The human element is the least secure and least controlled aspect of enterprise security. Because of the inherent vulnerability of human trust, we are prone to the tactics of social engineering. Social engineering: the primary method of convincing humans to give up sensitive data or click on a malicious link takes many forms. Common communication methods such as e-mail, social networking, and even the telephone are used to trick humans for malicious purposes. This chapter will focus on the human element of security and provide methods to protect against well-executed social engineering attacks. The importance of effective security awareness training will be presented, along with methods for securely using business networking sites, and methods to detect social engineering through e-mail, social media, and the telephone. Often, the threat to enterprise data comes from the associates who maintain the systems that transmit, process, and store data. User monitoring and physical security will complete the chapter on the human element of security.
This chapter will cover the following topics:
- Methods of social engineering
- Mitigation techniques for social engineering
- Detecting malicious e-mails
- Securely using business networking sites
- Effective security awareness training
The easiest thing to exploit in any enterprise is the people working in the enterprise. The reason is because we, as human beings, are naturally trusting and want to think that there are, in general, no ill intentions when another human being interacts with us. This is the very weakness that makes us humans susceptible to social engineering; the act of getting an individual to take an action or provide information for the purposes of unauthorized access or to gain private information. There are many methods used to social engineer an individual: e-mail, phone, social media, and in-person interaction. This adds to the complexity of thwarting such attacks because they are not always perpetrated in the same manner, and can be of high quality to ensure the bait is taken. What makes these attacks successful is their believability; the communication is in a context that makes the proposed scenario a possibility and not beyond imagination. Sometimes the e-mail phishing source will leverage a technique that we have been tuned to take a certain action every time with a mindless click of a mouse button. An example of this would be the Java pop up asking if we want to trust the source of the Java application and run whatever application it is that "requires" Java. The following pop up is actually created using the Social-Engineer Toolkit (SET), not a legitimate Java application:
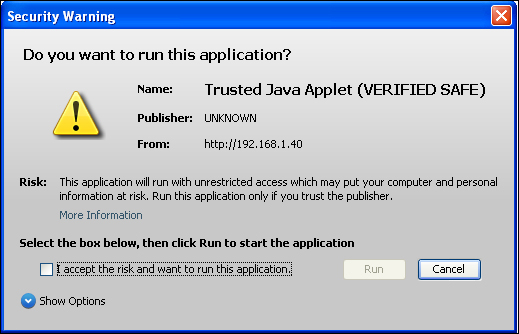
This "fake" Java pop up is indeed a Java pop up. Unfortunately, when it is trusted and the Run button is clicked, the hacker gains unauthorized access to the system. The setup is the all too familiar Java pop up; we are trained to click yes, to accept the risk, so we can see what it is we want to see, but while it seems benign, clicking yes allows an exploit to be run on the system. Though a closer examination of the pop up and the actions leading to the pop up should arouse suspicion as to why there is a pop up and whether the Java application is something that should be trusted, is the source trusted? In this case, the answer to the previous questions would be no.
The following screenshot is what the hacker saw in the scenario we just discussed: a connection to the victim, a fully patched Windows XP SP3 system.
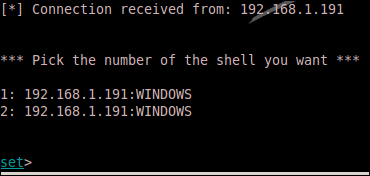
There are well-known social engineers such as Kevin Mitnick who pioneered the art of hacking the human, called social engineering. There are now well written open source tools to launch social engineering attacks such as SET, written and maintained by Dave Kennedy. Tools such as the SET can be used in training and in penetration testing to validate security awareness training efforts.
Social engineering is an important part of the enterprise security landscape and is the most successful attack vector next to SQL injection in poorly written web applications. If an enterprise is not focused on or aware of the threats social engineering poses, easily mitigated attacks will continue to be successful, many of which are not detectable by the most commonly used anti-virus and other endpoint protection methods. Mitigation is rather simple once end users understand what is a legitimate interaction versus a social engineering attempt; do not open, click, run, accept the request, or give away information. This may seem a daunting task but from an implementation perspective, this is the easiest- and lowest-cost solution to stopping most desktop malware. Complexity is introduced because retraining our trusting minds to first question and prove the intent before action is a learned response only mastered by repetition. Perhaps because the brain is the most complex computer, reasoning becomes the most effective method of mitigation; but we continue to fail the test in this area.
The diverse and convincing methods of social engineering are a contributing factor to the continued success of gaining unauthorized access to networks, systems, and sensitive data. Unsolicited e-mails and phone calls continue to be a method used by social engineers to install malicious software and convince users to provide credentials, and other information that aides in further exploitation of the target enterprise. The extremely skilled social engineer will leverage in-person techniques to gain physical access to the information that is desired.
The following is a simple diagram from http://faculty.nps.edu/ncrowe/oldstudents/laribeethesis.htm that shows the difference between the traditional hacker path versus the social engineer:

The next sections will cover these methods in more detail and provide methods to mitigate these techniques by applying sound security principles.
The methods of electronic phishing are becoming more complex as we become more educated on the simpler methods used successfully in the past. E-mail is the most common and the primary method of phishing as it reduces the risk to the social engineer and can be perpetrated completely online. As social media—such as Twitter and Facebook—has infiltrated the enterprise, using these communication methods has become a significant threat vector for malicious software infections such as botnets, Trojans, and viruses. It is important to be aware of the methods employed by social engineers in order to determine the best strategy to mitigate the threats each of them poses.
The most common method of social engineering continues to be e-mail as there has been little security built into the Internet e-mail system to thwart this malicious behavior. Even with solutions like Sender Policy Framework (SPF) designed to mitigate spam, spam continues. More can be learned about this solution at http://en.wikipedia.org/wiki/Sender_Policy_Framework. Anyone can send an e-mail to another person for free with complete anonymity. There are also several free e-mail services available on the Internet and e-mail addresses are easily customizable to look however the sender wants it to look. Additionally, e-mail addresses are easy to spoof making the e-mail look like it is coming from a legitimate source. Some methods used by attackers include the target enterprise's e-mail system that is configured in an insecure manner allowing the malicious e-mail sender to send extremely convincing e-mails to enterprise employees.
One example of a continuously successful type of spam looks as though it comes from a legitimate banking institution requesting payment information or other personal information in order to take over the account or steal the information directly. It is easy to spot a spam e-mail when the bank is incorrect, but when the institution is correct, it becomes increasingly more difficult to determine if the e-mail is legitimate by simply reading the e-mail and observing the sender and recipient e-mail addresses.
Identifying a spam e-mail is difficult and really should not be the responsibility of the end receiver to be an expert in identifying it; but when the controls in place fail or do not exist, the only method to avoid e-mail-based fraud is the knowledge the end user has to make the right decision. Long gone are the days of poorly written e-mails riddled with spelling and grammar errors that were easy indicators that the e-mail was fraudulent. A spam e-mail today is very well written with legitimate graphics, many times dynamically downloaded from the real entity to add to the bait, enticing the end user to click on the link given in the e-mail that will lead to fraud, theft, and installation of malware for further exploitation or annoyance. The crafty spammer understands spam analysis methods so spam is especially crafted to bypass analysis-based blocking. This requires more end-user diligence and more authenticity checks to detect and block unwanted e-mails. Unfortunately, this is a very complex and ever changing process that allows unsolicited e-mails to reach enterprise recipients; it merely reduces the number of e-mails that make it to the end user's e-mail inbox. Some cloud-based services and locally installed solutions provide a user-managed quarantine to allow flagged messages to be reviewed by the end user to determine if the e-mail is valid and authentic. If so, the e-mail can be removed from quarantine. While this is a good method to reduce false positives, it does rely on the ability of the end user to make the right decision.
The following are a few key indicators of a spam e-mail:
- There may be promised financial gain by taking action.
- The e-mail is unsolicited: the end user did not request or initiate the communication.
- The e-mail requests personal information such as account, SSN, and credit card numbers.
- The e-mail contains phrases such as, Urgent Action Required, validation of account by providing username and password are required to ensure the account is not suspended and shutdown. It may also ask for financial information.
- Sometimes, the e-mail may contain a link to perform the action requested. For example, an HTML e-mail will show the alias but hovering over the link will indicate the real URL. Also, viewing the HTML source of the e-mail will show the real URL.
In case an e-mail is received that seems like there may be a real issue with an online account, verification request, or some random message online, the best option is to manually browse to the known legitimate URL and check the validity of the request, removing any potential redirection through the link in the e-mail. Some of the most damning security breaches of the largest security companies were perpetrated through specially crafted e-mails to the targeted recipient. Understanding the methods used in a spam e-mail will provide a good starting point for detection/mitigation technologies and employee education. The next screenshot is a spam e-mail I received at my Gmail account. Let's analyze the e-mail for some of the indicators I mentioned previously. I will also point out a few characteristics of the e-mail by analyzing the e-mail header.
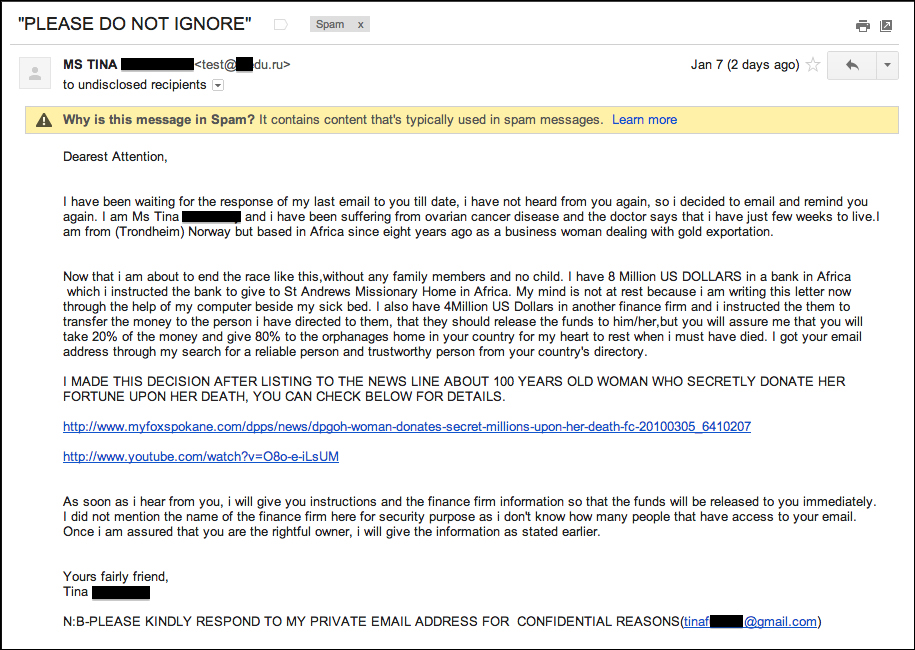
The most noticeable indicators are the subject line, in our case, "PLEASE DO NOT IGNORE". This emphasizes the importance of the e-mail to the receiver, and will tempt us to open and read the e-mail. The next indicator is the large sum of money—$4 million—of which the e-mail recipient will receive 20 percent if they engage with the sender. These are two of the primary indicators listed previously. Let's further analyze this e-mail to look for other inconsistencies.
Notice the sender address ends in .ru, though the sender indicates to send replies to a Gmail-based account at the bottom of the e-mail. This seems odd, doesn't it? Now let's look at the e-mail header. The e-mail header provides more technical details on where the e-mail originated from and how it was routed to the end recipient.
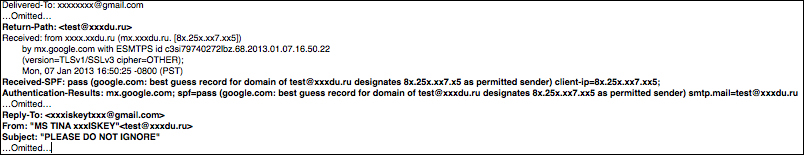
I have bolded the information of importance for this spam e-mail, as shown in the previous screenshot. First, the return path indicates yet another e-mail address—[email protected]. I have purposely obfuscated information with x's. This is the e-mail address of the sender as seen in the From field. Looking at the Reply-To field, we can see another e-mail indicating a different Gmail address. Essentially, there are three e-mail accounts referenced or used in this communication, further complicating the discovery of the "real" sender.
Next, let's look at the Received-SPF field. It states that the e-mail passes the SPF check. Knowing that the e-mail is spam, the SPF pass indicates the ineffectiveness of this authenticity check and leaves the recipient vulnerable to malicious e-mails. This is a clear indication that the source host is a spam solution and the sending e-mail was not spoofed. For the record, Gmail did indicate that this e-mail was spam, but what if it was delivered to another e-mail account. Would it have made it to the inbox leaving the receiver to decide if the e-mail is legitimate?
There are several e-mail solutions available for detecting and blocking spam—both in the cloud and locally—at the enterprise level. Leveraging these types of solutions would be a tier of protection and should be deployed with other security configurations to reduce the likelihood of spam making it to the inbox of enterprise users. The following is a list of other options to reduce the impact of a received spam:
- Set e-mail client to text only, disabling HTML e-mails
- Turn off auto preview of received e-mails
- Right-click on HTML-based e-mails and review the source code for their link information
- Read the e-mail header and look for inconsistencies similar to what we saw in our example
- Send the e-mail to the enterprise spam reporting e-mail address for security review
As with all facets of security, education on the subject is a must for an effective security program that reduces the threat of technologies used by the enterprise.
We have adopted social media as one of the best marketing tools to date and almost every industry and enterprise is leveraging the available technology. It is an easy way to reach a large number of potential clients and partners; but with any social medium, it can be used for malicious purposes too. When instant messaging was the most popular method to chat with friends, strangers, and peers, it was common to get unsolicited messages with a link and an enticing message to encourage the recipient to click on the link. Now, we get unsolicited followers (Twitter) who can view all communication sent to the public forum and send unsolicited messages in response to a key word used in the communication.
The idea of social media is great because the sender does not need to know everyone who receives the message and can allow marketing to a much larger crowd than the immediately known circle of influence. Additionally, some of the new forms of social media allow followers to resend the communication to their followers, furthering the reach of the initial communication.
The initial intent of the technologies in this space was for the home user, not the enterprise. Thus many of the typically required security controls for enterprise implementation are non-existent or poorly implemented. With the lack of enterprise focus and widespread use, the enterprise security teams struggle to protect the enterprise, as employees willingly use the technology without understanding the threats that are present. This is not as much an issue at a personal residence but can pose a significant threat to the enterprise.
The tactics used today leverage the common outbound permitted traffic of the enterprise, sending a link to a malicious site through the social media tool allowed from inside the enterprise network. Securing the communications is not the default for many of the tools in use, so credentials, and other information sent over this medium are readily available for eavesdropping. If social media technology is to be used by the enterprise, it is a must that the security team is involved to ensure the proper controls are in place and guidelines are developed for the proper enterprise usage of the technology. Neglecting to take this approach will lead to compromise and leakage of personal and enterprise sensitive data.
When leveraging social media technologies, it is difficult to protect the access once it is permitted. There are solutions available that can be implemented as a proxy to analyze the communications and block defined data from being transmitted over the communication medium. The most effective method is educating users of the technology about what to look for in communications that may be an attempt to social engineer employees and use diligence when using the technology. A formal set of guidelines for enterprise usage of such technologies should be developed, in addition to security policies that should include approved use of social media on behalf of the enterprise.
Note
There are several online resources for the development of social media policy. An Internet-based wizard driven tool such as PolicyTool (http://socialmedia.policytool.net/) may be a good start. However, the enterprise legal team should complete a careful review of the license agreement. This tool is an example and is not endorsed by the author.
Occasionally, to get the information or access desired, a social engineer will need to meet the target in person to perpetrate the scam. It may be that the desired systems are not Internet accessible such as a credit card reader, ATM, point of sale, or other critical systems intentionally inaccessible for security purposes. The social engineer will find a target with access to the system or device, and through coercion convince the user to infect their system that has access and leverage that exploitation to gain access to the intended target of value. There is speculation and substantial proof that Stuxnet (a recently discovered malware used against Iran) was perpetrated by providing infected USB media to contractors with access to internally protected nuclear facilities. The USBs were inserted into the contractor machines. Once on-site, the malware activated and attacked the internal systems causing significant damage to the nuclear systems. Somehow the contractors were convinced to plug the "trusted" USB drives into their laptops, more than likely through social engineering.
In order to gain access to a system or other information in a physical capacity, the social engineer will need to have a convincing story and play the part well. They are imposters and will be whoever they need to be to achieve the desired outcome. A great cartoon representation of the social engineer imposter comes from http://redwing.hutman.net/~mreed/warriorshtm/impostor.htm.
Just like this cartoon, it is a matter of picking the right mask to convince the target:

An example would be a computer repair technician coming on-site to fix a computer problem providing physical access to install software, modify hardware, or simply steal the desired system. This is one method used to install card skimmers in retail locations at point of sale, ATMs, and gas station pumps. The successful social engineer will gain as much information about the target as possible to be convincing, including choice of clothing, badges, paperwork, and so on to avoid suspicion and accomplish the goal.
In order to mitigate the in-person social engineering attacks, the enterprise must develop stringent physical access protocols to enterprise systems and restricted areas. The methods used can vary, but should include some combination of the following:
- Official identification (badges)
- Validated authorization
- Some form of secret, which may be a word or code, only given to assigned and dispatched persons to perform the on-site function
In addition to the initial validation of the on-site visit, basic physical security practices should be followed. For example, requiring a person to observe the technician at all times and requiring bag checks, and so on to stop or identify physical theft of systems. The social engineer may also use the information to develop the perfect exploit for the exact version of platform implemented or software installed.
An old but very effective method of social engineering is by phone. It has been a tactic for a long time since phones are available to more people and have been around longer than the Internet. It was the first anonymous method of contacting a target thus minimizing the risk of getting caught or leaving a trail for prosecution. This is still true today and social engineers are leveraging advances in technology to take this method further. Using tools that allow desktop sharing and remote control, attackers convince users that their computer has an issue; and to fix it, they must allow the attacker to remote access into the system to correct the issue. Once remote access is gained, the social engineer will install malicious software while the user watches, thinking that it is a program to fix the reported issue. This method has been on the rise in the last few years because it ensures the attack is successful with no waiting on a click of a malicious URL sent via e-mail.
In less sophisticated scenarios, the social engineer calls with a convincing story and persuades the end user to provide personal and business information, credentials, or whatever the social engineer is seeking to obtain. The most challenging component of detecting this method is anyone can be anybody on the phone. Through a little research, the social engineer can impersonate a high-level executive. The fear of letting down an executive alone will lead most end users to divulge information, even if warned to never provide that information to anyone over the phone.
As with all social engineering threats, it is the decision of the employee at the moment in time that matters the most. Preparing users for these types of encounters and knowing how to handle a pushy social engineer will be the most effective in mitigating this type of attack. Users can be prepared by providing them with the tactics used to get information from them such as the type of information being requested, the scenario in which they are being engineered, and teaching methods of questioning the social engineer. An effective method is to ask the engineer more detailed information about what they are asking, such as instead of providing your social security number to them, ask them what number they have on file or what are the last four digits of the number on file. Seek to get more information from the individual and, if necessary, ask for a callback number and involve the security team to determine the legitimacy of the contact. Additionally, if the internal number is not published, this can be an indication of a random call in hopes that the social engineer would get an answer. Asking how they obtained the number or other questions that may throw the engineer into a defensive position may end the conversation, because the target is not considered a soft target. In any circumstance, never provide confidential information to anyone on the phone.
As resumes may be making their official exit and the business networking sites provide the history and experience information hiring managers are looking for, a lot of specific information is made freely available to the public.
The following are a few example business networking sites:
- LinkedIn (http://www.linkedin.com)
- Plaxo (http://www.plaxo.com)
- Ziggs (http://www.ziggs.com)
- XING (http://www.xing.com)
Everyone from the lowest to the highest ranks in corporations builds comprehensive online profiles for business partners and potential employers to learn about them. This information may include work history, education, specialties, and current project information; all of which can be used to social engineer the individual.
The use of these sites is a significant business advantage due to the dynamic nature and features available to reach out and network with others in the same field or find job candidates. These sites usually have a feature that allows individuals to be e-mailed by those interested in doing business with others and can provide e-mail addresses, phone numbers, and other methods of contact or Internet presences maintained by the individual. These other accounts can also provide more information to build a successful social engineering attack.
The communication methods available within these sites provide a similar attack surface to e-mail and instant messaging. Under the guise of legitimate business interest, an engineer can send a malicious e-mail with a link to something that on the surface makes sense, but it leads to a compromised server that will install malicious software on the victim's system. For the normal user with limited access, this may not be as big of an issue versus if this is the CEO or a database administrator with access to very sensitive communications or data.
It is important to be aware that anything posted on the Internet is accessible to the public and caution should be practiced anytime this forum is used to communicate. There will be instances of unsolicited communication through the sites used for legitimate business purposes. All communication should be treated as untrusted unless from a known trusted source. All links should be examined before being clicked and careful examination of the context of the communication can provide an insight to the true nature of the communication. If the recipient does not know the sender, the communication should initially be considered unsolicited spam with a lower priority for replying or reading.
Job posting sites are a necessity and used by job seekers and employers to find available positions and candidates. Typically, career seekers upload their resume and create a profile highlighting their skills and capabilities for potential employers. To make sure that job candidates see the latest available positions, employers upload significant details about open positions to attract the right talent. Without this information, career moves and finding talent would be very challenging. Some level of detail must be provided by both parties to make sure the candidate and employer are a good fit.
While both parties are providing details in order to attract the other, the provided information can be too telling and allows a path for successful social engineering of both parties. The information provided by employers seeking candidates can include detailed information about systems, applications, and operating systems deployed. Information provided by the candidate not only includes job-related skills but personal information that anyone who pays for access to the site can use to reach the candidate.
A skilled social engineer will scour job postings to get as much detail as possible on the enterprise based on posted open positions, experience, and skill requirements. Usually the employer will provide information on type of systems, versions of software, and deployed solutions. The following is an example from a real posting on http://www.monster.com:
Database Administrator
- Working knowledge and experience with LAN-based network operating systems, preferably MS Windows 2000, XP, Windows 7 Enterprise, Server 2000, 2003, 2008, and Active Directory
- Microsoft SQL 2005, 2008; Oracle experience a plus
This information is a great starting point for the social engineer to impersonate as an MS associate addressing a license issue, an interested DBA asking more detailed questions, or a recruiter seeking more information on software versions to make sure they have it correct for potential candidates. Do you see how quickly a social engineer can develop a plausible storyline to gain credentials and other sensitive enterprise information?
Job seekers must also beware of unsolicited "recruiter" calls asking for more information such as social security number to get the process started with an "interested" employer. Sometimes, the interaction is less malicious and simply an effort to get a commission-based position filled; so a call is received about a skill set you don't have but you are told of a proposition about a great opportunity to make a lot of money. These are all methods of abusing and misusing information posted to job seeker-related sites. The next section will provide techniques for protecting the enterprise from social engineering attacks based on information posted in job openings.
It is certainly a fine line between just enough information and too much information for posting in job openings. Employers should be cautious about the details provided on job posting sites that would give too much insight on the inner workings of the enterprise. Avoiding furnishing specific software versions and operating systems to reduce the fingerprinting information for the attacker is ideal. It is common for a social engineer to use the information for a job posting site to call the target and get them to provide enough details to allow the engineer to develop an exploit specific to the target's version of software. Job postings should be generic and specify just enough information to get candidates with the right skills; the more detailed information can be presented during the interview process and skill-based aptitude tests. It is good practice to have HR, legal, and information security involved in public communications, including job postings especially in the areas involving IT.
