What Is War Driving?
The act of war driving itself is simply going around looking for wireless networks. This activity is also called access point discovery, LAN-Jacking, WLAN mapping, etc. Some people have also coined the terms War Walking and War Flying by walking or flying around looking for APs. Remember that looking for wireless networks does not necessarily mean that you are hacking. It's more like driving around and looking at what color the houses are painted. The danger, of course, is that some unscrupulous individuals may, while looking at the color of the house, notice that the front door has been left open. These individuals may not be able to resist the temptation to enter the house (or network). Of course, for ethical security researchers, this is not a problem and one can simply remove the binding between TCP/IP and their WLAN NIC in order to ensure that leasing an IP is impossible and no network exploration could possibly occur. For more information on how to unbind your networking protocols, see: http://www.worldwidewardrive.org/nodhcp.html.
War Driving: How Does it Work?
Before we jump into the hardware and software you'll need for war driving, let's first learn how wireless networks are actually discovered.
Before you can associate with an AP, you must know its SSID, another way of saying a network name for the wireless network. In a way, you could think of war driving as looking for SSIDs.
There are two association methods in 802.11—open network and closed network. It's important to note that closed network is not part of the 802.11 standard, but many vendors have implemented it in their products (under a variety of names in their management interfaces). In essence, the difference between these methods is that with open network, the AP tells you its SSID. With closed network, the user must have previous knowledge of the SSID (presumably you have pre-configured the SSID in their laptop). While it may be tempting, please don't think of an SSID as a shared password because SSIDs are broadcast in clear text and can be easily picked out of the air.
Here's how the two association methods work: With open network, the AP broadcasts management beacons (usually every 100 milliseconds) to advertise the SSID, as well as other parameters needed to associate with the AP (supported speeds, signal strength, etc). The client listens for these beacons. Then, when it wants to associate, it sends out an association request. The AP responds with an association response (success or failure). It looks like Figure 4.1. For closed networks, the client has to have prior knowledge of the SSID (because you've somehow told them the name). So, the client sends out probe requests (across all channels), which include a specific SSID. When an AP hears this request, if the SSID matches its own, it will reply with a probe response (and include information similar to what is contained in a management beacon). If the SSID does not match, it will simply ignore the probe request. Note that some APs will respond to a probe request with an SSID of “any” (yes, setting the SSID to the word “any”). Figure 4.2 shows a closed network conversation.
Figure 4.1. 802.11 protocol open network association.

Figure 4.2. Closed network association.

Finding the AP
In an open network, discovering SSIDs is easy because all you have to do is listen for the management beacons (Figure 4.3).
Figure 4.3. Listening for management beacons.

In a closed network, you must get lucky and happen to be listening during a legitimate association to capture the SSID contained in the probe request/response negotiation (Figure 4.4).
Figure 4.4. Listening for legitimate associations.

On the other hand, let's say that the attacker gets impatient and doesn't want to wait around for a legitimate association. One attack he can launch is to send a forged disassociate frame to the wireless client (making it look like it came from the AP), as illustrated in Figure 4.5. Once the wireless client is disassociated, it will automatically attempt to reconnect to the AP. The attacker can then listen and capture the SSID in the ensuing reassociation process (Figure 4.6).
Figure 4.5. Step 1—The attacker sends a disassociate frame to the associated wireless client. This causes the client to disassociate.

Figure 4.6. Step 2—The wireless client reassociates, and this conversation is captured by the attacker, who can then determine the SSID.

Later in the chapter, we will discuss software packages you can use to discover SSIDs. Keep in mind that these packages all work differently. For example, NetStumbler uses a combination of listening for management beacons and sending out probe requests. This makes it somewhat noisy and will not allow it to pick up closed network APs. On the other hand, applications like Kismet operate in a truly promiscuous mode (like a sniffer) so they cannot be detected and will also pick up closed network APs if they happen to overhear a probe request/response conversation.
Getting the Right Gear
In order to build your own war driving system, you'll need to get the appropriate hardware and software. Keep in mind that each war driving software application has its own requirements for the type of hardware it uses. This is like saying that you need Windows 2000 or Macintosh OS X in order to run a certain program. In this case, the software makes function calls that are unique to a specific chipset so you need to make sure that you get the right hardware card (chipset) for the software that you want to use.
Hardware Options
The three most popular chipsets used in wireless network cards are Hermes (made by Lucent), Prism (Intersil), and Aironet (Cisco). What makes this even more confusing is that some manufacturers use different chipsets in different products. For example, the Compaq WL110 uses a Hermes chipset, but the Compaq WL100 uses Prism. In general, however, most manufacturers stick to a specific chipset line (Table 4.1). For more examples, see: http://seattlewireless.net/?HardwareComparison.
| Hermes (Lucent) | Prism (Intersil) | Aironet (Cisco) |
|---|---|---|
| Orinoco | D-Link | Cisco |
| Toshiba | Linksys | Xircom |
| Cabletron | SMC | Dell |
| Dell | Addtron | |
| Compaq WL110 | Compaq WL110 | |
| IBM | Netgear | |
| Apple | Gemtek | |
| Zoom | ||
| Samsung | ||
| Senao |
Tip
One of the most popular wireless cards is the Orinoco card which comes in three versions: Bronze, Silver, and Gold. These models refer to the level of WEP support inherent in the card. Bronze does not support WEP. Silver supports 64-bit WEP. Gold supports 128-bit WEP. Other than that, the cards are identical. Remember that for war driving (and WEP cracking) applications, you do not need a gold card. You can use a silver or bronze card and still use NetStumbler (described later) to detect 128-bit WEP encrypted networks. However, you will not be able to connect to those networks in 128-bit WEP mode. Another factor to consider when selecting a wireless card is whether or not it supports external antennae. An external antenna will greatly increase your range and improve your war driving results, particularly important in mobile applications because without an external antenna, you will be relying upon the antenna built into your PCMCIA card. If your laptop is indeed on your lap, the antenna will be poorly positioned to receive wireless signals. In fact, using a USB adapter with an identical receive sensitivity to a PCMCIA card will often provide better results because you can position the adapter (and its “antenna”) on the dashboard, instead of being tucked away inside your laptop next to the car door. Of course, the best solution is to use an external antenna, such as a 5 dBi omni with a magnetic mount (Figure 4.7). Figure 4.7. 5 dBi Magnetic mount Omni Antenna.
|
Antennae generally have a standard connector called an N connector. On the other hand, wireless cards generally use a proprietary connector. To be able to adapt the proprietary connector to an N connector, you will need to get a cable called a pigtail, a short cable (usually a foot or less) that will let you connect an external antenna to your particular card. Remember that each pigtail is different and you need to ask for the kind made specifically for your wireless card (Figures 4.8, 4.9, and 4.10).
Figure 4.8. Orinoco and Cisco cards with pigtails.

Figure 4.9. Closeup of Orinoco card and pigtail.

Figure 4.10. Closeup of Cisco card and pigtail.

The last area of hardware to consider is a Global Positioning System (GPS). As we will see in a moment, some war driving applications will support GPS. We use GPS to record the exact coordinates of the AP as it is discovered. This way, you can go back home and make a nice map showing the exact locations of the wireless networks you discovered by using the latitude and longitude coordinates provided by the GPS. When you are selecting a GPS unit, make sure that it has the ability to output NMEA-compatible data. Typically, this is done over a serial (DB9) or USB interface. Some GPS devices are external, self-contained units (for use with a laptop), as shown in Figure 4.11. Other devices are integrated jackets that are designed specifically for pocket PCs (Figure 4.12).
Figure 4.11. Sample external GPS device.

Figure 4.12. Sample integrated GPS device.

Software Options
The most popular war driving software is Network Stumbler (Figure 4.13), also known as NetStumbler. It was written by Marius Milner and runs on Windows. Both PC and PDA versions are available. NetStumbler requires a card based on the Hermes chipset and supports GPS. It's free and can be downloaded from http://www.netstumbler.com. The Web site, founded by Wayne and Brad Slavin, is an excellent source for wireless news and also has very active forums.
Figure 4.13. Netstumbler screen shot.

On the Linux side, Kismet (Figure 4.14) can be downloaded free from http://www.kismetwireless.net. There is a PC and PDA version available that supports both Prism and Aironet chipsets. It also supports GPS.
Figure 4.14. Kismet screen shots.

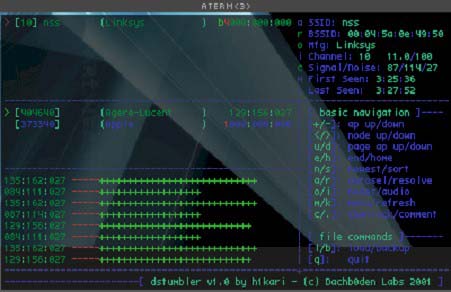
For BSD users, I highly recommend dstumbler (Figure 4.15), which is part of the bsd-airtools kit from Dachb0den Labs (http://www.dachb0den.com/projects/bsd-airtools.html). dstumbler works with NetBSD, OpenBSD, and FreeBSD using either Prism- or Hermes-based WLAN cards.
Figure 4.15. dstumbler screen shot.
If you're looking for a professional network discovery tool and you can afford the $3,495 price tag, you should consider using AirMagnet (http://www.airmagnet.com). It runs on the pocket PC platform (Figure 4.16) and there is also a laptop version available. For the money, AirMagnet has the best bells and whistles. The graphical interfaces display very useful and detailed info to help with site surveys and troubleshoot wireless networking problems.
Figure 4.16. Airmagnet.


