Follow the given instructions to get started:
- We double-check the
eap.conffile to ensure that PEAP is enabled: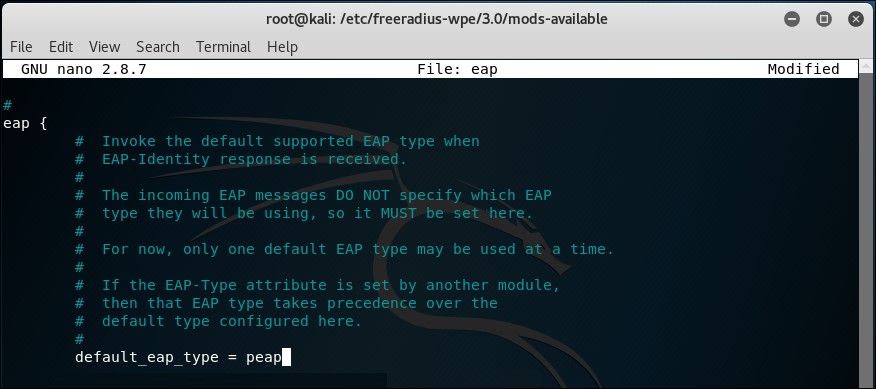
- We then restart the RADIUS server with
freeradius-wpe –s –X: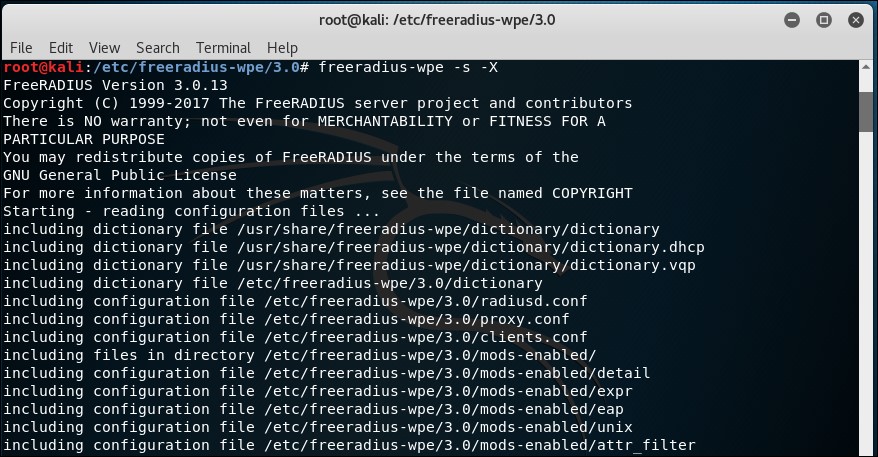
- We monitor the log file created by FreeRADIUS-WPE:
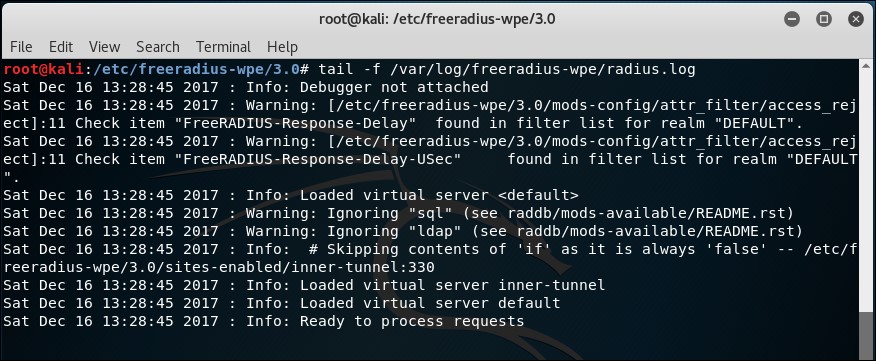
- Windows has native support for PEAP. Let's ensure that certificate verification has been turned off:
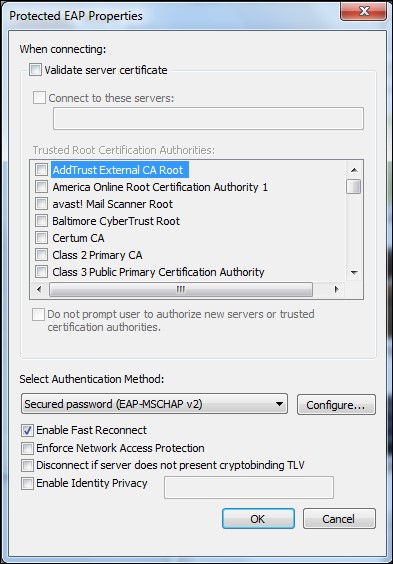
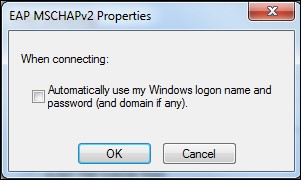
- We need to click on the Configure tab that is next to Secured password (EAP-MSCHAP v2) and tell Windows not to automatically use our Windows logon name and password:
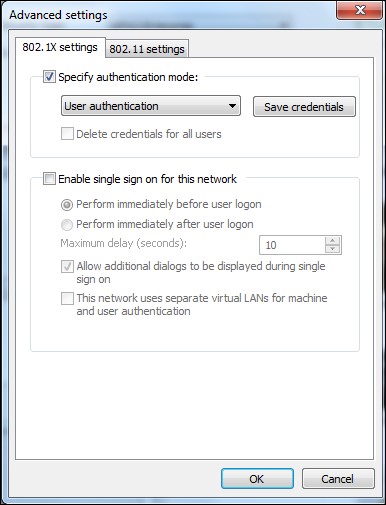
- We will also have to force it to select User authentication in the Advanced Settings dialog box:
- Once the client connects to the access point, the client is prompted for a username and password. We use
Monsteras the username andabcdefghias the password: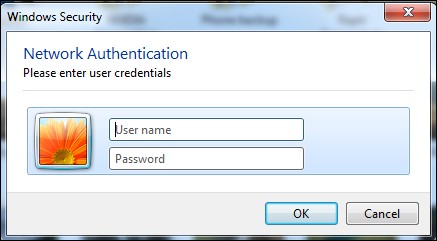
- As soon as we do this, you should be able to see the MSCHAP-v2 challenge response appear in the log file.
- We now use
asleapto crack this using a password list file that contains the passwordabcdefghi, and we are able to crack the password!
We set up our Honeypot using FreeRADIUS-WPE. The enterprise client is misconfigured to not use certificate validation with PEAP. This allows us to present our own fake certificate to the client, which it gladly accepts. Once this happens, MSCHAP-v2, the inner authentication protocol, kicks in. As the client uses our fake certificate to encrypt the data, we are easily able to recover the username, challenge, and response tuples.
MSCHAP-v2 is prone to dictionary attacks. We use asleap to crack the challenge and response pair, as it seems to be based on a dictionary word.
PEAP can be misconfigured in multiple ways. Even with certificate validation enabled, if the administrator does not mention the authentic servers in connect to these servers list, the attacker can obtain a real certificate for another domain from any of the listed certifying authorities. This will still be accepted by the client. Other variations of this attack are possible as well.
We will encourage you to explore the different possibilities in this section.
