CHAPTER 2
MALWARE FUNCTIONALITY
Now that we’ve covered how malware can infect, survive, and propagate across an enterprise, we’ll discuss the functionality of the various malware samples covered in the previous chapter. Today’s malware can perform any number of tasks; however, its core intent is to make money at your expense and generally steal precious information stored on your systems. In this chapter, we’ll cover some of the nasty ways malware can function once it’s on your computer.
What Malware Does Once It’s Installed
The goal depends on who wrote and/or who bought the malware and the purpose it is meant to serve and the content it is meant to deliver. Now let’s dive into the details of malware functionality and the platforms malware employs to steal information from your network.
Pop-ups
Pop-ups have plagued users for decades. They started as simple ads that were designed to generate income per click. Pop-ups were so successful that they became prevalent due to the income they could generate. Malware writers recognized this and used the same concept to infect systems using pop-ups. A well-crafted pop-up can fool a user into downloading and installing a file, which turns out to be malware. This malware can then generate its own pop-ups to generate ad-click income for its owner or perform other tasks, such as stealing information from the victimized system.
![]()
Pop-ups can be classified into two types, as discussed in the previous paragraph: pop-ups as payload and pop-ups as infection vector.
The threat of pop-ups prompted browser makers to create pop-up blockers. Pop-up blockers were either shipped in the form of plug-in or extensions or as built-in features that were turned on by default.
The rise of pop-up blockers then prompted malware writers to come up with ways to counteract the blockers. One of the most direct methods attackers use, in addition to URL redirection, is to inject pop-ups directly into a user’s computer from plug-in programs such as Java or Flash. Here’s a very simple JavaScript-based plug-in that would allow you to bypass a traditional pop-up blocker:
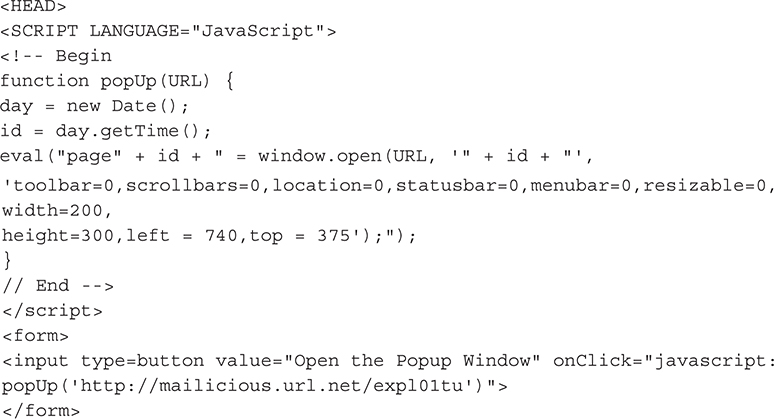
At first, this method proved to be effective, but browser makers wised up. They started blocking pop-ups generated from plug-in-based code that loaded from within a web page. This gave rise to blocking website scripts. This feature is an inconvenience to the everyday user because scripts on websites have to be allowed specifically for the website to function. But it is a good trade-off to keep yourself secure and free from pop-ups.
 Pop-up Threats
Pop-up Threats

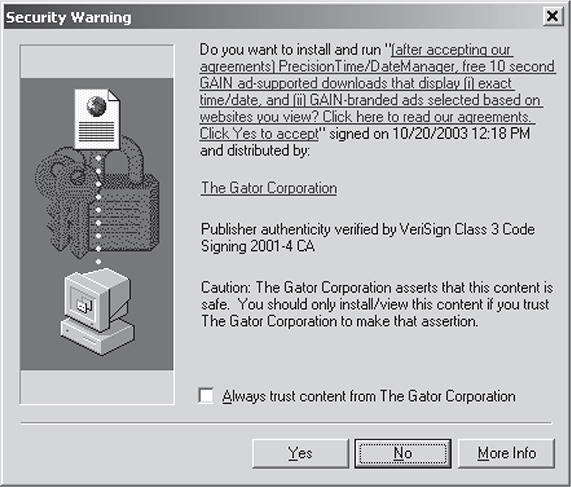
The threat from pop-ups is determined by their “click” factor; even my mother has fallen for it. Some pop-ups use specially crafted messages designed to social engineer the user into clicking on or moving the mouse over any part of the window, which then kicks off any number of actions. Some of the craftier pop-ups are even launched when the user clicks the “X” in the upper-right corner to close the window. The following is an example of a pop-up advertisement you might encounter.

Identifying Pop-up Blockers
Here’s a simple function you could run to identify the presence of a pop-up blocker on a host or to test the strength of your own pop-up blocker:
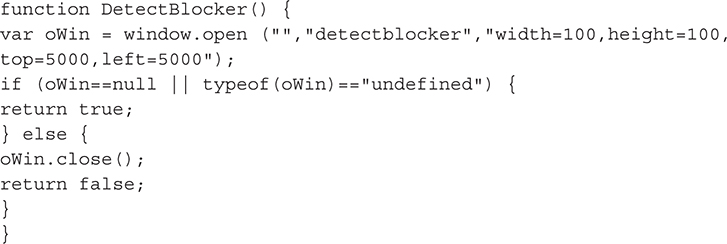
Bypassing Pop-up Blockers
Shady advertisers continually seek ways to circumvent pop-up restrictions. Some pop-up advertisements are generated using Adobe Flash. Using this method, a pop-up is not detected because no pop-ups are generated and the advertisement is then run within the current window. The code in the previous section is one of numerous methods that can be used to circumvent pop-up blockers. There are too many versions of pop-up blockers to cover in this book, so for the sake of example, we’ll focus on the methods used to bypass your pop-up blockers.
Pop-ups with HTML HTML pop-ups have failed to work since pop-up blockers can easily identify an HTML statement embedded within a web page like this one:
![]()
As you can see, any security program would quickly identify the snippet of code and not allow the link to be opened on click unless you pressed CTRL-C, were on a website where your security settings allowed pop-ups, and/or were using a very outdated browser.
![]()
It is always a good practice to update all Internet browsers that you are using on your systems to ensure you have not only all the new features but also all the security solutions that the browser manufacturers have developed for their browsers.
Pop-ups with JavaScript With Java, you can embed pop-ups within animations, which at one time were harder to detect than HTML but are not as hard to detect today. If you examine the following code snippet, you’ll see there are ways to generate pop-ups, but again, if a pop-up blocker is present, you won’t reach your target:
Example A


Pop-ups with Flash JavaScript can be delivered through a Flash animation, however. Although with Flash, you can also use ActionScript to create a pop-up:

 Pop-up Countermeasures
Pop-up Countermeasures
Most modern browsers come with pop-up-blocking tools; third-party tools tend to include other features such as ad filtering.
Pop-up Blocking
Many websites use pop-ups to display information without disrupting the currently open page. For example, if you are filling out a form on a web page and need extra guidance, a pop-up might give you additional instructions so you don’t lose any information already entered into the form.
Some web-based application installers such as the one used by Adobe Flash Player use a pop-up to install software. Be aware of what you are being asked to install. A hacker may include a web-based software install that will mimic and appear to be a legitimate program but in actuality be malware that would then legitimately install itself on your computer and open your computer to additional downloads and pop-ups.
With many Internet browsers, pressing the CTRL key while clicking a link allows you to bypass the pop-up filter. Although practically all browsers today have pop-up blockers, they have their own levels of functionality. With the large research and development budgets at their disposal, the larger browsers can be relied on to keep up with attackers’ injection methods. You also have the ability to customize each pop-up blocker to meet your needs specifically.
Search Engine Redirection
Webmasters or developers use redirection in their sites for several reason. Let’s take a quick look at some of these from both an administrative and a more malicious point of view in order to better understand how a simple feature that makes an administrator’s life easier can also be abused to further criminal activity.
Comparable Domain Names
Website visitors frequently mistype URLs, for example, gooogle.com or googel.com. Organizations often list these misspelled domains and redirect visitors to the correct location, in this instance, google.com. Also, the web addresses example.com and example .net could both redirect to a single domain or web page such as example.org. This method is often used to “reserve” other top-level domains (TLDs) with the same name or make it simpler for a true .edu or .net to redirect to a more recognizable .com domain.
Moving a Site to a New Domain
Why redirect a web page?
• A website might need to modify its domain name.
• A website author might transfer his or her pages to a new domain.
• Two websites might merge.
With URL redirects, an incoming link to an old URL could be sent to the correct location, for instance, if you’re moving to a new domain-name provider and need to forward visitors from your old server to a new server. There are numerous legitimate URL redirects, but in the spirit of this book, we are going to stick to covering the nefarious ways attackers can use URL redirection to infect your system.
Nefarious redirects might be from sites that have not yet realized there has been a change or from an older website that has allowed its domain-name registration to expire and a criminal entity has then purchased the domain name. Unsuspecting users then click the bookmark to the site, which they saved in their browser favorites. The same applies to search engines. They often retain old domain names and links in their databases and send search users to these old URLs. When a site uses a Moved Permanently redirect to the new URL, visitors almost always end up on the correct page. Also, in the next search engine pass, the search engine might detect and use the newer URL. However, attackers use this old information to their advantage. Now, with more reliable search engine indexing of websites, it is more difficult.
The primary issue with redirects is they give attackers the ability to lure visitors to a copy of a known site that is loaded with multiple injection points where visitors can click and then become infected with malware. The uses of URL redirection by malware are broad and many and primarily for monetary purposes. If you search the Internet, you will find thousands of forums where users complain about malware redirecting unknowing victims to pay-per-click sites like pornography and/or other shareware sites where the hacker is paid per visit by the owner of the site. Malware, once installed on a victim host, will typically generate several pop-ups and redirect the victim’s currently open browser to sites that pay the hacker when the victim visits and/or provide a means to distribute additional malware—similar to a drive-by download. The next illustration is an example of a drive-by-download. A drive-by download occurs when a victim visits a site and is asked to install new software, which in and of itself can be from a corporate source, but it introduces additional background downloading or malicious software that has the ability to install or execute any application it has been instructed (or preprogrammed) to.
Logging Outgoing Links
The access logs of almost all web servers keep some level of information about visitors—where they come from and how they browse the site. Typically, these servers will not log information about how a visitor leaves the site. This is because the visitor’s browser does not need to communicate with the original server when the visitor clicks an outgoing URL link; however, this information can be captured in quite a few ways.
The first way involves URL redirection. Instead of sending the client straight to the second site, links can direct to a URL on the first website’s domain that automatically redirects to the original target. This request leaves a trace in the server logs indicating which links were followed. This method can be used to detect which sites are being visited in order to plan attacks against those websites. You can also use this method if your goal is to quietly collect intelligence on an individual or group and you know they are visiting your site or a site you have taken control of. This method has the disadvantage of adding a sometimes significant delay to each additional request to the original website’s server.
From an attacker’s perspective, configuring your network to monitor or log all outbound HTTP and HTTPS site activity is smart. From a security analysis perspective, this configuration is especially helpful when trying to investigate a malware outbreak; you need to identify as quickly as possible infected machines before they attempt to update their code base or upgrade to another stage of Trojan. The updating of malware once on a system is becoming more and more commonplace as hackers attack networks with much more precision and skill than they used to.
Playing with Search Engines
Attackers can also modify metadata for search engine crawlers in order to catch more victims who are searching for specific terms without knowing how to search the Internet and/or identify valid sites properly. Redirect techniques have been used to trick website visitors for years. For instance, misleading information placed in a site’s index meta-name content or keywords section could be used inappropriately to trick or social engineer a victim into visiting the site in order to execute an attack on the client browser, initiate a drive-by download, or attempt to phish the victim for information. This method can alter the outcome of a search engine query in order to lure unknowing victims to the site.
Redirects have also been used to “steal” the page rank of one popular page and use it for a different purpose, usually involving the status code 302 HTTP or Moved Temporarily. Search engine providers recognize the problem and have been taking fitting actions to protect their users. Generally, sites that employ such techniques to control search engines are punished automatically by having their ranking lowered or by being excluded from the search index once a search engine firm discovers the fraud. But discovering the fraud can take weeks, if not months.
Manipulating Visitors
URL redirection is sometimes used in phishing attacks that confuse visitors about which website they’re visiting. This type of threat also quickly takes visitors to sites that store malicious code rather than the benign sites initially presented to victims.
 Redirection Techniques and Attacks
Redirection Techniques and Attacks

Attackers use several techniques to redirect visitors to their sites. First, we’ll cover the administrative features available, and then we’ll discuss how these features can be used for nefarious purposes.
Refresh Meta Tagging
In many cases, using the refresh meta tag is the simplest method for redirecting visitors. Following is a simple tag that shows what administrators typically do to refresh the information on their websites. Most news organizations use this method to ensure visitors who are on their site for an extended period of time see updated content. After a defined period of time, the browser refreshes and the newly added content appears. Take a look at this basic HTML tag; you can see it has been set to refresh after a count of 600 seconds or 5 minutes:
![]()
Now if you use this same HTML line with an added push, you can redirect a user to another site without generating a pop-up. Without arousing suspicion, an attacker could simply forward a visitor to a nefarious site after the visitor has viewed the intended website by simply rewriting the refresh tag like this:
![]()
The only difference in the refresh tag is a few extra HTML tags. Now every time a visitor browses to that site, after a few moments, he or she is redirected to a site that is loaded with client-side browser-based attacks and/or pay-per-clicks. If used too hastily, this feature can lead to visitors mistakenly identifying that the site is legitimate, not a nefarious site running malware in the background, before they can press their browsers’ Back button.
Manual Redirects
The simplest technique is to ask the visitor to follow a link to the new page, generally using an HTML anchor like this:
![]()
More often than not, malicious websites link sites together. For example, piracy sites that specialize in bootleg movies and/or illegally cracked software will typically link to pornographic sites and vice versa to support each other like a symbiotic team. Typically, most robust antivirus engines or anti-spyware sites will recognize a malicious site after the visitor has clicked it, and then the site is either blocked and/or the visitor is warned. However, more often than not, the visitor is not informed, the malicious site is not detected, and the visitor’s computer system is infected unknowingly.
HTTP 3xx Status Codes
Because of the HTTP protocol used by the World Wide Web, redirects can also be responses from web servers with 3xx status codes that lead visitors to other locations. The HTTP standard defines several status codes for URL redirection:
• 300 Multiple Choices (e.g., offer different languages)
• 301 Moved Permanently
• 302 Found (e.g., temporary redirect)
• 303 See Other (e.g., for results of CGI scripts)
• 307 Temporary Redirect
These status codes mandate that the URL of the redirect target is given in the Location: header of the HTTP response. The 300 Multiple Choices will usually show all choices in the body of the message and show the default choice in the Location: header.
Within the 3xx range, there are also status codes (not discussed here) that are significantly different from the previous redirects:
• 304 Not Modified
• 305 Use Proxy
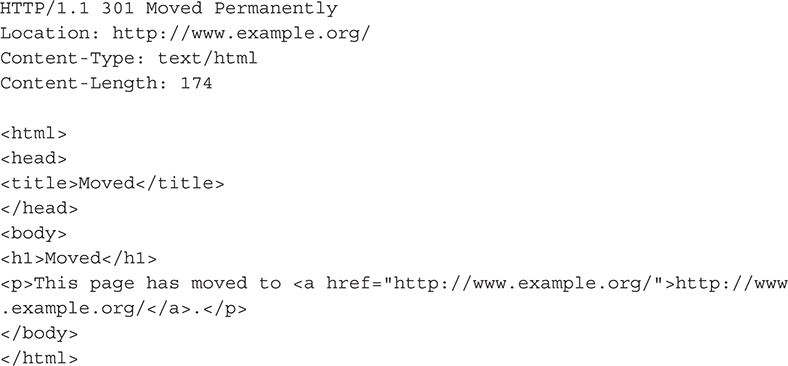
Here is a sample of a standard HTTP response that uses the 301 Moved Permanently redirect:
Using Server-Side Scripting for Redirects
Often, web authors do not have permission to produce these status codes: The HTTP header is generated by the web server applet and not interpreted from the file for that URL. Even for CGI scripts, the web server usually creates the status code automatically and allows custom headers to be added to the page by the script. To create HTTP status codes with CGI scripts, you need to enable nonparsed headers.
Sometimes, printing the Location: URL header line from a standard CGI script is enough. Many web servers choose one of the 3xx status codes for such replies.
The HTTP protocol requires that the forward be sent all by itself, without any web page information. As a result, the web developer who is using a scripting language to redirect the user’s browser to another page must ensure that the redirect is the first or only part of the response. In the ASP scripting language, this can also be finished using the methods response.buffer=true and response.redirect "http://www.example.com". When you use PHP, you can use header("Location: http://www.example.com");.
As per the HTTP standard, the Location header must have an absolute URL. When redirecting from one page to an additional page within the same site, using a relative URL is a common error. As a result, most browsers tolerate relative URLs in the Location header, but some browsers generate a warning that is shown to the end user.
Using .htaccess for Redirects
With the Apache web server, directory-specific .htaccess files (as well as Apache’s main configuration files) can be used. For example, use this to redirect a single page:
![]()
And use this to change domain names:

When employing .htaccess for this purpose, an admin would usually not require administrator permissions; although if the permissions are required, they can be disabled. When you have access to the Apache primary config file (httpd.conf), you should avoid using .htaccess files.
Refresh Meta Tag and HTTP Refresh Header
Netscape was the first to introduce a feature, often called meta-refresh, to refresh the displayed page after a defined period of time. Using this feature, it is possible to specify the URL of the new page, thereby switching one page for another, or to refresh some form of content found on the page. These are the types of meta-refresh options available:
• HTML <meta> tag
• An exploration of dynamic documents
• Proprietary extensions
A timeout of 0 seconds means an immediate redirect.
Here is an example of a simple HTML document that uses this technique:

This technique is functional for all web authors because the meta tag is contained inside the document itself.
For this technique, it is important to remember the following.
• The meta tag needs to be placed in the head section of the HTML file.
• The variable 0 used for this example may be replaced by another variable to achieve a delay of as many seconds. Many users feel delay of this kind is annoying unless there is a reason for it.
• This was a nonstandard addition by Netscape. It is supported by most web browsers.
Here is an example of achieving an identical effect by issuing a HTTP refresh header:

This response is easier for CGI programs to generate because you don’t need to change default status codes. Here is a simple CGI program that affects this redirect:
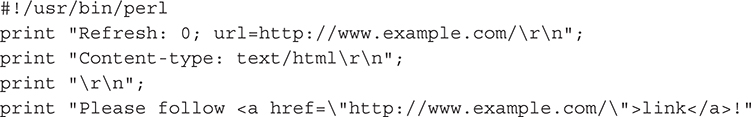
JavaScript Redirects
JavaScript offers several ways to show a different page in the current browser window. Quite commonly, these methods are used for redirects. However, there are numerous reasons to prefer HTTP headers or refresh meta tags (whenever possible) over JavaScript redirects:
• Security considerations.
• Some browsers don’t support JavaScript.
• Many crawlers (e.g., from search engines) don’t execute JavaScript.
![]()
If you search for “you are being redirected”, you’ll find that almost every JavaScript redirect employs different methods, making it very hard for web client developers to honor your redirect request without implementing all modules within JavaScript.
Frame Redirects
A somewhat different effect can be achieved by creating a single HTML frame that contains the target page:
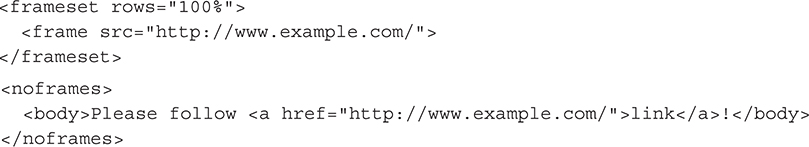
One main distinction of this redirect method is that for a frame redirect, the browser displays the URL of the frame document, not the URL of the target page, in the URL bar. This technique, generally called cloaking, may be used so the reader sees a more credible URL or, with more fraudulent intentions, to conceal a phishing site as part of website spoofing.
Redirect Loops
It is quite probable that one redirect leads to another redirect. For example, the URL http://www.example.com/URL_redirection (note the differences in the domain name) is first redirected to http://ww1.example.com/URL_redirection and again redirected to the right URL: http://test.example.com/URL_redirection. This is appropriate as the first redirection corrects the wrong domain name. The next redirection selects the correct language section. Finally, the browser shows the source page. Sometimes, however, a mistake by the web server can cause the redirection to point back to the first page, leading to a never-ending loop of redirects. Browsers typically break that loop after a few steps and present an error message instead.
 Redirect Countermeasures
Redirect Countermeasures
Redirects are quite annoying. After removing the malware responsible for the redirect, you must check the browser. Clear the browser’s cache and history and remove all add-ins and extensions—there is malware that installs add-ins or extensions that are responsible for the redirection.
Data Theft
Data theft is a rising problem primarily perpetrated by office workers with access to network resources such as desktop computers; mobile devices such as tablets and smartphones; and storage devices such as flash drives, multimedia gadgets, and even digital cameras capable of storing digital information. All of these devices typically store large amounts of corporate proprietary information that is regularly protected by network and security administrators. As employees often spend a large amount of time developing contacts, confidential, and copyrighted information for their company, they often feel they have some right to that information. They are also generally inclined to copy and/or delete part of it when they leave the company or misuse it while they are still employed.
Some employees will take information such as customers and business contacts and leverage them for personal gain or for side business. We have personally seen this method used numerous times by sales associates in order to generate additional revenue. A salesperson will commonly make a copy of the contact database for use in his or her next job. Generally, this is a clear abuse of the terms of employment. Although most organizations have implemented firewalls and intrusion-detection systems, very few take into account the danger posed by your average employee who regularly copies proprietary data to his or her work computer, mobile device, and in some cases, personal computer at home for individual gain or use by another company. The damage that is caused by data theft can be immeasurable considering today’s technology and an employee’s ability to transmit very large files in very short periods of time via email, web pages, USB devices such as flash drives and external hard drives, optical storage, and other handheld devices that can store large amounts of data.
When dealing with malware, the same things can occur and not even be connected with an employee of your organization. At times, an angry employee can even intentionally launch malware within an organization to steal data or to even just infect the network. Malware infection can occur through the use of removable media devices or direct Internet transmissions. As removable devices with increased hard drive capacity get smaller, quick thefts such as stealing synchronized smartphone information saved on a target system becomes easy.
It is now possible to store 1TB of data on a device that will fit in an employee’s pocket, data that could contribute to a business’s downfall. Malware is even being written to infect corporate and/or personal mobile devices to either steal information or enable the malware to infect the user’s personal computer in an attempt to propagate across the network into other devices for any number of purposes.
Mobile Device Malware
Mobile devices are now part of the corporate world. Most mobile devices such as iPhones, iPads, and Android-powered devices are directly connected to the corporate network. These devices pose a security threat because they are often connected to other unsecured networks as well when they are outside a corporate setting.
Attackers have recognized this trend so they have started targeting mobile devices for the purpose of data theft. Once these mobile devices are compromised and then connected to a corporate network, data can be exfiltrated out of the network system—especially if the malware is specifically written for a mobile device to steal corporate information.
Table 2-1 details some of the portable device malware samples that have come out in the past several years. Some of these are innocuous beyond doing damage to your device, but some will actually steal information directly off of your mobile device and send it to an attacker or propagate through networked systems once the mobile device is plugged into a docking station or synchronized wirelessly via Bluetooth.
Table 2-1 Mobile Device Malware
Click Fraud
Click fraud is a form of Internet-based crime that takes place in pay-per-click online advertisements when a person, script, or computer program imitates a real user of a system’s web browser by clicking an advertisement for the purpose of generating revenue for the advertising firm and the hacker who delivered the click fraud malware to the unknowing victim. Almost always the actual advertising that is clicked for profit is actually of no interest to the victim. Click fraud is a topic of some controversy and of increasing litigation due to advertising networks benefiting from the fraud on the backs of innocent consumers.
Pay-per-Click Advertising
Pay-per-click advertising (PPC advertising) is an arrangement in which webmasters, acting as publishers, display clickable links from advertisers in exchange for a charge per click. The biggest advertising networks today are Google’s AdWords/AdSense, Bing Ads, and Yahoo! Ads. These companies act in a dual role since they are also publishers of Internet content (on their search engines). This dual-role approach by large firms can potentially lead to conflicts of interest. For instance, these companies lose money to unnoticed click fraud when they pay out to the site publishers serving the ads, but they make more money when they collect fees from advertisers through regularly paid dues. Because of this difference between what Google or Yahoo! collects from advertising firms and what Google or Yahoo! pays out to advertisers, they profit directly and invisibly from click fraud.
 Click Fraud Threats
Click Fraud Threats

This type of click fraud is based around noncontracted parties who are not part of a team setup with pay-per-click advertising agreements. This lack of liability between parties can introduce criminal elements into the pay-per-click advertising process. Here are a few examples of noncontracting parties:
• Advertiser competition Some parties may wish to damage their competition in the same market by clicking their competition’s ads. This would inevitably force advertisers to pay out for unrelated clicks rather than customer-driven clicks.
• Publisher competition These parties may wish to frame a specific content publisher in order to drive advertisers to their own content publishing firm. When this occurs, the nefarious publisher makes it seem like the publisher is clicking its own ads rather than a customer. The advertising firm may then decide to end the relationship. Many publishers depend exclusively on revenue from advertising, and such attacks can put them out of business.
• Malicious intent As with vandalism or cyberterrorism, there are numerous motives for wishing to cause harm to either an advertiser or a publisher, even by people who have nothing to gain financially. Motives could include political-, personal-, or even corporate-based grudges. These cases are often the most difficult to identify because identifying or even tracking down the culprit is hard, and even if the culprit is found, there is not much legal action that can be taken since the Internet allows for so much anonymous activity.
Identity Theft
Identity theft can be used to support crimes, including illegal immigration, terrorism, drug trafficking, espionage, blackmail, credit fraud, and medical insurance fraud. Some individuals may attempt to imitate others for nonfinancial reasons such as to receive praise or notoriety for the victim’s achievements. When dealing with malware, identity theft comes in the form of your Internet identity being stolen in order to access your online accounts. These accounts could include your email accounts—both your ISP and webmail accounts—PayPal, eBay, Twitter, Facebook, Instagram, banking accounts, and other personal online accounts.
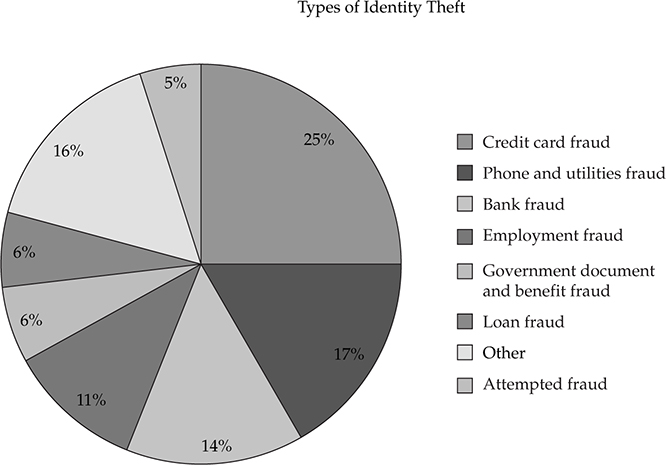
An attacker can use all of these fraudulently to portray himself or herself as the victim in order to steal personal information, money, or other items. Finally, by stealing your online identity, attackers can use this façade as a means to distribute malware to your friends and family. In the next few sections, we’ll briefly cover some of the types of identity theft so you better understand them when you see them. In this section, we’ll discuss the various forms of identity theft. First, consider these graphs that show international averages for the actual types of identity theft and how the stolen or fraudulent information is then used.

Financial Identity Theft
This type of fraud generally involves a victim’s bank accounts and/or personal information so the criminal can use current or open new financial lines of credit or accounts. In doing this, the criminal pretends to be the victim by presenting the victim’s correct name, address, date of birth, and any other personal information required to authenticate the criminal as being the victim. This type of identity theft is so commonplace today that probably one out of five of your friends could confirm this has happened to them.
Criminal Identity Theft
This type of identity theft occurs when a criminal uses your identity to perform criminal acts, so in the event of being caught by the police or an organization’s security team, your credentials would be used to divert suspicion from the criminal and his or her activities. Some people never learn they’ve been a victim of this type of theft if it’s a minor offense unless it’s localized within their state, although they could even be arrested for a more serious offense.
 Identity Theft Attacks
Identity Theft Attacks
In almost all cases, a criminal needs to get hold of personally identifiable information (PII) or documents about an individual in order to impersonate him or her in life or on the Internet. Criminals do this by
• Stealing letters or rummaging through rubbish containing personal information (dumpster diving) on trash night. One of my neighbors who works for a U.S. government intelligence agency had his trash rummaged through in the middle of the night a few years back. So be quite aware of what you throw away. This also applies to deleted items in your computer’s Recycle Bin and/or old files you leave sitting in your My Documents folder or /home/usr/%name% directory.
• Researching information concerning the victim in government registers, Internet search engines, or public records search services.
• Using your own installed programs to steal personal or account information in order to log in to vendor sites where more information can be gathered.
• Installing keyloggers and eavesdropping on your keyboard inputs in order to steal personal information, passwords, information on your friends, educational status, or professional dealings to obtain personal data.
• Stealing personal information from corporate computer databases at the victim’s workplace. The attacker can use malware to perform this task (Trojan horses, hacking).
• Advertising phony job offers (either full-time or work-from-home-based) to which the victim will innocently reply with his or her full name, address, curriculum vitae, telephone numbers, banking details, and/or security clearance levels.
• Social engineering a victim by impersonating a trusted entity such as a company, institution, or organization in an email in order to lure the victim into opening an attachment that would inject malware onto the victim’s computer, leading to the theft of personal information.
• Exploiting the victim’s social networking (Twitter, Facebook, Bebo, LinkedIn, LiveJournal) sites to learn additional details about a victim and potentially exploit friends or relatives of the victim to spread/propagate malware and steal additional identities.
• Performing voice phishing, or vishing. Criminals will call a victim pretending to be a government agency such as the IRS. They scare the target into giving up information, which can include a victim’s Social Security number and adjusted gross income figures, by threatening to file suit unless the information is forthcoming. In most cases, a person’s tax information can be accessed with these two pieces of information.
• Changing your email address thereby diverting account updates, billing statements, or account advisories to another location to either get current legitimate account info or to delay discovery of the identity theft.
 Personal Identity Theft Countermeasures
Personal Identity Theft Countermeasures
The hardest thing for any victim to do is clear his or her record once identity theft has occurred. For some, it can take months, if not years, to even get a credit score cleaned up. However, knowing how identity theft can occur will provide you with some significant perspectives on how you can protect yourself and limit your exposure to threats. Criminals will do whatever they need to do in order to steal your identity to complete their grand designs. The bottom line to understanding malware-based threats is to know what websites you visit and the content shown on them:
• Is this a very popular website where numerous people can report an issue?
• Does this website have a suspicious name, for example, www.paypal.com versus www.pay.pal.com?
• Understand what you are clicking before you click something.
• Understand a website before you start inputting personal information.
• Understand what you download and/or install from the Internet:
• Is this a well-known program from a well-respected site?
• Is this a well-known program from a suspicious site?
• After installing a program, did something odd start to occur with your PC?
Acquiring personal identifiers is made possible through severe breaches of privacy. Consumers are often gullible about who they provide their information to. In some cases, the criminal obtains documents or personal identifiers through physical theft, social engineering, or malware-based data theft. Guarding your personal information on your computer is critical to preventing identity theft. You can protect your information in so many ways that if they were all listed you’d be surprised at the available options. However, because this is a countermeasures section, we cover only a handful of them in order to give you some recommendations that might work best for you. Always remember the stronger the safeguard, the better your chances are at preventing identity theft. Finally, a good time to implement these safeguards is yesterday. Do not wait to be infected with malware before you perform any of the safeguards listed here.
• Three-factor authentication Use a three-part authentication process that includes a username (something you are), a password (something you know), and a secure ID or secure token (something you have). This approach is offered for players of Blizzard Entertainment’s World of Warcraft (where I am Go Alliance, Die Horde). It is called the Blizzard Authenticator, and it uses a set of six numerals that change every 30 seconds. Without this token, stealing Warcraft accounts is impossible. This method is also applicable to large corporations that use SecureComputing or RSA SecurID tokens.
• Computer authentication systems For instance, Pretty Good Privacy (PGP) or the GNU Privacy Guard (GPG) require the user to authenticate each time a transmission is sent and/or provide regular personal information to continue working on secure documents. These programs also provide a protected space from some types of malware.
• Offline secure data storage Moving your data to a secure offline removable device that is only plugged into your system when it is being used can be very helpful. This method is not perfect, but the less personal information you store on your computer that is typically readily accessible to malware or attackers, the better off you are.
• Password lockers This service is offered all over the Internet as a means of single-sign-on (SSO) or a place where, for a fee, you can store all of your passwords securely so they are not cached on your computer or written in some file stored on your PC or in your desk. Never store your usernames/passwords, credit cards/expirations/CCVs, and Social Security number/DOB in any text file or document that can be easily accessed and deciphered.
Keylogging
In this section, we will discuss the functionality of keyloggers and what information you can gather with them and how they can be used in order to steal information from a host. For the sake of this book, we will focus on malware-based keylogging functionality. However, it is important to make note of some of the other types as one computer can be infected and, through the use of its infrared port, microphone, and/or wireless interfaces, be used to siphon keystrokes from other machines within range of the infected computer. Most of this information should be considered an opener or overview for the rootkit chapters in Part II of this book, which will discuss in more depth the inner workings of user- and kernel-mode hooking techniques and rootkits.
Local Machine Software Keyloggers
These are software programs that are intended to work on the target computer’s operating system. Here are some of them.
Kernel Based This method is the most difficult both to write and to combat. Such keyloggers exist at the kernel level and are thus practically invisible. They almost always undermine the OS kernel and gain unauthorized access to the hardware, which makes them very powerful. A keylogger using this technique can act as a keyboard driver, for example, and thus gain access to any information typed on the keyboard as it goes to the OS.
Windows Based: GetMessage/PeekMessage You can attempt to hook these APIs directly in order to capture WM_CHAR information. WM_CHAR messages are posted to a window with the keyboard when a WM_KEYDOWN message is translated by the TranslateMessage function. The GetMessage() and PeekMessage() functions are both used to queue and dequeue Windows messages, which are connected to keyboard inputs. These are associated with GDI functions and are defined in user32.dll, which makes a call to ntdll.dll, which is later passed down to W32k.sys, which is in kernel land versus user land. So, if you’re attempting to gain kernel access to execute keystroke logging, this method is one to use.
Linux Based Sebek is a widely known white-hat input logging tool, which runs on several Linux kernel versions. It is a kernel patch that was initially developed with the intent to capture interactions between honeypots and intruders within honeypots. This will be discussed in more depth in Chapter 4, but in short, it is configured to capture several read and write activities from syscall.
Hook Based Keyloggers hook keyboard APIs provided by the OS. The issue with using hooks is the time added to system responses can bog down overall system performance. So, in short, operating directly through the kernel is much more efficient. Since most malware leverages hooking, however, we’ll cover some of these as well.
• WH_JOURNALPLAYBACK This hook provides applications with the ability to insert messages into the system queue. When you want to play back various series of events captured from the mouse or keyboard, use WH_JOURNALRECORD.
• WH_JOURNALRECORD This hook provides applications with the ability to record and monitor various input events. You can use this to record and store information from the entire system and then use WH_JOURNALPLAYBACK to later analyze the data inputs.
• WH_KEYBOARD This hook enables an application to monitor message traffic for literal keyboard messages directly from the keyboard, which are returned by the GetMessage() or PeekMessage() functions.
• WH_MOUSE_LL and WH_MOUSE These hooks are both associated with capturing and playing back mouse input events posted in the message queue.
Unique Methods Here, the hacker uses functions like GetAsyncKeyState and GetForegroundWindow in order to record the information regarding which window has focus and what state each key of the keyboard is in, telling the hacker what information is being input into which window. This is simple from an implementation perspective; however, it requires the state of each key to be polled several times per second, causing an obvious increase in CPU usage, and it can miss occasional keystrokes as data processes can sometimes lock up from time to time. The skilled coder could defeat both of these limitations by easily polling all key states several hundred times per second, which would not noticeably increase CPU usage on a given system.
Remote Access Software Keyloggers
These are local software keyloggers configured with additional characteristics to broadcast recorded data from the target computer to make the data accessible to the monitor at a remote location. Typically, information is sent out via FTP, email, or a hardware-based device and/or the criminal logs into the victim’s computer itself and views any type of preprogrammed data the keylogger was configured to collect.
Covert channels can be designed that would allow the malware publisher to return and log in to the keylogger application or provide the keylogger with covert methods in which to export its captured data to the publisher. There are several other types of keyloggers, but we are not going to cover these as they are beyond the scope of this edition of the book.
 Keylogger Attacks: Email Sinks Two Anchors—Keystroke Logger Helped
Keylogger Attacks: Email Sinks Two Anchors—Keystroke Logger Helped
The ability for an unauthorized person to infringe on your personal and corporate privacy can be devastating. When a criminal has access to your personal or corporate information, it can lead to many things that you would otherwise not want to occur. Consider the following attack on a news journalist, which was published in late 2008.
There are numerous articles on this event; however, here is a synopsis…. A longtime television newscaster was charged with illegally accessing a former co-anchor’s email account. She apparently became wise to the fact that personal details of her life were being leaked to gossip columnists, which over time led to her being dismissed from the news station. According to various articles, her email passwords were stolen using a keylogger that was hardware based and secretly stored all of the keystrokes she input into the system, including personal information and, most importantly, passwords to her corporate and private email accounts.
 Keylogger Countermeasures
Keylogger Countermeasures
Keyloggers are a serious threat to privacy, but you can take steps to mitigate their presence.
Software Keyloggers Currently, there is no easy way to prevent keylogging. In the future, software with secure I/O may be protected from keyloggers. Until then, the best plan is to use common sense and a mixture of several methods. It is possible to use software to track the keyboard’s connectivity and log its absence as a countermeasure against physical keyloggers. This method makes sense when the PC is almost always on.
Code Signing The 64-bit version of Windows puts into practice mandatory digital signing of kernel-mode device drivers, thereby restricting the installation of keylogging rootkits. This method requires all kernel-mode code to have its own digital signature. This is also the case for some of the more recent versions of Windows components for Vista and beyond. This method will authenticate installed software as legitimate from the actual source or publisher of the application. This process is neither available in earlier versions of Microsoft Windows nor is it available in almost all earlier versions of Unix-based operating systems.
This type of code signing cannot occur unless all kernel-mode software, device drivers, protected drivers, and drivers that stream any type of live protected content are all protected and actively signed by the Windows feature, Code Integrity. This feature ensures users are able to help administrators identify errors in the system when reviewing system logs. You can read more about the Code Integrity feature by visiting Microsoft’s website (http://www.microsoft.com).
In 2015, Microsoft introduced Device Guard, a new security mechanism in Windows 10. According to Microsoft, this new feature gives organizations the ability to lock down devices in a way that provides advanced malware protection against new and unknown malware variants. You’re in control of what sources Device Guard considers trustworthy, and it comes with tools that can make it easy to sign universal or even Win32 apps that may not have been originally signed by the software vendor.
Program Monitoring You should regularly review which applications are installed on your machine. If done on a regular basis, you should be able to identify newly installed programs easily that may have quietly installed themselves on your computer—programs related to spyware, adware, and/or simply malware installations.
Detection with Anti-Spyware Programs Most anti-spyware programs will attempt to detect active keystroke loggers and clean them when possible. You will generally only find this level of support through more dependable vendors versus generally unknown vendors that may actually support some spyware vendors.
It is important to note that anti-malware solutions have incorporated spyware and adware detection into their suites, making them a one-stop solution for detecting miscreants.
Firewalls These applications protect your computer’s ingress and egress traffic from unauthorized communications, and although they do a great job at this, a keylogger will still attempt to perform its task and record your computer’s input. However, if the keylogger does attempt to transmit its collected data out to the criminal and your firewall is configured to either block all unauthorized outbound traffic or alert you on all outbound connection attempts, your system will more than likely prevent the keylogger from transmitting the captured input.
Network Intrusion Detection/Prevention Systems These systems can alert you to any network communications that touch your network devices across your enterprise. An NIDS will clearly identify unencrypted keylogger transmissions that attempt to make incoming and outgoing network connections. If the transmissions are encrypted, it can be difficult to identify the activity as actual keylogger traffic rather than seeing a simple alert of an unknown connection. Regardless of whether the system is a network- or host-based IDS/IPS, it should alert you to actual outbound connections attempting to phone home.
Smart Cards Because of the integrated circuits on smart cards, they are not affected by keyloggers and other logging attempts. Smart cards can process information and return a unique challenge every time you log in. You generally cannot use the same information to log in again. This method adds an authentication factor to the security system that makes it much more difficult for malware to authenticate as the valid user. With cryptographic systems, each time you log in it emulates the strong encryption process we discussed earlier called three-factor authentication. This method is practically impossible to break unless you are able to hack the algorithm itself, which is next to impossible.
Anti-Keylogging Programs Keylogger discovery software is also available, which is a type of program that uses a set of “signatures” with a list of all known keyloggers and will work to remove the keylogger. The PC’s authorized users can then randomly run a scan against this list, and the software looks for the items from the catalog on the hard drive. One major drawback to this type of protection is that it only protects you from keyloggers on the signature-based list, with the PC remaining vulnerable to other keyloggers.
There are several methods not covered in this chapter as there are so many conceptual methods to counter keyloggers. We have attempted to list the ones most commonly used in security operations programs encountered in our travels.
Malware Behaviors
A spyware program is rarely unaccompanied on a computer: An infected machine can be rapidly infected by many other components. Users frequently become aware of unwanted behavior and degradation of system performance. A spyware infection can create significant unwanted CPU utilization rates, constant disk usage, and unwanted network traffic, all of which slow down the computer. Stability and permanence issues, such as application or systemwide crashes, are also an ordinary occurrence when spyware is present. Spyware, which interferes with networking software generally, makes it difficult to connect to the Internet.
Some spyware infections are not even noticed by the user. Users presume in those situations that the issues relate to hardware, Windows installation problems, or a virus. Some owners of badly infected systems contact technical support experts or even buy a new computer because the existing system “has become too slow” for their liking. Badly infected systems may need a clean reinstallation of all their software in order to get back to full functionality. Only rarely will a single piece of software render a computer unusable unless it has spread to additional system services.
Some other types of spyware (for example, Targetsoft) change system files so they will be more difficult to remove. Targetsoft modifies the Winsock Windows Sockets files. The removal of the spyware-infected file inetadpt.dll will end normal networking usage. Unlike users of numerous other operating systems, a typical Windows user has administrative privileges, mostly for ease of use. Because of this feature, any program the user runs (intentionally or not) has unrestricted access to the system, too. The prevalence of spyware, along with other threats, has led some Windows users to migrate to other platforms, such as Linux or Mac OS, which are significantly less susceptible to malware infections. These platforms do not allow any approved unrestricted access deeper into the operating system by default. As with other operating systems, Windows users are able to follow the principle of least amount of privilege and use nonadministrator least-access user accounts or reduce the privileges of specific vulnerable Internet-facing processes such as Internet Explorer. However, as this is not a default or “out-of-the-box” configuration, few users do this.
Advertisements
Many spyware programs infect victims with pop-up advertisements. Some programs simply display pop-up ads on a regular basis. For instance, some pop up every few minutes or when the user opens a new browser window, and some spyware programs will open dozens of ads within a given minute. Others display ads after the user visits a specific site, which is similar to targeted advertising. Spyware operators present this feature as desirable to advertisers, who may buy ad placement regarding specific consumer goods in pop-ups displayed when the user visits a particular site. It is also one of the reasons that spyware programs gather information on user behavior and surfing habits.
Many users grumble about annoying or offensive advertisements as well. As with countless banner ads, many spyware advertisements use animation or flickering banners that can be visually disturbing and annoying to users and, at times, make it unbearable to even surf the Internet. Pop-up ads for pornography often display erratically—and at the worst times (when your spouse brings you coffee). Links to these sites may be added to the browser window, history, or search function, which can later be examined by your employer or family. A number of spyware programs break laws, such as variations of the Zlob and Trojan-Downloader.Win32.INService, which have both been known to show undesirable child pornography sites that violate child pornography laws. This variant has also been known to pop up key-gens, cracks, and illegal software pop-up ads that violate copyright laws.
Another issue in the case of some spyware programs has to do with the substitution of banner ads on viewed websites. In some cases, certain spyware programs have been created specifically as Browser Helper Objects (BHOs) in order to record a user’s interactions quietly (keystrokes, pages surfed, and so on) during an SSL or HTTPS connection. Through this method of spyware-based BHOs, a criminal has direct access into anything you do while using Internet Explorer. The information that is recorded can also be sent anywhere on the Internet to be picked up and later analyzed, which could lead to some form of identity theft and/or fraud against the victim.
Spyware that uses BHO APIs can swap out references to a site’s own legitimate advertisements (which fund the site) with advertisements that a criminal has set up with a separate advertising firm, which give the spyware operator alternative funds to collect. This not only digs into the margins of advertising-funded websites, but can also be used to introduce seemingly innocent ads that later end up being drive-by-download malicious websites.
Adware/Spyware and Cookies
Anti-spyware and adware programs frequently report web advertisers’ HTTP cookies—small text files that follow browsing activity and are not in themselves spyware, but that are commonly used by spyware in order to get more information about victims prior to identity theft. Although cookies are not always innately malicious, many users object to third-party cookies using space on their personal computers for their (third-party) business purposes, and many anti-spyware programs offer to remove them. However, malware can also write its own cookies to the host hard disk in order to track a user’s browsing activity, which can later be used for identity theft and/or direct pop-up target advertising. Cookies in general are harmless and were created to help the user’s surfing experience, but when they are used to support criminal activity, they cross the threshold of helpful to hindrance. Cookies can track a number of surfing activities on the Internet:
• What advertisements have been viewed; this method can be used to ensure a user does not see the same advertisement twice.
• Which sites have been visited, which can also identify the sites a user is interested in visiting in order to learn more about that individual or organization.
• Information input into website forms to record personal information about a user. Over time enough personal information can be gathered to construct a sizable profile of the victim in order to steal his or her identity.
Adware/Spyware Examples
Here are a few examples of spyware programs that use cookies in order to record information about victims’ surfing habits. Adware and spyware can be categorized in families as far as functionality:
• AdwareWebsearch This is added to the victim’s IE toolbar and monitors the victim’s surfed sites and displayed advertisements from partner advertising firms.
• CoolWebSearch This program, with several dozen variants, has been one of the most dreaded types encountered in its time. It not only redirects your computer from the victim’s favorite sites, but also typically ends up at one of its advertising affiliate sites, taking your computer to a retail, electronic, gambling, or many other types of random sites. It does this by rewriting the victim’s host DNS file to direct DNS queries to the networks where these affiliates would look up faster.
• Gator Although I have not seen this tool in years, it is worth mentioning due to the concepts and lessons Gator provided us. This advertising program used to replace the banner advertisements of some pages with banners of their partnered affiliates. Gator was later sold to Claria Corporation, which changed the original model of Gator into several other smaller apps.
• Zlob This was an infamous Trojan for some time, as it would not only redirect your browser to numerous IT sites, but also download and quietly install and execute malicious applications on the victim’s computer.
Identifying Installed Malware
For this example let’s look at some of the locations where malware will typically install and run itself while trying to keep the victim from becoming aware of its presence. Most importantly, we are going to evaluate some of the reasons “why” it likes to hide in these locations and what impact it has on a victim’s computer. Keep in mind, however, that these are examples of where malware is commonly found on hosts and that each day new variants are improving and constantly changing in order to evade suspicion, detection, and removal.
Typical Install Locations
Almost all malware will install in similar directories in order to execute and propagate throughout a victim’s computer. These are some of the more common directories in which malware will install itself.
Windows Operating Systems
These are typical install locations where malware is found on Microsoft Windows (multiple versions):
• ApplicationData%Microsoft
• %System%[FileName].dll
• %Program Files%Internet Explorer[ FileName].dll
• %Program Files%Movie Maker[ FileName].dll
• %All Users Application Data%[ FileName].dll
• %Temp%[ FileName].dll
• %System%[ FileName].tmp
• %Temp%[ FileName].tmp
Unix/Linux Operating Systems
These are typical locations where malware is found on Unix/Linux operating systems (multiple builds):
• /bin/login
• /bin/.login
• /bin/ps
• /etc/
• /etc/rc.d/
• /tmp/
• /usr/bin/.ps
• /usr/lib/
• /usr/spool/
• /usr/scr/
Installing on Local Drives
Typically malware will attempt to install itself on every drive accessible on the host, whether to local or mapped network shares where the system has write permissions. Malware will install in the previously listed install paths on system partitions or in obfuscated file locations on any secondary partition available.
Modifying Timestamps
Malware will almost always modify its timestamp in order to hide from first-glance inspections.
Windows or Unix/Linux Operating Systems
Timestamps are universal file attributes, and malware on either operating system functions the same way. The chosen dates can match any timestamp on the victim’s computer ranging from
• System install dates
• System file dates
• A chosen date in time
Affecting Processes
Almost all malware will attempt to hook system and user processes in order to operate behind the scenes, become resilient to reboots and restarts, prevent itself from being stopped since these system and user processes and services are mandatory to the operation of the system, and prevent the victim from quickly identifying its activity.
Windows Operating Systems
These are typical system and user processes affected by malware found on Microsoft Windows (multiple versions):
• explorer.exe
• services.exe
• svchost.exe
• iexplorer.exe
Unix/Linux Operating Systems
These are some common processes modified on Unix/Linux operating systems (multiple builds):
• apached
• ftpd
• rpc.statd
• lpd
• syncscan
• update
Disabling Services
Typically, malware will attempt to disable specific operating-system features in order to continue to execute and propagate.
Windows Operating Systems
These are typical features malware attempts to disable on Microsoft Windows (multiple versions):
• Windows Automatic Update Service (wuauserv)
• Background Intelligent Transfer Service (BITS)
• Windows Security Center Service (wscsvc)
• Windows Defender Service (WinDefend)
• Windows Error Reporting Service (ERSvc)
• Windows Error Reporting Service (WerSvc)
Unix/Linux Operating Systems
These are some common services that are modified on Unix/Linux operating systems (multiple builds):
• apached
• ftpd
• rpc.statd
• lpd
• zssld
Modifying the Windows Registry
Here are some of the most common Registry locations where malware will install itself on a victim’s computer in order to execute and propagate:
• HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices
• HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersion
• HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsNTCurrentVersion
• HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersion
Summary
Malware and spyware today can do almost anything—target a single or multiple hosts and even target computers that are not directly networked within an enterprise. Malware can lead to varying levels of corporate and personal torture if and when information regarding your identity is stolen and used for other means. You need to be aware of the threats and goals and intent of malware in order to better combat its activity. With a better understanding of what malware does and how it can behave, your ability to protect your network from infection grows. Please use this information as a launch pad to learn more on a regular basis in order to understand and defend against the newest variants and their methods, intent, and functionality.


