Even though the case is still being loaded and Ingest Modules being run (as seen by the progress bar in the bottom right of the previous screenshot), an examiner can begin analyzing the case. Expanding the image file in the upper-left corner will show partitions/volumes identified by Autopsy:

Autopsy identified 28 partitions on our device. To find the data partition (since we know that's where the vast majority of the data we are interested in is stored), we can simply expand the allocated partitions until we find one that looks like the data partition:

In our image, volume 27 is the data partition. We can see it has an app directory (where APK files are stored), a data directory (where app data is stored), and a media directory (the symbolically linked location for the SD card).
Expanding the data directory will reveal information we should remember from Chapter 7, Forensic Analysis of Android Applications:

Right away, we can see com.android.providers.telephony and userdictionary. How to analyze these applications is covered in Chapter 7, Forensic Analysis of Android Applications; this is how to access the relevant files using Autopsy. For example, expanding com.android.providers.telephony will show the mmssms.db file needed to analyze SMS and MMS data:
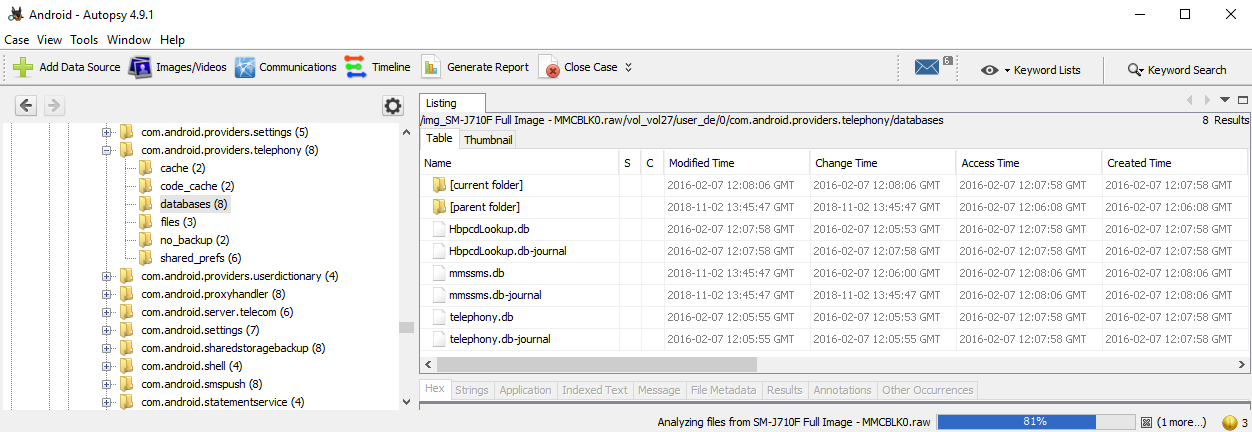
The Application tab lets the examiner view SQLite databases in a built-in viewer:

Now, let's take a look at the rest of Autopsy's features. Expanding the Views section on the left side of the screen will show results from a few of the Ingest Modules used:

The File Types view shows files identified by the File Type Identification module. Recent Files shows the results from the Recent Activity module; in this case it appears the device wasn't used for six days, then was used on the Final Day. Viewing the files identified here can show the user's activity in that time period. Note the red X, which indicates that some of these files were deleted but recovered by Autopsy:
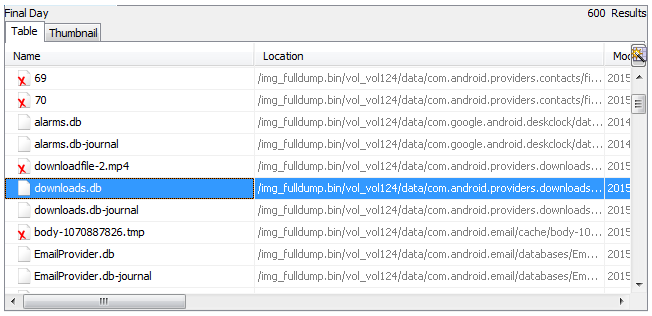
In our case, we can see that the downloads.db and EmailProvider.db databases were modified. Analyzing these files would show that an email with an attachment was received, and the attachment was then downloaded to the device.
Finally, the Views section identifies deleted files (which are very common on mobile devices as a result of wear-leveling), as well as large files (which can be useful for quickly finding images/video, or identifying steganography).
The Results section will show the output from the Android Analyzer and Keyword Search modules:

The Android Analyzer results seen under Extracted Content were mostly as expected. It is worth noting that the Contacts (1) section only points to the contacts.db file, and did not actually parse data from it. For example, the Call Logs displays data pulled from contacts2.db, as described in Chapter 7, Forensic Analysis of Android Applications:

The Extension Mismatch Detected results also show data we found in Chapter 7, Forensic Analysis of Android Applications. Several apps were described as having .cnt files that were actually JPEG images, and these were appropriately identified by Autopsy:

Double-clicking on any of these files will take the user to the location where the file was found in the filesystem.
The Keyword Hits section appropriately found many email addresses and phone numbers, however many of these were found within application files (that is, contact information for the developer of the app) and other places that were not actually stored by the user (this is very common with both mobile and computer forensic tools).
There are many other, more advanced, features of Autopsy that aren't covered here; to learn more, basis technology offers an Autopsy training course: https://www.autopsy.com/training/.
