On a LAN, it's normal to see ARP request/reply messages. However, when there is a large number of ARP requests, as shown in the following screenshot, this is an indication of an ARP storm, which is a form of Denial of Service (DoS) attack:
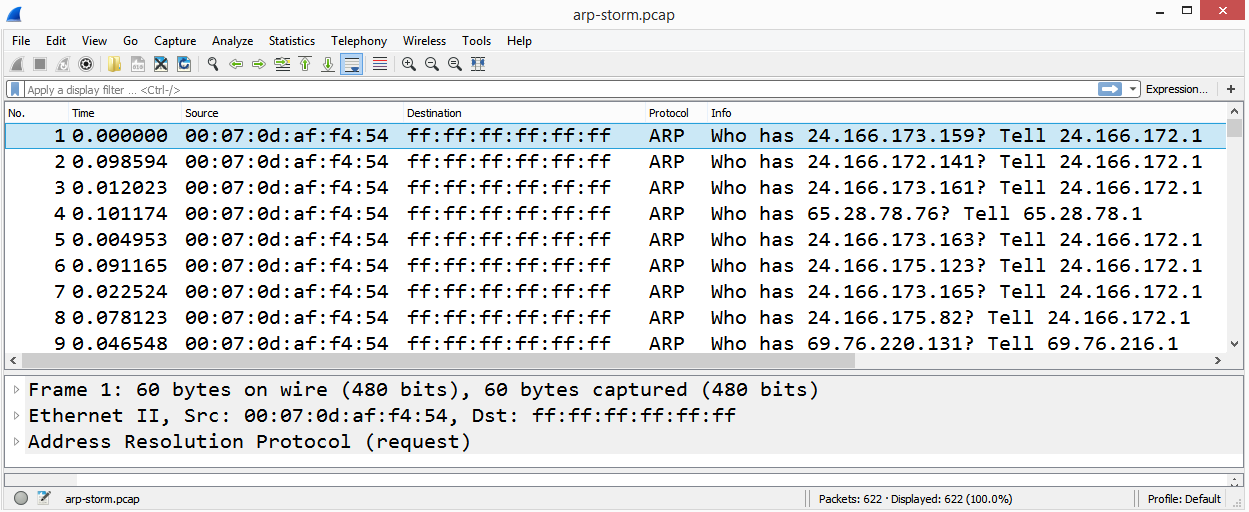
Let's step through how an ARP storm works:
- In order to efficiently deliver data, a switch uses a Content Addressable Memory (CAM) table that contains pairings of MAC addresses and their associated physical switch ports.
- An ARP storm floods the CAM table and overwhelms the switch with thousands of bogus entries.
- At that point, the switch simply acts as a hub and sends data out all of the ports, which can do the following:
- Allow sniffing with the possible exposure of sensitive data.
- Prevent the network from functioning normally.
As you can see, an ARP storm is possible. In Wireshark, you can monitor for ARP storms. To modify this, go to the ARP preferences by selecting an ARP header, right-click, and select Protocol Preferences | Open Address Resolution Protocol Preferences…, which will display the following screenshot:

Once in the Preferences menu, you can modify the following:
- Number of requests to detect during period: Enter an appropriate value, for example, 30 requests
- Detection period (in ms): Enter an appropriate value, for example, 100 ms
Although Wireshark can't prevent an ARP storm, it can help you identify a potential attack.
We now know that there are attacks such as spoofing and storming. How are these attacks launched? The following section outlines some of the tools that are available to launch an ARP attack on a LAN.
