Appendix A. Answers to the “Do I Know This Already?” Quizzes and End-of-Chapter Review Questions
Chapter 1
Do I Know This Already? Quiz
1. B, D. Domain controller SRV records are typically registered automatically if you install a new domain controller. DCs register the following SRV records automatically: _ldap, _kerberos, _gc, and _kpasswd. If you have to set up Skype for Business or other services, you might have to add SRV records manually. SRV records can be created manually and automatically. TXT and MX records normally have to be added manually into the zone. (Exception: You can write PowerShell scripts to automatically add resource records such as TXT or MX. Records normally are registered automatically through the dynamic update process, but they also can be added manually in the DNS manager console.)
2. B. Round robin is enabled by default on a Windows Server 2016 DNS server. With this setting, you can distribute web requests and network traffic through web servers. If you enable DNSSEC, you get more security. With the Enable Cache Against Pollution setting enabled in the DNS server properties, your DNS server ignores DNS resource records that come from servers that are not authoritative for them, to provide more security. If you enable BIND secondaries, you can use UNIX BIND DNS servers together with Microsoft DNS servers.
3. C. DNS data such as resource records in an Active Directory–integrated DNS zone are stored in the DomainDNSZones or ForestDNSZones Active Directory partition as AD objects and are replicated through the RPC network protocol. By default, this kind of network traffic runs encrypted. If you store resource records in a primary zone and you want to replicate them to a secondary DNS server, the terminology changes from zone replication to zone transfer. In this scenario, you have to allow zone transfer first, and the zone transfer network traffic between primary and secondary DNS servers is unencrypted. If you use an Active Directory–integrated DNS zone and you want to replicate that zone to a secondary DNS server, you also first have to enable zone transfer. In this case, zone transfer also produces unencrypted network traffic.
4. C. Here you want to replicate DNS data through Active Directory replication only to a specific DNS server, not to all servers in the domain or all servers in the forest, which are the two base possibilities through DomainDNSZones and ForestDNSZones. You must create a custom application directory partition and define the replication partners individually. In the zone properties of the test.com zone, you must change the replication scope to the name of the custom application directory partition.
5. A, B. You want to back up only the DNS data from the zone; you do not want to back up the complete Active Directory, including DNS zone data. Therefore, a system state backup is not the right choice; you would back up too much. With the Export-Csv PowerShell cmdlet, you cannot back up the DNS zone. With the dnscmd.exe tool, you can back up (export) zone data into a bak-file. With the PowerShell command Export-DnsServerZone, you also can back up DNS data from the zone.
6. C. In the registry database of a DNS server, normally the ISATAP entry is part of the Global Query Block List. Although you can add an ISATAP host resource record manually to the zone, this still is blocked and clients cannot use it until you remove the ISATAP entry from the registry.
7. B. If conditional forwarders are defined for a given domain, they are used instead of server-level forwarders.
8. B. You can ignore the note because a DNS delegation still was created with the setup of DNS3. You do not have to create a DNS delegation again. Canceling the wizard and trying to set up DNS4 as an additional domain controller for usa.pearson.com with PowerShell are not necessary because that requires too much administrative effort. The Install-ADDSDomainController PowerShell cmdlet has a parameter named CreateDNSDelegation.
In this case, you can set that parameter to a value of $false. Restarting DNS2 and repeating all steps in the Active Directory Installation Wizard is not a solution because it is not a network connectivity problem from DNS4 to DNS3. When you install an additional domain controller such as DNS4, you must have network connectivity to the forest root domain controller. Verifying network connectivity to the forest root domain controllers is not a mistake, but repeating all steps in the Active Directory Installation Wizard is not required and takes too much effort.
9. B. By default, the Windows Server 2016 DNS server opens a pool of 5000 UDP sockets: 2500 for IPv4 and 2500 for IPv6. The default socket pool size value is 2500.
10. A, C. Cache locking is configured as a percent value. For example, if the cache locking value is set to 50, the DNS server will not overwrite a cached entry for half the duration of the TTL. By default, the cache locking percent value is 100. This means that cached entries are not overwritten for the entire duration of the TTL. A low cache locking value increases the chance of a successful cache poisoning attack. Network traffic might be directed to a malicious site. After you have configured the new value for cache locking, you have to restart the DNS service. Clearing the DNS server cache is not necessary.
11. B. When you enable debug logging, you get information about the DNS request types and DNS query packet content. Debug logging is disabled by default on a Window Server 2016 DNS server. As in earlier versions, a Windows Server 2016 DNS server maintains a DNS server log. You can view the DNS server events in the Event Viewer in the Applications and Service Logs folder. It records common events such as Start/Stop DNS Service, Change DNS Configuration Settings, background loading, and zone signing events. You do not have to enable analytic event logging to get the requested information. DNS server analytic events enable you to track activity on the DNS server. An analytic event gets logged every time the server sends or receives DNS information. You can view Windows Server 2016 DNS analytic and debug logs in the Event Viewer. DNS monitoring does not deliver DNS request types and query packet contents.
12. B. Paul must become a member of the security group DNSAdmins because he needs administrative permissions to manage only the DNS server. If you add him to the Domain Admins security group, he gets too-broad permissions. If you add him to the Administrators security group, he gets local administrator permissions. If you add him to the DNSUpdateProxy security group, he cannot manage the DNS server.
End-of-Chapter Review Questions
1. A, C, E. You can protect your Windows Server 2016 DNS server against DNS amplification attacks with the new Response Rate Limiting (RRL) feature. This feature is disabled by default on a Windows Server 2016 DNS server.
With the PowerShell cmdlet Set-DnsServerResponse RateLimiting, you can enable RRL on a Windows Server 2016 DNS server. DNS servers usually use the global query block list to block name resolution to an ISATAP router, and the name ISATAP cannot be resolved to the IP address of the ISATAP router. For test purposes, you might want to remove the ISATAP entry from the DNS global query block list so that the DNS server can use the added hostname resource record named ISATAP to deliver the IP address of the ISATAP router to DNS clients.
You can add or remove entries in the DNS global query block list with the PowerShell cmdlet Set-DnsServerGlobalQueryBlocklist or using the dnscmd.exe tool or registry editing tools.
With Windows Server 2016, you can use DNS server zone transfer policies to specify whether to deny or ignore a zone transfer, based on criteria such as subnet or domain names.
With the PowerShell cmdlet Set-DnsServerZone TransferPolicy, you can update a zone transfer policy on a DNS server, to redefine the conditions of that zone transfer policy.
With the PowerShell cmdlet Set-DnsServerRecursion Scope, you can modify recursion scopes.
With the PowerShell cmdlet Set-DnsServerCache, you can modify the cache settings for a DNS server, such as the maximum cache size or the cache locking percent value. With the PowerShell cmdlet Set-DnsGlobalNamesZone, you can change the configuration settings for a GlobalNames zone.
2. B, D. With the PowerShell cmdlets Set-DnsServerResponseRateLimiting or Set-DnsServerRRL, you first have to enable the new Windows Server 2016 Response Rate Limiting (RRL) feature to protect against DDoS attacks. To exclude App1 from RRL and to ensure that RRL has no negative impact on App1 name resolution, add App1 to the RRL exception list using Add-DnsServerResponseRateLimitExceptionList.
With the PowerShell cmdlet Set-DnsServerDnsSec ZoneSetting, you can configure DNSSEC settings for a zone on a DNS server.
With the PowerShell cmdlet Set-DnsServerEDns, you can configure Extended DNS (EDNS) configuration settings, such as the EDNS information caching timeout. EDNS integrates some DNS protocol extensions concerning DNS data transport of UDP network packets.
With the PowerShell cmdlet Add-DnsServer SigningKey, you can add a key signing key (KSK) or zone signing key (ZSK) to a signed zone.
3. B. On a Windows Server 2016 DNS server, you can enable both analytical and audit logging with the tracelog.exe tool. This can be done through the following command: tracelog.exe -start Dns -guid #{EB79061A-A566-4698-9119-3ED2807060E7} -level 5 -matchanykw 0xFFFFFFFF -f C:analytic_audit.etl.
With the Set-DnsServerDiagnostics PowerShell cmdlet, you can set DNS server debugging and logging parameters, and you can enable debug logging instead of analytical logging.
With the PowerShell cmdlet Set-DnsServerSetting, you can easily import the DNS server settings from one DNS server to the other. You can get the DNS server settings from DNS1 with the following command: Get-DnsServerSetting -computername DNS1 -all | Export-Clixml C:DNS1settings.xml, $a = Import-Clixml C: DNS1settings.xml. After that, you can import the DNS server settings from DNS1 to DNS2 with the command Set-DnsServerSetting -computername DNS2 $a.
The Wusa.exe tool is the Windows Update Standalone Installer that can be used to install update packages.
4. A. On a Windows Server 2016 Nano Server, you can configure some basic local settings through the Nano Server Recovery Console.
You must enable the DHCP client on the Nano Server using the F4 key so that the Nano Server can obtain IP address configuration from the DHCP server. You do not have to reconfigure the NAP server on NAP1 because Windows Server 2016 DHCP server no longer supports DHCP NAP. You do not have to remove and re-create the DHCP reservation on the DHCP server because the other reservations for N01, N02, and N03 have worked fine. If you used the wrong MAC address for the reservation of N04 and you change the reservation for N04 to the correct MAC address, the Nano Server N04 still won’t get an IP address if the DHCP client is not enabled on its network interface.
You do not have to disable a firewall rule on the Nano Server N04 to get an IP address from the DHCP server.
5. B. Under the Advanced tab of the DNS server setting, you have the option Disable Recursion. Normally, this setting is not enabled on a DNS server. If you enable it, this DNS server cannot forward to any other DNS server independently if forwarding is configured through forwarders or conditional forwarders. Recursion (forwarding) is completely disabled in this case. That is the cause of the problem.
With the Store This Conditional Forwarder in Active Directory setting, you can save the forwarder in the Active Directory database, and the forwarder will be replicated automatically through AD replication to other DNS servers.
If recursion still is disabled, this will not solve the problem on this DNS server. The Use Root Hints If No Forwarders Are Available setting is a forwarder setting, not a conditional forwarder setting. In this question, a conditional forwarder was configured instead of a forwarder. Netmask ordering typically is enabled on a DNS server. This has nothing to do with the forwarding possibility on a DNS server, so it is not the correct answer.
6. B. You get maximum performance with a Windows Server 2016 Nano Server. Using a Server Core is also an option, to get faster performance than with GUI-based Windows Server 2016; however, Nano Server is smaller than a Server Core, so it is the smallest kind of DNS server you can use with Windows Server 2016.
You can deploy a new Windows Server 2016 Nano Server with DNS server through the New-NanoServer Image PowerShell cmdlet. A Nano Server offers up to 93 percent smaller VHD size, 92 percent fewer critical patches, and 80 percent fewer reboots. With the Install-WindowsFeature PowerShell cmdlet, you also can install the DNS server role; however, this question asks for a completely new DNS server, which means you also have to build the virtual hard disk for the DNS server. The Add-WindowsFeature PowerShell cmdlet does the same thing as the Install-WindowsFeature cmdlet. The New-Container PowerShell cmdlet creates a container from an existing container image. You cannot install a DNS server into a docker-based container.
7. C. When you want to create a DNS delegation, you can do that during the promotion process for a new domain controller of a new child domain. When you install the first domain controller of a new child domain in the Active Directory Installation Configuration Wizard in the DNS Options page, the option Create DNS Delegation is automatically selected and grayed out. The DNS delegation on a forest root DNS server automatically is created and a forwarder from the child DNS server to the forest root DNS server also is created.
You do not have to use the PowerShell cmdlet Add-DnsServerForwarder to add a forwarder on the child domain DNS server; additionally, you cannot create a DNS delegation manually with this command, so it is not the correct answer.
With the PowerShell cmdlet Install-ADDSForest, you can build a new forest with the installation of the forest root domain controller. You cannot create child domains with that PowerShell cmdlet.
Using the PowerShell cmdlet Install-ADDSDomainController, you cannot install a new first child domain controller with a delegated DNS server; instead, you can add more domain controllers to existing domains.
8. C. In the Recovery Console of a Windows Server 2016 Nano Server, you cannot define or configure the DNS server; Nano Server must use its network interface. Instead, you can do this with the PowerShell cmdlet Set-DnsClientServerAddress. You can define the computer name, gateway address, and IPv6 address of the Nano Server in the Nano Server Recovery Console.
Chapter 2
Do I Know This Already? Quiz
1. A, E. A stub zone hosts only the SOA record, NS record, and A record of authoritative DNS servers of a zone. In a stub zone, you have listed master DNS servers from a zone, and you can find the IP addresses of those master servers. You need this information to know about these DNS servers so that you can configure forwarding to them. Client resource records and records from other servers, such as mail servers and file servers, are not transferred to a stub zone.
2. A. With a file-based DNS zone, you cannot use the secure dynamic update feature. This is not correct. All other answers are correct.
3. D. You simply can copy the zone file from the DNS server of the productive domain to the DNS server of the future domain and import that file. You can select the zone file in DNS manager only if you copy it to the %systemroot%system32dns folder of that DNS server. When you create a forest trust between the two forests, you still cannot replicate Active Directory data between the forests. No option exists for replicating this through different forests. When you create a stub zone on the DNS server of the future domain, you lose all DNS records except SOA, NS, and A records of DNS servers. All resource records of all other servers and clients are not transferred to a stub zone. When you convert the stub zone to a primary zone, you do not have all the DNS data of pearson.com as in the productive domain. When you transfer the DNS data of pearson.com to a secondary DNS server, this server is not authoritative for the zone; instead, the zone in the future domain then is read only and DNS data is not saved in Active Directory.
4. B. You can secure the zone transfer from BIND1 to SEC1 through IPsec. You cannot use the Transaction Signature (TSIG) network protocol and TSIS resource records for that because Microsoft DNS servers do not support TSIG; instead, they use GSS-TSIG. It is not possible to configure Windows Servers running Microsoft DNS service to perform zone transfers from servers running BIND DNS configured as the master with TSIG protection. You also cannot use the HMAC-MD5 algorithm because Windows Server 2016 does not support this.
5. C. You should create an AD-integrated stub zone on DNS servers in usa.pearson.com because all DNS server records (NS records) in usa.pearsonucertify.com will be transferred from the DNS servers (master) in usa.pearsonucertify.com to the stub zone DNS server in usa.pearson.com.
You must select the stub zone type for the usa.pearson.com zone because the NS and A records of the DNS servers in usa.pearsonucertify.com are interesting only for you to know, not for clients or other servers. When you know the IP addresses of the new DNS servers in the zone usa.pearsonucertify.com through the stub zone, you can implement conditional forwarding on the DNS servers of usa.pearson.com to the new DNS servers of usa.pearsonucertify.com. When you create a conditional forwarder on a DNS server in usa.pearson.com, you can do that only if you know about the IP address of the DNS servers you want to forward.
You must get that IP address automatically through the use of a stub zone. You also can use a file-based stub zone, but this is not the best solution; you get more security and automatic replication of the stub zone to the other AD-integrated DNS server in the same domain only if you integrate the stub zone into Active Directory. Creating a secondary zone also will deliver NS and A records of the DNS server from usa.pearsonucertify.com, but it will do so for all other resource records as well (clients and other servers); this is not necessary because you have to know only about DNS servers.
6. A, B. You can use the dnscmd command-line utility and the Set-DnsServerGlobalNameZone PowerShell cmdlet to enable GlobalNames support.
7. D. Since Windows Server 2016, a DNS server supports the standards NSEC3 and RSA/SHA-2.
8. A. With Windows Server 2016, you have enhanced zone-level statistics possibilities. You can use ZoneQueryStatistics to get information about DNSKEY records on your DNS server. You cannot use ZoneUpdateStatistics because that gives you information about dynamic update behaviors. You cannot use ZoneTransferStatistics because that gives you information about zone transfer between master and secondary DNS servers. You cannot use RRLStatistics because that gives you information about Response Rate Limiting (RRL) behaviors, which is a new feature of Windows Server 2016.
9. C. DNS records added dynamically are time stamped. Static records that you enter manually have a time stamp value of 0; therefore, they will not be affected by aging and will not be scavenged out of the database. Instead, you must remove them manually. An exception to the exception arises if you use the new Windows Server 2016 PowerShell cmdlets, such as Add-DnsServerResourceRecordPtr or Add-DNSServerResourceRecordA. These cmdlets have a parameter named AgeRecord. Using this parameter, the DNS server can use a time stamp for the record that these cmdlets add.
10. C. You can use TLSA records. With Windows Server 2016 and DNSSEC, a new protocol called DANE (DNS-Based Authentication of Named Entities) enables you to securely specify exactly which TLS/SSL certificate an application or service should use to connect to your site. You can use TLSA records in four ways:
1) to specify the CA that will provide RLS certificates for the domain, 2) to specify the exact TLS certificate that should be used, 3) to specify the trust anchor to be used for validating the TLS certificate for the domain, and 4) to specify the exact TLS certificate that should be used for the domain, but without needing the TLS certificate to be signed by a valid CA (for self-signed certificates).
You cannot use TSIG, RRSIG, or DNSKEY resource records to verify the CA, certificate, or trust anchor.
11. D. You can stop the analytical event tracing on the DNS server with the tracelog -stop DNS command. You cannot stop analytical event tracing on the DNS server with the Set-DnsServer Diagnostics -EnableLoggingForServerStartStopEvent $true PowerShell command because that gives you log start and stop events of the DNS server. You also cannot use Set-DnsServer Diagnostics -DebugLogging 0x10000 to stop analytical event tracing on the DNS server because that enables DNS logging for sent packages. You cannot use the PowerShell cmdlet Stop-PefTraceSession because that stops a specified trace session of the Message Analyzer utility.
End-of-Chapter Review Questions
1. B. Since Windows Server 2016, you can use and add TLSA resource records or other unknown resource records. TLSA resources are needed for DANE configuration. You can use the DANE protocol to secure your SSL/TLS certificates via DNSSEC.
You can easily generate TLSA resource records through the TLSA online generator: https://www.huque.com/bin/gen_tlsa.
If you change the DNS zone to an AD-integrated zone with forest replication on a Windows Server 2012 R2 DNS server, this server does not support TLSA resource records. If you add another Windows Server 2016 DNS server as the secondary, you still cannot use TLSA resource records because a secondary zone is read-only and you cannot add any records manually there. If you enable BIND secondaries to use UNIX DNS servers as secondaries, you still have no DNS server where you can add TLSA resource records.
2. B. With the PowerShell command Start-DnsServerZoneTransfer, you can immediately start the DNS zone transfer process between the DNS server, DNS1, and the secondary DNS server, DNS2. This is the fastest solution. Converting the zone eu.pearson.com to an AD-integrated zone is not necessary because it is still saved in Active Directory on DNS1. You can change the zone on DNS2 from a secondary zone to an AD-integrated zone, but then you have AD replication of the DNS zone data and no zone transfer, which this question requires. For security reasons, using two DNS servers is recommended with an AD-integrated zone. With the Repadmin /replicate DNS2 DNS1 DC=eu,DC=pearson,DC=com command, you force the AD replication of the domain partition eu.pearson.com. If you add DNS2 to the notify list on DNS1, this reduces the zone transfer time for the zone transfer from DNS1 to DNS2 in the case of changes or new resource records on the zone, but it does not immediately force the zone transfer.
3. D. With the Add-DnsServerResourceRecord PowerShell cmdlet, you cannot change the TTL value of an existing resource record. With that PowerShell cmdlet, you can add a new resource record and define a new TTL for that record. For example: Add-DnsServer ResourceRecord -ZoneName “Contoso.com” -A -Name “SRV1” -Allow UpdateAny -IPv4Address “10.10.1.12 -TimeToLive 04:00:00 -AgeRecord.
4. A, D. Download and install the Windows Driver Kit (WDK) to get the tracelog.exe command-line utility. You can see tracelog.exe included when you install the WDK, Visual Studio, and the Windows SDK for desktop apps. With tracelog.exe, you can enable or disable DNS analytical logging. Debug logging is another option on the DNS server, but this is not the analytical logging feature. With the Test-DnsServer PowerShell cmdlet, you can run some tests on the DNS server, but this is not the DNS analytical feature. With nslookup and the -d2 parameter, you can test zone transfers, security options, and MX record resolution. With the -d2 parameter, you can get detailed debugging information through the analytical DNS logging feature.
Chapter 3
Do I Know This Already? Quiz
1. B. DHCP Policies are a possible cause because you can configure DHCP scope options through a DHCP Policy based on different criteria. It seems that a DHCP Policy is responsible for delivering other options to some clients. The DHCP failover feature is not the possible cause here because you have only a single DHCP server. DNS Policy also is no cause of this because you cannot deliver DHCP options through DNA Policies. With DNSSEC, you sign zones; this has nothing to do with which DHCP options a DHCP client gets.
2. C. You can use the Name Protection feature of the DHCP server to protect against name squatting attacks. Such conflicts happen if one client registers a name with DNS but another client is already using that name. With DHCP server policies (new Windows Server 2012 feature), you can create policies that deliver specific IP address and option information to clients based on a set of conditions. This enables you to have different types of IP devices receive addresses and other options from a subset of IP addresses in the scope range; it does not protect against such name squatting conflicts. With DNS server policies (new Windows Server 2016 feature), you can manipulate how a DNS server handles queries based on different factors.
As an example, you might create a DNS Policy to respond to queries asking for the IP address of a web server to respond with a different IP address based on the closest datacenter to the client. This differs from netmask reordering because the client does not have the same local subnet address of the web server, but the web server is closer than others from the client’s perspective. DNSSEC enables a DNS zone and all records in the zone to be signed cryptographically so that client computers can validate the DNS response.
DNS is often subject to various attacks, such as spoofing and cache tampering. DNSSEC helps protect against these threats.
3. A. You configure the DNS server’s IP address for the network interface of a DNS client through the Set-DnsClientServerAddress PowerShell cmdlet.
4. B. With the Sync-DnsServerZone PowerShell cmdlet, you synchronize DNS zone data and root hint data for a zone to the persistent storage. With the Start-DnsServerZoneTransfer PowerShell cmdlet, you start a zone transfer for a secondary DNS zone from master servers.
With the Add-DnsServerZoneTransferPolicy PowerShell cmdlet, you add a zone transfer policy to a DNS server.
With the Set-DnsServerZoneTransferPolicy PowerShell cmdlet, you update a zone transfer policy on a DNS server.
5. A, D, E, F. You should verify the DHCP Policies as a possible cause that clients from the Paris subnet are getting the wrong DNS server for name resolution through DHCP options configured through DHCP Policy. You also should verify the DNS server zone scope settings on the DNS server because name resolution could be restricted through a DNS Policy based on subnet criteria. You also have to verify the DNS server client subnet settings on a DNS server because the subnet Paris might have been accidentally added to a DNS server policy zone scope.
In addition, you should verify the DNS server recursion policy settings because selective recursion might be enabled, preventing clients from the subnet Paris from being forwarded to other DNS servers responsible for pearsonucertify.com. You do not have to verify DNS server options. You also do not have to verify DNS server zone transfer policies because you use them to manage which zones can be transferred between DNS servers.
6. B. You use the Get-NetRoute PowerShell cmdlet to list the routing table of the client. There you can see the IP address of the client-side tunnel endpoint of the Point-to-Site tunnel to Azure. You cannot use the PowerShell cmdlet Get-AzureVNetGateway because it shows you the configuration settings of the VPN gateway on Azure. You also first must install the Azure PowerShell module to make that command possible on the client. You cannot use the Get-NetIPInterface PowerShell cmdlet because it shows you only the interface settings, not the routing table. You cannot use the PowerShell cmdlet Get-VpnConnection because it also does not display the routing table.
7. D. DirectAccess clients on the Internet use the preconfigured NRPT settings to evaluate the DNS servers for name resolution to access internal resources. The DHCP server at the airport delivers an IP address, gateway, and DNS server so that public name resolution can happen.
The Name Resolution Policy Table (NRPT) delivers the DNS servers for the company name resolution. The entries in the NRPT are delivered through DirectAccess GPOs, which are created as part of the setup for the Direct-Access server. The DHCP server of the company normally is not responsible for delivering any IP settings for a DirectAccess client on the Internet.
8. B, C, D. You can use the Set-DnsServerRecursionScope PowerShell cmdlet to deactivate recursion for all clients through the existing default recursion scope. You must use the Add-DnsServerRecursionScope PowerShell cmdlet to add a scope for internal clients to allow recursion.
You can use the Add-DnsServerQueryResolutionPolicy PowerShell cmdlet to create the DNS server policy to configure selective recursion with different settings for external and internal clients.
You would not use the PowerShell cmdlet Add-DnsServer ResourceRecord here because it is necessary if you create DNS Policy zones and want to add records to those zones.
You would not use the Add-DnsServerClientSubnet PowerShell cmdlet because you do not want to configure recursion policy for a special subnet.
End-of-Chapter Review Questions
1. C. You should use Add-DnsServerQuery ResolutionPolicy -Name MalwarePolicy -Action IGNORE -ClientSubnet ‘EQ, CHSubnet1’ -Disable $false because this new DNS server policy blocks all name resolution traffic from subnet CHSubnet1. The existing policy CHPolicy allows name resolution, but the blocking policy is more powerful than this.
The parameter action has the value IGNORE, which means to not respond.
You should not use Add-DnsServerQuery ResolutionPolicy -Name MalwarePolicy -Action DENY -ClientSubnet ‘EQ, CHSubnet1’ -Disable $false because the parameter Action with a value of DENY means that it delivers a response with SERV-FAIL.
You should not use Add-DnsServerQuery ResolutionPolicy -Name MalwarePolicy -Action DENY -ClientSubnet ‘EQ,NYSubnet2’ -Disable $false because the parameter Action with a value of DENY means that it delivers a response with SERV-FAIL.
You should not use Set-DnsServerQuery ResolutionPolicy -Name NYPolicy -Action IGNORE -ClientSubnet ‘EQ, NYSubnet2’ -Disable $true because the subnet 192.168.6.0/24 is not a member of the zone scope NYScope. If the subnet is not part of the zone scope and DNS server policy, you cannot block name resolution traffic by disabling NYPolicy.
2. A. You should use the command Add-DnsServerClientSubnet -Name “AllowedNET” -IPv4Subnet 172.16.0.0/16 -PassThru. If you do not define the subnet behind the subnet name AllowedNET before you add the DNS server query resolution policy, it cannot identify the subnet.
With the PowerShell cmdlet Remove-DnsServerClientSubnet, you remove an existing subnet. With the PowerShell cmdlet Add-DnsServerResourceRecord, you add a DNS resource record to a DNS server zone scope.
With the PowerShell cmdlet Add-DnsServerZoneScope, you add a DNS server zone scope.
3. B. You should use the PowerShell command Add-DnsServerZoneTransfer Policy -Name “IntTransfer” -Action IGNORE -ServerInterfaceIP “ne,10.0.0.50” -PassThru -ZoneName “pearson.com” because this denies zone transfer traffic to DNS3.
You do not have to use Add-DnsServerZoneTransferPolicy -Name “IntTransfer” -Action ALLOW -ServerInterfaceIP “ne,10.0.0.49” -PassThru -ZoneName “pearson.com” or Add-DnsServerZoneTransferPolicy -Name “IntTransfer” -Action ALLOW -ServerInterfaceIP “ne,10.0.0.51” -PassThru -ZoneName “pearson.com” because you do not have to allow DNS2 and DNS3 again.
With the PowerShell command Add-DnsServerZoneTransferPolicy -Name “IntTransfer” -Action IGNORE -ServerInterfaceIP “ne,10.0.0.10” -PassThru -ZoneName “pearson.com”, you deny any zone transfer traffic to DNS1; this is wrong because DNS1 is the master DNS, not the secondary DNS server.
Chapter 4
Do I Know This Already? Quiz
1. B. In versions before Windows Server 2016, it was possible to enable or disable DNSSEC validation on the Advanced tab of the DNS server. In Windows Server 2016 DNS server, this setting is no longer possible. Instead, you can use PowerShell to enable or disable DNSSEC validation. You can do this with the following PowerShell command: (Get-DnsServer).DNS Setting.EnableDnsSec. With the PowerShell cmdlet Get-DnsServerDnsSecZoneSetting, you can verify DNSSEC zone settings. With the dnscmd.exe command, you also can enable DNSSEC validation on a Windows Server 2016 DNS server, but you must use 1 instead of 2 for the EnableDNSSEC parameter.
2. B. If the key master DC1 is offline and cannot be recovered, it is still possible to move the role to another server. This is known as seizing. When you want to seize the key master role, DC2 must have access to the zone’s existing private key data. This is the case if the keys are stored in AD (only for AD-integrated zones) or another shared location, such as a certificate or hardware security module (HSM).
If the zone’s private key data is not available, the role can still be seized, but new keys must be generated and the zone must be re-signed with them. Any distributed trust anchors for the zone must then be redistributed. Because you have no hardware solution (HSM module) in this scenario, you cannot get the key data from there. The zone is a file-based zone. When an AD-integrated zone is signed with DNSSEC, the private keys are also replicated to all DNS servers running DCs, with one exception: Private keys are not replicated to an RODC. Replication is not done to DC3, then, because it is an RODC. This is the reason you cannot get key data from Active Directory; you can get key data only from a certificate in this case.
3. A. You cannot use the DNSSEC Zone Signing Wizard to create DS records with that wizard. Only DNSKEY records can be automatically created through the wizard.
After you create them, you can view them in the DNS Manager in the TrustPoints folder. You can use the DS record set (DSSET), a file in the C: windowssystem32dns folder, to import DS records. You can import DS records from that file with the following PowerShell command for a zone named pearson.com: Import-DnsServerResourceRecordDS -ZoneName pearson.com -DSSetFile “c:windowssystem32dnsdsset-pearson.com. You also manually can add DS records with the DNS Manager or directly through PowerShell.
4. B. If trust anchors are not removed when a zone is unsigned, DNS servers will continue to attempt validation of DNS responses for the zone. However, this validation will fail and, therefore, DNS resolution for the zone will fail. When you unsign the zone, all RRSIG records automatically are removed from the zone if you use the DNSSEC Zone Signing Wizard for that. The NRPT settings do not have to be reconfigured because the DNSSEC clients still have to be enabled for DNSSEC to use it with other DNSSEC-enabled DNS servers or zones. The RRset is a set of DNSSEC records and is removed automatically through the unsigning process.
5. B. You can force the rollover with the PowerShell cmdlet Step-DnsServerSigningKey Rollover. For example, you can get the keys for the signed zone sec.pearson.com with the following PowerShell cmdlet: Get-DnsServerSigningKey -ZoneName “sec.pearson.com”. After that, you can force the KSK rollover that is waiting for a parent DS update on sec.pearson.com with the following PowerShell command: Step-DnsServerSigning KeyRollover -KeyID <ID> -ZoneName “sec.pearson.com” -force.
With the PowerShell cmdlet Invoke-DnsServerSigning KeyRollover, you can initiate a rollover of input keys for the specified DNS zone.
With the PowerShell cmdlet Enable-DnsServerSigning KeyRollover, you can enable rollover on the input key.
With the Grant-HgsKeyProtectorAccess PowerShell cmdlet, you can grant access to a Host Guardian Service (HGS) for a key protector. The HGS is used to protect Hyper-V shielded virtual machines. This has nothing to do with the question and, therefore, is a wrong answer.
6. A, D. You use the prepublishing rollover method for the ZSK that makes the new DNSKEY record available before signing. You propagate the key to all client caches, remove the old signatures, and create new ones with the new key. This does not double the size of your zone. It replaces signatures as they expire. You can roll over each zone and ZSK separately. You use the double signing method for KSK because you simultaneously sign the zone with both (old and new) keys. Both signatures are held in the zone until the old public key expires. When the time passes, the old key is removed. This reduces risk and is preferred for the KSK rollover.
7. A, C. On client1, you must update the GPO settings from the Default Domain Policy, which delivers the NRPT settings and makes client1 a DNSSEC-enabled client. After that, you can verify the DNSSECValidationRequired value with the Get-DnsClientNrptPolicy PowerShell cmdlet. You get the following output:
Namespace : .sec.pearson.com
QueryPolicy :
SecureNameQueryFallback :
DirectAccessIPSecCARestriction :
DirectAccess ProxyName :
DirectAccessDnsServers :
DirectAccessEnabled :
DirectAccessProxyType : NoProxy
DirectAccessQueryIPSecEncryption :
DirectAccessQueryIPSecRequired : False
NameServers :
DNSSECIPSecCARestriction :
DNSSECQueryIPSecEncryption :
DnSecQueryIPSecRequired : False
DNSSECValidationRequired : True
NameEncoding : Utf&WithoutMapping
You cannot use the Resolve-Dnsname PowerShell cmdlet to verify the DNSSECValidationRequired setting. With that you can query a signed zone with DNSSEC validation required, and if a trust anchor is present on DNS1, the query is successful even if validation is required.
8. B. Only one DS trust anchor has to be installed for the parent zone. Delegations establish a chain of authentication for child zones. If all zones in the chain are signed with DNSSEC, resolving DNS servers can have a single DS trust anchor installed, provided that appropriate DS records are available in the parent zone. This way, it is not necessary to install a trust anchor for every zone that a caching DNS server can validate. Build a chain of trust where it is sufficient for the DNS server to have only one DS trust anchor installed for the parent zone.
9. B, C. With dnscmd /retrieveroottrustanchor, you can install the root trust anchor. With the PowerShell command Add-DnsServerTrustAnchor -Root, you also can do so. With the PowerShell command Import-DnsServerTrustAnchor, you can import a trust anchor through the specified DS set file but not the root trust anchor. With Add-DnsServerTrustAnchor -KeyProtocol DNSSEC -CryptoAlgorithm RsaSha256, you can install trust anchors but not the root trust anchor; you also have to know the Base64Data value, which is the key data.
10. D, E. NSEC3 records hash the names of existing hosts. A zone that uses NSEC3 also has a NSEC3PARAM record. This is necessary for the proper functioning of NSEC3.
End-of-Chapter Review Questions
1. B. You cannot change the replication scope or zone type of a signed zone as long it is a signed zone. First, you must unsign the zone. Then you can change the replication scope of the zone from application directory partition to forest-wide replication. After that, you must re-sign the zone. When you create a new zone, you can choose to get the DNSSEC parameters for the zone from another zone through a file, but then the zone has another name and this is not wanted.
2. A. You must use the Key Master tab of the DNSSEC properties of the zone, and there you must select Use the Following DNS Server as the Key Master. You also must choose DC3 as the new key master. You must do that at DC3.
In this question, you are sure about the proper functionality of AD replication between DC3 in Azure and the on-premises domain controllers because AD replication was successfully tested. This also means that DC3 can resolve all necessary resource records of the other domain controllers. Thus, it should be possible to get all the names of the other domain controllers in the drop-down list on the Key Master page.
You cannot use the Reset-DnsServerZoneKey MasterRole -SeizeRole PowerShell command because, with the SeizeRole parameter, you do not perform an online role transfer, in which you can reach the original key master, DC1; instead, you seize the role to DC3, which means that keys must be generated, the zone must be re-signed, and trust anchors must be redistributed. This is not necessary if the key master is online and reachable, as in this scenario.
You also cannot use the Reset-DnsServerZone KeyMasterRole -Force PowerShell command because the Force parameter does not give you any confirmation about the transfer process.
3. F, I. DLV records are not necessary in a pure Windows environment. They are used together with BIND. BIND also is not necessary in this environment because you have only Windows servers. All other DNSSEC deployment steps are usable.
4. B. An RODC at a branch site cannot transfer DNS data or keys from Active Directory to a domain controller in a headquarters (HQ) site because such keys should not exist in an unsecure branch site. Instead, the RODC creates a secondary zone to transfer the DNS data from a primary DNS server. By default, the RODC uses the nearest writeable DC as the primary. In this case, this can be only DC1 or DC2 because no other domain controllers exist in this environment. The RODC cannot transfer the zone if that was not manually enabled on the primary DNS server.
You can enable zone transfer in the DNS Manager console or through PowerShell with the cmdlet Set-DnsServerPrimaryZone. After enabling zone transfer for the RODC, the zone can exist as secondary zone on the RODC. To allow UDP DNS replies larger than 512 bytes through the firewall, DNSSEC must work throughout the network.
In this scenario, however, the zone transfer was not allowed, and this is the more probable cause of the problem. Installing an additional RODC at the branch site is no solution because the RODC zone transfer must be enabled and you have doubled your AD replication traffic from the HQ site to the branch site. Installing an additional writeable domain controller at the branch site is a solution for getting a DNS server with a signed AD-integrated zone at the branch site, but you chose an RODC for the branch site for a reason: It is a physically unsecure site, so you do not want a writeable domain controller there.
5. A. A zone signed on a Windows Server 2008 R2 cannot be unsigned through the PowerShell cmdlet Invoke-DnsServerZoneUnsign. To unsign a zone on a legacy DNS server, you must use legacy procedures on the legacy server.
Chapter 5
Do I Know This Already? Quiz
1. A, B. DANE enables you to specify which CA is allowed to issue certificates for a resource and can authenticate TLS client or server entities without the use of a CA. DANE increases DNS response performance from Windows Server 2016 DNS servers because of the DNSSEC validation. DANE does not simplify certificate validation in a mixed IPv4/IPv6 environment because one domain name normally has one associated TLSA record; in this case, one TLSA record cannot match two different certificates.
2. D. Self-Signed Certificate Constraint is not a DANE operation mode. Instead, DANE can work in four different operation modes: 0, 1, 2, and 3. Mode 0 stands for CA specification: DANE accepts TLS certificates from only a specific CA. Mode 1 is for the Specific TLS certificate; only the exact TLS certificate can be used for the domain. This certificate must be issued by a valid CA. Mode 2 is for trust anchor assertion, which specifies the trust anchor to be used for validating the TLS certificates for the domain. Mode 3 is for domain-issued certificates, which specifies the exact TLS certificate that should be used for the domain; the TLS certificate does not need to be signed by a valid CA. This allows for the use of self-signed certificates.
3. A, C. You can use TLSA records to associate a TLS server certificate with the domain name where the record is found, thus forming a TLSA certificate association. TLSA records can be used to validate self-signed certificates and X.509 certificates from certification authorities (Symantec, Comodo, StartSSL, CACert, and so on). Normally, you use TLSA records together with DNSSEC and RRSIG records to protect the TLSA record.
4. B. You must use DomainIssuedCertificates because only with that value can you use TLSA records for self-signed certificates.
5. D. You should use the _443._tcp.usa.nutex.com. IN TLSA 3 1 1 TLSA record because it uses the TLSA Usage Field parameter 3 - DANE-EE: Domain Issued Certificate. This value disables the trust hierarchy inspection. The client has to trust only the referenced certificate in the TLSA record. The Matching-Type field has a value of 1, which means that the SHA-256 hash is used. You should not use _443._tcp.usa.nutex.com. IN TLSA 0 1 1 because this TLSA record uses the TLSA Usage Field parameter 0 - PKIX-TA: Certificate Authority Constraint. With this value, the client is invited to accept only defined certificate authorities. The certificate also must pass the trust hierarchy inspection. You should not use _443._tcp.usa.nutex.com. IN TLSA 1 1 1 because this TLSA record uses the TLSA Usage Field parameter 1 - PKIX-EE: Service Certificate Constraint. With this value, the client is invited to accept only defined certificates. You should not use _443._tcp.usa.nutex.com. IN TLSA 2 1 2 because this TLSA record uses the TLSA Usage Field parameter 2 - DANE-TA: Trust Anchor Assertion. With this value, the client must use a validated trust anchor.
6. D. You should use unknown record support because, with the newly added support for unknown record types (RFC 3597), you can add previously unsupported record types such as TLSA into Windows DNS server zones in binary format.
In this example, a TLSA record is added. TLSA records are required for DANE. Other examples for such unknown record types are SMIMEA, OPENPGPKEY, TA, and TALINK.
You should not use DANE because DANE is a validation mechanism to validate certificates and certificate authorities. DANE servers can verify whether a certificate really comes from the relevant CA.
You should not use DNS Policies because this feature (also a new Windows Server 2016 feature) controls how a DNS Server handles queries based on different parameters. For example, you might create a DNS Policy to respond to a query asking for the IP address of a web server with a different IP address, based on the closest datacenter to the client.
You should not use Response Rate Limiting because this feature (also a new Windows Server 2016 feature) tries to extenuate DNS amplification attacks. It does not allow you to add unknown records such as TLSA records.
You should not use IPv6 root hints because this feature (also a new Windows Server 2016 feature) allows a Windows Server 2016 DNS server to use IPv6 root servers for name resolution.
7. This is the correct order of steps:
1. e. Export the X.509 binary certificate data to the .CER file.
2. i. Open the TLSA record generator.
3. a. Fill in the Usage, Selector, and Matching Type fields.
4. c. Paste the X.509 binary data of the certificate into the TLSA record generator.
5. d. Fill in the port number with 443.
6. f. Fill in the transport protocol with TCP.
7. h. Fill in the domain name with pearson.com.
8. j. Select Generate.
9. k. Use the key value from the generated TLSA record as the Certificate-AssociationData parameter value on your Add-DnsServerResourceRecord command.
10. l. Add the TLSA record with Add-DnsServerResourceRecord.
The following steps are incorrect:
b. Use the thumbprint of your certificate as the CertificateAssociationData parameter value on your Add-DnsServerResourceRecord command. (You cannot use the thumbprint of a certificate as the CertificateAssociationData parameter value for your Add-DnsServer ResourceRecord command. You need the value generated through the TLSA record generator.)
g. Fill in the domain name with srv01.pearson.com. (You must use the name of the zone for the domain name parameter.)
8. A. Before you deploy the planned certificate chain, make sure that the TLSA records that match the planned certificate chain are published in addition to the records that match the current chain. After deploying the planned certificate chain, you can remove the TLSA records that match the previous chain. When your TLSA records are CNAME records pointing to a location where your organization’s issuing authority maintains suitable TLSA records for you, you can deploy new certificates from that authority without updating the server’s TLSA records. The burden of key rollover falls on that authority before it issues any certificates via a new certificate or key. Editing existing TLSA records to match a new certificate chain is not supported or recommended.
End-of-Chapter Review Questions
1. C. You must use the PEM format X.509 certificate data. You can generate that using the TLSA record generator online tool. You cannot use the public key, thumbprint, or serial number of the certificate to do so.
2. B. In Figure 5-13, you can see that the zone pearson.com is not signed with DNSSEC. You can add TLSA records to an unsigned zone (as shown in the figure), but then the TLSA record is not protected through a RRSIG record. You must sign the zone pearson.com with DNSSEC. After that, the TLSA record is protected through the RRSIG record. Requesting a new server certificate is not necessary because you have to then repeat the creation of the TLSA record. Removing Everyone from the ACL of the TLSA record removes access to the TLSA record for all; then no one can use the TLSA record for certificate validation. Activating DNSSEC client settings through GPO in the NRPT is necessary when you want to use DNSSEC internally for domain clients, but this will not secure the TLSA record on the DNS server.
3. B, C. Optimally, developers of application clients that depend on DANE-SRV want to reduce the wait time for end users trying to make a connection to a service. To make this possible, a DNS library might perform the SRV queries and TLSA queries in parallel. Performing TLSA queries in parallel with SRV record queries is not harmful from a security perspective and can yield some operational benefits. You also must use at least one TLSA record that authenticates the server’s certificate (RFC 7673).
4. The correct answer follows:
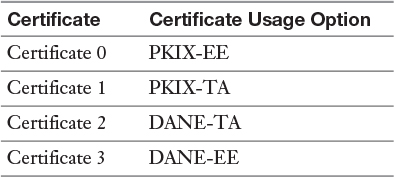
PKIX-EE is another term for Certificate Usage Option 0. PKIX-EE is another term for Certificate Usage Option 1. DANE-TA is another term for Certificate Usage Option 2. DANE-EE is another term for Certificate Usage Option 3.
Chapter 6
Do I Know This Already? Quiz
1. A. With the PowerShell cmdlet Export-DhcpServer, you can export the complete DHCP Server configuration, including scope configuration, to an XML file. This exports or backs up only the configuration settings, not the DHCP data. This is exactly what the question asks for. You can transfer the settings from one DHCP server to another, but not the DHCP data. With the PowerShell cmdlet Import-DhcpServer, you can import the previously exported DHCP configuration data into your new Windows Server 2016 DHCP server. With the Backup-DhcpServer PowerShell cmdlet, you perform a complete backup of all DHCP data (DHCP leases, reservation leases, and so on). With the Restore-DhcpServer PowerShell cmdlet, you can restore DHCP data.
2. C, D. On a Windows Server 2016 Nano Server, running a DHCP Server service is not possible. Therefore, you have to replace the Nano Server with a Windows Server 2016 Datacenter server with GUI or Server Core, install the DHCP server role, and authorize that server in ADDS. Then you can add DHCP2 as a DHCP failover replication partner. You cannot authorize DHCP2 in ADDS because you cannot install a DHCP server role on it. You can add DHCP2 to the domain pearson.com; however, it is still not a DHCP server and cannot work as a DHCP failover replication partner for DHCP1.
3. C. You cannot create a multicast scope with the default New Scope Wizard in the DHCP Manager or through the PowerShell cmdlet Add-DhcpServerv4Scope. You must use the New Multicast Scope Wizard in the DHCP Manager or the PowerShell cmdlet Add-DhcpServerv4 MulticastScope to create a multicast scope starting with 224.
4. B. You cannot add DHCP option 60 (pre-boot execution [PXE] client) with the Add-DhcpServerv4OptionDefinition PowerShell cmdlet. For that, you have to use the netsh command. You must configure 60, 66, and 67 because the WDS server also hosts the DHCP server on the same machine.
5. C. You need to install a DHCP relay agent as a solution so that DHCP client requests from Chicago and Subnet2 can be forwarded to DHCP1 as unicast traffic. The relay agent must be in that network, where the DHCP clients come from. Adding a second DHCP server in Subnet1 does not solve the problem because then you have two DHCP servers in the same subnet, which produces new problems. Installing a second DHCP server in Subnet2 and then using the DHCP failover feature seems to be a good idea because then DHCP clients from Subnet2 can get IP addresses from a DHCP server in their own network, but in this scenario, you cannot install an additional DHCP server in Chicago. You have no reason to install a DHCP relay agent in Paris because the Paris DHCP clients have no problems getting IP addresses from the DHCP server in Paris.
6. B. When the DHCP server is configured to perform DNS dynamic updates on behalf of DHCP clients, you can use the DHCP audit logs to monitor that. Event ID 31 is the event type about failed DNS dynamic update events. You cannot view that on a DNS server or the DHCP client. Events with event ID 30 are successful DNS dynamic update events.
7. B. When you have to use default settings, you cannot use the DHCP failover load sharing mode because the default setting for a split is 50:50. In this case, you must configure two DHCP servers manually with 70 percent of the scope on one DHCP server and 30 percent of the scope on the other DHCP server.
8. B. When you want to have less administrative effort and make the DHCP Server service highly available, you can do so through the DHCP failover feature in hot standby mode. Building a failover cluster requires much more administrative effort. A DHCP failover with load sharing mode works for a split-scope configuration and the Hyper-V replica feature makes Hyper-V VMs high available, but for that you need another Hyper-V host.
9. B. When you use DHCP Policies to direct foreign DHCP clients to a guest DNS suffix, you must use the FQDN and the operator Is Not Single Label because, in this question, you have foreign clients that are domain-joined clients at also.ch domain. Through Group Policies, you cannot register foreign DHCP clients using a guest DNS suffix. You use the DHCP Policy operator Is Single Label when the DHCP clients are workgroup clients and they have no suffix. You use the DHCP Policy condition MAC address to deliver the DHCP options of that DHCP Policy to specific clients with specific MAC addresses. In this case, you do not know about the MAC addresses of the foreign clients, so you cannot preconfigure these MAC addresses on the DHCP Policy as a condition. With a DNS zone scope policy, you can configure different name resolution answers based on different criteria for DNS clients. With a DNS recursion policy, you can configure DNS forwarding.
End-of-Chapter Review Questions
1. C, D, E. You should use the PowerShell cmdlet Backup-DhcpServer because it also backs up the failover relationship data, which you can use to restore to the previous relationship state. You should also use the PowerShell cmdlet Restore-DhcpServer because, if you have used the previous PowerShell cmdlet or you backed up manually through the DHCP manager, you can restore the failover relationship data with that.
You can view the restored failover relationship data through IPv4 Properties on the Failover tab. First the replication state appears as Recover Wait. You must wait so that it can sync up with its partner server before resuming normal operations on the network.
You also should use the PowerShell cmdlet Remove-Item because you need to first remove all files from the C:WindowsSystem32DHCP folder. This removes the corrupted database from the location DHCP1 is trying to read it from. After removing the files, you can start the DHCP service.
You should not use netsh dhcp server import because the failover relationship data is not part of the backup with that command.
You should not use netsh dhcp server export because that command does not include the failover relationship data in the backup, and you cannot use the backed-up files to restore it.
You should not use Stop-Service because it stops the DHCP service. It remains stopped after a database corruption.
2. The correct script is
$DNSDomain="pearson.com"
$DNSServerIP="172.16.1.10"
$DHCPServerIP="172.16.1.10"
$StartRange="172.16.1.150"
$EndRange="172.16.1.200"
$Subnet="255.255.255.0"
$Router="172.16.1.1"
Install-WindowsFeature -Name 'DHCP' -IncludeManagementTools
cmd.exe /c "netsh dhcp add securitygroups"
Restart-service dhcpserver
Add-DhcpServerInDC -DnsName $Env:COMPUTERNAME
Add-DhcpServerV4Scope -Name "DHCP Scope" -Start $StartRange -End
$EndRange -SubnetMask $Subnet
Set-DhcpServerV4OptionValue -DnsDomain $DNSDomain -DnsServer
$DNSServerIP -Router $Router
The correct answer is
a. IncludeAllSubFeature: B
b. IncludeManagementTools: __
c. Install-Package: __
d. Add-WindowsFeature: A
e. Add-DhcpServerinDC: D
f. Cmd.exe: C
g. Netsh.exe: __
h. Add-DhcpServerv4Class: __
i. Add-DhcpServerInDC: __
j. Add-DhcpServerV4Scope: E
k. Add-DhcpServerV4MulticastScope: __
l. Set-DhcpServerV4OptionValue: F
m. Add-DhcpServerv4OptionDefinition: __
3. A. You cannot use the DHCP failover feature for IPv6 scopes. This is possible only for IPv4 scopes. You can deliver IPv6 options; one of them is 00021, the SIP server domain list option. You can deliver IP addresses and options with IPv6 scopes. You also can configure exclusions and reservations for IPv6 scopes.
4. C. You should use the EnableAutoStateTransition setting because the DHCP server DHCP2 is in the PartnerDown state; it is assuming that its failover partner, DHCP1, is not operating. In a hot standby failover configuration, in which DHCP2 is the passive partner, normally this server responds to all client requests that it receives if DHCP goes down. If the Automatic State Transition setting is enabled, the automatic state transition process moves from the CommunicationsInterrupted state to the PartnerDown state when the state switchover interval expires.
With the PowerShell command Set-Dhcpserverv4Failover -AutoStateTransition $true, you can enable the automatic state transition here. If it is disabled, DHCP2 does not go into the PartnerDown state after the switchover interval expires.
You should not set Maximum Client Lead Time (MCLT) to 0 because this defines the maximum amount of time one server can extend a lease for a DHCP client beyond the time known by the partner server. The MCLT defines the temporary lease period given by a failover partner server and also determines the amount of time a server in a failover relationship waits in the PartnerDown state before assuming control over the entire IP address range.
You cannot set the Maximum Client Lead Time to 0; the default setting is 1 hour.
You should not use Enable State Switchover Interval because this is the interval after which a DHCP server automatically transitions its failover partner to a Partner Down state after loss of communication. This works only if automatic state transition is enabled. In this scenario, automatic state transition is disabled, so this interval does not work.
You should not use Change Reserve Percentage setting because, in a failover relationship configured in hot standby mode, administrators can specify a percentage of the address range of the scope as reserved for the hot standby server. The default value is 5 percent.
5. B, D. You should add Add-DhcpServerv4Scope to the maintenance role capability file as an additional visible cmdlet value. The maintenance role capability file defines all PowerShell cmdlets that are allowed to use the given Just Enough Administration (JEA) endpoint. You then must reregister the session configuration. When you add Paul to the DHCP Administrators security group, he has full DHCP administrator permissions. You cannot add a PowerShell cmdlet directly to the session configuration file; instead, the role definition is done in that file; the given PowerShell cmdlets will be applied under the virtual account. Adding Paul’s computer to the TrustedHosts list gives the client permission for remote PowerShell sessions, but this still is allowed because Paul had no problem connecting from his client to the DHCP server DHCP1.
Chapter 7
Do I Know This Already? Quiz
1. C, D. Since Windows Server 2012 R2, IPAM can use another SQL Server computer as an external location for its IPAM database. This is also possible with Windows Server 2016. When you migrate the IPAM database of IPAM1 to SQL1, you cannot use the SQL database on the other server for IPAM: IPAM1 is still running Windows Server 2012 and this server version does not support an external IPAM SQL database. When you install Microsoft SQL Server on IPAM1, you can use that database locally for IPAM and you can migrate from the WID database to SQL; however, this question asks about an external database solution.
2. C, E. You cannot exchange or replicate IPAM data between IPAM servers; no mechanism supports that. You also cannot replicate IPAM data between forests. A new feature of Windows Server 2016 IPAM enables you to manage DNS and DHCP servers distributed through multiple forests using Windows Server 2016 IPAM. To do so, you must have a two-way trust between the forests.
3. B. You must verify that the DHCP servers are in the security filtering list of the IPAM_DHCP Group Policy and have read permission. This is a prerequisite so that these managed servers can get the Group Policy settings from the IPAM_DHCP Group Policy. You can also manually add the computer account of the DHCP server into the security filtering list to force this. You then can restart the DHCP server or perform a Group Policy update. To display the DHCP server in the IPAM configuration console under Server Inventory with an IPAM access status of Unblocked, you must refresh the server access status to force the display.
Simply performing gpupdate /force again on DHCP2 will not work if DHCP2 has no read permission for the DHCP_IPAM Group Policy.
Adding DHCP2 to the IPAM_DC_NPS Group Policy does not help because this Group Policy is for DCs and NPS servers; they must be added to the security filtering list with read permissions, not the managed DHCP server.
When you refresh the server access status, DHCP2 still has no read permission to the IPAM_DHCP Group Policy.
4. C. During the default Windows Server 2016 IPAM provisioning process, the IPAM_DHCP Group Policy is created. This policy runs the ipamprovisioning.ps1 PowerShell script on the managed servers. This happens through the identity IPAMUG, which is a domain security group that has the IPAM server as a member. The IPAMUG security group automatically becomes a member of the local EventLogReaders security group of the managed servers so that the IPAM server can get access to DHCP events. The local Administrators security group and the Domain Administrators security group are not the correct identities the PowerShell script runs by default.
5. A, D. You can add a custom IPAM field through the PowerShell cmdlet Add-IPAMCustom Field before the CSV file import occurs. A field named Division does not exist by default in the IPAM database. To make the CSV data import possible, you must create that field. You can use the Import-IPAMAddress PowerShell cmdlet to import the IP addresses from the CSV file. You cannot use the Format-Custom PowerShell cmdlet to create or prepare a custom IPAM field. You do not have to use the Add-IPAMCustomValue PowerShell cmdlet because the values for the Division field come from the CSV file.
You have a CSV file with IP addresses, so you do not want to import a subnet or a range; you also do not have to use Import-IpamSubnet or Import-IpamRange. You do not have to ensure that the RIR field exists because here you want to import IP addresses from the file, not an IP address block. When you have public IP address blocks in a CSV file and you want to import them, you must use the RIR field and value.
6. A, D. You cannot view or monitor information about DNS reverse lookup zones in the IPAM management console. Instead, you use the PowerShell cmdlet Get-IPAMDnsZone for that. Alternatively, you can do that through the DNS Manager on the DNS server to verify the signing status of the reverse lookup zone. You cannot get reverse lookup zone information through the Event Catalog or the DNS and DHCP Server area of the IPAM configuration console.
7. C. When you want to use separated computers for the IPAM server and the SQL Server hosting the IPAM database, you must first create the IPAM SQL database. This starts with the SQL command CREATE LOGIN. Then you can use the SQL command CREATE DATABASE to create the new IPAM database. After that, you can use the PowerShell cmdlet Move-IpamDatabase to move the IPAM database.
8. B, D. You have to add the network service named Microsoft Windows Server IP Address Management in SCVMM to configure the integration between IPAM and SCVMM. An IP address range in IPAM is the same as an IP address pool in SCVMM.
End-of-Chapter Review Questions
1. C, D. You should use Get-IpamDhcpSuperScope because that PowerShell cmdlet enables you to identify the IPAM DHCP Superscope. $a = Get-IpamDhcpSuperScope Downtown.
After that, you can use a variable to change the access scope with the following command: Set-IpamAccessScope -IpamDhcpSuperscope $a -AccessScopePath GlobalDE.
You also should use Set-IpamAccessScope because that PowerShell cmdlet enables you to change the access scope for the SuperScope from GlobalCH to GlobalDE. You can do that with the new Windows Server 2016 parameter IpamDhcpSuperscope of Set-IpamAccess Scope: Set-IpamAccessScope -IpamDhcpSuperscope Downtown -AccessScopePath GlobalDE.
You should not use Set-IpamScope because it modifies settings of an existing DHCP scope managed through IPAM, but you cannot modify settings of a superscope or change the access scope with that PowerShell cmdlet.
You should not use Set-IpamRange because that PowerShell cmdlet modifies an existing IP range on IPAM. For example: Get-IpamRange -StartIPAddress 10.12.1.1 -EndIPAddress 10.12.1.254 | Set-IpamRange -NewManagedBy Service VMM -NewServiceInstance “vmm1.pearson.com” -PassThru.
2. D. You should synchronize IPAM2016 and VMM1 because the IPAM server IPAM2016 from the other company is a Windows Server 2016 server. You can use it for IPAM–VMM integration to centralize physical and virtual IP address space management. The IPAM server must be at least a Windows Server 2012 R2 for that.
You must create a VMM user account on the IPAM server and assign the IPAM ASM Administrator role on the global access scope to that account. On the VMM server, you must add the IPAM as a new network service. There you have to select Microsoft Windows Server IP Address Management and define the VMM user account as a Run As account.
After that, you can add logical networks through VMM or through IPAM, and they will be replicated with all settings through each other. You should not deploy an IPAM server on pearson.com because you still have a centralized solution for IP address space management: the SCVMM server. Additionally, you can use IPAMX from the integrated company’s forest in the future, to manage both forests (multiple-forest support is new to Windows Server 2016 IPAM).
You should not add the pearson.com forest to IPAM2016 because it has only two DHCP and DNS servers. All virtual machines’ IP addresses on pearson.com are managed through the SCVMM server.
You should not use a third-party IPAM solution because this involves too much administrative effort and produces too many migration costs. In the pearson.com forest, you have a field-tested environment. In the forest of the other company, you also have an existing IP address space-management solution with the existing Windows Server 2016 IPAM server IPAM2016. Migrating to a third-party solution would not be a fast or cheap solution.
3. B. You should create a scope policy on DHCP1 because you cannot replicate a DHCP Policy created on the server level. The DHCP Policy created on DHCP1 will be applied to all scopes on DHCP1, but it cannot be replicated through the DHCP failover replication process. This was not possible in Windows Server 2012 and is still not possible in Windows Server 2016.
If you create the DHCP Policy on the scope level, the DHCP Policy settings apply only to clients for that scope; this DHCP Policy, however, will be replicated to the DHCP failover partner.
You should not create a scope policy on DHCP2 because here the original scope is on DHCP1. You must create the scope-level DHCP Policy on DHCP1, not on DHCP2.
You should not select Import Policy on DHCP1 because you still have to create the DHCP Policy in DHCP1; it does not need be imported again. If you have created it in the IPAM console, the DHCP Policy is present and automatically applied to all scopes on DHCP1.
You should not select Import Policy on DHCP2 because if you import the DHCP Policy on DHCP2, it is still a policy on the server level. It will be applied to the scope on DHCP2, but it still cannot be automatically replicated through DHCP failover replication because it is not a scope-level DHCP Policy.
4. B. You should use $ip = Get-IpamAddress -IPAddress 10.12.1.1, Set-IpamAccessScope -IpamIP Number -InputObject $ip -AccessScopePath GlobalUSA -PassThru because the Set-IpamAccessScope PowerShell cmdlet has no IpamIPNumber parameter. You can set an access scope for an IP scope and assign the role through the access policy to that IP scope, but any newly configured IP address falls automatically under the Global access scope.
You cannot apply an access scope to a single IP address. You should not use $zone = Get-IpamDnsZone -ZoneType Forward -ZoneName pearson.com, Set-IpamAccessScope -IpamDnsZone -InputObject $zone -AccessScope Path GlobalUSA -PassThru because the Set-IpamAccessScope PowerShell cmdlet has the parameter IpamDnsZone and you can apply an access scope to a DNS zone. This works, so it is the wrong answer.
You should not use $scope = Get-IpamDhcpScope -AddressFamily “Ipv4”-ScopeID 10.0.0.0, Set-IpamAccess Scope -IpamDhcpScope -InputObject $scope -AccessScopePath GlobalUSA -PassThru because the Set-IpamAccessScope PowerShell cmdlet has the parameter IpamDhcpScope and you can apply an access scope to an IPAM DHCP scope. This works, so it is the wrong answer.
You should not use $record = Get-IpamDnsResource Record -ZoneName pearson.com -RecordName “PearsonServer” -RecordType A; Set-IpamAccessScope -IpamDns ResourceRecord -InputObject $record -AccessScopePath GlobalEurope -PassThru because the Set-IpamAccessScope PowerShell cmdlet has the parameter IpamDnsResourceRecord and you can apply an access scope to a DNS record. This works, so it is the wrong answer.
Chapter 8
Do I Know This Already? Quiz
1. C. You cannot configure the DHCP name protection feature simultaneously through a multiselection in the IPAM configuration console. From the DNS Dynamic Updates settings, only the setting Enable DNS Dynamic Updates is configurable through the Edit DHCP Server Properties window in the IPAM configuration console. This has nothing to do with the fact that both DHCP servers are in different forests. You can use the Set-DhcpServerv4Setting PowerShell cmdlet to configure the DHCP name protection feature on DHCP servers, but then it is not configured through IPAM. When you want to configure this setting through IPAM, you have to configure it twice. You cannot use the PowerShell cmdlet Get-IpamDhcp Server to change settings. With that cmdlet, you can display the status of a DHCP name protection setting for one or multiple DHCP servers.
2. B. DNS Dynamic Update Credentials are never part of a backup (synchronous or asynchronous), so after the DHCP database restore, new credentials must be configured for DHCP1. You do not have to configure new credentials for all DHCP servers because only DHCP1 was restored. When you restore ipam.mdf and ipam_log.ldf, you restore the IPAM WID database files. With that, you restore all IPAM configuration settings, but DHCP1 still has lost its configured credentials because these were not part of the DHCP database backup.
When you use the Set-IpamDiscoveryDomain PowerShell cmdlet, you can prevent the server discovery for domain controllers or other managed servers such as DNS or DHCP servers. You cannot use this cmdlet to discover restored credentials.
With the DiscoverDns, DiscoverDhcp, and DiscoverDc parameters of this cmdlet, you can allow or prevent server discovery. No parameter for NPS servers exists.
3. D. You cannot select both scopes and also disable dynamic updates for DNS PTR records for both scopes in the IPAM configuration console in one step. If multiple scopes are selected, you can only enable or disable DNS dynamic updates; you cannot configure Enable Name Protection, Dynamically Update DNS Records, Discard DNS A and PTR Records When Lease Is Deleted, Dynamically Update DNS Records for DHCP Clients That Do Not Request Updates, and Disable Dynamic Updates for DNS PTR Records.
A PowerShell cmdlet named Set-IpamDhcp Scope does not exist, so you cannot use it.
You cannot use the Set Access Scope setting to configure DHCP scopes. Access scopes are used to configure administrative permissions based on RBAC.
The only possibility with these answer choices is to use the Duplicate DHCP Scope feature in the IPAM configuration console.
4. C. When you use the DHCP failover feature to replicate the DHCP Policy to DHCP4, Scope2 is replicated to DHCP4 and you have only the DHCP Policy on Scope2 configured, not on both scopes. When you choose DHCP1 to create the DHCP Policy, this is the wrong DHCP server because Scope2 does not exist on DHCP1. You can use the Import DHCP Policy feature to apply the DHCP Policy created on DHCP2 on Scope2 to Scope4 on DHCP4. You cannot use Configure DHCP Policy and select both scopes because you cannot enable the Register DHCP Clients Using a Different DNS Suffix setting in this way. You can enable only the DNS dynamic update setting.
5. B. Debug Logging settings cannot be configured centrally directly through the Windows Server 2016 IPAM configuration console; you must launch the DNS Manager tool. When you select multiple DNS servers, you cannot select Launch MMC; this is not possible. You can select a single DNS server in IPAM and then select Launch MMC, but then you have to repeat this for the other nine DNS servers to configure Debug Logging through IPAM. When you go to the Server Inventory list and you select Edit Server, you cannot configure Debug Logging of that DNS server. When you go to the Server Groups list, you also can select only a single DNS server to get the Launch MMC setting for each server.
6. B. When you remove the subdomain, select the DNS server in the DNS and DHCP Servers list, and use the Create DNS Zone setting to create usa.pearson.com, the subdomain appears under Forward Lookup.
When you remove the subdomain and use New Delegation in the DNS Manager, this creates a DNS delegation, not a subdomain or zone.
When you use Reset Zone Status and Retrieve Server Data to update the IPAM information in the IPAM configuration console, this is a good idea for getting actual information, but the subdomain still does not display.
You can use the New Zone Wizard in the DNS Manager to create the subdomain and subzone usa.pearson.com, and it displays in IPAM with a white bullet and a Zone Status of No Data. When the first resource record is added to the zone (excluding SOA and NS), it automatically changes to a green bullet or you can force the display with Reset Zone Status and Retrieve Server Data.
7. B. The PowerShell command Invoke-GpoProvisioning must create the GPOs on a domain controller in the pucert.com forest. This can be done only with permissions in that forest. You have to grant the administrative account of pearson.com, which is performing the PowerShell command, minimum permission to create GPOs at pucert.com so that the GPOs can be created.
You do not have to grant the computer accounts of the managed servers the GPOApply permission in this step. For example, it is correct that a DHCP server in pucert.com must have the GPOApply permission on IPAM_DHCP GPO and that a DNS server in pucert.com must have the GPOApply permission on IPAM_DNS GPO, but this is not the configuration step to solve the error message for the InvokeGpoProvisioning command. You do not have to add IPAM1 to the IPAMUG security group because this is done automatically. Managed servers do not have to be a member of the IPAMUG security group.
8. A, C, D, G. You must create a new user role and then, in Operations and DNS Resource Record Management Operations, select AAAA Record Operations. Then you need to create a new access scope. After that, you create a new access policy and add the IPv6Admins security group and the new user role with the AAAA resource record operation permission. The last step is to select both DNS zones and then select Set Access Scope to apply the new access scope. You cannot edit the default access roles. The only default access scope is the Global scope, which you cannot edit. No default access policy exists.
End-of-Chapter Review Questions
1. B. You can change the DNS Dynamic Update Credentials on DHCP2 because you are member of the DHCP Administrators security group on all DHCP servers. This can be done on DHCP2 and all other DHCP servers in the list except on DHCP1 because this is an evenly recovered DHCP server and the DNS Dynamic Update credentials are not part of a DHCP backup.
When you recover the DHCP database, you first have to configure new credentials before you can change them. You can enable DHCP audit logging in the IPAM DHCP server properties, but you cannot configure the audit log path there. For that, you can use the Set-DhcpServer AuditLog PowerShell cmdlet.
The Automatically Update Statistics setting cannot be configured through the IPAM DHCP server properties.
The Backup Path also cannot be configured through the IPAM DHCP server properties.
2. B, F. When you select multiple IPv4 DHCP scopes in the IPAM management console, you can change only the description and the lease duration settings in one step for multiple scopes.
3. A. The State Switchover Interval setting is part of a DHCP failover relationship configuration. If automatic state transition is enabled, a DHCP server in a CommunicationInterrupted state automatically transitions to the Partner-Down state after a defined period of time. This period of time is defined by the State switchover interval; you can configure it under the Edit DHCP Failover Relationship setting.
4. C. In the IPAM configuration console, you can configure the following DNS server tasks: Launch MMC, Create DNS Zone, Create DNS Conditional Forwarder, Set Access Scope, and Retrieve Server Data. For every DNS server, you have to select Launch MMC to configure the automatic scavenging of stale records setting.
5. A, C. When the subzone is displayed with an empty white bullet under Forward Lookup, either it has no data or the actual zone information was not retrieved from the DNS server. To refresh the information displayed, you must select Reset Zone Status and Retrieve Server Data.
Chapter 9
Do I Know This Already? Quiz
1. D, E, H. With the IPAM scheduled task DnsServerConfiguration (new in Windows Server 2016), you can collect configuration information from DNS servers for display in the IP address space and server management functions. With the IPAM scheduled task ServerAvailability, you can collect service status information from DHCP and also DNS servers. With the IPAM scheduled task ServiceMonitoring, you can collect DNS zone status events from DNS servers.
2. Event: E; Search criteria: B, D, F. Security event 672 is a correct answer because this security event (672–An authentication service [AS] ticket was successfully issued and validated) comes from an NPS server. Because you have no NPS server in your environment, you cannot get these events. If you do not want to include events such as these, you can choose and exclude user or machine logon and correlated events. IPScope, MACAddress, and ClassID are correct answers because they are not possible IPAM IP address tracking events.
3. B, F. You should choose Event Catalog and IP Address Tracking because there you can configure IP address tracking by IP address, client ID, hostname, and username.
End-of-Chapter Review Questions
1. D. The DnsServerConfiguration task is new in Windows Server 2016. With this task, the IPAM server collects configuration information from DNS servers for display in the IP address space and for server-management functions.
2. C, D. IPAM enables you to create custom logical groups to improve the audit experience for DNS or DHCP servers. To apply custom fields to one or multiple DHCP or DNS servers, go to Server Inventory, select the servers, and use the Edit Server task to apply custom fields. For example, if you want to use PowerShell, you first must add a custom field named Building with Add-IpamCustomField and then add values with Add-IpamCustomValue.
3. C. The default IPAM underutilization threshold setting is 20 percent, and the IPAM overutilization setting is 80 percent. You can leave the overutilization threshold default settings.
Chapter 10
Do I Know This Already? Quiz
1. A, D. When you have to set up a router-to-router S2S (site-to-site) VPN connection between two Windows Server 2016 RAS servers in different sites and you want to use an IPsec-encrypted tunnel and persistent connection, you must create a demand-dial interface on both Windows Server 2016 Remote Access servers. During the interface configuration, you must define the dial-out credentials. You do not have to create a VPN connection profile because, in this scenario, no client has to connect into a VPN tunnel. You also cannot use the IPHTTPS interface for this because IPHTTPS is used for Direct-Access VPN connections, not for S2S router-to-router VPN connections.
2. B. You can get detailed statistics information about your S2S VPN interface through the PowerShell cmdlet Get-VPNS2SinterfaceStatistics. You cannot use the Get-VpnS2S Interface, Get-VpnDemandDialInterface, or Get-VpnS2SdemandDialInterface cmdlets.
3. A, B. You need a demand-dial interface for such an S2S VPN connection. You can choose the setting Persistent on the Options tab of the Properties page of the demand-dial interface; you also can configure it by clearing the Idle Timeout and Session Timeout settings on the NPS server the Remote Access server is using in the network policy and on the Constraint tab. On the calling router Remote Access server properties page, you cannot configure a persistent demand-dial VPN S2S connection. On the L2TP port settings on the calling router, you cannot configure this.
4. D. You can set custom IPsec policies for incoming VPN and S2S connections with the PowerShell cmdlet Set-VpnServerIPsecConfiguration. The following example command sets a custom IPsec policy like the one asked:
Set-VpnServerIPsecConfiguration -CustomPolicy-EncryptionMethod “AES128”-DhGroup “Group2” -PfsGroup “PFS2” -CipherTransformConstants “AES128”-IntegrityCheckMethod “SHA256” -AuthenticationTransformConstants “SHA256128” -PassThru
The PowerShell cmdlet Set-VpnAuthProtocol configures the authentication method for incoming S2S VPN interfaces on RRAS servers. This is not the correct answer because you have to configure a custom IPsec policy, not base authentication protocol settings. The following example uses this cmdlet to change the authentication method for incoming connections to Certificate:
Set-VpnAuthProtocol -UserAuthProtocolAccepted Certificate
The PowerShell cmdlet Set-Vpn ConnectionIPsec Configuration sets the IPsec parameters of a VPN connection. The following example first uses the Add-VpnConnection PowerShell cmdlet to add a VPN connection, and the second command uses Set-VpnConnectionIPsec Configuration to specify values for the CipherTransformsConstants, EncryptionMethod, IntegrityCheckMethod, and DHGroup parameters:
Add-VpnConnection -Name “Contoso” -ServerAddress 176.16.1.2 -TunnelType Ikev2, Set-VpnConnectionIPsec Configuration -ConnectionName “Pearson”-AuthenticationTransform Constants None -CipherTransformConstants AES256-EncryptionMethod AES256 -IntegrityCheck Method
The PowerShell cmdlet Set-NetIPsecDospSetting modifies existing IPsec DoS protection settings. The following example modifies the internal interface of an IPsec DoS protection setting by using the rule name:
Set-NetIPsecDospSetting -Name PearsonNet-CorpNet -PublicInterface Aliases PearsonNet2
5. D. You can use the PowerShell cmdlet Get-VpnAuthProtocol to verify which user authentication protocols your VPN server accepts. The following example receives authentication parameters configured for your Windows Server 2016 VPN server:
Get-VpnAuthProtocol | FL UserAuthProtocolAccepted
You can configure this with Set-VpnAuthProtocol -UserAuth ProtocolAccepted EAP.
The PowerShell cmdlet Get-VpnConnection retrieves specified VPN connection profile information.
The PowerShell cmdlet Get-VpnServerConfiguration delivers VPN server properties.
The PowerShell cmdlet Get-VpnS2Sinterface delivers configuration details about S2S interfaces.
6. D, E. Since Windows 7 and Windows Server 2008 R2 server, you can use the VPN Reconnect feature. You also need IKEv2, certificates, and PEAP. MS-CHAPv2 and PSK are not prerequisites for the VPN Reconnect feature. Windows Server 2016 VPN servers still support the VPN Reconnect feature.
7. Explanation: You can use the following possibilities to distribute VPN connection profiles: CMAK, Microsoft Intune, System Center Configuration Manager, Group Policies, and scripts.
8. D, E. You can use a Web Application Proxy together with ADFS (Active Directory Federation Services) to allow these users to access the web applications through HTTPS. The Web Application Proxy server can forward the authentication requests to the ADFS server; the ADFS server then delivers an access ticket to the client so that the user can access the web applications. When you use VPN connections (L2TP/IPsec or SSTP), you have a tunnel to the local network of the company, not just to the web applications. SSTP also works with HTTPS, but in this question, the users want to access only their web applications and no other internal resources, so Web Application Proxy is the best solution. An S2S VPN connection is used to connect sites through a VPN tunnel, not single clients with the local network.
9. C, G. You do not need a Certificate Authority and an IPv6 internal network for that. Only the DirectAccess IPsec-encrypted tunnel has to be an IPv6 network, at minimum. When you set up a single Edge Windows Server 2016 DirectAccess server, you can use the Getting Started Wizard; self-signed certificates then are created and installed automatically on the DirectAccess server for IP-HTTPS and the NLS server.
You do not need a Certificate Authority because the certificates do not have to come from this; however, for security reasons, it is more secure to implement a CA for the KDC Proxy and NLS certificate. The Network Location Server (NLS) is used so that DirectAccess clients can approve whether they are internal or external.
The KDC Proxy is used to authenticate DirectAccess clients through Kerberos.
The Network Connectivity Assistant (NCA) is a service on the DirectAccess client that is used to test the connectivity through the IPv6 IPsec tunnel and to allow monitoring.
Group Policies are created to configure DirectAccess server and client settings.
You cannot use DirectAccess without using Active Directory.
10. C. The Getting Started Wizard on the DirectAccess server was successfully completed. This means that the necessary Group Policy objects are successfully created and also the DirectAccess server settings Group Policy. The problem is that the public firewall on the public accessible interface of the DirectAccess server is not enabled and not configured through the Direct-Access server settings Group Policy. The IPsec connection security rule on this interface must be configured through this Group Policy.
When you run gpupdate /force, the GPO settings are applied, but because the public firewall profile is disabled, the firewall settings cannot be applied through the Group Policy.
When you restart the DirectAccess server, all firewall profiles are enabled and the public firewall settings also are applied through Group Policy.
You do not have to configure or create firewall rules because this all can be done through the DirectAccess server settings Group Policy.
11. A, D, F, H. DirectAccess clients can be any domain-joined computer that is running an Enterprise edition of the Windows 10, Windows 8.1, Windows 8.0, or Windows 7 operating systems. They also can connect to the Direct-Access server by using IPv6 and IPsec. The Getting Started Wizard on the DirectAccess server creates a set of GPOs and settings for DirectAccess clients. DirectAccess clients get all settings from GPOs. DirectAccess client computers can connect to DirectAccess servers located in different domains.
12. A. You should use the Set-DAEntryPointDC PowerShell cmdlet to point to another domain controller. When you have deployed a multisite DirectAccess configuration, you can verify the name of the domain controller closest to the entry point with the PowerShell cmdlet Get-DAEntrypointDC.
If the domain controller is not running, use the Set-DAEntryPointDC PowerShell cmdlet to point to another domain controller. After that, use gpresult to ensure that DirectAccess is getting the DirectAccess Server Group Policy Objects settings.
Using the Operation Status tab in the Remote Access Management Console is a good idea to identify problems with DirectAccess components, but in this case, you get no information displayed in the console because the DirectAccess server cannot read information from Active Directory.
When you use the Get-DnsClientNrptRule PowerShell cmdlet to verify NRPT settings, you do that on the DirectAccess client. This has nothing to do with the problem that the DirectAccess server cannot display the DirectAccess configuration and gets no information from Active Directory.
You should not manually edit DirectAccess Group Policy settings directly in the GPO; this always must be done through the Remote Access Management console.
End-of-Chapter Review Questions
1. C. A persistent S2S VPN connection has a constant connection. If the connection closes, it is reestablished immediately. You can configure the connection as persistent on the Properties page of the demand-dial interface on the Options tab. Alternatively, you can configure this at the Network Policy of the answering router by clearing the Idle Timeout and Session Timeout settings.
2. C, G. When you want to open only UDP port 500 for the VPN connection, you must choose IKEv2 as the tunnel protocol. Because IKEv2 will use the IPsec protocol, you can configure the idle disconnecting setting with the Set-VPNServerConfiguration PowerShell cmdlet.
3. C. When you want to add a VPN connection that uses a custom EAP authentication method, you can use the New-EapConfiguration PowerShell cmdlet to create an XML file with the specified EAP configuration. After that, you can use Add-VpnConnection to create a new VPN connection profile using this EAP configuration.
4. A, B. One Azure VPN gateway supports up to 128 P2S VPN connections. Only ExpressRoute offers redundant tunneling; Azure P2S and Azure S2S do not offer that. Here you have mobile clients that travel and are not always inside your on-premises site. When using an S2S tunnel solution, clients have a VPN tunnel connection to Azure only if they are at the on-premises site. When you upgrade to a high-performance Azure VPN gateway, you can increase the S2S tunnels to 30, but the P2S limit is still 128.
Chapter 11
Do I Know This Already? Quiz
1. A. You must register NPS1 in the domain or forest where the user accounts reside. In this case, this is the pearsonucertify.com domain. You also need to create a trust relationship between the two forests so that you can add the computer account of NPS1 from the pearson.com domain to the security group of pearsonucertify.com.
You do not have to add NPS1 to the security group in pearson.com because the user accounts are not in this domain.
You cannot replicate NPS settings between NPS servers; no such replication function exists. You can use the NPS configuration import/export feature to manually transfer NPS settings from one NPS server to another; you can write a PowerShell script to do that automatically and schedule it to run from time to time.
NPS1 needs read permissions on the user accounts of pearsonucertify.com.
You cannot register NPS servers in Azure AD.
2. C. You must create a new connection request policy to forward connection requests to a RADIUS server. This policy is the Proxy policy and has to stay at the top of the ordered list. If the request matches this policy, requests are forwarded to a RADIUS server. If the request does not match this proxy policy, the next policy applies, which is the default connection request policy (local authentication). When you simply use the default connection request policy, local authentication applies, so the NPS server can work only as a RADIUS server.
3. A, C. A RADIUS server cannot be added for authentication when VPN is not installed. In this case, the VPN feature is installed on VPN1. A RADIUS server cannot be added for authentication when the authentication type is Windows or when local NPS is installed. In this case, a local NPS is not installed on VPN1.
A RADIUS server cannot be added for the purpose of accounting when external RADIUS Accounting is not enabled. In this case, external RADIUS Accounting is enabled on VPN1. This means that you can use the Add-RemoteAccessRadius PowerShell cmdlet to add the RADIUS server to VPN1. You also can tell the RADIUS server R1 that VPN1 is the RADIUS client with the New-NpsRadiusClient PowerShell cmdlet.
4. A, D, E, G. You can configure only the following kinds of settings through NPS templates on a Windows Server 2016 NPS server: shared secrets, RADIUS clients, IP filters, and remote RADIUS servers.
5. A, C, D. You have to separate NPS log files from the system partition; otherwise, too many log files could bring down the operating system.
You can use a RADIUS server group to specify load-balancing settings either to determine the order in which the proxy uses the servers or to distribute the flow of RADIUS messages across all servers in the group to keep from overloading one or more servers with too many connection requests. Remote RADIUS server groups are unrelated to and separate from Windows groups.
You can use SQL logging instead of NPS log files, and you can use another server as the SQL Server. You can use Database Availability Groups (DAG) on SQL Server to make the database highly available there. In this case, the system disk cannot be filled with NPS log file information to bring down the NPS server.
6. A, C, E, G. To allow VPN clients to connect through the PEAP authentication method, you need the network policy condition NAS Port Type: Virtual (VPN). You also have to configure the Authentication Method Microsoft Protected EAP (PEAP). For PEAP to work, you need to prepare a PEAP certificate template on the CA and request a PEAP certificate for the NPS server so that you can apply that certificate in the network policy on the PEAP authentication method. You must define the type of network access server as Remote Access Server (VPN–Dial-up).
7. A, D. No PowerShell cmdlet exists for creating, modifying, or removing Windows Server 2016 NPS connection request policies. You cannot create connection request policies through NPS templates.
8. A, B, F. You must use the Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, and Tunnel-Type attributes as RADIUS attributes.
9. C, D. You can use the Export-NpsConfiguration PowerShell cmdlet to export NPS server settings, Network Policies, and connection request policies into an XML file. You can use the Import-NpsConfiguration PowerShell cmdlet to import them on the other server. SQL Server logging settings cannot be exported or imported through those commands.
End-of-Chapter Review Questions
1. A, D, E, G. You can use the Windows Server 2016 NPS RADIUS servers using a domain or local SAM user accounts database as the user account database for clients; you also can use them as Remote Access servers for multiple dial-up servers, VPN servers, or demand-dial routers, and you can centralize both the configuration of Network Policies and connection logging and accounting.
You can outsource dial-up, VPN, or wireless access to a service provider. The access servers can use the Windows Server 2016 RADIUS servers to authenticate and authorize connections that are made by members of your organization.
You also can centralize authentication, authorization, and accounting for a heterogeneous set of access servers.
You cannot remotely manage mobile devices through Enterprise Mobility with Windows Server 2016 NPS.
You cannot use the NPS servers as on-premises MFA authentication servers.
You also cannot use the Azure MFA authentication server as a RADIUS client because the Azure MFA authentication server can act as a RADIUS server, not as a RADIUS client. An Azure Multi-Factor Authentication Server also can be configured as a RADIUS proxy between RD gateway and NPS servers.
2. A, C, D, G. You have to create three connection request policies on the RADIUS proxy servers because when you want the NPS proxy to forward messages to multiple groups (in this case, you have three groups of RADIUS servers, one for every domain), you have to configure one connection request policy per group.
You also must create attribute manipulation rules because you have more than one location to which you want to forward connection requests. However, you must create a connection request policy for each location and then configure the policy with the remote RADIUS server group to which you want to forward messages, as well as with the attribute manipulation rules that tell NPS which messages to forward. These rules are defined through conditions—in this case, the User-Name condition. This is the username that the RADIUS client provides and is included by the NAS in the RADIUS Access-Request message. The value of this attribute is a character string that typically contains a realm name and a user account name.
On the RADIUS proxy servers, you have to add remote RADIUS server groups to tell RADIUS servers the proxy to which they have to forward the requests. The proxy does not need to be registered in Active Directory because it does not need access to the dial-in properties of user accounts.
You can replicate the RADIUS proxy configuration between both servers by using a script that copies the settings. Windows Server 2016 has no RADIUS proxy server group.
3. B, E. When you want to tell the RADIUS server which VPN servers are working as RADIUS clients, you have to use the New-NPSRadiusClient Power-Shell cmdlet on the RADIUS server to add the VPN servers as RADIUS clients. When you want to configure a Windows Server 2016 DirectAccess server with OTP and you want to use it as a RADIUS client, then you have to configure two certificate templates, one as an OTP certificate template and the second to enroll the certificate used by the DirectAccess server to sign OTP certificate enrollment requests.
4. A, E, F, G. You can configure the Shared Secrets (with autogenerating feature), Remote RADIUS Servers, RADIUS Clients, and IP Filters settings in Windows Server 2016 NPS templates. Network Access Protection (NAP) is deprecated on Windows Server 2016 NPS.
5. B. Windows Server 2016 NPS formats accounting data as XML that it sends to the report_event stored procedure in the SQL Server database that you designate in NPS. For SQL Server logging to function properly, you must have a stored procedure named report_event in the SQL Server database that can receive and parse the XML documents from NPS. For that reason, you must name the SQL stored procedure report_event.
Chapter 12
Do I Know This Already? Quiz
1. C. With the PowerShell cmdlet Set-DnsClientServerAddress, you can configure which DNS server(s) a client’s network interface must use. With the Set-NetIPAddress PowerShell cmdlet, you can modify configurations of an IP address, such as the assigned IP address and prefix length (subnet mask), but not DNS servers. With the New-NetIPAddress PowerShell cmdlet, you can add a new IP address to a network interface with the DefaultGateway parameter, but no DNS server parameter is available.
2. B. Since Windows Server 2016, you can configure the Packet Direct feature on network adapters. You can enable network adapters for using Packet Direct with the PowerShell cmdlet Enable-NetAdapterPacketDirect.
With the PowerShell cmdlet Enable-NetAdapterRdma, you can enable RDMA on the network adapters. This also improves throughput and reduces network latency, but Packet Direct is usable only with network adapters that have a minimum of 100 Gbps capability.
You can enable SR-IOV on a network adapter with the Enable-NetAdapterSriov PowerShell cmdlet, but SR-IOV enables network traffic to bypass the software switch layer of the Hyper-V virtualization stack. As a result, the I/O overhead in the software emulation layer is diminished and can achieve network performance that is nearly the same as in nonvirtualized environments.
You can enable SRIOV with the PowerShell cmdlet Enable-NetAdapterVmq, but VMQ is a scaling networking technology for the Hyper-V switch.
3. A. When you use the Set-NetIPAddress PowerShell cmdlet to reconfigure the IP address configuration of VM1 so that VM1 is in the same subnet as VM2, both can reach each other. VM1 and VM2 are distributed through two subnets, and when no router is configured to forward IP packets between them, they cannot reach each other. When you change the Hyper-V switch Switch1 to a public switch, this changes nothing for VM1 and VM2; they are still in different subnets. When you change the VM1 IP address to 192.168.93.3/19, you move VM1 to the subnet 192.168.96.0. Configuring the Datacenter Firewall to allow traffic between VM1 and VM2 is not the solution because they are still in different subnets.
4. C. When you add a new route to the routing table of the ISATAP router so that this router can automatically deploy IPv6 addresses to IPv6 hosts through stateless IPv6 configuration, you must use the Publish parameter of the New-NetRoute PowerShell cmdlet.
For example, with the following command, you add a route for interface 22 (which goes to IPv6 subnet where the IPv6 host resides) and the IPv6 network 2001:db8:0:2::/64: New-NetRoute -InterfaceIndex 22 -Destination Prefix 2001:db8:0:2::/64 -Publish Yes. The Advertising and Forward parameters must be used on the network interface, not in the routing table entry.
5. B. You cannot use 6to4 with NAT. Teredo and ISATAP can break through NAT.
6. A. The PowerShell command Enable-RemoteAccessRoutingDomain -Type All enables all tenants for BGP. The PowerShell cmdlet Set-RemoteAccessConfiguration modifies the configuration of a remote access role; you cannot configure or enable BGP with that.
With the PowerShell cmdlet Enable-NetworkSwitchFeature, you also cannot enable BGP.
With the PowerShell cmdlet Enable-BgpRouteFlapDampening, you enable route flap dampening, not BGP. When a BGP route is being advertised and withdrawn, making the routing table unstable, you can configure the BGP router to assign a dampening weight to the route, monitor it for flaps, and, accordingly, suppress or unsuppress it as required. This helps maintain a stable routing table and involves less processing by the BGP router.
7. B. When you connect from a client through an Azure P2S VPN connection to an Azure VNet, you can view the gateway address with the Get-NetRoute PowerShell cmdlet on the client. The tunnel endpoint of the P2S-tunnel is displayed under NextHop.
With the PowerShell cmdlet Get-NetIPAddress, you cannot see routing entries; instead, you can verify local IP address settings.
With the PowerShell cmdlet Get-NetIPInterface, you cannot see routing entries.
With the PowerShell cmdlet Get-BgpCustomRoutes, you can verify BGP custom routes. This is possible only when BGP is enabled.
End-of-Chapter Review Questions
1. C. You can solve the name resolution problem with the following PowerShell cmdlet: Add-DnsClientNrptRule -Namespace “usa.pearson.com” -DnsSecEnable -NameServers “172.16.0.10”. It seems that the DNS server DNS3 is not defined in the NRPT table on that client or is not added as a DNSSEC-enabled DNS server.
When you use the PowerShell cmdlet Get-DnsClientNRPTPolicy, you can view the NRPT settings, but you cannot solve the problem with that.
With the Resolve-DnsName PowerShell command, you can test the name resolution for an individual hostname, but this is not the solution.
With the Get-DnsClientCache PowerShell cmdlet, you can view the hostname cache of the client. This is a good idea because when the IP address changes, old information sometimes is still located in the hostname cache. However, this is not the solution in this case.
With the Get-NetRoute PowerShell cmdlet, you can view the routing table of that client. You can verify the correct routing settings for the DirectAccess tunnel, but in this case, the client cannot access internal resources in only usa.pearson.com. This means that the client can access resources in the other domains, so the DirectAccess tunnel is established and routing is correct.
2. B, C. You can use Resolve-DnsName to resolve the AAAA record to an IPv6 address of the network resource you want to reach. Example: $r = Resolve-DnsName -name www.pearson.com -type AAAA. After that, you can display the IPv6 address property of the $r variable to find the IPv6 address and the net route with the following PowerShell command: Find-NetRoute -RemoteIPAddress $r.ipv6address.
With the Get-NetTCPSetting PowerShell cmdlet, you can view TCP settings, but you cannot find out what IPv6 address and interface your host is using to a specific network resource.
With the Get-NetRoute PowerShell cmdlet, you can view the routing table and search for the specific routing entry. This works faster using Find-NetRoute, particularly when you have many routing table entries.
3. D. The client is part of the subnet 192.168.192.0. When you use 19 bits for the subnet mask, which means a subnet mask of 255.255.224.0, you can calculate the following possible subnets: 192.168.0.0, 192.168.32.0, 192.168.64.0, 192.168.96.0, 192.168.128.0, 192.168.160.0, 192.168.192.0, and 192.168.224.0.
4. C. To get a 6to4 interface displayed with ipconfig /all, a global IPv6 address must be configured on that client.
5. B. To use such PowerShell cmdlets, you must install the RSAT-RemoteAccess-PowerShell feature. The RSAT-RemoteAccess-Mgmt feature installs the graphical Remote Access console, but you cannot configure a RAS Gateway as a BGP-enabled LAN router. The RemoteAccess and Routing roles must be installed, but to use this PowerShell cmdlet, you also need to install the RSAT-RemoteAccess-PowerShell feature.
Chapter 13
Do I Know This Already? Quiz
1. A, C, E. To use Windows PowerShell to exclude folder targets outside the client’s site, use the Set-DfsnFolder -EnableInsiteReferrals cmdlet and set the value to $false; the DFS namespace server provides in-site referrals first and then provides referrals to other sites.
To enable failback to the original server in the client’s site, use the Set-DfsnFolder -EnableTargetFailback $true PowerShell command.
You also can change the Effective Referrals Ordering setting in the DFS Management tool on the folder properties to enable In-Site Referrals. You have to do that for the Marketing folder on DFS3 and the Accounting folder on DFS4. When you configure the folder target properties and you disable the Enable Referrals for This Folder Target setting, then you have disabled the target completely and no client can access the folder target.
2. The correct configuration order is the following. (First, you must ensure that both DFS servers are in the same domain. DFS Replication between DFS servers in different domains is not possible.)
Step 1. c. Remove DFS2 from pucertify.pearson.com and add DFS2 to pearson.com.
Step 2. b. Install DFS namespaces and the DFS Replication role on DFS1 and DFS2.
Step 3. a. Create a new replication group.
Step 4. d. Add DFS1 and DFS2 as replication group members.
Step 5. f. Select the full mesh replication topology.
Step 6. e. Configure replication scheduling.
Step 7. g. Define DFS1 as a primary member.
Step 8. i. Define the folder to replicate.
Step 9. h. Define the local path on other members.
Step 10. k. Wait for AD replication.
Step 11. j. Push initial replication by restarting the DFSR service on DFS1 and DFS2.
3. A. When you use cross-file RDC on very high-bandwidth network connections, cross-file RDC might add too much local processing time and negatively affect performance. In extremely large datasets (millions of files on a volume with a great deal of similarity), cross-file RDC can also negatively affect CPU and disk utilization. Consider disabling cross-file RDC when you replicate over LANs and very high-performance WANs. With the PowerShell command Set-DfsrConnection -DisableCrossFileRDC $true, you can disable cross-file RDC for a DFSR connection. Set-DfsrConnection -DisableCrossFileRDC $false is the default setting.
4. B. You can implement more fault tolerance by configuring Network Load Balancing (NLB) with round robin for the standalone namespace servers. They do not use Active Directory to store namespace information. Because of that, you must distribute the workload among the servers with NLB.
The best solution for fault tolerance is to migrate the standalone namespace to a domain-based namespace. This is possible because these servers are domain members; when the namespace is saved in Active Directory, it is replicated through AD replication among the domain controllers.
Adding another DFS server to BranchOffice2 is a good idea because, when one or two of the other DFS servers stop, this additional server can still offer the standalone namespace.
However, the namespace is still not saved in Active Directory. Moving the standalone namespace servers to Headquarters is not a good idea because then clients from BranchOffice2 cannot find a near DFS server in their site and they instead have to go to the Headquarters site; this reduces performance for the clients.
5. B, D. With the PowerShell cmdlet Restore-DfsrPreservedFiles, you can restore preserved files and folders. DFSR preserves conflicted, deleted, and preexisting files and folders. For all three types, DFS Replication moves the files to either <replicated folder>DfsrPrivateConflict And Deleted or <replicated folder>DfsrPrivatePreexisting. DFSR records these files in a manifest, either ConflictAndDeletedManifest.xml or PreExisting Manifest.xml, as appropriate. Specify the ConflictAndDeletedManifest.xml manifest to restore conflicted and deleted files and folders. Specify the PreExistingManifest.xml manifest to restore preexisting files and folders. You can use the Get-DfsrPreservedFiles cmdlet to view preserved files and folders. The AllowClobber parameter overwrites existing files that have the same names in the specified location.
6. C. The initial DFS Replication can take a long time and consume a large amount of network bandwidth when replicating a large set of files. Windows Server 2016 provides a feature that clones the database for the initial replication. To create a clone of the database, use the Export-DfsrClone PowerShell cmdlet to export the DFSR database and volume configuration XML file settings for a given local computer volume. On a large dataset, exports might take a long time to complete. You can use the Get-DfsrCloneState PowerShell cmdlet to determine the status of the export operation.
7. A. You need to use Distributed BranchCache mode because the BranchOffice site has no servers. You do not have to install the BranchCache feature on the clients because Windows 7 is part of the operating system as a service, but you have to enable the BranchCache service on the clients. You can do so through GPO, PowerShell, or the netsh utility locally. You must install the BranchCache feature (and also the BranchCache for Network Files feature) on the file server. You do not have to install BranchCache on SVR1 or SVR2 because they are not part of the BranchOffice site.
8. E. With the PowerShell cmdlet Enable-BCHostedServer -RegisterSCP, you must register the BranchCache host in Active Directory. With the PowerShell cmdlet Clear-BCCache, you delete all data in all data cache files and all hash cache files.
The PowerShell cmdlet Disable-BCServerOnBattery configures a client to ignore content discovery requests in distributed cache mode when operating on battery power.
The PowerShell cmdlet Enable-BCLocal enables the BranchCache service in local caching mode. In local caching mode, a client stores data in the BranchCache cache and attempts to read data from the local BranchCache cache, but it does not contact peers or attempt to contact a hosted cache server.
The Export-BCSecretKey PowerShell cmdlet exports a secret key to a file.
The Set-BCMinSMBLatency PowerShell cmdlet sets the minimum latency that must exist between client and server before transparent caching functions are used. Use this cmdlet to specify when client computers in branch offices start caching content from content servers based on the network latency, or delay, that occurs when the clients download content over a wide-area network (WAN) link.
The Set-BCAuthentication PowerShell cmdlet specifies the authentication mode for client computers. This can be set on a hosted cache server to enable clients to prove domain membership before uploading data.
9. A. On an application server, you must install and enable BITS and the BranchCache feature.
10. C, D. With the PowerShell command Get-NetFirewallProfile, you cannot view the firewall rules; instead, you can see the firewall profile settings.
With netsh branchcache show status, you can verify whether the BranchCache service is running, check the BranchCache mode, and see whether the firewall is enabled or disabled; however, you cannot view the firewall rules.
With netsh branchcache show status all, you can verify the networking status and the Peer Discovery Firewall rules state.
With the PowerShell cmdlet Get-BCStatus, you also can verify the Peer Discovery Firewall rules state.
End-of-Chapter Review Questions
1. A. To make it possible on DFS2 to use DFS PowerShell cmdlets, you have to install the File Server role.
2. B. When you want to get information about a specific connection schedule between specific DFS members of a DFS Replication group, you must use the Get-DfsrConnectionSchedule PowerShell cmdlet. With the PowerShell cmdlet Get-DfsrGroupSchedule, you get only the group schedule settings. With the PowerShell cmdlet Get-DfsReplicationGroup, you get the settings of a DFS Replication group, not the connection schedules. With the PowerShell cmdlet Get-DfsrMember, you get the list of members in a replication group.
3. A. DFSR creates a staging folder for each replicated folder. This staging folder contains the marshalled files sent between servers and allows replication without risk of interruption from subsequent handles to the file. By default, files larger than 256 KB stage during replication, unless RDC is enabled and using its default minimum file size; in that case, files larger than 64 KB are staged. When replicating on low-latency, high-bandwidth networks such as LANS and high-end WANs, it might be faster to allow certain files to replicate without first staging. If users do not frequently reopen files after modification or addition to a content set (such as during batch processing that dumps files onto a DFSR server for replication out to hundreds of nodes without any later modification), skipping the RDC and the staging process can lead to significant performance boosts.
You configure this using Set-DfsrMembership and the MinimumFile StagingSize parameter.
With the ConflictandDeletedQuotaInMB parameter, you specify the maximum size, in megabytes, for the ConflictsAndDeleted folder.
With the DisableMembership parameter, you disable the membership for a replication folder in a replication group. If you disable membership, DFS Replication stops replicating content on this computer but does not delete the replicated folder or its private replication data. This does not boost replication performance.
With the RemoveDeletedFiles parameter, you delete files and folders immediately following inbound replication. If this parameter has a value of $False, the DFS Replication member moves deleted files and folders to the Conflict-AndDeleted folder when the deletion replicates inbound.
Chapter 14
Do I Know This Already? Quiz
1. C, D. You should use up to 32 NICs in a team because standalone NIC Teaming supports up to 32 NICs in a team. SET supports only eight NICs in a team. You should use “Provides teaming in a VM” because only standalone NIC Teaming can be used to provide NIC Teaming in a VM. NIC Teaming in a VM applies only to vmNICs connected to external switches; vmNICs connected to internal or private switches show as disconnected when they are in a team.
NIC Teaming in Windows Server 2016 also can be deployed in a VM. SET does not support teaming in a VM. You should not use “Support for Hyper-V Network Virtualization SDN version (HNVv2)” because SET fully supports all the capabilities of HNVv2, including both NV-GRE and VXLAN operation.
You should not use “Requires identical NICs in a team” because SET requires all NICs in a team to be identical (same manufacturer, model, firmware, and driver).
2. B. You should use the PowerShell command Set-NetAdapterRss -Name * -Enabled $true because it enables Receive Side Scaling (RSS) on the VMs.
You should not use Enable-NetAdapterIPSecOffload because that PowerShell cmdlet enables IPSec task offloading, to reduce the workload from the main computer’s CPU to a dedicated processor on the network adapter. This has to do with only IPSec network traffic; you cannot distribute the network receiving processing across virtual processors with that.
You cannot use Set-VMNetworkAdapter because that PowerShell cmdlet configures many virtual network adapter settings, such as DHCPGuard, RouterGuard, IPSec Task Offloading, and Port Mirroring, but you cannot use it to enable RSS.
You cannot use Set-ReceiveConnector because this PowerShell cmdlet is a command from Exchange Server and is usable only with on-premises Exchange servers, not on Exchange Online; you cannot configure the distribution of network receiving processing across virtual processors with it.
3. Preconfiguration tasks: A, B; PowerShell commands: F, H, I. You should use Install-WindowsFeature “data-center-bridging” because if you want to manage DCB locally on a Windows Server 2016 server, you must install the feature for it. If you want to manage DCB only from a switch and you propagate the settings to an end device such as a network card on the server, you do not have to install the DCB feature on the server.
You should use Set-NetQoSdcbxSetting -Willing 0 because you cannot configure DCB settings such as traffic classes, PFC, and application priority locally at the server if the Willing bit is not set to false on a network card. First, you must set the Willing bit to false with this command. After that, you can enable DCB on the network adapter, or you can configure your DCB settings locally. If the DC Willing bit is true, the network card can accept configurations from a remote device such as another switch through DCB.
You should use Get-NetAdapterQos because you can use this PowerShell cmdlet even if you have not installed the DCB feature on the server to display DCB settings on network adapters.
You should use Disable-NetAdapterQos because this PowerShell cmdlet can be used without installing the DCB feature on the server to display DCB settings on network adapters.
You should use Enable-NetAdapterQos because this PowerShell cmdlet can be used without installing the DCB feature on the server to display DCB settings on network adapters.
You should not use import-module netqos, import-module dcbqos, or import-module netadapter because you do not have to import the modules. Since PowerShell 3.0, if you use a PowerShell cmdlet from a specific module, the module is imported automatically.
You should not use Set-NetQosPolicy because you must install DCB to configure existing QoS policies.
You should not use Get-NetQosFlow Control because you must install DCB to view QoS flow control settings.
You should not use Set-NetQosTrafficClass because you must install DCB to view QoS traffic class settings.
4. C. You should use Enable-NetAdapterRDMA because NIC6 and NIC7 are not enabled for RDMA. If you want more throughput, lower latency, and less CPU impact for these network cards, you can use RDMA. If you want to use RDMA and SET for a hyperconverged solution using Storage Spaces Direct, you must identify the network adapters with the Get-NetAdapter PowerShell cmdlet. Then you need to create the virtual switch connected to both of the physical network adapters and enable SET with New-VMSwitch -Name SETSwitch -NetAdapterName “<adapter1>”, “<adapter2>” -EnableEmbeddedTeaming $true. After that, you add the host vNICs to the virtual switch with the Add-VMNetwork Adapter PowerShell cmdlet and you configure the host vNIC to use a VLAN with the Set-VMNetworkAdapter Vlan PowerShell cmdlet. Then you can enable RDMA on the host vNIC adapters with the Enable-NetAdapterRDMA PowerShell cmdlet.
You should not use Set-NetAdapter because you cannot enable RDMA or SET with this PowerShell cmdlet.
You should not use Enable NetAdapterVmq because this PowerShell cmdlet enables Virtual Machine Queue on the network adapter. VMQ uses hardware packet filtering to deliver packet data from an external virtual machine network directly to virtual machines, which reduces the overhead of routing packets and copying them from the management operating system to the virtual machine. With VMQ, you cannot access host memory directly without the intervention of the CPU. For that, you have the RDMA capability.
You should not use New-VMSwitch because, with the New-VMSwitch PowerShell cmdlet, you can create a SET switch.
With the parameter EnableEmbeddedTeaming $true, you can enable SET for this switch; however, you do not get less CPU impact, which is the requirement in this exam question.
5. B. You should use IPv6 link local addresses because IPv6 link local IP addresses start with FE80. When private (cluster-only) networks with multiple NICs are detected, the cluster automatically recognizes IPv6 link local (FE80) IP addresses for each NIC on each subnet. This saves administrators time because they no longer have to manually configure IPv6 link local (fE80) IP address resources. Simplified SMB Multichannel and multi-NIC networks are new features of Windows Server 2016. Now you can use multiple NICs on the same failover cluster network subnet and SMB Multichannel is enabled automatically.
You should not use IPv6 site local unicast addresses because this is an obsolete IPv6 alternative. These addresses were similar to the private IP address ranges in IPv4. An organization could choose any IP address in the FEC0::/10 range. Since September 2004, these IPv6 addresses have been obsolete; new implementations must use global unicast IPv6 addresses instead; you cannot use these IPv6 addresses for a simplified SMB Multichannel Windows Server 2016 failover cluster configuration.
You should not use IPv6 unique local unicast addresses because they are used for tunnel configurations to avoid address collisions; you cannot use these IPv6 addresses for a simplified SMB Multichannel Windows Server 2016 failover cluster configuration.
You should not use IPv6 global unicast addresses because they are public accessible IPv6 addresses. The cluster network of a Windows Server 2016 failover cluster is a private network and does not have to be directly available for the public world.
You cannot use these IPv6 addresses for a simplified SMB Multichannel Windows Server 2016 failover cluster configuration in which multiple NICs can be automatically integrated into the same cluster subnet.
6. A, B, D, F, G, I. You should verify that Hyperthreading is enabled because you cannot use vRSS and VMQ without Hyperthreading enabled. With the PowerShell command Get-WmiObject -Class win32_processor | FT -Property NumberOfCores, NumberOfLogical Processors -auto, you can verify that Hyperthreading is enabled.
If you see values at NumberofCores and NumberofLogicalProcessors, Hyperthreading is enabled.
You should use Teaming Mode: Switch Independent because you have to use Switch Independent Teaming Mode as a prerequisite for a VMQ configuration; the difference between dependent teaming mode and independent teaming mode is that the bandwidth of multiple-teamed network adapters shuttles the network to different switches. In independent teaming mode, you can configure your team in active/active or active/standby. If you use active/passive, you use one adapter offline to function as a failover adapter in the event of an adapter failure.
You should use LoadBalancing Algorithm: Dynamic because the virtual adapters are registered separately across physical adapters and received traffic can be balanced; however, sending is balanced using the address hash method. This gives you an impressive balancing configuration. Dynamic mode also uses flowlets, a technique that breaks an existing TCP stream and moves it to another physical adapter. For example, imagine that you have 2x10 GB cards in a team that uses dynamic load balancing. VM1 produces a massive outbound file transfer that gets balanced to the first adapter. VM2 starts a small outbound transfer that is balanced to the second adapter. VM3 begins its own large transfer and is balanced back to the first adapter. Transfer on the second adapter finishes quickly, leaving two large transfers to share the same 10 GB adapter. Using the Hyper-V port or any address hash load-balancing method, you can do nothing about this except cancel a transfer and restart it, hoping to balance it to the second adapter. With the new method, one of the streams can be dynamically moved to the other adapter, hence the word Dynamic. Flowlets require the split to be made at particular junctions in the stream. It is possible for Dynamic to work even when a neat flowlet opportunity does not present itself.
You should use Enable VMQ on Network Adapters because you can use the PowerShell cmdlet Enable-NetAdapterVmq to enable every NIC for the VMQ feature. With Get-NetAdapterVmq, you can verify that VMQ is enabled on the interfaces.
You should use Set Base and Max CPUs with Set-NetAdapterVmq because this defines how CPUs can be used for VMQ on every interface. With the BaseProcessorNumber parameter of the PowerShell cmdlet Set-NetAdapterVmq, you specify the starting processor for the NIC to use for processing. With the MaxProcessors parameter of the PowerShell cmdlet Set-NetAdapterVmq, you can define the maximum number of CPUs that can be used from the interface.
You should use Enable vRSS with Enable-NetAdapterRSS because you have to enable vRSS on every VMQ network adapter if you want to use the RSS feature and distribute the workload across multiple CPUs. You also can do that with netsh interface tcp set global rss=enabled and in the Device Manager network adapter properties advanced settings.
You should not use TeamingMode: Switch Dependent because, to use VMQ, you must use a Teaming Mode of Switch Dependent; that provides the largest set of VMQ queues.
You should not use LoadBalancingAlgorithm: Transport Ports because this uses the source and destination TCP ports and the IP addresses to create a hash; then it assigns the packets that have that hash value to one of the available network adapters.
You should not use Set BaseProcessorGroup with Set-NetAdapterVmq because if you are using multiple NICs, you should not overlap the logical processor usage, if possible. For example, the first NIC might use cores 1 through 4 (ProcessorGroup0), the next might use cores 5 through 8 (ProcessorGroup1), and so on. For that, you can group the CPUs into ProcessorGroups, as in this PowerShell example: Set-NetAdapterVmq -Name NIC1 -BaseProcessorGroup -0 -BaseProcessorNumber 1 -MaxProcessor Number -Max Processors 4, Set-NetAdapterVmq -Name NIC1 -BaseProcessorGroup -1 -BaseProcessorNumber 5 -MaxProcessorNumber 8 -MaxProcessors 4.
You should not use Enable vRSS with Set-NetAdapter because with the PowerShell cmdlet Set-NetAdapter, you cannot enable RSS. For that, you have to use the PowerShell cmdlets Enable-NetAdapterRss or Set-NetAdapterRss.
7. VMs: C, D; PowerShell commands: F, G. You should use VM3 and VM4 because SR-IOV is supported on the guest machine only as of Windows 8 and Windows Server 2012. The host also has to be at least Windows Server 2012.
You should use the New-VMSwitch PowerShell cmdlet because first you have to create an external virtual switch. You can do that with the following PowerShell command: New-VMSwitch SR-IOV -netadaptername “SR-IOV” -EnableIoV $true.
With Get-VMSwitch, you can verify the properties of the created external VMSwitch. There you can verify settings such as IovVirtualFunctionCount, IoVirtualFunctioninUse, and IoVQueuePairCount. The IovVirtualFunctionCount parameter is the number of VFs that are currently available for use by guest operating systems. Each software-based NIC can be backed by a VF. Each VM can have up to eight software-based NICs. The IovVirtualFunctionsInUse parameter is the current number of VFs in use by guest operating systems. The IoVQueuePairCount parameter is the number of pairs that are available as hardware resources on the physical NIC. This varies among hardware vendors. In most cases, there will be as many pairs available as there are VFs. Depending on the vendor, additional functionality might be included in the VFs; for instance, a hardware vendor might support RSS in a guest operating system that is backed by a VF and requires more than one queued pair for this.
You should use Set-VMNetworkAdapter because this PowerShell cmdlet allows you to enable SR-IOV on the virtual network adapter of the VM. Example: Set-VM Network Adapter IOV8222 -IoVWeight 50 -PassThrough.
You should not use VM1 because the Hyper-V host operating system is not at least Windows Server 2012. You should not use VM2 because the guest operating system is not at least Windows 8.
You should not use Set-VM Host because you cannot access any settings about SR-IOV with this PowerShell cmdlet on the host.
You should not use Set-VMProcessor because you cannot access any settings about SR-IOV with this PowerShell cmdlet.
8.

The correct answer is (from top to bottom): NC, S-API, N-API, NC. You should use the Network Controller for automating the configuration of the network infrastructure because, through SDN, you can use policies and JSON files to automatically set up and configure network components such as virtual networks, gateways, and firewall settings.
For example, you can use policies to configure firewall rules and strengthen the stance of your infrastructure because you can prevent hosts in the same DMZ tier from communicating with one another, thus limiting the reach of an attack. When your segment security is defined by perimeter firewalls, you can’t reach this level of control in a scalable and manageable way.
You can use the Network Controller to manage the following physical and virtual network infrastructure components centrally: Hyper-V VMs and virtual switches, physical network switches, physical network routers, firewall software, VPN gateways, and load balancers.
You should use the Southbound API for “Network Controller communicates with the network” because, in SDN, the southbound interface is the OpenFlow (or alternative) protocol specification. Its main function is to enable communication between the SDN controller and the network nodes (both physical and virtual switches and routers) so that the router can discover network topology, define network flows, and implement requests relayed to it via northbound APIs.
The northbound interface describes the area of protocol-supported communication between the controller and applications or higher-layer control programs. You should use the northbound API for “Administrator communicates with Network Controller” because a northbound API interface is an interface that allows a particular component of a network to communicate with a higher-level component. Conversely, a southbound interface allows a particular network component to communicate with a lower-level component.
Northbound flow can be thought of as going upward, while southbound flow can be thought of as going downward. In architectural diagrams, northbound interfaces are drawn at the top of the applicable component and southbound interfaces are drawn at the bottom of the component.
You should use the Network Controller for Windows PowerShell, the REST API, and management applications to centrally manage your network environment through the network controller and to automate the configuration processes.
9.
Correct answers (from top to bottom): True, True, True, False, True, True, False, True, True.
You should answer True for the statement “Is using the Azure Virtual Filtering Platform (VFP) switch” because HNVv2 uses the Azure Virtual Filtering Platform (VFP) forwarding extension in the Hyper-V Switch. HNVv2 also is fully integrated into Microsoft Azure Stack, which includes the Network Controller in the SDN stack. VFP is a programmable switch that exposes an easy-to-program abstracted interface to network agents that act on behalf of network controllers such as the VNET controller and the SLB controller. By leveraging host components and doing much of the packet processing on each host running in the datacenter, the Azure SDN data plane scales nodes from 1 GB to 40 GB.
You should answer True for the statement “Cannot be used with any other third-party switch extension” because HNVv2 is implemented using the Azure VFP switch extension, which cannot be used with any third-party switch extension. Hyper-V switch extensions do not work with HNVv2 in the new SDN stack.
You should answer True for the statement “Broadcasts and subnet multicasts implemented using unicast replication” because, with Windows Server 2016 broadcast and subnet, multicasts are implemented using unicast replication. When a VM broadcasts a packet, HNV uses unicast replication to make a copy of the original packet and replace the destination IP and MAC addresses with the addresses of each VM in the same VSID; therefore, it converts the broadcast network traffic into unicast network traffic.
You should answer False for the statement “Is using Hyper-V switch extensions in the SDN stack” because Hyper-V switch extensions do not work with HNVv2 in the new SDN stack. HNVv2 is implemented using the Azure Virtual Filtering Platform (VFP) switch extension. You should answer True for “Can use cross-subnet multicast routing” because, in this scenario, the separated addresses (CAs and PAs), the policy settings of the Hyper-V hosts, and the address translation between the CA and the PA for inbound and outbound VM traffic isolate these sets of servers using either the NVGRE key or the VXLAN VNID. Furthermore, the virtualization mappings and transformation decouple the virtual network architecture from the physical network infrastructure. Although servers in the Pearson network and servers in the Pearson UCertify network reside in their own CA IP subnets (10.1.1/24), their physical deployment happens on two hosts in different PA subnets, 192.168.1/24 and 192.168.2/24, respectively. The implication is that cross-subnet virtual machine provisioning and live migration become possible with HNV.
You should answer True for the statement “For a VM establishing a connection to another VM in the same VSID, the Host Agent is responsible for MAC address resolution” because HNVv2 implements correct L2 switching and L3 routing semantics to work just as a physical switch or router would work. When a VM connected to an HNV virtual network attempts to establish a connection with another VM in the same VSID, it first needs to learn the CA MAC address of the remote VM. If the source VM’s ARP table has an ARP entry for the destination VM’s IP address, the MAC address from this entry is used. If an entry does not exist, the source VM sends an ARP broadcast with a request for the MAC address that corresponds to the destination VM’s IP address to be returned. The Hyper-V switch intercepts this request and sends it to the Host Agent. The Host Agent looks in its local database for a corresponding MAC address for the requested destination VM’s IP address.
You should answer False for the statement “For a VM establishing a connection to another VM in another VSID, nondefault routes are supported” because if a VM connected to an HNV virtual network wants to create a connection with a VM in a different VSID, a packet needs to be routed accordingly. HNV assumes a star network topology. Only one IP address in the CA space is used as the next-hop to reach all IP prefixes. This enforces a limitation to a single default route, so nondefault routes are not supported.
You should answer True for the statement “Forwarding table of the external switch does not grow with the increase in the VMs behind the physical port on the server” because VXLAN is a Layer 2 technology that enables you to create an L2 network on top of a Layer 3 network, providing further network isolation. VXLAN provides a virtual L2 network that stretches over multiple physical L2 networks. Therefore, provisioning resources in a cloud environment is not restricted to a single physical Layer 2 network. Physical servers can be a part of a VXLAN network as long as they are connected by IPv4 or IPv6 networks.
You should answer True for the statement “1 PA per NIC team member” because the PA sharing scheme for Windows Server 2012 R2 is 1 PA per VSID per host. For Windows Server 2016, it is one PA per NIC team member.
10. You should choose the statement “The Network Controller processes SLB commands that come in through the northbound API from the Windows Server 2016 System Center Virtual Machine Manager” because, in SDN, the northbound API enables you to configure, monitor, troubleshoot, and deploy new devices (by REST endpoint or a management application as VMM). The northbound API is the interface that enables SCVMM to communicate with the Network Controller.
You should choose the statement “The Network Controller communicates through the southbound API to the SLB Host Agent” because the southbound API allows the Network Controller to communicate with the network. The SLB Host Agent listens for SLB policy updates from the Network Controller. In addition, the Host Agent programs rules for SLB into the SDN-enabled Hyper-V virtual switches that are configured on the local computer. Between the Network Controller and the SLB Host Agent, the SLB MUX component processes inbound network traffic and maps VIPs (virtual IPs) to DIPs (datacenter IPs); then it forwards the traffic to the correct DIP. Each MUX also uses BGP to publish VIP routes to edge routers.
You should choose the statement “SRV01 and SRV02 communicate through east–west TCP/UDP traffic” because east–west communication is virtual network internal communication. North–south SLB communication comes from outside the virtual network from WAN.
11. A, C. You should deploy the Network Controller because then you have the basic computer and network infrastructure in place to proceed with the RAS Gateway deployment. The Network Controller communicates with network devices, services, and components by using the southbound API. With the southbound API, the Network Controller can discover network devices, detect service configurations, and gather all the needed information about the network. The Network Controller also offers RAS Gateway management. In SCVMM, the RAS Gateway is known as the Windows Server Gateway. Some Network Controller features for RAS follow:
![]() You can add and remove gateway VMs from the cluster and specify the level of backup required.
You can add and remove gateway VMs from the cluster and specify the level of backup required.
![]() Site-to-site virtual private network (VPN) gateway connectivity between remote tenant networks and your datacenter is accomplished using IPSec.
Site-to-site virtual private network (VPN) gateway connectivity between remote tenant networks and your datacenter is accomplished using IPSec.
![]() Site-to-site VPN gateway connectivity between remote tenant networks and your datacenter is accomplished using Generic Routing Encapsulation (GRE).
Site-to-site VPN gateway connectivity between remote tenant networks and your datacenter is accomplished using Generic Routing Encapsulation (GRE).
![]() Point-to-site VPN gateway connectivity is supported so that your tenants’ administrators can access their resources on your datacenter from anywhere.
Point-to-site VPN gateway connectivity is supported so that your tenants’ administrators can access their resources on your datacenter from anywhere.
![]() Layer 3 forwarding capability exists.
Layer 3 forwarding capability exists.
You should deploy the Software Load Balancer as well. This step is not required when deploying a RAS Gateway, but if you need simplicity and preview validation, this is recommended. You should not create an IP pool for GRE VIP addresses because you can create an IP pool after you have created the GRE VIP logical network. This is not a prerequisite for the RAS Gateway configuration in SCVMM 2016; it is the next step after creating the GRE VIP logical network.
You should not import a gateway service template because, after downloading the gateway service template from the Microsoft SDN GitHub repository, you need to copy the contents to a folder on your VMM server to which the VMM server has access. The download contains two templates, one for Generation 1 VMs and one for Generation 2 VMs. After that, you import the service template. All these steps must be done in SCVMM 2016 after you deploy the network controller and the SLB.
12. B, D. You should use distributed firewall policies because the new Windows Server 2016 SDN Network Controller Datacenter Firewall is a new service. This is a stateful multitenant firewall that tenant administrators can use to install and configure firewall policies to protect virtual networks.
You should use Network Security Groups because, with Windows Server 2016 Network Controller and SDN, the Network Security Groups can be used like Azure Network Security Groups in Azure. Through Network Security Groups, administrators can control access by permitting or denying communication between the workloads within a virtual network, from systems on a customer’s networks via cross-premises connectivity, and direct Internet communication. You can apply NSGs on the subnet or NIC levels. You can define rules about which source or destination port protocols are allowed or denied.
You should use an antimalware solution because the Windows Server 2016 Network Controller does not offer this. Instead, it offers the Datacenter Firewall, which administrators can use to install and configure firewall policies to protect virtual machine and networks.
You should use network traffic encryption because you cannot encrypt datacenter or virtual network traffic with the Windows Server 2016 Network Controller and the Datacenter Firewall.
End-of-Chapter Review Questions
1. You should use the following solution:
New-VMSwitch Switch1 -NetAdapterName “NIC1”, “NIC2” -EnableEmbeddedTeaming $true; Add-VMNetworkAdapter -SwitchName MyRDMAswitch -Name SMBRDMA1; Add-VMNetworkAdapter -SwitchName RDMAswitch -Name SMBRDMA2; Enable-NetAdapterRDMA “vEthernet (SMBRDMA_1)”, “vEthernet (SMBRDMA_2)”.
2. B. In this case, you cannot use the Enable-NetAdapterRss PowerShell cmdlet to enable Receive Side Scaling because the Hyper-V host processor does not support this feature. To reduce the number of processor cycles that are used, you can enable Receive Side Coalescing with the Enable-NetAdapterRsc cmdlet. This solution improves scalability by reducing the overhead for processing a large amount of network I/O traffic by offloading some of the work to the network adapters.
3. B. When you disable SMB Multichannel, SMB Direct is also disabled. With SMB Multichannel, SMB detects whether a network adapter has the RDMA capability and then creates multiple RDMA connections for that single session (two per interface). Without SMB Multichannel, SMB uses regular TCP/IP with the RDMA-capable network adapters (all network adapters provide a TCP/IP stack along with the new RDMA stack). When you disable SMB Multichannel, you still can use SET, RDMA, and RSS.
4. A, B, C, D, E. All answers are correct.
5. A, B, D. When you want to add a virtual gateway for a tenant, you have to verify the existence of the GatewayPool, the VirtualNetwork, and the VirtualSubnet because you have to select the VirtualSubnet to be used for routing between the Gateway and the VirtualNetwork. When you want to connect container endpoints to a tenant virtual network through the SDN stack, you have to install the private cloud plug-in into the container host (tenant) VM. The Network Proxy is used to allocate multiple IP addresses for container host VMs.
