1
Overview of Network Security
1. What is the need for network security? Explain its goals.
Ans.: During the last two decades, computer networks have revolutionized the use of information. Information is now distributed over the network. Authorized users can use computer networks for sending and receiving information from a distance. People can also perform various tasks such as shopping, bill payments and banking over a computer network. This implies that the computer networks are nowadays used for carrying personal as well as financial data. Thus, it becomes important to secure the network, so that unauthorized people cannot access such sensitive information.
For secure communication, there are some basic goals of network security that should be achieved. These are as follows:
![]() Confidentiality: This refers to maintaining the secrecy of the message being transmitted over a network. Only the sender and the intended receiver should be able to understand and read the message, and eavesdroppers should not be able to read or modify the contents of the message. To achieve confidentiality the message should be transmitted over the network in an encrypted form.
Confidentiality: This refers to maintaining the secrecy of the message being transmitted over a network. Only the sender and the intended receiver should be able to understand and read the message, and eavesdroppers should not be able to read or modify the contents of the message. To achieve confidentiality the message should be transmitted over the network in an encrypted form.
![]() Integrity: Any message sent over the network must reach the intended receiver without any modification made to it. If any changes are made, the receiver must be able to detect that some alteration has happened. Integrity can be achieved by attaching a checksum to the message. This checksum ensures that an attacker cannot alter the message and, hence, that integrity is preserved.
Integrity: Any message sent over the network must reach the intended receiver without any modification made to it. If any changes are made, the receiver must be able to detect that some alteration has happened. Integrity can be achieved by attaching a checksum to the message. This checksum ensures that an attacker cannot alter the message and, hence, that integrity is preserved.
![]() Availability: Information created and stored by an organization should be available all the time to authorized users, failing which the information ceases to be useful. Availability is also equally important for organizations, because unavailability of information can adversely affect an organization's day-to-day operations. For example, imagine the status/service of a bank if its customers are unable to make transactions using their accounts.
Availability: Information created and stored by an organization should be available all the time to authorized users, failing which the information ceases to be useful. Availability is also equally important for organizations, because unavailability of information can adversely affect an organization's day-to-day operations. For example, imagine the status/service of a bank if its customers are unable to make transactions using their accounts.
2. What are the principles of network security?
Ans.: The principles of network security include confidentiality, integrity, availability, nonrepudiation, access control and authentication.
![]() Confidentiality: Refer previous question.
Confidentiality: Refer previous question.
![]() Integrity: Refer previous question.
Integrity: Refer previous question.
![]() Availability: Refer previous question.
Availability: Refer previous question.
![]() Nonrepudiation: After a message has been sent and received, the sender and receiver should not be able to deny about the sending and receiving of the message, respectively. The receiver should be able to prove that the message has come from the intended sender and not from anyone else. In addition, the receiver should be able to prove that the received message's contents are the same as sent by the sender.
Nonrepudiation: After a message has been sent and received, the sender and receiver should not be able to deny about the sending and receiving of the message, respectively. The receiver should be able to prove that the message has come from the intended sender and not from anyone else. In addition, the receiver should be able to prove that the received message's contents are the same as sent by the sender.
![]() Access control: The term ‘access’ involves writing, reading, executing and modifying. Thus, access control determines and controls who can access what. It regulates which user has access to a resource, under what circumstances the access is possible and which operations the user can perform on that resource. For example, we can specify that user
Access control: The term ‘access’ involves writing, reading, executing and modifying. Thus, access control determines and controls who can access what. It regulates which user has access to a resource, under what circumstances the access is possible and which operations the user can perform on that resource. For example, we can specify that user A is allowed to only view the records in a database but not to modify them. However, user B is allowed to read as well as update the records.
![]() Authentication: Authentication is concerned with determining whom you are communicating with. Authentication is necessary to ensure that the receiver has received the message from the actual sender, and not from an attacker. That is, the receiver should be able to authenticate the sender, which can be achieved by sharing a common secret code word, by sending digital signatures or by the use of digital certificates.
Authentication: Authentication is concerned with determining whom you are communicating with. Authentication is necessary to ensure that the receiver has received the message from the actual sender, and not from an attacker. That is, the receiver should be able to authenticate the sender, which can be achieved by sharing a common secret code word, by sending digital signatures or by the use of digital certificates.
3. Define a network security attack?
Ans.: A network security attack refers to an act of breaching the security or authentication routines of a network. Such an act is a threat to the basic goals of secure communication, such as confidentiality, integrity and authentication.
4. Explain passive attacks and active attacks.
Ans.: Network security attacks can be classified into two categories—passive attacks and active attacks.
Passive Attacks
In a passive attack, the attacker indulges in eavesdropping, that is, listening to a communication channel and monitoring the contents of a message. The term ‘passive’ indicates that the main goal of the intruder is just to gather information and not to do any alteration to the message or harm the system resources. A passive attack is hard to recognize, as the message is not tampered with or altered; therefore, the sender and receiver remains unaware that the message contents have been read by another party. However, some measures such as encryption are available to prevent such attacks.
Two types of passive attacks are:
![]() Release of message contents: This type of passive attack involves (1) capturing the sensitive information that is sent via email or (2) tapping a conversation that is conducted over a telephone line.
Release of message contents: This type of passive attack involves (1) capturing the sensitive information that is sent via email or (2) tapping a conversation that is conducted over a telephone line.
![]() Traffic analysis: In this type of attack, an intruder observes the frequency and length of messages being exchanged between communicating nodes. A passive attacker can then use this information for guessing the nature of the communication that was taking place.
Traffic analysis: In this type of attack, an intruder observes the frequency and length of messages being exchanged between communicating nodes. A passive attacker can then use this information for guessing the nature of the communication that was taking place.
Active Attacks
In an active attack, an intruder either alters the original message or creates a fake message. This attack tries to affect the operation of system resources. When compared to passive attacks, it is easier to recognize an active attack, but harder to prevent it. Active attacks can be classified into four categories, as follows:
![]() Masquerade: In computer terms, ‘masquerading’ is said to happen when an entity impersonates another. In such an attack, an unauthorized entity tries to gain more privileges than it is authorized for. Masquerading is generally done by using stolen IDs and passwords, or through bypassing authentication mechanisms.
Masquerade: In computer terms, ‘masquerading’ is said to happen when an entity impersonates another. In such an attack, an unauthorized entity tries to gain more privileges than it is authorized for. Masquerading is generally done by using stolen IDs and passwords, or through bypassing authentication mechanisms.
![]() Replay: This active attack involves capturing a copy of the message sent by the original sender and retransmitting it later to bring about an unauthorized result.
Replay: This active attack involves capturing a copy of the message sent by the original sender and retransmitting it later to bring about an unauthorized result.
![]() Modification of messages: This attack involves making certain modifications to the captured message, or delaying or reordering the messages to cause an unauthorized effect.
Modification of messages: This attack involves making certain modifications to the captured message, or delaying or reordering the messages to cause an unauthorized effect.
![]() Denial of service (DoS): This attack prevents the normal functioning or proper management of communication facilities. For example, a network server can be overloaded by unwanted packets, thus resulting in performance degradation. DoS attacks can interrupt and slow down the services of a network, or even completely jam a network.
Denial of service (DoS): This attack prevents the normal functioning or proper management of communication facilities. For example, a network server can be overloaded by unwanted packets, thus resulting in performance degradation. DoS attacks can interrupt and slow down the services of a network, or even completely jam a network.
5. Explain various network security services.
Ans.: The International Telecommunication Union-Telecommunication Standardization Sector (ITU-T), also known as X.800, defines security service as ‘a service provided by a protocol layer of communicating open system, which ensures adequate security of the systems or of data transfers’. Another definition of security service is found in RFC 2828, which defines it as ‘a processing or communication service that is provided by a system to give a specific kind of protection to system resources; security services implement security policies and are implemented by security mechanisms’. According to X.800, security services are divided into five categories and 14 specific services (see Figure 1.1).

Figure 1.1 Security Services
![]() Authentication: This service provides the assurance that the communicating party at the other end of the line is the correct party. Two types of authentication services defined by X.800 are:
Authentication: This service provides the assurance that the communicating party at the other end of the line is the correct party. Two types of authentication services defined by X.800 are:
![]() Peer entity authentication: This provides authentication of the receiver or sender during the connection establishment phase in connection-oriented communication.
Peer entity authentication: This provides authentication of the receiver or sender during the connection establishment phase in connection-oriented communication.
![]() Data origin authentication: This service provides authentication of the data source in a connectionless communication.
Data origin authentication: This service provides authentication of the data source in a connectionless communication.
![]() Nonrepudiation: This service provides the assurance that the sender and receiver are not able to deny about the sending and receiving of the message, respectively. X.800 defines two types of services for nonrepudiation:
Nonrepudiation: This service provides the assurance that the sender and receiver are not able to deny about the sending and receiving of the message, respectively. X.800 defines two types of services for nonrepudiation:
![]() Origin nonrepudiation: This helps the receiver prove that the message was sent by the intended sender.
Origin nonrepudiation: This helps the receiver prove that the message was sent by the intended sender.
![]() Destination nonrepudiation: This helps the sender prove that the message was delivered to the intended receiver.
Destination nonrepudiation: This helps the sender prove that the message was delivered to the intended receiver.
![]() Data confidentiality: This service provides protection against the disclosure of data to unauthorized parties. For data confidentiality, X.800 defines four types of services:
Data confidentiality: This service provides protection against the disclosure of data to unauthorized parties. For data confidentiality, X.800 defines four types of services:
![]() Connection confidentiality: This provides confidentiality for all the messages transmitted between two users on a connection-oriented transmission, such as over a TCP connection.
Connection confidentiality: This provides confidentiality for all the messages transmitted between two users on a connection-oriented transmission, such as over a TCP connection.
![]() Connectionless confidentiality: This service provides confidentiality for all user data in a single data block.
Connectionless confidentiality: This service provides confidentiality for all user data in a single data block.
![]() Selective-field confidentiality: This provides confidentiality for a single message or some selected data fields of a message in a single data block or on a connection.
Selective-field confidentiality: This provides confidentiality for a single message or some selected data fields of a message in a single data block or on a connection.
![]() Traffic flow confidentiality: This provides confidentiality for the data derived from the traffic flow analysis.
Traffic flow confidentiality: This provides confidentiality for the data derived from the traffic flow analysis.
![]() Data integrity: This service provides assurance that data received by the receiver are exactly the same (with no modification, duplication, reordering, deletion or insertion) as sent by the authorized sender. For data integrity, the services defined by X.800 are as follows:
Data integrity: This service provides assurance that data received by the receiver are exactly the same (with no modification, duplication, reordering, deletion or insertion) as sent by the authorized sender. For data integrity, the services defined by X.800 are as follows:
![]() Connection integrity with recovery: This provides integrity to the entire user data or stream of messages on a connection. That is, it detects any modification, duplication, reordering, deletion, insertion or replay made to data or messages within an entire data or message sequence. If any change in data is detected, then this service tries to recover the original data.
Connection integrity with recovery: This provides integrity to the entire user data or stream of messages on a connection. That is, it detects any modification, duplication, reordering, deletion, insertion or replay made to data or messages within an entire data or message sequence. If any change in data is detected, then this service tries to recover the original data.
![]() Connection integrity without recovery: This service provides integrity to the entire user data or stream of messages on a connection. That is, it detects any change made to the messages or data, but does not try to recover the original data.
Connection integrity without recovery: This service provides integrity to the entire user data or stream of messages on a connection. That is, it detects any change made to the messages or data, but does not try to recover the original data.
![]() Selective-field connection integrity: This provides integrity to selected data fields within a block of user data or selected part of the message over a connection.
Selective-field connection integrity: This provides integrity to selected data fields within a block of user data or selected part of the message over a connection.
![]() Connectionless integrity: This provides integrity to a single data block or a single message in a connectionless communication and detects any modification made to data. It may also provide detection of replay attacks.
Connectionless integrity: This provides integrity to a single data block or a single message in a connectionless communication and detects any modification made to data. It may also provide detection of replay attacks.
![]() Selective-field connectionless integrity: This provides integrity of selected data fields within a block of user data in a connectionless communication and also detects any modification in these fields.
Selective-field connectionless integrity: This provides integrity of selected data fields within a block of user data in a connectionless communication and also detects any modification in these fields.
![]() Access control: This provides protection to data and resources from unauthorized access. This service defines the condition for accessing any data and controls the users who can access the resources.
Access control: This provides protection to data and resources from unauthorized access. This service defines the condition for accessing any data and controls the users who can access the resources.
6. Explain various security mechanisms. How are they related to security services?
Ans.: Security mechanisms have been defined by ITU-T (X.800). They are used to implement OSI security services and are incorporated into the suitable protocol layer. Some of the security mechanisms recommended by ITU-T (X.800) are shown in Figure 1.2.

Figure 1.2 Security Mechanisms
![]() Encipherment: This refers to the transformation of the message or data with the help of mathematical algorithms. The main aim of this mechanism is to provide confidentiality. The two techniques that are used for encipherment are cryptography and steganography.
Encipherment: This refers to the transformation of the message or data with the help of mathematical algorithms. The main aim of this mechanism is to provide confidentiality. The two techniques that are used for encipherment are cryptography and steganography.
![]() Data integrity: This refers to the method of ensuring the integrity of data. For this, the sender computes a check value by applying some process over the data being sent, and then appends this value to the data. On receiving the data, the receiver again computes the check value by applying the same process over the received data. If the newly computed check value is same as the received one, then it means that the integrity of data is preserved.
Data integrity: This refers to the method of ensuring the integrity of data. For this, the sender computes a check value by applying some process over the data being sent, and then appends this value to the data. On receiving the data, the receiver again computes the check value by applying the same process over the received data. If the newly computed check value is same as the received one, then it means that the integrity of data is preserved.
![]() Digital signature: This refers to the method of electronic signing of data by the sender and electronic verification of the signature by the receiver. It provides information about the author, date and time of the signature, so that the receiver can prove the sender's identity.
Digital signature: This refers to the method of electronic signing of data by the sender and electronic verification of the signature by the receiver. It provides information about the author, date and time of the signature, so that the receiver can prove the sender's identity.
![]() Authentication exchange: This refers to the exchange of some information between two communicating parties to prove their identity to each other.
Authentication exchange: This refers to the exchange of some information between two communicating parties to prove their identity to each other.
![]() Traffic padding: This refers to the insertion of extra bits into the stream of data traffic to prevent traffic analysis attempts by attackers.
Traffic padding: This refers to the insertion of extra bits into the stream of data traffic to prevent traffic analysis attempts by attackers.
![]() Routing control: This refers to the selection of a physically secured route for data transfer. It also allows changing of route if there is any possibility of eavesdropping on a certain route.
Routing control: This refers to the selection of a physically secured route for data transfer. It also allows changing of route if there is any possibility of eavesdropping on a certain route.
![]() Notarization: This refers to the selection of a trusted third party for ensuring secure communication between two communicating parties.
Notarization: This refers to the selection of a trusted third party for ensuring secure communication between two communicating parties.
![]() Access control: It refers to the methods used to ensure that a user has the right to access the data or resource.
Access control: It refers to the methods used to ensure that a user has the right to access the data or resource.
Security services and mechanisms share a close relationship with each other. One or more security mechanisms are used together to provide a security service. In addition, the same mechanism can also be used in many security services. Table 1.1 lists the security services along with the mechanisms that are used in these services.
| Security services | Security mechanisms |
|---|---|
| Authentication | Encipherment, digital signature and authentication exchange |
| Nonrepudiation | Data integrity, digital signature and notarization |
| Data confidentiality | Encipherment and routing control |
| Data integrity | Encipherment, data integrity, and digital signature |
| Access control | Access control mechanism |
7. Briefly explain the model for network security.
Ans.: With the phenomenal increase in the use of computer networks such as the Internet over the last few years, it has become essential to enhance the security of the network. To provide secured communication over the network, a general model of network security was created, which enhanced network security. This model consists of various components, which are as follows:
![]() Message: This is the information that is to be transmitted over the network.
Message: This is the information that is to be transmitted over the network.
![]() Principals: These refer to communication nodes, one which transmits the message (sender) and the other receives it (receiver).
Principals: These refer to communication nodes, one which transmits the message (sender) and the other receives it (receiver).
![]() Security-related transformation: This refers to the transformations made to the information to be sent, so that it is unreadable to an intruder. An example for such transformation includes either encryption of the message or inserting a message to verify the identity of the sender.
Security-related transformation: This refers to the transformations made to the information to be sent, so that it is unreadable to an intruder. An example for such transformation includes either encryption of the message or inserting a message to verify the identity of the sender.
![]() Secret information: This refers to the information that is shared between the two principals and used while applying the transformation at both the sender's and receiver's ends. For example, in case of encryption, the secret information can be a key used for encrypting and decrypting the message.
Secret information: This refers to the information that is shared between the two principals and used while applying the transformation at both the sender's and receiver's ends. For example, in case of encryption, the secret information can be a key used for encrypting and decrypting the message.
![]() Secure message: This refers to the message obtained after applying a transformation. It contains the secret code that helps the receiver retrieve the original message.
Secure message: This refers to the message obtained after applying a transformation. It contains the secret code that helps the receiver retrieve the original message.
![]() Logical information channel: This refers to the transmission route from a source to a destination, connected via a network. The route is established by the supportive use of communicating protocols by both parties.
Logical information channel: This refers to the transmission route from a source to a destination, connected via a network. The route is established by the supportive use of communicating protocols by both parties.
![]() Trusted third party: This is an entity that may either be responsible for transmitting the secret information to the two trusted parties while protecting it from an attacker, or may be responsible for settling disputes regarding the authenticity of a message transmission between two parties.
Trusted third party: This is an entity that may either be responsible for transmitting the secret information to the two trusted parties while protecting it from an attacker, or may be responsible for settling disputes regarding the authenticity of a message transmission between two parties.

Figure 1.3 Model of Network Security
According to this model, there are four basic tasks that are required for designing any security service. These tasks are:
![]() Designing an algorithm to perform security-related transformation. The algorithm should be designed in such a way that an intruder cannot defeat its purpose.
Designing an algorithm to perform security-related transformation. The algorithm should be designed in such a way that an intruder cannot defeat its purpose.
![]() Generating the secret information to be used with the algorithm.
Generating the secret information to be used with the algorithm.
![]() Developing some techniques for the sharing and distribution of the secret information.
Developing some techniques for the sharing and distribution of the secret information.
![]() Selecting a protocol to be used by the two parties. This protocol makes use of the secret information and security algorithm to achieve a specific security service.
Selecting a protocol to be used by the two parties. This protocol makes use of the secret information and security algorithm to achieve a specific security service.
This model secures the information in such a way that an intruder on the network cannot access it. However, within the organization, the information's security can still be threatened by unauthorized access, or by software attacks such as viruses and worms. To protect information from such threats, some security mechanisms should be implemented, as follows:
![]() Password-based login: This is used to deny access to all unauthorized users.
Password-based login: This is used to deny access to all unauthorized users.
![]() Screening login: This is used to detect and remove viruses, worms and other similar attacks.
Screening login: This is used to detect and remove viruses, worms and other similar attacks.
8. Categorize different types of network security attacks on the basis of security goals.
Ans.: As we know, for secured communication, some goals such as confidentiality, integrity and availability have been defined. However, these goals can be threatened by various security attacks. The categorization of attacks on the basis of security goals is shown in Figure 1.4.
![]() Attacks to integrity: The attacks that threaten the integrity of the data are masquerading, modification, repudiation and replay.
Attacks to integrity: The attacks that threaten the integrity of the data are masquerading, modification, repudiation and replay.
![]() Masquerading: Refer Question 4 in this chapter.
Masquerading: Refer Question 4 in this chapter.
![]() Modification: Refer Question 4 in this chapter.
Modification: Refer Question 4 in this chapter.
![]() Repudiation: Repudiation occurs when the message sender denies that the message was sent by him/her, or when the message receiver denies that the message was received by him/her.
Repudiation: Repudiation occurs when the message sender denies that the message was sent by him/her, or when the message receiver denies that the message was received by him/her.
![]() Replay: Refer Question 4 in this chapter.
Replay: Refer Question 4 in this chapter.
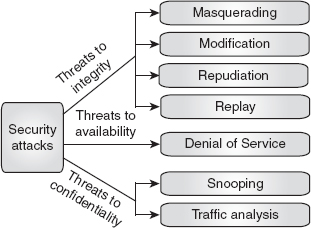
Figure 1.4 Categorization of Attacks in Relation to Security Goals
![]() Attacks to confidentiality: The attacks that threaten the confidentiality of data are snooping and traffic analysis.
Attacks to confidentiality: The attacks that threaten the confidentiality of data are snooping and traffic analysis.
![]() Snooping: Snooping refers to interception or unauthorized access of data. For example, an unauthorized entity may access a file containing confidential information during its transmission over a network and use that information for its benefits. Snooping can be prevented with the help of various encryption techniques, by making the data non-understandable to the unauthorized entity.
Snooping: Snooping refers to interception or unauthorized access of data. For example, an unauthorized entity may access a file containing confidential information during its transmission over a network and use that information for its benefits. Snooping can be prevented with the help of various encryption techniques, by making the data non-understandable to the unauthorized entity.
![]() Traffic analysis: Refer Question 4 in this chapter.
Traffic analysis: Refer Question 4 in this chapter.
![]() Attacks to availability: The attack that threatens availability is called denial of service (DoS).
Attacks to availability: The attack that threatens availability is called denial of service (DoS).
![]() Denial of service (DoS): Refer Question 4 in this chapter.
Denial of service (DoS): Refer Question 4 in this chapter.
Multiple-choice Questions
1. __________ ensures that a message was received by the receiver from the actual sender and not from an attacker.
(a) Authentication
(b) Authorization
(c) Integration
(d) None of these
2. Which of the following services is not an authentication service?
(a) Peer entity authentication
(b) Data origin authentication
(c) Data destination authentication
(d) None of these
3. Which of the following is a passive attack?
(a) Masquerade
(b) Replay
(c) Denial of service (DoS)
(d) Traffic analysis
4. Which of the following attacks is not a threat to the integrity of data?
(a) Masquerade
(b) Modification
(c) Repudiation
(d) Snooping
5. Which RFC document includes a definition of security service?
(a) RFC 2828
(b) RFC 2401
(c) RFC 3310
(d) RFC 6600
Answers
1. (a)
2. (c)
3. (d)
4. (d)
5. (a)
