Chapter 3
Introducing the VMM 2012 Architecture
Virtual Machine Manager 2012 has become the main tool for building the Microsoft private cloud and is now an important member of the System Center 2012 family of management products. This chapter describes the following:
- How VMM evolved from a patched-together collection of managers to today's sophisticated tool
- The capabilities of VMM that make it a complete solution for managing private clouds
- The architecture and main components of a VMM private cloud
Exploring the New Capabilities of VMM 2012
The traditional data center has a large variety of servers, clusters, hypervisors, network devices, storage devices, and other equipment. Most physical servers host dozens of virtual machines. Those virtual machines in turn host a variety of operating systems and applications. Most of them run some version of Windows and Linux. Another trend that can be observed in more and more enterprises is the combined use of several hypervisors. Hyper-V and XenServer have joined VMware, and the most appropriate hypervisor is chosen for a particular workload or scenario. Notably, Hyper-V R2 has made a lot of progress in the past two years, and the advent of Hyper-V in Windows Server 8 promises a breakthrough of Microsoft virtualization for both server and client. Multi-hypervisor is here to stay!
Your IT environment can be large, medium, or small; regardless of size, the chances are high that you work in the kind of heterogeneous environment described in the previous paragraph. You may already use or may be contemplating using several Microsoft System Center 2012 management applications. Most likely you will upgrade from their previous versions. Even if you haven't decided to upgrade, you should take a look at the different members of the System Center family: Operations Manager is a capable monitoring and reporting solutions for heterogeneous environments with Windows, Linux, and VMware. You might have considered using Data Protection Manager to protect your Windows applications and Hyper-V virtual machines. Perhaps you have already set up Configuration Manager for deploying and updating your clients and servers. You may even have thought of applying Service Manager in combination with Orchestrator to control the flow of your IT and data-center processes. Creating some sort of synergy across the different parts of your data center would really help your IT team.
Now that you have started to figure out how to transform your traditional data center into a private cloud, you need to take a closer look at Virtual Machine Manager (VMM). If Hyper-V is already a hypervisor of choice in your environment, you have probably implemented VMM 2008 R2 to deal with a collection of virtual machines. This product was nothing more than an extension of Hyper-V Manager and Failover Cluster Manager, although for some tasks you had to resort to the native Hyper-V and clustering tools. VMM 2008 R2 was not always aware of changes performed in the other tools, which could cause unexpected behavior. Not so with VMM 2012! Considerable effort was put into making VMM the primary tool for managing Hyper-V, VMware, and XenServer—and into avoiding the use of other managers. VMM 2012 is positioned to be the primary aid in building the foundation for a Microsoft private cloud that is not confined to Microsoft virtualization. It is surrounded and integrated with the other System Center 2012 modules to offer you superior control of the ever-expanding, diverse ecosystem of IT Infrastructure and, most important, the applications or services that help your organization operate successfully.
In summary, this piece of management software is aimed at the virtualized data center. It helps to configure and manage not only virtualization hosts and virtual machines but also the relevant networking and storage resources. Resource pooling is one of the essential characteristics of the cloud. VMM enables you to combine many of your server, storage, and network devices and organize them into capacity pools. This is a big step in the right direction, because traditionally these resource silos were managed separately and required dedicated IT staff. With its very good deployment capabilities, VMM makes it easy for you to create and deploy virtual machines and applications (or services, as they are now called). This product release and the other members of the System Center 2012 suite will help you build and operate the private cloud.
New Functionality
In this section, we'll briefly look at the tremendous amount of new functionality introduced with VMM 2012.
VMM Deployment
- You can install VMM in a Windows failover cluster. As of this release, it is possible to build a highly available VMM management server, allowing quick VMM failover while you perform hardware or software maintenance on one of the cluster nodes.
VMM Security Configuration
- Taking Operations Manager as its example, VMM allows you to create Run As accounts. It simplifies and speeds up the process of providing credentials while accessing or configuring a certain device or other cloud object. You don't have to remember all the passwords, and you control who is able to use those Run As accounts.
- You can create a Delegated Administrator and Self-Service User role to provide finer control in VMM. You don't want to assign full control to your fabric and clouds to all members of your IT department. You can delegate control to certain people and specify which parts of the fabric they can access.
- You can create a Read-Only Administrator user role and several other existing roles, such as the Delegated Administrator and Self-Service User roles. If you want to keep control over the private cloud but want certain users or customers to have a read-only view of their cloud objects, you can give them permission to view their own host groups, virtual machines, clouds, and library servers.
VMM Fabric Configuration
- You can discover physical servers without an operating system on the network and add the bare-metal servers to VMM management by installing a version of Windows Server that includes the Hyper-V role. This gives you the power to rapidly deploy a large number of physical servers and automatically configure them according to organizational standards.
- With minimal effort, you can create an operational Hyper-V cluster by joining multiple standalone Hyper-V servers. The wizard quickly collects all relevant data and configures the cluster automatically. You can also validate the cluster after you make changes, add or remove nodes, or uncluster the corresponding Hyper-V servers.
- You can manage Citrix XenServer hosts. This makes VMM the first private-cloud management solution that supports the three leading hypervisors. Because its architecture is similar to that of Hyper-V, XenServer is a logical extension of the hypervisors that could be managed in the previous version of VMM.
- You can create and configure networking resources consisting of logical networks, IP-address pools, MAC-address pools, load balancers, and VIP templates, which can be used to deploy virtualization hosts and virtual machines on any of the supported hypervisor platforms. With networking integration, administrators and delegated administrators can configure and assign networking resources without the full-time involvement of a specialized network administrator.
- You can create and configure storage resources with one or more storage classifications and pools, storage providers and storage arrays. By utilizing deep storage integration, administrators can assign storage to Hyper-V virtualization hosts without the full-time involvement of a specialized storage administrator. Of course, storage expertise and assistance are required during the configuration phase of VMM and the integration of all supported storage arrays. Once an agreed portion of enterprise storage has been made available to the storage pool by the storage administrator, the administrator can independently assign storage capacity to one or more private clouds. In the current release, this functionality is available only to Hyper-V hosts and clusters.
- You can scan Hyper-V and fabric-management servers to make sure they comply with a defined update baseline. You can verify the compliance status of these servers and use a configured Windows Server Update Services (WSUS) server to perform update remediation. Compliance management applies to Hyper-V servers and clusters, VMM management servers, VMM library servers, Windows software update servers and WDS/PXE servers.
- You can automatically schedule resource balancing of virtual machines across host clusters that support live migration technologies (dynamic optimization).
- You can automate the power management of virtualization hosts that have been idle for some time. Idle hosts can be automatically switched off after a graceful live migration of the virtual machines. When required, these hosts will be automatically switched on based on workload requirements (power optimization).
VMM Cloud Configuration
- In VMM, one or more private clouds can be created for an organization or department to organize a selected number of virtualization hosts in combination with a pool of storage, a variety of networking resources, and VMM library resources. If you are a hosting provider, you probably have a cloud for each customer. Virtual machines and services can be deployed to those private clouds.
- Server application virtualization (Server App-V) is integrated into VMM, adding the ability to create sequenced applications for deployment by VMM.
- The concept of a capability profile is introduced in VMM to define or to limit the resources that can be used by a virtual machine in a private cloud. There are default capability profiles for Hyper-V, VMware, and XenServer, but you can also create your own.
- Application profiles with configuration details about Server App-V, Microsoft Web Deploy, and SQL Server data-tier applications (DACs) can be created in VMM to deploy scripts, applications, and services in the private cloud.
- You can create a SQL Server profile with special instructions for a SQL instance when used with a SQL Server DAC as part of a virtual machine or service.
- You can deploy virtual machines to private clouds by means of virtual-machine and service templates.
- The Service Template Designer is introduced in VMM to create service templates, which can be used to deploy services to a cloud.
- You can scale out a service by adding additional virtual machines to a service that has already been deployed.
- You can update an existing service template using version management. If combined with multiple update domains and load-balanced virtual machines, it is possible to update an already deployed service without downtime for users.
- You can transfer service templates and virtual-machine templates by means of export and import.
- You can mark file-based/physical library resources as equivalent objects in different and often distant VMM libraries so that any identical file object (.vhd file, .iso file, or custom object) can be used from any VMM library when a virtual machine is deployed from a template. This enables you to use a single template across multiple sites.
Changed Functionality
Support for the following software is deprecated in the current version of VMM:
- Microsoft Virtual Machine Manager 2005 R2
- VMware ESX 3.0 and ESXi 3.0
- Microsoft SQL Server Express (VMM 2012 requires a fully featured version of Microsoft SQL Server)
The previous version of VMM already had limited self-service, but users had to log into a web portal that had limited functionality. Self-service users can now benefit from the VMM console and are not limited to using the web portal.
Resources for VMM 2012
For more information about VMM 2012, you can refer to the following URLs:
System Center Downloads
http://technet.microsoft.com/en-us/systemcenter/cc137824
Documentation
- System Center 2012 Technical Library:
- TechNet Library:
http://technet.microsoft.com/nl-nl/library/gg610610(en-us).aspx
- Microsoft Download Center:
Websites
- Microsoft Server and Cloud Platform:
www.microsoft.com/en-us/server-cloud/system-center/virtual-machine-manager.aspx
- VMM 2012 Survival Guide:
http://social.technet.microsoft.com/wiki/contents/articles/vmm-2012-survival-guide.aspx
- Virtual Machine Manager blog:
- Storage and Load Balancer Provider downloads:
- VMM 2012 Error Codes:
http://social.technet.microsoft.com/wiki/contents/articles/4906.aspx
Community (MVP) blogs
http://kristiannese.blogspot.com
http://mountainss.wordpress.com
http://workinghardinit.wordpress.com/author/workinghardinit/
Understanding the VMM Architecture
Designing and building a private cloud can be an interesting adventure, if not virgin territory. “Think before you build” is good advice, but it's difficult to plan something in a field that is mostly unknown to you. That's why you bought this book. Because there is little guidance in the land of private clouds, the following chapters will take you by the hand and guide you through that uncharted territory. This chapter doesn't yet focus on installing hardware or software components; it is intended to help you before you start your journey.
Prior chapters explain what a private cloud can mean to your company, its employees, and its customers. Your team has agreed to build that promising private cloud for your organization and you need to prepare for that daunting project. Although many components of the private cloud may be familiar to you, welding them all together requires new insights. Take some time to prepare. Read as much as you can about the cloud concept. Talk with your colleagues and your peers in the social media. Check the relevant blogs and forums on the Internet. Begin to define what you expect to achieve with the private cloud. Don't forget to involve corporate management; you need to know what they expect from IT.
So far you are doing quite well. What you are learning from this book should help you build an environment in which to learn, to test and verify your assumptions, and get hands-on experience building the foundation for your private cloud. Take ample time to think and to prepare for the journey.
Use your imagination and try to sketch the general picture. You can always adapt and modify your ideas before you finally begin to build your first production private cloud. Even after you build the infrastructure components of the private cloud, flexibility is your friend. After all, isn't that what you expected when you started to think of building a cloud in the first place? Cloud computing is still in its infancy. This is the time to experiment, learn from your mistakes, and adjust as necessary.
Your first step in designing a private cloud is to understand the major building blocks. A private cloud is built around familiar physical building blocks such as servers and clusters, networks, and storage. The generic word used for them is fabric. In the storage world, the word fabric is used to describe a collection of interconnected storage devices (SAN switches, storage arrays, tape robots, and so forth). In the context of the cloud, the term fabric includes servers, clusters, and networks, as well as storage.
So fabric is the pretty little word that encompasses the vast physical foundation of the private cloud. However, when you start thinking about architecting that fabric, it is a good idea to take a satellite view of your surroundings. Imagine booking a trip on one of the first commercial space flights. While in orbit, you get a fairly good opportunity to look at the world you thought you knew well, but now as you look down, you behold its abstraction, the impressive overall view from your shuttle window. While picturing the fabric as the foundation of the private cloud, you do not need to zoom in on the details just yet. Let's put in the bigger blocks first: servers and clusters, networks, and storage.
If you're not sure whether a private cloud would be appropriate or if you fear your company might be too small, think about the scale and complexity of your IT operations. Even if you have a limited number of physical servers and virtual machines, building a private cloud could mean making a new start with new principles to fight the often time-consuming manual labor needed to deploy servers and virtual machines and attach networks, VLANs, and all the different storage options. Instead of looking at the individual pieces, it is time to look at them as a fully functional and interconnected fabric. The biggest gains come from changing your attitude toward standardization, automation, elasticity, and self-service. Together the results will be rewarding, whether your private cloud is small, medium, or large.
If your cloud will serve a small number of customers, it will have one cluster with a few hosts, network, and storage devices. If your company has bigger aspirations, you may have hundreds of hosts, several networks, multiple locations with hundreds of VLANs, multiple load balancers, and numerous storage arrays. When you picked up this book, you were already convinced of the advantages that a private cloud offers you, your company, and the consumers of your cloud. You already want to build one. All you have to do is find out if your theory can land on earth and become a common practice.
Take your binoculars and zoom in one level. Ignore objects such as domain controllers, DNS servers, and DHCP servers. The relevant servers are virtualization hosts of several different flavors, clusters combining multiple virtualization hosts, and a variety of management or auxiliary servers. Think of hosts that manage deployment, hosts for managing and monitoring both virtual and physical machines, and hosts that take care of update management—and don't forget the prospect of a rapidly growing number of virtual machines.
The next major component of the fabric is the network. Again, this assumes that all the physical switches, routers, and load balancers that make the LAN and WAN are in place. The network either has no VLANs or the network administrator has already logically divided the network into multiple virtual LANs, each representing a location or a specific purpose. Wouldn't it be nice if you could abstract those networks by using meaningful names and you could find a way to manage the pools of static IP addresses?
The third important building block is storage. Without an abundance of storage, a cloud has little substance. Storage is the collection of storage arrays, pools of disks, and the individual disks (often called LUNs by SAN admins) assigned to servers. Like the networking component, storage is often in the hands of a specialized admin. More often than not, that dependency on specialists will prolong the deployment of new services. Wouldn't it be great if the consumer or an application administrator could easily recognize the different storage silos? Wouldn't it make your job easier if you could assign the appropriate quality and quantity of storage to a virtual machine, service, or entire cloud with little effort?
If self-service is one of the most important and useful characteristics of a private cloud, then self-service users shouldn't have to understand the technical building blocks in the cloud landscape. These artifacts should be completely abstracted.
Components of VMM
Depending on the size and scale of a private cloud, VMM can be deployed on one or several servers. If your environment is limited to a few Hyper-V hosts, all the components can be installed on one server. If you expect to host dozens or even hundreds of hosts with different hypervisors and possibly thousands of virtual machines, you need to take a more careful look at where to place the different components of VMM. A primary reason for this is to increase scalability, flexibility, serviceability, and availability.
Chapter 4 looks at the requirements for a number of different configurations. It gives a general overview of the different VMM components and how they can be distributed across multiple servers and locations.
Figure 3.1 gives an architectural view of VMM 2012 and shows some of the components described in the preceding paragraphs.
Figure 3.1 The VMM architecture
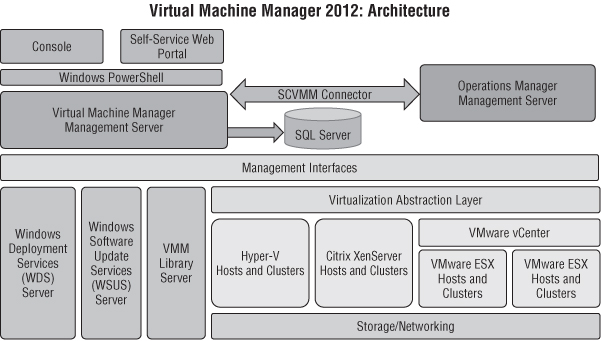
VMM Management Server
The central component of VMM is the VMM management server, which runs as a Windows service on each VMM server. This component is the first one to be installed and is responsible for communicating with the SQL Server database and for storing and retrieving the configuration, including all objects that are created and managed by VMM. This core service also stores performance information about the different fabric resources.
The VMM management server has a broker function and is responsible for the following tasks:
- Communicating with the database server for storing and providing information when a VMM client asks for information via the VMM console or a PowerShell cmdlet.
- Communicating with hosts via VMM agents and executing commands
- Communicating with VMM library servers via a VMM agent and executing commands
- Communicating with XenServer servers and executing commands
- Communicating with VMware vCenter servers and expediting commands
- Starting and stopping jobs
- Monitoring jobs
- Reporting progress, success, and failure
- Communicating with System Center components
The VMM management server is also supported in a virtual machine but should ideally be isolated from the servers it manages. A good location for a VMM server could be a Hyper-V cluster dedicated to System Center 2012 management.
A default installation of the VMM management server is performed on a single machine. This may make sense in a testing and development environment. The setup can be done quickly and easily. If you are setting up VMM for a private cloud of some size, your admins, users, or customers depend on it, so consider making VMM highly available.
If you are going to operate an enterprise-level private cloud, consider the consequences if your VMM-related servers are unavailable for a day, two days, a week, or possibly even longer. After you spend a good amount of time deploying and configuring VMM, the database will be filled with all relevant objects and resources. Several other cloud admins, application admins, or even external customers will depend on VMM. At that point, VMM will become a very important piece of software and will be the spider in the web of your private cloud. If you decide to cluster VMM, do you think making VMM highly available will suffice? You will need to cluster the database as well as the virtual-machine libraries.
Because all three functions (VMM management, VMM database, and VMM library) can't be in the same physical or guest cluster, it would perhaps be better to take another approach. Apart from VMM, you will probably also implement other members of the System Center 2012 family. Most management applications have the same high-availability requirements. In such cases, a good approach is to take two or more physical servers, provision some shared storage, build a Hyper-V cluster, and deploy the System Center products as Hyper-V highly available virtual machines. With all three important VMM components, you can also create three separate guest clusters: a two-node SQL Server guest cluster, a two-node VMM management server cluster, and a two-node file cluster for the VMM libraries. Of course, if you have already clustered the database and file servers, you can concentrate on building a highly available VMM management server. Chapter 4, “Setting Up and Deploying VMM 2012,” describes how to do this.
VMM Database
The VMM database is a Microsoft SQL Server database, which is installed on the VMM server itself, on a dedicated SQL Server machine, or on a SQL Server cluster. As of VMM 2012, a full version of SQL Server is required (see Chapter 4 for the exact requirements) and must be available before the other components can be installed. In a larger private cloud, a separately clustered SQL Server is highly recommended. It protects against problems with either the physical server or the SQL Server services and configuration. Monthly maintenance can be performed more easily, because vital services can be failed over between the nodes in the SQL cluster.
Size and scalability determine where to place the VMM database. As you will see in Chapter 4 in the section on VMM requirements, it is feasible to place the VMM database in a virtual machine (cluster) too.
VMM Console
The VMM console offers the primary graphical user interface for all private cloud administrators, delegated admins, read-only admins, and self-service users. However, what you can see and manage in the VMM console depends on your role. Some admins need to have full access to all fabric resources, such as servers, network, and storage. If you are in a consuming role, you only need to see your own clouds and have access to the computing, network, and storage resources for which you have permission. As a consumer, you want to quickly and efficiently deploy new virtual machines and services, deploy applications, and deploy the images that contain them. For such self-service users, the underlying infrastructure is invisible and fully abstracted as explained in Chapter 6, “Integrating Networking and Storage into VMM 2012,” and Chapter 7, “Deploying Hosts and Clusters in VMM 2012.”
The VMM 2012 interface differs considerably from earlier versions. The first remarkable difference is the ribbon, the flexible and context-sensitive tool used to access most detailed functions. As you can see on the bottom left of Figure 3.2, there are more Wunderbars, now called workspaces, and they have changed. Administration is now called Settings. It allows you to view or configure a variety of different settings. The Library and Jobs bar is still there, but Hosts has been placed under the new Fabric workspace, which hosts not only Servers but also Networking and Storage. Finally, the Virtual Machines category is now combined with Services in VMs and Services.
Figure 3.2 The VMM 2012 user interface
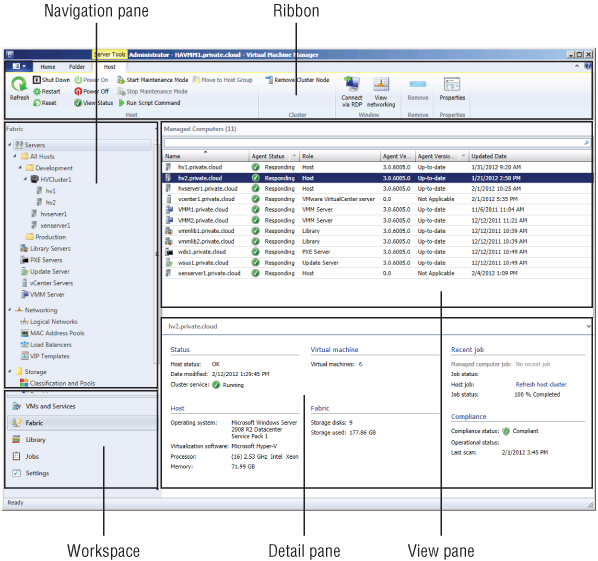
The VMM console is automatically installed with VMM Management Server, and a VMM console icon is placed on the desktop. The VMM console can be installed separately on a management computer and allow you to connect to VMM remotely. When you install the VMM console, you also get the VMM command shell, PowerShell. While the console is built on top of PowerShell, the console does not provide access to all the functionality available through a PowerShell cmdlet.
VMM Command Shell
The VMM command shell is the true engine of VMM. Like the console, the command shell is installed with each VMM management server. By default, two PowerShell modules are imported to the VMM server: virtualmachinemanager and BitsTransfer. You can check which commands are available in the module by issuing the following command:
Get-Command -Module -virtualmachinemanager
The BitsTranfer commands are used by VMM to start, stop, and suspend background intelligent transfer service (BITS) jobs. These jobs transport large quantities of data between systems, cleverly employing bandwidth only as it becomes available. VMM has a lot of bit transfers to do, so this module is loaded by default.
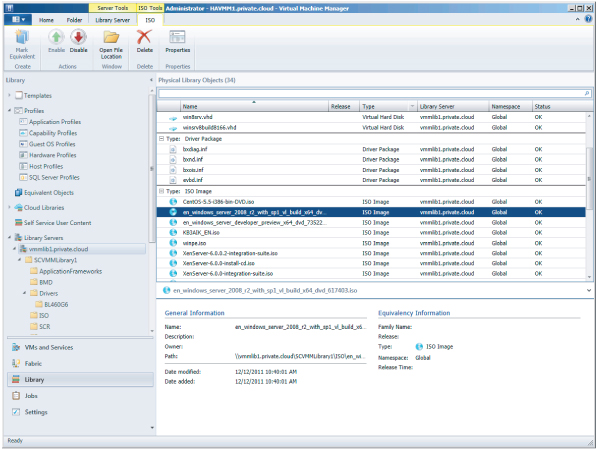
VMM Library
The VMM library (Figure 3.3) provides an easy way to configure a repository of the resources that help create a virtualization host, a virtual machine, an application, or service. Examples are .iso image files, virtual hard-disk files (.vhd, .vmdk), VM templates, PowerShell scripts (.ps1), Answer Files (.inf, .xml), SQL Server scripts (.sql), MSDeploy packages (.zip), Server App-V packages (.osd), virtual floppy (.vfd, .flp) files, driver files (.inf), Custom Resources (.cr), and complete clones of virtual machines. Chapter 5, “Understanding the VMM Library,” is dedicated to the VMM library.
Figure 3.3 Overview of the VMM Library
VMM Self-Service Portal
With VMM 2012 you can optionally install a web-based VMM Self-Service Portal. This component allows you to create a controlled environment where self-service users can create and manage their own virtual machines via a web interface. You can enable an application administrator to author, deploy, manage, and decommission applications in the private cloud. It is a good idea to configure this portal on a separate machine that hosts Internet Information Services (IIS).
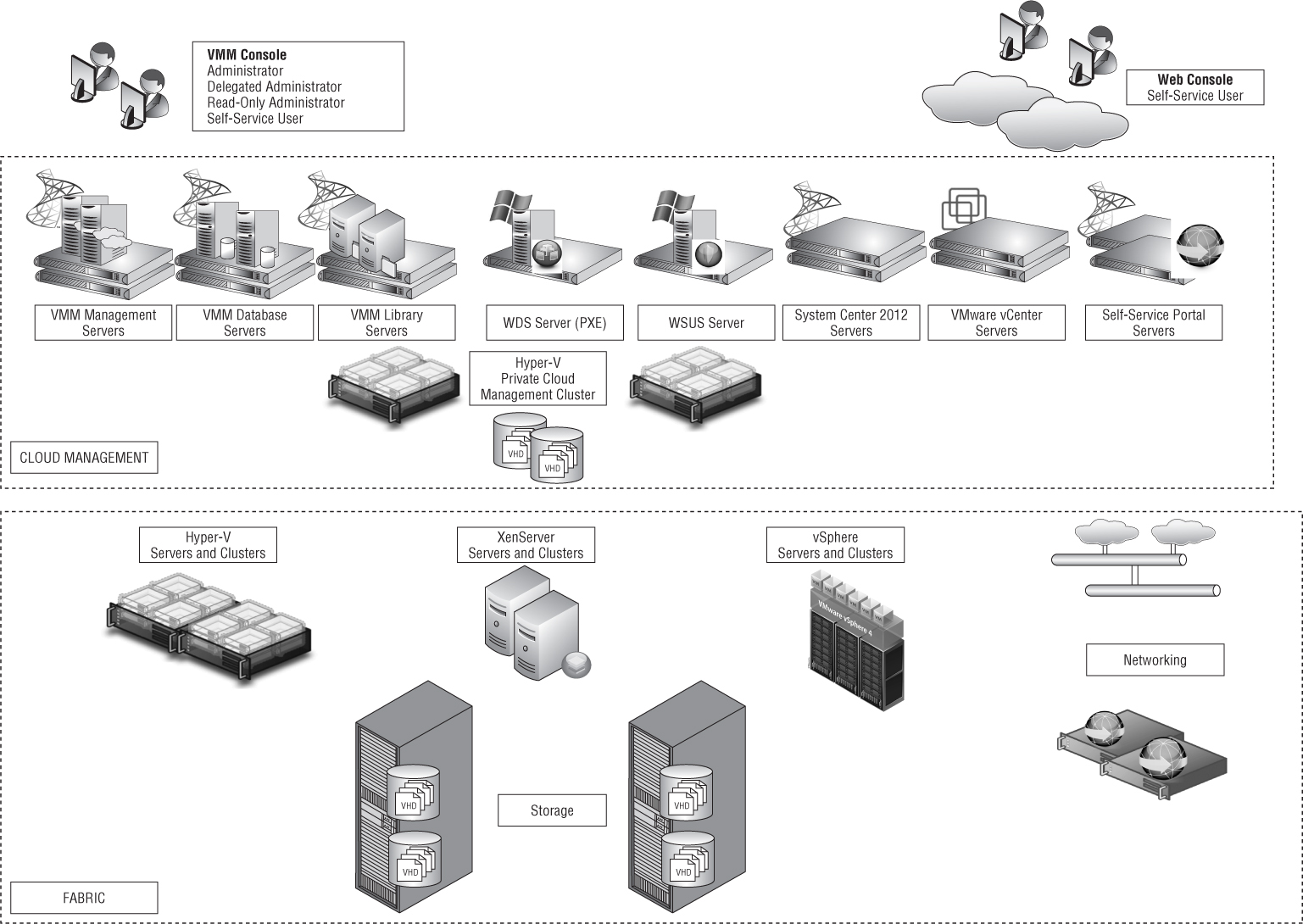
VMM 2012 Topology
If you combine all the components and add the virtualization host and auxiliary servers WSUS and WDS, the topology of Virtual Machine Manager 2012 resembles the landscape of Figure 3.4.
Figure 3.4 Overview of the VMM 2012 topology
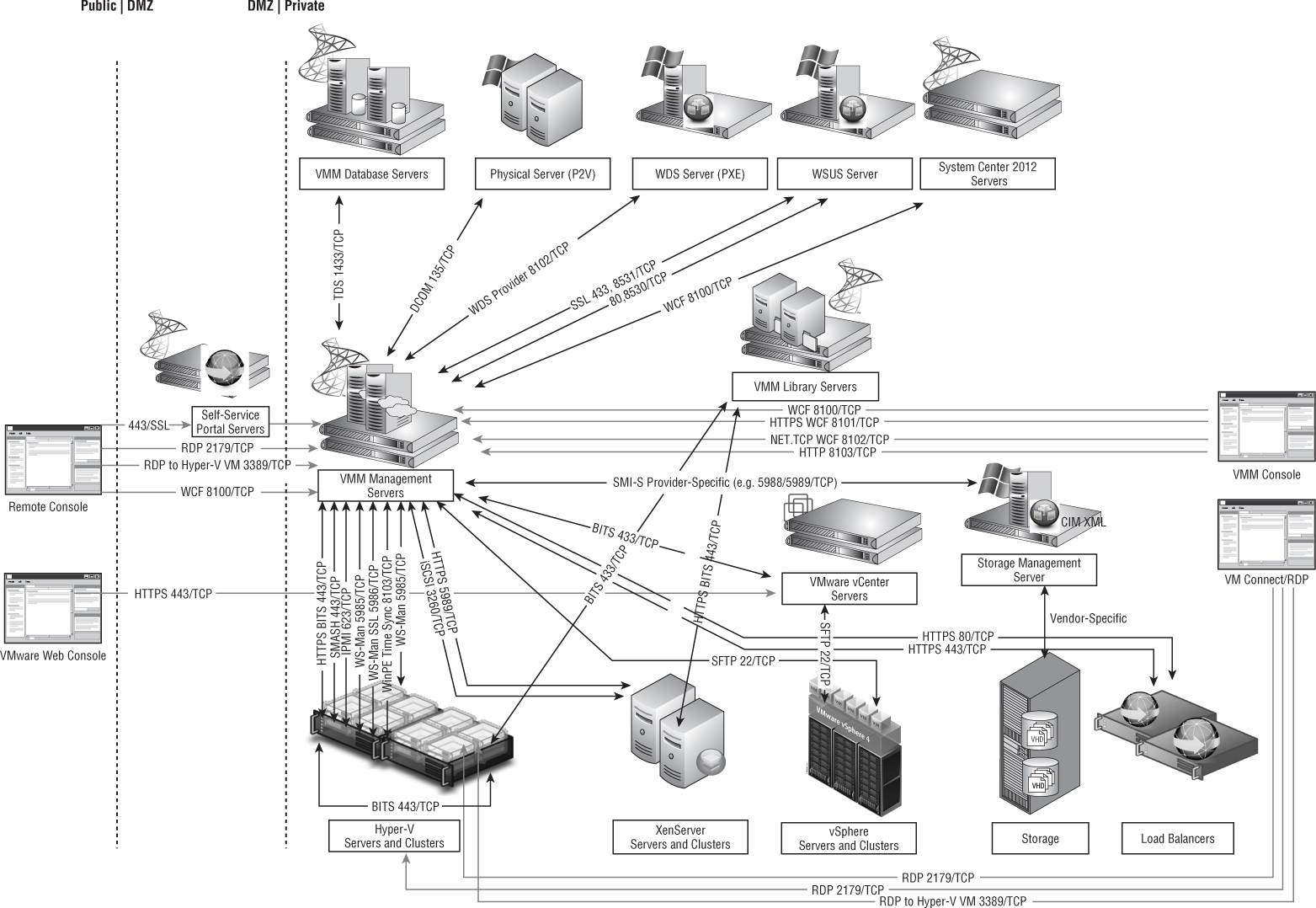
Ports and Protocols
When you set up the VMM management server, you can assign a number of ports for protocols that are used to communicate with a variety of devices as well as for executing file transfers between the different VMM components. As a security best practice, these default ports may be changed. VMM must be uninstalled (with retention of the database) and reinstalled to change any of these ports. Figure 3.5 shows the default ports that are configured when VMM and the VMM console are installed.
Figure 3.5 Default ports for VMM and the VMM console
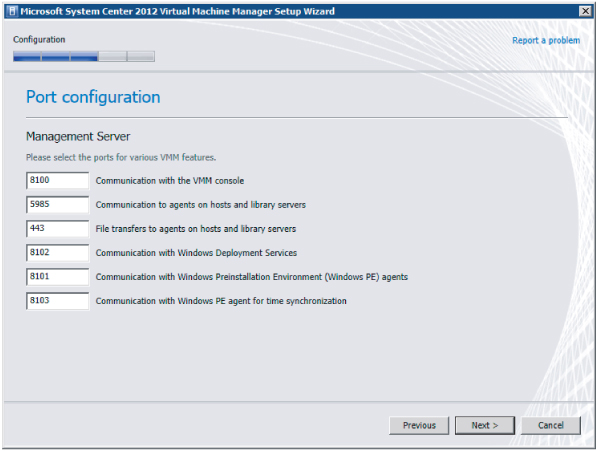
The default settings for the ports are listed in Table 3.1. Figure 3.6 represents these ports pictorially.
Table 3.1 The VMM Default Ports
| Connection Type | Protocol | Default Port |
| SFTP file transfer from VMware ESX 3.x hosts | SFTP | 22 |
| VMM management server to P2V source agent (control channel) | DCOM | 135 |
| VMM management server to load balancer | HTTP/HTTPS | 80/443 |
| VMM management server to WSUS server (data channel) | HTTP/HTTPS | 80/8530 |
| VMM management server to WSUS server (data channel) | HTTP/HTTPS | 443/8531 (SSL) |
| BITS port for VMM transfers (data channel) | BITS | 443 |
| VMM library server to hosts file transfer (data channel) | BITS | 443 (Max: 32768) |
| VMM host to hosts file transfer (data channel) | BITS | 443 (Max: 32768) |
| VMM self-service portal to VMM self-service portal web server | HTTPS | 443 |
| VMware Web Services communication | HTTPS | 443 |
| SFTP file transfer from VMM management server to VMware ESX Server 3i | HTTPS | 443 |
| OOB connection SMASH over WS-Man | HTTPS | 443 |
| VMM to VM data channel | HTTPS (BITS) | 443 |
| VMM to Windows host data channel | HTTPS (BITS) | 443 (Max: 32768) |
| OOB connection IPMI | IPMI | 623 |
| VMM management server to remote SQL Server database | TDS | 1433 |
| Console connections (RDP) to VMs via Hyper-V hosts (VMConnect) | RDP | 2179 |
| VMM management server to Citrix XenServer host (customization data channel) | iSCSI | 3260 |
| Remote desktop to virtual machines | RDP | 3389 |
| VMM management server to VMM agent on Windows Server–based host (data channel) | WS-Management | 5985 |
| VMM management server to in-guest agent VMM to Virtual Machine (control channel SSL) | WS-Management | 5985 |
| VMM management server to VMM agent on Windows Server–based host (control channel SSL) | WS-Management | 5986 |
| VMM management server to XenServer host (control channel) | HTTPS | 5989 |
| VMM console to VMM management server | WCF | 8100 |
| VMM self-service portal web server to VMM management server | WCF | 8100 |
| VMM console to VMM management server (HTTPS) | WCF | 8101 |
| Windows PE agent to VMM management server (control channel) | WCF | 8101 |
| VMM console to VMM management server (NET.TCP) | WCF | 8102 |
| WDS Provider to VMM management server | WCF | 8102 |
| VMM console to VMM management server (HTTP) | WCF | 8103 |
| Windows PE agent to VMM management server (Time Sync) | WCF | 8103 |
| VMM management server to Storage Management Service | WMI | Local call |
| VMM management server to cluster PowerShell interface | PowerShell | n/a |
| Storage management server to SMI-S provider | CIM-XML | Provider specific port |
| VMM management server to P2V source agent data channel | BITS | User-defined |
Figure 3.6 Overview of VMM 2012 ports and protocols
Summary
VMM arose from Microsoft's attempts to control its virtualization and cluster failover facilities. VMM 2008 R2 provided an incomplete solution, but VMM 2012 finishes that job and adds facilities for building and managing Microsoft private clouds.
A Microsoft private cloud rests on a fabric of servers, clusters, networks, and storage. By abstracting these elements, VMM 2012 enables the key cloud features of resource pools, elasticity, and self-service.
VMM 2012 is built on the VMM management server, which brokers requests between clients and the software underlying the abstracted fabric elements that clients see. It uses a full SQL Server database to keep track of all the pieces. Clients and administrators can communicate with the management server using a GUI, a command shell, or a self-service portal.
A key feature of private clouds is that all underlying fabric resources (virtualization hosts, storage, and network) are abstracted from the consumer of the private cloud.
