of a network.
Address Spoofing Attacks (3.6.6)
IP address spoofing attacks occur when a threat actor creates packets with false source IP address information to either hide the identity of the sender or to pose as another legitimate user. The threat actor can then gain access to otherwise inaccessible data or circumvent security configurations. Spoofing is usually incorporated into another attack, such as a Smurf attack.
Spoofing attacks can be non-blind or blind:
Non-blind spoofing: The threat actor can see the traffic that is being sent between the host and the target. The threat actor uses non-blind spoofing to inspect the reply packet from the target victim. Non-blind spoofing determines the state of a firewall and sequence-number prediction. It can also hijack an authorized session.
Blind spoofing: The threat actor cannot see the traffic that is being sent between the host and the target. Blind spoofing is used in DoS attacks.
MAC address spoofing attacks are used when threat actors have access to the internal network. Threat actors alter the MAC address of the host to match another known MAC address of a target host, as shown in Figure 3-11. The attacking host then sends a frame throughout the network with the newly configured MAC address. When the switch receives the frame, it examines the source MAC address.

Figure 3-11 Threat Actor Spoofs a Server’s MAC Address
The switch overwrites the current Content Addressable Memory (CAM) table entry and assigns the MAC address to the new port, as shown in Figure 3-12. It then forwards frames destined for the target host to the attacking host.

Figure 3-12 Switch Updates CAM Table with Spoofed Address
Application or service spoofing is another type of spoofing. With such an attack, a threat actor connects a rogue DHCP server to create an MITM condition.
Check Your Understanding—IP Vulnerabilities and Threats (3.6.7)

Refer to the online course to complete this activity.
TCP and UDP Vulnerabilities (3.7)
TCP and UDP are required for network communication. Application layer protocols require TCP or UDP services to function properly. However, threat actors have discovered TCP and UDP vulnerabilities that they exploit to leverage their attacks.
This section explains how TCP and UDP vulnerabilities are exploited by threat actors.
TCP Segment Header (3.7.1)
This section discusses attacks that target TCP and UDP. TCP segment information appears immediately after the IP header. The fields of the TCP segment are shown in Figure 3-13.

Figure 3-13 TCP Header
The flags for the six Control Bits field are as follows:
URG: Urgent pointer field significant
ACK: Acknowledgment field significant
PSH: Push function
RST: Reset the connection
SYN: Synchronize sequence numbers
FIN: No more data from sender
TCP Services (3.7.2)
TCP provides these services:
Reliable delivery: TCP incorporates acknowledgments to guarantee delivery instead of relying on upper-layer protocols to detect and resolve errors. If a timely acknowledgment is not received, the sender retransmits the data. Requiring acknowledgments of received data can cause substantial delays. Examples of application layer protocols that make use of TCP reliability include HTTP, SSL/TLS, FTP, and DNS zone transfers.
Flow control: TCP implements flow control to help minimize the delays introduced by reliable delivery. Rather than acknowledge one segment at a time, multiple segments can be acknowledged with a single acknowledgment segment.
Stateful communication: TCP stateful communication between two parties occurs during the TCP three-way handshake. Before data can be transferred using TCP, a three-way handshake opens the TCP connection, as shown in Figure 3-14. If both sides agree to the TCP connection, data can be sent and received by both parties using TCP.

Figure 3-14 TCP Three-Way Handshake
The figure demonstrates a TCP connection established in three steps:
Step 1. The initiating client requests a client-to-server communication session with the server.
Step 2. The server acknowledges the client-to-server communication session and requests a server-to-client communication session.
Step 3. The initiating client acknowledges the server-to-client communication session.
TCP Attacks (3.7.3)
Network applications use TCP or UDP ports. Threat actors conduct port scans of target devices to discover which services they offer.
TCP SYN Flood Attack
A TCP SYN flood attack exploits the TCP three-way handshake. Figure 3-15 shows a threat actor continually sending TCP SYN session request packets with a randomly spoofed source IP address to a target. The target device replies with a TCP SYN-ACK packet to the spoofed IP address and waits for a TCP ACK packet. Those responses never arrive. Eventually, the target host is overwhelmed with half-open TCP connections, and TCP services are denied to legitimate users.

Figure 3-15 TCP SYN Flood Attack
The following steps occur in Figure 3-15:
Step 1. The threat actor sends multiple SYN requests to a web server.
Step 2. The web server replies with SYN-ACKs for each SYN request and waits to complete the three-way handshake. The threat actor does not respond to the SYN-ACKs.
Step 3. A valid user cannot access the web server because the web server has too many half-opened TCP connections.
TCP Reset Attack
A TCP reset attack can be used to terminate TCP communications between two hosts. TCP can terminate a connection in a civilized (that is, normal) manner or in an uncivilized (that is, abrupt) manner.
Figure 3-16 shows the civilized manner, with TCP using a four-way exchange consisting of a pair of FIN and ACK segments from each TCP endpoint to close the TCP connection.
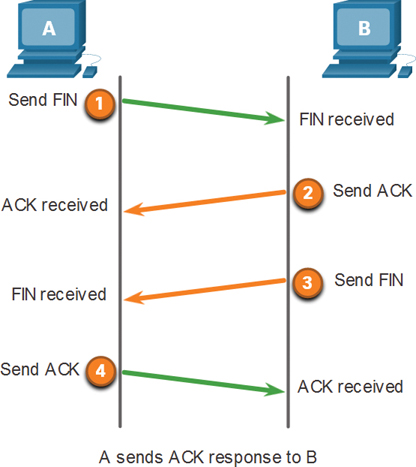
Figure 3-16 TCP Reset Attack
In the figure, terminating a TCP session uses the following four-way exchange process:
Step 1. When the client has no more data to send in the stream, it sends a segment with the FIN flag set.
Step 2. The server sends an ACK to acknowledge the receipt of the FIN to terminate the session from client to server.
Step 3. The server sends a FIN to the client to terminate the server-to-client session.
Step 4. The client responds with an ACK to acknowledge the FIN from the server.
With the uncivilized manner, a host receives a TCP segment with the RST bit set. This is an abrupt way to tear down the TCP connection and inform the receiving host to immediately stop using the TCP connection.
A threat actor could do a TCP reset attack and send a spoofed packet containing a TCP RST to one or both endpoints.
TCP Session Hijacking
TCP session hijacking takes advantage of another TCP vulnerability, although it can be difficult to conduct. A threat actor takes over an already authenticated host as it communicates with the target. The threat actor must spoof the IP address of one host, predict the next sequence number, and send an ACK to the other host. If successful, the threat actor can send (although not receive) data from the target device.
UDP Segment Header and Operation (3.7.4)
UDP is commonly used by DNS, TFTP, NFS, and SNMP. It is also used with real-time applications such as media streaming and VoIP. UDP is a connectionless transport layer protocol. It has much lower overhead than TCP because it is not connection oriented and does not offer the sophisticated retransmission, sequencing, and flow control mechanisms that provide reliability. The UDP segment structure, shown in Figure 3-17, is much smaller than TCP’s segment structure.
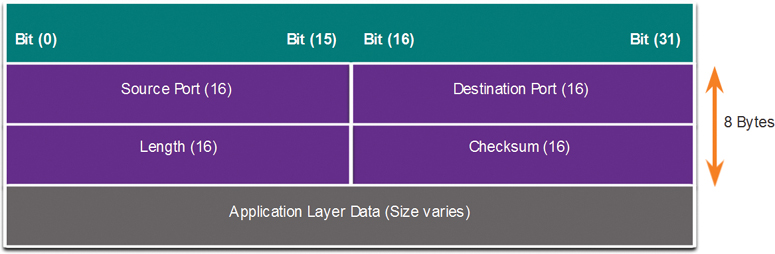
Figure 3-17 UDP Header
Although UDP is normally said to be unreliable (in contrast to TCP’s reliability), this does not mean that applications that use UDP are always unreliable, nor does it mean that UDP is an inferior protocol. It means that these functions are not provided by the transport layer protocol and must be implemented elsewhere, if required.
The low overhead of UDP makes it very desirable for protocols that make simple request-and-reply transactions. For example, using TCP for DHCP would introduce unnecessary network traffic. If no response is received, the device re-sends the request.
UDP Attacks (3.7.5)
UDP is not protected by any encryption. You can add encryption to UDP, but it is not available by default. The lack of encryption means that anyone can see the traffic, change it, and send it on to its destination. Changing the data in the traffic will alter the 16-bit checksum, but the checksum is optional and is not always used. When the checksum is used, the threat actor can create a new checksum based on the new data payload and then record it in the header as a new checksum. The destination device will find that the checksum matches the data without knowing that the data has been altered. This type of attack is not widely used.
UDP Flood Attacks
You are more likely to see a UDP flood attack. In a UDP flood attack, all the resources on a network are consumed. The threat actor must use a tool like UDP Unicorn or Low Orbit Ion Cannon. These tools send a flood of UDP packets, often from a spoofed host, to a server on the subnet. The program sweeps through all the known ports, trying to find closed ports. This causes the server to reply with an ICMP port unreachable message. Because there are many closed ports on the server, this creates a lot of traffic on the segment, which uses up most of the bandwidth. The result is very similar to the result of a DoS attack.
Check Your Understanding—TCP and UDP Vulnerabilities (3.7.6)

Refer to the online course to complete this activity.
IP Services
IP services include ARP, DNS, DHCP, and SLAAC. ARP resolves IPv4 addresses to MAC address, DNS resolves names to IP addresses, and DHCP and SLAAC automate the assignment of IP configurations on networks. However, threat actors have discovered IP service vulnerabilities that they exploit to leverage their attacks.
This section explains how IP services are exploited by threat actors.
ARP Vulnerabilities (3.8.1)
Earlier in this chapter, you learned about vulnerabilities with IP, TCP, and UDP. The TCP/IP protocol suite was not built for security. Therefore, the services that IP uses for addressing functions—such as ARP, DNS, and DHCP—are also not secure, as you will learn in this section.
Hosts broadcast an ARP Request to other hosts on the segment to determine the MAC address of a host with a particular IPv4 address, as shown in Figure 3-18. All hosts on the subnet receive and process the ARP Request. The host with the matching IPv4 address in the ARP Request sends an ARP Reply.

Figure 3-18 The ARP Process
Any client can send an unsolicited ARP Reply called a gratuitous ARP. This is often done when a device first boots up to inform all other devices on the local network of the new device’s MAC address. When a host sends a gratuitous ARP, other hosts on the subnet store the MAC address and IPv4 address contained in the gratuitous ARP in their ARP tables.
This feature of ARP also means that any host can claim to be the owner of any IPv4 or MAC address. A threat actor can poison the ARP caches of devices on the local network, creating an MITM attack to redirect traffic. The goal is to target a victim host and have it change its default gateway to the threat actor’s device. This positions the threat actor in between the victim and all other systems outside the local subnet.
ARP Cache Poisoning (3.8.2)
ARP cache poisoning can be used to launch various man-in-the-middle attacks.
ARP Request
Figure 3-19 shows how ARP cache poisoning works. In this example, PC-A requires the MAC address of its default gateway (R1); therefore, it sends an ARP Request for the MAC address 192.168.10.1.
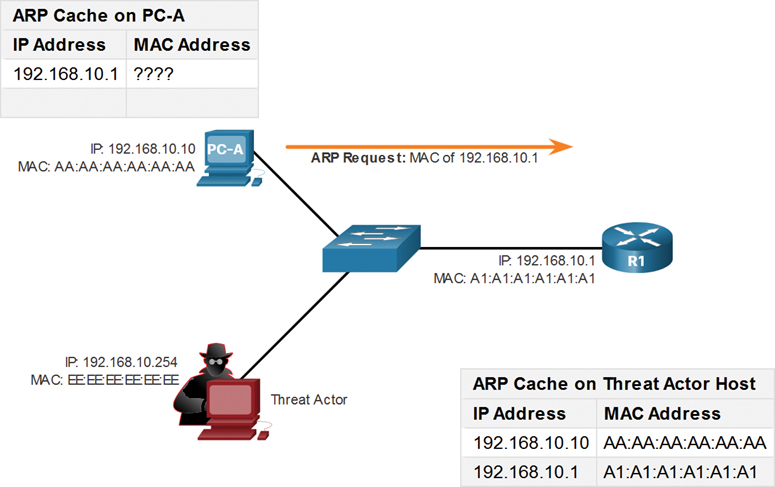
Figure 3-19 ARP Request to Poison the Cache on Other Devices
ARP Reply
In Figure 3-20, R1 updates its ARP cache with the IPv4 and MAC addresses of PC-A. R1 sends an ARP Reply to PC-A, which then updates its ARP cache with the IPv4 and MAC addresses of R1.

Figure 3-20 Devices Unknowingly Update the Cache with the Threat Actor’s MAC Address
Spoofed Gratuitous ARP Replies
In Figure 3-21, the threat actor sends two spoofed gratuitous ARP Replies using its own MAC address for the indicated destination IPv4 addresses. PC-A updates its ARP cache with its default gateway, which is now pointing to the threat actor’s host MAC address. R1 also updates its ARP cache with the IPv4 address of PC-A pointing to the threat actor’s MAC address.
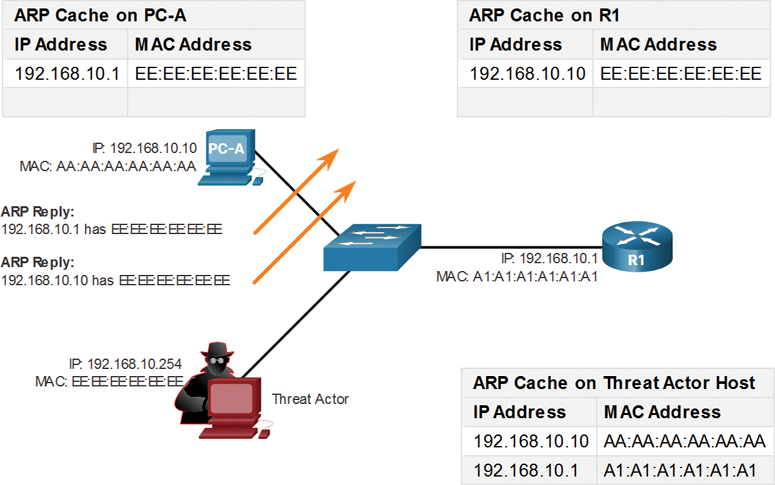
Figure 3-21 Threat Actor Sends Spoofed Gratuitous ARP Replies
The threat actor’s host is executing an ARP poisoning attack. An ARP poisoning attack can be passive or active. With passive ARP poisoning, a threat actor steals confidential information. With active ARP poisoning, a threat actor modifies data in transit or injects malicious data.
Note
There are many tools available on the internet to create ARP MITM attacks, including dsniff, Cain & Abel, ettercap, and Yersinia.
Video—ARP Spoofing (3.8.3)

Refer to the online course to view this video.
DNS Attacks (3.8.4)
The Domain Name System (DNS) protocol defines an automated service that matches resource names, such as www.cisco.com, with the required numeric network address, such as the IPv4 or IPv6 address. It includes the format for queries, responses, and data and uses resource records (RRs) to identify the type of DNS response.
Securing DNS is often overlooked. However, DNS is crucial to the operation of a network and should be secured accordingly.
DNS attacks include the following:
DNS Open Resolver Attacks
Many organizations use the services of publicly open DNS servers such as GoogleDNS (8.8.8.8) to provide responses to queries. This type of DNS server is called an open resolver. A DNS open resolver answers queries from clients outside its administrative domain. DNS open resolvers are vulnerable to multiple malicious activities, as described in Table 3-14.
Table 3-14 DNS Resolver Attacks
DNS Resolver Attack |
Description |
DNS cache poisoning attack |
Threat actors send spoofed, falsified resource record (RR) information to a DNS resolver to redirect users from legitimate sites to malicious sites. DNS cache poisoning attacks can be used to inform the DNS resolver to use a malicious name server that is providing RR information for malicious activities. |
DNS amplification and reflection attack |
Threat actors use DoS or DDoS attacks on DNS open resolvers to increase the volume of attacks and to hide the true source of an attack. Threat actors send DNS messages to the open resolvers, using the IP address of a target host. These attacks are possible because the open resolver will respond to queries from anyone asking a question. |
DNS resource utilization attack |
This DoS attack consumes all the available resources to negatively affect the operations of the DNS open resolver. The impact of this DoS attack may require the DNS open resolver to be rebooted or services to be stopped and restarted. |
DNS Stealth Attacks
To hide their identity, threat actors may use the DNS stealth techniques described in Table 3-15 to carry out their attacks.
Table 3-15 DNS Stealth Techniques
DNS Stealth Technique |
Description |
Fast flux |
Threat actors use this technique to hide their phishing and malware delivery sites behind a quickly changing network of compromised DNS hosts. The DNS IP addresses are continuously changed every few minutes. Botnets often employ fast flux techniques to effectively prevent malicious servers from being detected. |
Double IP flux |
Threat actors use this technique to rapidly change the hostname-to-IP address mappings and to also change the authoritative name server. This increases the difficulty of identifying the source of an attack. |
Domain generation algorithms |
Threat actors use these algorithms in malware to randomly generate domain names that can then be used as rendezvous points to their command and control (CnC) servers. |
DNS Domain Shadowing Attacks
With domain shadowing, a threat actor gathers domain account credentials in order to silently create multiple subdomains to be used during attacks. These subdomains typically point to malicious servers without alerting the actual owner of the parent domain.
DNS Tunneling (3.8.5)
Threat actors who use DNS tunneling place non-DNS traffic within DNS traffic. This method is often used to circumvent security solutions when a threat actor wishes to communicate with bots inside a protected network or exfiltrate data from the organization, such as a password database. When the threat actor uses DNS tunneling, the different types of DNS records are altered. This is how DNS tunneling works for CnC commands sent to a botnet:
Step 1. The command data is split into multiple encoded chunks.
Step 2. Each chunk is placed into a lower-level domain name label of the DNS query.
Step 3. Because there is no response from the local or networked DNS for the query, the request is sent to the ISP’s recursive DNS servers.
Step 4. The recursive DNS service forwards the query to the threat actor’s authoritative name server.
Step 5. The process is repeated until all the queries containing the chunks of data are sent.
Step 6. When the threat actor’s authoritative name server receives the DNS queries from the infected devices, it sends responses for each DNS query, which contain the encapsulated, encoded CnC commands.
Step 7. The malware on the compromised host recombines the chunks and executes the commands hidden within the DNS record.
To stop DNS tunneling, the network administrator must use a filter that inspects DNS traffic. Pay close attention to DNS queries that are longer than average, as well as those that have a suspicious domain name. DNS solutions such as Cisco OpenDNS block a lot of DNS tunneling traffic by identifying suspicious domains.
DHCP (3.8.6)
DHCP servers dynamically provide IP configuration information to clients. Figure 3-22 shows the typical sequence of a DHCP message exchange between client and server.

Figure 3-22 DHCP Operation
DHCP Attacks (3.8.7)
A DHCP spoofing attack occurs when a rogue DHCP server is connected to the network and provides false IP configuration parameters to legitimate clients. A rogue server can provide a variety of misleading information, including the following:
Wrong default gateway: The threat actor provides an invalid gateway or the IPv4 address of its host to create an MITM attack. This may go entirely undetected as the intruder intercepts the data flow through the network.
Wrong DNS server: The threat actor provides an incorrect DNS server address pointing the user to a malicious website.
Wrong IPv4 address: The threat actor provides an invalid IP address, invalid default gateway IPv4 address, or both. The threat actor then creates a DoS attack on the DHCP client.
Note
An IPv6 device receives its default gateway address from the Router Advertisement instead of from a DHCP server.
Say that a threat actor has successfully connected a rogue DHCP server to a switch port on the same subnet as the target clients. The goal of the rogue server is to provide clients with false IPv4 configuration information.
The following sections describe the steps in a DHCP spoofing attack.
1. Client Broadcasts DHCP Discovery Messages
In Figure 3-23, a legitimate client connects to the network and requires IP configuration parameters. The client broadcasts a DHCP Discover request, looking for a response from a DHCP server. Both servers receive the message.
2. DHCP Servers Respond with Offers
Figure 3-24 shows how the legitimate and rogue DHCP servers each respond with valid IP configuration parameters. The client replies to the first offer received.
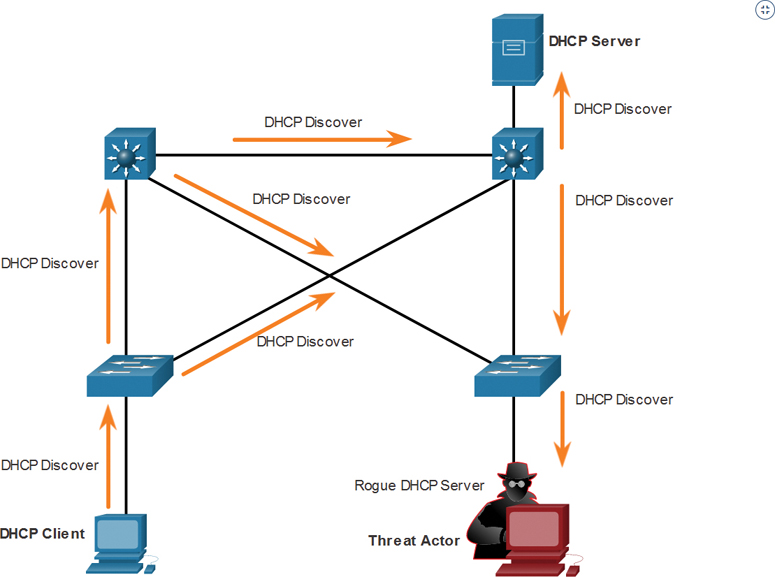
Figure 3-23 Client Broadcasts DHCP Discovery Messages
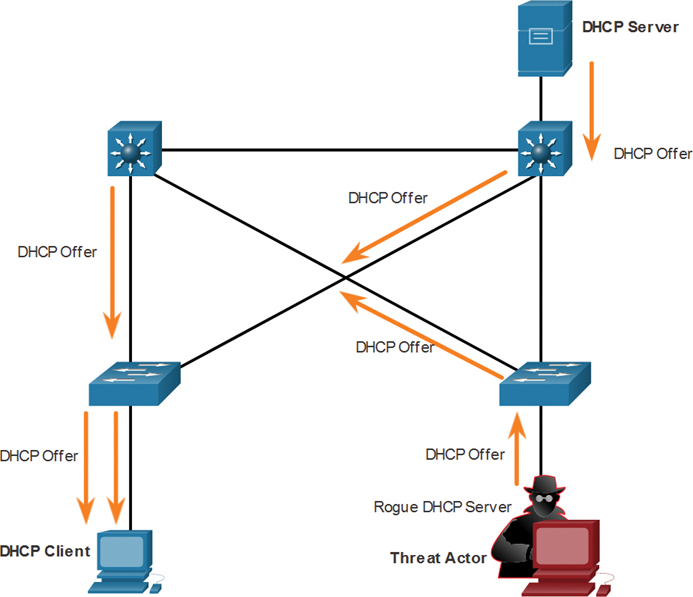
Figure 3-24 DHCP Servers Respond with Offers
3. Client Accepts Rogue DHCP Request
In this scenario, the client received the rogue offer first. It broadcasts a DHCP request accepting the parameters from the rogue server, as shown in Figure 3-25. The legitimate and rogue server each receive the request.

Figure 3-25 Client Accepts Rogue DHCP Request
4. Rogue DHCP Acknowledges the Request
Only the rogue server unicasts a reply to the client to acknowledge its request, as shown in Figure 3-26. The legitimate server stops communicating with the client because the request has already been acknowledged.
Lab—Explore DNS Traffic (3.8.8)
![]()
In this lab, you will complete the following objectives:
Capture DNS traffic
Explore DNS query traffic
Explore DNS response traffic
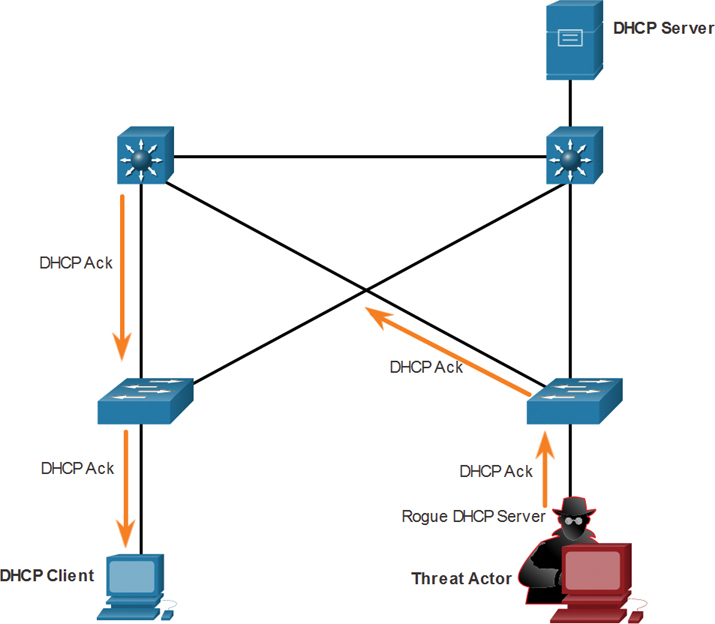
Figure 3-26 Rogue DHCP Acknowledges the Request
Network Security Best Practices (3.9)
IP services include ARP, DNS, and DHCP. ARP resolves IP addresses to MAC address, DNS resolves names to IP addresses, and DHCP automates the assignment of IP configurations on networks. Threat actors have discovered vulnerabilities in IP services that they can exploit to leverage their attacks.
This section describes the best practices for protecting a network.
Confidentiality, Integrity, and Availability (3.9.1)
It is true that the list of network attack types is long. But there are many best practices that you can use to defend your network, as you will learn in this section.
Network security consists of protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction.
Most organizations follow the CIA information security triad:
Confidentiality: Only authorized individuals, entities, or processes are allowed to access sensitive information. This confidentiality may require using cryptographic encryption algorithms such as AES to encrypt and decrypt data.
Integrity: This refers to protecting data from unauthorized alteration. Integrity requires the use of cryptographic hashing algorithms such as SHA.
Availability: Authorized users must have uninterrupted access to important resources and data. Availability requires implementing redundant services, gateways, and links.
The Defense-in-Depth Approach (3.9.2)
To ensure secure communications across both public and private networks, you must secure devices including routers, switches, servers, and hosts. Most organizations employ a defense-in-depth approach to security, also known as a layered approach. It requires a combination of networking devices and services working together. Consider the network in Figure 3-27.
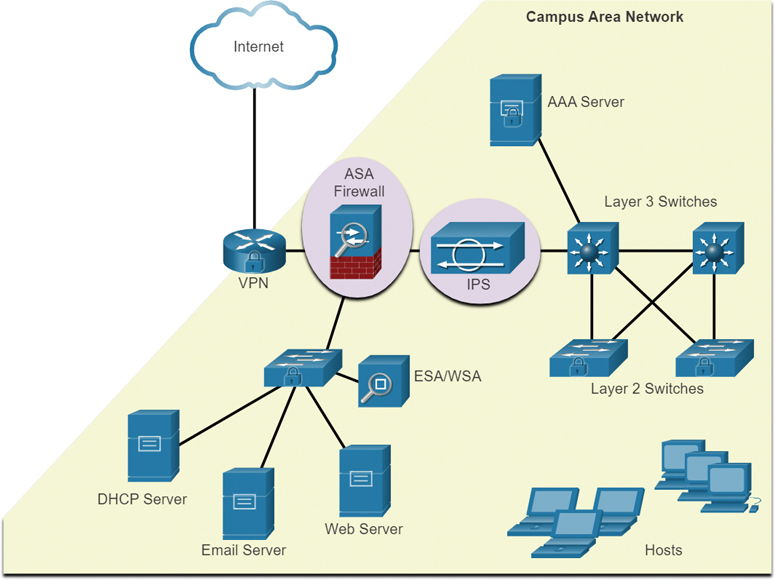
Figure 3-27 Protecting Against Network Attacks
In the network in this figure, all network devices including the router and switches are hardened, which means that they have been secured to prevent threat actors from gaining access and tampering with the devices.
It is important to secure data as it travels across various links. This may include internal traffic, but it is more important to protect the data that travels outside the organization to branch sites, telecommuter sites, and partner sites.
Firewalls (3.9.3)
A firewall is a system or group of systems that enforce an access control policy between networks. For example, in Figure 3-28, traffic arriving from any global sites on the internet is filtered through a firewall device. Based on configured policies, some traffic is allowed, and some traffic is denied.
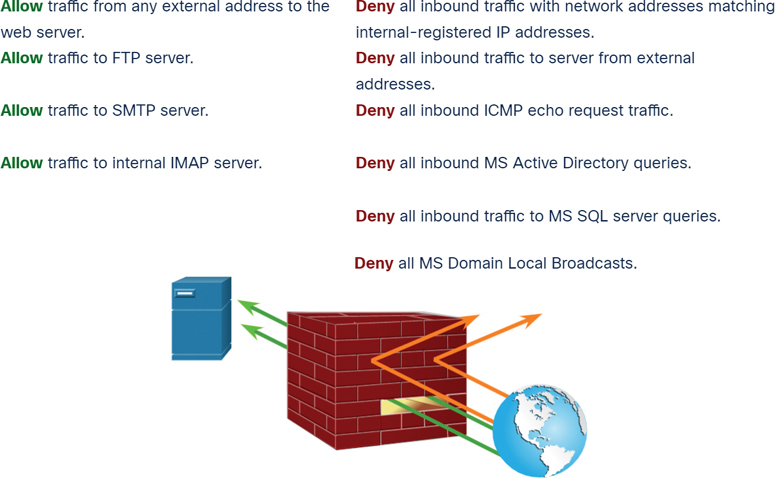
Figure 3-28 Firewall Operation
All firewalls share some common properties:
Firewalls are resistant to network attacks.
Firewalls are the only transit points between internal corporate networks and external networks because all traffic flows through the firewall.
Firewalls enforce the access control policy.
There are several benefits of using firewalls in a network:
They prevent the exposure of sensitive hosts, resources, and applications to untrusted users.
They sanitize protocol flow, which prevents the exploitation of protocol flaws.
They block malicious data from servers and clients.
They reduce security management complexity by offloading most of the network access control to a few firewalls in the network.
Firewalls also present some limitations:
A misconfigured firewall can have serious consequences for the network, such as becoming a single point of failure.
The data from many applications cannot be passed through firewalls securely.
Users might proactively search for ways around the firewall to receive blocked material, which can potentially expose the network to attack.
Network performance can slow down.
Unauthorized traffic can be tunneled or hidden so that it appears as legitimate traffic through the firewall.
IPS (3.9.4)
To defend against fast-moving and evolving attacks, you may need cost-effective detection and prevention systems, such as intrusion detection systems (IDSs) or the more scalable intrusion prevention systems (IPSs). The network architecture integrates these solutions into the entry and exit points of the network.
IDS and IPS technologies share several characteristics. IDS and IPS technologies are both deployed as sensors. An IDS or IPS sensor can be in the form of several different devices:
A router configured with Cisco IOS IPS software
A device specifically designed to provide dedicated IDS or IPS services
A network module installed in a Cisco Adaptive Security Appliance (ASA), switch, or router
Figure 3-29 shows how an IPS handles denied traffic:
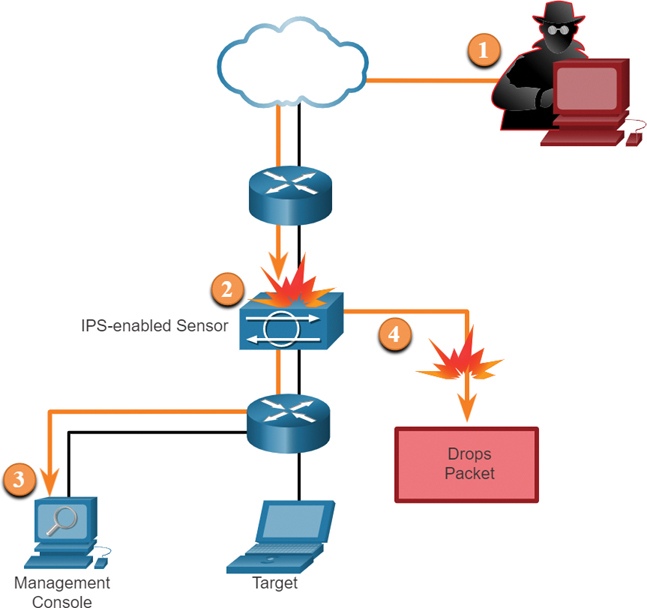
Figure 3-29 IPS Operation
Step 1. The threat actor sends a packet destined for the target laptop.
Step 2. The IPS intercepts the traffic and evaluates it against known threats and the configured policies.
Step 3. The IPS sends a log message to the management console.
Step 4. The IPS drops the packet.
IDS and IPS technologies detect patterns in network traffic by using signatures. A signature is a set of rules that an IDS or IPS uses to detect malicious activity. Signatures can be used to detect severe breaches of security, to detect common network attacks, and to gather information. IDS and IPS technologies can detect atomic signature patterns (single-packet) or composite signature patterns (multi-packet).
Content Security Appliances (3.9.5)
Content security appliances provide fine-grained control over email and web browsing for an organization’s users.
Cisco Email Security Appliance (ESA)
Cisco Email Security Appliance (ESA) is a special device designed to monitor Simple Mail Transfer Protocol (SMTP). Cisco ESA is constantly updated by real-time feeds from Cisco Talos, which detects and correlates threats and solutions by using a worldwide database monitoring system. This threat intelligence data is pulled by the Cisco ESA every three to five minutes.
Figure 3-30 shows how ESA works:

Figure 3-30 Cisco ESA in Operation
Step 1. The threat actor sends a phishing attack to an important host on the network.
Step 2. The firewall forwards all email to ESA.
Step 3. ESA analyzes the email, logs it, and discards it.
Cisco Web Security Appliance (WSA)
Cisco Web Security Appliance (WSA) is a mitigation technology for web-based threats. It helps organizations address the challenges of securing and controlling web traffic. The Cisco WSA combines advanced malware protection (AMP), application visibility and control, acceptable use policy controls, and reporting.
Cisco WSA provides complete control over how users access the internet. Certain features and applications—such as chat, messaging, video, and audio—can be allowed, restricted with time and bandwidth limits, or blocked, according to the organization’s requirements. WSA can perform blacklisting of URLs, URL filtering, malware scanning, URL categorization, web application filtering, and encryption and decryption of web traffic.
Figure 3-31 shows how WSA works:

Figure 3-31 Cisco WSA in Operation
Step 1. A corporate user attempts to connect to a website.
Step 2. The firewall forwards the website request to WSA.
Step 3. WSA evaluates the URL and determines that it is a known blacklisted site. WSA discards the packet and sends an access denied message to the user.
Check Your Understanding—Network Security Best Practices (3.9.6)

Refer to the online course to complete this activity.
Cryptography (3.10)
Even if an organization has the best defense-in-depth security possible, it needs to protect its data as it leaves the network. This section describes common cryptographic processes used to protect data in transit.
Video—Cryptography (3.10.1)

Refer to the online course to view this video.
Securing Communications (3.10.2)
Organizations must provide support to secure data as it travels across links. This applies to internal traffic, but it is even more important to protect the data that travels outside the organization to branch sites, telecommuter sites, and partner sites.
These are the four elements of secure communications:
Data integrity: Guarantees that a message was not altered. Any changes to data in transit will be detected. Integrity is ensured by using a hash-generating algorithm such as the legacy Message Digest version 5 (MD5) algorithm or the more secure Secure Hash Algorithm (SHA) family of algorithms.
Origin authentication: Guarantees that a message is not a forgery and comes from the person it purports to come from. Many modern networks ensure authentication with protocols such as hash message authentication codes (HMACs).
Data confidentiality: Guarantees that only authorized users can read a message, and if a message is intercepted, it cannot be deciphered within a reasonable amount of time. Data confidentiality is implemented using symmetric and asymmetric encryption algorithms.
Data nonrepudiation: Guarantees that the sender cannot repudiate, or refute, the validity of a message sent. Nonrepudiation relies on the fact that only the sender has the unique characteristics or signature for how that message is treated.
Cryptography can be used almost anywhere that there is data communication. In fact, the trend is toward all communication being encrypted.
Data Integrity (3.10.3)
Hash functions are used to ensure the integrity of a message. They guarantee that message data has not changed accidentally or intentionally.
In Figure 3-32, the sender is sending a $100 money transfer to Alex.
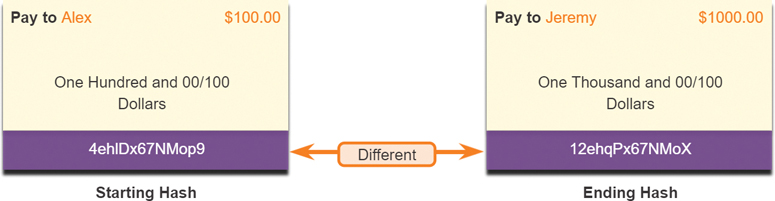
Figure 3-32 Data Integrity Example
In the figure, the sender wants to ensure that the message is not altered on its way to the receiver:
Step 1. The sending device inputs the message into a hashing algorithm and computes the fixed-length hash 4ehiDx67NMop9.
Step 2. This hash is then attached to the message and sent to the receiver. Both the message and the hash are in plaintext.
Step 3. The receiving device removes the hash from the message and inputs the message into the same hashing algorithm. If the computed hash is equal to the one that is attached to the message, the message has not been altered during transit. If the hashes are not equal, as shown in Figure 3-32, then the integrity of the message can no longer be trusted.
Note
Hashing algorithms only protect against accidental changes and do not protect data from changes deliberately made by a threat actor.
Hash Functions (3.10.4)
There are three well-known hash functions, described in this section.
MD5 with 128-Bit Digest
MD5 is a one-way function that produces a 128-bit hashed message. MD5 is a legacy algorithm that should be used only when no better alternatives are available. Use SHA-2 or SHA-3 instead.
In Figure 3-33, a plaintext message is passed through an MD5 hash function. The result is a 128-bit hashed message.

Figure 3-33 MD5 Hash Function
SHA Hashing Algorithm
SHA-1 is similar to the MD5 hash functions. Several versions exist. SHA-1 creates a 160-bit hashed message and is slightly slower than MD5. SHA-1 has known flaws and is a legacy algorithm. Use SHA-2 or SHA-3 when possible.
In Figure 3-34, a plaintext message is passed through a SHA hash function. The result is a hashed message.
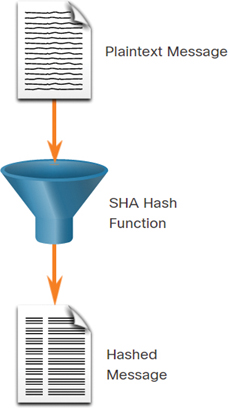
Figure 3-34 SHA Hash Function
SHA-2
SHA-2 includes SHA-224 (224 bit), SHA-256 (256 bit), SHA-384 (384 bit), and SHA-512 (512 bit). SHA-256, SHA-384, and SHA-512 are next-generation algorithms and should be used whenever possible.
SHA-3
SHA-3, which is the newest hashing algorithm, was introduced by the National Institute of Standards and Technology (NIST) as an alternative and eventual replacement for the SHA-2 family of hashing algorithms. SHA-3 includes SHA3-224 (224 bit), SHA3-256 (256 bit), SHA3-384 (384 bit), and SHA3-512 (512 bit). The SHA-3 next-generation family of algorithms should be used if possible.
While hashing can be used to detect accidental changes, it cannot be used to guard against deliberate changes. There is no unique identifying information from the sender in the hashing procedure. This means that anyone who has the correct hash function can compute a hash for any data. For example, when a message traverses a network, a potential threat actor could intercept the message, change it, recalculate the hash, and append it to the message. The receiving device would only validate against whatever hash is appended.
Therefore, hashing is vulnerable to man-in-the-middle attacks and does not provide security to transmitted data. To provide integrity and origin authentication, something more is required.
Origin Authentication (3.10.5)
To add authentication to integrity assurance, use a keyed hash message authentication code (HMAC), which uses an additional secret key as input to the hash function.
Note
Other message authentication code methods are also used. However, HMAC is used in many systems, including SSL, IPsec, and SSH.
HMAC Hashing Algorithm
As shown in Figure 3-35, an HMAC is calculated using any cryptographic algorithm that combines a cryptographic hash function with a secret key. Hash functions are the basis of the protection mechanism of HMACs.

Figure 3-35 HMAC Hash Function
Only the sender and the receiver know the secret key, and the output of the hash function depends on the input data and the secret key. Only parties who have access to that secret key can compute the digest of an HMAC function. This defeats man-in-the-middle attacks and provides authentication of the data origin.
If two parties share a secret key and use HMAC functions for authentication, a properly constructed HMAC digest of a message that a party has received indicates that the other party was the originator of the message. This is because the other party possesses the secret key.
Creating the HMAC Value
As shown in Figure 3-36, the sending device inputs data (in this case, Terry Smith’s $100 pay and the secret key) into the hashing algorithm and calculates the fixed-length HMAC digest. This authenticated digest is then attached to the message and sent to the receiver.
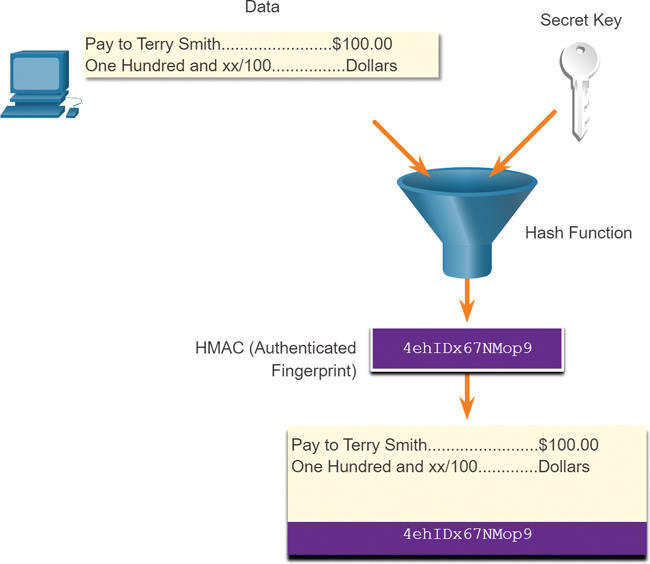
Figure 3-36 Creating the HMAC Value
Verifying the HMAC Value
As shown in Figure 3-37, the receiving device removes the digest from the message and uses the plaintext message with its secret key as input into the same hashing function. If the digest that is calculated by the receiving device is equal to the digest that was sent, the message has not been altered. In addition, the origin of the message is authenticated because only the sender possesses a copy of the shared secret key. The HMAC function has ensured the authenticity of the message.

Figure 3-37 Verifying the HMAC Value
Cisco Router HMAC Example
Figure 3-38 shows how HMACs are used by Cisco routers that are configured to use Open Shortest Path First (OSPF) routing authentication.
In the figure, R1 is sending a link-state update (LSU) regarding a route to network 10.2.0.0/16:
Step 1. R1 calculates the hash value using the LSU message and the secret key.
Step 2. The resulting hash value is sent with the LSU to R2.
Step 3. R2 calculates the hash value using the LSU and its secret key. R2 accepts the update if the hash values match. If they do not match, R2 discards the update.

Figure 3-38 Cisco Router HMAC Example
Data Confidentiality (3.10.6)
Two classes of encryption are used to provide data confidentiality. These two classes differ in how they use keys.
Symmetric encryption algorithms such as DES, 3DES, and Advanced Encryption Standard (AES) are based on the premise that each communicating party knows the pre-shared key. Data confidentiality can also be ensured using asymmetric algorithms, including Rivest, Shamir, and Adleman (RSA) and public key infrastructure (PKI).
Figure 3-39 highlights some differences between the symmetric and asymmetric encryption algorithm methods.

Figure 3-39 Differences Between Symmetric and Asymmetric Encryption
Symmetric Encryption (3.10.7)
Symmetric algorithms use the same pre-shared key to encrypt and decrypt data. A pre-shared key, also called a secret key, is known by the sender and receiver before any encrypted communications can take place.
To help illustrate how symmetric encryption works, consider an example where Alice and Bob live in different locations and want to exchange secret messages with one another through the mail system. In this example, Alice wants to send a secret message to Bob.
In Figure 3-40, Alice and Bob have identical keys to a single padlock. These keys were exchanged prior to sending any secret messages. Alice writes a secret message and puts it in a small box that she locks using the padlock and her key. She mails the box to Bob. The message is safely locked inside the box as the box makes its way through the postal system. When Bob receives the box, he uses his key to unlock the padlock and retrieve the message. Bob can use the same box and padlock to send a secret reply to Alice.
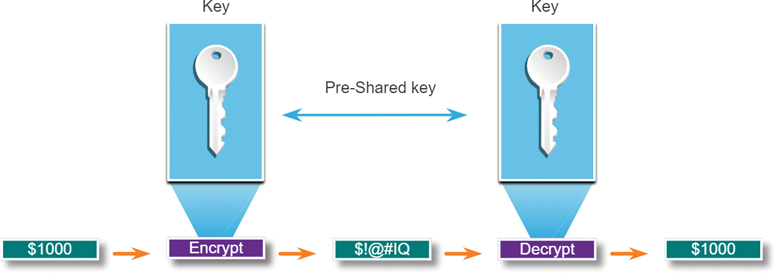
Figure 3-40 Symmetric Encryption Example
Today, symmetric encryption algorithms are commonly used with VPN traffic because symmetric algorithms use less CPU resources than asymmetric encryption algorithms. Encryption and decryption of data occur quickly on a VPN. When using symmetric encryption algorithms, like any other type of encryption, the longer the key, the longer it will take for someone to discover the key. Most encryption keys are between 112 and 256 bits. To ensure that encryption is safe, use a minimum key length of 128 bits. Use a longer key for more secure communications.
Well-known symmetric encryption algorithms are described in Table 3-16.
Table 3-16 Symmetric Encryption Algorithms
Symmetric Encryption Algorithms |
Description |
Data Encryption Standard (DES) |
|
3DES (Triple DES) |
|
Advanced Encryption Standard (AES) |
|
Software-Optimized Encryption Algorithm (SEAL) |
|
Rivest Cipher (RC) series algorithms |
|
Asymmetric Encryption (3.10.8)
Asymmetric encryption algorithms, also called public key algorithms, are designed so that the key that is used for encryption is different from the key that is used for decryption, as shown in Figure 3-41. The decryption key cannot, in any reasonable amount of time, be calculated from the encryption key and vice versa.
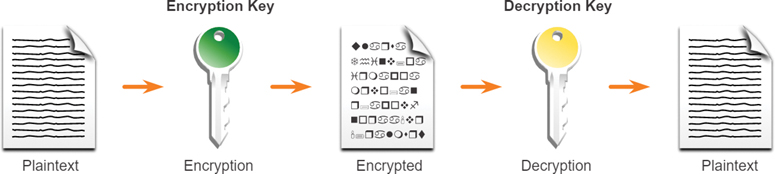
Figure 3-41 Asymmetric Encryption Example
An asymmetric algorithm uses a public key and a private key. Both keys are capable of the encryption process, but the complementary paired key is required for decryption. The process is also reversible. Data encrypted with the public key can be decrypted only with the private key. Asymmetric algorithms achieve confidentiality, authentication, and integrity by using this process.
Because the parties do not have a shared secret, very long key lengths must be used. Asymmetric encryption can use key lengths between 512 to 4096 bits. Key lengths greater than or equal to 1024 bits can be trusted, and shorter key lengths are considered unreliable.
Examples of protocols that use asymmetric key algorithms include:
Internet Key Exchange (IKE): This is a fundamental component of IPsec VPNs.
Secure Socket Layer (SSL): This is now implemented as the IETF standard Transport Layer Security (TLS).
Secure Shell (SSH): This protocol provides a secure remote access connection to network devices.
Pretty Good Privacy (PGP): This computer program provides cryptographic privacy and authentication. It is often used to increase the security of email communications.
Asymmetric algorithms are substantially slower than symmetric algorithms. Their design is based on computational problems, such as factoring extremely large numbers or computing discrete logarithms of extremely large numbers.
Because they are slow, asymmetric algorithms are typically used in low-volume cryptographic mechanisms, such as digital signatures and key exchange. However, the key management of asymmetric algorithms tends to be simpler than that for symmetric algorithms because usually one of the two encryption or decryption keys can be made public.
Common asymmetric encryption algorithms are described in Table 3-17.
Table 3-17 Asymmetric Encryption Algorithms
Asymmetric Encryption Algorithms |
Key Lengths |
Description |
512, 1024, 2048, 3072, 4096 |
|
|
Digital Signature Standard (DSS) and Digital Signature Algorithm (DSA) |
512–1024 |
|
Rivest, Shamir, and Adleman (RSA) encryption algorithms |
512–2048 |
|
ElGamal |
512–1024 |
|
Elliptic curve techniques |
160 |
|
Diffie-Hellman (3.10.9)
Diffie-Hellman (DH) is an asymmetric mathematical algorithm in which two computers generate an identical shared secret key without having communicated before. The new shared key is never actually exchanged between the sender and receiver. However, because both parties know it, the key can be used by an encryption algorithm to encrypt traffic between the two systems.
For example, DH is commonly used when
Data is exchanged using an IPsec VPN
SSH data is exchanged
Figure 3-42 illustrates how DH operates. The colors in the figure will be used instead of complex long numbers to simplify the DH key agreement process. The DH key exchange begins with Alice and Bob agreeing on an arbitrary common color (in this case, yellow) that does not need to be kept secret.
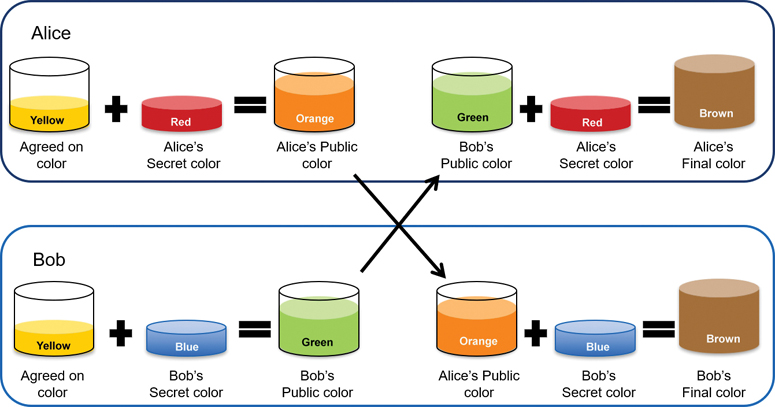
Figure 3-42 Diffie-Hellman Analogy
Next, Alice and Bob each select a secret color. Alice chooses red, and Bob chooses blue. These secret colors will never be shared with anyone. The secret color represents the chosen secret private key of each party.
Alice and Bob now mix the shared common color (yellow) with their respective secret color to produce a public color. Therefore, Alice will mix the yellow with her red color to produce a public color of orange. Bob will mix the yellow and the blue to produce a public color of green.
Alice sends her public color (orange) to Bob, and Bob sends his public color (green) to Alice.
Alice and Bob each mix the color they received with their own, original secret color (red for Alice and blue for Bob). The result is a final brown color mixture that is identical to the other’s final color mixture. The brown color represents the resulting shared secret key between Bob and Alice.
DH security uses very large numbers in its calculations. For example, a DH 1024-bit number is roughly equal to a decimal number with 309 digits. Considering that a billion is 10 decimal digits (1,000,000,000), you can easily imagine the complexity of working with not one but many 309-digit decimal numbers.
Unfortunately, asymmetric key systems are extremely slow for any sort of bulk encryption. Therefore, it is common to encrypt most traffic using a symmetric algorithm, such as 3DES or AES, and use the DH algorithm to create keys that will be used by the encryption algorithm.
Check Your Understanding—Cryptography (3.10.10)

Refer to the online course to complete this activity.
Summary (3.11)
The following is a summary of the sections in this chapter.
Current State of Cybersecurity
Network security breaches can disrupt e-commerce, cause the loss of business data, threaten people’s privacy, and compromise the integrity of information. Assets must be identified and protected. Vulnerabilities must be addressed before they are exploited. Mitigation techniques are required before, during, and after an attack. An attack vector is a path by which a threat actor can gain access to a server, host, or network. Attack vectors can originate inside or outside the corporate network.
Threat Actors
The term threat actor includes hackers, and it also refers to any other device, person, group, or nation-state that is, intentionally or unintentionally, the source of an attack. There are white hat, gray hat, and black hat hackers. Cybercriminals operate in an underground economy where they buy, sell, and trade attack toolkits, zero-day exploit code, botnet services, banking Trojans, keyloggers, and more. Hacktivists tend to rely on fairly basic, freely available tools. State-sponsored hackers create advanced, customized attack code, often using previously undiscovered software vulnerabilities called zero-day vulnerabilities.
Threat Actor Tools
Attack tools have become more sophisticated and highly automated. These new tools require less technical knowledge to implement than did some of the older tools. Ethical hacking involves many different types of tools used to test the network and keep its data secure. To validate the security of a network and its systems, many network penetration testing tools have been developed. Common types of attacks are eavesdropping, data modification, IP address spoofing, password-based, denial-of-service, man-in-the-middle, compromised-key, and sniffer attacks.
Malware
The three most common types of malware are worms, viruses, and Trojan horses. A worm executes arbitrary code and installs copies of itself in the memory of the infected computer. A virus executes a specific unwanted, and often harmful, function on a computer. A Trojan horse is non-self-replicating. When an infected application or file is downloaded and opened, the Trojan horse can attack the end device from within. Other types of malware are adware, ransomware, rootkits, and spyware.
Common Network Attacks
Networks are susceptible to reconnaissance, access, and DoS attacks. Threat actors use reconnaissance (or recon) attacks to do unauthorized discovery and mapping of systems, services, or vulnerabilities. Access attacks exploit known vulnerabilities in authentication services, FTP services, and web services. Types of access attacks are password, spoofing, trust exploitations, port redirections, man-in-the-middle, and buffer overflow attacks. Social engineering is an access attack that attempts to manipulate individuals into performing actions or divulging confidential information. DoS and DDoS are attacks that create some sort of interruption of network services to users, devices, or applications.
IP Vulnerabilities and Threats
Threat actors can send packets by using a spoofed source IP address. Threat actors can also tamper with the other fields in the IP header to carry out their attacks. IP attack techniques include ICMP, amplification and reflection, address spoofing, MITM, and session hijacking. Threat actors use ICMP for reconnaissance and scanning attacks. They launch information-gathering attacks to map out a network topology, discover which hosts are active (reachable), identify the host operating system (OS fingerprinting), and determine the state of a firewall. Threat actors often use amplification and reflection techniques to create DoS attacks.
TCP and UDP Vulnerabilities
TCP segment information appears immediately after the IP header. TCP provides reliable delivery, flow control, and stateful communication. TCP attacks include TCP SYN flood attack, TCP reset attack, and TCP session hijacking. UDP is commonly used by DNS, TFTP, NFS, and SNMP. It is also used with real-time applications such as media streaming and VoIP. UDP is not protected by encryption. UDP flood attacks send a flood of UDP packets, often from a spoofed host, to a server on the subnet. The result is very similar to the result of a DoS attack.
IP Services
Any client can send an unsolicited ARP Reply called a gratuitous ARP. This means that any host can claim to be the owner of any IP or MAC address. A threat actor can poison the ARP caches of devices on the local network, creating an MITM attack to redirect traffic. ARP cache poisoning can be used to launch various man-in-the-middle attacks. DNS attacks include open resolver attacks, stealth attacks, domain shadowing attacks, and tunneling attacks. To stop DNS tunneling, a network administrator must use a filter that inspects DNS traffic. A DHCP spoofing attack occurs when a rogue DHCP server is connected to a network and provides false IP configuration parameters to legitimate clients.
Network Security Best Practices
Most organizations follow the CIA information security triad: confidentiality, integrity, and availability. To ensure secure communications across both public and private networks, you must secure devices including routers, switches, servers, and hosts. This is known as defense-in-depth. A firewall is a system or group of systems that enforce an access control policy between networks. To defend against fast-moving and evolving attacks, you may need an intrusion detection systems (IDS) or a more scalable intrusion prevention systems (IPS).
Cryptography
The four elements of secure communications are data integrity, origin authentication, data confidentiality, and data nonrepudiation. Hash functions guarantee that message data has not changed accidentally or intentionally. Three well-known hash functions are MD5 with 128-bit digest, SHA hashing algorithm, and SHA-2. To add authentication to integrity assurance, use a keyed hash message authentication code (HMAC), which is calculated using any cryptographic algorithm that combines a cryptographic hash function with a secret key. Symmetric encryption algorithms using DES, 3DES, AES, SEAL, and RC are based on the premise that each communicating party knows the pre-shared key. Data confidentiality can also be ensured using asymmetric algorithms, including Rivest, Shamir, and Adleman (RSA) and the public key infrastructure (PKI). Diffie-Hellman (DH) is an asymmetric mathematical algorithm for which two computers generate an identical shared secret key without having communicated before.
Practice
The following lab activities provide practice with the topics introduced in this chapter. The labs are available in the companion Enterprise Networking, Security, and Automation Labs & Study Guide (CCNAv7) (ISBN 9780136634690). There are no Packet Tracer activities for this chapter.
Labs
![]()
Lab 3.5.7: Social Engineering
Lab 3.8.8: Explore DNS Traffic
Check Your Understanding
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to the ‘Check Your Understanding’ Questions” lists the answers.
1. Which network security statement is true?
All threats come from external networks.
Internal threats are always accidental.
Internal threats are always intentional.
Internal threats can cause greater damage than external threats.
2. What commonly motivates cybercriminals to attack networks as compared to hacktivists or state-sponsored hackers?
Fame seeking
Financial gain
Political reasons
Status among peers
3. Which type of hacker is motivated by protesting political and social issues?
Cybercriminal
Hacktivist
Script kiddie
Vulnerability broker
4. What is Trojan horse malware?
It is malware that can only be distributed over the internet.
It is software that appears useful but includes malicious code.
It is software that causes annoying computer problems.
It is the most easily detected form of malware.
5. A user receives a call from someone in IT services, asking her to confirm her username and password for auditing purposes. Which security threat does this represent?
Anonymous keylogging
DDoS
Social engineering
Spam
6. What is a ping sweep?
A DNS query and response protocol
A network scanning technique that involves identifying active IP addresses
A type of packet capturing software
A TCP and UDP port scanner to detect open services
7. How are zombies used in security attacks?
Zombies are infected machines that carry out a DDoS attack.
Zombies are maliciously formed code segments used to replace legitimate applications.
Zombies probe a group of machines for open ports to learn which services are running.
Zombies target specific individuals to gain corporate or personal information.
8. What is used to decrypt data that has been encrypted using an asymmetric encryption algorithm public key?
A different public key
A digital certificate
A private key
DH
9. What are the SHA hash generating algorithms used for?
Authentication
Confidentiality
Integrity
Nonrepudiation
10. Which of the following is true of an IPS?
It can stop malicious packets.
It has no impact on latency.
It is deployed in offline mode.
It is primarily focused on identifying possible incidents.
11. What is the term used to describe unethical criminals who compromise computer and network security for personal gain or for malicious reasons?
Black hat hackers
Hacktivists
Script kiddies
Vulnerability broker
12. What is the term used to describe a potential danger to a company’s assets, data, or network functionality?
Asymmetric encryption algorithm
Exploit
Threat
Vulnerability
13. What term is used to describe a guarantee that a message is not a forgery and does actually come from the person who is supposed to have sent it?
Data nonrepudiation
Exploit
Mitigation
Origin authentication
14. What term is used to describe a mechanism that takes advantage of a vulnerability?
Asymmetric encryption algorithm
Exploit
Threat
Vulnerability
15. Which of the following guarantees that the sender cannot repudiate, or refute, the validity of a message sent?
Data nonrepudiation
Exploit
Mitigation
Origin authentication
