An easier and more efficient approach is to use pre-built sandboxes for malware analysis. One of these sandboxes is Joe Sandbox. It supports automated dynamic analysis of different types of applications, including Windows, macOS, Linux, iOS, and of course Android. You can register for a free account and enable 10 free analyses per month. The sandbox for Android applications can be accessed here: https://www.joesandbox.com/#android.
Only a few simple steps are required to run an application in the sandbox:
- First, choose the file you want to analyze using the Choose file... button.
- Adjust the run time; you can run the application in the sandbox from 30 to 500 seconds
- Accept the terms and conditions, and click the Analyze button.
Once the analysis is complete, you will receive an email with a link to the analysis results. In our case, it was https://www.joesandbox.com/analysis/67297.
Let's walk through the HTML report and discuss its most important parts.
Joe Sandbox has its own detection mechanism based on automated analysis results. In our case, the sample got 72 points out of 100 and is classified as malicious:

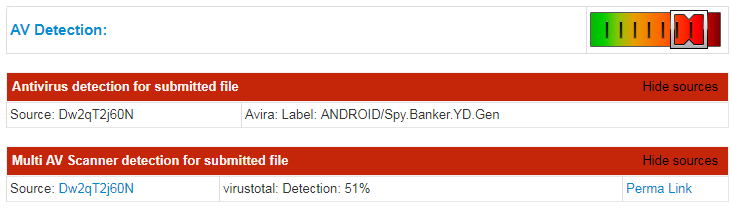
It also uses antivirus engines and VirusTotal to scan the uploaded sample. According to the report, our sample is detected as ANDROID/Spy.Banker.YD.Gen by Avira, and is also detected by 51% of antivirus engines on VirusTotal, as shown in the following screenshot:
According to the next section, our sample attempted to escalate its privileges, requesting root rights via running a su command, and then tried to add a new device administrator:

Let's look at the Networking section. It seems our sample attempted to download a new APK file, new.apk, from www.poog.co.kr, but failed to do so as the file was unavailable:

Another interesting section is E-Banking Fraud. Our sample contains package name strings related to banking; they may be used for the detection of banking applications installed on the device. Also, it is able to add an overlay to other applications, and has permission to list currently running applications:

The next section shows that the analyzed application requested permissions to perform phone calls in the background, send SMS, and write to SMS storage. Also, it's able to send SMS using SmsManager and end incoming calls; this is typical for banking Trojans:

The System Summary section shows us a list of potentially dangerous permissions our sample requested:

Let's look at each of them closely:
- CALL_PHONE: Allows an application to initiate phone calls
- GET_TASKS: Allows an application to collect information about currently running applications
- INTERNET: Allows an application to open network sockets
- READ_CONTACTS: Allows an application to read contacts data
- READ_PHONE_STATE: Allows an application to access phone state in read-only mode, including phone number and cellular network information
- READ_SMS: Allows an application to read SMS
- RECEIVE_SMS: Allows an application to receive SMS
- SEND_SMS: Allows an application to send SMS
- SYSTEM_ALERT_WINDOW: Allows an application to create windows shown on top of all other applications
- WAKE_LOCK: Allows an application to keep the processor from sleeping or the screen from dimming
- WRITE_CONTACTS: Allows an application to write contact data
- WRITE_EXTERNAL_STORAGE: Allows an application to write to external storage, for example, an SD card
- WRITE_SETTINGS: Allows an application to read or write the system settings
- WRITE_SMS: Allows an application to write SMS stored on the phone or its SIM card, or delete them
We already know that our sample attempted to download an APK file. If we look at the Persistence and Installation Behavior section, we see that it is able not only to download applications, but also to install them:

To survive reboots, the sample requested permission to execute the code after the phone is rebooted (RECEIVE_BOOT_COMPLETED), created a new wake lock to have the device stay on, and was able to start a service for autostart purposes:

Let's dive into the Hooking and other Techniques for Hiding and Protection section. The sample is able to abort broadcast events; it helps malicious application to hide phone events, such as incoming SMS:

Another interesting piece of information here is that our sample requested permission to terminate background processes:

The Language, Device and Operating System Detection section shows that the sample collects information about the SIM provider country code, service provider name, mobile country code, mobile network code, WiFi MAC address, voicemail number, operating system version, and unique device IDs, such as International Mobile Equipment Identity (IMEI), Mobile Equipment IDentifier (MEID), and Electronic Serial Number (ESN):
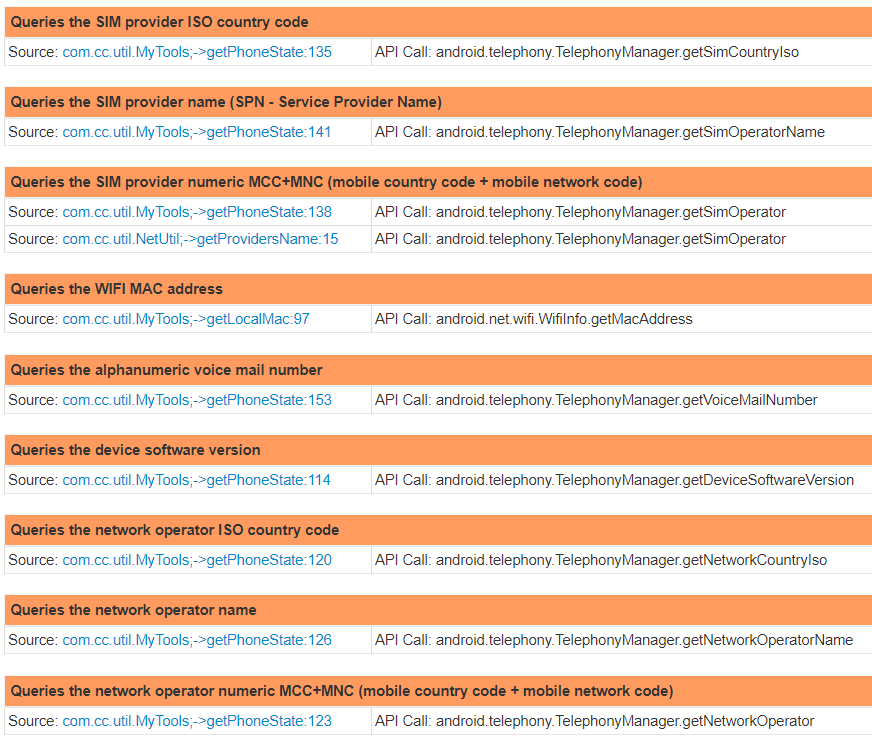
The following screenshot shows the unique device IDs collected by the sample:

The next section shows that the application monitors outgoing phone calls, is able to create SMS data, and checks whether a SIM card is installed:

What is more, it monitors incoming phone calls and reads originating phone numbers, parses SMS (body and originating number), and queries the list of installed applications and packages:

Finally, if we look at the URLs subsection of the Antivirus Detection section, we see that the APK file that our sample attempted to download was detected as malicious by Avira URL Cloud:

You may have noticed that there are more URLs in the previous screenshot; these are potentially malware command and control servers.
To sum up, let's gather together the pieces of information we got from the dynamic analysis of our sample with Joe Sandbox:
- Based on antivirus detection and the artefacts we have uncovered, the piece of malware we analyzed is a banking Trojan.
- It's able to download additional pieces of malware from www.poog.co.kr.
- It collects information about banking-related applications.
- It is able to add an overlay to other applications.
- It is able to monitor incoming and outgoing calls, read and write SMS messages, and intercept them.
- It is able to terminate the processes of other applications.
- It's able to collect information about the device it's running on.
- It requests permission to execute the code after the phone is rebooted for persistence.
- It potentially uses http://rtrjkrykki.iego.net/appHome/ or http://192.151.226.138:80/appHome/ as a command and control server.
The next sections will walk you through the steps required to perform static analysis of Android malicious applications.
