As illustrated in Chapter 7, "Sniffers and Electronic Eavesdropping," many network services (including but not limited to telnet, ftp, http, rsh, rlogin, and rexec) are vulnerable to electronic eavesdropping. This presents a major problem because even in a closed network environment, at bare minimum you must have secure means of moving files, setting permissions, running shell scripts, and so on.
To guard against attackers capturing your day-to-day network traffic, I highly recommend that you install Secure Shell (ssh). This chapter illustrates how to install and use the ssh server and client utilities.
Secure Shell is a secure login system and suitable replacement for telnet, rlogin, rsh, rcp, and rdist. As explained in the Secure Shell RFC:
Secure Shell supports several algorithms, including
BlowFish—A 64-bit encryption scheme developed by Bruce Schneier. Blowfish is often used for high-volume, high-speed encryption. (It's reportedly faster than both DES and IDEA.) To learn more, go to http://www.counterpane.com/blowfish.html.
Triple DES—DES is the Data Encryption Standard, a system from IBM, developed in 1974 and published in 1977. It's the U.S. Government standard for encrypting non- classified data. Learn more about DES at http://www.itl.nist.gov/div897/pubs/fip46-2.htm.
IDEA—The International Data Encryption Algorithm, a powerful block-cipher encryption algorithm that operates with a 128-bit key. IDEA encrypts data faster than Triple DES and is far more secure. Learn more about IDEA at http://www.nixu.fi/~pnr/netsec-lopulliset/1-0-practical-crypto.html#idea.
RSA—The Rivest-Shamir-Adelman algorithm, a widely used public-key/private-key cryptographic system. Learn more about RSA at http://www.rsa.com.
ssh's multi-algorithm support is more than simple window dressing. The authors added this support to create a more flexible and extensible product. ssh's architecture is such that the base protocol doesn't care which algorithm you use. Hence, if you later discover that one or more supported algorithms are fundamentally flawed, you can quickly switch without altering ssh's core protocol and functionality.
ssh also has several other advantages over its competitors. The most overt advantage is that ssh does not greatly alter your routine. In every respect, initiating a ssh session is as simple as (and similar to) initiating a telnet session. Both authentication and subsequent session encryption are transparent. Therefore, it has little or no learning curve. Get Secure Shell at http://www.ssh.fi.
Note
You can also obtain a precompiled ssh client and server at http://www.replay.com.
In this chapter, we'll focus on ssh from several angles:
Installing and configuring
sshProviding
sshservices in heterogeneous networksUsing
sshextended featuresTesting
ssh's ability to secure data
The ssh distribution consists of several programs. Table 10.1 describes each program's function.
Table 10.1. Programs in the ssh Suite
When you un-tar the ssh distribution, it will unpack to /ssh-1.2.27, which should contain the following files:
-rw-r--r-- 1 17275 operator 16879 May 12 04:18 COPYING -rw-r--r-- 1 17275 operator 60470 May 12 04:18 ChangeLog -rw-r--r-- 1 17275 operator 20528 May 12 04:18 INSTALL -rw-r--r-- 1 17275 operator 26467 May 12 04:19 Makefile.in -rw-r--r-- 1 17275 operator 9773 May 12 04:18 OVERVIEW -rw-r--r-- 1 17275 operator 22132 May 12 04:18 README -rw-r--r-- 1 17275 operator 3374 May 12 04:18 README.CIPHERS -rw-r--r-- 1 17275 operator 4512 May 12 04:18 README.DEATTACK -rw-r--r-- 1 17275 operator 1858 May 12 04:18 README.SECURERPC -rw-r--r-- 1 17275 operator 3914 May 12 04:18 README.SECURID -rw-r--r-- 1 17275 operator 2884 May 12 04:18 README.TIS -rw-r--r-- 1 17275 operator 87262 May 12 04:18 RFC -rw-r--r-- 1 17275 operator 75492 May 12 04:18 RFC.nroff -rw-r--r-- 1 17275 operator 2887 May 12 04:18 TODO -rw-r--r-- 1 17275 operator 8470 May 12 04:19 acconfig.h -rw-r--r-- 1 17275 operator 1919 May 12 04:19 arcfour.c -rw-r--r-- 1 17275 operator 1205 May 12 04:19 arcfour.h -rw-r--r-- 1 17275 operator 8648 May 12 04:19 auth-kerberos.c -rw-r--r-- 1 17275 operator 29046 May 12 04:19 auth-passwd.c -rw-r--r-- 1 17275 operator 3820 May 12 04:19 auth-rh-rsa.c -rw-r--r-- 1 17275 operator 14874 May 12 04:19 auth-rhosts.c -rw-r--r-- 1 17275 operator 20276 May 12 04:19 auth-rsa.c -rw-r--r-- 1 17275 operator 26760 May 12 04:19 authfd.c -rw-r--r-- 1 17275 operator 4640 May 12 04:19 authfd.h -rw-r--r-- 1 17275 operator 10438 May 12 04:19 authfile.c -rw-r--r-- 1 17275 operator 18769 May 12 04:19 blowfish.c -rw-r--r-- 1 17275 operator 994 May 12 04:19 blowfish.h -rw-r--r-- 1 17275 operator 4827 May 12 04:19 bufaux.c -rw-r--r-- 1 17275 operator 1870 May 12 04:19 bufaux.h -rw-r--r-- 1 17275 operator 3878 May 12 04:19 buffer.c -rw-r--r-- 1 17275 operator 2224 May 12 04:19 buffer.h -rw-r--r-- 1 17275 operator 10318 May 12 04:19 canohost.c -rw-r--r-- 1 17275 operator 9615 May 12 04:19 cipher.c -rw-r--r-- 1 17275 operator 4124 May 12 04:19 cipher.h -rw-r--r-- 1 17275 operator 32322 May 12 04:19 clientloop.c -rw-r--r-- 1 17275 operator 5218 May 12 04:19 compress.c -rw-r--r-- 1 17275 operator 1818 May 12 04:19 compress.h -rwxr-xr-x 1 17275 operator 17995 May 12 04:18 config.guess -rw-r--r-- 1 17275 operator 16320 May 12 04:20 config.h.in -rw-r--r-- 1 17275 operator 1538 May 12 04:18 config.sample -rwxr-xr-x 1 17275 operator 22876 May 12 04:18 config.sub -rwxr-xr-x 1 17275 operator 218850 May 12 04:20 configure -rw-r--r-- 1 17275 operator 36080 May 12 04:20 configure.in -rw-r--r-- 1 17275 operator 7542 May 12 04:19 crc32.c -rw-r--r-- 1 17275 operator 729 May 12 04:19 crc32.h -rw-r--r-- 1 17275 operator 21017 May 12 04:19 crypt.c -rw-r--r-- 1 17275 operator 3335 May 12 04:19 deattack.c -rw-r--r-- 1 17275 operator 393 May 12 04:19 deattack.h -rw-r--r-- 1 17275 operator 22976 May 12 04:19 des.c -rw-r--r-- 1 17275 operator 2496 May 12 04:19 des.h -rw-r--r-- 1 17275 operator 1891 May 12 04:19 emulate.c -rw-r--r-- 1 17275 operator 472 May 12 04:19 emulate.h -rw-r--r-- 1 17275 operator 2017 May 12 04:19 getput.h drwxr-xr-x 8 17275 operator 1024 May 12 04:19 gmp-2.0.2-ssh-2 -rw-r--r-- 1 17275 operator 17982 May 12 04:18 gnu-COPYING-GPL -rw-r--r-- 1 17275 operator 880 May 12 04:18 host_config.sample -rw-r--r-- 1 17275 operator 8736 May 12 04:19 hostfile.c -rw-r--r-- 1 17275 operator 6053 May 12 04:19 idea.c -rw-r--r-- 1 17275 operator 1672 May 12 04:19 idea.h -rw-r--r-- 1 17275 operator 10043 May 12 04:19 includes.h -rwxr-xr-x 1 17275 operator 4772 May 12 04:18 install-sh -rw-r--r-- 1 17275 operator 4642 May 12 04:18 libdes-ARTISTIC -rw-r--r-- 1 17275 operator 25510 May 12 04:18 libdes-COPYING -rw-r--r-- 1 17275 operator 2419 May 12 04:18 libdes-README -rw-r--r-- 1 17275 operator 4807 May 12 04:19 log-client.c -rw-r--r-- 1 17275 operator 7942 May 12 04:19 log-server.c -rw-r--r-- 1 17275 operator 16216 May 12 04:19 login.c -rw-r--r-- 1 17275 operator 12320 May 12 04:19 make-ssh-known- hosts.1.in -rwxr-xr-x 1 17275 operator 21221 May 12 04:18 make-ssh-known-hosts.pl -rw-r--r-- 1 17275 operator 4442 May 12 04:19 match.c -rw-r--r-- 1 17275 operator 7873 May 12 04:19 md5.c -rw-r--r-- 1 17275 operator 543 May 12 04:19 md5.h -rw-r--r-- 1 17275 operator 4071 May 12 04:19 memmove.c -rw-r--r-- 1 17275 operator 2755 May 12 04:19 mpaux.c -rw-r--r-- 1 17275 operator 1455 May 12 04:19 mpaux.h -rw-r--r-- 1 17275 operator 76542 May 12 04:19 newchannels.c -rw-r--r-- 1 17275 operator 26045 May 12 04:19 packet.c -rw-r--r-- 1 17275 operator 7239 May 12 04:19 packet.h -rw-r--r-- 1 17275 operator 17185 May 12 04:19 pty.c -rw-r--r-- 1 17275 operator 1727 May 12 04:19 pty.h -rw-r--r-- 1 17275 operator 2390 May 12 04:19 putenv.c -rw-r--r-- 1 17275 operator 13494 May 12 04:19 random.c -rw-r--r-- 1 17275 operator 13617 May 12 04:19 randoms.c -rw-r--r-- 1 17275 operator 3465 May 12 04:19 randoms.h -rw-r--r-- 1 17275 operator 23729 May 12 04:19 readconf.c -rw-r--r-- 1 17275 operator 5845 May 12 04:19 readconf.h -rw-r--r-- 1 17275 operator 8954 May 12 04:19 readpass.c -rw-r--r-- 1 17275 operator 84 May 12 04:19 remove.c -rw-r--r-- 1 17275 operator 969 May 12 04:19 rfc-pg.c -rw-r--r-- 1 17275 operator 21377 May 12 04:19 rsa.c -rw-r--r-- 1 17275 operator 3296 May 12 04:19 rsa.h -rw-r--r-- 1 17275 operator 7319 May 12 04:19 rsaglue.c -rw-r--r-- 1 17275 operator 4892 May 12 04:19 scp.1 -rw-r--r-- 1 17275 operator 52417 May 12 04:19 scp.c -rw-r--r-- 1 17275 operator 22461 May 12 04:19 servconf.c -rw-r--r-- 1 17275 operator 6432 May 12 04:19 servconf.h -rw-r--r-- 1 17275 operator 691 May 12 04:18 server_config.sample -rw-r--r-- 1 17275 operator 26334 May 12 04:19 serverloop.c -rw-r--r-- 1 17275 operator 3192 May 12 04:19 signals.c -rw-r--r-- 1 17275 operator 20180 May 12 04:19 snprintf.c -rw-r--r-- 1 17275 operator 1525 May 12 04:19 snprintf.h -rw-r--r-- 1 17275 operator 1668 May 12 04:19 socketpair.c -rw-r--r-- 1 17275 operator 4007 May 12 04:19 ssh-add.1 -rw-r--r-- 1 17275 operator 8658 May 12 04:19 ssh-add.c -rw-r--r-- 1 17275 operator 6265 May 12 04:19 ssh-agent.1 -rw-r--r-- 1 17275 operator 24600 May 12 04:19 ssh-agent.c -rw-r--r-- 1 17275 operator 15705 May 12 04:19 ssh-askpass.c -rw-r--r-- 1 17275 operator 5824 May 12 04:19 ssh-keygen.1 -rw-r--r-- 1 17275 operator 23105 May 12 04:19 ssh-keygen.c -rw-r--r-- 1 17275 operator 38632 May 12 04:19 ssh.1.in -rw-r--r-- 1 17275 operator 35544 May 12 04:19 ssh.c -rw-r--r-- 1 17275 operator 36564 May 12 04:19 ssh.h -rw-r--r-- 1 17275 operator 60224 May 12 04:19 sshconnect.c -rw-r--r-- 1 17275 operator 37107 May 12 04:19 sshd.8.in -rw-r--r-- 1 17275 operator 156444 May 12 04:19 sshd.c -rw-r--r-- 1 root root 0 Jun 17 21:56 sshdir.txt -rw-r--r-- 1 17275 operator 4754 May 12 04:19 sshsia.c -rw-r--r-- 1 17275 operator 653 May 12 04:19 sshsia.h -rw-r--r-- 1 17275 operator 870 May 12 04:19 strerror.c -rw-r--r-- 1 17275 operator 2356 May 12 04:19 tildexpand.c -rw-r--r-- 1 17275 operator 11621 May 12 04:19 ttymodes.c -rw-r--r-- 1 17275 operator 5384 May 12 04:19 ttymodes.h -rw-r--r-- 1 17275 operator 30968 May 12 04:19 userfile.c -rw-r--r-- 1 17275 operator 4949 May 12 04:19 userfile.h -rw-r--r-- 1 17275 operator 33 May 12 04:19 version.h -rw-r--r-- 1 17275 operator 1498 May 12 04:19 xmalloc.c -rw-r--r-- 1 17275 operator 1039 May 12 04:19 xmalloc.h drwxr-xr-x 2 17275 operator 1024 May 12 04:19 zlib-1.0.4
To make and install ssh, first run configure:
$ ./configure
This will take several minutes while configure identifies your system type and verifies that you have the necessary files to compile ssh. After configure returns you to a prompt (and assuming it doesn't report any critical errors), make ssh like this:
$ make
The make will also take several minutes—as many as 10, depending on your processor's speed. During that time, watch the output messages for errors.
When the make finishes, you should have these executables in your ssh directory:
scpsshssh-addssh-agentsshdssh-keygen
After verifying this (file * | grep utable), complete the installation:
$ make install
This will place your ssh utilities in /usr/local/ tree and make the ssh documentation.
If you're not in a terrific hurry to get ssh running, consider using the configure options specified in Table 10.2. If you set these at build time, you won't have to do so later in configuration files. (Also, some options available at build time are not available later, such as adding TCP Wrapper support.)
Table 10.2. configure Command-Line Options
| Option | Function |
|---|---|
--disable-client-port-forwardings | Disables all client-based port forwarding (except X11). |
--disable-client-x11-forwarding | Disables all client X11 forwarding. |
--disable-server-port-forwardings | Disables all server-based port forwarding except X11 forwarding. |
--disable-server-x11-forwarding | Disables server-based X11 forwarding. |
--disable-suid-ssh | Installs sshwithout the suidbit. |
--enable-kerberos-tgt-passing | Specifies that ssh should build with Kerberos ticket support. Kerberos is a network authentication protocol developed at MIT, often used to secure network sessions. Learn more at http://web.mit.edu/kerberos/www/. |
--prefix=PREFIX | Specifies an alternate directory tree for ssh's support files and binaries. The default is /usr/local. |
--srcdir=DIR | Specifies an alternate locationfor source files. |
--with-des | Specifies that ssh should build with single-pass DES support. |
--with-libwrap[=PATH] | Specifies that ssh should build with TCP Wrappers support. |
--with-none | Specifies that ssh should build with support for unencrypted sessions. (Not recommended.) |
--without-blowfish | Specifies that ssh should build without Blowfish support. Blowfish is a 64-bit encryption scheme developed by Bruce Schneier. It's often used for high-volume, high-speed encryption, and is faster than both DES and IDEA. |
--without-idea | Specifies that ssh should build without IDEA support. International Data Encryption Algorithm (IDEA) is a powerful block-cipher encryption algorithm that operates with a 128-bit key. IDEA encrypts data faster than DES and is far more secure. |
--without-rsh | Specifies that sshshould never use rsh. |
--with-path=PATH | Specifies what path a user is dropped into when he logs in with the ssh client. (By default, users are dropped into their home directory.) |
--with-securid[=PATH] | Specifies that ssh should build with support for the Security Dynamics SecurID card. |
--with-socks | Specifies that ssh should build with support for SOCKS firewalls. |
--with-socks4 | Specifies that ssh should build with support for SOCKS version 4 firewalls. |
--with-socks5 | Specifies that ssh should build with support for SOCKS version 5 firewalls. |
--with-tis[=DIR] | Specifies that ssh should build with support for Trusted Information Systems' authentication server. |
--with-x | Adds X support. |
After building ssh, your next step is to verify (or change, if necessary) options in your ssh configuration files. Those files are
/etc.sshd_config(Thesshserver configuration file)/etc/ssh_config(Thesshclient configuration file)
/etc/sshd_config is the ssh server configuration file. By default, it looks like this:
# This is ssh server systemwide configuration file. Port 22 ListenAddress 0.0.0.0 HostKey /etc/ssh_host_key RandomSeed /etc/ssh_random_seed ServerKeyBits 768 LoginGraceTime 600 KeyRegenerationInterval 3600 PermitRootLogin yes IgnoreRhosts no StrictModes yes QuietMode no X11Forwarding yes X11DisplayOffset 10 FascistLogging no PrintMotd yes KeepAlive yes SyslogFacility DAEMON RhostsAuthentication no RhostsRSAAuthentication yes RSAAuthentication yes PasswordAuthentication yes PermitEmptyPasswords yes UseLogin no # CheckMail no # PidFile /u/zappa/.ssh/pid # AllowHosts *.our.com friend.other.com # DenyHosts lowsecurity.theirs.com *.evil.org evil.org # Umask 022 # SilentDeny yes
Table 10.3 lists these options and others, and explains what they do.
Table 10.3. /etc/sshd_config Options
You generally need to make your options permanent, but sshd does allow you to set several options at the command line on startup. The next section covers sshd startup command-line options.
Use the command-line options listed in Table 10.4 to either set or override configuration options in /etc/sshd_config.
Table 10.4. sshd Startup Command-Line Options
/etc/sshd_config is the ssh client configuration file. By default, it looks like this:
# This is ssh client systemwide configuration file. This file provides # defaults for users, and the values can be changed in per-user configuration # files or on the command line. # Configuration data is parsed as follows: # 1. command line options # 2. user-specific file # 3. systemwide file # Any configuration value is only changed the first time it is set. # Thus, host-specific definitions should be at the beginning of the # configuration file, and defaults at the end. # Sitewide defaults for various options # Host * # ForwardAgent yes # ForwardX11 yes # RhostsAuthentication yes # RhostsRSAAuthentication yes # RSAAuthentication yes # TISAuthentication no # PasswordAuthentication yes # FallBackToRsh yes # UseRsh no # BatchMode no # StrictHostKeyChecking no # IdentityFile ~/.ssh/identity # Port 22 # Cipher idea # EscapeChar ~
Table 10.5 lists these options and others, and explains what they do.
Table 10.5. /etc/ssd_config Options
After you set your desired configuration options, start sshd (as root) like this:
$ sshd
Note
If /usr/local/sbin isn't in your path, either add it to the path before executing sshd or start sshd using its full path: /usr/local/sbin/sshd. Also, note that sshd runs as a background process by default. Therefore, you needn't explicitly send it to the background (sshd &).
Now your ssh server is running. Let's run through how to use the various client utilities.
To start the ssh client, issue the ssh command plus your username and the hostname or IP address you want, like this:
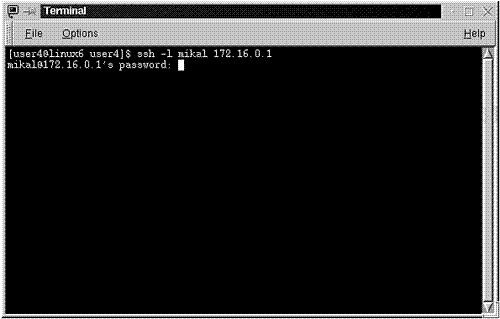
$ssh –l mikal 172.16.0.1
In response, the remote ssh server will request a password. Please see Figure 10.1.
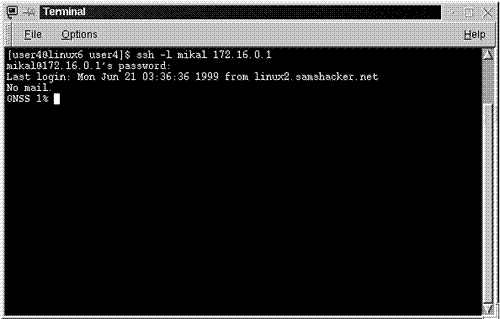
After you provide the correct password, ssh will log you in and drop you to a shell prompt. From then on, your session will behave precisely like a telnet session. Please see Figure 10.2.
Note
The first time you connect to a remote ssh server, you'll be confronted with the following message:
Host key not found from the list of known hosts. Are you sure you want to continue connecting (yes/no)?
Choose yes if you're connected to the correct host. From then on, you'll no longer receive this warning message. (Note that unless you add hosts to your known hosts configuration beforehand, you will receive this message when you connect to an unknown host for the very first time.)
The ssh client supports several command-line options, summarized in Table 10.6.
Table 10.6. ssh Client Command-Line Options
scp provides file copying across hosts using transparent ssh authentication and encryption. Whenever possible, use scp to move files.
Syntax is user@host1:filename user@host2:filename, like this:
$ hacker@linux1:scp.txt hacker@linux2:scp.txt
Table 10.7 summarizes scp command-line options.
Table 10.7. scp Command-Line Options
To strengthen your network's resistance to electronic eavesdropping, you should provide ssh services systemwide. To do so, you can get various commercial ssh versions for Microsoft Windows and Macintosh from DataFellows. But if you're on a tight budget or simply want to experiment, I recommend Tera Term Pro + TTSSH for Windows.
Tera Term Pro (written by T. Teranishi) is a popular telnet client for Microsoft Windows.
Application: Tera Term Pro
Required: None.
Config Files: terraterm.ini.
Security History: None.
Notes: Get Tera Term Pro at http://hp.vector.co.jp/authors/VA002416/teraterm.html.
Tera Term Pro does not come with native ssh support. However, Robert O'Callahan wrote an excellent ssh extension for it, available at http://www.zip.com.au/~roca/ttssh.html.
To end up with a fully ssh-compliant application, you must install both Tera Term Pro and TTSSH. Here's how:
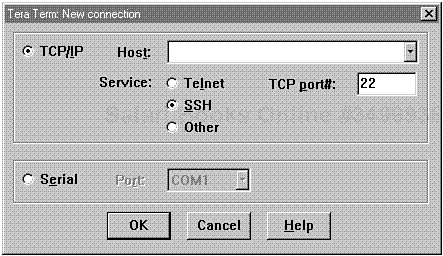
After downloading Tera Term Pro (ttermp23.zip), unzip its contents to a temp directory and run SETUP.EXE. The setup program will install Tera Term to C:PROGRAM FILESTTERMPRO and create a menu entry for it. Please see Figure 10.3.
Next, download TTSSH (ttssh14.zip) and unzip its contents to C:PROGRAM FILESTTERMPRO. This will add TTXSSH.DLL and TTSSH.EXE to the file list. Finally, instead of launching Tera Term Pro from the menu, make a shortcut to TTSSH.EXE and use this when you connect to a ssh server.
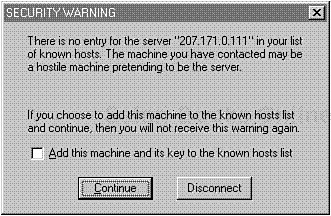
When you start TTSSH for the first time, it will prompt you for a server and ask whether you want standard telnet or ssh. Please see Figure 10.4.
Here, you enter a hostname or IP address. In response, TTSSH contacts the server, and when it detects that the new host is not in your hosts database, it prompts you to add an entry. Please see Figure 10.5.
And finally, TTSSH will ask you to enter your username and password. Please see Figure 10.6.
From then on, your session will appear and act just like a telnet session. You can run any program that you can normally run on the console. Please see Figure 10.7.
Your choices for Macintosh ssh clients are limited. Two very good (and free) tools are
Nifty Telnet, available at http://www.lysator.liu.se/~jonasw/freeware/niftyssh/.
Sassy Software's Better Telnet, available at http://www.cstone.net/~rbraun/mac/telnet/.
Unfortunately, due to patent issues, neither product can be legally used in the United States. (Of course, that may stop companies, but I know many individuals who pay no attention. Do so at your own risk.)
On the other hand, if you do scrupulously adhere to the letter of the law, your sole choice is the DataFellows F-Secure SSH for Mac, a commercial product available at http://www.datafellows.com/f-secure/ssh/mac/.
Note
If you have a JVM, you can also try MindTerm, a Java-based ssh client that can run standalone or within a Web browser. The package also offers tools to incorporate SSL into future applications. Check it out at http://www.mindbright.se/mindterm.
At the end of this chapter, I point to various documents that describe the ssh protocol in great detail. These will help you understand ssh's design and protocol. However, I wanted to offer some less academic examples of how ssh can protect your data.
First, let's look at how ssh prevents crackers from sniffing your interactive shell sessions. For this example, I monitored traffic between two intranet hosts:
On 172.16.0.2 (Windows NT), I installed SocketSpy, a Winsock sniffer and popular debugging tool. SocketSpy captures and displays Winsock traffic in real-time.
This configuration simulates an attacker on your intranet, armed with a sniffer (on Windows NT), who's trying to compromise your Linux server. To do so, he must capture usernames and passwords. Let's look at the difference between a standard telnet session and a session armored by ssh.
For the first pass, I initiated a telnet session from 172.16.0.2 to 172.16.0.1 as user mikal, with the password 8q2q4q8. What follows is the SocketSpy capture. (I've snipped irrelevant output for brevity's sake.)
First, SocketSpy caught the initial connection:
14:16:42:521 WSAStartup (wVersionRequested = 0x0101) returns (NO ERROR)
WSAData.wVersion =0x0101
.wHighVersion = 0x0202
.szDescription = WinSock 2.0
.szSystemStatus = Running (duh)
.iMaxSockets = 32767
.iMaxUdpDg = 65467
.VendorInfo = returns (NO ERROR)
14:16:42:521 htonl (0xAC100001) returns (0x010010AC)
14:16:42:521 inet_addr (172.16.0.1) returns (0x010010AC)
14:16:42:521 socket (af=PF_INET, type=SOCK_STREAM, protocol=6) returns (SOCKET=616)
14:16:42:521 setsockopt (SOCKET=616, SOL_SOCKET, SO_OOBINLINE=TRUE) returns (NO ERROR)
14:16:42:531 WSAAsyncSelect (SOCKET=616, hWnd=0x000D01AA, wMsg=0x0405, lEvent=0x00000010) returns (NO ERROR)
14:16:42:531 htons (0x0017) returns (0x1700)
14:16:42:531 ntohs (0x1700) returns (0x0017)
14:16:42:531 connect (SOCKET=616, SOCKADDR.length=16,
.family=AF_INET
.port=23
.address=172.16.0.1) returns (WSAEWOULDBLOCK)Next, SocketSpy caught 172.16.0.1 providing a login prompt:
14:16:42:722 recv (SOCKET=616, buf=0x0043F082, len=1022, flags=0x0000) returns (23 bytes) 0000: 0D 0A 0D 0A 49 52 49 58 20 28 47 4E 53 53 29 0D ….IRIX.(GNSS). 0010: 0A 0D 00 0D …. 14:16:42:722 recv (SOCKET=616, buf=0x0043F097, len=1001, flags=0x0000) returns (WSAEWOULDBLOCK) 14:16:42:722 WSAGetLastError () returns (WSAEWOULDBLOCK) 14:16:42:722 send (SOCKET=616, buf=0x0043F488, len=3, flags=0x0000) returns (3 bytes) 0000: FF FC 21 ..! 14:16:42:722 recv (SOCKET=616, buf=0x0043F084, len=1020, flags=0x0000) returns (7 bytes) 0000: 6C 6F 67 69 6E 3A 20 login:.
And finally, it caught the username and password on login:
14:16:44:424 recv (SOCKET=616, buf=0x0043F080, len=1024, flags=0x0000) returns (1 bytes) 0000: 6D m 14:16:44:594 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 69 i 14:16:44:764 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 6B k 14:16:44:925 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 61 a 14:16:44:985 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 6C l 14:16:46:116 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 39 8 14:16:46:507 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 77 q 14:16:46:747 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 31 2 14:16:46:928 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 77 q 14:16:47:148 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 32 4 14:16:47:278 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 77 q 14:16:47:558 send (SOCKET=616, buf=0x0043F488, len=1, flags=0x0000) returns (1 bytes) 0000: 35 8
Note
I initiated the attack from Windows NT for variety's sake. In practice, attackers could be listening from any machine (using any operating system) on the instant network segment.
Now let's look at a session between the same two machines, this time running Secure Shell.
SocketSpy captures the initial connection:
14:37:08:953 WSAStartup (wVersionRequested = 0x0101) returns (NO ERROR)
WSAData.wVersion =0x0101
.wHighVersion = 0x0202
.szDescription = WinSock 2.0
.szSystemStatus = Running (duh)
.iMaxSockets = 32767
.iMaxUdpDg = 65467
.VendorInfo = returns (NO ERROR)
14:37:08:963 ntohs (0x1600) returns (0x0016)
14:37:08:963 connect (SOCKET=616, SOCKADDR.length=16,
.family=AF_INET
.port=22
.address=172.16.0.1)
returns (WSAEWOULDBLOCK)However, as you can see here, SocketSpy gleaned only senseless data from the login. The traffic was encrypted:
14:37:09:064 recv (SOCKET=616, buf=0x02230040, len=60000, flags=0x0000) returns (15 bytes) 0000: 53 53 48 2D 31 2E 35 2D 31 2E 32 2E 32 37 0A SSH-1.5-1.2.27. 14:37:09:064 send (SOCKET=616, buf=0x0012FABC, len=18, flags=0x0000) returns (18 bytes) 0000: 53 53 48 2D 31 2E 35 2D 54 54 53 53 48 2D 31 2E SSH-1.5-TTSSH-1. 0010: 34 0A 4. 14:37:09:164 recv (SOCKET=616, buf=0x02230040, len=60000, flags=0x0000) returns (276 bytes) 0000: 00 00 01 0B 00 00 00 00 00 02 11 A8 F8 B8 A8 B3 0010: 0E 1E 00 00 …. 14:37:09:164 send (SOCKET=616, buf=0x01660600, len=156, flags=0x0000) returns (156 bytes) 0000: 00 00 00 94 40 2C CD 49 03 01 11 A8 F8 B8 A8 B3 ….@,.I…….. 0010: 0E 1E 04 00 ….
ssh can armor your shell sessions at both ends, preventing attackers on either side from capturing login sequences. But that's not all. Although most folks use ssh strictly for secure telnet-like sessions, it offers other amenities. For example:
With Holger Trapp's extensions,
sshcan provide secure RPC sessions, useful in armoring NIS. To learn more, read Using SSH to Increase the Security of ONC RPC Services, located at ftp://ftp.tu-chemnitz.de/pub/Local/informatik/sec_rpc/README.RPC.You can run encrypted PPP sessions atop standard
sshconnections, effectively establishing tunneled PPP between two networks on the Internet. This offers quick-and-dirty VPN functionality. To see an early implementation of this, go to http://sites.inka.de/sites/bigred/sw/ssh-ppp-new.txt.sshoffers extensive TCP forwarding options, so you can use it to communicate with outside entities from behind a firewall.
Because ssh offers these options, you can use it to armor many different session types. For example, suppose you offer X services on your heterogeneous intranet to Mac or Windows users. You might choose a tool like X-Win32 from Starnet Communications.
Note
X-Win32 is a PC-based X server that provides seamless X connectivity between Windows and UNIX/Linux. Check it out at http://www.starnet.com/.
X sessions are often encrypted with DES. However, you can pile on additional armor and specify other algorithms using ssh's forwarding functions.
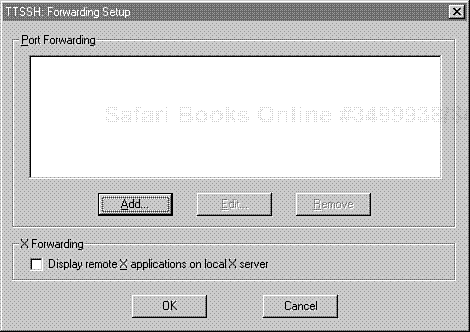
If you're using Tera Term Pro/TTSSH as your ssh client on the PC end, specify your X forwarding options by choosing Setup, Forwarding from the main menu. This will display a forwarding dialog. Please see Figure 10.8.
Here, choose Add to specify a new port forwarding entry. In response, Tera Term Pro/TTSSH will display the Port Forwarding configuration window, where you can specify your options. Please see Figure 10.9.
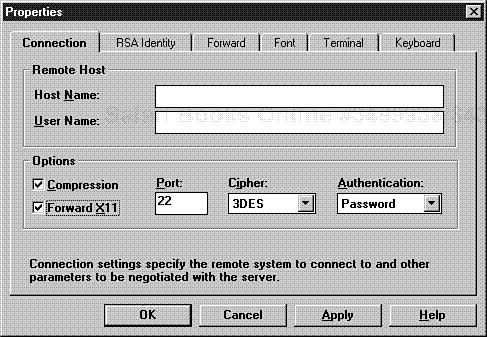
Alternately, if you're using F-Secure SSH (commercial version), go to the main menu and click Edit, Properties. F Secure SHH will display the Properties window with the Connection tag active. Here you can set your forwarding options. Please see Figure 10.10.
But ssh's forwarding and tunneling capabilities aren't limited to X. Theoretically, you can use ssh to forward and tunnel any TCP-based service, even mail. For a good example of this, please see How to Securely Send and Retrieve Your CCS Mail via SSH at the Northeastern University's College of Computer Science, located at http://www.ccs.neu.edu/groups/systems/howto/howto-sshtunnel.html.
Does ssh have a significant security history? Yes. Early versions suffered from buffer overflows, and some allowed users with expired accounts to initiate a session. However, these problems have been relatively minor and were eliminated in recent releases.
Caution
Make sure that you're using the latest ssh release. Crackers are familiar with security weaknesses in earlier versions, and such weaknesses have been incorporated into several popular scanner regimens. For example, Saint (covered in Chapter 8, "Scanners") scans for ssh weaknesses. The most recently affected distribution was on Debian. In December 1998, independent researchers noted a buffer overflow. In response, Debian quickly released patches. Go here for more information: http://www.debian.org/Lists-Archives/debian-security-announce-9812/msg00002.html.
The following documents present various views on and approaches to using Secure Shell.
Getting Started with SSH, Kimmo Suominen. In this document, Suominen demonstrates various ways to use SSH, including to protect X sessions (http://www.tac.nyc.ny.us/~kim/ssh/).
Kerberos/DCE, the Secure Shell, and Practical Internet Security, Wayne Schroeder, San Diego Supercomputer Center. In this document, Schroeder explores Secure Shell's practical advantages for wide-scale security in environments that do not have a full Kerberos/DCE installation (http://www.sdsc.edu/~schroede/ssh_cug.html).
SSH Connection Protocol, T. Ylonen, T. Kivinen, M. Saarinen, T. Rinne, and S. Lehtinen. This is Internet
draft-ietf-secsh-connect-06.txt, the official specification for the SS Connection Protocol as of June 1999 (http://www.ietf.org/internet-drafts/draft-ietf-secsh-connect-06.txt).SSH Protocol Architecture, T. Ylonen, T. Kivinen, M. Saarinen, T. Rinne, and S. Lehtinen. This is Internet
draft-ietf-secsh-architecture-04.txt, the official specification for the SSH Protocol Architecture as of June 1999 (http://www.ietf.org/internet-drafts/draft-ietf-secsh-architecture-04.txt).The Secure Shell, Peter Simons and Andreas Reichpietsch. This document offers a detailed technical overview of Secure Shell, including the algorithms used and the process of secure data exchange(http://www.cys.de/simons/publications/ssh/).
The Ssh (Secure Shell) FAQ, Thomas König (http://www.uni-karlsruhe.de/~ig25/ssh-faq/).
Updates to SSH protocol, Tatu Ylonen. This document describes the SSH protocol in exceptional detail http://lists.w3.org/Archives/Public/ietf-tls/msg00555.html).
Finally, note that ssh can only secure sessions between the server and a ssh client. Therefore, you cannot use ssh to secure any TCP-based service (like HTTP) between your server and clients that are not ssh-enabled. For this, you need something that is generically recognized by popular Web browsers, such as Secure Sockets Layer. To learn how, please see Chapter 15, "Secure Protocols."
Because electronic eavesdropping tools (hardware and software) are well known and continue to proliferate, Secure Shell is a necessity. Unfortunately, you cannot control how foreign networks handle their authentication, but within your own, you can use Secure Shell to establish baseline security of data in transit.