Chapter 4
ACL Concepts
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
How do ACLs filter traffic?
How do ACLs use wildcard masks?
How do you create ACLs?
What are the differences between standard and extended IPv4 ACLs?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
Introduction (4.0)
Say that you have arrived at your grandparents’ residence. It is a beautiful gated community with walking paths and gardens. For the safety of the residents, no one is permitted to get into the community without stopping at the gate and presenting the guard with identification. You provide your ID, and the guard verifies that you are expected as a visitor. He documents your information and lifts the gate. Imagine if the guard had to do this for the many staff members who entered each day. The security department has simplified this process by assigning a badge to each employee that can be scanned to automatically raise the gate. You greet your grandparents, who are anxiously awaiting you at the front desk. You all get back into the car to go down the street for dinner. As you exit the parking lot, you must again stop and show your identification so that the guard will lift the gate. Rules have been put in place for all incoming and outgoing traffic.
Much like the guard in the gated community, an access control list (ACL) may be configured to permit and deny network traffic passing through an interface. The router compares the information within a packet against each access control entry (ACE), in sequential order, to determine if the packet matches one of the ACEs. This process is called packet filtering. Let’s learn more!
Purpose of ACLs (4.1)
This section describes how ACLs filter traffic in small- to medium-sized business networks.
What Is an ACL? (4.1.1)
Routers make routing decisions based on information in each packet’s header. Traffic entering a router interface is routed solely based on information in the routing table. The router compares the destination IP address with routes in the routing table to find the best match and then forwards a packet based on the best match route. A similar process can be used to filter traffic using an access control list (ACL).
An ACL is a series of IOS commands that are used to filter packets based on information found in the packet header. By default, a router does not have any ACLs configured. However, when an ACL is applied to an interface, the router performs the additional task of evaluating all network packets as they pass through the interface to determine if each packet can be forwarded.
An ACL uses a sequential list of permit or deny statements known as access control entries (ACEs).
Note
ACEs are also commonly called ACL statements.
When network traffic passes through an interface configured with an ACL, the router compares the information within the packet against each ACE, in sequential order, to determine whether the packet matches one of the ACEs. This process is called packet filtering.
Several tasks performed by routers require the use of ACLs to identify traffic. Table 4-1 lists some of these tasks and provides examples.
Table 4-1 Tasks That Use ACLs
Task |
Example |
Limit network traffic to increase network performance |
|
Provide traffic flow control |
|
Provide a basic level of security for network access |
|
Filter traffic based on traffic type |
|
Screen hosts to permit or deny access to network services |
|
Provide priority to certain classes of network traffic |
|
Packet Filtering (4.1.2)
Packet filtering controls access to a network by analyzing the incoming and/or outgoing packets and forwarding them or discarding them based on given criteria. Packet filtering can occur at Layer 3 or Layer 4, as shown in Figure 4-1.

Figure 4-1 Packet Filtering in the OSI Model
Cisco routers support two types of ACLs:
Standard ACLs: These ACLs only filter at Layer 3, using the source IPv4 address only.
Extended ACLs: These ACLs filter at Layer 3 using the source and/or destination IPv4 address. They can also filter at Layer 4 using TCP, UDP ports, and optional protocol type information for finer control.
ACL Operation (4.1.3)
An ACL defines a set of rules that give added control for packets that enter inbound interfaces, packets relayed through the router, and packets that exit outbound interfaces of the router.
ACLs can be configured to apply to inbound traffic and outbound traffic, as shown in Figure 4-2.

Figure 4-2 ACLs on Inbound and Outbound Interfaces
Note
ACLs do not act on packets that originate from the router itself.
An inbound ACL filters packets before they are routed to the outbound interface. An inbound ACL is efficient because it saves the overhead of routing lookups if the packet is discarded. If a packet is permitted by the ACL, it is processed for routing. Inbound ACLs are best used to filter packets when the network attached to an inbound interface is the only source of packets that need to be examined.
An outbound ACL filters packets after they are routed, regardless of the inbound interface. Incoming packets are routed to the outbound interface, and they are then processed through the outbound ACL. Outbound ACLs are best used when the same filter will be applied to packets coming from multiple inbound interfaces before exiting the same outbound interface.
When an ACL is applied to an interface, it follows a specific operating procedure. For example, here are the operational steps used when traffic has entered a router interface with an inbound standard IPv4 ACL configured:
Step 1. The router extracts the source IPv4 address from the packet header.
Step 2. The router starts at the top of the ACL and compares the source IPv4 address to each ACE, in sequential order.
Step 3. When a match is made, the router carries out the instruction, either permitting or denying the packet, and the remaining ACEs in the ACL, if any, are not analyzed.
Step 4. If the source IPv4 address does not match any ACEs in the ACL, the packet is discarded because there is an implicit deny ACE automatically applied to all ACLs.
The last ACE statement of an ACL is always an implicit deny that blocks all traffic. By default, this statement is automatically implied at the end of an ACL even though it is hidden and not displayed in the configuration.
Note
An ACL must have at least one permit statement; otherwise, all traffic will be denied due to the implicit deny ACE statement.
Packet Tracer—ACL Demonstration (4.1.4)

In this activity, you will observe how an ACL can be used to prevent a ping from reaching hosts on remote networks. After removing the ACL from the configuration, the pings will be successful.
Check Your Understanding—Purpose of ACLs (4.1.5)

Refer to the online course to complete this activity.
Wildcard Masks in ACLs (4.2)
A wildcard mask is similar to a subnet mask but the reverse. In this section, you will learn how to calculate the inverse wildcard mask.
Wildcard Mask Overview (4.2.1)
In the previous section, you learned about the purpose of ACL. This section explains how ACLs use wildcard masks. An IPv4 ACE uses a 32-bit wildcard mask to determine which bits of the address to examine for a match. Wildcard masks are also used by the Open Shortest Path First (OSPF) routing protocol.
A wildcard mask is similar to a subnet mask in that it uses the ANDing process to identify which bits in an IPv4 address to match. However, a wildcard mask and a subnet mask differ in the way they match binary 1s and 0s. Unlike with a subnet mask, in which binary 1 is equal to a match, and binary 0 is not a match, with a wildcard mask, the reverse is true.
Wildcard masks use the following rules to match binary 1s and 0s:
Wildcard mask bit 0: Match the corresponding bit value in the address.
Wildcard mask bit 1: Ignore the corresponding bit value in the address.
Table 4-2 lists some examples of wildcard masks and what they would match and ignore.
Table 4-2 Examples of Wildcard Masks
Wildcard Mask |
Last Octet (in Binary) |
Meaning (0—match, 1—ignore) |
0.0.0.0 |
00000000 |
|
0.0.0.63 |
00111111 |
|
0.0.0.15 |
00001111 |
|
0.0.0.248 |
11111100 |
|
0.0.0.255 |
11111111 |
|
Wildcard Mask Types (4.2.2)
Using wildcard masks takes some practice. The following sections provide examples to help you learn how wildcard masks are used to filter traffic for one host, one subnet, and a range IPv4 addresses.
Wildcard to Match a Host
In this example, the wildcard mask is used to match a specific host IPv4 address. Say that ACL 10 needs an ACE that only permits the host with IPv4 address 192.168.1.1. Recall that 0 equals a match, and 1 equals ignore. To match a specific host IPv4 address, a wildcard mask consisting of all zeros (that is, 0.0.0.0) is required.
Table 4-3 lists, in decimal and binary, the host IPv4 address, the wildcard mask, and the permitted IPv4 address.
Table 4-3 Wildcard to Match a Host Example
|
Decimal |
Binary |
IPv4 address |
192.168.1.1 |
11000000.10101000.00000001.00000001 |
Wildcard mask |
0.0.0.0 |
00000000.00000000.00000000.00000000 |
Permitted IPv4 address |
192.168.1.1 |
11000000.10101000.00000001.00000001 |
The 0.0.0.0 wildcard mask stipulates that every bit must match exactly. Therefore, when the ACE is processed, the wildcard mask will permit only the 192.168.1.1 address. The resulting ACE in ACL 10 would be access-list 10 permit 192.168.1.1 0.0.0.0.
Wildcard Mask to Match an IPv4 Subnet
In this example, ACL 10 needs an ACE that permits all hosts in the 192.168.1.0/24 network. The wildcard mask 0.0.0.255 stipulates that the very first three octets must match exactly, but the fourth octet does not need to match.
Table 4-4 lists, in decimal and binary, the host IPv4 address, the wildcard mask, and the permitted IPv4 addresses.
Table 4-4 Wildcard Mask to Match an IPv4 Subnet Example
|
Decimal |
Binary |
IPv4 address |
192.168.1.1 |
11000000.10101000.00000001.00000001 |
Wildcard mask |
0.0.0.255 |
00000000.00000000.00000000.11111111 |
Permitted IPv4 address |
192.168.1.0/24 |
11000000.10101000.00000001.00000000 |
When the ACE is processed, the wildcard mask 0.0.0.255 permits all hosts in the 192.168.1.0/24 network. The resulting ACE in ACL 10 would be access-list 10 permit 192.168.1.0 0.0.0.255.
Wildcard Mask to Match an IPv4 Address Range
In this example, ACL 10 needs an ACE that permits all hosts in the 192.168.16.0/24, 192.168.17.0/24, …, 192.168.31.0/24 networks. The wildcard mask 0.0.15.255 would correctly filter that range of addresses.
Table 4-5 lists, in decimal and binary the host IPv4 address, the wildcard mask, and the permitted IPv4 addresses.
Table 4-5 Wildcard Mask to Match an IPv4 Address Range Example
|
Decimal |
Binary |
IPv4 address |
192.168.16.0 |
11000000.10101000.00010000.00000000 |
Wildcard mask |
0.0.15.255 |
00000000.00000000.00001111.11111111 |
Permitted IPv4 address |
192.168.16.0/24 to 192.168.31.0/24 |
11000000.10101000.00010000.00000000 11000000.10101000.00011111.00000000 |
The highlighted wildcard mask bits identify which bits of the IPv4 address must match. When the ACE is processed, the wildcard mask 0.0.15.255 permits all hosts in the 192.168.16.0/24 to 192.168.31.0/24 networks. The resulting ACE in ACL 10 would be access-list 10 permit 192.168.16.0 0.0.15.255.
Wildcard Mask Calculation (4.2.3)
Calculating wildcard masks can be challenging. One shortcut method is to subtract the subnet mask from 255.255.255.255. The following sections provide examples to help you learn how to calculate the wildcard mask using the subnet mask.
Example 1
Say that you wanted an ACE in ACL 10 to permit access to all users in the 192.168.3.0/24 network. To calculate the wildcard mask, subtract the subnet mask (that is, 255.255.255.0) from 255.255.255.255, as shown in Table 4-6.
The solution produces the wildcard mask 0.0.0.255. Therefore, the ACE would be access-list 10 permit 192.168.3.0 0.0.0.255.
Table 4-6 Wildcard Mask Calculation—Example 1
Starting value |
255.255.255.255 |
Subtract the subnet mask |
–255.255.255. 0 |
Resulting wildcard mask |
0. 0. 0.255 |
Example 2
In this example, say that you wanted an ACE in ACL 10 to permit network access for the 14 users in the subnet 192.168.3.32/28. Subtract the subnet (that is, 255.255.255.240) from 255.255.255.255, as shown in Table 4-7.
This solution produces the wildcard mask 0.0.0.15. Therefore, the ACE would be access-list 10 permit 192.168.3.32 0.0.0.15.
Table 4-7 Wildcard Mask Calculation—Example 2
Starting value |
255.255.255.255 |
Subtract the subnet mask |
–255.255.255.240 |
Resulting wildcard mask |
0. 0. 0. 15 |
Example 3
In this example, say that you needed an ACE in ACL 10 to permit only networks 192.168.10.0 and 192.168.11.0. These two networks could be summarized as 192.168.10.0/23, which is a subnet mask of 255.255.254.0. Again, you subtract 255.255.254.0 subnet mask from 255.255.255.255, as shown in Table 4-8.
This solution produces the wildcard mask 0.0.1.255. Therefore, the ACE would be access-list 10 permit 192.168.10.0 0.0.1.255.
Table 4-8 Wildcard Mask Calculation—Example 3
Starting value |
255.255.255.255 |
Subtract the subnet mask |
–255.255.254. 0 |
Resulting wildcard mask |
0. 0. 1.255 |
Example 4
Consider an example in which you need an ACL number 10 to match networks in the range 192.168.16.0/24 to 192.168.31.0/24. This network range could be summarized as 192.168.16.0/20, which is a subnet mask of 255.255.240.0. Therefore, subtract 255.255.240.0 subnet mask from 255.255.255.255, as shown in Table 4-9.
This solution produces the wildcard mask 0.0.15.255. Therefore, the ACE would be access-list 10 permit 192.168.16.0 0.0.15.255.
Table 4-9 Wildcard Mask Calculation—Example 4
Starting value |
255.255.255.255 |
Subtract the subnet mask |
– 255.255.240. 0 |
Resulting wildcard mask |
0. 0. 15.255 |
Wildcard Mask Keywords (4.2.4)
Working with decimal representations of binary wildcard mask bits can be tedious. To simplify this task, Cisco IOS provides two keywords to identify the most common uses of wildcard masking. Keywords reduce ACL keystrokes and make it easier to read an ACE.
The two keywords are
host: This keyword substitutes for the 0.0.0.0 mask and indicates that all IPv4 address bits must match to filter just one host address.
any: This keyword substitutes for the 255.255.255.255 mask and indicates to ignore the entire IPv4 address or to accept any addresses.
In the command output in Example 4-1, two ACLs are configured. The ACL 10 ACE permits only the 192.168.10.10 host, and the ACL 11 ACE permits all hosts.
Example 4-1 ACLs Configured Without Keywords
R1(config)# access-list 10 permit 192.168.10.10 0.0.0.0 R1(config)# access-list 11 permit 0.0.0.0 255.255.255.255 R1(config)#
Alternatively, the keywords host and any could be used to replace the highlighted output. The commands in Example 4-2 accomplishes the same task as the commands in Example 4-1.
Example 4-2 ACLs Configured Using Keywords
R1(config)# access-list 10 permit host 192.168.10.10 R1(config)# access-list 11 permit any R1(config)#
Check Your Understanding—Wildcard Masks in ACLs (4.2.5)

Refer to the online course to complete this activity.
Guidelines for ACL Creation (4.3)
This section provides guidelines for creating ACLs.
Limited Number of ACLs per Interface (4.3.1)
In a previous section, you learned about how wildcard masks are used in ACLs. This section discusses guidelines for ACL creation. There is a limit on the number of ACLs that can be applied on a router interface. For example, a dual-stacked (that is, IPv4 and IPv6) router interface can have up to four ACLs applied, as shown in Figure 4-3.

Figure 4-3 ACLs Limited on Interfaces
Specifically, a dual-stacked router interface can have
One outbound IPv4 ACL
One inbound IPv4 ACL
One inbound IPv6 ACL
One outbound IPv6 ACL
Say that R1 has two dual-stacked interfaces that need to have inbound and outbound IPv4 and IPv6 ACLs applied. As shown in Figure 4-4, R1 could have up to 8 ACLs configured and applied to interfaces.

Figure 4-4 ACLs Limit Example
In this case, each interface would have four ACLs: two ACLs for IPv4 and two ACLs for IPv6. For each protocol, one ACL is for inbound traffic and one for outbound traffic.
Note
ACLs do not have to be configured in both directions. The number of ACLs and their direction applied to the interface will depend on the security policy of the organization.
ACL Best Practices (4.3.2)
Using ACLs requires attention to detail and great care. Mistakes can be costly in terms of downtime, troubleshooting efforts, and network service. Basic planning is required before configuring an ACL.
Table 4-10 presents some ACL best practices.
Table 4-10 Guidelines for ACLs
Guideline |
Benefit |
Base ACLs on the organization’s security policies. |
This will ensure that you implement organizational security guidelines. |
Write out what you want an ACL to do. |
This will help you avoid inadvertently creating potential access problems. |
Use a text editor to create, edit, and save all your ACLs. |
This will help you create a library of reusable ACLs. |
Document ACLs by using the remark command. |
This will help you (and others) understand the purpose of an ACE. |
Test ACLs on a development network before implementing them on a production network. |
This will help you avoid costly errors. |
Check Your Understanding—Guidelines for ACL Creation (4.3.3)

Refer to the online course to complete this activity.
Types of IPv4 ACLs (4.4)
This section compares IPv4 standard and extended ACLs.
Standard and Extended ACLs (4.4.1)
The previous sections describe the purpose of ACLs as well as guidelines for ACL creation. This section covers standard and extended ACLs and named and numbered ACLs, and it provides examples of placement of these ACLs.
There are two types of IPv4 ACLs:
Standard ACLs: These ACLs permit or deny packets based only on the source IPv4 address.
Extended ACLs: These ACLs permit or deny packets based on the source IPv4 address and destination IPv4 address, protocol type, source and destination TCP or UDP ports, and more.
For example, Example 4-3 shows how to create a standard ACL. In this example, ACL 10 permits hosts on the source network 192.168.10.0/24. Because of the implied “deny any” at the end, all traffic except for traffic coming from the 192.168.10.0/24 network is blocked with this ACL.
Example 4-3 Standard ACL Example
R1(config)# access-list 10 permit 192.168.10.0 0.0.0.255 R1(config)#
In Example 4-4, the extended ACL 100 permits traffic originating from any host on the 192.168.10.0/24 network to any IPv4 network if the destination host port is 80 (HTTP).
Example 4-4 Extended ACL Example
R1(config)# access-list 100 permit tcp 192.168.10.0 0.0.0.255 any eq www R1(config)#
Notice that the standard ACL 10 is only capable of filtering by source address, while the extended ACL 100 is filtering on the source and destination Layer 3 and Layer 4 protocol (for example, TCP) information.
Note
Full IPv4 ACL configuration is discussed in Chapter 5, “ACLs for IPv4 Configuration.”
Numbered and Named ACLs (4.4.2)
For IPv4, there are both numbered and named ACLs.
Numbered ACLs
ACLs 1 to 99 and 1300 to 1999 are standard ACLs, while ACLs 100 to 199 and 2000 to 2699 are extended ACLs, as shown in Example 4-5.
Example 4-5 Available ACL Numbers
R1(config)# access-list ? <1-99> IP standard access list <100-199> IP extended access list <1100-1199> Extended 48-bit MAC address access list <1300-1999> IP standard access list (expanded range) <200-299> Protocol type-code access list <2000-2699> IP extended access list (expanded range) <700-799> 48-bit MAC address access list rate-limit Simple rate-limit specific access list template Enable IP template acls Router(config)# access-list
Named ACLs
Using named ACLs is the preferred method when configuring ACLs. You can name standard and extended ACLs to provide information about the purpose of each ACL. For example, the extended ACL name FTP-FILTER is far easier to identify than the ACL number 100.
The ip access-list global configuration command is used to create a named ACL, as shown in Example 4-6.
Note
Numbered ACLs are created using the access-list global configuration command.
Example 4-6 Example of a Named ACL
R1(config)# ip access-list extended FTP-FILTER R1(config-ext-nacl)# permit tcp 192.168.10.0 0.0.0.255 any eq ftp R1(config-ext-nacl)# permit tcp 192.168.10.0 0.0.0.255 any eq ftp-data R1(config-ext-nacl)#
The following are the general rules to follow for named ACLs:
Assign a name to identify the purpose of the ACL.
Names can contain alphanumeric characters.
Names cannot contain spaces or punctuation.
It is suggested that a name be written in CAPITAL LETTERS.
Entries can be added or deleted within an ACL.
Where to Place ACLs (4.4.3)
Every ACL should be placed where it has the greatest impact on efficiency.
Figure 4-5 illustrates where standard and extended ACLs should be located in an enterprise network.
Say that the objective is to prevent traffic originating in the 192.168.10.0/24 network from reaching the 192.168.30.0/24 network. Extended ACLs should be located as close as possible to the source of the traffic to be filtered. This way, undesirable traffic is denied close to the source network, without crossing the network infrastructure.
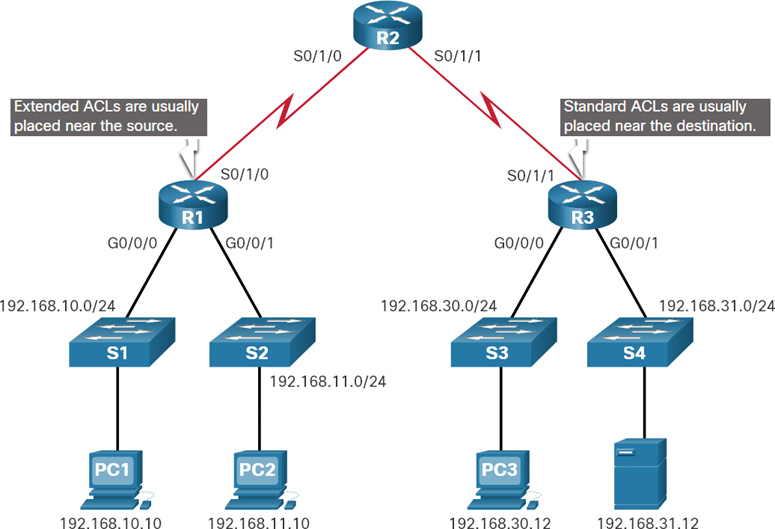
Figure 4-5 Example of Where to Place ACLs
Standard ACLs should be located as close to the destination as possible. If a standard ACL were placed at the source of the traffic, the “permit” or “deny” would occur based on the given source address, regardless of the traffic destination.
Placement of an ACL and, therefore, the type of ACL used, may also depend on a variety of factors, as listed in Table 4-11.
Table 4-11 ACL Placement Factors
Factors Influencing ACL Placement |
Explanation |
The extent of organizational control |
|
Bandwidth of the networks involved |
|
Ease of configuration |
|
Standard ACL Placement Example (4.4.4)
Following the guidelines for ACL placement, standard ACLs should be located as close to the destination as possible.
In Figure 4-6, the administrator wants to prevent traffic originating in the 192.168.10.0/24 network from reaching the 192.168.30.0/24 network.
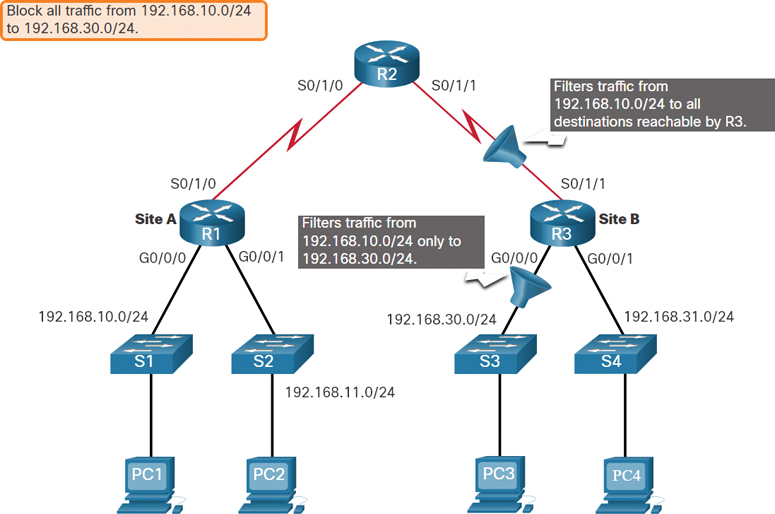
Figure 4-6 Standard ACL Example Topology
Following the basic placement guidelines, the administrator would place a standard ACL on router R3. There are two possible interfaces on R3 to which to apply the standard ACL:
R3 S0/1/1 interface (inbound):The standard ACL can be applied inbound on the R3 S0/1/1 interface to deny traffic from the .10 network. However, it would also filter .10 traffic to the 192.168.31.0/24 (.31 in this example) network. Therefore, the standard ACL should not be applied to this interface.
R3 G0/0 interface (outbound):The standard ACL can be applied outbound on the R3 G0/0/0 interface. This will not affect other networks that are reachable by R3. Packets from the .10 network will still be able to reach the .31 network. This is the best interface to place the standard ACL to meet the traffic requirements.
Extended ACL Placement Example (4.4.5)
Extended ACLs should be located as close to the source as possible to prevent unwanted traffic from being sent across multiple networks only to be denied when it reaches its destination.
However, an organization can only place ACLs on devices that it controls. Therefore, the extended ACL placement must be determined in the context of where organizational control extends.
In Figure 4-7, for example, Company A wants to deny Telnet and FTP traffic to Company B’s 192.168.30.0/24 network from its 192.168.11.0/24 network while permitting all other traffic.

Figure 4-7 Extended ACL Example Topology
There are several ways to accomplish these goals. An extended ACL on R3 would accomplish the task, but the administrator does not control R3. In addition, this solution would allow unwanted traffic to cross the entire network, only to be blocked at the destination, which would affect overall network efficiency.
The solution is to place on R1 an extended ACL that specifies both source and destination addresses. There are two possible interfaces on R1 to apply the extended ACL:
R1 S0/1/0 interface (outbound): The extended ACL can be applied outbound on the S0/1/0 interface. However, this solution would process all packets leaving R1, including packets from 192.168.10.0/24.
R1 G0/0/1 interface (inbound): The extended ACL can be applied inbound on the G0/0/1, and only packets from the 192.168.11.0/24 network are subject to ACL processing on R1. Because the filter is to be limited to only those packets leaving the 192.168.11.0/24 network, applying the extended ACL to G0/1 is the best solution.
Check Your Understanding—Guidelines for ACL Placement (4.4.6)

Refer to the online course to complete this activity.
Summary (4.5)
The following is a summary of the sections in this chapter.
Purpose of ACLs
Several tasks performed by routers require the use of ACLs to identify traffic. An ACL is a series of IOS commands that are used to filter packets based on information found in the packet header. A router does not have any ACLs configured by default. However, when an ACL is applied to an interface, the router performs the additional task of evaluating all network packets as they pass through the interface to determine whether the packets can be forwarded. An ACL uses a sequential list of permit or deny statements, known as ACEs. Cisco routers support two types of ACLs: standard ACLs and extended ACLs. An inbound ACL filters packets before they are routed to the outbound interface. If a packet is permitted by the ACL, it is then processed for routing. An outbound ACL filters packets after being routed, regardless of the inbound interface. When an ACL is applied to an interface, it follows a specific operating procedure:
Step 1. The router extracts the source IPv4 address from the packet header.
Step 2. The router starts at the top of the ACL and compares the source IPv4 address to each ACE, in sequential order.
Step 3. When a match is made, the router carries out the instruction, either permitting or denying the packet, and the remaining ACEs in the ACL, if any, are not analyzed.
Step 4. If the source IPv4 address does not match any ACEs in the ACL, the packet is discarded because there is an implicit deny ACE automatically applied to all ACLs.
Wildcard Masks
An IPv4 ACE uses a 32-bit wildcard mask to determine which bits of the address to examine for a match. Wildcard masks are also used by the Open Shortest Path First (OSPF) routing protocol. A wildcard mask is similar to a subnet mask in that it uses the ANDing process to identify which bits in an IPv4 address to match. However, a wildcard mask and a subnet mask differ in the way they match binary 1s and 0s. Wildcard mask bit 0 matches the corresponding bit value in the address. Wildcard mask bit 1 ignores the corresponding bit value in the address. A wildcard mask is used to filter traffic for one host, one subnet, and a range of IPv4 addresses. A shortcut for calculating a wildcard mask is to subtract the subnet mask from 255.255.255.255. Working with decimal representations of binary wildcard mask bits can be simplified by using the Cisco IOS keywords host and any to identify the most common uses of wildcard masking. Keywords reduce ACL keystrokes and make it easier to read ACEs.
Guidelines for ACL Creation
There is a limit on the number of ACLs that can be applied on a router interface. For example, a dual-stacked (that is, IPv4 and IPv6) router interface can have up to four ACLs applied. Specifically, a router interface can have one outbound IPv4 ACL, one inbound IPv4 ACL, one inbound IPv6 ACL, and one outbound IPv6 ACL. ACLs do not have to be configured in both directions. The number of ACLs and the direction in which they are applied to the interface depend on the security policy of the organization. Basic planning is required before configuring an ACL and includes the following best practices:
Base ACLs on the organization’s security policies.
Write out what you want the ACL to do.
Use a text editor to create, edit, and save all of your ACLs.
Document ACLs by using the remark command.
Test the ACLs on a development network before implementing them on a production network.
Types of IPv4 ACLs
There are two types of IPv4 ACLs: standard ACLs and extended ACLs. Standard ACLs permit or deny packets based only on the source IPv4 address. Extended ACLs permit or deny packets based on the source IPv4 address and destination IPv4 address, protocol type, source and destination TCP or UDP ports, and more. ACLs 1 to 99 and 1300 to 1999 are standard ACLs. ACLs 100 to 199 and 2000 to 2699 are extended ACLs. Using named ACLs is the preferred method when configuring ACLs. Standard and extended ACLs can be named to provide information about the purpose of each ACL.
The following are basic rules to follow for named ACLs:
Assign a name to identify the purpose of an ACL.
Names can contain alphanumeric characters.
Names cannot contain spaces or punctuation.
It is suggested that the name be written in CAPITAL LETTERS.
Entries can be added or deleted within an ACL.
Every ACL should be placed where it has the greatest impact on efficiency. Extended ACLs should be located as close as possible to the source of the traffic to be filtered. This way, undesirable traffic is denied close to the source network without crossing the network infrastructure. Standard ACLs should be located as close to the destination as possible. If a standard ACL were placed at the source of the traffic, the “permit” or “deny” would occur based on the given source address, regardless of the traffic destination. Placement of the ACL may depend on the extent of organizational control, bandwidth of the networks, and ease of configuration.
Practice
The following Packet Tracer activity provides practice with the topics introduced in this chapter. The instructions are available in the companion Enterprise Networking, Security, and Automation Labs & Study Guide (CCNAv7) (ISBN 9780136634690). There are no labs for this chapter.
Packet Tracer Activity

Packet Tracer 4.1.4: ACL Demonstration
Check Your Understanding Questions
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to the ‘Check Your Understanding’ Questions” lists the answers.
1. What two functions describe uses of access control lists? (Choose two.)
ACLs assist a router in determining the best path to a destination.
ACLs can control which areas a host can access on a network.
ACLs provide a basic level of security for network access.
Standard ACLs can filter traffic based on source and destination network addresses.
Standard ACLs can restrict access to specific applications and ports.
2. Which three statements describe how an ACL processes packets? (Choose three.)
A packet is compared with all ACEs in the ACL before a forwarding decision is made.
A packet that has been denied by one ACE can be permitted by a subsequent ACE.
An implicit deny at the end of an ACL rejects any packet that does not match an ACE.
Each ACE is checked only until a match is detected or until the end of the ACL.
If an ACE is matched, the packet is either rejected or forwarded, as directed by the ACE.
If an ACE is not matched, the packet is forwarded by default.
3. Which three statements are best practices related to placement of ACLs? (Choose three.)
Filter unwanted traffic before it travels onto a low-bandwidth link.
For every inbound ACL placed on an interface, ensure that there is a matching outbound ACL.
Place extended ACLs close to the destination IP address of the traffic.
Place extended ACLs close to the source IP address of the traffic.
Place standard ACLs close to the destination IP address of the traffic.
Place standard ACLs close to the source IP address of the traffic.
4. Which two characteristics are shared by standard and extended ACLs? (Choose two.)
Both filter packets for a specific destination host IP address.
Both include an implicit deny as a final entry.
Both permit or deny specific services by port number.
They both filter based on protocol type.
They can be created by using either descriptive names or numbers.
5. Which two statement describes a difference between the operation of inbound and outbound ACLs? (Choose two.)
Inbound ACLs are processed before the packets are routed.
Inbound ACLs can be used in both routers and switches.
Multiple inbound ACLs can be applied to an interface.
Multiple outbound ACLs can be applied to an interface.
Outbound ACLs are processed after the routing is completed.
Outbound ACLs can be used only on routers.
Unlike outbound ACLs, inbound ACLs can be used to filter packets with multiple criteria.
6. In which configuration would an outbound ACL placement be preferred over an inbound ACL placement?
When a router has more than one ACL
When an interface is filtered by an outbound ACL and the network attached to the interface is the source network being filtered within the ACL
When an outbound ACL is closer to the source of the traffic flow
When the ACL is applied to an outbound interface to filter packets coming from multiple inbound interfaces before the packets exit the interface
7. What wildcard mask will match networks 10.16.0.0 through 10.19.0.0?
0.252.255.255
0.0.255.255
0.0.3.255
0.3.255.255
8. What type of ACL offers increased flexibility and control over network traffic?
Extended
Extensive
Named standard
Numbered standard
9. Which statement describes a characteristic of standard IPv4 ACLs?
They can be configured to filter traffic based on both source IP addresses and source ports.
They can be created with a number but not with a name.
They filter traffic based on destination IP addresses only.
They filter traffic based on source IP addresses only.
10. What wildcard mask will match network 10.10.100.64/26?
0.0.0.15
0.0.0.31
0.0.0.63
0.0.0.127
