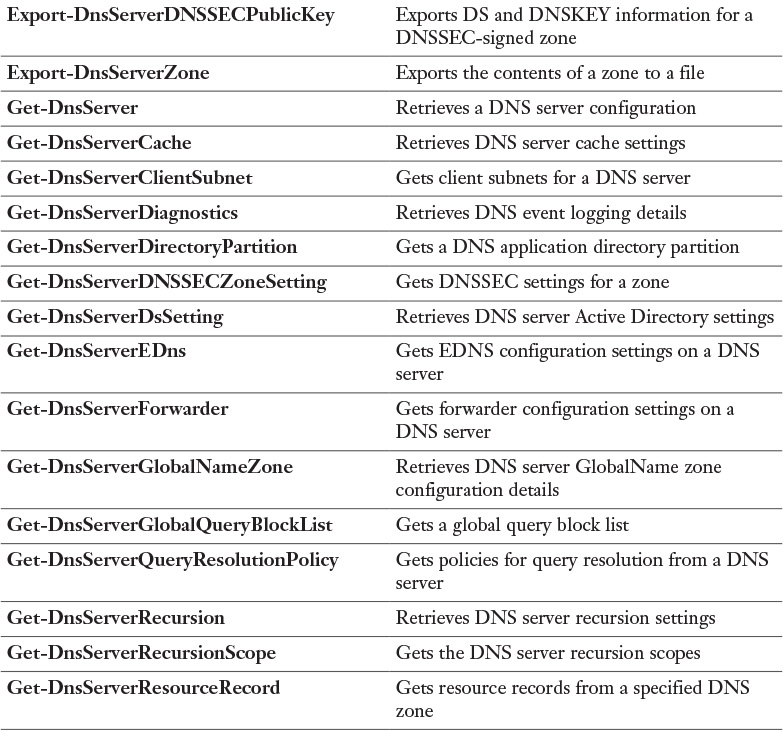
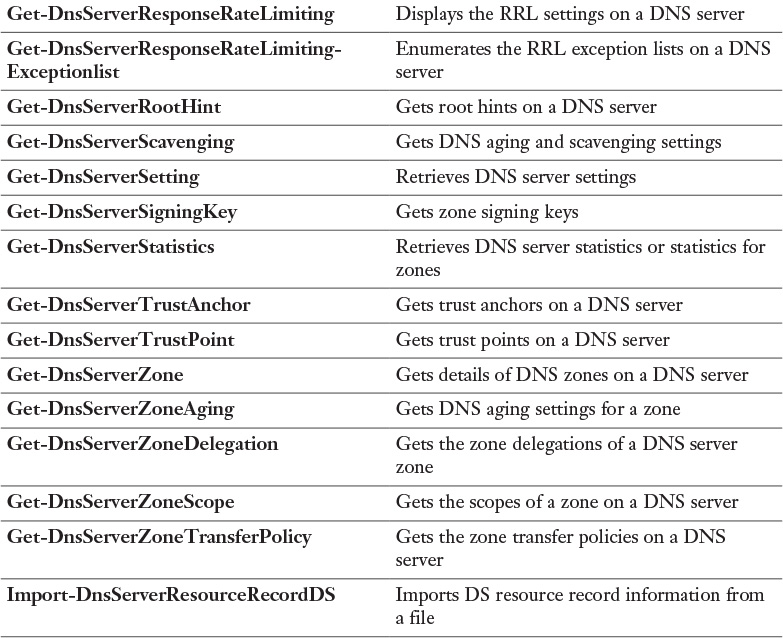
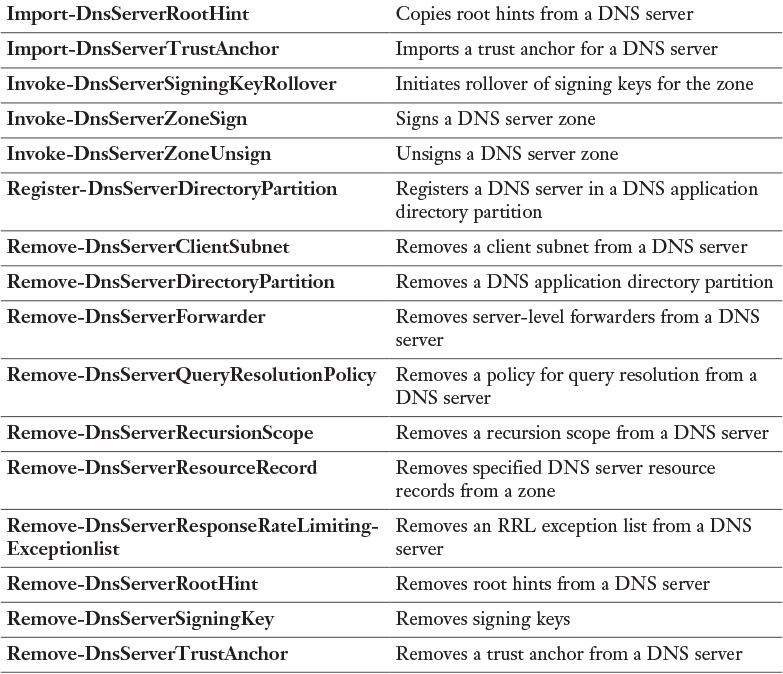
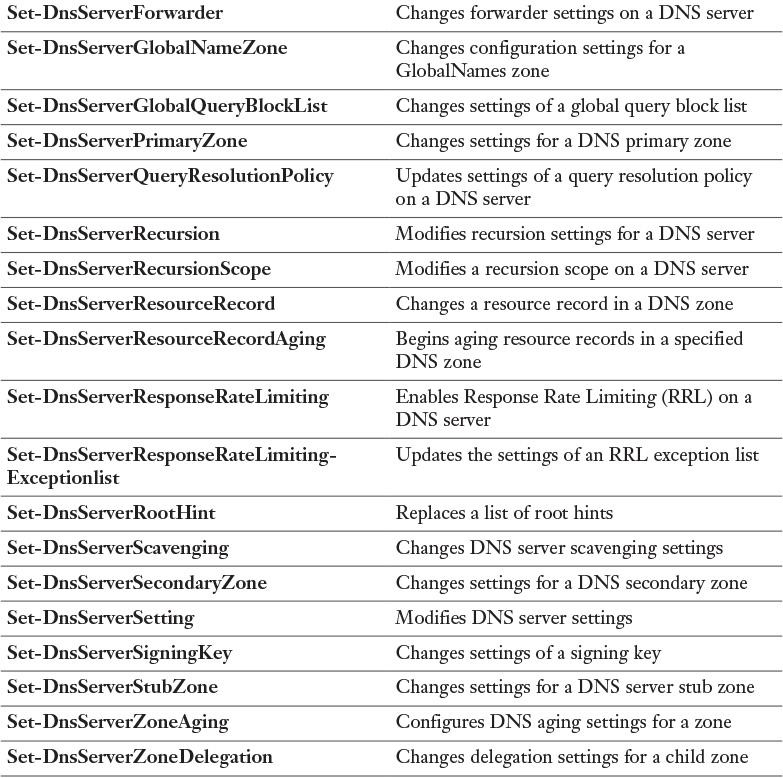
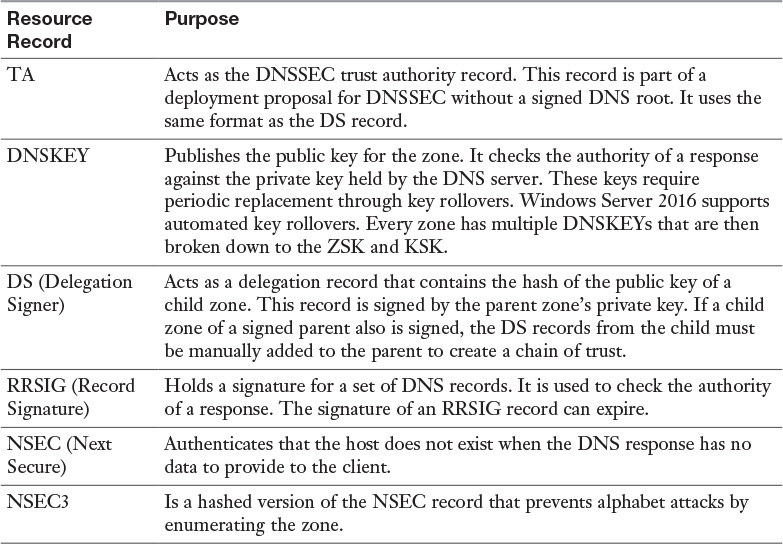
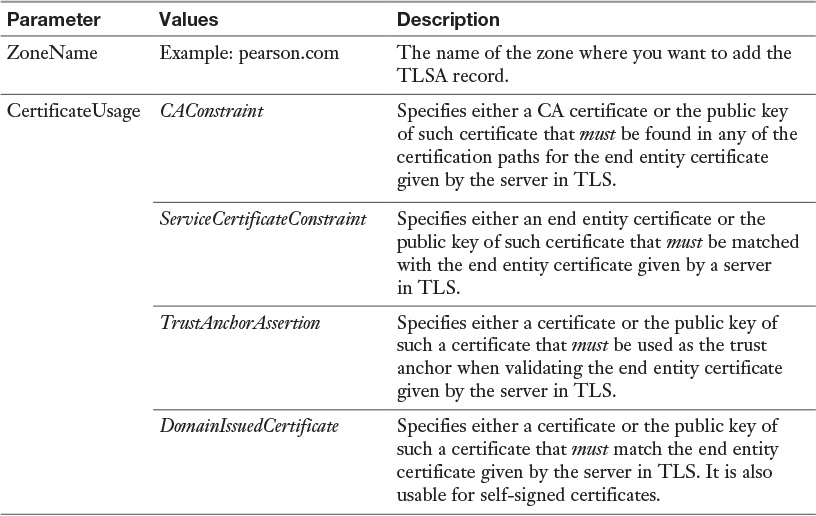
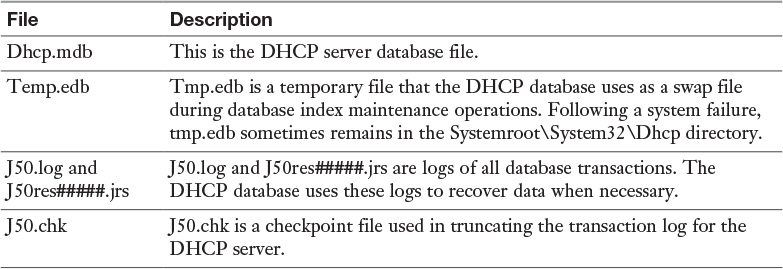
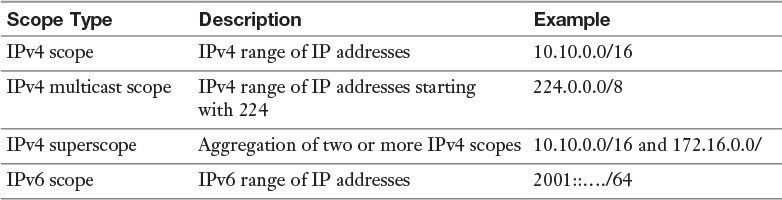
Appendix C. Memory Tables Answer Key

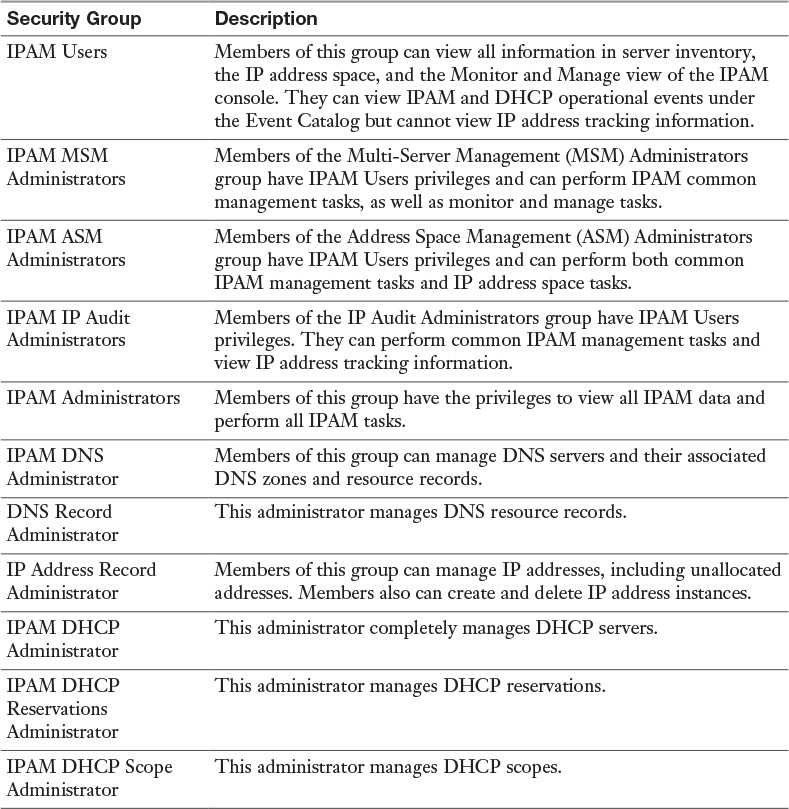
Best Practices for Using the IPAM Event Catalog:
![]() Account logon event auditing should be enabled on DCs and NPS servers. Without this preconfiguration, the IPAM server cannot display account logon events in the IPAM Event Catalog.
Account logon event auditing should be enabled on DCs and NPS servers. Without this preconfiguration, the IPAM server cannot display account logon events in the IPAM Event Catalog.
![]() The security event log size should be large enough to allow the periodic audit task to complete data collection before it is rolled over.
The security event log size should be large enough to allow the periodic audit task to complete data collection before it is rolled over.
![]() For better performance and disk space management, IPAM Event Catalog data purge should be performed periodically to reduce the amount of data used for IPAM events.
For better performance and disk space management, IPAM Event Catalog data purge should be performed periodically to reduce the amount of data used for IPAM events.
![]() The audit log file location for both DHCP IPv4 and IPv6 leases must be configured in a common order. The IPAM audit task selects the log files from one network share per server.
The audit log file location for both DHCP IPv4 and IPv6 leases must be configured in a common order. The IPAM audit task selects the log files from one network share per server.
![]() The DHCP audit log file should be large enough for one day, to ensure that no lease events are lost because of size overruns.
The DHCP audit log file should be large enough for one day, to ensure that no lease events are lost because of size overruns.
![]() Be sure to select an optimal time period for a query. Typically, a query interval of 3 days to 15 days is optimal.
Be sure to select an optimal time period for a query. Typically, a query interval of 3 days to 15 days is optimal.
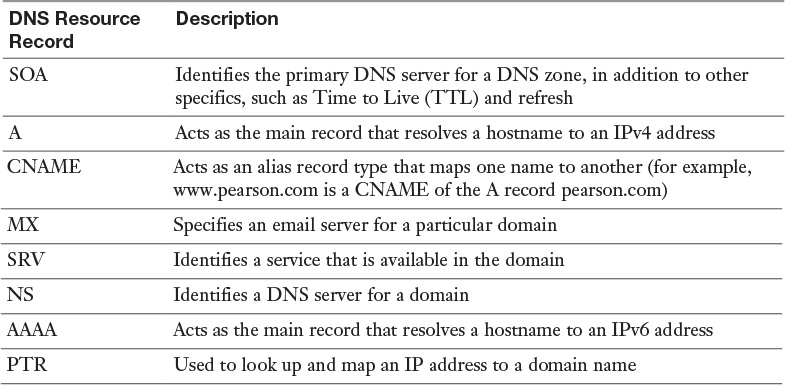
The following list outlines the most important technologies, services, and components of a Windows Server 2016 DirectAccess solution:
![]() DirectAccess server
DirectAccess server
![]() DirectAccess client
DirectAccess client
![]() Active Directory
Active Directory
![]() DNS server
DNS server
![]() NLS
NLS
![]() KDC proxy
KDC proxy
![]() Certification service
Certification service
![]() Certificates
Certificates
![]() DNS64
DNS64
![]() 6to4/ISATAP/Teredo
6to4/ISATAP/Teredo
![]() Group Policy
Group Policy
![]() NCA
NCA
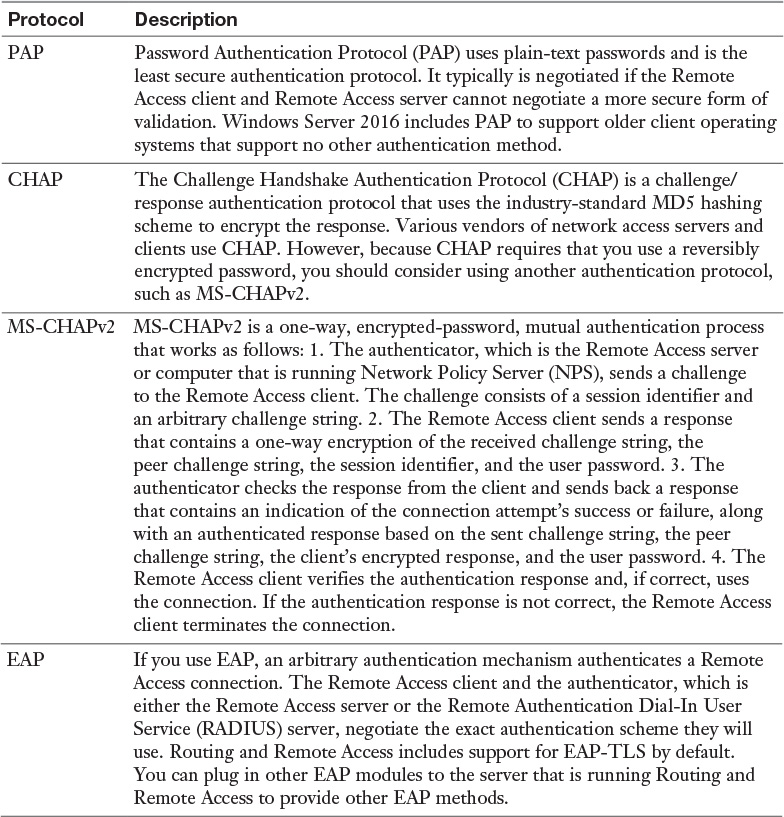
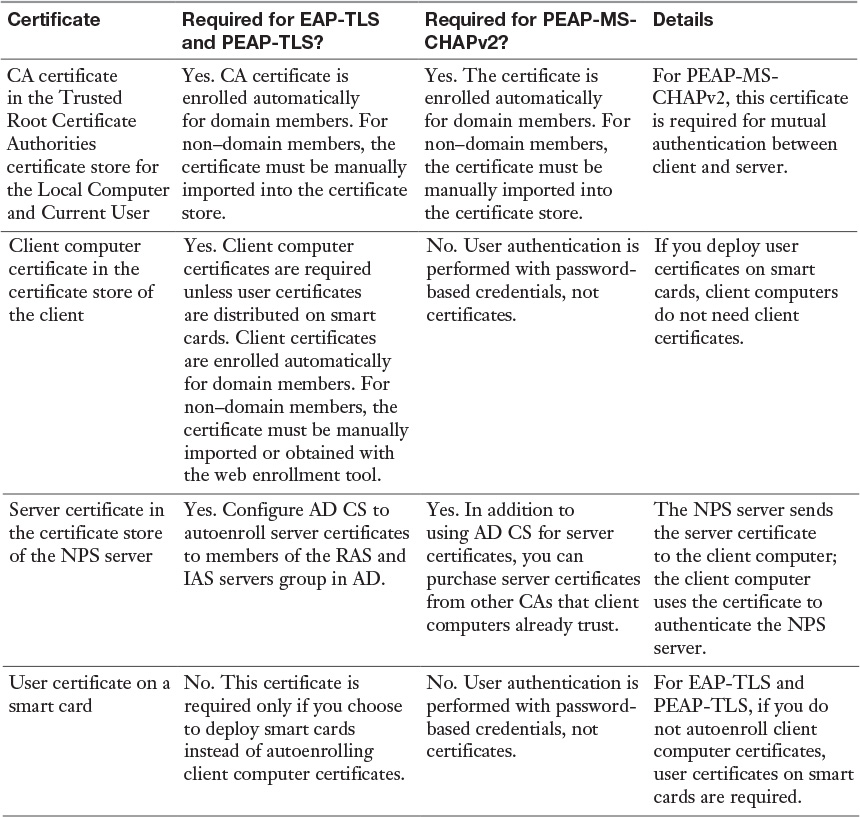
With PEAP-MS-CHAPv2, PEAP-TLS, or EAP-TLS as the authentication method, a Windows Server 2016 NPS server must use a server certificate that meets the minimum server certificate requirements. A client accepts the authentication attempt of the server when the server certificate meets the following requirements:
![]() The subject name contains a value. If you issue a certificate to your server running NPS that has a blank subject name, the certificate is not available to authenticate your NPS server.
The subject name contains a value. If you issue a certificate to your server running NPS that has a blank subject name, the certificate is not available to authenticate your NPS server.
![]() The computer certificate on the server chains to a trusted root Certificate Authority (CA) and does not fail any of the checks that are performed by CryptoAPI and that are specified in the remote access policy or network policy.
The computer certificate on the server chains to a trusted root Certificate Authority (CA) and does not fail any of the checks that are performed by CryptoAPI and that are specified in the remote access policy or network policy.
![]() The computer certificate for the NPS server or VPN server is configured with the Server Authentication purpose in Extended Key Usage (EKU) extensions. (The object identifier for Server Authentication is 1.3.6.1.5.5.7.3.1.)
The computer certificate for the NPS server or VPN server is configured with the Server Authentication purpose in Extended Key Usage (EKU) extensions. (The object identifier for Server Authentication is 1.3.6.1.5.5.7.3.1.)
![]() The server certificate is configured with a required algorithm value of RSA.
The server certificate is configured with a required algorithm value of RSA.
![]() The Subject Alternative Name extension, if used, must contain the DNS name of the server.
The Subject Alternative Name extension, if used, must contain the DNS name of the server.
Chapter 12
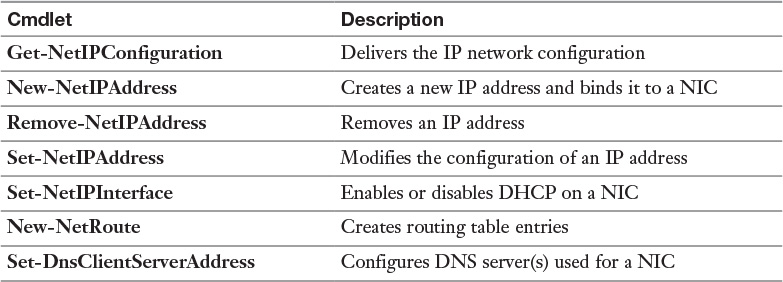
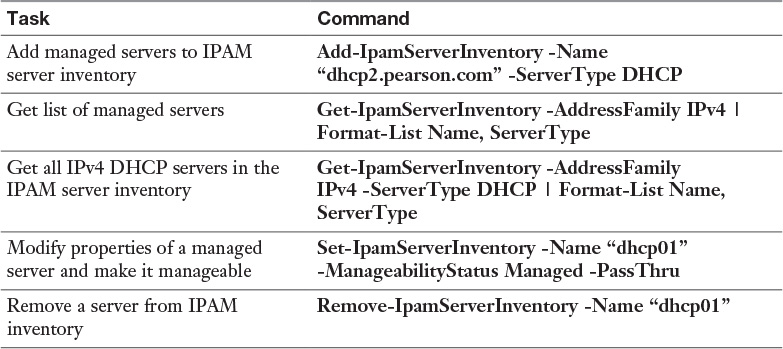
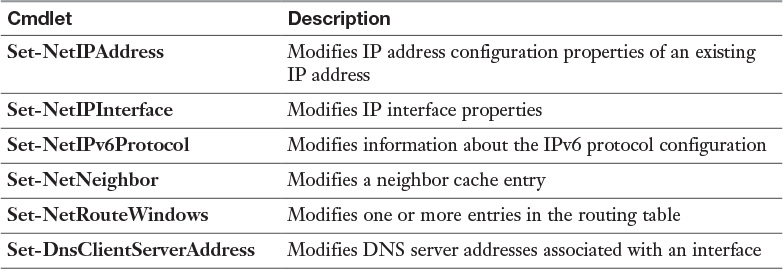
To configure a static IP address for a server in an IPv4 configuration, you need to determine the following settings:
![]() IPv4 address
IPv4 address
![]() Subnet mask
Subnet mask
![]() Default gateway
Default gateway
![]() DNS servers
DNS servers
On IPv4 networks, you can assign addresses to an interface in three ways:
![]() Manually, by using static addresses
Manually, by using static addresses
![]() Dynamically, by using DHCP server
Dynamically, by using DHCP server
![]() Automatically, by using APIPA
Automatically, by using APIPA
IPv6 address assignment is slightly different. For example, IPv6 addresses can be assigned to an interface in four ways:
![]() Manually, by configuring one or more IPv6 addresses on the interface
Manually, by configuring one or more IPv6 addresses on the interface
![]() Stateful, by using address autoconfiguration through DHCPv6 server
Stateful, by using address autoconfiguration through DHCPv6 server
![]() Stateless, by using autoconfiguration based on the receipt of router advertisement messages
Stateless, by using autoconfiguration based on the receipt of router advertisement messages
![]() Stateful and stateless (both), by address autoconfiguration
Stateful and stateless (both), by address autoconfiguration
Each IPv6 address is 128 bits long. The prefix is the part of the address that contains the bits with fixed values or the subnet prefix’s bits. The prefix is equivalent to the network ID for IPv4 addresses. IPv6 subnets, prefixes, routes, and address ranges are represented in the same way as CIDR notations. An IPv6 prefix is represented in address/prefix length notation. For example, 2001:DB8::/48 (a route prefix) and 2001:DB8:0:2D4C::/64 (a subnet prefix) are IPv6 address prefixes. IPv6 uses prefixes instead of a subnet mask.
Tip
You can view the prefix policies by using the Get-NetPrefixPolicy PowerShell cmdlet (see Figure 12-14).
Tip
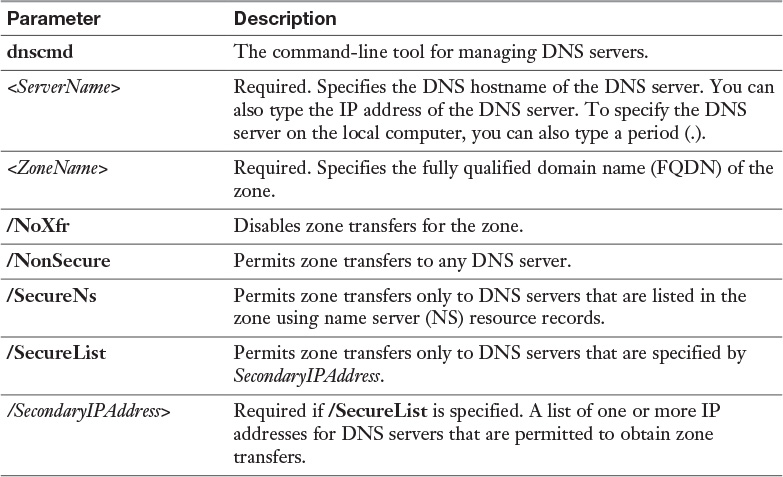
By default, DNS servers on Windows Server 2008 or later have a global query block list that prevents ISATAP resolution even when the host record is created and properly configured. You need to remove ISATAP from the global query block list in DNS if you are using an ISATAP host record to configure ISATAP clients. You can do that with the PowerShell cmdlet Set-DnsServerGlobalQueryBlockList or the following command: dnscmd /config /globalqueryblocklist.
To use the DFS features, the following requirements must be met:
![]() The forest must be at the forest functional level of Windows Server 2008 or newer.
The forest must be at the forest functional level of Windows Server 2008 or newer.
![]() The domain must be at the domain functional level of Windows Server 2008 or newer.
The domain must be at the domain functional level of Windows Server 2008 or newer.
![]() The namespace servers must be running Windows Server 2008 or newer.
The namespace servers must be running Windows Server 2008 or newer.
You can modify settings for the DFS root with the PowerShell cmdlet Set-DfsnRoot. You can use this cmdlet to enable or disable the following settings:
![]() Site costing
Site costing
![]() In-site referrals
In-site referrals
![]() Root scalability
Root scalability
![]() Target failback
Target failback
With the following command, you can enable root scalability, which allows the DFS namespace server to poll domain controllers for updates:
Set-DfsnRoot -Path "\PearsonPUcertify" -EnableRootScalability $True
-TimeToLiveSec 900
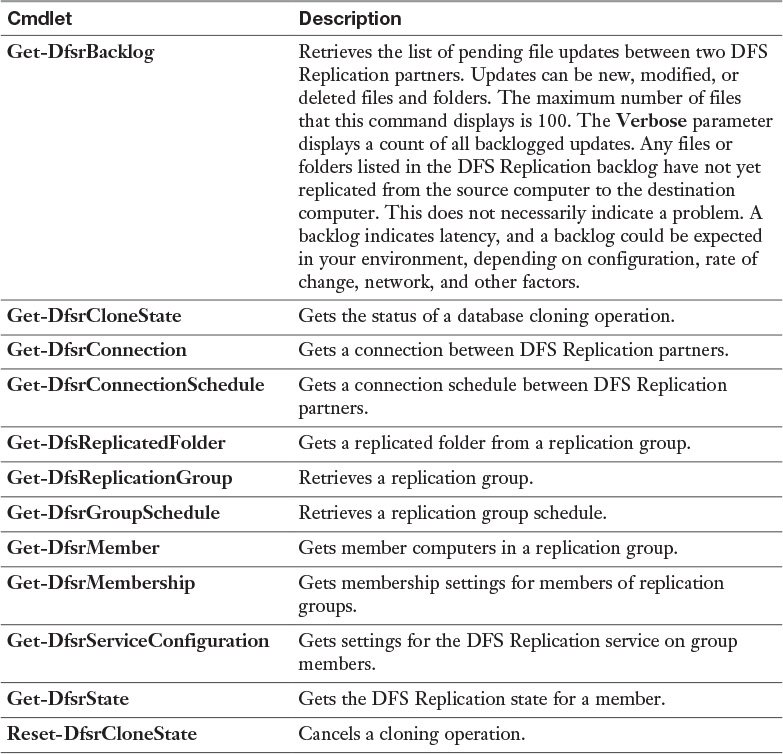
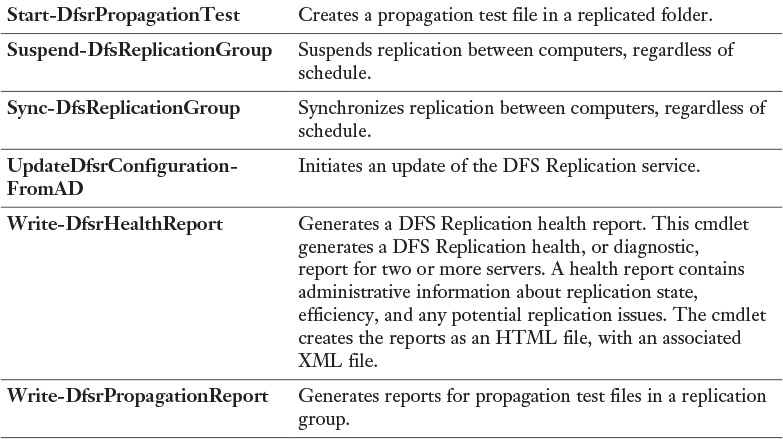
With the PowerShell cmdlet Write-DfsrHealthReport, you can generate a DFSR health report to verify replication and get information about replication bandwidth savings through the use of RDC or errors. Figure 13-40 shows an example of this command and example output of an error in the report when the problem lies in the DFS Replication service on DFS2.
With the PowerShell cmdlet Sync-DfsReplicationGroup, you can force the synchronization of DFS Replication. Take a look at this example:
Sync-DfsReplicationGroup -GroupName "ReplicaGroup1" -SourceComputer
Name DFS1 -DestinationComputerName DFS2 -DurationInMinutes 1
The following example retrieves the first 100 unreplicated changes between the local computer and the upstream computer, DFS2, for the replication group RepliGroup1 and the replicated folder named Data:
Get-DfsrBacklog -SourceComputerName "DFS2" -GroupName "RepliGroup1"
-FolderName "Data"
DFSR uses Remote Differential Compression (RDC), a client/server protocol that can be used to efficiently update files over a limited-bandwidth network.
You can enable and disable cross-file RDC with the following PowerShell cmdlet:
Set-DfsrConnection -DisableCrossFileRDC $true
You cannot recover files from the ConflictAndDeleted and Preexisting folders except from backup.
Use the Windows PowerShell cmdlets Get-DfsrPreservedFiles and RestoreDfsr-PreservedFiles to allow the recovery of files from these folders. You can restore these files and folders into their previous location or a new location. You can choose to move or copy the files, and you can keep all versions of a file or only the latest version.
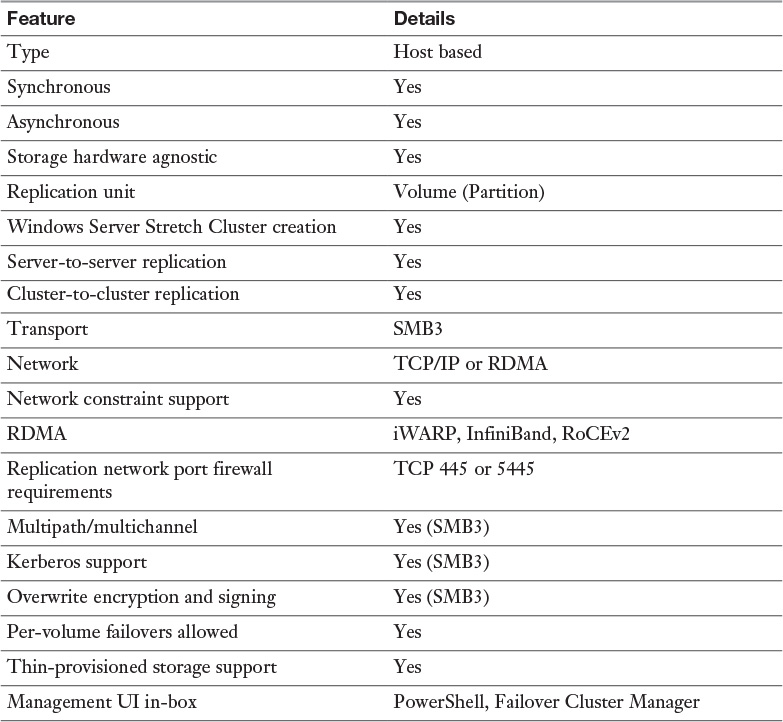
DFS includes database-management tasks that use database cloning to help you perform initial database replication. Furthermore, DFS includes tasks that can recover the DFS database in case of data corruption. A new Windows Server 2016 feature is the capability to clone the DFS database for initial replication, to dramatically improve performance during initial synchronization. You also can use the Data Deduplication feature to reduce bandwidth consumed when replicating file data.
The primary benefits of BranchCache are as follows:
![]() Reduces the network use on WAN connections between headquarters and branch offices
Reduces the network use on WAN connections between headquarters and branch offices
![]() Locally caches frequently used files on computers in the branch office
Locally caches frequently used files on computers in the branch office
![]() Improves the performance of applications that use HTTP or HTTPS, SMB, or BITS
Improves the performance of applications that use HTTP or HTTPS, SMB, or BITS
You can configure BranchCache in two different modes (see Figure 13-45):
![]() Hosted cache mode (HCM): This mode operates by deploying a computer that is running Windows Server 2008 R2 or newer versions as a hosted cache server in the branch office. Client computers locate the host computer so that they can retrieve content from the hosted cache when it is available. If the content is not available in the hosted cache, the content is retrieved from the content server over a WAN link. The content is then provided to the hosted cache, which serves successive client requests.
Hosted cache mode (HCM): This mode operates by deploying a computer that is running Windows Server 2008 R2 or newer versions as a hosted cache server in the branch office. Client computers locate the host computer so that they can retrieve content from the hosted cache when it is available. If the content is not available in the hosted cache, the content is retrieved from the content server over a WAN link. The content is then provided to the hosted cache, which serves successive client requests.
![]() Distributed cache mode (DCM): For smaller remote offices, you can configure BranchCache in distributed cache mode without requiring a server. In this mode, local client computers running Windows 7 or newer maintain a copy of the content and make it available to other authorized clients that request the same data. This eliminates the need to have a server in the branch office. However, unlike hosted cache mode, this configuration works per subnet only. In addition, clients that hibernate or disconnect from the network cannot provide content to other requesting clients.
Distributed cache mode (DCM): For smaller remote offices, you can configure BranchCache in distributed cache mode without requiring a server. In this mode, local client computers running Windows 7 or newer maintain a copy of the content and make it available to other authorized clients that request the same data. This eliminates the need to have a server in the branch office. However, unlike hosted cache mode, this configuration works per subnet only. In addition, clients that hibernate or disconnect from the network cannot provide content to other requesting clients.
You also can use the Enable-BCHostedClient PowerShell cmdlet to configure BranchCache in hosted cache mode. The following commands enable hosted cache mode by using SVR1.pearson.com as the hosted cache server for HTTPS and clients running Windows 10:
Enable-BCHostedClient -ServerNames SVR1.pearson.com -UseVersion
Windows10
The following cmdlet enables hosted cache mode and registers Service Connection Points in AD DS:
Enable-BCHostedServer -RegisterSCP
The following cmdlet enables distributed cache mode on the server:
Enable-BCDistributed
With the PowerShell cmdlet Get-BCStatus, you can verify the correct BranchCache configuration on the file server, BranchCache host, or BranchCache client.
You can use the netsh branchcache show status all command to display the BranchCache service status.