Most contemporary security books focus on network security, which is admittedly a hot issue. However, a point often overlooked is that servers are more vulnerable to physical attack than remote attack. Some frequent culprits include:
In fact, not only is your server more likely to be hacked with an ax than a spoofing utility, but when this tragedy occurs, the after-effects can be far more devastating. If your system is remotely hacked, you can always reboot, reinstall, or reconfigure, but when your system is physically damaged or compromised, you have a problem.
For these reasons, physical security should be your first aim. Although many physical security measures seem obvious (because they consist chiefly of exercising common sense), users routinely fail to implement them.
In recognition of these facts, it's time for a brief refresher course in basic physical computer security. Let's work from the outside in:
Server location and physical access
Network topologies
BIOS and console passwords
Biometrics access controls
Network hardware
General hardware security
The two most important points are where your server is located and who has physical access to it. Security specialists have long held that if malicious users have physical access, security controls are useless. Is this true? Absolutely. With rare exceptions, nearly all computer systems are vulnerable to onsite attack.
Of course, attack in this context can mean many things. For example, suppose you gave a malicious user 10 seconds alone with your servers. Could they do any substantial damage in that timeframe? You bet. They could perform primitive denial-of-service attacks by disconnecting wires, unplugging network hardware, or rebooting your servers.
Note
Denial of service is a condition that results when a user maliciously renders a server inoperable, thereby denying computer service to legitimate users. Learn more in Chapter 17, "Denial-of-Service Attacks."
But these acts are rare in office settings. Instead, your main concern should be authorized local users, folks who have at least limited authorization to access your system. It's been estimated that insiders initiate 80% of all intrusions. The reason is that insiders are privy to information that remote attackers often cannot obtain.
But that's not the only advantage insiders have. Trust is another. In many companies, trusted employees roam around freely without fear of being questioned. After all, they're supposed to be onsite, and no one thinks twice about their presence unless they enter a restricted area. So, how do you protect your system from the enemy within?
Government agencies and Internet service providers have ample experience in this regard, and it's worth following their lead. If your system is company-based, you should make provisions for a network operations center (NOC).
An NOC is a restricted area that houses your servers. They are typically bolted down, fastened to racks, or otherwise secured, along with essential network hardware.
Ideally, your NOC should be a separate office to which few people have access. Those who are authorized should be given keys. (One good method is to use card keys that restrict even authorized users to certain times of day.) Finally, it's worth keeping a written access log and mandating that even authorized personnel must sign in and out.
Also, ensure that your NOC or computer room adheres to these requirements:
It should be located inside other office space and away from the public, preferably not on the ground floor.
It and the passageways leading to it should be completely opaque: no glass doors.
Doors leading to it should have metal shields that extend from the lock casing to the door's surrounding frame. This prevents intruders from tampering with the lock's sliding bolt.
If you employ surveillance (closed circuit TV or time-elapsed stills), run your signal from the camera to a remote VCR. This ensures that if thieves swipe your equipment and take the videotape, you'll still have the goods.
Keep all storage media in a safe or, better yet, at an entirely different location.
Additionally, you'll need strict written policies that forbid average employees from entering the NOC. You should incorporate these policies into your employment contracts. This way, all employees are made aware of your policies and know that if they violate them, they may face dismissal.
As for more specific policies, I recommend these documents:
A Survey of Selected Computer Policies from Institutions of Higher Education at Brown University. This contains nicely compiled summaries of security policies from various institutions. It's at http://www.brown.edu/Research/Unix_Admin/cuisp/.
CAF "Academic Computing Policy Statements" Archive at the Electronic Freedom Foundation. This is an interesting archive. The policies of many schools are examined and subjected to critique. Naturally, because EFF is a privacy-lobbying group, its critique often demonstrates holes, inconsistencies, or ambiguities in policies. This is probably more useful for determining what not to do. It's at http://www.eff.org/pub/CAF/policies/.
Site Security Handbook, Request for Comments 2196 / FYI 8. This updated version (September 1997) covers many important points. Find it at ftp://nic.merit.edu/documents/fyi/fyi8.txt .
The San Francisco State University Computing and Communications Services Security Guide. A good example policy, located at http://www.sfsu.edu/~helpdesk/docs/rules/security.htm.
Network topology consists of your network's layout, its various components, and how they're linked together. Because network topology determines how hardware devices are linked and how information flows across those links, it has definite security implications. This section will briefly focus on those implications and how you can minimize risk.
Many network topologies exist, but three in particular are common to Local Area Networks (LANs):
Bus
Ring
Star
When choosing one of these topologies, you'll need to consider three chief risks:
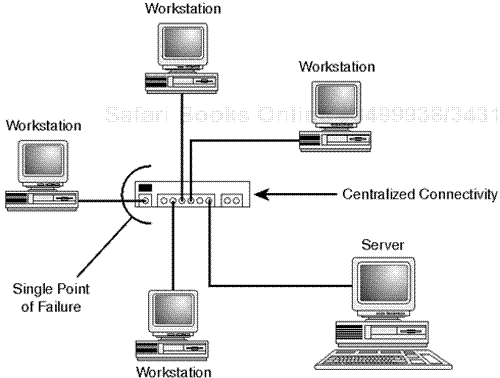
The single point of failure—. This is a point (a server, hub, wire, or router) to which one or more network devices are connected. When this connection point fails, one or more workstations lose network connectivity. Every network has at least one point of failure. In mission-critical networks, your aim is to minimize the effects of an outage—damage control, in other words. As you'll see, different topologies pose different limitations in this regard.
Susceptibility to electronic eavesdropping—. This is the practice of surreptitiously capturing network traffic. All topologies are susceptible to electronic eavesdropping to some degree. However, some topologies are more susceptible than others. (Learn more about electronic eavesdropping in Chapter 7, "Sniffers and Electronic Eavesdropping").
Fault-tolerance—. In this context, this is your network's ability to take a licking and keep on ticking. If one, two, or five workstations fail, will remaining workstations continue to operate? If your network is fault-tolerant, the answer is yes.
In the bus topology (also called linear bus topology), a single data feed—your network backbone—supports all network devices. Please examine Figure 2.1.
Typical bus networks are supported by an uninterrupted coax-based backbone. This offers two single points of failure: the server and the backbone. If either fails, all workstations can lose network connectivity.
Is such a network fault-tolerant? That depends on whether each workstation has a full network operating system installation and the necessary applications to perform mission-critical tasks. If not, the network is not fault-tolerant.
In past years, such networks were probably not fault-tolerant. The configuration depicted in Figure 2.1 was common for Novell NetWare networks of yore. The typical configuration was a file server accompanied by diskless clients or workstations. When these workstations lost network connectivity, work came to a halt.
Note
Diskless clients are machines that have the bare minimum of software, usually a boot diskette or firmware that can call a boot server and receive boot commands. Such machines have no local applications and can even operate without a hard disk drive.
On the other hand, if all workstations in Figure 2.1 had a full Linux install, some work could continue even if the backbone went down.
Either way, bus topology is not your best choice, for several reasons. First, if you're stringing a Linux network, you're probably aiming to use client-server technology (on an intranet, perhaps). Bus networks perform poorly in these environments. Typical bus backbones handle one transmission at a time and sport a high collision rate. This is unsuitable because client-server transactions mandate succeeding or constant connections between hosts. Heavy Web traffic on a bus network, for example, could result in degraded performance.
Also, because bus network traffic is confined to a single wire, it's difficult to troubleshoot for traffic jams, packet collision, and dropped packets. This is exacerbated by a lack of the centralized control you can achieve using intelligent hubs or switches.
Finally, bus topology is highly susceptible to eavesdropping. Barring the use of additional controls, any workstation in Figure 2.1 could intercept transmissions intended for any of its counterparts.
So, if all this is true, why use bus topology at all? Here's why: It's quick, cheap, and reasonably effective—a great solution for a closed network in your home.
In ring topology, again, there's a single network feed to which all machines are connected. Please see Figure 2.2.
Much like bus topology, ring topology sports at least two single points of failure: the server and the wire. If either goes down, all workstations can lose network connectivity.
In this scenario, however, other failures can also disrupt the network. Whereas bus topology doesn't generally impose any dangers if workstations go down, ring topology can. In ring topology, machines function as repeaters. A message sent from the server to Workstation C, for example, might well be passed to Workstation A, Workstation B, and finally Workstation C. Hence, if the server and Workstation B go down, Workstations A and C may be unable to transmit messages, and vice versa. If Workstations A and C go down, the server and Workstation B may be cut off from each other.
Note
Exceptions to this include Fiber Distributed-Data Interface (FDDI) networks.
As you've probably surmised, ring topology offers several avenues for attackers. First, they can easily implement denial-of-service attacks by knocking out selected workstations. More importantly, because messages are passed in the same direction and may traverse multiple workstations en route, ring topology is quite susceptible to electronic eavesdropping.
The star topology's overt distinction from bus and ring topology is its centralization. In star topology, all workstations on the current segment connect to a single hardware device, typically a switch or hub. Please see Figure 2.3.
This can enable individual management and troubleshooting of each workstation's feed. Also, unlike ring networks, star networks can survive multi-station failure. Even if three workstations fail, the fourth will continue to operate unhindered. And if workstations are properly outfitted, such a configuration can be quite fault-tolerant.
In addition, star networks offer major security advantages over their bus and ring counterparts. Using advanced network hardware, you can perform refined segmentation (breaking your network into islands) and shield each workstation's feed from eavesdropping with encryption.
Of course, star networks have disadvantages, too. One is that their centralization offers a critical single point of failure. If attackers knock out your network hardware, they can down entire segments. Additionally, star network performance can slow down under heavy loads, especially if you're using run-of-the-mill hubs instead of switches that segregate bandwidth. This is because every transmission must pass through a central station.
Before making a topology choice, you'll need to consider many factors, including
Whether each workstation will have local software.
Other network operating systems you may be using.
Protocols your network will run.
Bandwidth and distance requirements.
I recommend star topology and, if you can afford it, some intelligent network hardware. Either way, here are some tips to minimize risk:
Choose a topology or network implementation that offers centralized connection management and troubleshooting.
If your network is large, break it into segments. This allows better management and better security by limiting how far a security compromise can go.
Design your network with fault-tolerance and failure in mind. When you're setting it up, try to limit it to the least number of single points of failure.
Isolate your hardware from users by keeping it out of common areas.
Isolate your wiring. If possible, run your main network cables through the walls and provide connections via faceplates/patch cables at each desk. This will help prevent covert physical wiretaps. (Many companies run their wiring in overhead space above the ceiling. Try to avoid this. In buildings with multiple offices, all tenants on the same floor share this space. Someone in an adjacent office can easily hop on a ladder, push up the ceiling tiles, and snag your wire.)
If you can afford it, use encryption-enabled hardware and software LAN-wide.
Network hardware security is another vital issue. Mistakes made at this level can lead to disaster. To understand why, please examine Figure 2.4.
As depicted in Figure 2.4, your router is a critical attack point, a gateway through which your users communicate with the outside world, and vice versa. If attackers successfully bring down your routers, switches, or hubs, they can deny service to many people.
Note
Compare this to operating system-specific network attacks. Suppose your network was composed of three Linux machines, three Windows machines, and three Macs. Suppose further that some attackers instituted a denial-of-service attack that targeted Windows systems. Their attack, if successful, would take out three workstations but leave the remaining six workstations unaffected. In contrast, when attackers down your router (a single point of failure), your entire network is effectively incapacitated.
You can avoid a compromise of network hardware by employing some common sense security practices. In most cases, these steps will be sufficient because hardware vulnerabilities in network hardware are uncommon when compared to software vulnerabilities.
More often, network hardware compromise results from operator error. Many users fail to enable encryption or to set administrative, maintenance, and user passwords. This leaves the hardware's out-of-the-box configuration intact and opens your system to attack.
Table 2.1 enumerates possible avenues of attack that are attributable to default configuration or hardware vulnerability.
Table 2.1. Common Network Hardware Password Issues
| Hardware | Issue |
|---|---|
| 3Com Switches | The maintenance login (debug) and password (synnet) for various 3Com switches, including CoreBuilder and SuperStack II, are widely known. Change them, or contact 3Com at http://www.3com.com for more information. |
| Ericsson Tigris | Some Ericsson Tigris routers allow remote users to send valid commands without authenticating them. This has been fixed in versions 11.1.23.3 and later. If you have an earlier version, upgrade it, or visit ACC at http://www.acc.com for more information. |
| Ascend Pipeline/MAX | Ascend Pipeline and MAX default passwords are widely known. For instructions on how to change them, go to http://www.ascend.com/2694.html. Bay Networks Some Bay Networks products have an account without a password. This information has been widely distributed. Check yours now; the account is User. If this puts you into interactive mode, set a password for the account. |
| BreezeCom Adapters | Some BreezeCom station adapters have hard-coded passwords that cannot be altered. These passwords have been widely distributed. Since the passwords are hard-coded, there's nothing you can do. |
| Catalyst 1800 | The Cisco Catalyst 1800 default password is widely known. Change it. |
| Cisco IOS 9.1 | Hardware running IOS 9.1 may leak strings, including passwords, from recent transmissions. Upgrade to the newest version. |
| Compaq Netelligent | The default password for the Compaq Netelligent 8500 (superuser) is widely known. Change it. |
| DCM BRASX/I01 | The default password for the Data Comm for Business BRASX/I01 is widely known. Change it. |
| Develcon Orbitor | The Orbitor bridge and router product default passwords (password and BRIDGE) are widely known. Change them. |
| Digital ATMswitch | The default usernames and passwords for the ATMswitch 900F are widely known. If you didn't change them, do so now. |
| FlowPoint 2000 | Some FlowPoint 2000 DSL routers have a default password of admin. Be sure to change yours. |
| Motorola CableRouter | Motorola CableRouter products are vulnerable to direct attacks via default login and password. Attackers telnet to port 1024, login as cablecom, and provide router as a password. Change these values and upgrade if necessary. |
| SmartSwitch | The default password for the SmartSwitch Backup SBU6C and SBU14C (by Cabletron) is well known. Change it. |
| Shiva VPN Gateway | Default passwords for the Shiva VPN Gateway (shiva or isolation) are widely known. Change them. |
| WebRamp M3 | The WebRamp M3 router allows remote connections via Telnet even after you disable this functionality. Be certain to change your administrative password immediately. |
Also, be sure to isolate your network hardware from local users who aren't trusted. Many routers, bridges, and switches provide the means to perform onsite password recovery. Unsupervised users with physical access can undertake these procedures.
Note
Password recovery techniques vary. In some cases, attackers can perform recovery on the spot. In other cases, they must first string a dumb terminal or PC to the router. From there, they can force a reboot using flash memory and reinitialize the unit. As a result, the router disregards stored values, and attackers can either view or change the password. Attackers need ample time alone to do this, which makes such an attack difficult to execute. However, recovery procedures do exist, so you should only grant trusted personnel physical access to your network hardware. (Learn more about these and other attacks in Chapter 5, "Password Attacks.")
Finally, here are several steps to take whenever you're installing new or used network hardware:
Set administrative, maintenance, and user passwords to prevent attackers from gaining access via defaults. Also, ensure that these passwords differ from other administrative passwords on your network.
Most routers (and some switches) support encryption but don't employ it by default. Ensure that encryption is enabled.
If you don't need administrative remote control (Telnet access), disable it.
If your network hardware has sensitive ports, filter and block access to them.
If your network hardware provides options for either time-outs or session verification, use them. These will prevent attackers from hijacking or spoofing sessions.
When you're securing workstations, your main concerns are physical access and theft. Typical preventative tools you'll employ include the following:
Most architectures (X86, PPC, Sparc, and so on) support either BIOS/PROM passwords, console passwords, or both. Hardware manufacturers provide these password systems as an extra security layer—an obstacle to discourage casual users from snooping.
BIOS or PROM passwords prevent malicious users from accessing system setup, while console passwords more frequently protect workstation single-user modes. Either way, these password systems are at least marginally effective and you should use them whenever possible.
However, do be sure to set your setup or single-user password. If you don't, you may end up regretting it. Today, default BIOS setup keys and passwords for nearly every manufacturer are well known. Table 2.2 lists a few.
Table 2.2. Well-Known BIOS Entry Keys and Passwords
Also, be sure to use a password that's different from other passwords you've used on the network. This ensures that if your BIOS or console password is later cracked, it won't expose applications or other machines to attack.
Ideally, though, you shouldn't rely on BIOS and console passwords as a serious line of defense because they have inherent flaws. One flaw is that attackers can wipe out BIOS passwords simply by shorting out the CMOS battery. In other cases, they don't even need to do that because the motherboard manufacturer has included a jumper which, when properly set, will wipe the CMOS clean.
Furthermore, attackers are frequently armed with BIOS blasters (programs that wipe BIOS settings clean) or BIOS password-capture utilities. These tools are widely available. Table 2.3 lists a few such tools.
Table 2.3. BIOS Blaster and Capture Utilities
| Tool | Description |
|---|---|
!BIOS by Bluefish | The !BIOS package is an all-purpose BIOS attack suite featuring blasters, capture utilities, and decryption tools. !BIOS will successfully defeat most modern BIOS password protection. Get it at http://home1.swipnet.se/~w-12702/11A/FILES/!BIOS310.ZIP. |
AMIDECOD | This utility will decode BIOS passwords on American Megatrends systems. Get it at http://www.swateam.org/noleech.pl?amidecode.zip. |
| AMI Password Viewer | This utility from KORT reads, decrypts, and displays AMI BIOS passwords. Get it at http://www.rat.pp.se/hotel/panik/archive/skw-ami.zip. |
AW.COM | This utility by Falcon n Alex cracks Award BIOS passwords. Get it at http://www.lls.se/~oscar/files/pwd/aw.zip. |
A more Orwellian approach to physical hardware security is to use biometric access devices. These tools authenticate users based on their biological characteristics, including
Body odor
Facial structure
Fingerprints
Retinal or iris patterns
Vein layout
Voice
Let's briefly look at the history of biometric identification.
Biometric identification is a relatively new field, although its roots reach back to ancient Egypt, when Pharaohs signed certain decrees with a thumbprint.
The first substantial biometric inroads were made in the 19th century. In 1893, Sir Francis Galton demonstrated that no two fingerprints were alike, even in cases of identical twins. Not long after, Sir Edward Henry devised the Henry System, which is still used today.
Henry's system classified ridges on fingertips into eight categories: the accidental, the central pocket loop, the double loop, the plain arch, the plain whorl, the radial loop, the tented arch, and the ulnar loop. By analyzing these patterns and establishing from eight to sixteen points of comparison between samples, police can positively identify criminals.
Note
Fingerprinting is regarded as an infallible science. And in most instances it is, providing that the target has fingerprints. Not everyone does. Several rare skin diseases can distort fingerprints or destroy them altogether. The best known is Epidermolysis Bullosa, an inherited condition that typically attacks children while they're still in the womb. Epidermolysis Bullosa victims may have partial fingerprints or none at all.
Until the mid-20th century, fingerprinting technology was surprisingly primitive. Obtaining prints from criminals involved direct, physical impressions from hand to ink. Armed with these prints, which were stored on paper cards, criminologists conducted visual comparisons against samples taken at the crime scene.
Over time, this system was superseded by more advanced technology. Today, the FBI stores some 200 million fingerprints (29 million of which are unique, and the remainder are from repeat offenders) using the Fingerprint Image Compression Standard. This standard provides space-effective digital storage of fingerprints that would otherwise occupy thousands of terabytes. And, as you might expect, computers do most of the matching.
Digital fingerprinting technology is now so inexpensive that some firms are incorporating it into PCs. Compaq, for example, is piloting a fingerprint ID system on PCs sold in Japan, with a price tag of about $135.00. The system uses a camera to capture an image of your fingerprint, which is later used to authenticate you during logon.
But fingerprints are just the beginning. In recent years, scientists have identified several unique biological characteristics that can be used for identification. Of these, distinctive retinal patterns have attracted the most substantial interest. Please see Figure 2.5.
The retina, which handles peripheral vision, is an infinitesimally thin tissue that converts light into electrical signals. These signals are then transmitted to the brain. The retina is composed of several layers, and retinal scanners use two layers in particular. The outer layer contains reflective, photoreceptive structures called cones and rods that process light. Beneath these, in the choroid layer, the retina houses complex blood vessel systems.
Identification specialists report that retinal scans are exceptionally reliable and in many ways superior to fingerprints. For example, retinal patterns offer many more points for matching than fingerprints do—anywhere from 700 to 4,200. For this reason, retinal scanners are classed as high biometrics, or biometric systems with an exceedingly high degree of accuracy.
However, retinal scans are sometimes insufficient, and they may not work at all if users are blind, partially blind, or have cataracts. Additionally, retinal scanners have a disproportionately high false negative or rejection rate. That is, although there's little chance of a retinal scanner authenticating an unauthorized user, authorized users are often rejected on their first pass.
Still more recent technology has focused on voice patterns. However, these systems can be unreliable. For example, there have been instances where voice recognition failed because the user had bronchitis, a cold, laryngitis, and so forth.
There are pros and cons to biometric access control. On the one hand (no pun intended), such controls offer a high degree of assurance, especially systems that use fingerprint data. However, there are practical obstacles to instituting a wholly biometric approach.
First, when you expand biometric controls beyond the scope of your own workstation, you can face privacy issues. For example, suppose that you run a small ISP and you decide to institute biometric access controls systemwide. Even if your employees sign a release, they can later sue for invasion of privacy—and perhaps prevail.
In retinal scans, your eye is bombarded with infrared light. The photoreceptive structures in the outer layer respond by reflecting this light, and the resulting reflection produces an image of your retina's blood vessel patterns.
Note
Privacy concerns with biometric access control systems are very real, although they arise from arcane sources. It's been argued, for example, that retinal scans contain personal medical information. Signs of drug abuse, hereditary disease, and even AIDS can be detected in retinal patterns. Hence, maintaining a retinal pattern database could conceivably leave you open to litigation. Similarly, fingerprints can reveal criminal convictions, which also constitute sensitive data.
Beyond legal issues, biometric access control systems have social implications. Your employees may resent such controls and perceive them as a privacy violation, whether they say so or not. This could foster a hostile work environment, even if not overtly.
Perhaps the strangest drawback of biometric access control systems lies in their effectiveness. Such systems perform at least rudimentary logging, and therefore they create an incontrovertible record of exactly who performed which duties and when they were performed. This deprives your personnel of plausible deniability. In certain lawsuits, records from your biometric access control system could be used against you.
Caution
I hope that you're not using your computers for illegal activity. But if you are, you should probably pass on biometric access controls or at least disable their logging facilities. Nothing spoils an otherwise clean hack like incontrovertible logs.
Finally, biometric access controls are unsuitable in environments that extend beyond your local network. For example, you can't force remote users to use biometric devices, even if you'd like to.
These problems aside, biometric access controls are excellent when used in-house, in close quarters, among trusted co-workers. I'd certainly recommend employing them in your inner office on machines used to control and administrate your network.
Unfortunately, there aren't many Linux-compatible biometric access control tools. Table 2.4 lists a few of them, what they do, and where to learn more about them.
Table 2.4. Linux-Compatible Biometric Access Tools
| Product or Service | Description |
|---|---|
| Biomouse | This is a mouse from American Biometric that reads your fingerprints. It works well with Linux 2.0 or greater. Check it out at http://www.biomouse.com/. |
| IrisScan | This is a networked biometric authentication system that supports 256 workstations per LAN segment. Users are authenticated by random iris patterns, which are purportedly even more accurate and reliable than retinal scans. And although IrisScan requires NT on the server, it can be used to secure heterogeneous environments. Check out IrisScan at http://www.iriscan.com. |
| SecureStart/ISA | This is a fingerprint authentication system from I/O Software that authenticates users prior to boot. It comes with a compact fingerprint scanner that connects to an ISA card, and it works with Linux 2.0 or better. Check it out at http://www.iosoftware.com/bioapps/ssisa.htm. |
| Verivoice | This system, available for Linux 2.0+, verifies your identity using voice recognition. Check it out at http://www.verivoice.com/. |
To learn more about biometric identification, check out these sites:
A View From Europe. An interview with Simon Davies that focuses on biometric privacy issues. It's at http://www.dss.state.ct.us/digital/news11/bhsug11.htm.
Biometrics Explained. A fine document by Gary Roethenbaugh, an industry analyst at the International Computer Security Association (ICSA). It's at
http://www.icsa.net/services/consortia/cbdc/explained.shtml.Fight the Fingerprint. These folks see a biometric future, and they don't like it. As their opening page explains: "We Stand Firmly Opposed to All Government Sanctioned Biometrics and Social Security Number Identification Schemes!" It's at http://www.networkusa.org/fingerprint.shtml.
The Association for Biometrics (AfB) and International Computer Security Association (ICSA) Glossary of Biometric Terms. It's at http://www.icsa.net/services/consortia/cbdc/glossus1.shtml.
The BioAPI Consortium. This group was established to help developers integrate biometric identification into existing standards and APIs. It's at http://www.bioapi.org/.
The Biometric Consortium. "…the U.S. Government's focal point for research, development, test, evaluation, and application of biometric-based personal identification/ verification technology…" Hmmm. It's at http://www.biometrics.org/.
Modem security is an arcane but often-debated subject. Can modems leave you open to attack? Maybe… it depends on how your system is laid out. In general, though, the answer is that yes, modems can be a security risk. For this reason, corporations like Sun Microsystems have restricted their employees from installing modems in their desktops.
If your system is small (two or three workstations), you know who uses modems and you can apply various security controls, such as unplugging modem lines when they're not in use. However, if you're managing an enterprise network, you'll need to physically remove modems from most or all networked machines.
Modems pose not just an outside threat (attackers culling information about your network), but also an internal threat. Local users can use modems to send out sensitive information on a wholesale basis. If you're dead set against removing modems (perhaps your employees need them to perform certain tasks), at least install dial-out tracking devices or software. Such tools can capture every number dialed. One good product for this purpose is Whozz Calling from Mountain Systems, Inc. (It's a little pricey, though.) Check it out at http://www.mtnsys.com/pages/prices.htm.
Note
If your employees need modems for limited tasks, consider allocating these jobs to standalone workstations with minimal configurations and little or no sensitive data. This way, if something goes wrong, you can quickly reinstall without fear that a security breach can either threaten the network at large or result in leaks of sensitive information.
Some products allow you to apply modem access control and even encryption. The next section lists a few.
Advanced Engineering Concepts, Inc.
1198 Pacific Coast Highway #D-505
Seal Beach, CA 90740
Phone: (310) 379-1189
Fax: (310) 597-7145
ModemLock is a firmware/software combination that connects between a computer and an external modem. It encrypts the modem's data stream using DES and supports modem access control. It runs up to 40 hours on a 9-volt battery, has an AC adapter, and has a maximum throughput of approximately 1,900 characters per second.
IC Engineering, Inc.
P.O. Box 321
Owings Mills, MD 21117
Phone: (410) 363-8748
Email:
[email protected]
This add-on device has many, many features, including callback authentication, password protection, firmware password storage (inaccessible to internal users), non-volatile memory storage, PBX and LAN support, and a completely configurable interface. It works on any RS-232 device. To learn more about how Modem Security Enforcer operates, examine its online maintenance manual at http://www.bcpl.lib.md.us/~n3ic/mse/mseman.html.
CoSYSTEMS Inc.
3350 Scott Blvd., Building 61-01
Santa Clara, CA 95054
Phone: (408) 748-2190
Fax: (408) 988-0785
CoSECURE is a UNIX application that applies access control to modems on the SPARC platform. Dial-up ports can be completely secured in a variety of ways.
Cettlan Inc.
17671 Irvine Blvd., Suite 201
Tustin, CA 92780
Phone: (714) 669-9490
Fax: (714) 669-9513
Email: [email protected]
PortMarshal provides high-level DES encryption and authentication to remote dial-in connections. You can apply access control to some 256 ports, and the product generates copious audit logs. Reports include graphical analysis features for determining peak traffic times, usage summaries, and so forth. Unfortunately, PortMarshal management software supports only Windows 95/NT at this time. But for the functionality this product provides, it's worth adding an NT box to your network.
Still another threat is theft, either of your entire system or its individual components. Thieves need not steal your server. They can remove hard disk drives, memory, or expansion cards. The following section lists various tools that can help you secure your system and these components.
Laptop Lockup
253 So. Van Ness Ave.
San Francisco, CA 94103
Email:
[email protected]
Laptop Lockup prevents laptop theft using tamper-resistant steel cables and a brass padlock that attach the laptop to a desk or table. The product supports a wide range of laptops, PowerBooks, and so on.
Flex-Lock-50
Pioneer Lock Corporation
487 South Broad Street
Glen Rock, NJ 07452
Phone: (201) 652-9185
FlexLock-50 locks down workstations with half-inch wire cabling that will resist bolt cutters, wire cutters, and hacksaws. Pioneer also offers bottom-plate systems that attach workstations to tables and desks.
Newland Design Limited
John Street, Carnforth, Lancashire
LA5 9ER, England, UK
Phone: 44 (0)1524 733424
Email:
[email protected]
Computer Guardian is a non-platform-dependent anti-theft system for PCs. It consists of an expansion card and software on an external diskette. When the PC is moved or its components are tampered with, the system emits a loud siren likely to scare the thief and alert others.
Computer Security Products, Inc.
P.O. Box 7544
Nashua, NH 03060
Phone: (800) 466-7636
Fax: (603) 888-3766
Email:
[email protected]
Do you have a large network? PHAZER is a fiber-optic security device that detects physical tampering. This monitoring system relies on a closed loop of fiber-optic wire. If the loop is broken, an alarm is generated. PHAZER is great for securing university computer labs or other large networks.
You might also consider taking steps to identify your system in case it's stolen. Thousands of computers are stolen each year, and victims rarely recover them even after police investigate. Some users fail to keep receipts, others fail to jot down serial numbers, and so on. If you don't take these measures, you'll have a difficult time identifying your machine once a criminal reformats the drives.
Some common safeguards that can assist law enforcement include the following:
Maintain meticulous records on all your hardware, including model and serial numbers. You'll need these later if police are called. It's often not enough that you can recognize your machine by its dings, cracks, and crevices. Police usually demand something more substantial, like serial numbers, bills of sale, and so on.
Permanently mark your components with unique identifiers using indelible ink, fluorescent paint, or UV paint/ink that is visible only under black light. In particular, mark your motherboard, expansion cards, disk drives, the unit casing's interior and exterior walls, and your monitor.
In addition, you may want to investigate proprietary marking or ID solutions. Two in particular are STOP and Accupage.
STOP
30 Myano Lane, Suite 36
Stamford, CT 06902
Phone: (888) STOPTAG / (203) 359-9361
STOP is a two-tiered theft prevention and identification system. First, an indelible chemical tattoo is etched into your hardware. This tattoo identifies the equipment as stolen property. A special metal plate is placed on top of this that will adhere even under 800 pounds of pressure. Thieves can only defeat STOP by physically cutting away the tattooed, plated chassis.
Accupage Limited
P.O. Box 26
Aldershot, Hampshire
GU12 5YP, UK
Email:
[email protected]
Accupage is a hardware system that embeds an indelible message into a PC, containing the identity of the PC's rightful owner. Police can later examine this message to determine ownership and whether the PC has been stolen. Accupage is being integrated into some new laptops, but older desktop systems can be retrofitted.
Some security and ID measures can backfire or leave you open to invasion of privacy. In my opinion, Intel's Pentium III serial number is one such example.
The Pentium III sports a permanent, unique, 96-bit serial number. This number can identify your machine not only to vendors, but also to remote Web hosts. Herein lies the problem.
Intel initially insisted that since all models were shipped with this functionality disabled, there was no privacy threat. In fact, Intel contended that only users could reactivate it, and therefore only users who wanted to be tracked would be exposed.
This was untrue.
Weeks after Intel's initial statements were released, a German hacking zine reported that remote attackers could get the serial number without the user's express consent, even after the serial number option was disabled. As of this writing, Intel has been scrambling to minimize public fears (no doubt to save its chip from a boycott).
Through Intel's smoke screen, here's what I see:
Intel suggests that the serial number benefits consumers. Balderdash. It benefits online merchants who want to track the public's movements and buying habits.
In hardwiring its serial number, Intel has thrown in with other cabals that yearn for an Orwellian society.
To date, I haven't seen any electronic retail outlets warn consumers of the Pentium III privacy threat. Have they just not gotten around to it?
I believe that Intel gambled that most users are inexperienced. Newbies would never suspect anything, and even if they did, they would have no way to confirm their suspicions.
I will never purchase a Pentium III and will never advise anyone else to do so unless Intel posts the open source for its serial number system. As someone who very much values his privacy, I find Intel's behavior in this instance repugnant. Which Web sites I visit is my business and my business alone. In my opinion, Intel's serial number scheme is no less intrusive than someone accompanying me to the library, breathing down my neck, and gawking at what books I've checked out. Or worse, reporting that information back to someone else!
To learn more about the Pentium III controversy, check out these links:
"Pentium III serial number is soft-switchable after all," a discussion of how the folks at c'tmagazine cracked the Pentium III serial number system (http://www.heise.de/ct/english/99/05/news1/).
The Big Brother Inside Home Page. Here, get the unabridged story with many articles and links http://www.privacy.org/bigbrotherinside/.
Good physical security is all about common sense. Whenever possible, implement all security procedures prescribed by your hardware manufacturer. In particular, watch for default passwords and such.
Also, if you're currently using used network hardware, it's worth tracking down supplemental documentation on the Internet. Older network hardware may harbor various flaws.
Finally, perhaps the best tip is this: Take every possible precaution to prevent unauthorized users from gaining physical access to your servers or network hardware.