Educating the employees of an organization about general security practices and specific enterprise policies is the purpose of security awareness training. In essence, the security department attempts to reduce security incidents in the environment by presenting basic security principles in the hopes that the end user will not take an action that can cause the enterprise risk through data loss or downtime. The effectiveness of such a training has continued to be scrutinized. However, it is a requirement for standards such as the PCI DSS and is, in general, a good practice.
In order for security awareness training to be effective, it must be tailored to the organization and the various teams that will receive the training. Not all individuals or teams will have the same knowledge of technology and security, so a one size fits all approach will not have the intended effects on the security of the organization. There are components that are generic enough that they should be included in all the presentations of the material such as general and acceptable use of common technologies in the enterprise, data protection, and password management.
Providing users with easy to understand and follow guidelines is the key to material retention and proper action when a scenario is realized. Once the material has been presented, a series of exercises should be given to test the users' knowledge on security in the enterprise as it pertains to their common and unique circumstances. An administrative assistant will have different scenarios than a database administrator, though each must know how to react to prevent a security incident such as handling a phishing e-mail. Once the material has been created and presented to associates, it is imperative to maintain education to ensure coverage of the latest threats and methods at least semiannually. Testing of the associate population on a quarterly or semiannual basis will give the security team ample data to determine what works and what needs to be improved in the training material. Additionally, testing can provide data that is indicative of certain behaviors that may require more attention in training materials.
There are several ways to keep the enterprise population aware of current threats and keep security awareness topics fresh in their minds. The ultimate goal of security awareness training is that the automatic user action taken would be the correct action whether it is not clicking on a malicious URL, inserting a USB found on the ground into their computer, or refusing to provide credentials to a stranger on the phone. In the sections we are about to see, computer-based training, instructor-led training, and other awareness training methods will be covered providing information and guidance for each method.
Security awareness training is an excellent way to provide a face to IT security and foster an environment of cooperation and collaboration that will positively impact security in the enterprise. It is also important to note that the more effective security awareness training is, the more associates will increase their overall secure computing knowledge that can be leveraged at the office and at home. It is more likely that the user's home computer will be subjected to more threats than in the office, whether a target or part of a wide cast net. Computer use is typically more risky at home due to lack of controls, and so it is important to educate users to exercise caution whenever using technology, no matter where it is being used.
There are several free and paid for training materials, and options for security awareness training. Though official training may only occur once or twice a year, to increase effectiveness there should be multiple methods employed more regularly to educate and keep the concepts fresh in the enterprise associates' mind. This can be done in the form of regular newsletters, posters, and office pinups. Providing an easily accessible interface to IT security is also a requirement for effective enterprise security. Materials should always have a method of contacting IT security. Providing a friendly interface will increase cooperation across the enterprise reducing security incidents because proactive action will be taken. Depending on the budget allocated for such efforts, training can be as simple or elaborate as needed; it must be effective and measurable. All materials used in security awareness training must be demographically aware, ensuring the education is tailored to the right audience(s). The following table shows the possible pros and cons with each of the covered training methods:
|
Training method |
Pros |
Cons |
|---|---|---|
|
Computer-based training |
Very cost effective and users can take them at their own pace. This solution is the simplest to implement and provides flexibility for user location and time to access the training. |
Cost of productivity loss unless users are willing to train on their own time. |
|
Instructor-led (classroom) |
Promotes interaction and allows questions to be asked and answered in a positive environment. |
Can be difficult to get all the users together in a class. Additional cost for productivity loss. |
|
Newsletters (on-going) |
Regular updates, can address current trends. Also great for recent incident lessons learned. May also be coupled with associate surveys to measure retention of concepts. |
May be difficult to keep readers' attention and ensure the publication is read. Regular e-mails may become annoying to users. |
In order to reach a large number of enterprise users, computer-based training (CBT) may be the best option. It is common for large enterprises to employ this method for multiple reasons:
- The large numbers of users that must participate in the training reduces the cost associated with lost productivity and facilities.
- Delivering the material in this format allows for each user to go through the training at their own pace over the time period given to complete the material. Everyone learns at a different rate and this medium allows each user to move at their own pace without impacting others going over the same material.
- The electronic format of the material can be accessed at anytime—maybe even from home—allowing users to be in a comfortable environment conducive for their learning or to simply go back over previously viewed material to ensure retention of the material.
In general, this method is popular because it can drastically reduce the cost of security awareness training and allows for central management of changes whether in sections of material or the whole learning package. Typically, there are quizzes along the way and a test at the end of the training; this can all be centrally managed with a CBT course greatly reducing the effort of training facilitation and material maintenance.
The primary benefits of CBT training are:
- No written materials needed
- No requirement for instructors
- Training can be completed on employee's time
It can be argued that some subject matter is better taught in person with human-to-human interaction. The effectiveness of one method over another is dependent on several factors. Classroom training allows working through realistic scenarios and in-class participation leads to questions (maybe with character twists) that can be added to truly test retention of concepts. These factors may influence the determination to select a delivery method.
Classroom training does, however, require a lot more planning and cost to facilitate versus CBT and this is exponentially based on the number of associates that must be trained.
Methods to reduce cost may include:
- Offering the training at several locations simultaneously, effectively reducing the overall time required for training
- Facilitating a co-sponsored training offering with other local enterprises to share the cost and foster local collaboration
Instructor-led training can provide added benefits not available to an associate leveraging a CBT course to learn material such as simple question-and-answer sessions or getting more clarity on a training topic. This method may also yield more measurable results for a wider range of skill sets because a good instructor will be able to gauge the retention of the students while teaching and adjust accordingly to ensure the student gets what they are supposed to get from the training. Other methods of training do not have this characteristic and may be less effective at a holistic approach of teaching security awareness; basics are best suited for other methods.
A method to measure how well IT security is keeping the enterprise population educated and aware of enterprise security is through the use of associate surveys at random intervals. There does not need to be a regular occurrence of surveys, however, regular newsletters can provide a constant reminder of good security practices. Without a consistent security message being presented to users, the security awareness program may continue to be a mindless and unfortunate annoyance to the enterprise users measurable improvement in security. Though the survey would be less about opinions and more like a quiz, it is a light touch interactive method to get vital information on how the enterprise population has retained security principles and thinks about security and the training methods used by IT security.
Surveys can be extremely effective because they can be submitted anonymously, allowing the associates to be honest and provide constructive criticism, without the fear of retaliatory actions. Associates may also find this a great way to share their thoughts on a topic without having others offering opinions such as in a classroom setting. Requesting inputs from associates on a quarterly basis is enough to get the data needed without overwhelming them, and allows IT security the time to gather the results and make adjustments where necessary. If beneficial, the associates can be provided with a method of contact for situations when something may need additional clarification, or IT security seeks more information in order to resolve an issue and develop in an area of weakness.
Areas of common knowledge are generic security issues that can be understood and that relate to every associate, such as policies or securing a commonly used technology such as e-mail. There are security topics that each enterprise associate should be aware of and must understand that are not role specific or based on individual expertise. A quick look at the list of policies in the employee handbook should provide these topics; if this does not exist, please see Chapter 3, Security As a Process to learn what standard policies should exist. Implemented enterprise security policies should be the basis of the security awareness training for all associates to ensure everyone is operating from the same set of expectations and understands how their role affects the security of the enterprise. The common knowledge sections of the training should be globally relevant and able to be grasped by all associates regardless of any specific role in the organization. This training can also include activities recently observed in the news such as new hacking cases, or other scams that the associates may become a target of while working or at home. A majority of security incidents are a result of users bringing unsafe home computing habits to the workplace. The security of the enterprise is the responsibility of every associate, not only the IT security team.
In addition to the common knowledge material developed around enterprise security policies and expected behaviors, there is a need for specialized material that is role specific. Each department has unique roles within the enterprise and will access, use, and create various types of data of varying levels of sensitivity. For instance, an administrative assistant will not necessarily need to know the best way to handle credit card numbers in a database, but a DBA will need to know this.
As trust models are developed and roles more accurately defined, the correct training material will become more apparent. Some roles can be grouped together based on the data types and processes shared amongst the defined roles to simplify the effort by reducing the number of specialized training packages that need to be developed. By specializing materials per the unique roles in the organization, the more complex facets of data security can be presented to limited users. This will increase the effectiveness for these specialized groups while not alienating general users in roles that do not have access to sensitive data or processes. Therefore, in theory, their actions would less likely cause significant loss or compromise.
For training to be more than mundane and have the intended effect on enterprise security, it must be intentional in nature and not a checkbox exercise. There have been several studies over the years on the topic of effective training that focus on the methods by which humans learn best. The methods commonly used by all successful training packages leverage several forms of information dissemination and recollection techniques to ensure retention for individual learning types.
In general, there should be a combination of:
- Visual presentation
- Guided and free participation
- Note taking
- Material review
Effective tools should be leveraged such as posters and office area materials that will jog the users' memory on a topic from training and impact how the users behave. The NTL Institute (http://www.ntl.org) developed "The Learning Pyramid" explaining passive and active methods of learning. The following diagram is a depiction from the Centre for Teachin g Excellence Blog (http://cte-blog.uwaterloo.ca/):
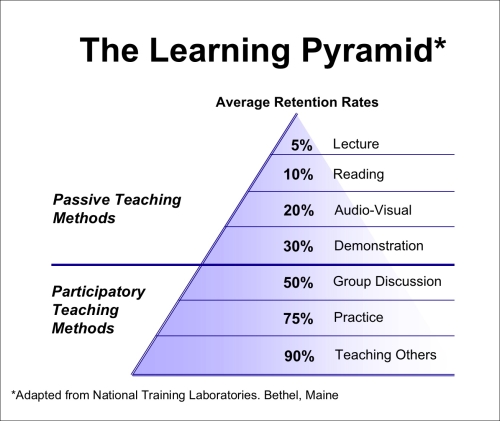
Well-developed training material is the difference between an effective security awareness program and a failure that only meets a compliance requirement. A method to ensure the selected training methods and materials are suitable for their intended purpose is to select users that represent the intended audiences and trial run the training, get feedback, and test for retention. Early planning and focused development of the training program will yield higher success rates in retention and a measurable positive impact on enterprise security.
As with anything taught and learned, regular digestion of the material maintains retention and forces new habits. As stated earlier, security awareness training is an on-going process and cannot only be used as an annual or semiannual exercise. Formal training may be provided at these intervals; but as new methods are used to exploit the human aspect of technology, continued training via newsletters, posters, e-mails, and other mediums must be a part of the program to reach optimal effectiveness.
Tip
A good exercise for the security team is to run random security awareness checks using tools such as the SET written by Dave Kennedy, or commercial solutions such as PhishMe (http://www.phishme.com) to test user responses to simulated social engineering scenarios.
Actions must be repeated several times before they become a habit; this is the intention of security awareness training programs. It is important to note that all data gathered during these checks is to be non-retributory, as the reason for the check is to validate the effectiveness of training, not to hold persons responsible. It is negligible to punish employees when not properly trained on how to handle security-related issues. Consistent training and communication on security and expectations must take precedence; future infractions can be weighed for actions to be taken.
