"Disregard mountains. Acquire empires" | ||
| --Hannibal (probably) | ||
This chapter discusses the recently identified KRACK vulnerabilities and explores the current state of the tools that enable the identification of vulnerable devices. This chapter is a deep dive into the inner workings of the WPA2 handshake and is recommended for advanced readers.
KRACK stands for Key Reinstallation AttaCKs. It's a tranche of vulnerabilities publicly disclosed in October 2017 by a team from KU Leuven. The attack is the exploitation of a fundamental flaw in the WPA2 handshake, allowing resending of a stage of the handshake in order to overwrite cryptographic data. This chapter will cover the attack at a theoretical level and provide some guidance on the successful identification and exploitation of this vulnerability.
Let's look at the WPA2 handshake, the standard for which can be found in the IEEE 802.11 standards, accessible here: http://ieeexplore.ieee.org/document/7792308/. For this explanation we are starting post-association and authentication stage as the vulnerability is not affected by those.
The Pairwise Transient Key (PTK) used for encryption is made up of five attributes:
- A shared secret key known as the Pairwise Master Key (PMK)
- A nonce value created by the access point (ANonce)
- A nonce value created by the user station (SNonce)
- The access point MAC address (APMAC)
- The user station MAC address (STAMAC)
Throughout the process, Message Identification Codes (MIC) are used to provide a level of integrity and security. While these are integral to the process, they are not used in the resulting cryptographic data. Here's a representation:
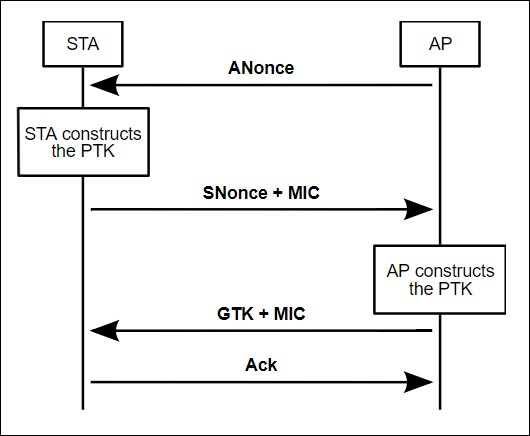
At this time, as a result of the initial authentication and association process, both the user station and the access point have the PMK, the access point MAC address, and the user station MAC address. In addition, each stage will have a Key Replay Counter keeping track of the order of packets; this will come into play later:
- Stage 1: The access point transmits the ANonce value to the user station, which provides the user station with everything it needs to generate the PTK. The user station creates the PTK and now holds the key it will use for encryption.
- Stage 2: The user station sends back its own nonce value along with a MIC. The access point now holds everything that it needs to create the PTK. The access point creates the PTK and is in the same state as the user station.
- Stage 3: The access point creates and sends the Group Temporal Key (GTK) to the user, which enables the reading of non-directed traffic such as multicast/broadcast traffic.
- Stage 4: The user station returns an acknowledged statement.
Following the four-stage handshake, the user station can now send encrypted data to the access point and have it accepted. At this point, the negotiation phase is complete and the user station is free to use the network.
