"The loftier the building, the deeper the foundation must be laid." | ||
| --Thomas Kempis | ||
Nothing great can be built on a weak foundation, and in our context, nothing secure can be built on something that is inherently insecure.
WLANs, by design, have certain insecurities that are relatively easy to exploit, for example, by packet spoofing, packet injection, and sniffing (this could even happen from far away). We will explore these flaws in this chapter.
In this chapter, we shall look at the following:
- Revisiting WLAN frames
- Different frame types and subtypes
- Using Wireshark to sniff management, control, and data frames
- Sniffing data packets for a given wireless network
- Injecting packets into a given wireless network
Let's get started!
As this book deals with the security aspects of wireless, we will assume that you already have a basic understanding of the protocol and the packet headers. If not, or if it's been some time since you worked on wireless, this would be a good time to revisit this topic again.
Let's now quickly review some basic concepts of WLANs that most of you may already be aware of. In WLANs, communication happens over frames. A frame would have the following header structure:
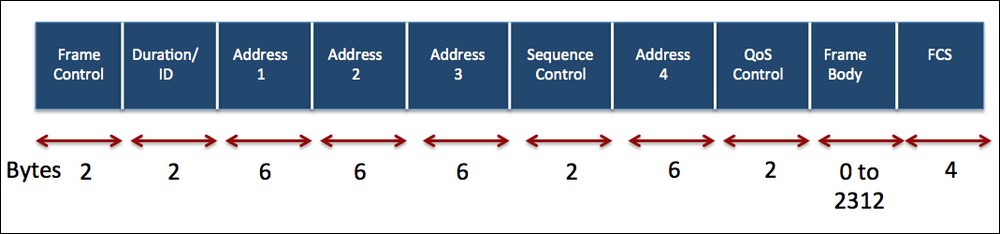
The Frame Control field itself has a more complex structure:

The Type field defines three types of WLAN frame:
- Management frames: Management frames are responsible for maintaining communication between access points and wireless clients. Management frames can have the following subtypes:
- Authentication
- Deauthentication
- Association request
- Association response
- Reassociation request
- Reassociation response
- Disassociation
- Beacon
- Probe request
- Probe response
- Control frames: Control frames are responsible for ensuring a proper exchange of data between access points and wireless clients. Control frames can have the following subtypes:
- Request to Send (RTS)
- Clear to Send (CTS)
- Acknowledgement (ACK)
- Data frames: Data frames carry the actual data that is sent on the wireless network. There are no subtypes for data frames.
We will discuss the security implications of each of these frames when we discuss different attacks in later chapters.
We will now look at how to sniff these frames over a wireless network using Wireshark. There are other tools—such as Airodump-NG, Tcpdump, or Tshark—that you can use for sniffing as well. We will, however, mostly use Wireshark in this book, but we encourage you to explore other tools as well. The first step to do this is to create a monitor mode interface. This will create an interface for our adapter, which allows us to read all wireless frames in the air, regardless of whether they are destined for us or not. In the wired world, this is popularly called promiscuous mode.
