10
System Security
1. What do you mean by the term intruders? Explain intrusion techniques in brief.
Ans.: Intruders are the attackers who attempt to breach the security of a network. They attack the network in order to get unauthorized access. Intruders are of three types, namely, masquerader, misfeasor and clandestine user.
![]() Masquerader is an external user who is not authorized to use a computer, and yet tries to gain privileges to access a legitimate user's account. Masquerading is generally done either using stolen IDs and passwords, or through bypassing authentication mechanisms.
Masquerader is an external user who is not authorized to use a computer, and yet tries to gain privileges to access a legitimate user's account. Masquerading is generally done either using stolen IDs and passwords, or through bypassing authentication mechanisms.
![]() Misfeasor is a legitimate user who either accesses some applications or data without sufficient privileges to access them, or has privilege to access them, but misuses these privileges. A misfeasor is generally an internal user.
Misfeasor is a legitimate user who either accesses some applications or data without sufficient privileges to access them, or has privilege to access them, but misuses these privileges. A misfeasor is generally an internal user.
![]() Clandestine user is either an internal or external user who gains administrative control of the system and tries to avoid access control and auditing information.
Clandestine user is either an internal or external user who gains administrative control of the system and tries to avoid access control and auditing information.
Intrusion Techniques
The intruders always indulge in finding some way to gain access to the system or to increase the number of privileges assigned to them. To do this, the intruders need access to information that should have been protected, such as some legitimate user's password. After learning the password of an authorized user, intruders can use it to log on to the system and misuse the privileges assigned to the authorized user. Some techniques that the intruders can use to learn others' passwords are as listed here:
![]() They can try the passwords that are by default assigned to standard accounts such as administrator, as it is possible that the administrators may not change their passwords.
They can try the passwords that are by default assigned to standard accounts such as administrator, as it is possible that the administrators may not change their passwords.
![]() They can thoroughly test all the short passwords made up of one, two or three characters.
They can thoroughly test all the short passwords made up of one, two or three characters.
![]() They can intercept the communication between the host system and a remote user.
They can intercept the communication between the host system and a remote user.
![]() They can use a malicious program, such as a Trojan horse, to get around the restrictions imposed on access.
They can use a malicious program, such as a Trojan horse, to get around the restrictions imposed on access.
![]() They can try the words that are available in the system's online dictionary or that are expected to be used.
They can try the words that are available in the system's online dictionary or that are expected to be used.
![]() They can try the users' personal information such as their IDs, phone numbers, room numbers, names of their spouses and children, birthdates, etc.
They can try the users' personal information such as their IDs, phone numbers, room numbers, names of their spouses and children, birthdates, etc.
Besides learning passwords, the intruders can go for other ways to gain access to the system or to gain further privileges. For example, they can exploit attacks such as buffer overflows on a program that executes with certain privileges.
2. Discuss password protection approaches.
Ans.: Generally, passwords are stored by the system in a password file along with the user IDs. Thus, to protect passwords from being captured by the intruders, it is necessary to protect the password file. There are two ways to protect the password file, as listed here:
![]() One-way function: The system does not store the passwords in a clear form in the password file; rather, it applies a function on the user's password and stores the resulting value in the password file. Whenever a user attempts to log on to the system with the help of his or her user ID and password, the system applies the same function on the supplied password. Then it checks whether the newly computed value matches with the stored value. If so, the user is authenticated and allowed access; otherwise, access is denied. The advantage of using this method of protecting the password file is that even if an intruder gets access to the password file, he or she will not be able to get the passwords.
One-way function: The system does not store the passwords in a clear form in the password file; rather, it applies a function on the user's password and stores the resulting value in the password file. Whenever a user attempts to log on to the system with the help of his or her user ID and password, the system applies the same function on the supplied password. Then it checks whether the newly computed value matches with the stored value. If so, the user is authenticated and allowed access; otherwise, access is denied. The advantage of using this method of protecting the password file is that even if an intruder gets access to the password file, he or she will not be able to get the passwords.
![]() Access control: Another means of protecting the password file is by restricting access to the password file. Only a few users such as the system administrator must be allowed to access the password file.
Access control: Another means of protecting the password file is by restricting access to the password file. Only a few users such as the system administrator must be allowed to access the password file.
3. Explain any two approaches for intrusion detection.
Ans.: To prevent intruders from getting unauthorized access to the system, intrusion prevention and intrusion detection can be used. Intrusion prevention is a process that involves detecting the signs of intrusion and attempting to stop the intrusion efforts. On the other hand, intrusion detection is a process that involves monitoring the actions occurring on the network or in the computer systems. In intrusion detection, analysis is done to detect the sign of violations of computer security policies, standard security policies or acceptable use of policies.
It is not possible to completely prevent the efforts of intruders as they constantly try to find their way into the secured system. Hence, we mainly focus on intrusion detection, as it helps collect more information about intrusions. There are generally two approaches for intrusion detection, as listed here:
![]() Statistical anomaly detection: In this category, the behaviour of legitimate users is evaluated over some time interval. That is, their actions are captured as statistical data and then, by applying certain rules on the collected data, their behaviour is checked to determine the legitimacy of the users. This can be achieved by two ways, namely, threshold detection and profile-based detection.
Statistical anomaly detection: In this category, the behaviour of legitimate users is evaluated over some time interval. That is, their actions are captured as statistical data and then, by applying certain rules on the collected data, their behaviour is checked to determine the legitimacy of the users. This can be achieved by two ways, namely, threshold detection and profile-based detection.
![]() Threshold detection: In threshold detection, thresholds are defined for all users as a group, and the total number of events that are attributed to the user are measured against these threshold values. The number of events is assumed to round up to a number that is most likely to occur, and if the event count exceeds this number, then intrusion is said to have occurred.
Threshold detection: In threshold detection, thresholds are defined for all users as a group, and the total number of events that are attributed to the user are measured against these threshold values. The number of events is assumed to round up to a number that is most likely to occur, and if the event count exceeds this number, then intrusion is said to have occurred.
![]() Profile-based detection: In profile-based detection, profiles for all users are created, and then matched with available statistical data to find out if any unwanted action has been performed. A user profile contains several parameters; therefore, change in a single parameter is not a sign of alert.
Profile-based detection: In profile-based detection, profiles for all users are created, and then matched with available statistical data to find out if any unwanted action has been performed. A user profile contains several parameters; therefore, change in a single parameter is not a sign of alert.
![]() Rule-based detection: In this category, certain rules are applied on the actions performed by the users. These rules can determine whether an action performed by any user is suspicious enough to be classified as an intrusion attempt. Rule-based detection is classified into two types, namely, anomaly detection and penetration identification.
Rule-based detection: In this category, certain rules are applied on the actions performed by the users. These rules can determine whether an action performed by any user is suspicious enough to be classified as an intrusion attempt. Rule-based detection is classified into two types, namely, anomaly detection and penetration identification.
![]() Anomaly-based detection: In anomaly-based detection, the usage patterns of users are collected, and certain rules are applied to check any deviation from the previous usage pasterns. The collected patterns are defined by the set of rules that includes past behaviour patterns of users, programs, privileges, time-slots, terminals, etc. The current behaviour patterns of the user are matched with the defined set of rules to check whether there is any deviation in the patterns. In this approach, a large database of rules is needed.
Anomaly-based detection: In anomaly-based detection, the usage patterns of users are collected, and certain rules are applied to check any deviation from the previous usage pasterns. The collected patterns are defined by the set of rules that includes past behaviour patterns of users, programs, privileges, time-slots, terminals, etc. The current behaviour patterns of the user are matched with the defined set of rules to check whether there is any deviation in the patterns. In this approach, a large database of rules is needed.
![]() Penetration identification: In penetration identification, an expert system is maintained that looks for any unwanted attempts. This system also contains rules that are used to identify the suspicious behaviour and penetrations that can exploit known weaknesses. Here, the rules are generated by interviewing experts such as system administrators and security analysts. The data collected in the interview process consist of known penetration scenarios and events that may threaten the security of the system. Thus, the rules are confined to the system and the operating system that is being used.
Penetration identification: In penetration identification, an expert system is maintained that looks for any unwanted attempts. This system also contains rules that are used to identify the suspicious behaviour and penetrations that can exploit known weaknesses. Here, the rules are generated by interviewing experts such as system administrators and security analysts. The data collected in the interview process consist of known penetration scenarios and events that may threaten the security of the system. Thus, the rules are confined to the system and the operating system that is being used.
4. Explain audit records.
Ans.: An audit record (also known as audit log) is a very important tool used in intrusion detection. Audit records are used to track the actions performed by users. If any user tries to get unauthorized access in a network, then traces of such actions can be detected in these records, so that appropriate measures can be taken. Audit records can be categorized into two types, namely, native auditrecords and detection-specific audit records.
![]() Native audit records: Almost all multiuser operating systems come with in-built accounting software that collects information about the actions of each user. The advantage of using this approach is that there is no need for additional collection software. However, the disadvantage is that some of the needed information may not be available in the native audit record or may be in a form that is not convenient to use.
Native audit records: Almost all multiuser operating systems come with in-built accounting software that collects information about the actions of each user. The advantage of using this approach is that there is no need for additional collection software. However, the disadvantage is that some of the needed information may not be available in the native audit record or may be in a form that is not convenient to use.
![]() Detection-specific audit records: These records record only specific information that is related to the detection of unauthorized access in a network. These types of records contain more focused information, but duplication of information may happen. The advantage of using this approach is that it could be made vendor-independent and can be ported onto different systems. However, the disadvantage of this approach is the extra overhead, as two accounting packages need to remain on a single machine.
Detection-specific audit records: These records record only specific information that is related to the detection of unauthorized access in a network. These types of records contain more focused information, but duplication of information may happen. The advantage of using this approach is that it could be made vendor-independent and can be ported onto different systems. However, the disadvantage of this approach is the extra overhead, as two accounting packages need to remain on a single machine.
Irrespective of the type, each audit record contains some fields, as listed here:
![]() Subject: This field gives the information of the user or process or terminal who has started an action.
Subject: This field gives the information of the user or process or terminal who has started an action.
![]() Action: This field defines the operation performed by the user (subject) on an object. For example, read/write, login, execute, print, I/O activity, etc.
Action: This field defines the operation performed by the user (subject) on an object. For example, read/write, login, execute, print, I/O activity, etc.
![]() Object: This field provides the information of the receiver who has received the action. For example, database record, a disk file or an application program.
Object: This field provides the information of the receiver who has received the action. For example, database record, a disk file or an application program.
![]() Exception-condition: This field stores the result of any exception condition, if any occurs because of the actions performed by the subject on the object.
Exception-condition: This field stores the result of any exception condition, if any occurs because of the actions performed by the subject on the object.
![]() Resource-usage: This field records the information regarding the usage of resources in performing an action. For example, the disk space, or CPU time used by an action, number of lines printed or displayed, or number of I/O units used.
Resource-usage: This field records the information regarding the usage of resources in performing an action. For example, the disk space, or CPU time used by an action, number of lines printed or displayed, or number of I/O units used.
![]() Time-stamp: This field indicates the unique date and time stamp that indicates when an action was executed.
Time-stamp: This field indicates the unique date and time stamp that indicates when an action was executed.
5. Why is distributed intrusion detection needed? Explain its architecture.
Ans.: A typical organization consists of a large collection of hosts distributed over a LAN or supported by an internetwork. One way to detect intrusion in such an organization is to use stand-alone intrusion detection systems on individual hosts. Though this type of defence is possible, it has not proved to be much effective. Thus, a better and more effective defence is required, which is achieved through coordination and cooperation among the intrusion detection systems across the network.
Figure 10.1 shows the architecture of a distributed intrusion detection system that was developed at the University of California. It consists of the following three components:
![]() Host agent module: This is an audit collection module that runs as a background process on the system being monitored. It is responsible for collecting information related to security on the host and reporting this to the central manager.
Host agent module: This is an audit collection module that runs as a background process on the system being monitored. It is responsible for collecting information related to security on the host and reporting this to the central manager.
![]() LAN manager agent module: This module works in a similar manner as that of a host agent module. However, the difference is that it examines the LAN traffic, as its name implies, rather than security-related events. It also reports the results of analysis to the central manager.
LAN manager agent module: This module works in a similar manner as that of a host agent module. However, the difference is that it examines the LAN traffic, as its name implies, rather than security-related events. It also reports the results of analysis to the central manager.
![]() Central manager module: This is the main module that is responsible for processing and correlating the reports received from the host agent module and LAN manager agent module in order to detect the intrusion.
Central manager module: This is the main module that is responsible for processing and correlating the reports received from the host agent module and LAN manager agent module in order to detect the intrusion.
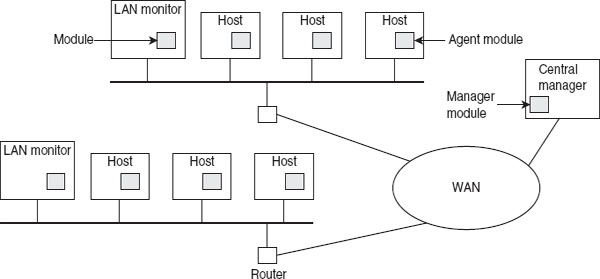
Figure 10.1 Architecture of Distributed Intrusion Detection System
6. List some issues in the design of distributed intrusion detection systems.
Ans.: Although distributed intrusion detection systems are an effective way to prevent intrusion across the network, there are still some issues in its design. These issues are discussed as follows:
![]() In case different hosts in a network are not similar (that is, heterogeneous environment), the native audit collection system used by each host may differ. Further, if intrusion detection is used, different hosts may have their own format for security-related audit records. This necessitates a distributed intrusion detection system to deal with different audit formats.
In case different hosts in a network are not similar (that is, heterogeneous environment), the native audit collection system used by each host may differ. Further, if intrusion detection is used, different hosts may have their own format for security-related audit records. This necessitates a distributed intrusion detection system to deal with different audit formats.
![]() The intrusion detection system can be implemented using either centralized or decentralized architecture. If centralized architecture is used, the entire audit data is collected and analyzed at
a single central location. Though centralizing the data makes the task of correlating the reports easier, it results in a serious bottleneck in case of failure of the central location. On the other hand, if decentralized architecture is used, we have more than one location to collect and analyze the data. To work effectively, the coordination and exchange of information among these locations is required, which results in an extra overhead. Therefore, the choice of which architecture is to be employed is a matter of concern.
The intrusion detection system can be implemented using either centralized or decentralized architecture. If centralized architecture is used, the entire audit data is collected and analyzed at
a single central location. Though centralizing the data makes the task of correlating the reports easier, it results in a serious bottleneck in case of failure of the central location. On the other hand, if decentralized architecture is used, we have more than one location to collect and analyze the data. To work effectively, the coordination and exchange of information among these locations is required, which results in an extra overhead. Therefore, the choice of which architecture is to be employed is a matter of concern.
![]() As many nodes in the network are responsible for collecting and analyzing the audit data, either the raw audit data or summary data needs to be transmitted across the network. This necessitates ensuring the integrity and confidentiality of data being transmitted. Integrity refers to ensuring that the data is not altered by the intruder, and confidentiality is about maintaining the secrecy of the data.
As many nodes in the network are responsible for collecting and analyzing the audit data, either the raw audit data or summary data needs to be transmitted across the network. This necessitates ensuring the integrity and confidentiality of data being transmitted. Integrity refers to ensuring that the data is not altered by the intruder, and confidentiality is about maintaining the secrecy of the data.
7. What are honeypots?
Ans.: Honeypots are a recent innovation in intrusion detection technology. They are the traps that are designed to attract the potential intruders and, thus, track their activities. The main aim of such systems is to collect the information about the intruder's activities, deviate them from accessing the critical systems and boost them to stay on the system for more time so that the network administrator can take actions accordingly.
Honeypots are fabricated to look like real systems by putting real-looking information into them, so that they appear valuable to the potential intruders. However, legitimate users are not allowed to know about or access these systems. Thus, if anyone accesses the honeypots, he or she is a potential attacker. Honeypots are equipped with sensors and loggers to detect accesses and to track the intruder's activities.
8. How are passwords stored in a password file in the UNIX operating system? How are users authenticated?
Ans.: Earlier, in the UNIX operating system, passwords of all users were stored in plaintext in the password file, and the password file was protected by allowing it to be accessed only by the system administrator and privileged users. However, this practice may prove dangerous because any mistake in programming or any other error can make the password file vulnerable to attack. Thus, a new scheme is now used in the UNIX operating system, where the passwords are not stored in plaintext in the password file; instead, a hash of the password is computed and stored in the password file.
Each user in UNIX is allowed to choose a password of maximum eight printable characters, which are converted using 7-bit ASCII to form a 56-bit value. This 56-bit value is used as the encryption key in the encryption function, crypt(3). The crypt(3) function is based on the Data Encryption Standard (DES) algorithm. In UNIX, DES algorithm is modified with the help of 12-bit salt—a value indicating the time a password was assigned to a user. To store a password in the password file, the modified DES algorithm takes a 64-bit block consisting of 0s and encrypts it using the 56-bit encryption key. The resulting 64-bit ciphertext block serves as input for the next encryption. A total of 25 encryptions are performed, and the final obtained 64-bit ciphertext is converted to 11 printable characters. This hashed password is then stored in the password file along with the user ID and the salt.
At the time a user attempts to log on to the system, he or she presents his or her user ID and password to the system. The UNIX operating system uses the supplied user ID as index to find the corresponding entry in the password file. After finding the entry, it extracts the plaintext salt and hashed
password. The salt along with the password supplied by the user are given as input to the crypt(3) function, which then repeats the same process as described earlier to compute the hash of the password. If the newly computed value matches with the stored value in the password file, the user is authenticated; otherwise, the access is denied.
9. Discuss some password selection strategies.
Ans.: Generally, users choose passwords that are short and easy to remember. However, such passwords may be easily guessed, making it simple for intruders to hack into the corresponding user's accounts. On the other hand, if passwords given to the users are long and are randomly generated, it is not effectively possible to crack the passwords. However, such passwords are hard to remember for the users. Thus, some password-selection strategies have been introduced with the aim of building a password that cannot be easily guessed and can be easily remembered. These strategies are listed here:
![]() User education: This strategy is based on educating the users about the importance of using strong passwords that are difficult to guess. The users can also be provided with certain guidelines that help them in choosing hard-to-guess passwords. Though this strategy is simple, it generally fails, especially when there are a large number of users. This is because many users simply ignore the guidelines of selecting strong passwords, while others are unable to judge what a strong password is.
User education: This strategy is based on educating the users about the importance of using strong passwords that are difficult to guess. The users can also be provided with certain guidelines that help them in choosing hard-to-guess passwords. Though this strategy is simple, it generally fails, especially when there are a large number of users. This is because many users simply ignore the guidelines of selecting strong passwords, while others are unable to judge what a strong password is.
![]() Computer-generated passwords: In this strategy, the system randomly generates passwords for the users. Being random, these passwords may or may not be correctly pronounceable. Thus, it becomes difficult for the users to remember the passwords. The situation becomes even worse in case the password is not pronounceable because, in that case, the user does not have any choice except to write down the password somewhere, which makes it subject to be stolen by an intruder. Therefore, this technique is not so popular among the users.
Computer-generated passwords: In this strategy, the system randomly generates passwords for the users. Being random, these passwords may or may not be correctly pronounceable. Thus, it becomes difficult for the users to remember the passwords. The situation becomes even worse in case the password is not pronounceable because, in that case, the user does not have any choice except to write down the password somewhere, which makes it subject to be stolen by an intruder. Therefore, this technique is not so popular among the users.
![]() Reactive password checking: In this strategy, the system executes its own password cracker at regular intervals of time to identify passwords that can be guessed easily. The idea is to determine easy-to-guess passwords and to reject them, thus, improving password security. The system also notifies the corresponding users about the cancellation of their passwords. The disadvantage of this strategy is that any easy-to-guess password in the system remains vulnerable to attack as long as it is not found by the password cracker of the system.
Reactive password checking: In this strategy, the system executes its own password cracker at regular intervals of time to identify passwords that can be guessed easily. The idea is to determine easy-to-guess passwords and to reject them, thus, improving password security. The system also notifies the corresponding users about the cancellation of their passwords. The disadvantage of this strategy is that any easy-to-guess password in the system remains vulnerable to attack as long as it is not found by the password cracker of the system.
![]() Proactive password checker: This strategy allows users to select their passwords on their own. However, it provides sufficient guidance to the users at the time of password selection so that they can select passwords that are strong as well as easy to remember. To achieve this, the system may employ certain rules that must be followed by each user while selecting the password. For example, the system may enforce a rule that the password must be minimum eight characters long and must be the combination of lower case letters, upper case letters and numeric digits. Now, at the time of password selection, if all rules are followed by the user, the system allows the password, else rejects it.
Proactive password checker: This strategy allows users to select their passwords on their own. However, it provides sufficient guidance to the users at the time of password selection so that they can select passwords that are strong as well as easy to remember. To achieve this, the system may employ certain rules that must be followed by each user while selecting the password. For example, the system may enforce a rule that the password must be minimum eight characters long and must be the combination of lower case letters, upper case letters and numeric digits. Now, at the time of password selection, if all rules are followed by the user, the system allows the password, else rejects it.
The proactive password checker strategy is based on creating a balance between the strength of the password and user acceptability. This is essential because, if the system chooses a complex algorithm for determining whether a selected password is acceptable, then too many password rejections may occur and, as a result, the user may not find the system user-friendly. In contrast, if the system uses a simple algorithm, then it may enable a password cracker to understand the basis of password selection and, thus, help them to guess the passwords easily.
10. What do you understand by malicious software?
Ans.: Malicious software (shortened form malware) are programs that generate threats to the computer system and stored data. They could be in the form of viruses, worms, Trojan horses, logic bombs and zombie programs. All malicious programs fall under two categories: one that require a host program such as an application program or a system program in order to be executed by the operating system, and another that can be executed by the operating system independently. Some examples of malicious programs belonging to first category include viruses and logic bombs, while worms and zombie programs are examples of the second category.
11. What is a virus? Explain different types of viruses.
Ans.: Virus (stands for Vital Information Resources Under Seize) is a program or small code segment that is designed to replicate, attach to other programs and perform unsolicited and malicious actions. It enters into the computer system from external sources such as CD, pen drive or e-mail and executes when the infected program is executed. Further, as an infected computer gets in contact with an uninfected computer (for example, through computer networks), the virus may pass on to the uninfected system and destroy data.
Just as flowers are attractive to the bees that pollinate them, virus host programs are deliberately made attractive to victimize the user. They become destructive as soon as they enter a system or are programmed to lie dormant until activated by a trigger. The different types of virus are discussed as follows:
![]() Boot sector virus: This virus infects the master boot record of a computer system. This virus moves the boot record to another sector on the disk, or replaces it with the infected one. It then marks that sector as a bad sector on the disk. This type of virus is very difficult to detect since the boot sector is the first program that is loaded when a computer starts. In effect, the boot sector virus takes full control of the infected computer.
Boot sector virus: This virus infects the master boot record of a computer system. This virus moves the boot record to another sector on the disk, or replaces it with the infected one. It then marks that sector as a bad sector on the disk. This type of virus is very difficult to detect since the boot sector is the first program that is loaded when a computer starts. In effect, the boot sector virus takes full control of the infected computer.
![]() File-infecting virus: This virus infects files with the extensions .com and .exe. This type of virus usually resides inside the memory and infects most of the executable files on a system. The virus replicates by attaching a copy of itself to an uninfected executable program. It then modifies the host programs and, subsequently, when the program is executed, it executes along with it. File-infecting virus can only gain control of the computer if the user or the operating system executes a file infected with the virus.
File-infecting virus: This virus infects files with the extensions .com and .exe. This type of virus usually resides inside the memory and infects most of the executable files on a system. The virus replicates by attaching a copy of itself to an uninfected executable program. It then modifies the host programs and, subsequently, when the program is executed, it executes along with it. File-infecting virus can only gain control of the computer if the user or the operating system executes a file infected with the virus.
![]() Polymorphic virus: This virus changes its code as it propagates from one file to another. Therefore, each copy of virus appears different from others; however, they are functionally similar. This makes the polymorphic virus difficult to detect, like the stealth virus. The variation in copies is achieved by placing superfluous instructions in the virus code or by interchanging the order of instructions that are not dependent. Another more effective means to achieve variation is by using encryption. A part of the virus, called the mutation engine, generates a random key that is used to encrypt the rest of the virus. The random key is kept stored with the virus, while the mutation engine changes by itself. At the time the infected program is executed, the stored key is used by the virus to decrypt itself. Each time the virus replicates, the random key changes.
Polymorphic virus: This virus changes its code as it propagates from one file to another. Therefore, each copy of virus appears different from others; however, they are functionally similar. This makes the polymorphic virus difficult to detect, like the stealth virus. The variation in copies is achieved by placing superfluous instructions in the virus code or by interchanging the order of instructions that are not dependent. Another more effective means to achieve variation is by using encryption. A part of the virus, called the mutation engine, generates a random key that is used to encrypt the rest of the virus. The random key is kept stored with the virus, while the mutation engine changes by itself. At the time the infected program is executed, the stored key is used by the virus to decrypt itself. Each time the virus replicates, the random key changes.
![]() Stealth virus: This virus attempts to conceal its presence from the user. It makes use of compression such that the length of infected program is exactly same as that of the uninfected version. For example, it may keep intercept logic in some I/O routines so that when some other program requests for information from the suspicious portions of the disk using these routines, it will present the original uninfected version to the program. The Stoned Monkey virus is an example
of stealth virus. This virus uses ‘read stealth’ capability, and if a user executes a disk-editing or antivirus program to examine the main boot record, the user would not find any evidence of infection.
Stealth virus: This virus attempts to conceal its presence from the user. It makes use of compression such that the length of infected program is exactly same as that of the uninfected version. For example, it may keep intercept logic in some I/O routines so that when some other program requests for information from the suspicious portions of the disk using these routines, it will present the original uninfected version to the program. The Stoned Monkey virus is an example
of stealth virus. This virus uses ‘read stealth’ capability, and if a user executes a disk-editing or antivirus program to examine the main boot record, the user would not find any evidence of infection.
![]() Multipartite virus: This virus infects both boot sectors and executable files, and uses both mechanisms to spread. It is the worst virus of all because it can combine some or all of the stealth techniques along with polymorphism to prevent detection. For example, if a user runs an application infected with a multipartite virus, the virus activates and infects the hard disk's master boot record. Moreover, the next time the computer starts; the virus gets activated again and starts infecting every program that the user runs. One-half virus is an example of a multipartite virus, which exhibits both stealth and polymorphic behaviour.
Multipartite virus: This virus infects both boot sectors and executable files, and uses both mechanisms to spread. It is the worst virus of all because it can combine some or all of the stealth techniques along with polymorphism to prevent detection. For example, if a user runs an application infected with a multipartite virus, the virus activates and infects the hard disk's master boot record. Moreover, the next time the computer starts; the virus gets activated again and starts infecting every program that the user runs. One-half virus is an example of a multipartite virus, which exhibits both stealth and polymorphic behaviour.
12. What are the typical phases of operation of a virus?
Ans.: Virus is a destructive program that attaches to other programs, replicates itself and performs malicious actions when the host program is executed. The whole operation of a virus involves the following four phases.
![]() Dormant phase: This is the initial phase in the lifetime of a virus. During this phase, the virus remains idle; however, later, it is activated due to occurrence of some events including the date, time, capacity of disk beyond limit or the presence of some other program or file. It may be noted that this phase exists only in case of some viruses and not all.
Dormant phase: This is the initial phase in the lifetime of a virus. During this phase, the virus remains idle; however, later, it is activated due to occurrence of some events including the date, time, capacity of disk beyond limit or the presence of some other program or file. It may be noted that this phase exists only in case of some viruses and not all.
![]() Propagation phase: During this phase, the virus replicates itself and infects other programs as well as some disk areas by putting its identical copies (referred to as clones) into them. All the infected programs now contain the same virus, which has already entered into the propagation phase.
Propagation phase: During this phase, the virus replicates itself and infects other programs as well as some disk areas by putting its identical copies (referred to as clones) into them. All the infected programs now contain the same virus, which has already entered into the propagation phase.
![]() Triggering phase: In this phase, the virus is activated to enter the execution phase, so that it can perform its intended action. The activation of the virus may occur due to the events as specified in dormant phase. In addition, it also takes into account the number of times a single copy of virus replicates itself.
Triggering phase: In this phase, the virus is activated to enter the execution phase, so that it can perform its intended action. The activation of the virus may occur due to the events as specified in dormant phase. In addition, it also takes into account the number of times a single copy of virus replicates itself.
![]() Execution phase: This is the last phase of the virus's operation where it performs the function for which it was designed. The functions performed by viruses range from simple harmless functions such as displaying a message on the screen to serious malicious functions such as destroying programs and data files.
Execution phase: This is the last phase of the virus's operation where it performs the function for which it was designed. The functions performed by viruses range from simple harmless functions such as displaying a message on the screen to serious malicious functions such as destroying programs and data files.
13. Write a short note on the following:
(a) Worms
(b) Trojan horses
(c) Logic bomb
(d) Spyware
Ans.: (a) Worms: Worms are programs constructed to infiltrate into legitimate data processing programs and alter or destroy the data. They often use network connections to spread from one computer system to another; thus, worms attack systems that are linked through communication lines. Once active within a system, worms behave like a virus and perform a number of disruptive actions. To reproduce themselves, worms make use of network medium such as: network mail facility, in which a worm can mail a copy of itself to other systems, remote execution capability, in which a worm can execute a copy of itself on another system and remote log in capability, whereby a worm can log into a remote system as a user and then use commands to copy itself from one system to another.
Both worms and viruses tend to fill computer memory with useless data thereby preventing users from using memory space for the intended applications or programs. In addition, they can destroy or modify data and programs to produce erroneous results, as well as halt the operation of a computer
system or network. Similar to a virus, the operation of a network worm also involves dormant, propagation, triggering and execution phases.
(b)Trojan horse: A Trojan horse is a malicious program that appears to be legal and useful but concurrently does something unexpected, such as destroying existing programs and files. It does not replicate itself in the computer system and, hence, it is not a virus. However, it usually opens the way for other malicious programs such as viruses to enter into the computer system. In addition, it may also allow unauthorized users to access the information stored in the computer.
Trojan horses spread when users are convinced to open or download a program because they think it has come from a legitimate source. They can also be included in software that is freely downloadable. They are usually subtler, especially in the cases where they are used for espionage. They can be programmed to self-destruct, without leaving any evidence other than the damage they have caused. The most famous Trojan horse is a program called back orifice, which is an unsubtle play of words on Microsoft's Back Office suite of programs for NT server. This program allows anybody to have the complete control over the computer or server it occupies.
(c)Logic bomb: A logic bomb is a program or portion of a program that lies dormant until a specific part of program logic is activated. The most common activator for a logic bomb is date. The logic bomb periodically checks the computer system date and does nothing until a pre-programmed date and time is reached. It could also be programmed to wait for a certain message from the programmer. When logic bomb sees the message, it gets activated and executes the code. A logic bomb can also be programmed to activate on a wide variety of other variables such as when a database grows past a certain size or a user's home directory is deleted. For example, the well-known logic bomb is a Michelangelo, which has a trigger set for Michelangelo's birthday. On the given birth date, it causes system crash or data loss or other unexpected interactions with existing code.
(d)Spyware: Spyware are the small programs that install themselves on computers to gather data secretly about the computer user without his or her consent and report the collected data to interested users or parties. The information gathered by the spyware may include e-mail addresses and passwords, net surfing activities, credit card information, etc. Spyware often gets automatically installed on your computer when you download a program from the Internet or click any option from pop-up windows in the browser.
14. What is an antivirus? What are its approaches?
Ans.: An antivirus is an application software that is used for providing protection against malicious software. It is a software utility that (upon installing on a computer) detects viruses and, if found, tries to remove them. The built-in scanner of antivirus software scans all the files on the computer's hard disk to look for particular types of code within programs. Most antivirus programs include an auto-update feature that enables the program to download profiles of new viruses so that it can check for the new viruses as soon as they are discovered. The most popular available antivirus software includes Norton antivirus, McAfee antivirus and Quick Heal antivirus.
Antivirus Approaches
A simple and ideal approach against threat of viruses is to prevent them from entering into the system. Practically, it is not possible to achieve total prevention; however, the frequency of successful virus attacks can be reduced. Thus, an alternative approach is used that is based on the detection, identification and removal of viruses from the infected programs.
![]() Detection: In case the system has been infected by viruses, the first step is to identify that the infection has occurred and where it has occurred, that is, the location of the virus.
Detection: In case the system has been infected by viruses, the first step is to identify that the infection has occurred and where it has occurred, that is, the location of the virus.
![]() Identification: After the infection has been detected and the virus located, the next step is to determine the specific type of virus that has infected the file.
Identification: After the infection has been detected and the virus located, the next step is to determine the specific type of virus that has infected the file.
![]() Removal: After identifying the specific virus in a file, the final step is to remove it completely from the infected file and to bring the file back to its original state. The virus must be removed from all the systems in the network in order to prevent it from spreading further.
Removal: After identifying the specific virus in a file, the final step is to remove it completely from the infected file and to bring the file back to its original state. The virus must be removed from all the systems in the network in order to prevent it from spreading further.
15. List and brief the different generations of antivirus software.
Ans.: Earlier, viruses were simple code fragments; thus, antivirus software packages used for those viruses were also simpler. However, with the evolution in virus as well as antivirus technology, the attackers have generated more complex viruses that are not easily detectable. To protect against such viruses, antivirus software have also grown complex. The growth of antivirus software has been divided into four generations which are as follows:
![]() First generation: The antivirus software of this generation used simple scanners that rely on virus signatures to detect viruses. It detects viruses that have basically the same structure and the same bit pattern in all copies. However, these types of scanners can detect only the known viruses. Another type of scanner used in the first generation maintains a record of the program length, and monitors the change in length for detecting the viruses.
First generation: The antivirus software of this generation used simple scanners that rely on virus signatures to detect viruses. It detects viruses that have basically the same structure and the same bit pattern in all copies. However, these types of scanners can detect only the known viruses. Another type of scanner used in the first generation maintains a record of the program length, and monitors the change in length for detecting the viruses.
![]() Second generation: The antivirus software of this generation used heuristic scanners that rely on some heuristic rules to detect virus infections. One approach to detect virus infection is to scan the files and look for code fragments that are usually related to viruses. For example, in case of a polymorphic virus, the scanner may determine the starting of the encryption loop and then find the encryption key. Once the scanner has found the key, it cleans the virus infection from the infected program by decrypting the code fragment with the key and then returns the virus-free program back to service.
Second generation: The antivirus software of this generation used heuristic scanners that rely on some heuristic rules to detect virus infections. One approach to detect virus infection is to scan the files and look for code fragments that are usually related to viruses. For example, in case of a polymorphic virus, the scanner may determine the starting of the encryption loop and then find the encryption key. Once the scanner has found the key, it cleans the virus infection from the infected program by decrypting the code fragment with the key and then returns the virus-free program back to service.
Another approach for detecting virus infection is integrity checking. In this approach, a checksum is added at the end of each program. If any program gets infected by a virus, however, with no change in the checksum, the change in program can be detected by performing an integrity check. On the other hand, if a virus is so complex that it changes the checksum in addition to the program, then an encrypted hash function can be used to deal with the virus. By storing the encryption key at a different location from that of the program, we can prevent a virus from generating a new hash code and then encrypting it. Moreover, the use of the hash function instead of checksum prevents the virus from adapting the program to generate the same hash code as previously.
![]() Third generation: The antivirus software of this generation are the memory-resident programs that do not take into account the structure of viruses or heuristic rules to identify them. Rather, they scan the program to look for a small set of actions that indicate the infection and then deal with the viruses. An advantage is that it is not required to maintain any signatures or rules for a wide range of viruses in order to detect an infection.
Third generation: The antivirus software of this generation are the memory-resident programs that do not take into account the structure of viruses or heuristic rules to identify them. Rather, they scan the program to look for a small set of actions that indicate the infection and then deal with the viruses. An advantage is that it is not required to maintain any signatures or rules for a wide range of viruses in order to detect an infection.
![]() Fourth generation: The antivirus software of this generation are the packages that use scanning and activity trapping components in conjunction. These packages also comprise the access control capability, which restricts the viruses from entering into the system and updating the files for spreading the infection. All these features collectively strengthen the ability of the antivirus software.
Fourth generation: The antivirus software of this generation are the packages that use scanning and activity trapping components in conjunction. These packages also comprise the access control capability, which restricts the viruses from entering into the system and updating the files for spreading the infection. All these features collectively strengthen the ability of the antivirus software.
16. What is digital immune system? Explain how it works.
Ans.: With the increased use of Internet-based capabilities such as integrated mail systems (Lotus Notes and Microsoft Outlook) and mobile-program systems (Java and ActiveX), the threat of Internet-based virus propagation has also risen. Therefore, IBM has developed the digital immune system in response to these Internet-based virus threats. The goal of this system is to offer a very fast response time so that the viruses can be removed instantly as they enter into the system. Whenever a new virus is introduced into an organization, it is automatically captured by the digital immune system, which then examines it, adds detection and shielding for it and removes it from the system. The immune system also passes the information related to that virus to the other systems that are running the IBM antivirus, so that those systems can detect this virus before it begins to run.
The operation of the digital immune system involves the following steps (see Figure 10.2):
1. The monitoring program installed on each client machine in the organization detects the presence of a virus using various heuristic rules based on system behaviour, virus signatures or unexpected changes in the programs. In case any program on a client machine is found infected by a virus, the monitoring program sends a copy of that program to the administrative machine within the organization.
2. The administrative machine encrypts the copy of infected program received from monitoring program and forwards it to a central virus analysis machine.
3. The virus analysis machine is responsible for analyzing the infected program to detect new viruses. It creates an environment in which the infected program can be executed and analyzed. During execution, the structure and behaviour of the virus is analyzed and, based on this analysis, a virus signature is extracted. Now, the virus analysis machine examines the infected program for the extracted signature and produces a prescription for identifying and removing that virus.
4. The prescription produced by the virus analysis machine is then sent back to the administrative machine from where the infected program came.
5. The administrative machine sends the prescription to the infected client machine as well as to other client machines in the organization.
6. The prescription is also forwarded to all the subscribers and the individual user who are outside the organization network, so that they too can protect their systems from the new virus.
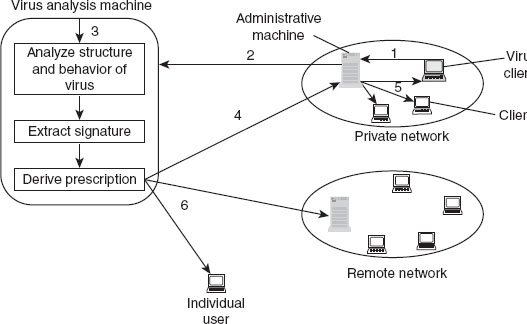
Figure 10.2 Operation of Digital Immune System
17. Discuss on behaviour-blocking software?
Ans.: Behaviour-blocking software is an approach to countering viruses that, unlike other approaches, is integrated with the operating system of a host computer. To detect a program for viral infections, it monitors the behaviour of a program in real time to determine any malicious actions. In case any attempt for a malicious action is detected, the behaviour-blocking software blocks the malicious action before it can affect the system. Certain malicious actions for which a program is analyzed are as follows:
![]() Attempts for viewing, opening, deleting and modifying files
Attempts for viewing, opening, deleting and modifying files
![]() Attempts for formatting disk drives
Attempts for formatting disk drives
![]() Starting network communications
Starting network communications
![]() Changes in important system settings
Changes in important system settings
![]() Changes in the logic of executable files.
Changes in the logic of executable files.
Behaviour-blocking software can block the malicious behaviours of a program in real time and/or terminate the entire program if it detects that the program may cause threat as it executes. The advantage of this software over other antivirus approaches is that it is able to detect and then block the malicious actions even if the instructions of a malicious code are modified or rearranged in order to evade detection. However, the disadvantage is that the as behaviours of a malicious code can be identified only after actually executing it on the machine, the malicious code may cause severe destruction to the system before its behaviours have been detected and blocked by the behaviour-blocking software.
18. What do you mean by firewall? Describe its characteristics.
Ans.: The progressive use of the Internet in organizations has opened up possibilities for the outside world to interact with internal networks, creating a great threat to the organization. Usually, organizations have huge amount of confidential data, leaking of which may prove to be a serious setback. Moreover, it is also necessary to protect the internal network against malicious programs such as virus and worms. Therefore, some mechanism is needed to ensure that the valuable data within the organization remains inside, as well as that outside attackers cannot break the security of the internal network.
A firewall is a mechanism that protects and isolates the internal network from the outside world. Simply put, a firewall prevents certain outside connections from entering into the network. It traps inbound or outbound packets, analyses them, and then permits access or discards them. Basically, a firewall is a router or a group of routers and computers that filter the traffic and implement access control between an un-trusted network (Internet) and the more trusted internal networks. Depending on the criteria used for filtering traffic, there are three common types of firewalls: packet filters (or packet-filtering router), application-level gateways and circuit-level gateways.
The characteristics of a firewall are as follows:
![]() A firewall specifies a single choke point by consolidating all the security-related capabilities into a single system or a set of systems. This results in simplified security management.
A firewall specifies a single choke point by consolidating all the security-related capabilities into a single system or a set of systems. This results in simplified security management.
![]() The choke point stops vulnerable services from entering or exiting through the network, prevents the intruders from accessing the protected network and protects against attacks such as IP spoofing.
The choke point stops vulnerable services from entering or exiting through the network, prevents the intruders from accessing the protected network and protects against attacks such as IP spoofing.
![]() It provides support for performing various Internet functions such as mapping a local address to an Internet address or maintaining logs for recording the usage of Internet, etc.
It provides support for performing various Internet functions such as mapping a local address to an Internet address or maintaining logs for recording the usage of Internet, etc.
![]() Virtual private networks can be implemented using firewalls.
Virtual private networks can be implemented using firewalls.
![]() A firewall specifies a single location from where all security-related events can be monitored and analyzed. Alarms and audits can also be used with firewall systems to protect against unauthorized events.
A firewall specifies a single location from where all security-related events can be monitored and analyzed. Alarms and audits can also be used with firewall systems to protect against unauthorized events.
19. List some limitations of firewalls.
Ans.: Though the firewall is an effective means of providing security to an organization, it has certain limitations, which are as follows:
![]() A firewall provides effective security to the internal network if it is configured as the only entry-exit point in the organization. However, if there are multiple entry-exit points in the organization and firewall is implemented at just one of them, then the incoming or outgoing traffic may bypass the firewall. This makes the internal network susceptible to attack through the points where the firewall has not been implemented.
A firewall provides effective security to the internal network if it is configured as the only entry-exit point in the organization. However, if there are multiple entry-exit points in the organization and firewall is implemented at just one of them, then the incoming or outgoing traffic may bypass the firewall. This makes the internal network susceptible to attack through the points where the firewall has not been implemented.
![]() A firewall is designed to protect against outside attacks. However, it does not have any mechanism to protect against internal threats such as an employee of a company who unknowingly helps an external attacker.
A firewall is designed to protect against outside attacks. However, it does not have any mechanism to protect against internal threats such as an employee of a company who unknowingly helps an external attacker.
![]() The firewall does not provide protection against any virus-infected program or files being transferred through the internal network. This is because it is almost impossible to scan all the files entering in the network for viruses. To protect the internal network against virus threats, a separate virus detection and removal strategy should be used.
The firewall does not provide protection against any virus-infected program or files being transferred through the internal network. This is because it is almost impossible to scan all the files entering in the network for viruses. To protect the internal network against virus threats, a separate virus detection and removal strategy should be used.
20. Discuss the packet-filtering router firewall.
Ans.: A packet-filtering router, also known as screening router or screening filter, is the one of the oldest firewall technologies that operates at the network layer. It examines the incoming and outgoing packets by applying a fixed set of rules on them and, thus, determines whether to forward the packets or to reject them. The rules used for filtering the packets are defined based on the following information contained in a network (IP) packet.
![]() The IP address of the system from where the packet has come
The IP address of the system from where the packet has come
![]() The IP address of the system for which the packet is destined
The IP address of the system for which the packet is destined
![]() The transport layer protocol used such as TCP or UDP
The transport layer protocol used such as TCP or UDP
![]() Transport-level address (that is, port number) of source and destination, which identifies the application such as Telnet or SNMP
Transport-level address (that is, port number) of source and destination, which identifies the application such as Telnet or SNMP
![]() The interface of the router where the packet came from or is destined to.
The interface of the router where the packet came from or is destined to.
The filtering rules specify which packets are allowed to pass through and in which direction they should flow, that is, from external to internal network or vice versa. Each rule has a specified action associated with it, either to allow or to deny a packet. Thus, there are two sets of filtering rules: allow, which permits the traffic, and deny, which discards the traffic. While examining a packet, if a match is found with any of the allow set of rules, then the packet is forwarded to the desired destination. On the other hand, if a match is found with any of the deny set of rules, the packet is discarded. In case no match is found, the default action is taken. The default policy can be either to forward or discard the packet. The former default policy provides more ease of use to the end users; however, it offers a reduced level of security. In contrast, the latter default policy is more conservative; however, it provides more security. Therefore, generally, the implementation of a firewall is initiated with default discard policy and, later, packet filtering is enforced by applying the rules one by one.
Advantages
Some advantages of packet filters are as follows:
![]() They are simple, since a single rule is enough to indicate whether to allow or deny the packet.
They are simple, since a single rule is enough to indicate whether to allow or deny the packet.
![]() They are transparent to the users; the users need not know the existence of packet filters.
They are transparent to the users; the users need not know the existence of packet filters.
![]() They operate at a fast speed as compared to other techniques.
They operate at a fast speed as compared to other techniques.
![]() The client computers need not be configured specially while implementing packet-filtering firewalls.
The client computers need not be configured specially while implementing packet-filtering firewalls.
![]() They protect the IP addresses of internal hosts from the outside network.
They protect the IP addresses of internal hosts from the outside network.
Disadvantages
Some disadvantages of packet filters are as follows:
![]() They are unable to inspect the application layer data in the packets and thus, cannot restrict access to ftp services.
They are unable to inspect the application layer data in the packets and thus, cannot restrict access to ftp services.
![]() It is a difficult task to set up the packet-filtering rules correctly.
It is a difficult task to set up the packet-filtering rules correctly.
![]() They lack support for authentication and have no alert mechanisms.
They lack support for authentication and have no alert mechanisms.
![]() Being stateless in nature, they are not well suited to application layer protocols.
Being stateless in nature, they are not well suited to application layer protocols.
21. What kind of attacks is possible on packet-filtering firewalls. Suggest appropriate countermeasures.
Ans.: Though packet-filtering firewalls operate at a fast speed and do not require users to be aware of packet filters, they are still prone to some attacks, which are as follows:
![]() IP address spoofing: In this attack, an intruder external to the organization's network sends a packet towards the network. The IP address of this packet is the same as that of one of the hosts in the network. The attacker thinks that he or she can penetrate into the internal network by spoofing IP address and, therefore, can attack on the systems easily. To prevent such attacks, packet-filtering firewalls should discard all the packets coming to the organization's network, which contains the IP address of any internal host.
IP address spoofing: In this attack, an intruder external to the organization's network sends a packet towards the network. The IP address of this packet is the same as that of one of the hosts in the network. The attacker thinks that he or she can penetrate into the internal network by spoofing IP address and, therefore, can attack on the systems easily. To prevent such attacks, packet-filtering firewalls should discard all the packets coming to the organization's network, which contains the IP address of any internal host.
![]() Source routing attack: In this attack, an intruder specifies the pre-defined route that a packet should take to reach its destination by selecting a particular option in the IP packet header. By choosing such an option, the intruder hopes that the packet-filtering firewall will bypass the security measures of checking the source routing information. The countermeasure for this attack is that packet-filtering firewalls should discard all the packets that are using this option.
Source routing attack: In this attack, an intruder specifies the pre-defined route that a packet should take to reach its destination by selecting a particular option in the IP packet header. By choosing such an option, the intruder hopes that the packet-filtering firewall will bypass the security measures of checking the source routing information. The countermeasure for this attack is that packet-filtering firewalls should discard all the packets that are using this option.
![]() Tiny fragment attack: In this attack, an intruder takes advantage of the IP packet fragmentation option and intentionally divides the original IP packet into small fragments. This is done to force the TCP header information to go into a separate packet fragment. The intruder hopes that the filtering rules that are based on the TCP header information can be circumvented this way, and that the packet-filtering firewall can be fooled such that it will examine only the first fragment of the packet and the rest will bypass through it without any checks. This attack can be prevented by discarding all the fragmented packets that are using TCP as the upper-layer protocol type.
Tiny fragment attack: In this attack, an intruder takes advantage of the IP packet fragmentation option and intentionally divides the original IP packet into small fragments. This is done to force the TCP header information to go into a separate packet fragment. The intruder hopes that the filtering rules that are based on the TCP header information can be circumvented this way, and that the packet-filtering firewall can be fooled such that it will examine only the first fragment of the packet and the rest will bypass through it without any checks. This attack can be prevented by discarding all the fragmented packets that are using TCP as the upper-layer protocol type.
22. Write a short note on application-level gateways.
Ans.: An application-level gateway operates at the application layer of the OSI model. It is also termed as a proxy server (or simply called proxy), which handles the flow of application-level traffic. The operation of application-level gateways is as follows:
1. A user contacts the application gateway with the help of a TCP/IP application such as Telnet, FTP or HTTP.
2. In response, the application gateway asks the user for the name, IP address and other information about the remote host that is to be accessed. It also asks the user to present its user ID and password to access the gateway.
3. The user supplies a valid user ID, password and other desired information to the gateway.
4. After verifying the user, the application gateway contacts the application running on the remote host on behalf of the user. The TCP segments comprising the application data are exchanged between the two end points.
5. Now, the application gateway serves as a proxy of the original user and delivers application data in both directions, from remote host to the user and vice versa.
Advantages
Application-level gateways are considered the most secure type of firewalls since they provide a number of advantages, which are as follows:
![]() The entire communication between the internal and external network happens only through the application gateways. This protects the internal IP addresses from the external network.
The entire communication between the internal and external network happens only through the application gateways. This protects the internal IP addresses from the external network.
![]() The use of application gateways provides transparency between the users and the external network.
The use of application gateways provides transparency between the users and the external network.
![]() They understand and implement high-level protocols such as HTTP and FTP.
They understand and implement high-level protocols such as HTTP and FTP.
![]() They support functions such as user authentication, caching, auditing and logging.
They support functions such as user authentication, caching, auditing and logging.
![]() They can process and manipulate the packet data.
They can process and manipulate the packet data.
![]() Strong user authentication can be enforced with application gateways.
Strong user authentication can be enforced with application gateways.
![]() They can disallow access to certain network services and allow others at the same time.
They can disallow access to certain network services and allow others at the same time.
Disadvantages
Some disadvantages of application-level gateways are as follows:
![]() Each new network service requires a number of proxy services to be added. Thus, application-level gateways are not scalable.
Each new network service requires a number of proxy services to be added. Thus, application-level gateways are not scalable.
![]() The addition of proxy services causes client applications to be modified.
The addition of proxy services causes client applications to be modified.
![]() Application gateways operate at a slower speed and, as a result, network performance degrades.
Application gateways operate at a slower speed and, as a result, network performance degrades.
![]() As they rely on the support provided by the underlying operating system, they are vulnerable to the bugs in the system.
As they rely on the support provided by the underlying operating system, they are vulnerable to the bugs in the system.
23. When the system administrator trusts the internal users, what type of firewall is to be used? What are its advantages and disadvantages?
Ans.: For a situation where the system administrator trusts the internal users, circuit-level gateways are the best suited. Circuit-level firewalls operate in a similar manner as that of packet-filtering firewalls, except that they operate at the session and transport layers of the OSI model. Whenever a session is to be established between a host in the internal network and a host outside the internal network, two TCP connections are to be established, one between the TCP user in the internal network and the circuit-level gateway, and another between the circuit-level gateway and the TCP user in the external network. After both the connections have been established, the circuit-level gateway forwards the packet from one connection to another without inspecting their contents. This is because, in circuit-level gateways, the session is validated before opening the connections. Thus, there is no need to examine the packet contents once the session has been established.
Circuit-level gateways maintain a virtual table to store session-related information of all the valid connections. This information includes the session date, a unique session identifier, connection state, IP addresses of source and destination, the sequencing information and the physical network interface through which the packet has come and has to go. Rather than allowing all packets that meet the rule set requirements to pass, it allows only those packets that are part of a valid, established connection.
Advantages
Some advantages of circuit-level gateways are as follows:
![]() They operate at a faster speed as compared to application-level gateways.
They operate at a faster speed as compared to application-level gateways.
![]() They offer more security than packet filters.
They offer more security than packet filters.
![]() They are not subject to IP address spoofing attacks.
They are not subject to IP address spoofing attacks.
![]() They perform network address translation (NAT) by changing source node IP address to its own and, thus, protecting internal host IP addresses from the external network.
They perform network address translation (NAT) by changing source node IP address to its own and, thus, protecting internal host IP addresses from the external network.
Disadvantages
Some disadvantages of circuit-level gateways are as follows:
![]() They are unable to perform security checks on higher-level protocols.
They are unable to perform security checks on higher-level protocols.
![]() They can restrict access only to TCP protocol subsets.
They can restrict access only to TCP protocol subsets.
![]() They have only a confined audit event generation capability.
They have only a confined audit event generation capability.
24. What is the role of bastion host?
Ans.: A bastion host is a system in an organization's internal network that acts as a vital point in the security of the network. This system is distinguished from other systems by the firewall administrator and serves as a platform for an application-level or circuit-level gateway. The hardware platform of the bastion host executes a secured version of the operating system and, therefore, behaves like a trusted system. Moreover, only limited proxy applications that are considered necessary by the network administrator, such as Telnet, DNS and SMTP, are installed on the bastion host. It requires additional authentication if any user wants access to these proxy services, and each proxy service needs its own authentication. Thus, the role of bastion host is to enhance the security of the network, so that it becomes more difficult for intruders to gain access to the internal network.
25. Describe the common types of firewall configurations.
Ans.: Firewalls may be implemented as a single system, such as a single packet filter or a single application gateway, or it may be implemented as a combination of packet filters and application gateways. There are three possible firewall configurations, which are as follows:
![]() Screened host firewall, single-homed bastion: In this firewall configuration, a packet filter and an application gateway (bastion host) are used in combination. The packet filter checks the traffic from the Internet to the internal corporate network and from the internal corporate network to the Internet, based on the specific rule. It allows packets from outside the network to enter the internal network if it is destined for the application gateway. Similarly, it allows packets from the internal network to move to the outside network only if the packet has originated from the application gateway. The application gateway is responsible for performing authentication and proxy functions.
Screened host firewall, single-homed bastion: In this firewall configuration, a packet filter and an application gateway (bastion host) are used in combination. The packet filter checks the traffic from the Internet to the internal corporate network and from the internal corporate network to the Internet, based on the specific rule. It allows packets from outside the network to enter the internal network if it is destined for the application gateway. Similarly, it allows packets from the internal network to move to the outside network only if the packet has originated from the application gateway. The application gateway is responsible for performing authentication and proxy functions.
This firewall configuration enhances the security of the network by implementing both packet-level and application-level filtering. The intruder now has to penetrate two separate firewalls in order to breach the security of the network. Moreover, it allows the network administrator more freedom in defining security policy. However, the demerit of this configuration is that internal hosts are connected to the packet filter as well as the application gateway. Therefore, if the security of the packet filter router is compromised, then an intruder can gain access to the whole internal network.
![]() Screened host firewall, dual-homed bastion: In this firewall configuration, the internal hosts of the network are not directly connected to the packet filter. Rather, the packet filter is directly connected only to the application gateway, which has separate connections with the internal hosts. This arrangement overcomes the problem of a screened host, single-homed bastion configuration. Thus, even if the packet filter is successfully attacked by an intruder, he or she gains access only to the application gateway and not to the whole network.
Screened host firewall, dual-homed bastion: In this firewall configuration, the internal hosts of the network are not directly connected to the packet filter. Rather, the packet filter is directly connected only to the application gateway, which has separate connections with the internal hosts. This arrangement overcomes the problem of a screened host, single-homed bastion configuration. Thus, even if the packet filter is successfully attacked by an intruder, he or she gains access only to the application gateway and not to the whole network.
![]() Screened subnet firewall: In this firewall configuration, two packet filters and one application gateway are used. One of the packet filters connects the outside network with the application gateway and other packet filter connects the internal hosts with the application gateway. It is the most secured type of configuration as an intruder has to attack three levels before gaining an access to the internal network.
Screened subnet firewall: In this firewall configuration, two packet filters and one application gateway are used. One of the packet filters connects the outside network with the application gateway and other packet filter connects the internal hosts with the application gateway. It is the most secured type of configuration as an intruder has to attack three levels before gaining an access to the internal network.
26. What do you understand by a trusted system?
Ans.: A computer and operating system that can be relied upon to a determined level to implement a given security policy is referred to as a trusted system. In other words, a trusted system is defined as the one system whose failure may cause a specified security policy to be compromised. Trusted systems are of prime importance in areas where it is required to protect the system resources or the information on the basis of levels of security defined; that is, where multilevel security is needed. For example, in military, the information is classified into various levels such as unclassified (U), confidential (C), secret (S) and top secret (TS), and each user is allowed to access only certain levels of information. In addition to military, the trusted systems are also being prominently used nowadays in banking and financial areas.
Central to the trusted systems is the reference monitor, which is an entity residing in the operating system of a computer and entrusted the responsibility of making all the access-control-related decisions on the basis of the defined security levels. The reference monitor is expected to be tamperproof, always invoked and subject to independent testing.
Multiple-choice Questions
1. Which of the following is a type of intruder?
(a) Masquerader
(b) Misfeasor
(c) Clandestine user
(d) All of these
2. The __________ strategy aware all the users about the importance of non-guessable or strong passwords.
(a) User education
(b) Reactive password checking
(c) Proactive password checker
(d) None of these
3. A virus is a computer __________.
(a) File
(b) Network
(c) Program
(d) Database
4. A __________ replicates itself by creating its own copies, in order to bring the network to a halt.
(a) Worm
(b) Virus
(c) Trojan horse
(d) Logic bomb
5. The __________ generation of antivirus software uses heuristic scanners.
(a) First
(b) Second
(c) Third
(d) Fourth
6. The digital immune system was developed by __________.
(a) HCL
(b) IEEE
(c) ANSI
(d) IBM
7. The firewall should be situated __________.
(a) Outside a network
(b) Inside a network
(c) Between a network and the outside world
(d) None of these
8. __________ firewall is mostly used in small businesses.
(a) Packet-filtering
(b) Circuit-level gateway
(c) Application-level gateway
(d) None of these
9. Circuit-level gateways are __________ as compared to packet filters.
(a) Less secure
(b) More secure
(c) Slower
(d) None of these
10. The trap set to attract the potential intruders is known as __________.
(a) Honeypot
(b) Trapdoor
(c) Proxy
(d) All of these
Answers
1. (d)
2. (a)
3. (c)
4.(a)
5.(b)
6.(d)
7.(c)
8.(a)
9.(b)
10.(a)
