We can proceed with the following steps:
- In the case of WPA, the matter is a bit more complicated. The
iwconfigutility cannot be used with WPA/WPA2 Personal and Enterprise, as it does not support it. We will use a new tool calledwpa_supplicantfor this lab. To useWPA_supplicantfor a network, we will need to create a configuration file, as shown in the following screenshot. We will name this filewpa-supp.conf: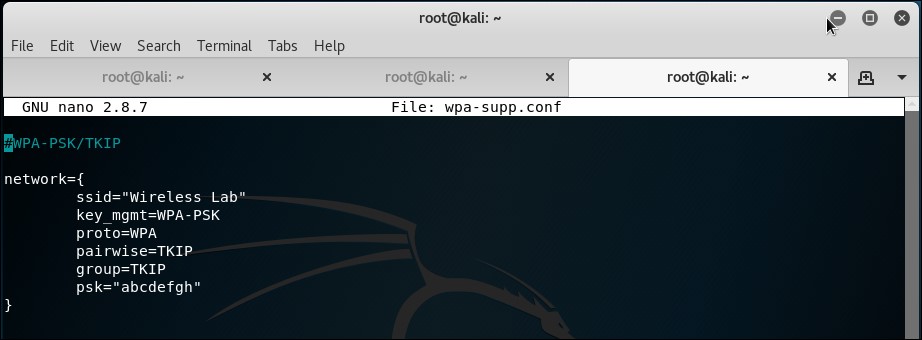
- We will then invoke the
wpa_supplicantutility with the following command:wpa_supplicant -D wext -i wlan0 -c wpa-supp.conf - This will connect the device to the WPA network we just cracked. Once the connection is successful,
wpa_supplicantwill give you the message: Connection to XXXX completed. - For both the WEP and WPA networks, once you are connected, you can use
dhclientto grab a DHCP address from the network by typingdhclient3 wlan0.
The default Wi-Fi utility iwconfig cannot be used to connect to WPA/WPA2 networks. The de-facto tool for this is wpa_supplicant. In this lab, we saw how we can use it to connect to a WPA network.
Q1. What packets are used for packet replay?
- Deauthentication packet
- Associated packet
- Encrypted ARP packet
- None of the above
Q2. When can WEP be cracked?
- Always
- Only if a weak key/passphrase is chosen
- Under special circumstances only
- Only if the access point runs old software
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
