Chapter 11. Windows Server 2016 Network Policy Server
This chapter covers the following subjects:
![]() Implementing RADIUS: This chapter explains the overall purpose and scenarios for RADIUS servers, proxies and clients, and use of both the RADIUS protocol and Windows Server 2016 Network Policy Servers (NPS) to implement RADIUS solutions.
Implementing RADIUS: This chapter explains the overall purpose and scenarios for RADIUS servers, proxies and clients, and use of both the RADIUS protocol and Windows Server 2016 Network Policy Servers (NPS) to implement RADIUS solutions.
![]() Implementing RADIUS proxy: This chapter examines different scenarios for using Windows Server 2016 NPS as a RADIUS proxy.
Implementing RADIUS proxy: This chapter examines different scenarios for using Windows Server 2016 NPS as a RADIUS proxy.
![]() Implementing RADIUS clients: You learn how to configure a Windows Server 2016 VPN server as a RADIUS client with the NPS console, Routing and Remote Access console, or PowerShell commands (with the learning focus on PowerShell commands).
Implementing RADIUS clients: You learn how to configure a Windows Server 2016 VPN server as a RADIUS client with the NPS console, Routing and Remote Access console, or PowerShell commands (with the learning focus on PowerShell commands).
![]() Configuring NPS templates: This chapter explains the elements and use of NPS templates and demonstrates how you can use them to reduce time and cost efforts when you have to configure multiple NPS servers.
Configuring NPS templates: This chapter explains the elements and use of NPS templates and demonstrates how you can use them to reduce time and cost efforts when you have to configure multiple NPS servers.
![]() Configuring RADIUS Accounting: You can configure a Windows Server 2016 NPS server for RADIUS Accounting so that the NPS server logs accounting information to log files on the local hard disk or on a Microsoft SQL Server database.
Configuring RADIUS Accounting: You can configure a Windows Server 2016 NPS server for RADIUS Accounting so that the NPS server logs accounting information to log files on the local hard disk or on a Microsoft SQL Server database.
![]() Certificates: This chapter discusses the use of certificates for Windows Server 2016 NPS servers. It tells which authentication methods are dependent on which kind of certificates, explains the differences in certificate-based authentication methods, and shows how to configure certificate templates for EAP/PEAP.
Certificates: This chapter discusses the use of certificates for Windows Server 2016 NPS servers. It tells which authentication methods are dependent on which kind of certificates, explains the differences in certificate-based authentication methods, and shows how to configure certificate templates for EAP/PEAP.
![]() Connection request policies: Connection request policies are condition sets and settings that allow administrators to designate which RADIUS servers do the authentication and authorization of connection requests that a Windows Server 2016 NPS server receives from RADIUS clients.
Connection request policies: Connection request policies are condition sets and settings that allow administrators to designate which RADIUS servers do the authentication and authorization of connection requests that a Windows Server 2016 NPS server receives from RADIUS clients.
![]() Network Policies for VPN wireless and wired clients: In this chapter, you learn about creating Windows Server 2016 NPS Network Policies and using network policy categories. You also explore the ordering of Network Policies, network policy key settings, and configuration of NPS for VLANs.
Network Policies for VPN wireless and wired clients: In this chapter, you learn about creating Windows Server 2016 NPS Network Policies and using network policy categories. You also explore the ordering of Network Policies, network policy key settings, and configuration of NPS for VLANs.
![]() Importing and exporting NPS policies: You can export Windows Server 2016 NPS Network Policies, connection request policies, and shared secrets for RADIUS clients and members of RADIUS server groups for a Windows Server 2016 NPS server.
Importing and exporting NPS policies: You can export Windows Server 2016 NPS Network Policies, connection request policies, and shared secrets for RADIUS clients and members of RADIUS server groups for a Windows Server 2016 NPS server.
This chapter covers the overall purpose and scenarios for RADIUS servers, proxies and clients, and the RADIUS protocol and Windows Server 2016 Network Policy Servers (NPS) for implementing RADIUS solutions. It describes how to configure NPS UDP port information, to forward connection requests to another NPS server or RADIUS server, register NPS servers in Active Directory, and configure a Windows Server 2016 VPN server as a RADIUS client.
In addition, the chapter covers different scenarios using Windows Server 2016 NPS as a RADIUS proxy. It shows how to configure a Windows Server 2016 VPN server as a RADIUS client with the NPS console, Routing and Remote Access console, or PowerShell commands (with a learning focus on PowerShell commands). You also learn in this chapter how to configure a Windows Server 2016 DirectAccess server as a RADIUS client and how to plan and configure OTP certificate templates.
Furthermore, you learn about using NPS templates to reduce time and cost efforts when you have to configure multiple NPS servers. To pass the exam, you must know how to configure a Windows Server 2016 NPS server for RADIUS Accounting so that the NPS server logs accounting information to log files on the local hard disk or on a Microsoft SQL Server database. You also have to learn the different NPS Accounting options and differences, how to use certificates for Windows Server 2016 NPS servers, and which authentication methods are dependent on which kinds of certificates.
This chapter explains the differences in certificate-based authentication methods and shows how to configure certificate templates for EAP/PEAP. You learn about connection request policies, condition sets and settings that allow administrators to designate which RADIUS servers do the authentication and authorization of connection requests that a Windows Server 2016 NPS server receives from RADIUS clients.
This chapter also covers the default connection request policies, details how to create new connection requests and Network Policies, and discusses the main connection request policy tasks. (Important: At the time of writing this book, no PowerShell cmdlets existed to create or manage connection requests or Network Policies.)
The key topic selections, memory tables, key term definitions, and exam preparation questions give you powerful tools to increase your knowledge about Windows Server 2016 Network Policy Server for the Microsoft exam 70-741 and your work.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter or simply jump to the “Exam Preparation Tasks” section for review. If you are in doubt, read the entire chapter. Table 11-1 outlines the major headings in this chapter and the corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and End-of-Chapter Review Questions.”
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. You are responsible for configuring a Windows Server 2016 NPS server named NPS1 in the forest pearson.com. You have another forest named pearsonucertify.com. You want NPS1 to have permissions to read dial-in properties of pearsonucertify.com user accounts. Which configuration step accomplishes this?
a. Add NPS1 to the RAS and IAS Servers security group of pearsonucertify.com.
b. Add NPS1 to the RAS and IAS Servers security group of pearson.com.
c. Register nps2.pearsonucertify.com on pearsonucertify.com and replicate NPS server configuration settings from NPS1 to NPS2.
d. Use the Azure AD Connect tool to synchronize pearsonucertify.com user accounts to Microsoft Azure and register NPS1 on Azure AD.
2. You are responsible for implementing a Windows Server 2016 NPS server as a RADIUS server and RADIUS proxy. Which configuration setting do you have to configure?
a. Use the default connection request policy.
b. Create a new proxy connection request policy and move it to the top in the ordered list.
c. Create a new proxy connection request policy and move it under the default connection request policy in the ordered list.
d. Create a new network policy to forward requests to RADIUS server.
3. You must configure a Windows Server 2016 VPN server named VPN1 as a RADIUS client so that connection requests are forwarded to a Windows Server 2016 RADIUS server named R1. The VPN server feature is installed on VPN1. Local NPS is not installed on VPN1. External RADIUS Accounting is enabled on VPN1. Which PowerShell cmdlets can you use to configure this? (Choose two.)
a. On VPN1, use Add-RemoteAccessRadius.
b. On VPN1, use Add-WindowsFeature NPAS.
c. On R1, use New-NpsRadiusClient.
d. On VPN1, use New-NpsRadiusClient.
4. You are responsible for planning the implementation of 200 Windows Server 2016 VPN servers as RADIUS clients and 12 Windows Server 2016 servers as RADIUS servers in different sites of your network environment. Which kinds of settings can you preconfigure through NPS templates? (Choose four.)
a. Shared secrets
b. Network policy conditions
c. SQL Server logging settings
d. RADIUS clients
e. IP filters
f. RADIUS authentication/accounting port numbers
g. Remote RADIUS servers
5. Your Windows Server 2016 NPS server works as a RADIUS server. It stops processing connection requests and prevents users from accessing network resources. The NPS server is configured to use local NPS log files. Which configuration can prevent such problems? (Choose three.)
a. Keep NPS log files separate from the system partition.
b. Use an NPS replica server.
c. Use a RADIUS server group.
d. Use SQL logging instead of NPS log files.
6. You want to configure your Windows Server 2016 NPS server to allow VPN clients to connect through the PEAP authentication method. Which components do you have to prepare to make that possible? (Choose four.)
a. Network policy condition: NAS Port Type: Virtual (VPN)
b. Network policy condition: Service Type
c. Network policy constraint: Authentication Methods
d. Network policy constraints: NAS Port Type
e. PEAP certificate template and certificate
f. Encrypted shared secret
g. Type of network access server
7. You have to create a new connection request policy on your Windows Server 2016 NPS server. Which two configuration options are not viable solutions for this task? (Choose two.)
a. New-NpsConnectionRequestPolicy
b. New Connection Request Policy Wizard
c. NPS Getting Started Standard Configuration
d. NPS templates
8. Which RADIUS attributes do you have to use in a network policy for wireless connectivity on your Windows Server 2016 NPS server to identify VLAN membership as criteria, to define whether a user is allowed or denied authentication? (Choose three.)
a. Tunnel-Medium-Type
b. Tunnel-Pvt-Group-ID
c. Tunnel-Server-Auth-ID
e. Login-LAT-Group
f. Tunnel-Type
9. You want to replicate Network Policies and connection request policies from a Windows Server 2016 NPS server named NPS1 to another Windows Server 2016 NPS server named NPS2. Which PowerShell cmdlets can you use to accomplish this? (Choose two.)
a. Export-BinaryMiLog
b. Export-ScheduledTasks
c. Export-NpsConfiguration
d. Import-NpsConfiguration
e. Export-Clixml
f. Import-Clixml
Foundation Topics
Implementing RADIUS

With the use of a RADIUS server, you can collect and maintain network access user authentication, authorization, and accounting data in a central location.
A Windows Server 2016 RADIUS server manages centralized connection, authentication, and authorization. Organizations that maintain network access, such as ISPs, must manage a variety of network access methods from a single administration point, regardless of the type of network access equipment they use.
The RADIUS standard supports this requirement. RADIUS is a client/server protocol that enables network access equipment, used as RADIUS clients, to submit authentication and accounting requests to a RADIUS server.
You can use Windows Server 2016 NPS as a RADIUS server in these scenarios (see Figure 11-1):
![]() Using a domain or local SAM user accounts database as a user account database for clients.
Using a domain or local SAM user accounts database as a user account database for clients.
![]() Using Remote Access on multiple dial-up servers, VPN servers, or demand-dial routers. You want to centralize both the configuration of Network Policies and connection logging and accounting.
Using Remote Access on multiple dial-up servers, VPN servers, or demand-dial routers. You want to centralize both the configuration of Network Policies and connection logging and accounting.
![]() Outsourcing dial-up, VPN, or wireless access to a service provider. The access servers can use RADIUS to authenticate and authorize connections that are made by members of your organization.
Outsourcing dial-up, VPN, or wireless access to a service provider. The access servers can use RADIUS to authenticate and authorize connections that are made by members of your organization.
![]() Centralizing authentication, authorization, and accounting for a heterogeneous set of access servers.
Centralizing authentication, authorization, and accounting for a heterogeneous set of access servers.
Tip
What is the RADIUS client? Clients such as wireless portable computers and other computers running client operating systems are not the RADIUS clients. RADIUS clients are network access servers such as wireless access points, 802.1X-capable switches, and VPN and dial-up servers because they use the RADIUS protocol to communicate with RADIUS servers such as Windows Server 2016 NPS servers.
By default, Windows Server 2016 NPS listens for RADIUS traffic on ports 1812, 1813, 1645, and 1646 for both IPv6 and IPv4 for all installed network adapters. However, many access servers use ports 1645 for authentication requests and 1646 for accounting requests. No matter which port numbers you decide to use, make sure that NPS and your access server are configured to use the same ones. To configure NPS UDP port information, you can do the following steps:
Step 1. Open the NPS console.
Step 2. Right-click Network Policy Server, and then click Properties.
Step 3. Click the Ports tab and examine the settings for the ports. If your RADIUS authentication and RADIUS Accounting UDP ports vary from the default values provided (1812 and 1645 for authentication, and 1813 and 1646 for accounting), type your port settings in Authentication and Accounting.
Step 4. To use multiple port settings for authentication or accounting requests, separate the port numbers with commas.
The Windows Server 2016 Network Policy Server (NPS) is part of the Network Policy and Access Services server role. Figure 11-2 shows the installed Network Policy and Access Service (NPAS) role.
You can use a Windows Server 2016 NPS server as a RADIUS server, client, or proxy to forward connection requests to another NPS server or RADIUS server.
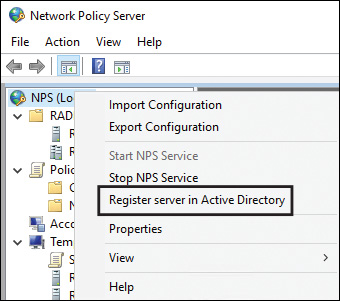
Registering the NPS Server in Active Directory

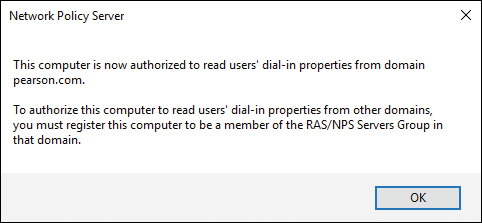
A Windows Server 2016 NPS server should be registered in Active Directory (see Figure 11-3). The RADIUS server must have access to the user account information in Active Directory.
You can register the NPS server using the NPS console (see Figure 11-4), but you also can do so through the command prompt with the command netsh ras add registeredserver. In addition, you can add the computer account of the NPS server as a member of the RAS and IAS Servers computer security group to register the NPS server in Active Directory.
Figure 11-5 shows the default message after successful registration of the NPS server in Active Directory. Membership in the Domain Admins security group (or equivalent) is the minimum required to complete this procedure.
A Windows Server 2016 NPS as a RADIUS server can verify network access authentication credentials. If the user’s credentials are approved and RADIUS authorizes the connection attempt, the RADIUS server authorizes the user’s access based on configured conditions. It also logs the network access connections in an accounting log.
When the NPS server is a member of a domain, it performs authentication by comparing user credentials that it receives from network access servers with the credentials that are stored for the user account in AD DS. In addition, NPS authorizes connection requests by using Network Policies and by checking user account dial-in properties in AD DS.
When using Windows Server 2016 Network Policy Server as a RADIUS server, you configure network access servers, such as wireless access points and VPN servers, as RADIUS clients.
RADIUS Client Configuration

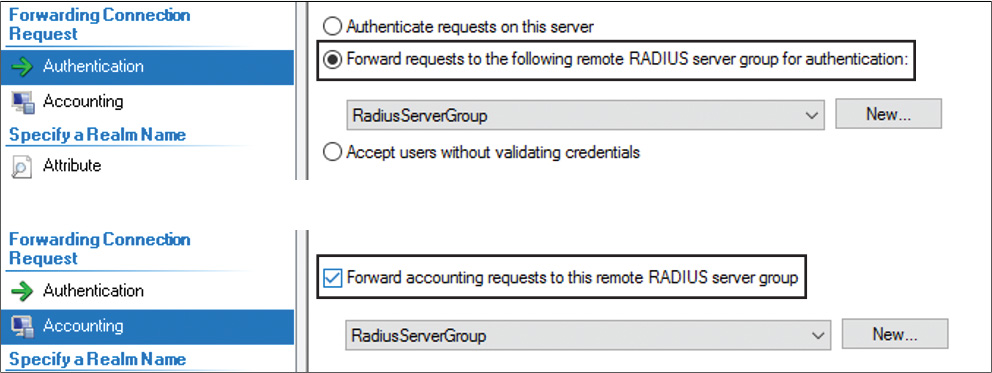
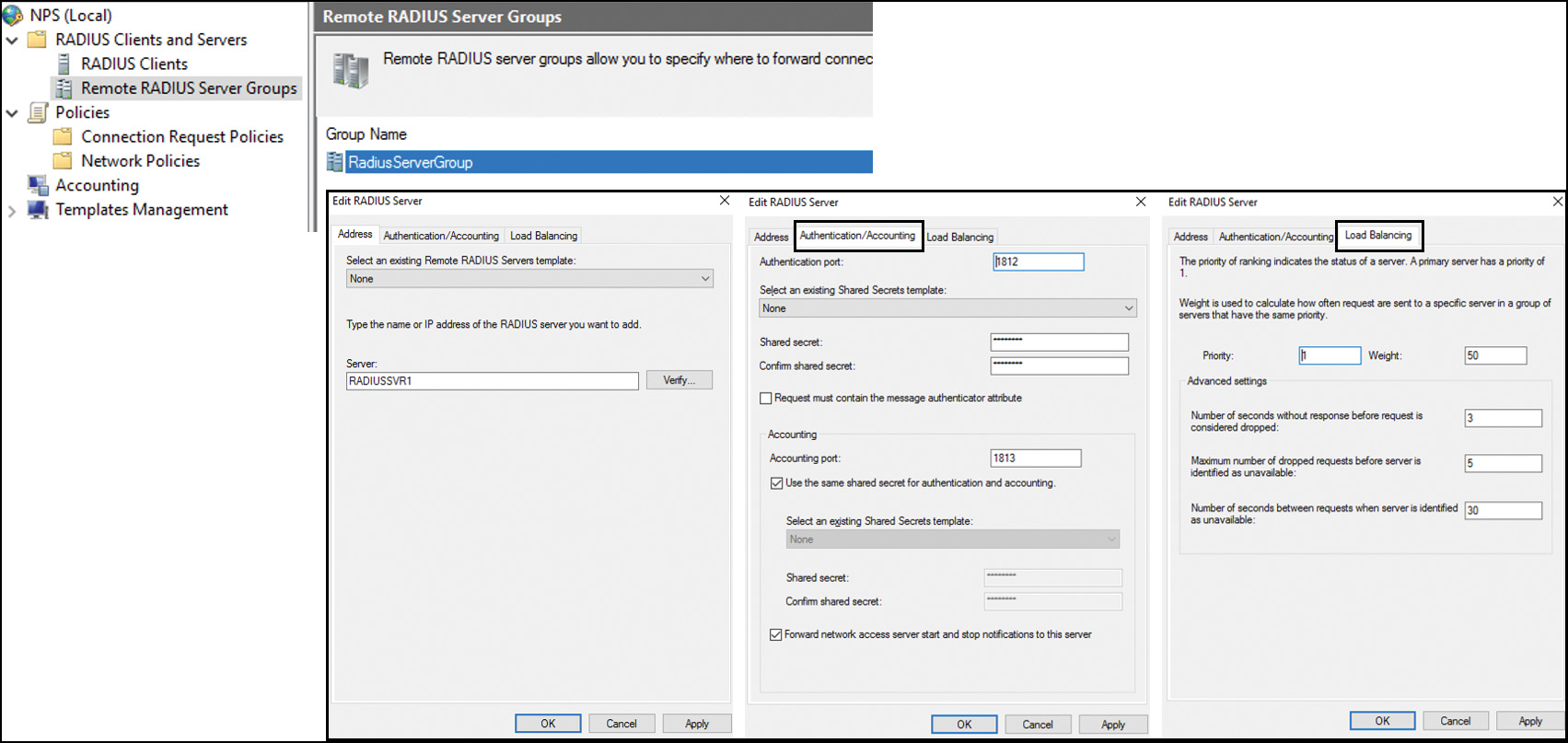
To configure a Windows Server 2016 VPN server as a RADIUS client, you also must install the NPAS role on the Windows Server 2016 VPN server. In the NPS console, you can configure authentication and accounting request forwarding to the RADIUS server group (if you have only one RADIUS server, you also have to create a RADIUS server group and then add the RADIUS server to this group). Figure 11-6 shows the settings of a connection request policy.
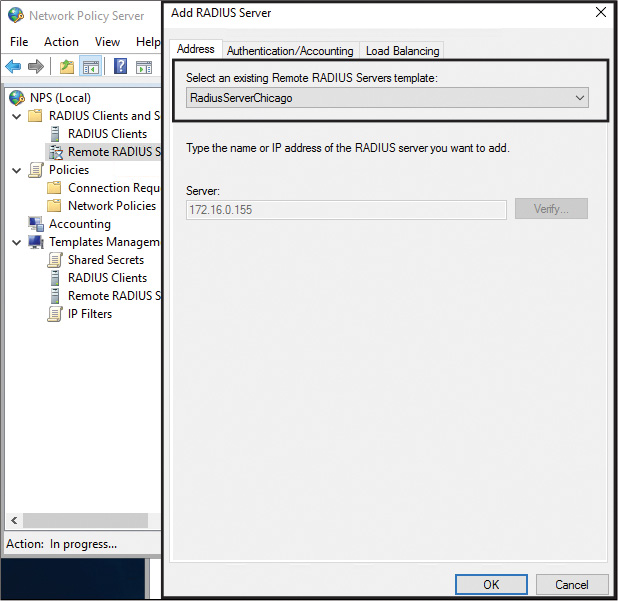
You also have to configure Network Policies that the NPS server uses to authorize connection requests, and you can configure RADIUS Accounting so that the NPS server logs accounting information to log files on the local hard disk or in a Microsoft SQL Server database. In the case of configuring an NPS server as a RADIUS client, you have to add a remote RADIUS server group with the Authentication/Accounting and Load Balancing settings (see Figure 11-7).
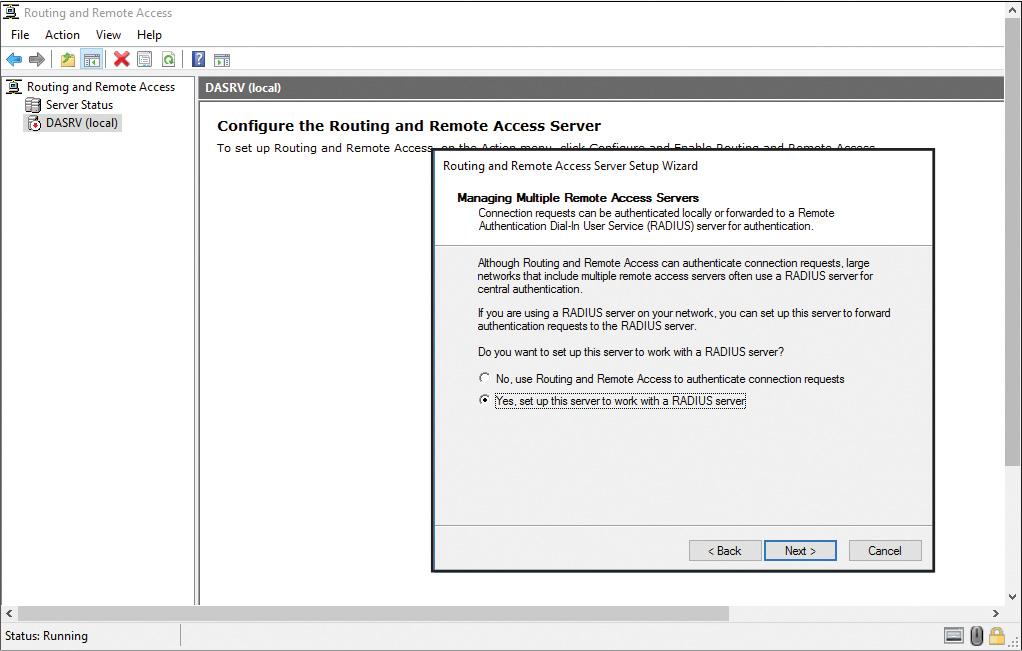
A Windows Server 2016 NPS server enables the use of a heterogeneous set of wireless, switch, remote access, or VPN equipment. You also can use the Routing and Remote Access Service to configure forwarding to a RADIUS server (see Figure 11-8).
When you set up a Windows Server 2016 VPN server as a RADIUS client, you have to know the names of the RADIUS servers you want to connect to.
The Routing and Remote Access Server Setup Wizard asks you for the Primary and Alternate RADIUS servers and the shared secret; it does not ask you about the Remote RADIUS Server Group as in the NPS console.
The wizard automatically adds two Remote RADIUS Server Groups to the list in the NPS console. These are named Microsoft Routing and Remote Access Service Authentication Servers and Microsoft Routing and Remote Access Service Accounting Servers.
A RADIUS server has access to user account information and can verify network access authentication credentials. If the user’s credentials are authentic and RADIUS authorizes the connection attempt, the RADIUS server authorizes the user’s access based on configured conditions (see Figure 11-9). It then logs the network access connection in an accounting log.
Using RADIUS, you can collect and maintain the network access user authentication, authorization, and accounting data in a central location instead of on each access server.
Implementing RADIUS Proxy

When using an NPS server as a RADIUS proxy, you configure the NPS server to forward to other RADIUS servers. You can create different NPS configurations for the following solutions:
![]() Wireless access
Wireless access
![]() Organizational dial-up or VPN remote access
Organizational dial-up or VPN remote access
![]() Outsourced dial-up or wireless access
Outsourced dial-up or wireless access
![]() Internet access
Internet access
![]() Authenticated access to extranet resources for business partners
Authenticated access to extranet resources for business partners
The following configuration examples demonstrate how you can configure NPS as a RADIUS server and a RADIUS proxy:
![]() NPS as a RADIUS server: NPS is configured as a RADIUS server, the default connection request policy is the only configured policy, and all connection requests are processed by the local NPS server. The NPS server can authenticate and authorize users whose accounts are in the domain of the NPS server and in trusted domains.
NPS as a RADIUS server: NPS is configured as a RADIUS server, the default connection request policy is the only configured policy, and all connection requests are processed by the local NPS server. The NPS server can authenticate and authorize users whose accounts are in the domain of the NPS server and in trusted domains.
![]() NPS as RADIUS proxy: NPS server is configured as a RADIUS proxy that forwards connection requests to remote RADIUS server groups in two untrusted domains. The default connection request policy is deleted, and two new connection request policies are created to forward requests to each of the two untrusted domains. In this example, NPS does not process any connection requests on the local server.
NPS as RADIUS proxy: NPS server is configured as a RADIUS proxy that forwards connection requests to remote RADIUS server groups in two untrusted domains. The default connection request policy is deleted, and two new connection request policies are created to forward requests to each of the two untrusted domains. In this example, NPS does not process any connection requests on the local server.
![]() NPS as both RADIUS server and RADIUS proxy: In addition to the default connection request policy, which specifies that connection requests must be processed locally, a new connection request policy is created that forwards connection requests to an NPS or other RADIUS server in an untrusted domain. This second policy is named the Proxy policy. In this example, the Proxy policy appears first in the ordered list of policies. If the connection request matches the Proxy policy, the connection request is forwarded to the RADIUS server in the remote RADIUS server group. If the connection request does not match the Proxy policy but does match the default connection request policy, NPS processes the connection request on the local server.
NPS as both RADIUS server and RADIUS proxy: In addition to the default connection request policy, which specifies that connection requests must be processed locally, a new connection request policy is created that forwards connection requests to an NPS or other RADIUS server in an untrusted domain. This second policy is named the Proxy policy. In this example, the Proxy policy appears first in the ordered list of policies. If the connection request matches the Proxy policy, the connection request is forwarded to the RADIUS server in the remote RADIUS server group. If the connection request does not match the Proxy policy but does match the default connection request policy, NPS processes the connection request on the local server.
![]() NPS as a RADIUS server with remote accounting servers: The local NPS server is not configured to perform accounting and the default connection request policy is revised so that RADIUS Accounting messages are forwarded to an NPS server or other RADIUS server in a remote RADIUS server group. Although accounting messages are forwarded, authentication and authorization messages are not forwarded; the local NPS server performs these functions for the local domain and all trusted domains.
NPS as a RADIUS server with remote accounting servers: The local NPS server is not configured to perform accounting and the default connection request policy is revised so that RADIUS Accounting messages are forwarded to an NPS server or other RADIUS server in a remote RADIUS server group. Although accounting messages are forwarded, authentication and authorization messages are not forwarded; the local NPS server performs these functions for the local domain and all trusted domains.
![]() NPS with Remote RADIUS to Windows User Mapping: NPS acts as both a RADIUS server and a RADIUS proxy for each individual connection request by forwarding the authentication request to a remote RADIUS server while using a local Windows user account for authorization. This configuration is implemented by configuring the Remote RADIUS to the Windows User Mapping attribute as a condition of the connection request policy.
NPS with Remote RADIUS to Windows User Mapping: NPS acts as both a RADIUS server and a RADIUS proxy for each individual connection request by forwarding the authentication request to a remote RADIUS server while using a local Windows user account for authorization. This configuration is implemented by configuring the Remote RADIUS to the Windows User Mapping attribute as a condition of the connection request policy.
To configure NPS as a RADIUS server, you can use either standard configuration or advanced configuration in the NPS console or in Server Manager. To configure NPS as a RADIUS proxy, you must use advanced configuration.
Implementing RADIUS Clients

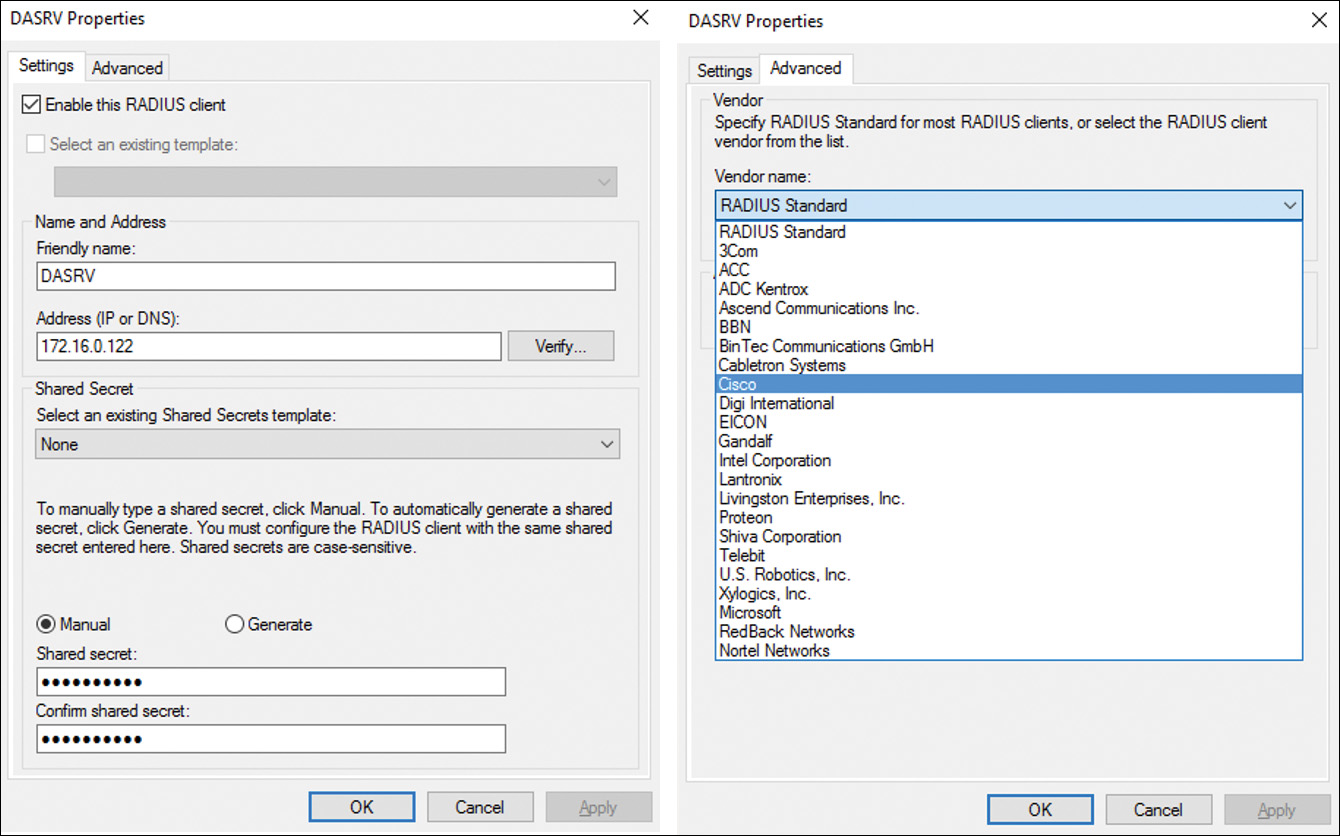
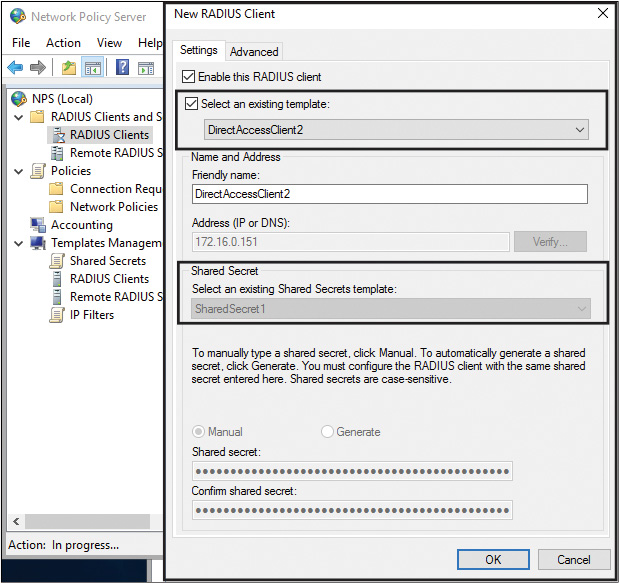
To implement a Windows Server 2016 RADIUS client, you simply have to add the RADIUS client to the list of RADIUS clients on the Windows Server 2016 RADIUS server. You can do this in the NPS console with New RADIUS Client (see Figure 11-10). You must type in a friendly name, IP address, or DNS name of the RADIUS client and a shared secret.
When you use a Microsoft VPN Server or a Microsoft DirectAccess server as a RADIUS client, you can use RADIUS Standard as the vendor name. When your RADIUS client is a Cisco device, you have to choose Cisco as the vendor name.
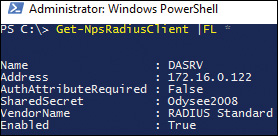
You also can add the RADIUS client to the Windows Server 2016 RADIUS server through the PowerShell cmdlet New-NpsRadiusClient (see Figure 11-11).
With the PowerShell cmdlet Get-NpsRadiusClient, you can display all settings of the RADIUS client you have applied (see Figure 11-12).
With the PowerShell cmdlet Remove-NpsRadiusClient, you can remove the RADIUS client from the list of RADIUS clients on a Windows Server 2016 NPS RADIUS server. With the PowerShell cmdlet Set-NpsRadiusClient, you can change settings for the RADIUS client.
Configuring a VPN Server as a RADIUS Client
When using Network Policy Server as a RADIUS server, you configure network access devices, such as wireless access points or VPN servers, as RADIUS clients to forward authentication and accounting requests to a RADIUS server. Table 11-2 lists some of the most important PowerShell cmdlets you can use to configure RADIUS servers and clients.

You cannot use the Add-RemoteAccessRadius PowerShell cmdlet to add an external RADIUS server into the RADIUS Server Group on a Windows Server 2016 VPN server. If VPN is not installed, the authentication type is Windows Authentication on the VPN server. Figure 11-13 shows the output of the Add-RemoteAccessRadius PowerShell cmdlet and the wrong authentication setting on the VPN server in the Routing and Remote Access console.
You cannot use the Remove-RemoteAccessRadius PowerShell cmdlet to remove an external RADIUS server from the RADIUS Server Group on a Windows Server 2016 VPN server if the external RADIUS server you want to remove is the last RADIUS server in the list of RADIUS servers on the VPN server (see Figure 11-14).
Configuring a DirectAccess Server as a RADIUS Client
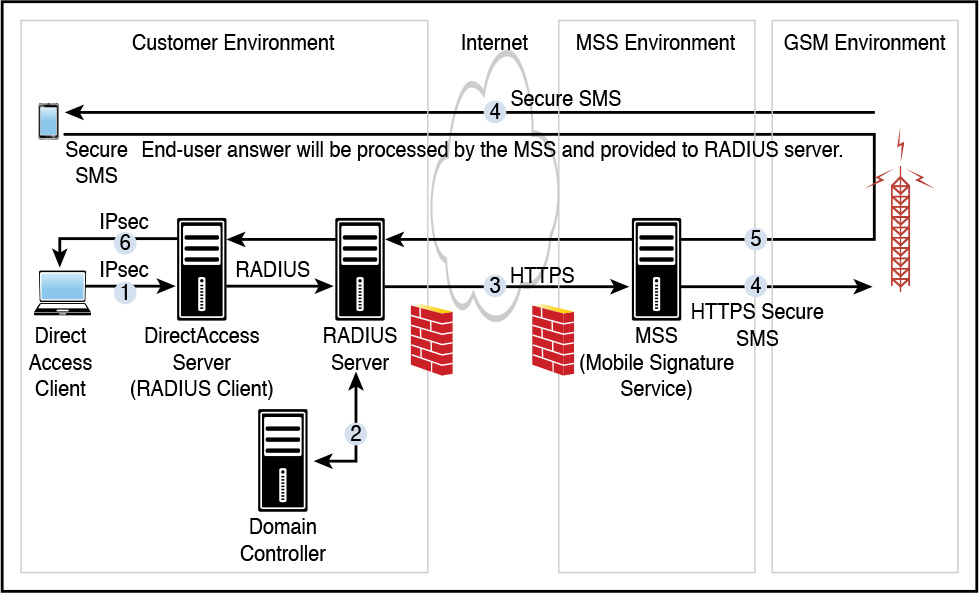
Suppose you want to use a Managed Secure Authentication Service with a Mobile Signature Service (MSS) from a third-party company as a two-factor authentication solution to implement secure login authentication for remote devices. You also want to implement that through the use of Windows Server 2016 DirectAccess with OTP and a RADIUS server.
Figure 11-15 shows such an example deployment in which a user requests remote access with Windows Server 2016 DirectAccess. The DirectAccess server (RADIUS client) sends the RADIUS requests to the RADIUS server to authenticate the users. The RADIUS server invokes the MSS over SOAP and provides the answer back to the RADIUS client. The RADIUS server also can be connected to Active Directory, where the end user’s details such as phone number and credentials are stored.
The authentication data flow for that scenario involves the following steps:

Step 1. When a user tries to connect to the Windows Server 2016 DirectAccess server (RADIUS client), the DirectAccess server makes a request to the defined RADIUS server to authenticate the end user with the MobileID.
Step 2. The RADIUS server (optionally) verifies the user credentials against Active Directory and/or maps to a valid mobile phone user.
Step 3. The RADIUS server (which enabled the MobileID plug-in) calls the MobileID service.
Step 4. The third-party MSS platform ensures that the end user’s signature request is allowed and forwards the signature request to the end user’s mobile phone.
Step 5. The MSS platform processes the end user answer and provides it to the RADIUS server.
Step 6. After the RADIUS server verifies the third-party MSS platform response, the answer is forwarded to the RADIUS client. The Windows Server 2016 DirectAccess server processes this answer to grant or reject the DirectAccess connection request.
To configure the Windows Server 2016 DirectAccess server for this scenario, you have to do the following:
Step 1. Deploy a Single Remote Access server with Advanced Settings.
Step 2. On the Remote Access server, open Server Manager and click Remote Access in the left pane.
Step 3. Right-click Remote Access Server in the Servers pane, and select Remote Access Management.
Step 4. Click Configuration.
Step 5. In the DirectAccess Setup window, under Step 2–Remote Access Server, click Edit.
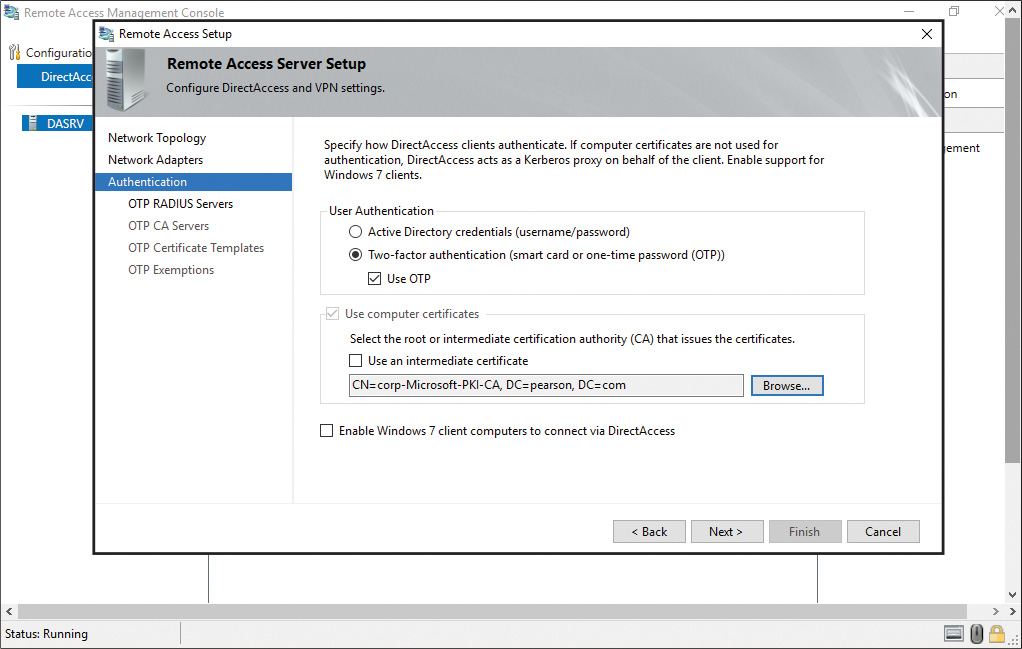
Step 6. Click Next three times, and in the Authentication section, select Two-Factor Authentication (Use Computer Certificates is selected automatically) and Use OTP (see Figure 11-16). Verify that the root CA is set to the name of the CA of the organization. Click Next.
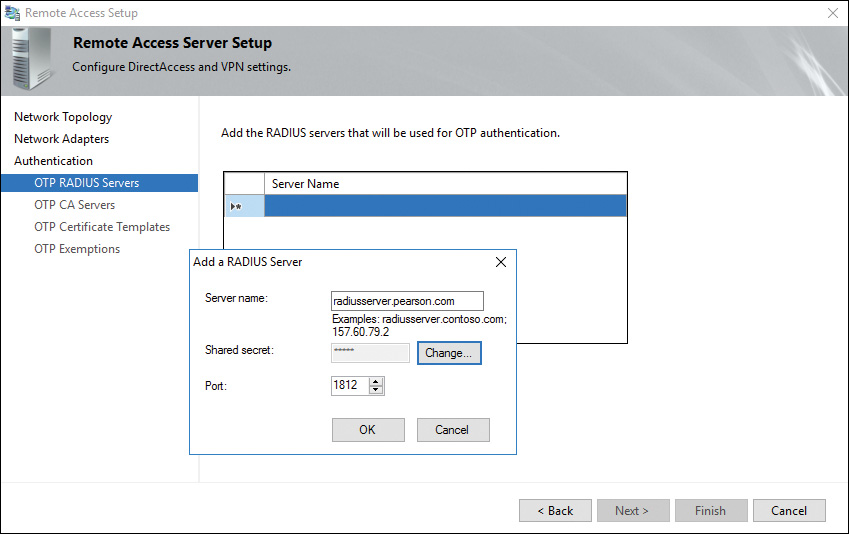
Step 7. In the OTP RADIUS Servers section, double-click the blank Server Name field (see Figure 11-17).
Step 8. In the Add a RADIUS Server dialog box, type the server name of the RADIUS server in the Server Name field. Click Change next to the Shared Secret field, and type the same password that you defined at the RADIUS server (see Figure 11-17). Click OK twice, and then click Next.
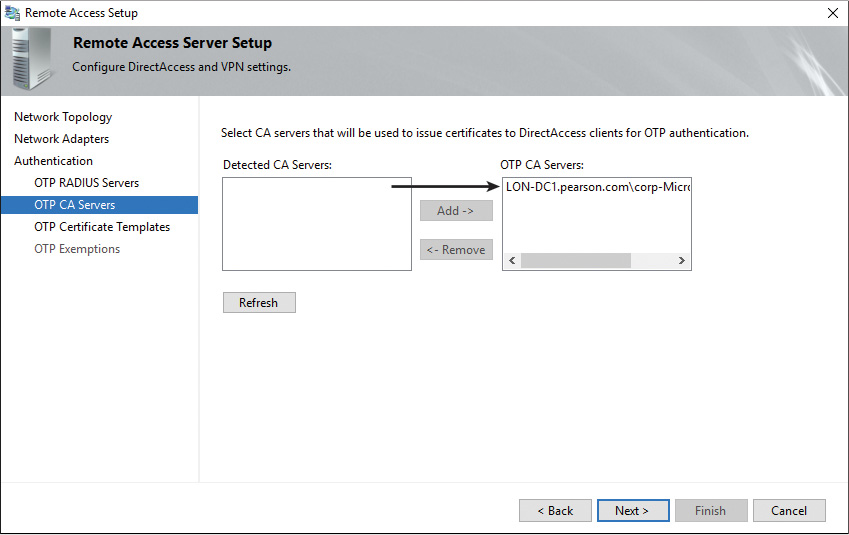
Step 9. In the OTP CA Servers section, select the organization’s CA server under Detected CA Servers and add this CA to the OTP CA Servers list. This CA then can be used to issue certificates to DirectAccess clients for OTP authentication (see Figure 11-18).
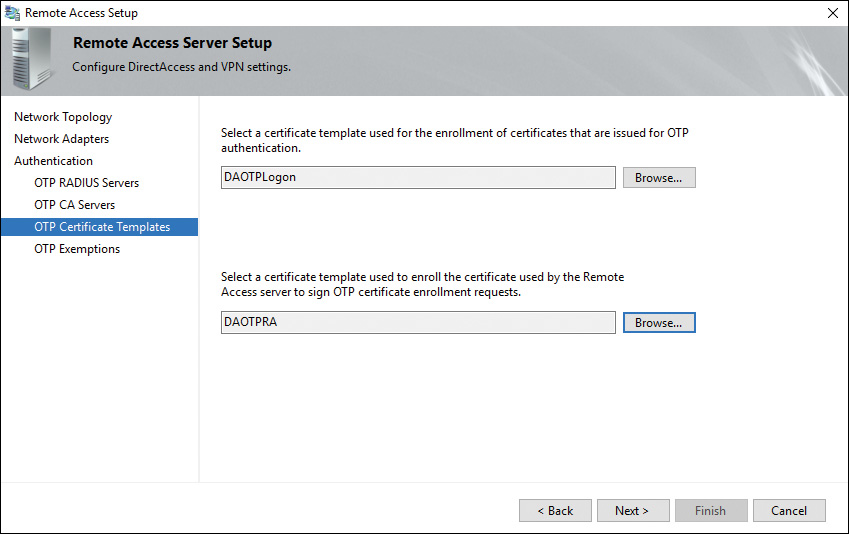
Step 10. In the OTP Certificate Templates section, select the OTP certificate template and the certificate template used to enroll the certificate that the DirectAccess server uses to sign OTP certificate enrollment requests (see Figure 11-19).
The certificate templates must have been created previously on the organization’s internal CA. The following two lists describe the necessary steps to create both certificate templates.
To create a certificate template used to sign OTP certificate requests:
a. On the internal CA, select the certtmpl.msc utility from the command line.
b. In the Certificate Templates Console, in the details pane, right-click the Computer template and click Duplicate Template.
c. On the Compatibility tab in the Properties of New Template dialog box, in the Certification Authority list, click Windows Server 2016; in the Resulting Changes dialog box, click OK. In the Certificate Recipient list, click Windows Server 2016; in the Resulting Changes dialog box, click OK.
d. In the Properties of New Template dialog box, click the General tab.
e. On the General tab, in Template Display Name, type DAOTPRA as the name. Set the Validity Period to 2 days, and set the Renewal Period to 1 day. If the Certificate Templates warning displays, click OK.
f. Click the Security tab, and then click Add.
g. In the Select Users, Computers, Service Accounts, or Groups dialog box, click Object Types. In the Object Types dialog box, select Computers and then click OK. In the Enter the Object Names to Select box, type the name of the DirectAccess server and click OK; in the Allow column, select the Read, Enroll, and Autoenroll check boxes. Click Authenticated Users, select the Read check box under the Allow column, and clear all other check boxes. Click Domain Computers and uncheck Enroll under the Allow column. Click Domain Admins and Enterprise Admins, and click Full Control under the Allow column for both. Click Apply.
h. Click the Subject Name tab, and then click Build from This Active Directory Information. In the Subject Name Format list, select DNS Name; make sure that the DNS Name box is checked, and click Apply.
i. Click the Extensions tab, select Application Policies, and then click Edit. Remove all existing application policies. Click Add; in the Add Application Policy dialog box, click New, enter DA OTP RA in the Name field, enter 1.3.6.1.4.1.311.81.1.1 in the Object Identifier field, and click OK. In the Add Application Policy dialog box, click OK. In the Edit Application Policies Extension dialog box, click OK. In the Properties of New Template dialog box, click OK.
To create and deploy a certificate template for OTP certificates issued by the organization’s CA:
a. In the Certificate Templates Console, in the details pane, right-click the Smartcard Logon template and click Duplicate Template.
b. In the Properties of New Template dialog box, on the Compatibility tab in the Certification Authority list, click Windows Server 2016; in the Resulting Changes dialog box, click OK. In the Certificate Recipient list, click Windows Server 2016; in the Resulting Changes dialog box, click OK.
c. In the Properties of New Template dialog box, click the General tab.
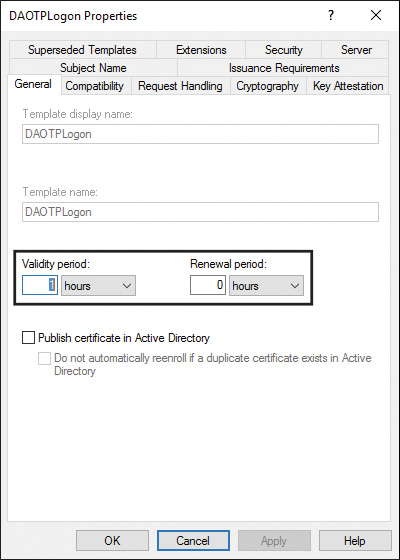
d. On the General tab, in Template Display Name, type DAOTPLogon. In Validity Period, in the drop-down list, click Hours. In the Certificate Templates dialog box, click OK and make sure that the number of hours is set to 1. In Renewal Period, type 0.
e. Click the Security tab, select Authenticated Users in the Allow column, and select the Read and Enroll check boxes. Click OK. Click Domain Admins and Enterprise Admins, and click Full Control in the Allow column for both. Click Apply.
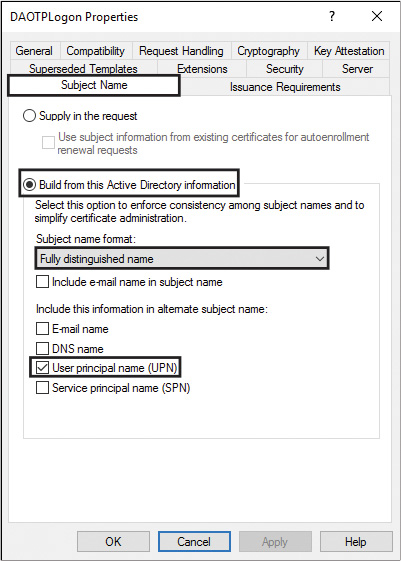
f. Click the Subject Name tab, and then click Build from This Active Directory Information. In the Subject Name Format list, select Fully Distinguished Name; also make sure that the User Principal Name (UPN) box is checked, and click Apply.
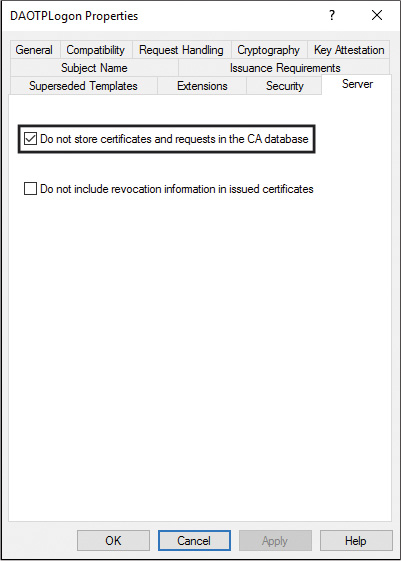
g. Click the Server tab, select the Do Not Store Certificates and Requests in the CA Database check box and clear the Do Not Include Revocation Information in Issued Certificates check box. In the Properties of New Template dialog box, click Apply.
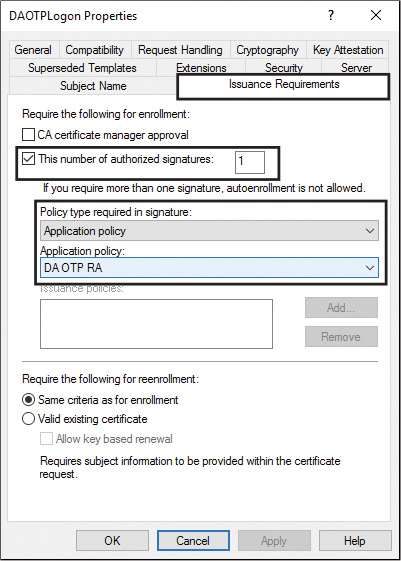
h. Click the Issuance Requirements tab, select the This Number of Authorized Signatures check box, and set the value to 1. In the Policy Type Required in Signature list, select Application Policy; in the Application Policy list, select DA OTP RA. In the Properties of New Template dialog box, click OK.
i. Click the Extensions tab, and in Application Policies, click Edit. Delete Client Authentication, keep SmartCardLogon, and click OK twice.
j. Close the Certificate Templates Console.
k. On the Start screen, type certsrv.msc and then click Enter.
l. In the Certification Authority console tree, expand the name of the CA, click Certificate Templates, right-click Certificate Templates, point to New, and click Certificate Template to Issue.
m. In the list of certificate templates, click DAOTPRA and DAOTPLogon, and click OK.
n. In the details pane of the console, you should see the DAOTPRA certificate template with Intended Purpose of DA OTP RA and also the DAOTPLogon certificate template with Intended Purpose of Smart Card Logon.
o. Restart the services.
p. Close the Certification Authority console.
q. Open an elevated command prompt. Type CertUtil.exe -SetReg DBFlags +DBFLAGS_ENABLEVOLATILEREQUESTS, and click Enter.
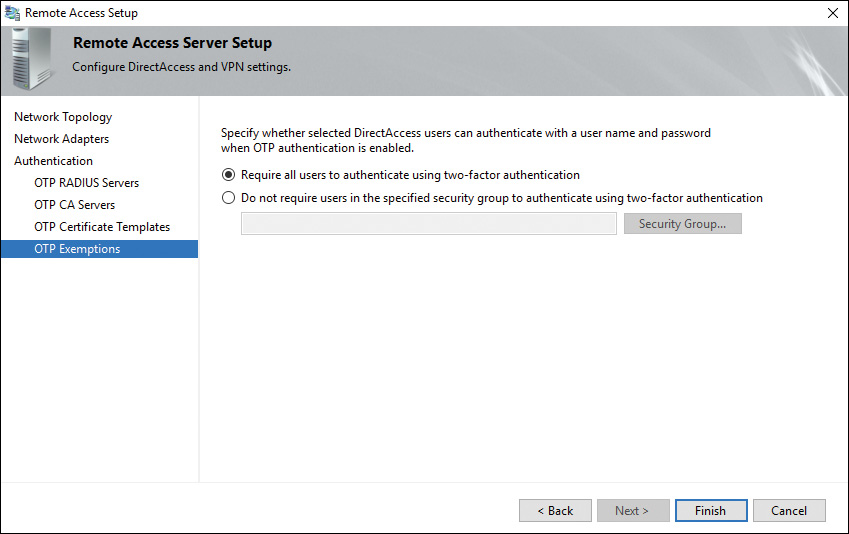
Step 11. In the OTP Exemptions section, select Require All Users to Authenticate Using Two-Factor Authentication if all users must use OTP authentication. Choose Do Not Require Users in the Specified Security Group to Authenticate Using Two-Factor Authentication if you want to exclude some users from OTP authentication (see Figure 11-20).
Step 12. Create a Probe user with the username DAProbeUser and the password DAProbePass on the RADIUS server.
OTP Certificate Template Planning for Windows Server 2016 DirectAccess Server RADIUS Client
When you want to configure a Windows Server 2016 DirectAccess server as a RADIUS client, each DirectAccess client requires an OTP authentication certificate to gain access to the internal network. You must configure two templates on your internal CA for the OTP certificate. Note the following when configuring the OTP certificate templates:
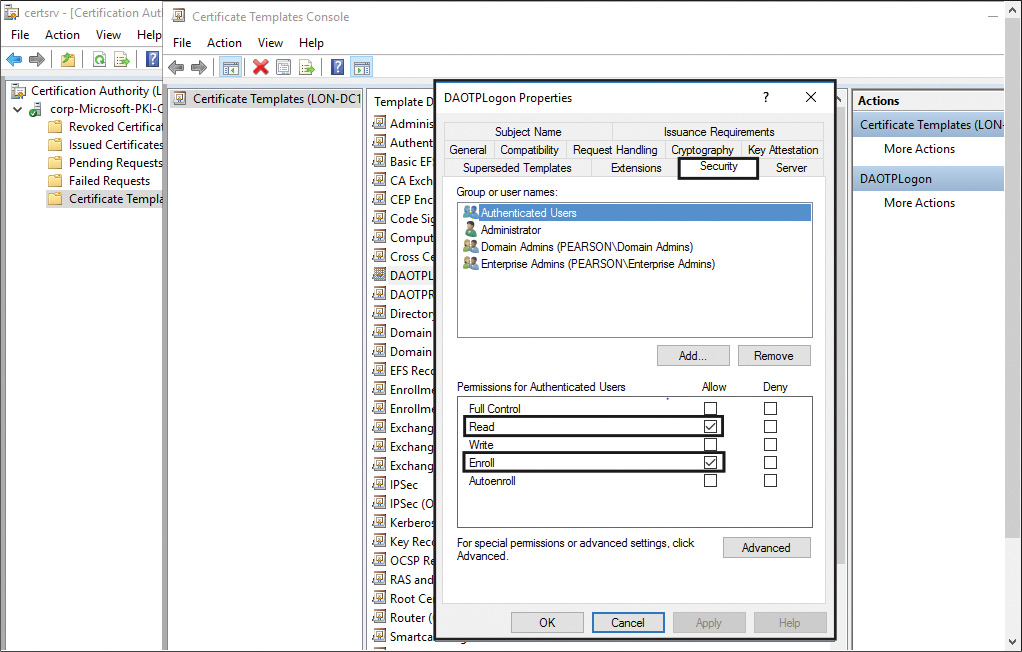
![]() All users who need to perform OTP authentication must have read and enroll permissions for this template (see Figure 11-21).
All users who need to perform OTP authentication must have read and enroll permissions for this template (see Figure 11-21).

![]() The subject name should be built from AD information, to ensure that the subject name matches the OTP username and not the name of the Remote Access server that performs the certificate request. The subject name must be in the fully distinguished name format, and the subject alternative name must be in UPN format. This ensures that the enrolled OTP certificate is valid for smart card Kerberos authentication (see Figure 11-22).
The subject name should be built from AD information, to ensure that the subject name matches the OTP username and not the name of the Remote Access server that performs the certificate request. The subject name must be in the fully distinguished name format, and the subject alternative name must be in UPN format. This ensures that the enrolled OTP certificate is valid for smart card Kerberos authentication (see Figure 11-22).
![]() The intended purpose of the certificate must be Smart Card Logon (see Figure 11-23).
The intended purpose of the certificate must be Smart Card Logon (see Figure 11-23).
![]() Issuance must require one authorized signature. The signature must be configured with the predefined DirectAccess OTP application policy set in the registration authority signing certificate template (see Figure 11-24).
Issuance must require one authorized signature. The signature must be configured with the predefined DirectAccess OTP application policy set in the registration authority signing certificate template (see Figure 11-24).
![]() The validity period should be set to 1 hour (see Figure 11-25).
The validity period should be set to 1 hour (see Figure 11-25).
![]() The renewal period should be set to 0 (see Figure 11-25).
The renewal period should be set to 0 (see Figure 11-25).
![]() Certificates and requests should not be stored in the CA database (see Figure 11-26).
Certificates and requests should not be stored in the CA database (see Figure 11-26).
![]() The certificate Enhanced Key Usage parameter must be set correctly, as follows: For the DirectAccess registration signing certificate template, use the key 1.3.6.1.4.1.311.81.1.1 (see Figure 11-27); for the OTP authentication certificate template, use the key 1.3.6.1.4.1.311.20.2.2 (see Figure 11-28).
The certificate Enhanced Key Usage parameter must be set correctly, as follows: For the DirectAccess registration signing certificate template, use the key 1.3.6.1.4.1.311.81.1.1 (see Figure 11-27); for the OTP authentication certificate template, use the key 1.3.6.1.4.1.311.20.2.2 (see Figure 11-28).
Configure NPS Templates

You can use NPS templates to precreate configuration elements such as RADIUS clients or preshared keys (PSK), which you can reuse on a local NPS server or export for other NPS servers. NPS templates are a way for companies with many NPS servers and access clients to reduce time and cost effort. The following settings can be configured with Windows Server 2016 NPS templates:
![]() Shared Secrets
Shared Secrets
![]() RADIUS Clients
RADIUS Clients
![]() Remote RADIUS Servers
Remote RADIUS Servers
![]() IP Filters
IP Filters
Figure 11-29 shows where to configure NPS templates.
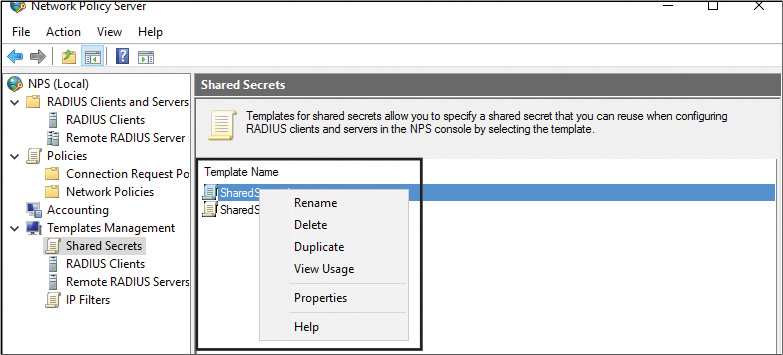
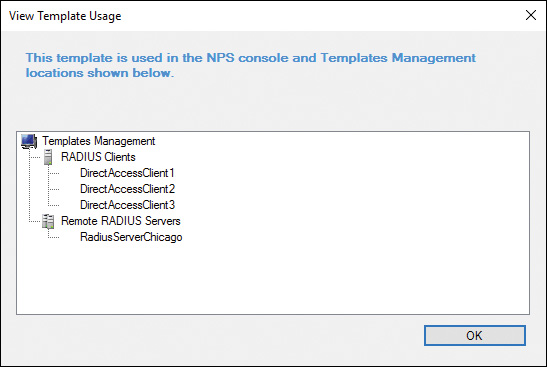
You can rename, delete, duplicate, or view usage with NPS templates. Figure 11-30 shows the possible NPS templates tasks, and Figure 11-31 gives an example of the use of a shared secret NPS template.
You can apply a RADIUS client and Shared Secret NPS template in the New RADIUS Client window; you can apply a Remote RADIUS Server NPS template in the Add RADIUS Server window. See Figures 11-32 and 11-33.
Tip
You also can list your Shared Secret NPS templates with the PowerShell cmdlet Get-NpsSharedSecretTemplate.
Configure RADIUS Accounting
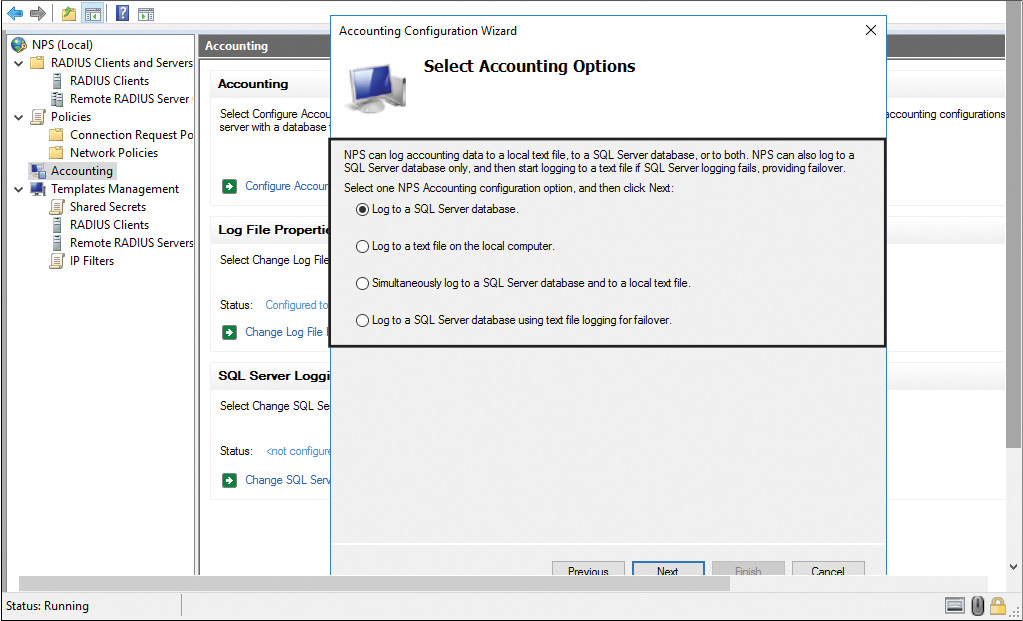
You can configure a Windows Server 2016 NPS server for RADIUS Accounting so that the NPS server logs accounting information to log files on the local hard disk or on a Microsoft SQL Server database. Figure 11-34 shows the four different NPS accounting options you can configure in the Accounting Configuration Wizard; the following list describes them further:

![]() SQL logging only: With this choice, you can configure a data link to a SQL Server that allows NPS to connect to and send accounting data to the SQL Server. In addition, the wizard can configure the database on the SQL Server to ensure that the database is compatible with NPS SQL Server logging.
SQL logging only: With this choice, you can configure a data link to a SQL Server that allows NPS to connect to and send accounting data to the SQL Server. In addition, the wizard can configure the database on the SQL Server to ensure that the database is compatible with NPS SQL Server logging.
![]() Text logging only: With this setting, you can configure NPS to log accounting data to a text file.
Text logging only: With this setting, you can configure NPS to log accounting data to a text file.
![]() Parallel logging: With this setting, you can configure the SQL Server data link and database. You can also configure text file logging so that NPS logs simultaneously to the text file and the SQL Server database.
Parallel logging: With this setting, you can configure the SQL Server data link and database. You can also configure text file logging so that NPS logs simultaneously to the text file and the SQL Server database.
![]() SQL logging with backup: With this setting, you can configure the SQL Server data link and database. In addition, you can configure text file logging that NPS uses if SQL Server logging fails.
SQL logging with backup: With this setting, you can configure the SQL Server data link and database. In addition, you can configure text file logging that NPS uses if SQL Server logging fails.
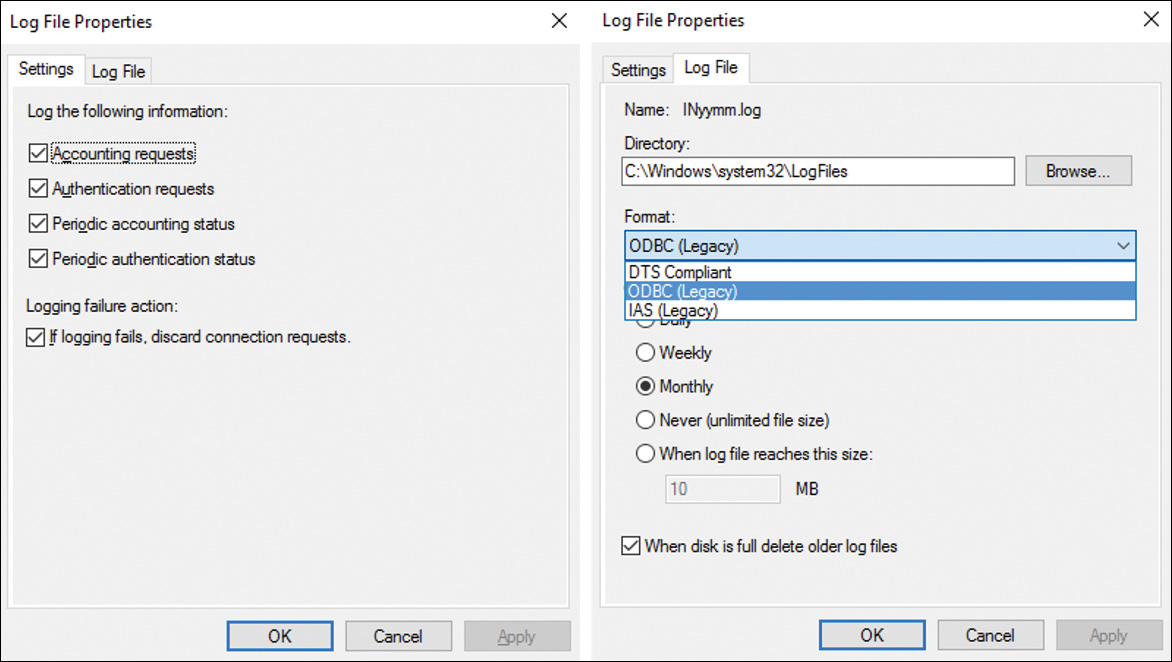
NPS Log File Properties
Figure 11-35 shows the log file properties and which log information you can choose.

Tip
To prevent NPS log files from filling the hard drive, it is recommended that you keep them on a partition that is separate from the system partition. If RADIUS Accounting fails due to a full hard disk drive or other causes, NPS stops processing connection requests, preventing users from accessing network resources.
NPS SQL Server Logging

When you set up NPS Accounting and you have selected Log to a SQL Server Database on the Accounting Configuration Wizard to use SQL Server as a repository for NPS Radius Accounting information, you have to enter the data link information (SQL Server name, authentication, SQL database name). Figure 11-36 shows the Data Link Properties window.
Tip
Windows Server 2016 NPS formats accounting data as XML and sends it to the report_event stored procedure in the SQL Server database that you designate in NPS. For SQL Server logging to function properly, you must have a stored procedure named report_event in the SQL Server database that can receive and parse the XML documents from NPS.
ping user-name

These ping requests include fictional usernames.
When NPS processes these requests, the event and accounting logs become filled with access reject records, making it more difficult to keep track of valid records. When you configure a registry entry for ping user-name, NPS matches the registry entry value against the username value in ping requests by other servers.
A ping user-name registry entry specifies the fictional username (or a username pattern, with variables, that matches the fictional username) sent by RADIUS proxy servers and network access servers.
When NPS receives ping requests that match the ping user-name registry entry value, NPS rejects the authentication requests without processing the requests.
ping user-name is not installed by default. You must add ping user-name to the registry. You can add an entry to the registry using a registry editor.
You can add ping user-name to the following registry key as a string value: HKEY_LOCAL_ MACHINESystemCurrentControlSetServicesIAS Parameters. Item: ping user-name, value: REG_SZ, data: User name.
Certificates

To establish an IPsec security association, the VPN client and the VPN server must use the IKE protocol to exchange computer certificates. In either case, the VPN client and server authenticate each other at the computer level. Computer certificate authentication is recommended because it is a much stronger authentication method than using a preshared key. L2TP VPN connections can use certificates for encryption, integrity, and data authentication. If you want to configure a Windows Server 2016 NPS server with PEAP, you need a certificate. You can use certificates from an internal Certificate Authority (CA) or a public CA.
Using Certificates for Windows Server 2016 NPS Servers
When you use the Windows Server 2016 NPS for a VPN server, you use the following authentication methods so that the NPS server hosts the connection request policies and Network Policies for the VPN connections:
![]() Protected Extensible Authentication Protocol (PEAP)
Protected Extensible Authentication Protocol (PEAP)
![]() Extensible Authentication Protocol (EAP)
Extensible Authentication Protocol (EAP)
![]() Microsoft Encrypted Authentication (MS-CHAP)
Microsoft Encrypted Authentication (MS-CHAP)
![]() Microsoft Encrypted Authentication version 2 (MS-CHAPv2)
Microsoft Encrypted Authentication version 2 (MS-CHAPv2)
MS-CHAPv2 and MS-CHAP can work without using certificates, but PEAP must use certificates.
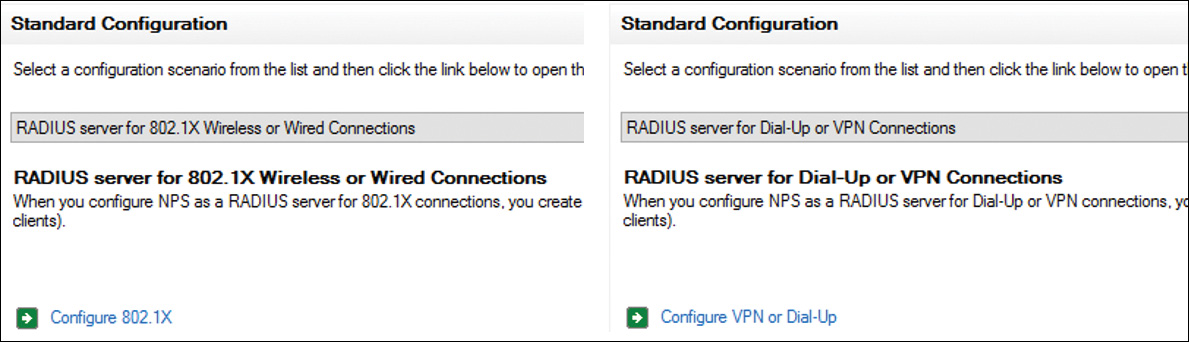
You can configure a Windows Server 2016 NPS for the following two configuration scenarios:
![]() Dial-up or VPN connections
Dial-up or VPN connections
![]() 802.1X wireless or wired connections
802.1X wireless or wired connections
Figure 11-37 shows the standard NPS configuration scenarios.
When you use NPS as a RADIUS server for dial-up or VPN connections, your choices are MS-CHAP, MS-CHAPv2, EAP-MSCHAPv2, PEAP, and Smart Card or Other Certificate. For 802.1X wireless or wired connections, your choices are Smart Card or Other Certificates, EAP-MSCHAPv2, and PEAP.
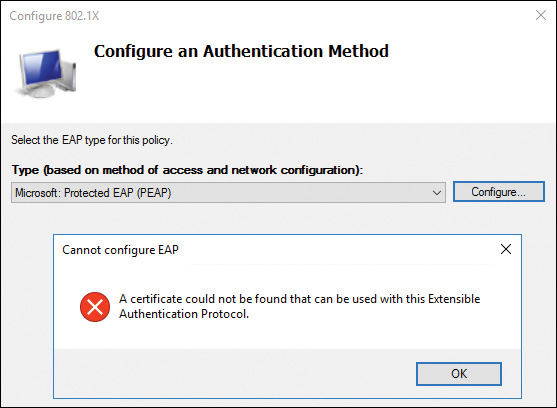
When you select Smart Card or Other Certificates or PEAP, and you have not prepared a valid certificate on the NPS server, you get an error message like the one in Figure 11-38.
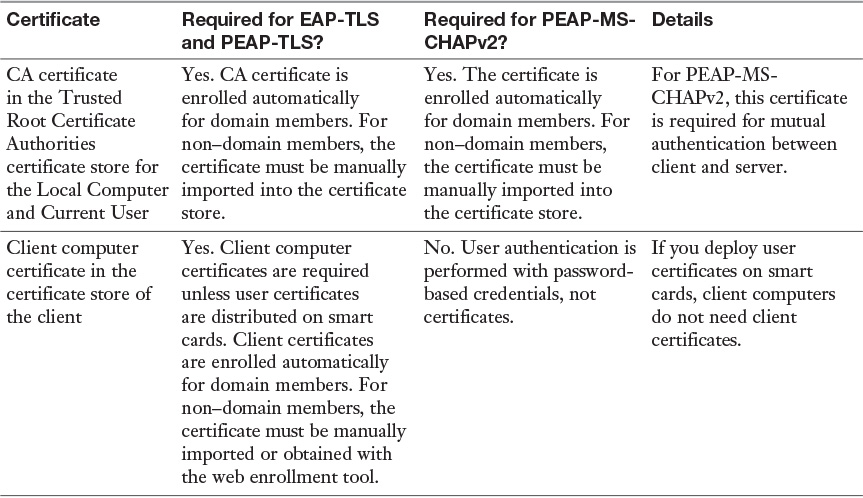
Table 11-3 shows the certificates that are required to successfully deploy each of the certificate-based authentication methods on a Windows Server 2016 NPS server.
Configuring Certificate Templates for EAP and PEAP

With PEAP-MS-CHAPv2, PEAP-TLS, or EAP-TLS as the authentication method, a Windows Server 2016 NPS server must use a server certificate that meets the minimum server certificate requirements. A client accepts the authentication attempt of the server when the server certificate meets the following requirements:
![]() The subject name contains a value. If you issue a certificate to your server running NPS that has a blank subject name, the certificate is not available to authenticate your NPS server.
The subject name contains a value. If you issue a certificate to your server running NPS that has a blank subject name, the certificate is not available to authenticate your NPS server.
![]() The computer certificate on the server chains to a trusted root Certificate Authority (CA) and does not fail any of the checks that are performed by CryptoAPI and that are specified in the remote access policy or network policy.
The computer certificate on the server chains to a trusted root Certificate Authority (CA) and does not fail any of the checks that are performed by CryptoAPI and that are specified in the remote access policy or network policy.
![]() The computer certificate for the NPS server or VPN server is configured with the Server Authentication purpose in Extended Key Usage (EKU) extensions. (The object identifier for Server Authentication is 1.3.6.1.5.5.7.3.1.)
The computer certificate for the NPS server or VPN server is configured with the Server Authentication purpose in Extended Key Usage (EKU) extensions. (The object identifier for Server Authentication is 1.3.6.1.5.5.7.3.1.)
![]() The server certificate is configured with a required algorithm value of RSA.
The server certificate is configured with a required algorithm value of RSA.
![]() The Subject Alternative Name extension, if used, must contain the DNS name of the server.
The Subject Alternative Name extension, if used, must contain the DNS name of the server.
When using PEAP and EAP-TLS, NPS servers display a list of all installed certificates in the computer certificate store, with the following exceptions:
![]() Certificates that do not contain the Server Authentication purpose are not displayed.
Certificates that do not contain the Server Authentication purpose are not displayed.
![]() Certificates that do not contain a subject name are not displayed.
Certificates that do not contain a subject name are not displayed.
![]() Registry-based and smart card logon certificates are not displayed.
Registry-based and smart card logon certificates are not displayed.
Connection Request Policies

Connection request policies are condition sets and settings that allow administrators to designate which RADIUS servers do the authentication and authorization of connection requests that the NPS server receives from RADIUS clients.
Connection request policies allow you to designate whether the local NPS server processes connection requests locally or whether they are forwarded for processing to another RADIUS server. With connection request policies, you can use NPS servers as a RADIUS server or RADIUS proxy, based on a variety of factors:
![]() Time of day and day of the week
Time of day and day of the week
![]() Realm name in the connection request
Realm name in the connection request
![]() Connection type you are requesting
Connection type you are requesting
![]() RADIUS client’s IP address
RADIUS client’s IP address
Default Connection Request Policy

The default connection request policy uses NPS as a RADIUS server and processes all authentication requests locally. You can delete the default connection request policy if you do not want the NPS server to act as a RADIUS server and process connection requests locally. When you install an NPS server, the default connection request policy is created with the following conditions:
![]() Authentication is not configured.
Authentication is not configured.
![]() Accounting is not configured to forward accounting information to a remote RADIUS server group. Attribute manipulation is not configured with rules that change attributes in forwarded connection requests.
Accounting is not configured to forward accounting information to a remote RADIUS server group. Attribute manipulation is not configured with rules that change attributes in forwarded connection requests.
![]() Forwarding Request is turned off, which means that the local NPS authenticates and authorizes connection requests.
Forwarding Request is turned off, which means that the local NPS authenticates and authorizes connection requests.
![]() Advanced attributes are not configured.
Advanced attributes are not configured.
![]() The default connection request policy uses NPS as a RADIUS server.
The default connection request policy uses NPS as a RADIUS server.
Figure 11-39 shows the Overview, Conditions, and Settings of the default NPS connection request policy.
Creating a New Connection Request Policy
If the NPS server has to work as both a RADIUS server, processing connection requests locally, and a RADIUS proxy, add a new connection request policy using the following steps; then verify that the default connection request policy is the last policy processed by placing it last in the list of policies:

Step 1. In Server Manager, click Tools, and then click Network Policy Server.
Step 2. In the console tree, double-click Policies.
Step 3. Right-click Connection Request Policies, and then click New Connection Request Policy.
Step 4. Use the New Connection Request Policy Wizard to configure your connection request policy and, if not previously configured, a remote RADIUS server group.
Connection Request Policy Tasks

Figure 11-40 shows the possible tasks you can do with connection request policies on a Windows Server 2016 NPS server:
![]() Move Up
Move Up
![]() Move Down
Move Down
![]() Disable
Disable
![]() Delete
Delete
![]() Rename
Rename
![]() Duplicate Policy
Duplicate Policy
Network Policies for VPN Wireless and Wired Clients

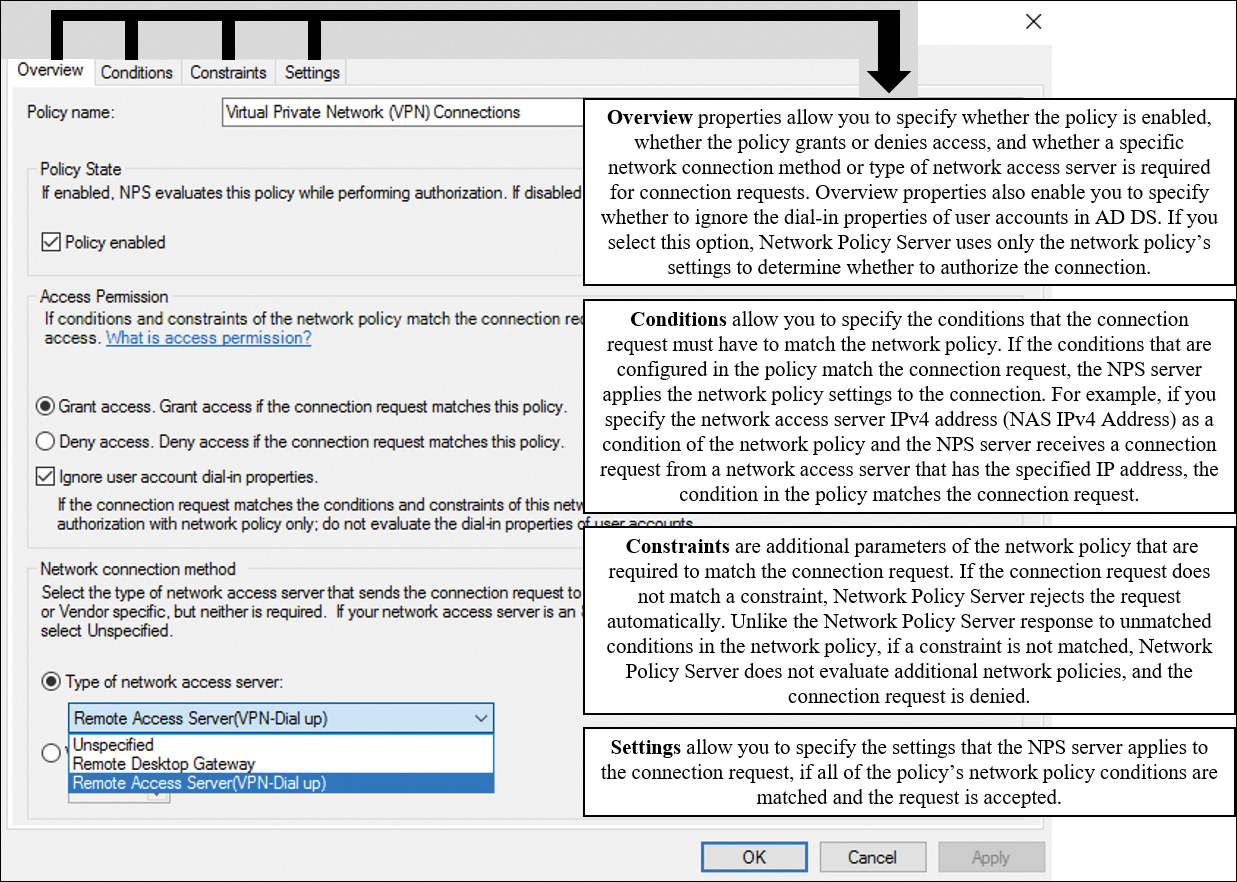
A Windows Server 2016 NPS network policy is a set of conditions, constraints, and settings that enable you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
Figure 11-41 shows where you can create a new Windows Server 2016 NPS network policy.
Each network policy has four categories of properties (see Figure 11-42).
Network Policy Ordering

When a Windows Server 2016 NPS performs the authorization of a connection request, it compares the request with each network policy in the ordered list of policies, starting with the first policy and then moving down the list of configured policies.
If NPS finds a policy whose conditions match the connection request, NPS uses the matching policy and the dial-in properties of the user account to perform authorization. If the dial-in properties of the user account are configured to grant access or control access through network policy and the connection request is authorized, NPS applies the settings that are configured in the network policy to the connection.
If NPS does not find a network policy that matches the connection request, the connection request is rejected unless the dial-in properties on the user account are set to grant access.
If the dial-in properties of the user account are set to deny access, NPS rejects the connection request.
Network Policy Key Settings

When you use the New Network Policy Wizard to create a network policy, the value that you specify in Network Connection Method is used to automatically configure the Policy Type condition. Figure 11-43 shows the choices.
If you select Unspecified, NPC evaluates the network policy that you create for all connection types that are using any kind of network access server. If you specify a network connection method, NPS evaluates the network policy only if the connection request originates from the type of network access server that you specify.
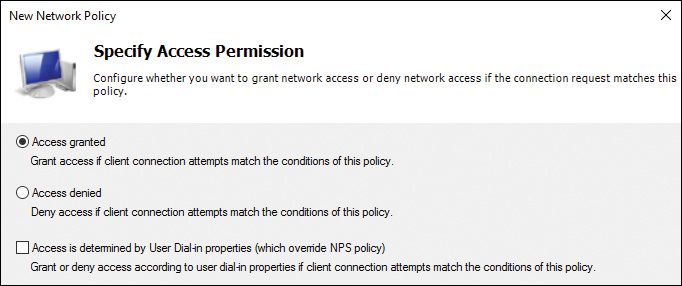
On the Specify Access Permission page, you must select Access Granted if you want the policy to allow users to connect to your network. If you want the policy to prevent users from connecting to your network, select Access Denied. Figure 11-44 shows the Specify Access Permission page.
When you want access permission to be determined by the user’s dial-in properties in AD DS, you can select Access Is Determined by User Dial-in Properties.
You can create a network policy for 802.1X wired or wireless with the following steps:
Step 1. On the NPS server, in Server Manager, click Tools and then click Network Policy Server.
Step 2. Click NPS (Local). Select the server.
Step 3. In Getting Started and Standard Configuration, select RADIUS Server for 802.1X Wireless or Wired Connections.
Step 4. Click Configure 802.1X Using a Wizard. The New IEEE 802.1X Secure Wired and Wireless Connections Wizard opens.
Step 5. Follow the instructions in the wizard to finish creating your new policies.
Network Policy Conditions
Figure 11-45 lists all possible conditions in an NPS network policy.
Configuring NPS for VLANs
You can provide visitors with wireless access to the Internet without allowing them access to your organization’s network.
With VLANs, you can create logical network resources groups that exist in different physical locations or subnets. For example, members of your marketing department and their network resources might be located in several different buildings at your organization, but you can place all of these resources on one VLAN that uses the same IP address range. The VLAN then functions as a single subnet.
You can also use VLANs when you want to segregate a network between different groups of users. After you have determined how you want to define your groups, you can create security groups in Active Directory and then add members to the groups.
You can use the following steps to configure a network policy for VLANs:

Step 1. On the NPS server, in Server Manager, click Tools and then click Network Policy Server.
Step 2. Double-click Policies, click Network Policies, and then, in the details pane, double-click the policy that you want to configure.
Step 3. In the policy Properties dialog box, click the Settings tab.
Step 4. In RADIUS Attributes, ensure that Standard is selected.
Step 5. In the details pane, the Service-Type attribute is configured with a default value of Framed. By default, for policies with access methods of VPN and dial-up, the Framed-Protocol attribute is configured with a value of PPP. To specify additional connection attributes required for VLANs, click Add. The Add Standard RADIUS Attribute dialog box opens.
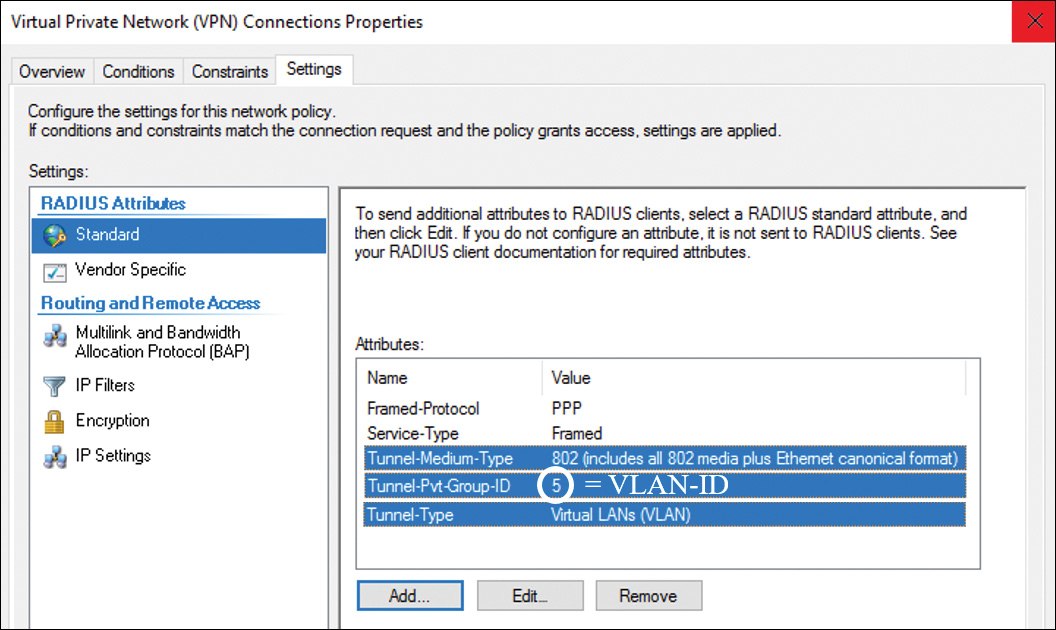
Step 6. In Add Standard RADIUS Attribute, in Attributes, scroll down and add the following attributes:
![]() Tunnel-Medium-Type: Select a value appropriate to the previous selections you have made for the policy. For example, if the network policy you are configuring is a wireless policy, select Value: 802 (Includes All 802 Media Plus Ethernet Canonical Format).
Tunnel-Medium-Type: Select a value appropriate to the previous selections you have made for the policy. For example, if the network policy you are configuring is a wireless policy, select Value: 802 (Includes All 802 Media Plus Ethernet Canonical Format).
![]() Tunnel-Pvt-Group-ID: Enter the integer that represents the VLAN number to which group members will be assigned.
Tunnel-Pvt-Group-ID: Enter the integer that represents the VLAN number to which group members will be assigned.
![]() Tunnel-Type: Select Virtual LANs (VLAN).
Tunnel-Type: Select Virtual LANs (VLAN).
After Step 6, the configuration should look like Figure 11-46.
Step 7. In Add Standard RADIUS Attribute, click Close.
Import and Export NPS Policies

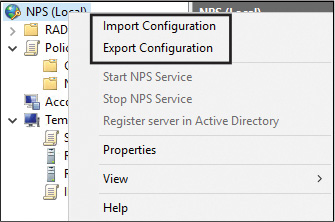
You can export NPS Network Policies, connection request policies, and shared secrets for RADIUS clients and members of RADIUS server groups for a Windows Server 2016 NPS server through the NPS console (see Figure 11-47).
After selecting Export Configuration, you get an information dialog box, which informs you that unencrypted shared secrets are part of the configuration file. The dialog box also tells you that the SQL Server Logging settings are not exported to the file and must be manually configured (see Figure 11-48).
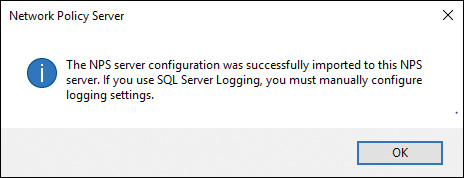
After importing the NPS settings, you get another information dialog box about SQL Server Logging settings (see Figure 11-49).
You also can import or export the NPS settings through PowerShell with the cmdlets Import-NpsConfiguration and Export-NpsConfiguration.
Exam Preparation Tasks
Review All the Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 11-4 lists these key topics and the page numbers where each is found.

Complete the Tables and Lists from Memory
Print a copy of Appendix B, “Memory Tables” (on the book’s website), or at least the section for this chapter, and complete the tables and lists from memory. Appendix C, “Memory Tables Answer Key,” also on the website, includes completed tables and lists to check your work.
Definition of Key Terms
Define the following key terms from this chapter and check your answers in the glossary.
RADIUS client
RADIUS server
RADIUS proxy
RADIUS protocol
NPS server
connection request policy
Network Policy
Network Access Protection
Health Registration Authority
HCAP
End-of-Chapter Review Questions
1. You want to implement some Windows Server 2016 NPS servers as RADIUS servers. You must use EAP authentication. Which scenarios can you configure? (Choose four.)
a. Use a domain or local SAM user accounts database as the user account database for clients.
b. Remotely manage mobile devices through Enterprise Mobility solutions.
c. Use the NPS servers as on-premises MFA authentication servers.
d. Use Remote Access on multiple dial-up servers, VPN servers, or demand-dial routers. Centralize both the configuration of Network Policies and connection logging and accounting.
e. Outsource dial-up, VPN, or wireless access to a service provider. The access servers can use RADIUS to authenticate and authorize connections that are made by members of your organization.
f. Use the Azure MFA authentication server as a RADIUS client for the NPS servers.
g. Centralize authentication, authorization, and accounting for a heterogeneous set of access servers.
2. You want to set up high-availability solutions to forward VPN authentication requests to different RADIUS servers. You install and configure two Windows Server 2016 NPS servers as RADIUS proxy servers. Your domain name is pearson.com. You want to forward connection requests to untrusted domains. Which components on the RADIUS proxy servers do you have to configure to allow them to work as RADIUS proxies to forward requests to Windows Server 2016 RADIUS servers in the domains pucertify.com, eu.pucertify.com, and usa.pucertify.com? You also want to prevent administrative overhead and incorrect configuration on both RADIUS proxy servers. (Choose four.)
a. Create three connection request policies.
b. Create one connection request policy.
c. Create an attribute manipulation rule.
d. Add remote RADIUS server groups.
e. Add three new Network Policies.
f. Add a RADIUS proxy server group to pearson.com.
g. Copy NPS proxy configuration between both RADIUS proxy servers with a script.
h. Configure one RADIUS proxy server group and add the servers into that group.
3. You have to set up 100 servers worldwide. You have to configure 50 VPN servers to forward authentication requests to Windows Server 2016 RADIUS servers in different locations. You also have to configure 50 Windows Server 2016 DirectAccess servers with OTP to forward authentication requests to Windows Server 2016 RADIUS servers. Which PowerShell cmdlet do you have to use on your Windows Server 2016 RADIUS servers to integrate the VPN servers, and how many certificate templates do you need for the Direct-Access OTP RADIUS clients? (Choose two.)
a. Add-RemoteAccessRadius
b. New-NpsRadiusClient
c. Add-NpsRadiusClient
e. 2 certificate templates
f. 1 certificate template
4. You have 200 RADIUS servers in your enterprise. You have configured NPS templates to reduce administrative overhead. Which settings can you configure with NPS templates? (Choose four.)
a. Shared Secrets
b. Connection Request Policies
c. Network Policies
d. Network Access Protection
e. Remote RADIUS Servers
f. RADIUS Clients
g. IP Filters
5. You configure a Windows Server 2016 NPS server as a RADIUS server, and you configure RADIUS Accounting with SQL Server as a repository for accounting data. If no usable stored procedure exists, which SQL query command do you have to run?
a.
CREATE
PROCEDURE
[
dbo
].[Report_NPS]
b.
CREATE
PROCEDURE
[
dbo
].[Report_Event]
c.
CREATE
PROCEDURE
[
dbo
].[Report_XML]
CREATE
PROCEDURE
[
dbo
].[Report_RADIUS]