7.2. System Model
Dynamics of state evolution
A susceptible accepts a communication request with a probability  , where the subscript
, where the subscript  represents reception, and the superscript
represents reception, and the superscript  designates control functions of the network. At any given time
designates control functions of the network. At any given time  , there are
, there are  infective-susceptible pairs. Susceptible nodes are hence transformed to infectives at rate
infective-susceptible pairs. Susceptible nodes are hence transformed to infectives at rate  , where
, where  is the rate at which a particular pair of nodes “meet,” which is assumed to be the same for all pairs (i.e. homogeneous mixing assumption). Propagation of the worm, therefore, can be contained through appropriate regulation of
is the rate at which a particular pair of nodes “meet,” which is assumed to be the same for all pairs (i.e. homogeneous mixing assumption). Propagation of the worm, therefore, can be contained through appropriate regulation of  subject to
subject to 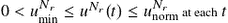 . The lower bound
. The lower bound  arises due to the minimum QoS requirements for data traffic, since the acceptance probability has to be the same irrespective of whether the request arrives from another infective, susceptible, or recovered node. The latter is due to the fact that a recipient node cannot distinguish the type of a transmitter in advance and has no choice but to treat all requests the same — since otherwise all infective nodes can be trivially blacklisted. The upper bound
arises due to the minimum QoS requirements for data traffic, since the acceptance probability has to be the same irrespective of whether the request arrives from another infective, susceptible, or recovered node. The latter is due to the fact that a recipient node cannot distinguish the type of a transmitter in advance and has no choice but to treat all requests the same — since otherwise all infective nodes can be trivially blacklisted. The upper bound  (which can be normalized to
(which can be normalized to 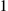 ) provides the reception rate that nodes use for providing the desired QoS in the absence of security considerations, i.e. during the “normal” operation of the network.
) provides the reception rate that nodes use for providing the desired QoS in the absence of security considerations, i.e. during the “normal” operation of the network.
We now consider the dissemination of security patches in the network. A predetermined set of nodes, referred to as dispatchers (e.g. BS for cellular and exit-points for delay-tolerant networks), are preloaded with the patches. We assume that the dispatchers cannot be infected, and that there are  dispatchers where
dispatchers where  is as usual the total number of nodes in the network and parameter
is as usual the total number of nodes in the network and parameter  is between
is between  and
and 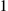 . Each node communicates with the dispatchers, and thereby fetches security patches, at the overall rate of
. Each node communicates with the dispatchers, and thereby fetches security patches, at the overall rate of  at time
at time  . The parameter
. The parameter  depends on node density, mobility parameters, allowable transmission rates, etc. The control function
depends on node density, mobility parameters, allowable transmission rates, etc. The control function  , with subscript
, with subscript 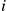 denoting immunization, can be used to regulate the bandwidth consumed in propagation of patches: the higher the value of
denoting immunization, can be used to regulate the bandwidth consumed in propagation of patches: the higher the value of  , the higher is the recovery rate but so is the rate of resource consumption in patch transmissions. Clearly, if the node that receives the patch is a susceptible node, it installs the patch and its state changes to recovered. If an infective receives the patch, the patch may fail to heal it, or, the worm may prevent its installation. We capture the above possibility, by introducing a coefficient
, the higher is the recovery rate but so is the rate of resource consumption in patch transmissions. Clearly, if the node that receives the patch is a susceptible node, it installs the patch and its state changes to recovered. If an infective receives the patch, the patch may fail to heal it, or, the worm may prevent its installation. We capture the above possibility, by introducing a coefficient  :
:  occurs when the patch is completely unable to remove the worm from infectives and only immunizes the susceptibles, whereas
occurs when the patch is completely unable to remove the worm from infectives and only immunizes the susceptibles, whereas  represents the other extreme scenario where a patch can equally well immunize and heal susceptibles and infective nodes.1 Now, if the patch heals an infective, its state changes to recovered, else it continues to remain an infective.
represents the other extreme scenario where a patch can equally well immunize and heal susceptibles and infective nodes.1 Now, if the patch heals an infective, its state changes to recovered, else it continues to remain an infective.
The worm at an infective host “kills” it with rate proportional to  at a given time
at a given time  , where superscript
, where superscript  designates this is a control function of the malware; this is accomplished by executing specific codes with a probability of choice. The worm regulates the death process by appropriately choosing
designates this is a control function of the malware; this is accomplished by executing specific codes with a probability of choice. The worm regulates the death process by appropriately choosing  at each
at each  , subject to
, subject to  . The upper bound arises due to processor constraints and the resulting limitations on the maximum rate of execution of such codes. Let
. The upper bound arises due to processor constraints and the resulting limitations on the maximum rate of execution of such codes. Let  ,
,  . Our discussions lead to the following system of differential equations representing the dynamics of the system:
. Our discussions lead to the following system of differential equations representing the dynamics of the system:
![]() (7.1a)
(7.1a)
 (7.1b)
(7.1b)
![]() (7.1c)
(7.1c)
and also satisfy the following constraints at all  :
:
![]() (7.2)
(7.2)
Thus,  constitute the system state functions,
constitute the system state functions,  constitutes the network control functions and
constitutes the network control functions and  constitutes the malware’s control function. Note that nodes use identical reception, patching, and killing rate functions irrespective of the states in their neighborhoods since they do not know these states. Nevertheless, since these rates are allowed to vary with time, they can be chosen in accordance with how the overall network states are expected to evolve.
constitutes the malware’s control function. Note that nodes use identical reception, patching, and killing rate functions irrespective of the states in their neighborhoods since they do not know these states. Nevertheless, since these rates are allowed to vary with time, they can be chosen in accordance with how the overall network states are expected to evolve.
Henceforth, wherever not ambiguous, we drop the dependence on  and make it implicit. Fig. 7.1 illustrates the transitions between different states of nodes and the notations used.
and make it implicit. Fig. 7.1 illustrates the transitions between different states of nodes and the notations used.
Defense and attack objectives
The total damage inflicted by the malware during the network operation interval  is due to the presence of infectives, the death of nodes, the resources consumed for spreading the security patches, and the QoS deterioration due to the reduction of reception rate. Infectives can perform harmful activities over time. Dead nodes are inoperative and thus inflict a time-accumulative cost on the network. The bandwidth overhead at time
is due to the presence of infectives, the death of nodes, the resources consumed for spreading the security patches, and the QoS deterioration due to the reduction of reception rate. Infectives can perform harmful activities over time. Dead nodes are inoperative and thus inflict a time-accumulative cost on the network. The bandwidth overhead at time  due to the media scanning and transmission of the security packets by the dispatchers is
due to the media scanning and transmission of the security packets by the dispatchers is 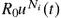 . Due to the reception rate control, the susceptibles lose a
. Due to the reception rate control, the susceptibles lose a  fraction of packets transmitted by all nodes which degrades the overall QoS. We therefore consider the aggregate network damage at time
fraction of packets transmitted by all nodes which degrades the overall QoS. We therefore consider the aggregate network damage at time  as a combination of
as a combination of  . We adopt a linear cost function in this chapter for analytical tractability. Note that the damage function can be scaled so that one of the coefficients may be chosen as unity: we choose the one associated with the instantaneous bandwidth overhead. Thus, the damage over the interval
. We adopt a linear cost function in this chapter for analytical tractability. Note that the damage function can be scaled so that one of the coefficients may be chosen as unity: we choose the one associated with the instantaneous bandwidth overhead. Thus, the damage over the interval  is2
is2
 (7.3)
(7.3)
where  relates to the final tally of the dead nodes. The coefficients are all non-negative and represent the relative importance of each corresponding term in the overall damage, e.g. if the worm gains the most by killing, and thereby completely disabling nodes,
relates to the final tally of the dead nodes. The coefficients are all non-negative and represent the relative importance of each corresponding term in the overall damage, e.g. if the worm gains the most by killing, and thereby completely disabling nodes,  . Let
. Let  .
.
The network seeks to choose its control vector  so as to minimize the above while the malware seeks to choose its control
so as to minimize the above while the malware seeks to choose its control  so as to maximize the above, subject to satisfying state constraints (7.2) and ensuring that
so as to maximize the above, subject to satisfying state constraints (7.2) and ensuring that
![]() (7.4a)
(7.4a)
![]() (7.4b)
(7.4b)
In Section 7.3, we model their interactions resulting from opposing objectives as a dynamic game. The formulation relies on the following result that allows us to ignore the state constraints without any loss of generality. The proof is similar to that of Lemma 6.1 in the previous chapter and is hence omitted for brevity.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.

