CHAPTER 1
Healthcare Industry
This chapter covers Domain 1, “Healthcare Industry,” of the HCISPP certification. After you read and study this chapter, you should be able to:
• Understand the general organization of the United States healthcare system as well as select international healthcare delivery systems.
• Recognize the roles that make up the healthcare delivery system and how these interact with the information security professional.
• Understand the systems and taxonomies used to provide coding of healthcare information and to facilitate exchange of information in patient care delivery and payment.
• Be aware of the financial components of delivering and sustaining healthcare operations.
• Comprehend privacy and security aspects within health information management.
• Describe the information protection implications of third-party relationships in healthcare organizations.
• Appreciate the relationship between information privacy and security concepts with respect to foundational health data management approaches.
• Identify the standards and formats for data interoperability and exchange in clinical operations.
Over the past few decades, the complexity of a typical healthcare organization has increased. Beginning with the earliest hospitals and clinics, operations included direct patient care, hospitality, food service, janitorial, and engineering, to name a few ancillary functions. While those functions may be provided by third-party suppliers today, they are still imperative to caring for patients. Today, the complexity is increased as organizations form into integrated delivery systems where payers, providers, and other components are organized into one entity. This results in a very diverse workforce.
In many communities, the healthcare systems that reside in the area are primary employers or sources of income. This is important to know from a healthcare information protection perspective because the stakes are high and the organization must remain solvent. A data breach or cybersecurity event can erode trust or cause financial penalties that shift resources from patient care.
An extremely rich mixture of highly educated and talented physicians, nurses, administrators, and medical technicians provide direct and indirect patient care. Adding to the complexity, the numerous environments in which healthcare is delivered bring even more diversity to the categories of caregivers and support personnel that are necessary. Healthcare is delivered in hospitals, clinical offices, specialty diagnostic centers, and even the home. The challenges are equally complex for those of us who are charged with protecting the information privacy and security along with these medical professionals in the multitude of environments. One solution does not fit all scenarios to safeguard individually identifiable health information. This chapter will introduce and provide a brief overview of these categories of healthcare organization staff and their various qualifications.
Along with the complexity of the healthcare organizations, the reliance on third-party relationships has increased. This chapter presents an overview of the role and impact that third-party organizations play in healthcare. From suppliers of services to emerging technologies that augment employed staff and increase capabilities, the healthcare organization has many external relationships. A significant number of these are considered critical to operations. Relationships can be established by contracts, partnerships, or subsidiaries to the organization. It becomes interesting when the third party serves multiple industries, with healthcare being only one of them. Cloud service providers are a great example of a third party that has become integral to healthcare organizations. The growing pains for both sides have provided learning examples.
We will start with an introduction to the types of third-party relationships and related services on which healthcare organizations depend. Later, we will focus on the management processes available to address third-party–supplier risk to the healthcare organization.
Types of Organizations in the Healthcare Sector
From the origins of sanitariums and spas, which were more like warehouses for the sick and dying, our modern healthcare system has evolved rapidly into a very complex, highly technical, and essential component of communities and public health. Healthcare is less about a place than a process today. It can be delivered in hospitals, homes, and via mobile phones. Patients expect access to care in multiple settings and on-demand. Providers’ expectations and demands are increasingly decentralized, digital, and instantaneous. Those who work in the healthcare sector understand the current reality of what a healthcare organization can be, compared to what a healthcare organization was only two or three decades ago.
Let’s start with an overview of the major participants in the delivery of healthcare, which involves distinct groups: patients, providers, payers, and external stakeholders (such as suppliers, regulators, and the surrounding community). These groups play key roles that distinguish them from others even as the point of care may evolve.
Patients
No discussion about healthcare and healthcare information security and privacy starts without an acknowledgment of the patient. In the simplest terms, the patient is why we do what we do. A patient is a person who seeks assistance with matters of health (physical and mental), improvement of health status, or treatment of illness. The care patients seek can be preventative in nature, interventional, rehabilitative, or in recovery from a previous incident.
People can serve different roles on behalf of a patient. Proxies and advocates often assist the patient in navigating the provider and payer systems. These individuals may be family members, members of volunteer organizations, or commercial business entities. The key point is that these entities act primarily on behalf of the patient because the patient care system is complex, or the individual patient needs assistance to participate in their care. The central transaction in healthcare is the conversation between provider and patient. We protect information to ensure that the interchange is complete, protected, and maintained for all the different, legitimate uses of the information.
A patient can have an inpatient or an outpatient status. An inpatient is administratively admitted to the healthcare organization for 24 hours or more. In these cases, a bed is traditionally the unit of measure for occupancy rates. For periods of less than 24 hours, the patient is considered in outpatient status. Outpatient status is also known as ambulatory. In some cases, a patient may be admitted in an observation status, which can last up to 48 hours without formal admission as an inpatient. Many patients enter the healthcare system through the emergency department. Typically, the admission status of these patients is determined once they are stabilized. For example, a patient who visits an emergency room is considered an outpatient status if the patient is released within 24 hours.
Outpatient care is provided in numerous types of healthcare settings, including hospitals, medical clinics, associated facilities, and even their own home environments. Increasingly, many surgical and treatment procedures are safe and possible outside of the traditional hospital setting. Advances in technology have reduced the need for inpatient admissions. This evolution has fostered changes in where care can be provided. Today you can find urgent care centers in shopping centers, and patients can undergo some surgical procedures outside a hospital facility. This evolution has been fostered by changes in favorable regulatory guidance and reimbursement rules.
The patient can also be viewed through the lens of the data that constitutes a healthcare facility’s identity. This is important, because a protecting a patient’s identifiable information is significantly different from information protection and other security and privacy concerns applicable and important in other industries. For example, a patient can be identified by his or her name, date of birth, Social Security number, or home address. These identifiers are similar across other data collection activities of personally identifiable information (PII). However, patients can also have unique information referencing genetic code, billing codes, treatment codes, and images, to name just a few data elements. If PII is disclosed in an unauthorized manner or to an unauthorized viewer, the disclosure violates patient privacy and can also be used to fraudulently receive medical services or alter a medical record. Such disclosure can be a problem in terms of identity theft, financial impact to a patient and a provider organization, and patient safety.
Compounding the issue is that, unlike PII, most protected health information (PHI) is difficult to change (if not impossible) if it has been corrupted or misused in some way. For example, a bank account or even a Social Security number can be replaced, although the unauthorized disclosure of this information is a problem. The disclosure of a patient’s medical history, however, is far more difficult to remedy. If the information is spoofed by someone in order to fraudulently receive healthcare services, the actual patient will have difficulty fixing the problem. In some cases, the imposter receives care, and that care is integrated into the victim’s medical record. The addition of this information could result in patient safety and care issues (such as blood type mismatches, drug interactions, and so on). If certain diagnoses such as mental health issues or highly sensitive diseases are disclosed, that element of privacy and confidentiality cannot be regained or remedied.
Providers
“Provider” is a broad term that may refer to a single healthcare provider, such as a physician, nurse, or therapist who helps in identifying, preventing, or treating an illness or injury. The term can also describe an organization that employs, contracts, or organizes people who deliver services to patients. Various types of organizations deliver healthcare as providers, such as hospitals, specialized clinics, and even home healthcare agencies. As mobile applications and cloud-based technologies become more advanced, virtual healthcare provider organizations are emerging. In these virtual organizations, caregivers are linked with patients without regard to geographic location. The technology platform is the healthcare organization. By 2022, the virtual healthcare market in the United States is anticipated to earn revenues of $3.5 billion.1
When multiple types of provider organizations, both inpatient and outpatient services, are organized into a coordinated system of clinics and hospitals, they are called integrated delivery systems. These systems can be organized into a single corporate structure, or the systems can provide care, services, or supplies under terms of contracts and other legally binding agreements. The systems are established to increase efficiency and reduce redundancy in providing quality healthcare.
At this point, you know the central transaction in healthcare. The interaction between provider and patient is foundational to the entire system. Understanding the fundamental importance of patient-provider communications can help guide information security professionals. Our role is to look for solutions that improve the communications while maintaining security. At the same time, we must avoid actions that negatively impact the physician-patient interactions.
If you walk into any provider organization, you will notice a wide variety of occupations involved. There are people performing roles ranging from janitorial services to open-heart surgery. There are teams cleaning rooms and others delivering babies. People perform clinical, administrative, or support services to care for patients. The variety of occupations and different levels of education and competency that exist in healthcare differentiates the healthcare industry from many other industries. The US government identifies almost 50 different categories of healthcare practitioners, technologists, and healthcare support occupations.2 This is in addition to the numerous business and information technology types of professionals that constitute the healthcare organization workforce that must work together efficiently and effectively. From the lowest skilled, entry-level employee to the most senior executive or seasoned physician, the entire organization works in an interconnected way to provide patient care. The following sections cover several of the major categories of healthcare organization occupations you should know about.
Nurses
Nursing is the largest occupational category in any healthcare provider organization. Nursing staff serve a variety of roles and responsibilities, and more than half of US nurses work in provider organizations. In the United States, almost 3.5 million nursing professionals are in the workforce today, accounting for nearly three of every five healthcare professional and technical jobs in the country.3 Nurses are a professional category of caregiver, with many countries requiring specific education and licensing requirements. Although there are millions of nurses in the workforce, the demand for nursing remains unmet. Presently, there may be as many as 200,000 unfilled nursing jobs in the United States, primarily because of the lack of nursing educators and education resources. In 2018, the American Association of Colleges of Nursing reported that US nursing schools turned away more than 75,000 qualified applicants from baccalaureate and graduate nursing programs because of an insufficient number of faculty, clinical sites, classroom space, and clinical preceptors, as well as budget constraints.4 General categories of nursing include nurses’ aides, licensed practical nurses, registered nurses, and nurse practitioners.
Nurses are essential and influential in the delivery of healthcare. They have impressive levels of education, training, and certification and are indispensable in every aspect of clinical workflow. Beyond direct patient care, nurses are also invaluable when serving in administrative and executive functions of the healthcare business. In the healthcare industry, nurses are prominent in the exam room as well as in the board room. Nursing professionals are highly sought after, and many nurses serve in areas outside of direct patient care. Nurses working in health education roles, in privacy and security areas, and in data analytics are not uncommon.
Nurses’ Aides Nurses’ aides provide a great deal of patient care in a variety of healthcare settings from the physician’s office, to the hospital, to long-term care environments. As an occupation that is related to hospital orderlies and attendants, nurses’ aides perform services that include moving, repositioning, and lifting patients. They may also provide numerous patient services related to personal care, feeding, bathing, comforting patients, and keeping patients at ease. The education level of most nurses’ aides is post-high school (a diploma or certificate). It is not uncommon for healthcare organizations to require at least a competency exam that the nurses’ aide also needs to pass.
Registered Nurses and Certified Registered Nurses The care that registered nurses (RNs) provide is more directly involved in coordinating with physicians and other healthcare providers. Whether in an emergency room (ER) or an intensive care unit (ICU), RNs are working at the front lines of patient care. RNs also have a large role in educating patients and the public about health status, post-discharge instructions, and a variety of other concerns related to healthcare. Of course, RNs work in the same environments as all other nurses, but because of their additional education, training, and credentialing, RNs can work independently in some nontraditional healthcare environments such as correctional facilities, schools, and summer camps. Most commonly, RNs receive a bachelor’s degree in nursing. It is possible, however, to obtain RN licensure with an associate degree in nursing or a diploma from select nursing programs. All RNs must obtain a license by passing a national RN licensing exam.
An advanced registered nursing career track is the certified registered nurse anesthetist (CRNA). These nurses can provide anesthesia to patients for any surgery or procedure that requires it. Whereas this responsibility was previously reserved for physicians, CRNAs enable small-market and rural hospitals to control costs by reducing staffing expense while maintaining the standard of care. To become a CRNA, the process includes obtaining a bachelor’s degree in nursing or an equivalent, often obtaining a master of science degree in nursing (MSN), and being a licensed RN. Additionally, a CRNA must have clinical experience in an acute care setting. They need to demonstrate one year of experience in an area such as the ICU as opposed to long-term care or rehabilitation units. In addition to all this, they also must complete an accredited nurse anesthesia educational program. Finally, they are required to pass a national certification examination.
A second example of an advanced registered nurse specialty is the certified nurse midwife (CNM). This nurse usually has completed a bachelor’s degree and an MSN program. The board certification is in the profession of midwifery. CNMs specialize in providing care such as birthing services for women who are not experiencing high-risk pregnancies.
Nurse Practitioners Within the nursing profession, the role of nurse practitioner (NP) has emerged to extend and expand the capabilities of caregivers due to workforce shortages and advances in medicine. RNs may undergo additional training to be able to diagnose medical conditions, order treatment, prescribe drugs, and make referrals much as a physician would. To become an NP, one must first be an RN. Then, after additional, advanced classroom and clinical education, the RN is credentialed as an NP. The types of practices in which NPs work are almost limitless. They serve in primary care settings such as pediatrics, family practice, and geriatrics and in specialty care areas such as OB/GYN, oncology, dermatology, and pain management.
To become an NP, the RN must obtain an MSN or the doctor of nursing practice (DNP) degree. Then the candidate must pass a national board certification exam. The NP will take the exam based on the specific clinical focus area of their educational program—in other words, if the program concentrated on geriatrics, the certification exam would do the same. Once these hurdles are cleared, the board-certified NP can apply for additional credentials, such as a Drug Enforcement Agency (DEA) registration number to be able to prescribe controlled substances in addition to the medications the NP licensing allows.
Licensed Practical/Vocational Nurses A licensed practical nurse (LPN) or a licensed vocational nurse (LVN) works under the supervision of an RN. The choice of occupational title depends on the US state in which the nurse is employed. The duties and qualifications are the same for LPN and LVN. These nurses must complete a year-long (typically) certified educational program. Often these programs are affiliated with a teaching hospital that provides some hands-on experience for the students. After they complete the program, students must pass an additional licensing exam. LPNs and LVNs work in every area of healthcare provision—in hospitals, of course, but they also may provide care in skilled nursing facilities, rehabilitation centers, or even a patient’s home. Through home healthcare, the continuum of care extends from the hospital back into the patient’s normal living environment, which has a demonstrated positive impact on outcomes.
Physicians
Physicians have been providing healthcare since as far back as time has been recorded. Hippocrates, in around 350 BC, is considered the “father of modern medicine.”5 In contrast, modern nursing began in the nineteenth century—although the services of nursing in patient care have certainly taken place as long as people have been sick and injured.
From the very beginning to today, the central relationship in healthcare has been between the doctor and the patient. A physician’s main role is to diagnose and treat injuries and illnesses for their patients. Surgeons, who are a specialized type of physician, treat patients by operating to treat injuries, diseases, and deformities. Almost all physicians obtain a bachelor’s degree and then complete four more years in an accredited medical school. There has always been a measure of importance placed on applied performance under the guidance of a current physician. So, after medical school, on-the-job training continues as an intern for a year. Then the student must complete a residency, usually focusing on a specialty or area of increased proficiency, such as cardiology or internal medicine.
Like a nurse, a doctor must obtain a license to practice and hold the credential of doctor of medicine (MD) or doctor of osteopathic medicine (DO). It is also common for MDs and DOs to take additional exams for board certification. There are board certifications (sometimes more than one) for all the various specialties. After training and licensing is completed, physicians are permitted to prescribe medications and order, perform, and interpret diagnostic tests independently. In addition, each physician is also required to be credentialed specifically to practice in a particular hospital or healthcare organization. This is an internal function of the healthcare organization. Organization personnel verify the background and qualifications of the physician and grant the physician privileges to practice medicine within the organization.
As mentioned, a physician can be a general practitioner with responsibilities in family medicine, internal medicine, or other primary care types of areas. Otherwise, based on additional, focused training and experience, physicians and surgeons (called specialists) can concentrate on an individual disease or condition, or on a specific physiologic system. To help illustrate the number and variety of these specialties, Table 1-1 contains some of the most common specialties with a brief description. The specializations listed in Table 1-1 are not comprehensive. There is variation internationally as countries may differ in how they subdivide and recognize specialty practices. The common factor for determining specialization, however, is according to the defined group of patients, diseases, skills, or philosophy on which the physician focuses.

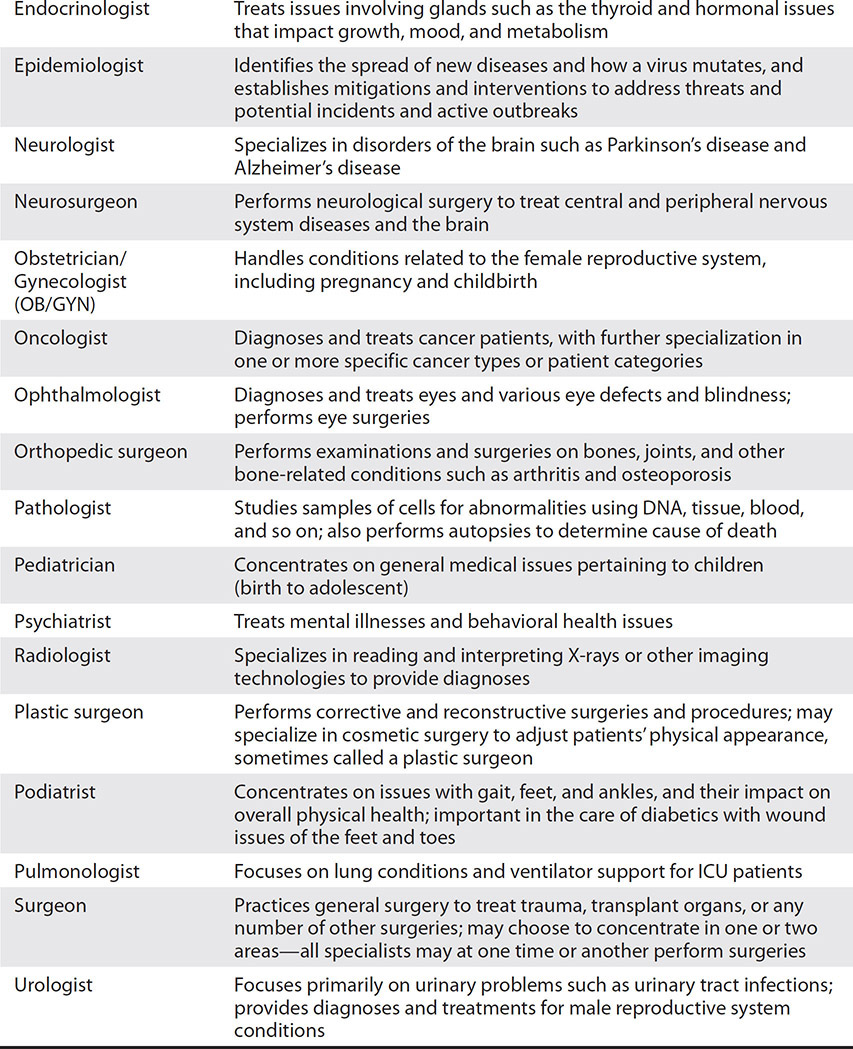
Table 1-1 List of Specialist Physicians with Descriptions
Physician Assistants
The physician assistant (PA) is another provider role that has evolved separately by broadening the nursing role. Collectively, the NP, CRNA, and PA are often called “physician extenders” because they have absorbed traditional roles and responsibilities reserved for physicians to help increase the availability of advanced care. Physician extenders have also proven invaluable by often improving quality (certainly not lessening it), reducing costs, and increasing access. The PA is recognized as another general category of healthcare professional or staff who also has a license to practice medicine under the guidance of a physician. This recognition is not universal across international health systems. Primarily a US healthcare physician extender, the PA may not be recognized in other countries.
Most often, a candidate for PA already has a bachelor’s degree, but some programs confer one as part of completing the PA curriculum. In any case, PA programs typically require approximately two to three years of schoolwork with clinical rotations in all areas of PA practice, such as internal medicine, family practice, emergency medicine, and so on. In some cases, a graduating PA decides to specialize in a specific clinical area and obtains additional training and experience. This process is similar to physicians gaining experience through specialty rotations but involves a much shorter length of time. PAs provide the same patient care functions as a physician, but they must work under the direction and oversight of a physician. One difference is in performing surgery: a PA can aid a physician-surgeon but cannot conduct the surgery independently. As with all nurses and physicians, there is a licensing requirement for PAs.
Medical Technicians
When you hear someone referred to as a medical technician, it is similarly overarching, like doctor or nurse. There are numerous subcategories of medical technicians that fully describe the expertise and technical aptitude of any particular area. First, the general category of medical technician describes the kind of work done in clinical laboratories performing tests and exams. A medical technician has practical knowledge and ability in a particular clinical area. They also must be able to understand medical data produced by their specific equipment and how it relates to the patient. They are the first line of interpreters of results. While they do not make diagnoses, they can certainly reduce error and rework when they recognize inaccuracies in data, such as in a blood bank or microbiology laboratory. Another type of medical technician operates medical devices in support of performing procedures in the specific clinical practice. This would include diagnostic imaging, cardiac catheterization, and hemodialysis. The reports and findings of tests and examinations made by all of these different types of medical technicians are used by physicians to diagnose and treat patients. It is important to note that even with sophisticated testing technologies and highly skilled medical technicians, the actual interpretations and diagnoses remain the role of the physician.
Biomedical Technicians and Clinical Engineers Biomedical technicians and clinical engineers are the personnel who maintain (and operate) medical devices. One of the key differences between these types of medical technicians and the technicians discussed in the preceding section is that biomedical technicians and clinical engineers typically do not require extensive training on human anatomy, physiology, and clinical technique. With respect to education, clinical engineers have an educational requirement that exceeds that for a biomedical technician, including a four-year degree at least. A biomedical technician, much like other medical technicians, may have a two-year degree or a certificate of training from a healthcare vocational training program. In any case, both clinical engineers and biomedical technicians work in conjunction with other medical technicians to operate and maintain all of the various medical devices and technologies safely in the healthcare organization.
Other Provider Types with Specific Access
Based on how they provide clinical services to the patient, several other healthcare providers and support personnel handle protected health information. All the following providers require varying levels of licensure and certification requirements as well. Some jurisdictions internationally still require physicians to serve in these roles.
• Emergency medical technicians EMTs require special training to provide first response to emergency situations and handle traumatic injuries and medical care at accident scenes and other locations.
• Social workers This profession concentrates on patients’ quality of life and subjective wellbeing and administer to individuals, groups, and communities. Areas of practice include research, counseling, crisis intervention, and teaching.
• Psychologists A medical professional, they provide patient care with respect to behavior and mental processes and counselling services, and they may conduct research within academic settings.
• Psychiatrists An MD that focuses on examining and treating disorders of the mind or mental health. They can prescribe medication. Their evaluation of the patient consists of a consideration of symptoms and complaints to determine if the origin is physical illness or injury, mental disorders, or a combination.
• Pharmacists These professionals are responsible for dispensing medications and ensuring their proper and safe use. They are an integral part of the healthcare team in that they often provide meaningful education and counseling for patients who are receiving medication. A doctor of pharmacy (PharmD) degree from an accredited pharmacy program is required. This is followed by successfully passing licensure exams.
Administration
No healthcare organization could succeed without another significant part of the healthcare workforce—the administration. There are many examples of providers who perform administrative roles in the organization, such as chief medical officer physicians or department managers who started their careers as medical technologists. However, many administrative positions are held by people not trained as providers but with education and experience focused on clerical, managerial, and executive competencies.
Administration describes all the various people that administratively support the provision of healthcare. At every level of the healthcare organization, from the chief executive officer to the ward clerk, administrative individuals provide appropriate levels of management and leadership. At the most senior level, administration refers to the management of internal and external forces to achieve specific goals. One of the key responsibilities for senior administrators is to recruit and retain quality physicians, to ensure appropriate staffing levels, and to manage performance. Below this level, the administration strives to achieve their objectives and allocate resources appropriately. Much like all the other healthcare professions, administrators can have a general focus across many areas, such as a chief operating officer or a physician’s office manager. On the other hand, many administrators specialize in a given area, such as information technology or finance.
In terms of education and training, the path to administrative positions mirrors that of other healthcare professions and categories. For more senior-level positions, at least a bachelor’s degree is needed. In many cases, especially in a specialty area such as information technology or finance, a graduate degree is often preferred. It is also preferred that administrators in these positions have previous experience working in healthcare organizations. For other administrative positions, a combination of a high school diploma and on-the-job training is required. Board certification is available to administrators of all types, from general administrators, to information technology, to finance. The certification of administration personnel provides a common framework for peer-to-peer relationships with healthcare provider colleagues.
Environmental Services
Without janitorial or housekeeping services, a healthcare organization could not open its doors. The regulatory and patient safety issues that healthcare organizations face make environmental concerns very important, especially because these types of services, including maintenance, alterations, and construction, happen in areas where patients are or will be.
Environmental service personnel also provide laundry operations and linen distribution. Coupled with housekeeping services, these personnel integrate in the overall management of beds within the organization. How quickly a room or a bed can be made ready after a patient is discharged can mean significant added revenue, but if this is done incorrectly, patient safety, satisfaction, and outcomes can suffer because rooms are transitioned quickly, but they lack cleanliness, for example. Infection control plays a large role and can be a huge revenue drain on healthcare organizations considering the number of hospital-acquired infections and readmissions that can result from a lack of proper cleanliness.
Healthcare Clearinghouse
A medical claims clearinghouse is a third-party system that interprets or “scrubs” claim data between US provider systems and private insurance payers. According to the US Department of Health and Human Services, a healthcare clearinghouse is a “public or private entity, including a billing service, repricing company, or community health information system, which processes non-standard data or transactions received from one entity into standard transactions or data elements, or vice versa.”6 The electronic claims submission clearinghouse intermediates between provider financial charges and insurers’ denial or acceptance of the claims for payment. Providers can submit bills directly to health insurers, but many choose to deal with clearinghouses in the middle to increase efficiency. Healthcare clearinghouses are subject to HIPAA and have an important role in addressing information privacy and security during electronic data interchanges.
Healthcare Organizational Behavior
Now that we have discussed the healthcare players and their roles, let’s briefly look at how they interact (and why that matters to us). In short, you will want to acknowledge the power and politics in healthcare organizations. As noted in the specific professions, these roles have long histories, and their relationships and interactions have been influenced by political factors as well as clinical practices. Before the mid-twentieth century, the predominant healthcare roles were doctors and nurses. The relationship between the two professions is so intense that a Wisconsin physician, Leonard Stein, famously coined the term “Doctor-Nurse Game” in 1967 to help explain and understand the relationship. The major (and not complimentary) objectives of the game demonstrate the underlying communication problems between doctors, nurses, and, by extension, all allied health professions.7 Some debate that the game has ended as nursing professions have advanced in status and power within healthcare organizations, but others are not ready to declare that victory.8
The evolution of the healthcare workforce has led to complex organizational behavior dynamics. The need for a variety of allied healthcare professions, such as specialized medical technicians and myriad administrative personnel, came from the reliance on and success of clinical and information technology. Healthcare organizations must now more than ever work together.
The connection between organizational behavior and understanding information protection in healthcare is about knowing your customer. The healthcare organization is unlike any other customer or end user a security professional will serve. The interaction of nurses, physicians, administration, and medical technicians consists of multiple perspectives and priorities. Healthcare security professionals must take it all into account with respect to protecting information. You cannot apply information privacy and security in healthcare exactly as it is applied in other critical infrastructure organizations, such as telecommunications or industrial control system industries. To understand why is to master the power and politics at play.
We’ve established that healthcare starts with the patient, and the central relationship in healthcare is the doctor–patient relationship. Anything that interferes with that relationship must be clinically reasonable (and legally defensible). A successful healthcare information security and privacy practitioner must account for this. For instance, installing the latest vulnerability update for an operating system considered a critical fix is a top priority in most organizations with information systems. The edict to stop work and push out the patch remotely from information technology servers may well be the industry best practice. But in healthcare, that edict may interfere with patient care and can cause patient safety issues. Remember that medical devices are increasingly networked and will require the same vulnerability updates. Imagine what would happen if an automatic push across the organization caused a cardiac catheterization lab system to reboot in the middle of a patient procedure; patient safety could be at risk. (This is one over-simplified example.)
Safely implementing health information technology and security is already identified as a potential issue in healthcare-adverse events (those related to patient safety).9 The key concept is that a healthcare organization chart, a seniority list, or a corner office will not always illustrate the power within the healthcare organization. When developing and implementing an information protection strategy, you must consider and include input from physicians (who may or may not be employees of the organization), nurses, and anyone else who is providing direct patient care.
Health Insurance
Whether healthcare is funded by a public source, such as the government, or reimbursed by private entities, such as health insurers, someone has to pay the bill for services rendered. Both in the United States and internationally, it is uncommon for an individual to “self-pay,” so most payers are commonly described as third parties. In sum, a payer is almost always someone other than the patient who finances or reimburses the cost of healthcare.
Healthcare Across the Globe
Healthcare delivery has patients, providers, and payers in every model in countries around the world. To highlight this, we present several major healthcare systems. Our starting point is the US healthcare system. You will observe a contrast with the US private and public payers with the rest of the global healthcare delivery systems. As a security professional, you are not expected to have a deep understanding of international healthcare systems; a high-level understanding of major components is enough. You may begin to put privacy and security issues into context based on knowing who pays for healthcare and how providers are regulated. There is intentionally no evaluation of one delivery system over another in this book; each has its own merits and opportunities for improvement.
United States
The US healthcare system consists of both private payers and public insurers. What sets the United States apart from the rest of the world is the extent to which healthcare costs are met by private payers, or health insurance companies. Health insurance is a way for individuals to be protected against large medical expenses by joining a larger population where the risk of medical expenses is estimated for the entire group. The insurance company charges a monthly premium applicable to the entire target population. In this way, the costs of medical care are spread out across the group. Under the heading of “private payer,” several considerations are described in the following sections.
Indemnity Insurance
This model for insurance payment is based on fee-for-service. A patient receives healthcare services, pays for it at the point of care, and then submits a claim to the insurance company for reimbursement. In this scenario, the patient has the maximum freedom of choice in physicians and other services. Of course, this scenario also results in the highest cost. Indemnity plans usually have an out-of-pocket maximum. Once the beneficiary reaches their annual limit for medical expenses, the insurer pays the entire bill. There is no patient payment for services unless the provider charges more than the usual and customary fee. The patient will be responsible for charges above that amount.
Employer-Based Insurance
The reliance on health insurance in the United States is a relatively recent development. The growth can be directly traced to employers offering coverage as an employment benefit, in addition to salary and other enticements. This may be related to federal government’s regulatory pressures to freeze wages during World War II. Employer-based healthcare became increasingly common as a result. Employer-based coverage comes in two types: fully insured plans and self-funded plans. Each version has legal and tax incentives for both employers and employees. The US Census Bureau reported that, in 2015, about 67 percent of the population was covered by private health insurance, and about 56 percent of that group was covered by employer-based health insurance.10 Figure 1-1 depicts the narrative in the next few paragraphs of US healthcare expenditures by payer type: self-pay, private insurance, Medicare and Medicaid, and other (third-party payers such as non-custodial parental support, state workers compensation, court settlements from a liability insurer, and so on).

Figure 1-1 Distribution of US healthcare expenditures in 2018, by payer (Source: Office of the Actuary in the Centers for Medicare and Medicaid Services)
Fully Insured Health Plans In this type of fee-for-service plan, the employer purchases government-licensed insurance that is regulated at the state level depending on the states in which the insurer operates. The federal government has jurisdiction as well. The insurance company collects premiums and bears the financial risk if what the company pays out goes beyond the collected premiums.
There are three primary types of government-licensed health insurance organizations:
• Commercial health insurers In some cases, these companies, called indemnity insurers, may be owned by stockholders or policyholders (as a mutual insurance company). Aetna is an example of a stock company version of a commercial health insurer.
• Blue Cross and Blue Shield plans (BCBS) About 90 million people are covered by a BCBS plan. Traditionally, they were not-for-profit plans, and many still are today. Some BCBS have organized to be more like commercial, for-profit entities under special state laws by state hospital (Blue Cross) and state medical (Blue Shield) associations. Most plans offer managed care plans, such as health maintenance organization (HMO) and preferred provider organization (PPO) plans, as well as traditional insurance plans.
• Health maintenance organizations HMOs cover approximately 70 million people today. HMOs usually are licensed under special state laws that recognize that HMOs tightly integrate health insurance with the provision of healthcare. HMOs are both provider and payer. Examples include Kaiser Permanente and Harvard Pilgrim.
Self-Funded Employee Health Benefit Plans In these plans, the employer has the responsibility of paying directly for healthcare services. Funds are reserved to pay claims, and the employer contracts with one or more third parties to administer the insurance benefits. With a self-funded plan, the employer bears most of the financial risk. The employer can contract with an entity called a third-party administrator that specializes in this business. The other options are to contract with health insurers or HMOs to manage the benefits for the employer.
Managed Care
As a mechanism to control cost, improve quality, and increase access, managed care has evolved from an unproven concept almost 50 years ago to a major component of healthcare delivery and resourcing today. The key feature of managed care is in the integration of healthcare provision and payment within one organization. Virtually all private health coverage now involves some aspect of managed care. The managed care organization develops financial incentives to drive patient behavior and provider treatment decisions. At the same time, the managed care organizations rely on objective data analysis to develop treatment protocols that are shared to improve provider practices. Although also intended to control costs and increase efficiency, managed care organizations rely on controlling access to limit waste. Part of this process is a requirement for patients and referring providers to obtain prior authorizations for certain services. Some argue the gatekeeping function of referral management and prior authorizations can be an intrusion into the patient–provider relationship.
The following are the four main types of managed-care options:
• Health maintenance organization Patients are enrolled by paying the HMO a monthly or annual fee. They are then eligible to receive care from providers that have aligned with the HMO. The patient typically has a low or no deductible, but instead a small copayment for each service.
• Preferred provider organization This is a fee-for-service health plan with several providers that have aligned with the PPO. If the patient chooses a participating provider, the cost of medical care is discounted to the enrollee. If not, the health plan pays a lower amount for the provider’s service and the patient pays the rest. The patient may incur higher deductibles and coinsurance payments with a PPO. The result is more choice for the patient, yet at a higher cost.
• Point-of-service (POS) This type of plan combines the most attractive elements of both HMOs and PPOs. In exchange for a deductible and higher coinsurance payment on a one-time basis, an HMO enrollee can choose to use a service that is outside the HMO plan. This is in contrast to a strict HMO policy of not reimbursing care received out of network (under the HMO-only model).
• High-deductible health plan with savings option (HDHP/SO) This type of plan usually takes the form of a health savings account (HSA). For a relatively low premium, an enrollee gets catastrophic insurance coverage. For all healthcare received up to catastrophic care, the enrollee must pay a high deductible. To offset this, enrollees are able to save wages before tax in a special type of account to be used to pay any deductibles.
The government is the primary payer in most developed countries and is integral to the overall provision of healthcare. In contrast to other countries, government spending for healthcare in the United States is designed to address populations not served by private insurance. These government-sponsored plans are also typically structured in a managed-care design:
• Medicaid Each US state allocates the money it receives from the federal government to provide medical assistance primarily to the elderly, poor, and disabled. For the most part, recipients are pregnant women, children and babies, people with disabilities, and, in some cases, the elderly poor.
• Medicare Medicare provides insurance coverage for individuals age 65 and older or those who are younger than 65 but have long-term disabilities. It is funded and administered by the federal government. There is no qualification related to income level, only age or disability status.
• Department of Defense Military Health System (MHS) The federal government provides funding for health benefits for active-duty service members and retired service members, as well as their dependents, through the MHS. This network has aspects of direct care (military hospitals) but also purchases healthcare from the commercial sector through a managed-care network called TRICARE.
• Veterans Health Administration (VHA) Veterans of US military service are eligible for care through the federal VHA program, which operates a network of hospitals and treatment centers that provide care specifically to this population.
• Indian Health Service (IHS) Eligible Native Americans may receive care through the IHS within IHS facilities. They may also receive care at non-IHS facilities with payment provided by the federal government.
Depending on what services are covered and the level of reimbursement, many Americans pay premiums for more than one health insurance plan. Often plans overlap. For this reason, healthcare financing in the United States is a complex assortment of programs that can be integrated. A significant concern with the financing system is that it leaves still millions of Americans with too little or no health insurance coverage.
To address the uninsured and underinsured in America, the Patient Protection and Affordable Care Act (PPACA) was enacted in 2010. The law is often abbreviated to the Affordable Care Act (ACA) or nicknamed “Obamacare.” The ACA was the most significant reform of US healthcare since Medicare and Medicaid were started in 1965.11 The exact numbers are hard to obtain, but sources indicate that more than 20 million people have benefitted from the regulatory reform, about half of the estimated population without insurance or enough coverage. The ACA continues to be a hotly debated political topic, even though it was passed into law. Several unsuccessful attempts were made to challenge the act in US courts. Another source of concern is that some studies showed that premiums paid by individuals increased dramatically post-implementation. Figure 1-2 offers a state-by-state view of the changes in how much an individual must pay annually. The sweeping nature of the ACA will continue to drive ongoing changes in the structure and financial operation of healthcare organizations in the United States.

Figure 1-2 Premium growth after ACA (2015–2016) (Source: Business Insider)12
Internationally, a single-payer system financed by government (public) funds is most common. However, private insurance or self-pay options do exist for some countries. Depending on the country or healthcare system, providers may be able to choose to accept both private and public funds. In some systems, the two types of financing sources operate separately. A select few of those systems are presented in the following sections. Common among these, the government (with few exceptions) collects all healthcare fees and pays all healthcare costs. In short, providers in these countries bill one entity (not the patient) for their services. It is important to understand the financing systems for healthcare delivery on an international level compared as a percentage of each country’s gross domestic product (GDP). Figure 1-3 is authored by the Organisation for Economic Cooperation and Development (OECD) and demonstrates overall spending by government and private sources on healthcare.
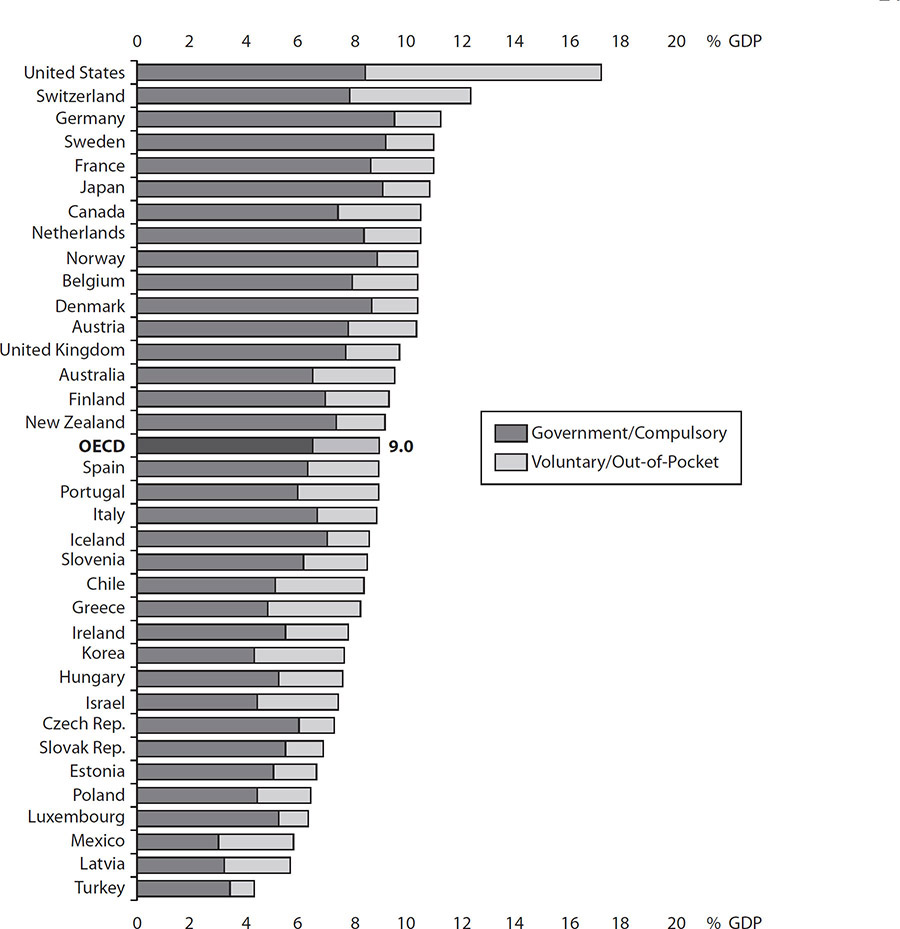
Figure 1-3 Health spending in OECD countries, 2016 (Source: Health at a Glance 2017, OECD Indicators)
Canada
Canada’s healthcare system is an example of a single-payer system in which the government offers universal coverage. The system is funded through taxes collected. The physicians delivering the care, however, are not government employees and provide services under a fee-for-service model. Canada has a publicly funded Medicare system, with most services provided by the private sector. In this single-payer system, basic services are provided by private doctors (since 2002 private doctors have been allowed to incorporate), who submit claims to the government (payer) for services rendered. The entire fee is paid by the government at the same rate. Each province may opt out of the program, though none currently does.
To be compliant with government mandates, all health plans in Canada must be
• Available to all residents of Canada
• Comprehensive in coverage
• Accessible without financial and other barriers
• Portable within the country and while traveling
• Publicly administered
United Kingdom
The UK’s National Health Service (NHS) is a government agency that is organized and resourced to provide universal health coverage. NHS is publicly funded via taxes and is founded on the belief that all citizens have an entitlement to healthcare. Healthcare services include basic services, primary care, specialty care, and inpatient care, along with radiology and laboratory services. That said, private insurance also exists because some types of services are not covered by NHS—usually elective conditions. Approximately seven million people, or 12 percent of the population, are covered by private plans.
In terms of out-of-pocket costs, there are only a few cost-sharing arrangements for publicly covered services. Patients may pay a prescription drug copayment per prescription, while all drugs prescribed for inpatient care in NHS hospitals are free to the patient. NHS dentistry services are also subject to copayments.
European Union
The European Union (EU) does not have any administrative or authoritative role in healthcare. Although each health system is run at an individual member-nation level, the systems are primarily publicly funded through taxation. For the most part, healthcare in the EU is considered universal healthcare. This includes larger systems in Germany, France, Italy, and Spain. There is private funding for healthcare, which is a personal contribution toward meeting anything not funded by taxpayer contribution. This can be totally private funds paid either out-of-pocket or by personal- or employer-funded insurance. Membership in the EU enables citizens to carry a European health insurance card and provides reciprocal emergency healthcare funding for citizens who are visiting other member nations. In fact, this benefit extends to several other European nations that are not currently in the European Union.
Japan
There is measurably more government control of healthcare in Japan, which also has a universal health coverage model. At a national level, in this model, the pricing of services is set by the government, which also subsidizes local governments, third-party payers, and providers for the cost of providing healthcare (which does not actually equal what the government sets as a fee). The government does this to help these entities implement national-level policies. Japan has 47 prefectures (regions) and 1742 municipalities that operate the nation’s healthcare system. However, all of these local healthcare entities adhere to detailed regulations set and enforced at a national level. Although funding is provided by the government, there are gaps in coverage; for instance, some hospitalization costs are not fully covered. Therefore, supplementary private health insurance is held by most of the adult population.
Stakeholders
The healthcare information protection practitioner may require an understanding of the broad impacts of negative events, such as a cybersecurity attack, that can affect entities beyond the healthcare organization. These entities, or stakeholders, have an interest in or an impact on the healthcare organization, and they are also affected by events that occur within the healthcare organization. Stakeholders can be many and diverse, from individuals to entire corporations.
Healthcare organizations are critical to the infrastructure of communities. In many communities, the local healthcare organization is probably one of the central institutions in the area and is likely a major employer as well. It is also likely that it is one of the most prevalent buyers and users of services, supplies, and products that are either directly related to patient care or indirectly related to supporting patient care operations.
Local government is also considered a stakeholder, because it has a direct impact on operations in the healthcare organization and is also responsive to things that happen with the facility. In other words, for example, a hospital that shuts down a service such as the emergency room and institutes an alternative care strategy may impact local public administration and policy.
Coding and Classification Systems and Standards
Coding is the transformation of clinical workflow from any type of description in narrative or words into numerical data sets, or codes, that are used for documenting disease descriptions, injuries, symptoms, and conditions. Think of coding in healthcare as a form of translation, from language to numbers. There are many reasons this translation has to be done. One of the most important reasons is the amount of information that is found in healthcare information stores like medical records and billing reports. Using codes to standardize and organize helps providers describe the care they deliver. The translation also assists reimbursement and data surveillance activities by creating and using a taxonomy that contains common meaning.
Related to the use of codes, classification systems facilitate the terminology and taxonomy to be further organized for ease of use. Some of the leading examples of classification systems, such as DRGS and ICD-10, are described in this section. Because the terminology of diagnosis and treatment is so complex, classification systems bridge the gaps in understanding what clinical information means.
The compilation of codes and classification systems culminates in various standards for the common formats and definitions for important data. With all of the complexity between healthcare information technologies, interoperability and systems integration depend on sharing information and collaboration. Standards for the data include rules and procedures that organizations must adopt to share the information appropriately and efficiently. HIPAA is an example of a large set of standards meant to secure and control information exchanges of PHI.
Diagnosis-Related Group (DRG)
A DRG is a classification system used for quality of care and reimbursement matters. It is the basis of the US healthcare system reimbursement under Medicare plans. Patients are classified using DRGs, which helps to identify and organize the types of patients and conditions a healthcare organization treats into cohorts of common diagnoses, also known as a case mix. The DRG classification system can standardize the costs incurred by a provider, which influences billing and reimbursements. The following components are used to determine case mix as defined by the US Centers for Medicare and Medicaid Services (CMS):
• Severity of illness A measure of the mortality or incapacity for a patient with a specific disease.
• Prognosis A prediction of the likely outcome of a diagnosis. Included in the prognosis is any probability for changes in severity, positive or negative. Prognosis also consists of an estimate of the patient’s quality of life and estimated chances for survival.
• Treatment difficulty Consideration for the complexity or inability for a provider to accurately provide prognosis when examining a patient. The case mix considers the problems that result in treatment including the need to care for the patient very closely until more certainty is obtained.
• Need for intervention The possible outcomes if no intervention to the illness happens.
• Resource intensity Based on a specific illness, the amount of diagnostic, therapeutic, and bed services that are needed to properly treat the patient.
DRGs are designed to replace reimbursement based on fee-for-service billing with the Prospective Payment System (PPS), which uses DRGs and predetermined reimbursement rates for hospitals for services and treatment of specific conditions and to help determine prospective payment rates. There are more than 500 DRG classifications—for example, hernia procedures for a patient age 0 to 17 and fracture of femurs are two examples of DRG classifications. Within a DRG, services and processes should be similar and standard across any group of patients with a particular condition. Adjustments are made for the hospital’s case mix, as mentioned earlier, which is a way to account for differences in consumption of resources. Provider organizations are expected to adjust practice patterns to reduce variations that have minimal, if any, demonstrated clinical value. The provider assumes risk for any additional costs that exceed the DRG rate.
Because of concerns with PPSs, other arrangements have been formulated. For example, because of claims that hospitals were discharging patients too early because of DRG guidelines, financing mechanisms known as bundled payments emerged. In this model, payers and providers share risk at a more episodic level or per clinical case, tailoring the reimbursements to a specific patient care experience. Another example of a compromise between fee-for-service and lump-sum DRG reimbursements is Accountable Care Organizations (ACOs). In the ACO model, a willing coalition of physicians, healthcare organizations, and other provider groups agree to work together to deliver high-quality care and share financial risk for a common group of patients. ACOs were endorsed by the ACA, and CMS administers the reimbursement program. The ACO is a fee-for-service model, but the use of quality indicators and cost-savings approaches are rewarded with financial incentives such as bonuses for providers.
International Classification of Diseases (ICD)
The International Statistical Classification of Diseases and Related Health Problems, commonly abbreviated to ICD, is the foremost and most widely known hierarchal medical classification system. It is managed under the purview of the World Health Organization (WHO) to categorize diseases so that morbidity and mortality rates can be tracked and reported. The use of ICD codes—14,000 in total—is significant in the digitization of healthcare records and electronic record systems.
For example, code 382.9 is used for “unspecified otitis media,” a disorder characterized by inflammation, swelling, and redness in the middle ear. Instead of having to provide all that verbiage, medical billers can communicate the details of the diagnosis for the purposes of payment with a simple number up to six digits long that is internationally understood. Beyond facilitating the reimbursement of healthcare services, standardized codes make data analysis possible by providers and payers alike. ICD classifications of diagnoses and procedures are also suited for output reporting to regulators and for data analysis functions, where data aggregation is advantageous. The resource use and quality of healthcare can be improved by using ICD codes and data analytics to reduce unnecessary tests and services, and health status outcomes can be obtained and compared.
CMS mandated ICD-10 (tenth revision) adoption in the United States as of October 2015. However, because of concerns about the amount of codes, complexity, and cost of implementation, the United States uses a modified version of ICD-10. Published as “ICD-10 Clinical Modification” (ICD-10-CM) and a procedural classification called “ICD-10 Procedure Coding System” (ICD-10-PCS), these variations were developed by the National Center for Health Statistics (NCHS). In 2019, WHO approved ICD-11, which will go into effect in January 2022.
Systematized Nomenclature of Medicine Clinical Terms (SNOMED CT)
Another type of coding standard prevalent in healthcare is SNOMED CT. This is a repository of healthcare terms that is multilingual so it can be used worldwide. It facilitates a capability called semantic interoperability, which is important to the connection of SNOMED CT content to ICD-10, along with other coding standards. The repository contains over 311,000 discrete elements that are used to support accurate coding, retrieval, and analysis to comprehensively support clinical practices.
SNOMED CT is designed for the electronic exchange of clinical health information and is a required standard in the US Healthcare Information Technology Standards Panel and the Office of the National Coordinator for Health Information Technology (ONC) for certification of health information technology (health IT). A key use of SNOMED CT is to create interoperability between electronic health records (EHRs). In contrast to ICD, SNOMED CT is specifically used to describe extensive clinical terminology that is meant more as machine language to construct the EHR. ICD codes are useful for outputs such as medical billing and reporting in public health surveillance. SNOMED CT is a detailed terminology framework of concepts, descriptions, and relationships that works better for developing inputs into healthcare systems, which resemble data flow diagrams or flowcharts. Efforts are underway to integrate SNOMED CT and ICD, possibly when the ICD-11 standard is published.
Additional Coding Systems
Several other coding systems and standards have complementary or specific uses in healthcare. The following sections provide an introductory view of several that serve an administrative and clinical purpose for classification of payment, treatment, and healthcare operations. These may also be imperative for the continued digitization of healthcare information.
Logical Observation Identifiers Names and Codes (LOINC)
LOINC is a widely accepted coding system specially formulated for identifying laboratory and clinical observations. To be able to exchange observations and measurements electronically across multiple independent lab systems, LOINC uses a universal code system with a maximum field size of seven characters. This results in more than 71,000 LOINC values, which enable data transfer among providers, clinical laboratories, and public health authorities.
Ambulatory Patient Group (APG)
This classification system is used in outpatient services reimbursement. Hospitals may use it for emergency room care that does not become an inpatient admission. Otherwise, the system is used in settings such as same-day surgery clinics and primary care offices. It classifies patients into more than 300 outpatient services. The purpose of the APG system is to outline the resources required to provide necessary care. It is analogous to DRG, which classifies inpatient services.
Ambulatory Payment Classification (APC)
APC is mainly a US coding system that is used for Medicare reimbursement. It is applicable only to hospitals and is used as an outpatient prospective payment system. As the DRG system is used to bill inpatient services, when an emergency room or hospital-based service does not lead to a patient admission, outpatients services are billed to Medicare using the APC system. The APC system accounts for every resource used in the outpatient visit. The standard is being considered for wider use in US states under Medicaid reimbursement as well as some private third-party insurers.
Resource Utilization Groups (RUG)
These are commonly used in US long-term care or skilled nursing facilities reimbursed by Medicare and Medicaid. The RUG system consists of categories that reflect levels of resource needs to facilitate risk adjustment and complexity of care factors specific to long-term care. The primary use is for insurance billing purposes. There are 44 classifications that describe variables affecting care, such as patient status and the care needed by activity levels, underlying illnesses, the complexity of the care, and patient cognitive status.
Current Procedural Terminology (CPT)
The CPT system is used by all US healthcare payers and providers to document and report medical, surgical, radiology, laboratory, anesthesiology, and evaluation and management (E/M) services. The CPT is a five-character code that supports reimbursement by listing services provided. The initial version was published by the American Medical Association (AMA) in 1966, and the codes are updated every year. The rules for assigning CPT codes are complex, and there can be variation in how much a provider is reimbursed based on the accuracy and completeness of CPT coding. There are three categories of CPT codes:
• Category I Numeric codes that start at 00100 and end at 99499 and describe a healthcare service and procedure.
• Category II Alphanumeric codes that assist with measuring clinical performance if used. They are not mandatory.
• Category III Provisional codes used to track emerging technology, procedures, and services.
National Drug Code (NDC)
As required by the US Federal Food, Drug, and Cosmetic Act (FD&C Act), drug products are assigned a unique code—an NDC—that is ten or eleven digits in three distinct segments. The codes and corresponding drug identifications are listed in a repository called the NDC Directory, which is maintained by the Food and Drug Administration (FDA). The information in the NDC Directory is updated every day and is used worldwide to identify specific products and sizes by manufacturer. Not every drug has a corresponding NDC; only those that are submitted to the directory and marketed for human use.
Healthcare Common Procedure Coding System (HCPCS)
The Healthcare Common Procedure Coding System (HCPCS) is used much like the ICD system to accomplish medical coding. HCPCS (nicknamed “hick picks”) is an outpatient system used to ensure that hospital procedures and physician services are reported and processed in an orderly and consistent manner. (The ICD system is used in some outpatient scenarios, but all inpatient coding.) There are two levels of HCPCS codes. Level 1 codes are, in essence, CPT codes which, as explained earlier, describe products and services healthcare providers deliver. Level 2 codes are used for additional procedures and materials that are not included in Level 1 codes. Examples of items included in Level 2 codes are medical equipment, medical devices, or medical transport.
Revenue Cycle
An understanding of the financial components of healthcare delivery may help you better understand and build security cost–benefit analyses in your organization. The revenue cycle in healthcare includes billing, payment, and reimbursement. Without attention to resource allocation and fair compensation for healthcare services, these services would not happen—at least they would not happen to the extent that the healthcare system of today would have state-of-the-art technology, highly trained professionals, and well-apportioned facilities available.
Claims Processing and Third-Party Payers
If a third party is the payer for healthcare services, claims processing comes into play. For example, in a simplified patient-provider transaction, the provider may charge $100 for a service, and the patient may pay a $25 copay. The remainder of the bill, $75, is sent to the third-party payer as a claim against the insurance or government reimbursement.
The claims process actually begins prior to the patient’s appointment. Preapproval is often required, in which the third-party payer must authorize the doctor visit, all or a portion of the services, and any of the recommended follow-up care. Without preapproval, third-party payers can reduce the amount of reimbursement owed, or they may even deny the claim. The patient would then become fully responsible for paying the bill in its entirety.
With preapproval, the normal process for claims would include the physician sending the bill (after copay) to the third-party claims-processing center. Although providers can submit claims manually on paper forms, they more commonly file the claims electronically. Estimates show that electronic claims are three times less expensive than submitting via paper. However, securing the electronic transaction is a concern for healthcare information privacy and security. The claims-processing center compares the patient information and any relevant documentation of the services provided to the explanation of benefits (the policy terms and conditions). Once the third party determines all preapproved services were delivered and covered in the policy, it will submit payment for the remaining balance to the physician.
Payment Models
In the healthcare revenue cycle, claims processing leads to payment or reimbursement for services. The models for these payments have distinct features. In the dominant model, fee-for-service, providers are paid for each service rendered to a patient. This model is used in managed-care plans or when a government payer is involved. Without reiterating how those models work, variations of the fee-for-service model exist and should be understood by healthcare employees. These are discussed in the following sections.
Bundled Payment
Bundled payment is a more predetermined payment model than fee-for-service. In this model, a healthcare provider is compensated based on expected costs for each acute-care episode, not necessarily the actual costs. The parameters of the event, however, are determined by clinical judgment. The episode must have a clear beginning and end, require defined services, and have established clinical guidelines that allow for best practices. Conditions such as cataract surgery, services for end-stage renal disease, and coronary artery bypass grafting (CABG) to improve blood flow to the heart are bundle payment candidates. Bundled payments are central to any healthcare reform debate (in the United States) because of their ability to help reduce healthcare costs, and they are championed by physicians and administrators alike.
Capitation
An even more predetermined compensation model, capitation is a payment arrangement of a set amount for each person covered by the third-party payer. Providers agree in advance to accept a capitated amount, which is a fixed and predetermined payment amount for each person, based on a specified time period in which that person seeks care. A common way to describe this is “per member, per month” system for the provisions of capitation and coverage to which a healthcare provider agrees. To be clear, capitation does not relate to a specific episode of care or event, like fee-for-service and bundled payments. The average expected amount of care for each member that the payer disburses is calculated, and the payer enlists providers that agree to accept this payment. Providers accept a level of risk that they will be able to provide adequate care at some funding amount less than the capitated amount to therefore make a profit. If the amount of care exceeds the capitated amount, the provider takes the loss for excess spending—even if the care was clinically necessary.
The US Evolving Payment Model
Even with alternatives to fee-for-service, additional models of payment (sometimes discussed as part of healthcare reform in the United States) are worth mentioning. The patient-centered medical home (PCMH) and the accountable-care organization (ACO) models are presented here.
In the PCMH model, patient treatment is coordinated by a primary-care manager who makes sure the patient receives appropriate levels of care. This can mean that clinically necessary referrals to specialists or diagnostic tests are vetted by the primary-care manager. As they are approved, these treatments, tests, and referrals are explained to the patient to reduce confusion and help increase the likelihood of patient compliance. Confusion and lack of patient compliance are issues that increase waste and redundancy.
PCMH has a goal of building a relationship for the benefit of the patient that includes physicians, selected family members, and the patient. There is a high degree of integration of information technology and health information exchange (requiring privacy and security considerations). All of these attempt to provide the right care at the right time at the best value from both the perspective of the patient and the provider (healthcare organization).
Physicians, hospitals, and other relevant health service professionals are testing a model that joins them together contractually to provide a broad set of healthcare services. This is an ACO, which is formally organized and applicable currently to Medicare patients only. Even though the ACO may not consist of organizations within the same corporate structure, the intent is to deliver seamless, coordinated care. In fact, as the name states, within the framework of the ACO contract, this organization is accountable to providing such care.
The payment model in healthcare must change from fee-for-service to something more efficient and effective. Churning out services for chronic diseases without regard to improving outcomes can no longer be reimbursed. An ACO (and the PCMH) model strives to improve quality and reduce hospital admissions (and readmissions) and emergency-room visits. In return, costs are contained, and the participating providers can share in the savings.
Medical Billing
An important component of the healthcare revenue cycle, medical billing is how healthcare providers initiate the process for payment. A claim is generated based on the services and products provided and a medical billing professional sends the payment request to payers, typically a healthcare insurance company, the government, or the individual. Providers may employ a couple different strategies in submitting their bills (or claims for payment). Depending on the size of the provider organization, larger practices tend to submit bills electronically to the payer. In smaller practices, it is more common for the forms to be completed on paper. Because the analog data must be converted to digital before submission, an entity called a clearinghouse receives these paper forms from multiple small practices, converts them to digital files, and submits them to the various payers.
A clearinghouse is not a healthcare provider; it is an entity that works in the middle of the transaction between a healthcare provider and whomever is providing payment or reimbursement. The clearinghouse function is not limited to changing paper-based information to digital. It also serves to improve handling claims and revenue collection of the provider by simplifying the process. For a small practice, having most, if not all, bills rejected because the data fields do not conform to the payers’ proprietary format can cause significant financial distress, maybe even bankruptcy. Clearinghouses can serve a significant role in increasing efficiency and reducing errors.
Assuming the data elements are all present and in the correct formatting, another hurdle that providers must overcome in the billing process is medical necessity. Payers review bills to make sure the patient was covered and the services were a medical necessity. The guidelines for medical necessity are established by different state agencies and even by each payer, but all should be located in the federal Medicare statute, which outlines what is reasonable and necessary. In the event a service is deemed not a medical necessity, the claim is denied or rejected, and the provider is notified, usually in the form of explanation of benefits (EOB) or electronic remittance advice (ERA), which also explains why the claim was returned unpaid.
It is clear that in the United States, medical billing is a complex process with almost countless payers and oft-changing regulations. Many argue that this results in measurable additional administrative waste generated in the healthcare system. The administrative burden is necessary, however, and securing these transactions starts with understanding the importance of the interconnections.
Transaction Standards
From the various coding standards such as ICD-10 and CPT, we must be aware that the communication of the codes between provider and payer aligns to transaction standards. As we alluded to in the previous section, rejection of claims happens pretty regularly. Common reasons for rejection are incorrect codes and sometimes non-standard code use. Assuming proper use of transaction standards, you will want to be familiar with how to secure their transfer for continuous and reliable business and clinical operations.
HIPAA Transaction and Code Sets (TCS)
Healthcare information protection professionals are likely aware of the sections of the Health Insurance Portability and Accountability Act (HIPAA) that cover privacy and security standards, just two of the four standards or rules that make up HIPAA. The other sections cover identifiers and transactions and code sets.
The electronic transfer of healthcare information generates information security concerns, so you must have an awareness of this area. The Identifier Rule in HIPAA mandates that uniform identifiers be used for health insurance plans, providers, employers, and patients to facilitate electronic transfer of information. HIPAA TCS are associated rules that also standardize the electronic exchange of healthcare information. The exchanges are computer-to-computer and need no human involvement. The underlying processes are based on electronic data interchange (EDI) standards. The application of this standardizes what types of codes healthcare practitioners use when communicating with payers. For example, HIPAA TCS sets CPT as the standard for procedure codes and ICD as the standard for diagnoses. There are competing code frameworks, but HIPAA TCS forces adoption of one over another. With the Identifier Rule, HIPAA TCS is intended to produce efficiency and cost reduction as part of a concept called “administrative simplification.”
ASC X12N Claim Protocol
The American National Standards Institute (ANSI) Accredited Standards Committee (ASC) X12 developed this protocol for HIPAA transactions as part of a larger body of work for all electronic transactions. Many industries including healthcare use X12-based standards as well as adopting X12 XML schemas as they emerge. There are over 315 X12-based standards. X12N—note the N—is the nomenclature used for healthcare claims. As part of administrative simplification, electronic transaction standards mandated or proposed under HIPAA are also compliant with X12 standards. One way to think of the ANSI format is as a form that consists of the HIPAA TCS standards that is then transmitted. The following list is a sample of X12N electronic transaction formats that are part of HIPAA TCS standards:
• Health Care Claims or Equivalent Encounter Information (X12N 837)
• Eligibility for a Health Plan (X12N 270/271)
• Referral Certification and Authorization (X12N 278 or NCPDP for retail pharmacy)
• Health Care Claim Status (X12N 276/277)
• Enrollment and Disenrollment in a Health Plan (X12N 834)
• Health Care Payment and Remittance Advice (X12N 835)
• Health Plan Premium Payments (X12N 820)
• Coordination of Benefits (X12N 837 or NCPDP for retail pharmacy)
ANSI chartered the ASC to oversee the evolution of the X12 standard. ASC X12 version 5010 is the current protocol.
National Uniform Billing Committee (NUBC)
In 1975, the AHA chartered the NUBC because they recognized the need for providers and payers to have and use a common billing form with standardized data. The NUBC was started with the responsibility to create and manage the streamlined billing components. The first uniform bill (UB) was published in 1982 as UB-82, which was updated a decade later by UB-92 after an eight-year hold on any changes during initial adoption. This was the standard for paper-based medical billing until 2004, when UB-04 was available. This version of the standard medical claims form was digitized to support electronic transmission. The current version has 81 separate fields known as form locators (FLs). Each FL has a specific purpose, but some FLs are currently not used.
Reimbursement
Reimbursement is the final step of the revenue cycle. As claims are processed and bills are submitted (and resubmitted), the desired outcome from the provider’s perspective is to receive reimbursement for the cost of the healthcare. In a word, reimbursement is repayment for expenses incurred. It is uncommon for reimbursement to equal expenses, however. Healthcare providers and payers continually work together to set rates of reimbursement and adjust them against a standard loosely defined as charges that are “usual, customary, and reasonable.” That standard is increasingly squeezed to lower reimbursement rates, which constrains providers that may have capital investments that rely on the margin between cost and repayment. But the counterargument (from payers) is that consistently squeezing reimbursement rates encourages providers to be more efficient and productive.
Workflow Management
Workflow management in the healthcare setting describes the various clinical and business processes providers use. These processes are complex and dynamic. To reduce cost and improve quality, there are efforts to streamline, automate, and reengineer workflow processes with which you should become familiar. Many have information security implications, because with electronic information and EHRs, sensitive data moves through the information system. Often healthcare organizations interoperate, merge, or otherwise create a larger scale of operations. In these cases, workflow management may have information protection challenges in connecting legacy systems, for example. Organizational management of workflow leads to greater efficiency, better access to quality healthcare, and improved patient safety across care settings.
Clinical Workflow
Clinical workflow includes the various processes and patterns of actions clinicians use to deliver healthcare. With regard to electronic information and EHRs, clinical workflow describes how the data moves through the information system, by whom, to whom, when, and how often. Proper management of the workflow assists with compliance and achievement of practice objectives for quality and efficiency. Using health information systems to automate various clinical workflows can have a positive impact on clinical outcomes, minimize medical errors, and reduce costs over time compared to manual processing.
Examples of clinical workflow components include actions taken to register a patient, document patient information gathered during an appointment, develop a treatment plan, prescribe any follow-up tests and medications, provide patient education material, schedule future visits, and process bills or claims, among others. Many processes and subprocesses are involved as a patient moves through the physical organization. The need for electronic data related to these actions must also operate in a synchronized, parallel fashion through the information systems.
Figure 1-4 depicts the general idea of clinical workflow. The figure is intended to illustrate the integrated process involving clinicians, administrative personnel, and technicians, and the example used is not comprehensive. Because there are more interactions and participants in the typical clinical workflow, a single diagram probably cannot depict the entirety of the typical clinical workflow.
Figure 1-4 Clinical workflow
Business Process Reengineering (BPR)
Business process reengineering is the review and transformation of central business processes to improve performance measures such as throughput, quality, and efficiency. These improvements typically come from automation of manual processes or the implementation of a new technology. The change is characterized as dramatic, with outcomes that are significant versus incremental. An example is the use of radio-frequency identification (RFID) logistics systems to track patients, supplies, and equipment via a networked information system.
Some major activities of BPR:
• Focus centrally on customer requirements
• Enable the core process improvements, typically with information technology
• Create business teams with multidepartment representation responsible for an entire process
• Challenge status quo within the organization
• Make the process improvements an enterprise-wide effort
BPR has a continuous cycle that an organization can use to address improvement opportunities. That lifecycle is depicted in Figure 1-5. Notice the lack of a distinct start and stop timeline—BPR should be part of a broader, continuous improvement program in the complex and dynamic healthcare organizational environment.
Figure 1-5 BPR lifecycle
Value Stream Mapping (VSM)
As a business process improvement concept, value stream mapping is rooted in lean-management techniques made popular by Toyota decades ago. VSM is a way to gain improvement by assessing current processes and making changes to arrive at a desired state at a designated time. The focus that leads to improvement involves eliminating waste as much as possible. Although the concept emerged from the manufacturing industry, it has been used in the healthcare environment. The seven categories of waste listed here certainly pertain to healthcare organizations, indicating that value streaming can be relevant and effective in healthcare:
• Faster-than-necessary pace This refers to overproduction, when too much of a good or service is created. The impact is a damaged production flow, quality, and productivity. At the end of the process, storage is required and lead time wastes result.
• Waiting This is the time wasted while goods are not being transported or worked on.
• Conveyance This refers to the transport process by which goods are moved around; specifically important are any instances of double-handling and excessive movement.
• Processing This refers to an overly complex solution for a simple procedure and includes unsafe production. The impact of this category of waste is poor layout and communication and unnecessary motion.
• Excess stock Surplus levels of unnecessary inventory results in greater lead times, increased difficulty identifying problems, and significant storage costs.
• Unnecessary motion Ergonomic waste is to be avoided and requires employees to use excess energy such as picking up objects, bending, or stretching.
• Correction of mistakes Avoid any cost associated with defects or the resources required to correct them.
Regulatory Environment
Healthcare is a highly regulated industry. The US healthcare industry’s influential regulators include the US Department of Health and Human Services (HHS), the Centers for Medicare and Medicaid Services (CMS), the Food and Drug Administration (FDA), and the Centers for Disease Control and Prevention (CDC), to name a few. These are just a sample of the government entities with authority to regulate healthcare organizations. These regulators have a principal responsibility over enforcing the law as well as clarifying the guidance they implement. Each plays an important and distinct role as the laws they enact have a specific purpose and scope, although there are examples of overlap.
Federal regulators work in tandem with state level legislatures and local lawmakers such as health departments and state insurance commissioners. In many cases, state governments have enacted legislation that has surpassed or satisfied gaps in federal regulations for healthcare. An example is the state of Massachusetts that mandated health insurance coverage for all its citizens in 2006, before the federal ACA. The Massachusetts law has been amended in several ways since then to make it consistent with the ACA, and for other reasons.
The regulatory environment is not limited to government agencies enforcing laws. Healthcare is impacted by other types of regulatory actors as well, including agencies that assess or audit the payers and providers against standards and acceptable practices. Some standards are mandatory, and others are voluntary, such as standards created by the Joint Commission, formerly the Joint Commission on Accreditation of Healthcare Organizations (JCAHO). However, even voluntary standards often can have the same impact as legal requirements. In the case of the Joint Commission, healthcare organizations have determined that absent JC accreditation (meeting the JC standards) may have a detrimental effect on government reimbursement, payer network inclusion, or patient perceptions.
Another example of external forces that impact healthcare from a regulatory aspect is litigation. From time to time, a legal case will be brought against healthcare organizations. Consider anti-trust cases, for example. Imagine that an independent physician organization brings suit against a large integrated health system that yields influence on those physicians to refer exclusively to the health system or risk some form of penalty later.
Figure 1-6 shows some examples of regulatory pressures that impact healthcare. From a healthcare information protection perspective, you will be most concerned with laws such as HIPAA, and, if you are working in or with member states of the European Union (EU), the General Data Protection Regulation (GDPR). Additionally, you will spend the most time learning and adhering to state, local, and organizational regulatory guidance in the form of laws as well as policies and procedures. We will cover this topic in greater depth in Chapter 4. For now, it is enough to have a foundational view that healthcare delivery is accomplished only by simultaneously providing quality patient care, meeting business objectives, and complying with myriad regulatory impacts.
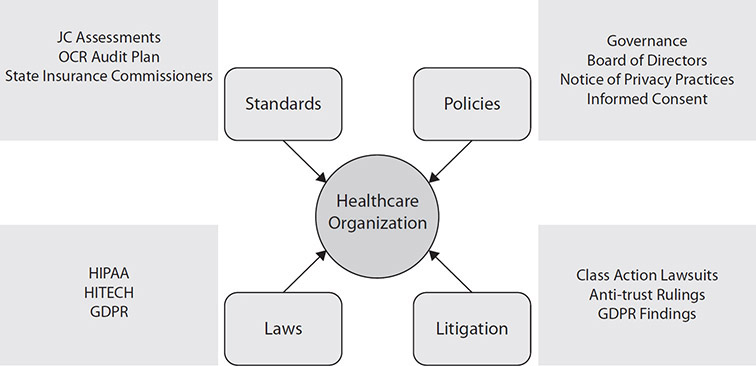
Figure 1-6 Some of the regulatory forces that influence healthcare organizations
Patient Rights
Another aspect of the regulatory environment is the protection of patients from various types of harm—for our purposes, harm from unauthorized access to information, loss of sensitive data, and lack of data availability. In fact, some types of cybersecurity issues can result in adverse patient care events. Regulatory oversight helps to provide assurance for patients and the communities in which providers deliver care.
Patient rights are expectations patients should have and obligations providers must respect. They can be written into laws such as the HIPAA Privacy and Security Rules. Patient rights can be specific to an organization and codified in organizational policy. Typically, a patient would receive a copy of relevant patient rights, or they are made available on the provider’s web sites.
Following are some examples of patient rights that are applicable to information protection concerns:
• You must get a written explanation of how the provider may use, store, and share the information.
• You must be provided access to your records, obtain copies, and request changes.
• The provider must allow you to limit use or disclosure of your information outside of regular healthcare treatment, payment, and operations.
• The provider must notify you in the event of any information security breaches that are reportable under HIPAA breach notification law.
Patient Care and Safety
Yet another reason why the healthcare industry is regulated so extensively is because of the importance of quality patient care and the need for patient safety. Healthcare information security can be related to these concerns in that data breaches, denial of service (DoS) attacks, and ransomware attacks are just a few of the potential threats to healthcare information security that could negatively impact the quality of patient care and endanger the patient. The potential for harm has been recognized by US regulators. For example, to warn against manipulation of clinical systems and clinical data or even manipulation to patient data, the FDA and the US Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued an alert in 2015, based on a vulnerability where an infusion system could permit an attacker to remotely control a device and alter therapy administration.
The Cybersecurity Information Sharing Act (CISA) was published in an attempt to address the growing threats from cyberattackers in the United States by improving the opportunities for government and private organizations to exchange cybersecurity-related information. This information sharing between government agencies and providers has several benefits specific to healthcare, one of which is reducing the likelihood that a vulnerability in a clinical system or medical device can be exploited. Regulators have begun to enable an environment where risk data can be shared. A notable group working on increased public–private partnerships in healthcare information security is the Health Care Industry Cybersecurity (HCIC) Task Force. The task force members represent a wide variety of government and private sector organizations within the healthcare and public health sector. Participation comes from healthcare providers and payers as well as stakeholders such as privacy advocates and academic researchers. Some of the key participant groups are medical device manufacturers and industry groups related to medical device security. The task force recognizes the connection between healthcare information security and the impact on patient care. It highlighted the following six imperatives in its report to Congress,14 along with recommendations for best courses of action for public–private partnerships to make improvements:
• Define and streamline leadership, governance, and expectations for healthcare industry cybersecurity
• Increase the security and resilience of medical devices and health IT
• Develop the healthcare workforce capacity necessary to prioritize and ensure cybersecurity awareness and technical capabilities
• Increase healthcare industry readiness through improved cybersecurity awareness and education
• Identify mechanisms to protect R&D efforts and intellectual property from attacks or exposure
• Improve information sharing of industry threats, risks, and mitigations
Public Health Reporting
Sometimes, healthcare organizations collect information from patients that is legitimately needed by public health officials. These are third parties that are not vendors but are most likely government agencies. In the United States, the HIPAA Privacy Rule makes provisions for healthcare organizations to legally disclose protected health information to public health and safety agencies for the benefit of public health. Provisions regarding public health reporting in the United States can be complex and vary among jurisdictions. Generally, public health requires disclosure to identify threats to the health and safety of the total community and individuals. Along with reporting of births or deaths, the Department of HHS in the United States allows public health reporting that consists of the following:15
• Child abuse or neglect
• Quality, safety, or effectiveness of a product or activity regulated by the FDA
• Persons at risk of contracting or spreading a disease
• Immunizations, disease registrations (such as cancer), and substance abuse
• Workplace medical surveillance when healthcare is provided at the request of the employer or as a member of the employer’s workforce
Similar provisions for public health reporting exist in the EU as well, according to the GDPR, which allows public health reporting for data controllers “pursuant to legal obligation of the controller under GDPR Article 6(1)(c)” and (when) “processing necessary for reasons of public interest in the area of public health . . . such as ensuring high standards of quality and safety of healthcare and of medicinal products” under GDPR Article 9(2)(i).”16 Allowances for public health reporting is an almost universal exception to the information protection guidelines.
Even though healthcare organizations are generally permitted (and often required) to disclose patient information for public health reporting purposes, there are still things to consider before disclosure. The information provided should be limited to only what is required. In the United States, HIPAA provides guidance for minimum necessary uses and disclosures of and requests for PHI—that is, healthcare organizations must take reasonable precautions to disclose the minimum amount of PHI necessary to accomplish the public health purpose.
Clinical Research
Clinical research is the investigation of wellbeing and disease in individuals. It is the way we figure out how to prevent, diagnose, and treat illness. Clinical research depicts a wide range of components of examination and study. Basically, it includes human study participants and applies basic research done in labs into new medicines and data to improve patient care. Clinical trials are used for research in the study of disease transmission, physiology and pathophysiology, health services, education, outcomes, and mental health. The safety and effectiveness of treatments and healthcare interventions is known today because of appropriate clinical research. Randomized controlled trials are the basis for “evidence-based medicine.” Appropriate clinical research is defined by standards and measures that are collectively known as Good Clinical Research Practice (GCP).
Good Clinical Research Practice (GCP)
To conduct research involving human subjects, the principles of GCP must be followed. There is generally accepted concurrence that GCP is critical to the ethical conduct of clinical research. Human subject protection (HSP) is a core component of GCP. The FDA publishes regulations and procedural guidance on the conduct of clinical trials. In the United States, the FDA has overseen regulatory matters in GCP and has contributed to the international adoption of GCP and HSP principles.
From an information protection perspective, clinical research differs from public health reporting in terms of use and disclosure of the PHI. Prior consent from participants is not always feasible or possible. In those cases, researchers in the United States can use an internal institutional review board (IRB) or a privacy board to obtain a waiver to any required patient consent. This is a very significant concept that can enable researchers to comply with the HIPAA Privacy Rule and other HSP guidance when researchers need permission. Increased disclosure of patient information is authorized for purposes of clinical research under HIPAA. When the information is used for clinical research, controls that would be required under HIPAA may be absent. You should be aware of the impact of clinical research on any data use scenario. A good IRB or privacy board will use documented protocols and controls to safeguard the protected health information as well as the privacy of research participants. Those would incorporate assurances that the use or disclosure of the patient information adds only a minimum of risk to privacy for the individual. An IRB or privacy board provides oversight in these cases and requires researchers to have the following:
• Alternative controls planned or in place to safeguard protected health information
• Suitable records disposal and destruction plans for patient information when it’s no longer needed
• Written statements to prohibit reuse or disclosure of patient information unless permitted by law or the IRB or privacy board
• Sound reasons for why the research is not possible without a waiver to permit access to and use of the patient information
An IRB operates under the principles of the Belmont Report, which was written by the National Commission for the Protection of Human Subjects of Biomedical and Behavioral Research as an outcome of the National Research Act of 1974. The Commission was established to examine what fundamental underlying ethical principles should be present in this type of research. The Belmont Report attempts to summarize the findings by the Commission as it disclosed the behaviors the researchers exhibited.
Some clinical research is supplied to a healthcare organization through a third party called a contract research organization (CRO). A CRO provides support to healthcare organizations conducting very specialized types of biopharmaceutical development, preclinical research, clinical trials management, and drug safety. For the most part, these advanced research types are done by leading pharmaceutical, biotechnology, and medical device industry companies. The CROs also support academic medical centers, the government, and international organizations. The ability to partner with CROs enables the development and evaluation of all the various trials of safety and efficacy, but not have to have internal staff from the healthcare organization dedicated to the research. For medical devices, the CRO gathers clinical data to support an FDA regulatory premarket submission, drive product adoption, support product reimbursement, or monitor post-market product use. It brings expertise and streamlined processes at a much more cost-effective level than what would be experienced by the healthcare organization if it had to do the same processes itself.
De-identification of Patient Information
Removing any individually identifiable information from the data set helps us be reasonably certain no one can identify someone else based on the remaining information. There are two ways to do this: First is expert determination, in which a person trained in de-identification through complex processes concludes that the algorithms used and the resulting data are sufficiently anonymized and the risk of identification minimal. The second way is simply to remove completely these same categories of identifiable data, which, under the HIPAA Privacy Rule, is called the safe harbor method.
The following list provides the standard categories and sources of data that may be individually identifiable information according to the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-122.
• Name, such as full name, maiden name, mother’s maiden name, or alias
• Personal identification number, such as Social Security number (SSN), passport number, driver’s license number, taxpayer identification number, patient identification number, and financial account or credit card number
• Address information, such as street address or e-mail address
• Asset information, such as Internet Protocol (IP) or media access control address, or other host-specific persistent static identifier that consistently links to a particular person or small, well-defined group of people
• Telephone numbers, including mobile, business, and personal numbers
• Personal characteristics, including photographic image (especially of face or other distinguishing characteristic), X-rays, fingerprints, or other biometric image or template data (such as retina scan, voice signature, or facial geometry)
• Information identifying personally owned property, such as vehicle registration number or title number and related information
• Information about an individual that is linked or linkable to one of the above (such as date of birth, place of birth, race, religion, weight, activities, geographical indicators, employment information, medical information, education information, and financial information)
Additional health informatics standards in this area also call out risks related to rare data and small sample sizes. For example, ISO 25237, Health Informatics – Pseudonymization, contains principles and requirements for privacy protection using pseudonymization services (which replace PII fields with artificial IDs, or pseudonyms) for the protection of personal health information (see the “International Organization for Standardization (ISO) 25237:2017” sidebar). Organizations that perform pseudonymization or rely on organizations that perform such services may find this guidance very helpful. There are several clauses that are central to the ISO 25237 standard. These relate to de-identification components, such as streamlining down to one concept and method for pseudonymization. Other clauses outline the particular policy framework for pseudonymization with minimal requirements for re-identification. As a healthcare information privacy and security professional, you might be most interested in the clause that addresses the risk assessment processes for how effective pseudonymization is and how likely re-identification might be.
Another source of guidance on de-identification is the Integrating the Healthcare Enterprise (IHE) “De-Identification Handbook.” This material provides an integrated view of the design, approaches, and risks of de-identification as a goal. The end result is proper removal of PHI through various methods such as removing data elements and pseudonymization. The guide also covers re-identification. The general process must be customized and should be adapted to specific situations. There is no universal de-identification profile that fits every organization and situation for data needs. Specifically, this means that each reviewer must create a profile specific to the information being processed, applicable laws and regulations, organizational policies, the operational environment, and more. The design and operation of any de-identification profile or system must be validated and monitored. Validation should occur early in the design phase, again when the system is going live, and during operational use. The characteristics of many data sets change over time, and monitoring production de-identification systems helps ensure that they remain effective over time. It is also important to remember data that is appropriately de-identified for one purpose (such as a clinical trial) may not be correctly de-identified for a new use of the data (such as using the same data set for a public health database).
Clinical researchers are afforded some flexibility in the ability to share information legally without gaining prior or additional patient consent. Some of the provisions researchers may apply to use or disclose protected health information without authorization by the research participant are listed here:
• Limited data sets Some of the patient information can be excluded, and what remains is the minimum number and types of identifiers needed, if any. You would usually have a data use agreement (DUA) in place for use of a limited data set that would also determine who needs to know the information and for what purposes.
• Accounting of disclosures Researchers must keep and be able to provide a record of all information disclosed, by whom, and to whom outside of the research organization (such as another research organization doing similar trials) during the life of the research.
• Data use agreements Before the use or disclosure of a limited data set to an external person or organization, the HIPAA Privacy Rule requires the use of a DUA, which outlines several provisions to protect the data because the limited data set is still PHI. The DUA must do the following:
• Outline for what purpose the data is permitted to be used.
• Identify authorized recipients and users of the data.
• Limit additional, unintended uses once the information is disclosed. Exceptions for law enforcement reasons and specifically granted within the DUA are allowed.
• Extend the obligation to protect the sensitive information from unauthorized disclosure to the authorized recipient. The recipients must extend the same requirement for any further authorized disclosures.
• The recipient must report unauthorized disclosures to the source that provided the data.
• If data is de-identified, the recipient should be prohibited from making attempts to re-identify individuals.
• If the data is breached, the recipient must make reasonable efforts required by law to remedy the event.
Healthcare Records Management
The proper management of healthcare records is an application of the overall information management lifecycle that applies to paper-based records and digital records alike. Healthcare information can be collected and stored on all types of media, such as paper, photography film, optical disks, microfilm, magnetic tapes, CD-ROMs, DVDs, hard disk drives, solid-state drives, floppy disks, or USB flash drives. Records can be retrieved from physical storage in records rooms and warehouses. More commonly today in the digital environment, electronic information is found in application-specific databases, diagnostic biomedical devices, master patient indexes, patient medical records, and health information files. All information has a lifecycle with various phases in which information exists, and healthcare records are no exception.
All phases of healthcare records management require information protection. You need to understand some very important concepts related to the collection, use, storage, and disposal of medical information. The special protections and sensitivity of the healthcare information require certain provisions that may not be present in other information protection policies and procedures outside of healthcare organizations. Mishandling healthcare records can lead to patient safety issues as well as financial penalties or litigation.
A good healthcare records management process enables the organization to protect transactional and historical evidence across the entire continuum of treatment, payment, and operations. An effective records management system can improve provider practices, enhance quality of care, and save resources over time. Following are some specific reasons for a solid healthcare records management system:
• Maintains needed information for as long as the information is useful
• Satisfies requirements for retrieval for forensics and legal discovery
• Lowers costs of management of records over the lifecycle, including destruction
• Ensure business resiliency by providing access to archives that are reliable
• Improves reliability of data backups when information is retrieved
• Collects and maintains ownership and accountability of records
There are many reasons healthcare organizations collect data and maintain records. Obtaining information for records is not normally a problem. Overcollection, however, is usually the concern. Medical record information comes from a variety of sources and is used internally and externally. For example, records resulting from a recording of physician notes and orders are sources, and these same records may be used for data exchange for referrals to other providers or for reimbursement from insurers. Records may be used to report to public health or for collaboration in outside research.
Record Retention
The lifecycle of records management begins when information is created and ends when the information is no longer needed and properly destroyed. In the time period between, during health records retention, various issues may arise. Health records retention is concerned with how long an organization must maintain a record and for what reasons. The challenge is that there is a scarcity of regulatory guidelines for how long medical records must be maintained in every case. Generally, organizations develop their policy using a patchwork of statutes, regulations, case law, and state medical board position statements. In Table 1-2, an example from the American Health Information Management Association (AHIMA) Retention and Destruction of Health Information brief is provided to depict the types of guidance that exist in the United States for healthcare records custodians.

Table 1-2 AHIMA Recommendations for the Retention and Destruction of Health Information
As healthcare records have evolved from paper-based to digital, you might think the problems are becoming easier to manage, but this is not always the case. Digital data storage is, of course, relatively inexpensive and accessible compared to having to maintain large rooms filled with paper records. However, there is still a legacy of increasingly inactive paper charts that organizations must address. Managing protection and facilitating the infrequent access to paper is cumbersome and expensive. The second part of the challenge is related to the shift to digital records. Because paper records consume physical space, records retention policies and procedures were created as an imperative to make the best use of physical space. With digital storage, the space required is minimal, and too often, records retention is not established or adapted to these record sets.
Once an organization establishes a records retention policy, it needs to communicate the policy to patients along with information about how the patient can access their own information. At a minimum, record retention policies must do the following:
• Help the organization meet all the different requirements for uses of the records. Of course patient care is the primary requirement, but there are legal and research needs that can extend reasons for maintaining the records. For example, records involved in any open investigation, audit, or litigation must not be destroyed until the litigation case has been closed.
• Specify the types of information and the timeframes for keeping the records.
• Differentiate any variances based on the forms of storage, such as paper or electronic media.
• Present destruction options and standard operating procedures that include secure disposal methods.
Destruction of Patient Health Information
A retention schedule will end in a process for safely and securely destroying healthcare records. The destruction process must adhere to legal requirements and organizational policies. This is not a decision or a process that a healthcare information security professional is going to make individually. An information governance guidance is created by clinical and business leaders in the organization who consider the clinical, legal, and operations reasons to maintain records. This guidance must be in place and followed. When a record is no longer needed, it must still be protected until it is destroyed; records are often lost or accessed illegally at this point in the lifecycle because custodians relax controls.
Record retention and destruction processes have ambiguous and conflicting standards to follow. Some regulations and jurisdictions require the organization to create an abstract of the destroyed patient information prior to destruction, notify patients when destroying patient information, or specify the method of destruction used to render the information unreadable. In Chapter 5, you will learn about the technical and operational components of different health records destruction such as purging, degaussing, and data overwriting. Organizations should reassess their methods of destruction annually based on current technology, accepted practices, and availability of timely and cost-effective destruction services.
An important document that organizations must maintain is the permanent record of the destruction of the health records. Organizations should ensure that they can provide the following for evidence of secure destruction:
• Date of destruction
• Method of destruction
• Description of the disposed records
• Inclusive dates
• A statement that the records were destroyed in the normal course of business
• The signatures of the individuals supervising and witnessing the destruction
Access Control
Access control refers to the safeguards used to limit access to system resources after a user’s account credentials and identity have been authenticated and access to the system granted. Three major access control models are used to prevent unauthorized access to healthcare records:
• Mandatory access control (MAC) Typically used in military organizations, user access is defined by computer policy, is strictly enforced, and is relatively constant. The owner of the asset is not able to make changes unless the policy is reconfigured. Access control lists store the access properties associated with each computing asset (data, files, record, system, and so on).
• Discretionary access control (DAC) The least restrictive control grants the asset owner total control of settings on demand. Users can be granted rights to change access permissions and have control over healthcare records and other medical data. This can pose security risks and threats if used improperly.
• Role-based access control (RBAC) This approach is more realistic and is aligned with most risk-based organizational models. User access is limited based on predetermined definitions of what access a person in a job or function should need.
Authentication, Authorization, and Accounting (AAA)
Three individual access control terms—authentication, authorization, and accounting—are the components of a structure that regulates access to information by administering policies and monitoring use. The objective is to ensure authorized users have legitimate access. These combined processes are a necessity for secure computer and network use.
Authentication is the process of determining that the user who requests access is who they claim to be. This is typically accomplished by requiring a unique set of credentials to gain access, such as a unique username and valid password. If the credentials match what is stored in the identity management database (sometimes called the AAA server), the user is granted access to the network. If the credentials do not match, access to the resource is denied.
Authentication provides the framework for the next component, user authorization for performing certain tasks. Once authenticated, the user needs authorization, or a level of permission, to accomplish various actions based on policies. Authorization is the process of enforcing these policies. Each authenticated user may be authorized for different types of access or activities.
To measure resources a user consumes during access, the AAA concludes with accounting. A component of auditing in general, accounting documents and reports the consumption of resourcing time and session activity that assists in management of access control.
The reality is that in many hospitals, if not many healthcare organizations, finely tuned access control is almost impossible. It is nonetheless important, and compliance with access control standards is directed by regulation. You should be aware of the factors that make access control difficult. With an EHR, guarding against unauthorized access to PHI is complex. Patient care is dynamic, personalized, and often involves many hospital employees in many roles. Determining who needs access is tough. Access is not predictable or certain for any individual provider, and configuring an EHR to support frequent changes is infeasible. When patient care is provided in an emergency setting, who has access to EHRs is even more difficult to predict with any certainty. As a result, most organizations allow more access than is required; once an employee is authenticated to the EHR, they can access any patient’s medical record. This is not an effective implementation of access control.
The other problem is how much PHI is accessed. The frequency of access to PHI in an EHR can be several million events per week in a typical provider organization. With so many accesses by too many users with too much access, you can imagine that log management and audit is almost impossible. Trying to find unauthorized access is a daunting task.
Using role-based authority and authorization controls without a firm understanding of healthcare workflow can cause problems. Because many roles in the organization change frequently, the access and privilege process must be flexible. For example, a physician may be a pediatrician, so he or she will have access and privileges to view and edit children’s medical records yet be prohibited from accessing adult records in the ICU. However, if the physician is accessing the system while participating in a medical records peer review process, he or she may be granted temporary, expanded access.
Least Privilege
The general security objective of least privilege involves granting users the minimum access rights that they need to perform their official duties. In healthcare, that means healthcare records are treated as confidential, access is denied by default, and access must be explicitly granted. How a healthcare organization maintains healthcare records using least privilege will be written as policy, and that policy will state who has access.
Separation of Duties
No single user should have the permissions or authorization in the healthcare record system to complete high-risk tasks independently. A good access control system is configured to ensure that no individual has total control of security configurations. Separation of duties prevents against many instances of insider threats and employee mistakes that can lead to compromise of healthcare records. The adherence to separation of duties also mitigates a situation where multiple users with least privilege access join together to increase access to information, which would be unauthorized on an individual basis.
Third-Party Relationships
A discussed earlier, the first party in healthcare is the patient. A physician, a provider group, or another healthcare organization is the second party. Another very important component in the healthcare industry are third parties that supply or operate on behalf of the healthcare organization. These entities comprise any of the external organizations that supply or support the first and second parties in the clinical and business activities involved in healthcare. For those third parties that also handle PHI as part of their business relationships, special privacy and security concerns exist.
Vendors
A vendor is a person or an entity that sells, supplies, or provides a service or product. Most healthcare organizations rely on many vendors. It is impractical, if not impossible, for a healthcare organization to employ or own all the various services and suppliers it needs to operate. For example, a healthcare organization may obtain contracted services for housekeeping and maintenance rather than try to operate those services with employed staff of the organization.
The reliance on these external relationships introduces privacy and security considerations, because the vendors and suppliers will be under the same regulatory obligations that affect the healthcare organization. The healthcare organization will maintain the responsibility to ensure that the external entities comply with these regulations.
Increased emphasis on information protection has moved healthcare organizations and industry oversight authority (including government) to establish cohesive vendor management or credentialing solutions. For instance, in Canada and relative to PHIPA (Personal Health Information Protection Act), there are privacy and confidentiality concerns with sharing of information between healthcare providers and third-party vendors. Canada has established a nationwide vendor credentialing system that enables healthcare providers a level of assurance that third-party vendors understand PHIPA and will comply.
In many cases, a vendor may have many different customers that are not healthcare organizations. Their service or product may or may not be healthcare related. For instance, a vendor can be an office furniture company and may sell all of the interior design and furnishings for a hospital waiting room, administrative offices, and conference rooms. At the same time, a medical supply company that provides durable medical equipment, surgical supplies, and hospital quality beds is also a vendor. The office furniture company undoubtedly sells furniture to a variety of business types, while the medical supply company probably does not have any customers outside of healthcare organizations and practices. For either of these vendor types, the healthcare organization, if large in size and purchasing power, will be a significant customer.
A vendor will employ members of the community based on the vendor’s successful relationship with the hospital. For example, the nonprofit Henry Ford Health System in the Detroit metro area specifically emphasizes diversity and minority- and women-owned business in its supply chain database, which consists of more than 300 active vendors in this category.18 The company’s large purchasing power works to support not only the employment rate in the community, but the minority-owned business goals. You can see how the vendor (and the community) depends on the business of healthcare.
Because the relationship between vendors and the healthcare organization is so important and probably very competitive, healthcare organizations establish written policies to govern these relationships. Some of the major components of these policies include the following:
• Definition of the relationship
• Limits to gifts or gratuities
• Establishment and authority for oversight
• On-premises access rules
• Fundraising guidelines
Other special considerations are vendor-specific. For instance, vendors that work with academic medical centers have provisions for publishing by employees, seminar attendance and funding, and honorariums for speaking engagements. All of these provisions are meant to establish and maintain the integrity of the relationships. Unfair advantage of one vendor over another in many communities can mean the difference between a vendor business’s success or failure.
Business Partners
A business partner is a particular subcategory of vendor in healthcare organizations. Although business partners provide a product or service for the healthcare organization, the relationship between the healthcare organization and this vendor is not a transactional type. Business partners are characterized as having a longer or recurring relationship with the healthcare organization, commonly described in a contract or formal, written obligation. These relationships are particularly of interest when the business partner handles PHI for the healthcare organization. In the United States, a business partner is sometimes called a business associate. These vendors are subject to, like the healthcare organization, industry-specific privacy laws, such as HIPAA. Therefore, it is crucial for the healthcare organization, as well as any business associates, to understand how they must comply with the relevant regulations, even if the vendor does not serve only the healthcare industry.
Consider a data center provider, for example. The provider may serve the healthcare organization by maintaining all of the data storage, providing applications, and performing backup procedures offsite. The provider may also do this for the local public school system, a retail department store, and other non-healthcare clients. In any case, this vendor must maintain its data center according to the appropriate healthcare regulations, such as HIPAA. This would include signing a special contract, such as a business associate agreement (BAA), that specifically outlines the data center provider’s responsibilities and any provisions for noncompliance. You can imagine how complex this can be for a vendor.
Several requirements, with respect to the content of the BAA, follow:19
• The business associate must have appropriate safeguards to prevent use or disclosure of information other than as provided for by its contract.
• The business associate must report to the covered entity any use or disclosure of the information not provided for by its contract of which it becomes aware.
• The business associate must ensure that any agents or subcontractors agree to the same restrictions and conditions that apply to the business associate with respect to the individually identifiable health information being processed.
• The business associate must also make available protected health information for patient access and amendment, must make any amendment provided to it from the covered entity, and must provide an accounting of disclosures.
• The business associate must make its internal practices, books, and records relating to the use and disclosure of protected health information available to HHS for purposes of determining the covered entity’s compliance.
• At termination of the contract, the business associate must return or destroy all protected health information. The contract must also authorize termination of the contract if the business associate is in material violation.
The following list provides some examples of business associates. Whether or not they are business associates depends, again, on whether the contract involves the use, disclosure, transmission, or maintenance of PHI.
• Electronic health records and clinical software application vendors who plan, install, and support their products
• Any information technology vendor that provides cloud services to include data storage, application services, security, and hardware management
• Utilization review and management companies that analyze referral patterns and outcomes data to help shape the best and most efficient treatment options
• Physician office answering services that interact with patients and providers on behalf of the healthcare organization
• Data conversion, de-identification, and data analysis service providers
• Medical billing and coding specialists that are not part of the healthcare organization as employees, which can be work-from-home, decentralized businesses
• Academic healthcare researchers, under some circumstances where HIPAA applies
• Third-party medical transcription companies that convert the provider’s verbal dictation to a written or digital format
• Health information exchanges (HIEs), e-prescribing gateways, and other health information organizations that standardize transactions and make interchange of information easier
• Companies that destroy documents and computer drives, delete electronic equipment memory, and shred paper records as needed
• Patient safety or accreditation organizations that require access to records for investigations
• Third-party administrators and pharmacy benefit managers that are similar to utilization review firms
Without question, healthcare organizations that are not subject to HIPAA (in other words, international organizations) have third parties that serve as business partners/associates in relationships that are structured similarly to how they are structured in the United States. International business partner relationships tend to be a little more strategic in nature than a relationship with a vendor that supplies goods and products to the healthcare organization. International business partners extend or supplement healthcare services, and this integrated nature of the partnership is evident in organizations that support both US and Canadian firms (for example). They will attest to complying with US HIPAA (as a business associate) as well as complying with requirements under PIPEDA, Canada’s Personal Information Protection and Electronic Documents Act.
Regulators
The role of loc al and national governments is a prime example of a third party with a tremendous impact on healthcare organizations, and it’s not reserved for US healthcare. Although the US government, principally through Medicare and Medicaid, is the primary payer, it also heavily regulates the industry. As the governments of most other developed nations fund healthcare completely, government oversight there is more pervasive. In the United Kingdom, for instance, the National Health Service oversees healthcare through the Department of Health, the General Medical Council, and the Nursing and Midwifery Council. Figure 1-7 provides a snapshot of various government agencies’ oversight relative to healthcare.
Figure 1-7 Selected government oversight agencies relative to healthcare
State and Local Government
Most likely, your interaction with the government as a third party will be at the individual state or community level. As the saying goes, politics and healthcare are local, so many of the decisions and events that happen at a national level may not have as much of a direct impact on how you do your job as the local government decisions do. For instance, as a regulatory mechanism, state governments must approve of the building of new facilities or the offering of new services under a provision called “certificate of need.” In the United States, as of 2019, 37 states still require the measure, at least in part, to control capital expenditures and, theoretically, control healthcare costs.20 Their success is arguable, but for a healthcare organization interested in opening a cardio-thoracic surgery ward to increase revenue, for example, not obtaining a certificate of need can be a huge setback. To build the facilities or deliver the service without local government approval can result in fines and penalties, or can at least render the services not reimbursable.
Local governments can also influence healthcare organizations in very positive ways. One way is by partnering on things, such as a community health needs assessment. Such partnerships help both the local government health agencies and the healthcare organization determine a strategic plan for delivering healthcare to the various populations in the community. Local government can allocate where public resources should be expended. The healthcare organization can plan for prevention, intervention, and rehabilitation services targeted to what the community needs. The possible categories are almost infinite, but may include the following:
• At-risk teens initiative
• Community asthma prevention program
• Homeless health initiative
• Injury prevention program
• Poison control center
• Wellness fairs
Law Enforcement
Because you are working in information protection, law enforcement is another direct impact of local government. Although every privacy and security law has a provision for law enforcement access to patient information, it is not unfettered access. Your role may be to provide law enforcement personnel with the information they require based on organizational policies, laws, and their need to know. For instance, disclosure of protected information usually must be in response to written requests from law enforcement officials. It may be difficult to refuse a police officer standing at your desk asking for access to a record of a patient who came through the ER last night, but you may have to do just that.
Tort Law and Malpractice
In the United States, the government plays another role as a third party. This role is through the judiciary process and it is a very direct role in healthcare through tort law and malpractice. These are complex concepts that deserve much more attention than can be devoted to them in this text. However, an introduction to the terms and how they add to the highly regulated healthcare industry will help you understand more about how third parties impact healthcare provision. To start, tort law comprises civil (versus criminal) acts that provide patients a remedy against wrongful acts committed against them. We find tort actions in the healthcare industry due to the following:
• Negligence
• Intentional torts
• Infliction of mental distress
For the information privacy and security practitioner, intentional tort is something to note because it covers failure to properly secure information. Although a data breach may be caused by negligence and certainly may cause infliction of mental distress, tort law applies sometimes when failure to ensure confidentiality of patient information is related to intentional acts.
This leads us to malpractice, which is a special kind of tort law that is familiar to healthcare professionals. A malpractice lawsuit is based upon alleged negligence or carelessness by a healthcare provider. The charges can be civil or criminal depending on the nature of the offense. Under the law, malpractice is conduct that is considered wrong or unethical based on a standard of professionalism specific to the occupational responsibilities. The conduct is also considered intentional or negligent. Typically, the issue is not information security and does not involve a healthcare information security and privacy practitioner. However, malpractice can be applicable to cybersecurity issues. Cyberattacks and data breaches are sometimes considered impactful to direct patient care and safety. This impact is in addition to the traditional identity theft, data loss, and financial crimes caused by cybersecurity incidents. When a cyberattack results in a patient safety incident, it may be reasonable to consider negligence as a contributing factor in allowing the cyberattack to occur.
Nongovernment Regulators
When it is said that “healthcare is one of the most highly regulated industries,” this means more than just official government oversight. There are several significant examples of nongovernment regulatory third parties that shape healthcare organizations around the world. The focus on improving the safety and efficacy of patient care is one of the primary components that all accreditation organizations have in common. Through peer review and education, accreditation has proven effective in shaping healthcare organizations through third-party relationships.
Joint Commission The Joint Commission (formerly the Joint Commission on Accreditation of Healthcare Organizations and, previous to that, the Joint Commission on Accreditation of Hospitals) is an independent, not-for-profit organization located in the United States. During the last 25 years, the Joint Commission has begun to develop an international presence as well. For about 100 years, it has accredited and certified healthcare organizations against standards of practice. It currently provides this service for more than 20,000 healthcare organizations and programs in the United States. You may note that the Joint Commission International operates in Spain, particularly, and across Europe. It is, in fact, an extension of the US Joint Commission. Joint Commission accreditation is considered mandatory to demonstrate a healthcare organization’s commitment to quality and compliance with performance standards. In fact, in the United States, some reimbursement conditions depend on the organization having a current Joint Commission certification.
Accreditation Association for Ambulatory Health Care Recognizing the shift from inpatient services to outpatient or ambulatory care settings, another US nongovernment third party began looking at quality and safety issues in physician groups, outpatient clinics, and any other ambulatory patient care centers. The Accreditation Association for Ambulatory Health Care (AAAHC) develops standards with regard to patient safety, quality, value, and measurement of performance. Because its focus is in ambulatory healthcare, its surveys can be particularly efficient and meaningful, with better-equipped, peer-based accreditation processes.
Accreditation Canada In Canada, a similar organization, Accreditation Canada (formerly known as Canadian Council on Health Services Accreditation, or CCHSA) accredits more than 1000 client organizations ranging from regional health authorities, to hospitals and community-based programs and services. Like the Joint Commission and the AAAHC, the surveyors and auditors are not government employees, and the do not take direction from the government. Both the Joint Commission and Accreditation Canada use experienced professionals to conduct surveys and audits, including physicians, nurses, health executives and administrators, and medical technicians from the allied health professions.
European Union Regulators
The value of accreditation of healthcare organizations is debated in the European Union. Because healthcare is fully funded by the government, third-party accreditation of peers is not uniformly valued or respected. Many believe such efforts should be focused on mandatory compliance verified through government inspection and auditing. Nonetheless, third-party organizations performing accreditation have grown rapidly during the last 30 years in Europe.
To begin to look objectively at the issues, the World Health Organization (WHO) conducted one of the first international studies in 2000. This and subsequent studies have focused more on evidence of accreditation’s impact on healthcare organizations’ patient care, safety, and quality improvement efforts. Currently, there are eighteen national organizations active in Europe. The trend is in more programs and more participating healthcare organizations and more surveys of healthcare organizations.
Other Third-Party Relationships
In addition to the impacts from external relationships with vendors, business partners, and regulators, other emerging relationships impact the healthcare delivery system. One relationship you should understand is the growing collaboration among (sometimes competing) healthcare delivery systems and security and privacy information sharing groups.
Information Sharing and Analysis Centers
Information Sharing and Analysis Centers (ISACs) are trusted entities that help organizations in the United States protect their organizations and personnel from cyber and physical security threats. The concept of ISACs were specified in Presidential Decision Directive-63 (PDD-63), signed May 22, 1998. The Directive also introduced and endorsed the need for ISACs to partner with government.
Services provided by the typically nonprofit ISACs include collection, analysis, and sharing of actionable threat information. Figure 1-8 shows some of the sources of intelligence that ISACs provide. In the figure, notice the sources of threat intelligence, which include open source and proprietary source intelligence. These sources can contribute to a threat intelligence platform hosted by the sources themselves or by another organization collecting and analyzing the information sent using Structured Threat Information Expression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII) language standards. The threat intelligence platform provides updates to the security tools used by healthcare organizations, many of which are effective for detection, response, and recovery.

Figure 1-8 Sample threat intelligence service from ISAC
A single healthcare organization by itself probably could not provide enough resources to gather and analyze the vast amounts of threat intelligence that an ISAC can provide. In some cases, the ISACs establish the threat levels for their sectors based on the threat warning and incident reporting capabilities they offer.
ISACs are in the business to facilitate information, not sell it. To maintain situational awareness across the various critical infrastructure sectors, ISACs collaborate and share threat and mitigation information with one another and other partners through the National Council of ISACs.
Healthcare Information Sharing and Analysis Center (H-ISAC) The healthcare sector has a devoted ISAC in the H-ISAC, a trusted community of critical infrastructure owners and operators within the health and public health sector. The H-ISAC offers threat intelligence, reporting capabilities, and information sharing, but it devotes extra emphasis to threats and adversary actions that target healthcare and public health. The H-ISAC also expands the surveillance capabilities for the healthcare sector by its integration and collaboration with the entire National Council of ISACs.
Medical Device Innovation, Safety, and Security Consortium (MDISS)
MDISS is a nonprofit public health and patient safety organization focused on medical device cybersecurity. The group takes a collaborative approach, where a threat faced by one organization or medical device is understood to be a threat faced by all. Therefore, the group was established to foster more communication and sharing of practices that will benefit the entire healthcare delivery system. MDISS aims to improve the safety and security of medical devices by assisting their membership with guidance on technology solutions as well as policy and procedures. The organization embraces government–private sector partnerships to leverage industry expertise in device vulnerabilities and government counsel in regulatory requirements. The intention of the group is to be focused on patient safety, approaching medical device security from an epidemiological model, which means looking at the problems from an incident, spread, and control perspective like a disease. This lens is familiar to healthcare public health interventions and is thought to help improve medical device security. This group works together with other collaborative groups such as the H-ISAC, the Healthcare Information and Management Systems Society (HIMSS), and the FDA.
Administering Third Parties
With all of these external forces and third-party relationships shaping the healthcare organization, administering them is a fundamental element in reducing information risk (of unauthorized disclosure). You know that the BAA, which is unique to the United States, is one formal (written) tool that helps reduce information risk. You also need to know about other agreements and documents that are used in the United States and internationally. All are prenegotiated and defined common understandings necessary to protect the confidentiality, integrity, or availability of patient information. A few of note are the service level agreement, the data sharing agreement, and the legal contract.
Service Level Agreements
The service level agreement (SLA) is a document that outlines the support or products to be provided by the third-party organization and any processes against which the healthcare organization can measure success. Consider network uptime, for example. If the third party agrees to keep the network connected and operating for a particular frequency, that becomes the expectation of the healthcare organization. The measurement can be the frequency—such as 99.999 percent of a full 24-hour day, seven days a week. If the network does not perform to that standard, the healthcare organization may suffer consequences. SLAs also contain remediation steps when things go wrong, including steps for complaint escalation, financial penalties, severance of the agreement, and so on.
Data Sharing Agreements
A data sharing agreement (or data use agreement) is a similarly used document that describes access to and expectations for a third party’s use of an organization’s patient information. These documents are similar in function to and may be used with a BAA in the United States. It will clearly indicate and limit the specific data elements exchanged, the period of time the data sharing will occur, the systems the third party will access, how the entity will use the data, and provisions for the eventual disposal of the information. These agreements can cover additional parameters, but the main element of the agreement is to protect the healthcare organization by spelling out exactly how the information will or will not be disclosed. This is important because, ultimately, the healthcare organization is responsible for safeguarding the information. In a data sharing agreement, it is imperative to ensure that there is a bona fide and legal “need to know” for the third party.
Chain of Trust Agreements
These agreements are not unique to healthcare. In the United States, this function can be satisfied within the BAA. A chain of trust agreement provides an administrative control via a contract between sender and receiver healthcare organizations for secure information exchange. It establishes the technical controls for information exchange and obliges each party to adhere to them. In this way, both parties agree to ensure the confidentiality and integrity of PHI. If the information exchange involves multiple parties, multiple chain of trust agreements are required.
Legal Contracts
Finally, the most official and binding of third-party administrative tools is the legal contract. In many ways, the SLA and the data sharing agreement can evolve into a formal contract. Generally speaking, there are four main elements of a contract:
• It must be between two or more parties.
• All parties must be competent to consent.
• The agreement must be something of value.
• The agreement must be lawful.
Where formal contracts differ from an SLA and a data sharing agreement is in the complexity and content. SLAs and data sharing agreements tend to be specifically focused on a service or product, with terms and conditions related to measurements and quality or specific acts and tasks. However, all of these documents are used to set clear expectations, avoid costly legal actions, and provide safe handling of patient information. The formal contract would include more detail about responsibilities, resources, assumptions, and limits of liabilities over the life of the contract. Often the SLA and data sharing agreement serves as an attachment to a formal, long-term contract with a third party (which may provide multiple services).
Understand Foundational Health Data Management
Like any industry that relies on information, healthcare organizations must adhere to proper data management principles. To do this, they should organize their data management around concepts that are considered best practices. Information consisting of data can comprise many different forms in every part of the healthcare organization, including written instructions, treatment plans, images, audio files, video clips, paper documents, and digital files. Successful organizations work to transform the information into a strategic asset, organizing and leveraging it into a resource as valuable as any clinical technology or financial asset it has.
The foundation of a strong healthcare data management program includes four major areas:
• Data profiling This discovery process leads into the data quality process by determining where data quality rules and requirements should focus. Steps in this activity include gathering frequency and basic statistic reports, relationships in tables, phrase and element analysis, and business rules discovery.
• Data quality The objective of this process is to standardize, validate, and verify the data. Adequate checks and oversight must be in place to ensure that data is relevant, accurate, timely, and accessible, to name a few data quality characteristics. The specific techniques of parsing, transformation, verification, and validation help to enable normalization of the data for data integration.
• Data integration Multiple sources of data are combined to obtain an organizational data repository or collection of source data. This effort involves removing duplicate data and consolidating sources using powerful locating and matching technology.
• Data augmentation Once the data reaches this step, the process concludes with enhancing and enriching the data with new data or missing elements. For example, adding demographic, geographic, or credit information can be useful. In this stage, data management algorithms and methods are used for clinical and business data analytics.
In addition to the foundational concepts, your program will need to have policies and procedures that accomplish the following:
• Governance Leadership must be applied to strategically align processes and technology, with a uniform view across the organization. Because data governance is not just an IT issue, a data governance committee must include senior-level executives and specialists from other business and clinical areas (along with IT representatives), who provide vision and authority to the data governance function.
• Stewardship Ownership and accountability are important in managing data. Data is a valuable asset, and all personnel who have and use data must understand their individual roles in ensuring prioritization of data, maintaining trust in data, and reporting and tracking data issues to resolution.
• Architecture Related to the location of data and how it flows through the organization, inventory and documentation make up the first step. Then the organization must identify the stakeholders and the relevant information lifecycle. Additionally, data architecture involves defining the organization’s metadata, or its data about data. An element of metadata could be “patient record” and could include multiple elements such as date of birth, appointment date, prescriptions, and so on. Because this information may be used by multiple departments or even across different organizations, having metadata called patient record number that is uniformly defined can streamline the myriad processes that rely on these associated data elements.
• Standards With all the business processes and clinical workflows that operate within healthcare, the effort to establish and maintain data with common understanding and meaning is important (and one of the reasons the coding of medical practices with ICD-10, for example, is so essential). Data standards are founded using a combination of regulations, customs, and user acceptance.
• Security Assuring confidentiality, integrity, and availability of data, both in paper form and digital, is a central concern of any data management program. Within healthcare, a lack of protection of data from unauthorized (accidental or intentional) modification, destruction, or disclosure can be a violation of law, a matter of risk to patient safety, or both.
Managing Information Flow and Lifecycle in Healthcare Environments
An information flow in healthcare is a pathway that any identifiable piece of information, or of information type that is pertinent in the healthcare domain, follows from sender to recipient and from input to output. Types of information can range from entire databases, to images and sound recordings, to elementary variables related to a patient care event. During the information flow, information is examined, created, updated, and deleted as needed. As illustrated in Figure 1-9, information moves across the continuum of care from patient to provider and then to nonprovider entities in the care path. Healthcare information protection professionals must successfully manage and protect this health information as it moves internally within the organization and externally.
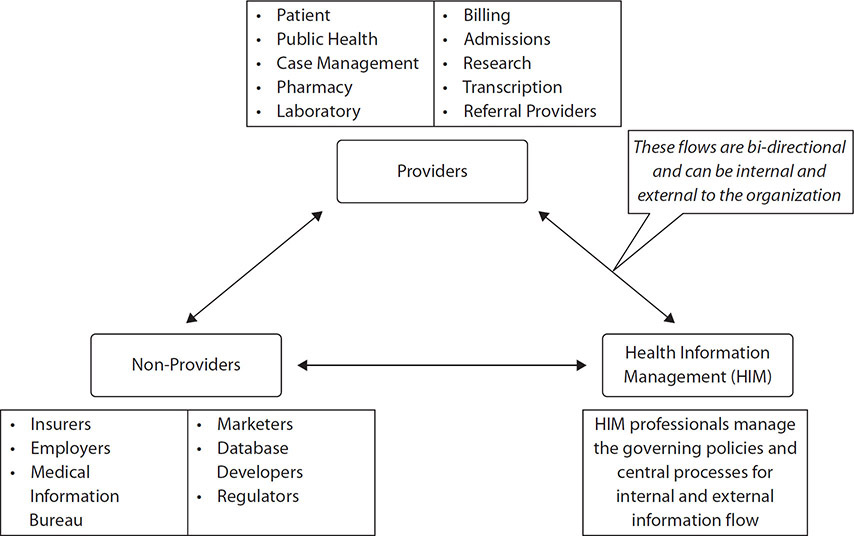
Figure 1-9 Overview of healthcare information flow
Data sharing in healthcare is an essential component of patient care, research, and quality initiatives. Within the organization, providers consider it an imperative to be able to easily access things required for patient care, such as medication lists and laboratory results, precisely when they need it. Even after care is provided, sharing information is important in settings such as peer record review, where procedures are reviewed and measured against organizational and clinical standards. The intent is to discuss best practices, share common experiences, and, in the end, maximize scarce resources by reducing duplication and ineffective processes.
Many healthcare organizations devote a tremendous amount of research and academic training as part of the care they provide. Commonly, these are either purely research providers or teaching hospitals. Enabling these organizations to exchange their findings or even collaborate on research in real time advances medical care. Results become more useful with combining larger data sets on drug responses. Adding genomic data on patients to the clinical trials could really begin to predict exactly what therapies are helpful at an individual level. Data sharing reduces trial-and-error medicine that is costly and may be the source of patient safety risks.
One study has shown that sharing data between provider organizations has saved 92,000 lives and $9.1 billion over four-and-a-half years.21 Much more impressive numbers result from extrapolating data-sharing benefits across an entire nationwide healthcare system. Improving patient outcomes, streamlining processes, and reducing patient safety risks are all benefits of data sharing.
Enabling one healthcare organization to communicate with others is a challenge, even though healthcare language is based on accepted clinical terminology, standardized code sets, and the same mission of diagnosis and treatment. In addition, the ability to interconnect with other third parties can create administrative and management problems.
For instance, each healthcare organization that uses an information system to automate workflow, an EHR, or a patient administration system probably purchases that system from a commercial manufacturer. Some government healthcare organizations’ information systems may be government-developed. Recently, many government healthcare organizations have adopted commercial off-the-shelf EHRs, though the government EHRs may still require interconnection to government-developed business or clinical systems used only within government healthcare organizations. In any case, based on the company that develops the EHR system, interoperability is often difficult. The outcome is that valuable data locked is locked away, unless the systems are from the same manufacturer. As patients typically move from one healthcare organization to another, based on referrals for advanced care, for example, or healthcare organizations desire to submit bills to payers, healthcare organizations must be able to send and receive data no matter what proprietary system they (or their counterparts) use. Throughout the remainder of this chapter, you will be introduced to emerging standards, taxonomies, and interoperability efforts for healthcare information that are intended to improve the secure transfer and use of information between organizations and information systems.
What should be clear at this point is that healthcare information must move along the clinical workflow of patient care, and if the information is not available or reliable, patient care suffers and patient safety may be at risk. Additionally, information has a lifecycle that must be managed to ensure that confidentiality, integrity, and availability are maintained. The goals of confidentiality, integrity, and availability must be aligned with information sharing for patient care. Properly understanding information flow and information lifecycle management (ILM) is essential to reduce costs as well.
The ILM cycle, depicted in Figure 1-10, involves the following phases:

Figure 1-10 Information records management life cycle
1. Create The information must be available, trusted, reliable, and concise, no matter the source of the information—the patient, a provider, or any number of different medical devices and diagnostic tools.
2. Store Records must be stored and protected while in the possession of the provider. The value of the information (classification) will determine how long an organization will keep the information. Policies establish the length of time the records are useful and after which outdated records are discarded. The records should be maintained with the same level of availability to providers and with the same level of integrity as long as the information is useful.
3. Use Information has to be used in a manner consistent with the reasons it was collected and never for a provider’s personal gain. For example, data used for treatment typically cannot be used for published research if the patient did not consent to such use.
4. Share Probably the most important feature of use within the information life cycle is protecting the information during transfer. Healthcare organizations use data; that is a given. As the data moves throughout the organization, between organizations, and between providers and payers, safeguards are needed to assure confidentiality, integrity, and availability.
5. Dispose The final step in the process is the most vulnerable. Too many times data is lost or disclosed in an unauthorized manner when the organization no longer deems the information useful. During the transfer of the information for disposal, a data leak or breach occurs because safeguards are relaxed. Until data is destroyed, it needs to be protected.
A key part of any information security strategy is disposing of data once it’s no longer needed. Failure to dispose of data properly can lead to serious breaches of data protection and privacy policies, compliance problems, and added costs. Paper records as well as digital information can be lost easily prior to destruction. The essential message to healthcare information security and privacy professionals is this: Data breaches happen, and they can happen to your organization. And they are most likely to happen when you let your guard down at the disposal step in the ILM.
Three common disposal methods are used with paper or digital information:
• Purging This is the indisputable erasing of data from the storage device in such a way that the data may never be recovered. It can be accomplished by overwrite, block erase, and cryptographic erasure, using dedicated, standardized device sanitize commands.
• Cleansing or clearing The organization can use software or hardware products to overwrite storage space on the media with nonsensitive data, using the standard read and write commands for the device.
• Destruction The organization can purge media before submitting it for destruction. There are numerous ways of physically destroying media, including the drive shredders, pulverization, incineration, and acid.
Specific techniques used to dispose of information properly include the following:
• Zeroing This process erases data on the disk and overwrites it with all zeros.
• Degaussing In this process, the magnetic media is erased and returned to its initial blank state through the use of high-powered electromagnets.
• Sanitizing This process purges all identifying data elements from the record or database through data element removal, de-identification, masking, or anonymization.
• Overwriting Data is overwritten with random data until the current data is no longer retrievable.
It is common to use several of these methods to destroy data, depending on the value of the data and the media in use. In some cases, the process involves performing the action a number of times to ensure that the data cannot be recovered.
Data Lifecycle Management (DLM)
DLM concept is different from ILM, though it is similar to ILM as an approach to manage data throughout its lifecycle. DLM is concerned with information at the file level, which is more abstract in nature and less concerned with the use of the data within the file. ILM would deal with the specific information within that file, such as a patient’s height, weight, age, and test results. In other words, DLM deals with entire files of data, while ILM deals with the details within the files.
DLM has sharpened the focus of healthcare organizations and underscored the need for professionals dedicated to managing data and information assets. Proper management includes protection of the assets, but it also incorporates using the data and information to benefit the healthcare delivery system. Health informatics is an activity that has emerged to help healthcare organizations apply a thorough and effective approach to data lifecycle management. Health informatics is information engineering applied to the field of healthcare and deals with the tools and procedures needed for optimizing healthcare information.
Health Data Characterization
Data sharing and interchange typically must be intentional. Based on law, contractual agreements, and technical compatibility, interoperability has to be a premeditated and determined effort. Beyond the concepts of data standards and the languages of healthcare, a couple other topics are important to consider—namely, data classification and data taxonomy. Even if data is technically compatible to exchange between organizations, not all data is equal, and individual organizational policies and procedures must be considered. Attending to health data characterization through proper data classification and data taxonomy makes information exchange feasible. To that end, data analytics is another stakeholder of accurate health data characterization, which relies on correct data classification and taxonomy methods.
Data Classification
ILM requires that a healthcare organization establish a classification system based on the value of the information. It is important to note that this type of data classification differs from that of computer programming, which is also called classification, but relates more to labeling the data to differentiate it into classes and sets. In the ILM context, data classification is required to apply a value relative to the sensitivity and criticality of the information, as defined by the organization. This value will determine what level of information protection controls will be applied to information collected, stored, used, shared, and eventually disposed of.
Your organization must determine what categories to use to classify data. There is no prescribed naming convention and there is no specific number of classification categories you can use. Your choices may be based on regulatory requirements and organizational governance. However, a common structure used by many organizations has four levels of sensitivity and one level of open access:
• Confidential If data in this top sensitivity level is lost, stolen, or compromised in some form or fashion, it is likely to result in significant, long-term harm to the institution or individuals to whom the data refers or belongs.
• Sensitive This level has relative value less than confidential, but it is still important to protect. Losing the data will increase risk to the organization, even if it’s just reputational damage. Strategy planning documents or inter-organizational correspondence can be considered sensitive.
• Restricted This may also be termed “private” and includes material that would cause “undesirable effects” if publicly available but may not raise operational risk. Employee retention statistics or salary ranges are often classified as restricted or private.
• Proprietary This is the least restrictive classification but mandates internal company use only and should be based on proprietary use for authorized personnel only. Disclosure outside the company may impact competitive advantage. Many organizational briefings or meeting notes can be classified at this level.
• Public The data is available outside the organization, and the unauthorized disclosure, alteration, or destruction of this classification of data would result in little or no risk to the organization.
Data Taxonomy
Data taxonomy relates to categorizing data into a standardized format with common meaning. Data taxonomy leads to simplicity and facilitates data sharing. As an example, the term “psychologist” can indicate a specialized healthcare provider who is independent of organization and distinct from other provider professions, such as social worker or counselor. Such distinctions help to facilitate appropriate data analysis and information sharing. Having a data taxonomy introduces convenience and reduces wasted efforts in trying to establish common definitions and context. Data taxonomy has also proven effective in streamlining payment and reimbursement activities.
Healthcare Provider Taxonomy Code Set and National Provider Identifier The Healthcare Provider Taxonomy Code Set is contained in HIPAA as a standard. The taxonomy is arranged in a hierarchy of specific codes with descriptions and definitions. Using the taxonomy, you can identify healthcare providers by their type, classification, and provider specialty. The code set comprises two sections—Individuals and Groups of Individuals, and Non-Individuals—and is updated twice a year. Each provider’s 10-digit code is structured into three distinct levels: provider type, classification, and area of specialization.
As of 1996, HIPAA requires the adoption of standard unique numbers that identify healthcare providers, as established by the NPI (National Provider Identifier) Final Rule, issued in January 2004. The NPI number is required many health insurance claims and enrollment applications. One of the provisions of the ACA requires all providers of medical or other items or services and suppliers that qualify for an NPI to include their NPI number on all applications to enroll in the Medicare and Medicaid programs and on all claims for payment submitted under these programs.
EDI X12 Code Lists Electronic Data Interchange (EDI) X12 is an electronic data format that is governed by standards released by the Accredited Standards Committee (ASC) X12. It is used to exchange specific data between two or more trading partners. A “trading partner” refers to a third-party organization, group of organizations, or some other entity. A trading partner in the US healthcare context is most often a business associate. Some large organizations that act as trading partners impose strict rules and requirements for EDI transactions, which may be in the form of specific data format requirements for some elements, requirements to contain specific segments (segments that are not mandatory in EDI X12 standard being made mandatory), and others. HIPAA recognizes the trading partner and outlines the need to provide requirements in a separate companion guide document. Companion guides are used to inform the user on important interactions with the application, such as access and understanding how to transmit requests and understand responses. It is essential that these documents be followed to the letter when healthcare organizations implement EDI systems.
Following are key EDI transactions within HIPAA:
• 837 Medical claims with subtypes for Professional, Institutional, and Dental varieties
• 820 Payroll Deducted and Other Group Premium Payment for Insurance Products
• 834 Benefits enrollment and maintenance
• 835 Electronic remittances
• 270/271 Eligibility inquiry and response
• 276/277 Claim status inquiry and response
• 278 Health Services Review request and reply
Data Analytics
Possibly the most compelling argument for proper data characterization is data analytics. With standard classification and taxonomy, comparative analysis on larger and larger volumes of data becomes a reality at a reasonable cost. Previously, data analytics would be constrained to individual organizations because of incompatibility of policies, procedures, and information systems. At best, data analytics were applicable only to one particular organization. Any comparisons most likely suffered from data latency, because results could not be shared in real time. Today, however, alliances and data analytic firms are able to aggregate and process terabytes and petabytes of data from dozens of healthcare organizations almost instantly and simultaneously to provide outcome measures and lower costs over time.
The evolution of data analytics has information systems able to process more data faster and more economically. As organizational data becomes more compatible and standardized, big data has exploded in many industries, including healthcare. Figure 1-11 shows some of the major sources of data that are available to healthcare organizations.

Figure 1-11 Big data sources in healthcare
Healthcare organizations, like other organizations that use data analytics, can be described by measuring against three major levels of capabilities, which explain how organizations use data and analytics to create competitive advantage and become top performers:
• Aspirational A beginning level, focusing on efficiency or simply trying to justify an action. At this point the organization may not have a clear view of how to get value from analytics, and the required level of executive sponsorship may not be apparent. The organization may also have immature or incomplete information retention processes, which would affect the ability of the analytics process to gather, aggregate, and manipulate the information. Decisions are based more on intuition rather than proper data and analysis.
• Experienced At this level, more strategy and business initiatives are enabled by data analytics. The principle benefit is realized in growing revenue through data analysis. There is still a lack of personnel with technical skills to fully leverage the data. These organizations also do not have mature data governance policies, including clear ownership. At this point, the organization can get and use the data, but is not able to reliably and securely share it with other organizations.
• Transformed At this level of proficiency, analytics are used to set a course of action as compared to retrospectively defending an outcome for an organization. And it is at this level that data analytics can provide an advantage over competition. But there still may be problems in exploiting the benefits of the data because the organization can have limited resources or too many priorities to commit to other than more data analytics growth. These organizations continue to mature as they ensure people, processes, and technologies are aligned to maximize data analytics and differentiate the organization from others.
Healthcare as a worldwide industry has a common dilemma: the pressure to reduce costs and improve outcomes. Big data offers many positive impacts fort healthcare, such as facilitating a reduction in fraud, waste, and abuse. From a clinical perspective, big data initiatives have helped reduce medication errors and improve quality healthcare outcomes. The healthcare industry, however, has been slower to adopt the power of data analytics than other industries, such as retail and manufacturing. Stricter regulatory pressures in healthcare may lead to a perception that data analytics would be less effective and possibly illegal in some scenarios.
Healthcare organizations, particularly those subject to HIPAA, must make several considerations with regard to data analytics:
• Third parties that provide or share data analytics technologies or capabilities with healthcare organizations are subject to HIPAA according to clarifications provided by the Omnibus Rule. Before the clarification, healthcare industries were often hesitant to enter into data analytics arrangements with third parties.
• HIPAA prohibits selling of PHI. With large data stores moving from the healthcare organization to third-party organizations that provide analytics, services paid for or reimbursed may be considered marketing or selling of data.
• Allowances are made for compound authorizations in research. It was previously illegal to ask research participants to authorize data collection and add on an authorization to keep the data for future research use after the original study. HIPAA, as amended by the Health Information Technology for Economic and Clinical Health (HITECH) Act, allows for compound authorizations.
• Data de-identification methods such as data masking or anonymization can be used to maintain the usefulness of the data for analytics, and they reduce the risk of unauthorized disclosure of large sets of data.
Data Interoperability and Exchange
Data taxonomy and other standardization methods enable data interoperability and exchange. Interoperability in healthcare refers to the ability of different information systems, devices, or applications to connect in a coordinated manner, within and across organizational boundaries, to access and use data cooperatively among stakeholders, with the intended goal of optimizing health for individuals and populations.23
The ways in which health data can be exchanged is governed by standards and enabled by architectures with an objective to effectively and securely transfer the correct information to authorized users when it is needed. Significant numbers of connections and integrations in healthcare settings and information systems depend on an interoperable exchange of data. Beneath the requirement for interconnection and exchange, the importance of usability and reliability of the information is a concern you will address.
Your organization may participate in several types of data exchanges. These components occur with varying degrees of interoperability and may occur simultaneously within a single healthcare setting:
• Foundational interoperability There are baseline requirements that must be met for systems to establish basic interconnectivity. These must be in place before any consideration can be made for determining requirements to format what is sent and understand what is received.
• Structural interoperability Defines the syntax, structure, and format of healthcare data exchange (the message format standards) that is required for secure transfer of data between systems, maintaining data integrity. It also ensures that there is no alteration or degradation of the data contents that would change the purpose and meaning.
• Semantic interoperability This capability is needed to facilitate the exchange of information and to make sense of it so the information is usable. Semantic interoperability relies on common taxonomies and vocabulary to best enable the receiving system to interpret data for the end-user consumption. This high-level interchange of patient information across different healthcare information technology systems is useful in improving healthcare treatment, payment, and operations.
• Organizational interoperability Includes technical, policy, social, and organizational elements that enable secure transfer and use of healthcare information by end users located in different organizations. Information transfer must also be on time and unimpeded to achieve organizational interoperability. Beyond the technical specifications interoperability requires, organizational interoperability also elevates the need for underlying ILM and DLM workflows to be aligned and optimized for the best patient care outcomes and provider satisfaction across multiple organizations.
The concept of “meaningful use” in EHRs arose from the implementation of the HITECH Act, which was included in the American Recovery and Reinvestment Act (ARRA) of 2009 that amended HIPAA. The act provided for incentive payments to healthcare organizations that did more than just adopt an EHR. “Meaningful use” means that providers implemented an EHR certified by the Office of the National Coordinator for Health Information Technology (ONC) that demonstrates technological capability, functionality, and security requirements of the US Secretary of Health and Human Services to achieve improvements to patient care. This incentive ended in 2015. After that time, provider organizations that had not implemented an EHR and demonstrated meaningful use could expect to incur penalties from the federal government. Specifically, eligible providers who did not demonstrate meaningful use successfully for an EHR during a specific time period associated with a reimbursement request from CMS will receive a reduced Medicare payment, such as a 3 percent reduction in reimbursement.
The meaningful use program evolved over time to encourage interoperability as well. CMS provides incentives to encourage eligible clinicians to use health IT, most notably certified EHR technology. CMS believes that EHR technology enables clinicians to submit information electronically in a format CMS can process efficiently and effectively. Meaningful use has been replaced by the Medicare EHR Incentive Program. In 2015, the Medicare Access and CHIP Reauthorization Act (MACRA) was passed, and the Medicare EHR Incentive Program became one of the four components of the new Merit-Based Incentive Payment System (MIPS).
Health Level 7 (HL7)
HL7 is a nonprofit, ANSI accredited, international standards developing organization that provides a framework and standards dealing with the exchange, integration, sharing, and retrieval of EHI. The organization aligns its work and standards through ISO. HL7 includes several families of interconnection standards, including Fast Health Interoperability Resource (FHIR); Clinical Document Architecture (CDA); Consolidated CDA (C-CDA); ERH/PHR System Functional Models, Version 2, Version 3; Arden Syntax; and the Reference Information Model (RIM). This organization consists of healthcare information technology professionals, healthcare and health administration professionals, and members of multiple government agencies (CDC, ONC, FDA, and so on). By implementing interoperability standards, healthcare organizations can better deliver patient care and convey clinically significant information that typically would be unavailable because of system incompatibilities.
To help EHRs interconnect, the HL7 has published the EHR System Functional Model, which defines EHRs in terms of important functionality. Using the clinical workflow expected of various patient care settings, the group defined functional profiles with standard descriptions, which are applicable globally. HL7 leads interoperability effort so that providers and manufacturers develop standardized EHR functionality instead of trying to cobble them together after-market.
Integrating the Healthcare Enterprise (IHE)
Related to HL7, IHE is an international organization that contributes to the use of standards and protocols to improve interoperability. It promotes the coordinated use of standards developed by HL7 and many other standards development organizations by establishing clinical workflow profiles (such as for cardiology or dental) of existing interoperability standards involving coordinated communication. This enables organizations to purchase systems with tested interoperability capabilities.
IHE creates standards, such as the EHR function standards, and focuses on how organizations implement them. Systems that conform to IHE interoperability specifications are typically easier to implement, easier to interoperate with, and more effectively support provider information use. For example, organizations purchasing any EHR or clinical information system can refer to applicable IHE documentation, require compliance from vendors, and streamline system implementation and interoperability. Vendors and health systems can claim conformance to IHE specifications following rigorous testing with exchange partners for a given interoperability profile.
IHE publishes standard implementation specifications (profiles) across several domains:
• IHE Cardiology (CARD)
• IHE Dental (DENT)
• IHE Endoscopy (ENDO)
• IHE Eye Care (EYECARE)
• IHE IT Infrastructure (ITI)
• IHE Pathology and Laboratory Medicine (PaLM)
• Merger of IHE Anatomic Pathology and IHE Laboratory domains
• IHE Patient Care Coordination (PCC)
• IHE Patient Care Device (PCD)
• IHE Pharmacy (PHARM)
• IHE Quality, Research and Public Health (QRPH)
• IHE Radiation Oncology (RO)
• IHE Radiology (RAD)
• IHE Surgery
Digital Imaging and Communications in Medicine (DICOM)
When it comes to information system interoperability, the healthcare industry’s reliance on digital images captured from numerous devices, in addition to numerical results and words, creates incredible complexity. Digital diagnostic imaging devices, called modalities (X-ray, ultrasound, computed tomography, and so on), need a standard method for transferring images and information between medical devices and for use in various vendors’ EHRs. Each imaging device initially creates the image in a proprietary format. The American College of Radiology (ACR) and the National Electrical Manufacturers Association (NEMA) formed a joint committee in 1983 to develop a standard known today as DICOM. This standard is found in ISO 12052:2017 within the field of health informatics.
DICOM, using ISO 12052:2017, promotes interoperability of medical imaging equipment by specifying the protocols required for transferring digital images across a network. The guidance does not, however, prescribe testing protocols for compliance and does not guarantee interoperability.
Devices used to capture and transfer images can be manufactured by any vendor that complies with the DICOM standard. Images can be stored in databases that can be analyzed using data analysis tools. Leveraging DICOM has resulted in advances in medical imaging and has led to picture archiving and communication systems (PACS), which make up some of the most complex, networked medical devices in healthcare. These can consist of dozens of modalities, set up in a local area networked (LAN) configuration connected to several different types of servers for image processing, demographic patient data integration with the images, and file transfer to end-user viewing stations. PACS is also accessible via the Web when a dedicated web server is added to the architecture. Many healthcare organizations must accommodate a PACS as a LAN within their LAN because its footprint is large. DICOM is an evolving standard that enables the PACS to communicate within its own component and to interface with other systems in the same organization and those outside the organization.
Legal Medical Record
Back when medical records were made up of paper charts, documents, film images, and files, a legal medical record included the entire content related to an individual patient. That began to change with the introduction of paper-to-digital records conversion. Patients have also become more involved with the contents of the records related to regulatory changes, legal issues in healthcare, and patient education available on the Internet. The impact of the definition of a medical record is in what is disclosed to law enforcement and for legal proceedings. Only that which constitutes a legal medical record is to be disclosed. The contents of a legal medical record should (at least) do the following:
• Support patient care decisions Legal medical records can reduce costs, improve care, and increase efficiency.
• Full accounting and documentation of the care provided It is the responsibility of the creator of the record to keep the record in an unaltered form and authenticated by that individual.
• Serve as evidence in legal proceedings about such care A healthcare organization must maintain a legal medical record.
Not all health information is digital, and much remains in paper format. Some of the paper information constitute valid elements of a legal medical record. When a healthcare organization defines its legal medical records as having both paper and digital information, the records are called hybrid legal medical records. Along with the location of the various databases where the electronic information resides, a medical record must have references to the sources of the paper-based information it includes.
The security and privacy implications of medical records are significant. The first challenge in defining a legal medical record is that no standard exists.24 Each organization is required to define the contents for itself. Some components are more obvious and universal than others. For instance, information related to medication orders, pathology reports, and emergency department records would certainly be part of any legal medical record. Administrative data and documents, however, are usually excluded. Other excluded items could be authorization forms for the release of information, incident or patient safety reports, and psychotherapy notes. To identify which documents can be excluded, healthcare organizations typically call these items working documents.
Chapter Review
Healthcare is a dynamic, complex, and highly regulated industry. The computer networks and interconnections are part of the US national critical infrastructure, but the importance and reliance on a safe and secure healthcare delivery system is important worldwide.
This chapter builds a foundation of understanding the organizations in which an information security and privacy professional may work. The start of the chapter includes a general overview and discussion of the various healthcare organizations that make up the industry. The healthcare workforce is diverse and ranges from manual labor trades to highly educated professions. At the center of the healthcare system is the patient. The types of organizations that support the healthcare of the patient are provider, payer, and healthcare clearinghouse organizations. Many external entities also support the healthcare industry. In this chapter, we introduced key stakeholders, such as the surrounding community, that provide sources of labor as well as support businesses not related to direct patient care. Jobs and the local economy may depend on these stakeholders’ partnership with the healthcare organization. The impact of information sharing with third parties outside the healthcare organizations is relevant to information protection considerations. For example, vendors, suppliers, and regulators are forces that have impact. Where third parties handle sensitive information on behalf of the healthcare organization, the relationship may introduce risk to each of the organizations that must be addressed.
The healthcare system requires a financial mechanism to allocate resources. In the United States, the financial processes are relatively complex with coding, billing, and payment processing components. It is significant to understand how the US employer-based and private insurance models work. In most other countries, the government (single-payer) model is the predominant model. These differences may present unique challenges for you as a healthcare information privacy and security professional.
To facilitate the general financing models as well as support the delivery of efficient quality of care, the healthcare industry relies on an extensive coding taxonomy of which information privacy and security professionals need to be aware. The chapter continues with a presentation of the categories of foundational health data management principles. The end product of coding, health data management and delivery of patient care, is a legal medical record that patients, providers, and regulators can depend on to document and communicate the overall events and experiences that are healthcare. Understanding these topics help shape your knowledge and use of information through its lifecycle and help you properly manage products central to healthcare. Whether you work in healthcare already or are just now entering the healthcare workforce to provide information protection services, you will make your work easier if you understand the important points of this chapter.
Very few healthcare organizations can exist independently of third parties that are imperative to business and clinical operations. Many of the external entities that support healthcare organizations are considered vendors, business partners, or suppliers. In the United States, a special affiliation is in place based on prevailing legal guidance, HIPAA. Third parties that handle protected health information on behalf of healthcare organizations are called business associates, and they are also subject to HIPAA. Third parties can also be external stakeholders, such as government agencies, legal authorities, and accrediting organizations. Each of these entities plays a role in ensuring that the healthcare organization operates within established guidelines. In this chapter, we also covered the various information-sharing third parties and healthcare organizations. As information privacy and security professionals, you will need to understand how to share information securely to avoid cybersecurity threats while not exposing your organization to additional risk.
This chapter concludes with an overview of foundational health data management concepts. The understanding of data lifecycle management and classification levels of data are not unique to healthcare, but these and other privacy and security concepts concerning data must be tailored to the healthcare environment to avoid degrading clinical operations or risking patient safety. As the digitization of healthcare information increases, the need for and use of initiatives such as data analytics are introducing challenges for continued protection of large volumes of data that are shared in many new ways with other healthcare organizations and third parties. The standards and formats for data interoperability in clinical operations are important to identify and secure in this emerging data flow, such as DICOM, HL7, IHE, and X.12, to increase efficiency. The end result of the interoperability and data exchange in healthcare is the legal medical record. This central artifact is important to you as an information protection professional because the organization relies so heavily on its contents for healthcare decisions as well as the record’s status as a legal document to be used in regulatory matters and litigation.
Questions
1. Which of these types of nurses requires the highest level of formal education?
A. Licensed practical nurses
B. Registered nurses
C. Nurses’ aides
D. Independent duty nurses
2. If a payer is a public source, which of these would be the source of funds?
A. Employer group
B. Health maintenance organization
C. Public health agency
D. Government entity
3. An inpatient is defined as an individual who
A. Receives rehabilitation for hip replacement Monday through Thursday, 5 PM to 6 PM
B. Checks into the emergency room and is admitted overnight for more than 24 hours
C. Undergoes knee surgery and is transported to assisted-living residence
D. Is admitted to a sleep study overnight from 11 PM to 8 AM
4. Who is the primary payer in most developed countries for healthcare?
A. Self-pay
B. Employers
C. Government
D. Military
5. “Per member, per month” is a common way to describe a payment model called
A. Capitation
B. Bundled payment
C. Accountable care
D. Managed care
6. Reimbursement for healthcare services must be
A. Unusual, customary, and reasonable
B. Usual, per customer, and reasonable
C. Usual, customary, and rational
D. Usual, customary, and reasonable
7. The standard development organization established to help electronic health records to interconnect is
A. LOINC
B. ICD-10
C. DICOM
D. HL7
8. A researcher who wants to adhere to Good Clinical Research Practices would be most concerned with
A. Patient availability
B. Human subject protection
C. Informed consent
D. Notice of privacy practices
9. At what stage of information lifecycle management are you most likely to have a data breach?
A. Create
B. Store
C. Use
D. Dispose
10. If you were asked to de-identify yesterday’s patient appointment list containing medical record number (MRN), patient names, and time of appointment, what action would be most appropriate?
A. Delete all MRNs and change patients name to “PATIENT.”
B. Change the names to historical figures and delete times of appointment.
C. Increase each MRN by 15 and use only the last names of the patients.
D. Only use patients name and times of appointment.
11. A formal, written agreement that describes the access to and expectations for a third party’s use of patient information is a _____________________ agreement.
A. Service level
B. Business partner
C. Liability limit
D. Data sharing
12. Generally speaking, almost all regulatory guidance allows sharing of patient information without additional patient consent to whom?
A. Next of kin
B. Law enforcement
C. Media
D. Clergy
13. When a provider is accused of an action such as not properly reviewing mammograms and misdiagnosing breast cancer, they may have committed what?
A. Adverse event
B. Practice preference
C. Case management
D. Malpractice incident
14. A new data classification technology was purchased by your healthcare organization. One of the features of the tool is the ability to mark data with metadata elements to signify the data protection levels. With this tool, you will begin to identify and classify all protected health information as what?
A. Private
B. Sensitive
C. Confidential
D. Restricted
15. Bull Run Health Insurer, your employer, has asked for your participation on the committee to establish the organization’s legal medical record. The charter of the group clearly states the regulatory obligation that the organization must have a legal medical record. The objectives of the legal medical record are also provided for your review. Those objectives are to reduce costs, improve care, and increase efficiency for clinical and business operations. After a few meetings, you are asked how the new policy can outline delegation for changes to an individual record to increase provider efficiency. What requirement for the legal medical record do you advise the group they are forgetting, if any?
A. Support patient care decisions.
B. Include full accounting and documentation of the care provided.
C. Serve as evidence in legal proceedings about such care.
D. There is nothing forgotten. There are no agreed upon standards for this action.
Answers
1. B. Registered nurses generally require the highest level of formal education completed compared to the other choices. Typically, the designation signifies a baccalaureate degree or completion of a healthcare organization–sponsored curriculum. The other categories of nurses accomplish education and experience requirements as part of applied training or through employment.
2. D. An employer group or employer-based healthcare insurance would be considered a private payer. A health maintenance organization can be a method of organizing delivery of care under a government payer plan, such as Medicare, but it is not a public source of funds. A public health agency is unlikely to reimburse providers for care as part of their surveillance responsibilities. Therefore, the best answer is D, a government entity that uses public tax dollars or other publicly acquired funds to fund or reimburse providers for healthcare.
3. B. A recurring appointment each day from 5 PM to 6 PM is an outpatient visit, as are appointments that do not require admissions officially into the hospital. The knee surgery with transportation to an assisted-living residence implies discharging the patient to his or her home. A sleep study, although overnight, is not an admission to a hospital. The emergency room that results in a formal admission into the hospital fits the definition of inpatient care.
4. C. The government is the primary payer in most developed countries of the world. Only a small percentage of individuals pay out-of-pocket for their healthcare. While employers are a sizable percentage of health insurance financers in the United States, this far less common internationally. The military, as a portion of government-provided health insurance, is partially correct, but it is not the primary payer.
5. A. “Per member, per month” describes capitation. This is a common measurement of what funds are provided to a healthcare organization for the delivery of care. The amount is preset and made available prior to the covered period of time. It has to relate to each individual over that measured period of time. Bundled payment, accountable care, and managed care are all somewhat related to financing healthcare, but none is specifically defined or measured in terms of each covered life over a period of time.
6. D. The only correct combination of adjectives is “usual, customary, and reasonable.” All of the others are not found within any typical definition of what charges are reimbursable.
7. D. Health Level 7 (HL7) is an organization that develops standards for electronic health record interconnectivity. LOINC is Logical Observation Identifiers Names and Codes and is limited to identifying laboratory and clinical observations. ICD-10 is International Classification of Diseases (ICD), 10th revision, and is used to communicate a level of detail for purposes of payment to the payers with a simple number up to six digits long that is internationally understood. DICOM is Digital Imaging and Communications in Medicine and is used to facilitate the transmission of digital images from radiology exams, for example.
8. B. Human subject protection is an overall provision that researchers must be concerned with as the concept is central to Good Clinical Research Practices. The other choices are components of protection of the study participants, and each may add to a relevant and compliant human subject protection approach.
9. D. Even though any stage of the information lifecycle can have risk of data breach, the create, store, and use stages are not the most likely for data loss. When data is marked for disposal or destruction, either in paper or digital format, it is imperative to continue to apply safeguards against loss, because too many examples exist where data is no longer needed and it is no longer protected, at which point, it is stolen or lost.
10. A. The best choice to remove all personally identifiable information and protected health information is to remove the MRN and anonymize all patient names. Choices B and D allow sensitive data elements to remain or do not reduce the chance of easy re-identification. Adding information to the MRN and leaving patient names would have no obscuring or de-identifying impact.
11. D. Generally, a data sharing agreement would be used to communicate these expectations and requirements unless another contractual agreement already outlines the same. A, B, and C are documents that serve other purposes that have little to do with information protection.
12. B. Most regulatory guidance has provisions for sharing patient information with law enforcement without additional patient consent. A, C, and D would all require additional patient consent.
13. D. If they practice with negligence as in this scenario, they will likely endure malpractice lawsuits. A, adverse event, is usually related to a mistake or failure of a process—not necessarily by one person. B is not an official term, but each provider has preferences in how they practice medicine. C, case management, is a general term for nursing and administration staff members who help properly utilize medical resources by managing the care and treatment for patients with extended care plans with referrals to specialists and possibly inpatient stays.
14. C. Marking the data confidential affords the highest level of protection category commonly used outside of military and government organizations. In any case, protected health information should be protected at the highest category level even if different terminology is used in an organization. A and D are synonymous. Both are incorrect because protected health information is regulated by government agencies and made publicly available, which would certainly have more than undesirable effects on the organization. While the data is considered sensitive, B is incorrect because sensitive is less restrictive than confidential, and the loss of the data is a significant risk to the organization.
15. B. Of the provided options, including a full accounting and documentation of the care provided is most accurate. A legal medical record must be unaltered and accurate. The creator must ensure the integrity of the legal medical record. With that in mind, A and C are more relevant to why you must have a legal medical record that is unaltered and accurate. It is used for patient care decisions and often is a document used in legal proceedings. D has some validity in that organizations have to establish their definition and contents of their legal medical record. In this scenario, it is not relevant because the group has forgotten the need for the record to be accurate with a full accounting and documentation of care provided.
References
1. Nelson, J., B. Sung, S. Venkataram, and J. Moore. 2017. “Transforming care delivery through virtual health.” Deloitte Consulting, https://www2.deloitte.com/content/dam/Deloitte/us/Documents/life-sciences-health-care/us-lshc-transforming-care-delivery-virtual-health.pdf.
2. US Bureau of Labor Statistics. 2019. “Occupational Employment and Wages, May 2018; 31-0000 Healthcare Support Occupations (Major Group).” https://www.bls.gov/oes/current/oes310000.htm.
3. Carnevale, A. P., N. Smith, and A. Gulish. 2015. “Nursing: Supply and Demand Through 2020.” Georgetown University Center on Education and the Workforce, https://repository.library.georgetown.edu/bitstream/handle/10822/1050292/Nursing-Supply-Final.pdf?sequence=1&isAllowed=y.
4. Rosseter, R. 2019. “Nursing Shortage.” American Association of Colleges of Nursing (AACN), https://www.aacnnursing.org/news-information/fact-sheets/nursing-shortage.
5. Miles, S. H. 2005. The Hippocratic Oath and the ethics of medicine. Oxford, UK: Oxford University Press.
6. US Department of Health and Human Services Office of the Assistant Secretary for Planning and Evaluation. 2000. “Standards for Privacy of Individually Identifiable Health Information. Final Privacy Rule Preamble. Health Care Clearinghouse.” https://aspe.hhs.gov/report/standards-privacy-individually-identifiable-health-information-final-privacy-rule-preamble/health-care-clearinghouse.
7. Stein L. I. 1967. “The Doctor-Nurse Game.” Archives of General Psychiatry, 16(6):699–703. https://doi:10.1001/archpsyc.1967.01730240055009.
8. Holyoake, D. D. 2011. “Is the doctor-nurse game being played?” Nursing Times, 107(43):12–14.
9. The Joint Commission. 2008. “Sentinel Event Alert 42: Safely implementing health information and converging technologies.” https://www.jointcommission.org/en/resources/patient-safety-topics/sentinel-event/sentinel-event-alert-newsletters/sentinel-event-alert-issue-42-safely-implementing-health-information-and-converging-technologies/.
10. United States Census Bureau. 2016. “Health Insurance Coverage in the United States: 2015.” https://www.census.gov/content/dam/Census/library/publications/2016/demo/p60-257.pdf.
11. Obama, Barack. 2016. “United States Health Care Reform: Progress to Date and Next Steps.” Journal of the American Medical Association, 316(5):525–32. JAMA Network, https://jamanetwork.com/journals/jama/fullarticle/2533698.
12. Bryan, B. 2016. “Here’s how much the price of Obamacare changed this year for every state in the US.” Business Insider, May 30. https://www.businessinsider.com/obamacare-price-change-for-every-state-in-us-2016-5.
13. US Department of Health and Human Services, Office for Civil Rights. 2013. “HIPAA Administrative Simplification,” (45 CFR Parts 160, 162, and 164). https://www.hhs.gov/sites/default/files/hipaa-simplification-201303.pdf.
14. Health Care Industry Cybersecurity Task Force. 2017. “Report on Improving Cybersecurity in the Healthcare Industry.” https://www.phe.gov/Preparedness/planning/CyberTF/Documents/report2017.pdf.
15. OCR HIPAA Privacy Rule. 2003. Disclosure for Public Health Activities. [45 CFR 164.512(b)]. https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/understanding/special/publichealth/publichealth.pdf.
16. Intersoft Consulting. 2016. “General Data Protection Regulation (GDPR): Art. 6 GDPR, Lawfulness of processing.” https://gdpr-info.eu/art-6-gdpr.
17. Skipper, J. 2012. “Individuals’ Access to Their Own Health Information,” ONC Policy Brief. HealthIT.gov, https://www.healthit.gov/sites/default/files/pdf/individual-access-06-03-2012.pdf.
18. Henry Ford Health System. 2019. “Supplier Diversity.” https://www.henryford.com/about/supply-chain/diversity.
19. Amatayakul, M. 2002. “United Under HIPAA: a Comparison of Arrangements and Agreements” (HIPAA on the Job series). Journal of AHIMA, 73(8):24A–D.
20. National Conference of State Legislatures (NCSL). 2019. “CON–Certificate of Need State Laws.” http://www.ncsl.org/research/health/con-certificate-of-need-state-laws.aspx.
21. Monegain, B. 2013. “Data-sharing initiative reduces deaths.” Healthcare IT News, https://www.healthcareitnews.com/news/data-sharing-initiative-reduces-deaths.
22. Savage, L., M. Gaynor, and J. Adler-Milstein. 2019. “Digital Health Data and Information Sharing: A New Frontier for Health Care Competition?” Antitrust Law Journal, 82(2):593–621.
23. Health Information and Management System Society (HIMSS). 2017. HIMSS Dictionary of Health Information and Technology Terms, Acronyms, and Organizations, 5th edition. Chicago: HIMSS.
24. AHIMA. 2011. “Fundamentals of the Legal Health Record and Designated Record Set.” Journal of AHIMA, 82(2):44: expanded online version, https://library.ahima.org/doc?oid=104008#.XjxoojFKhPY.
