Antimalware policies are easy to deploy to collections of Configuration Manager Clients and will specify how Endpoint Protection protects them from different malware and threats. Several settings, such as the scan schedule, the types of files and folders to scan, and actions taken when malware is detected are typical settings that you would configure in the policies to fit the targeted computers.
When you enable Endpoint Protection on your client computers, the default Endpoint Protection policy is applied. You may also use additional policy templates, which you can import from the console, or create your own custom policies to meet the specific needs of your environment.
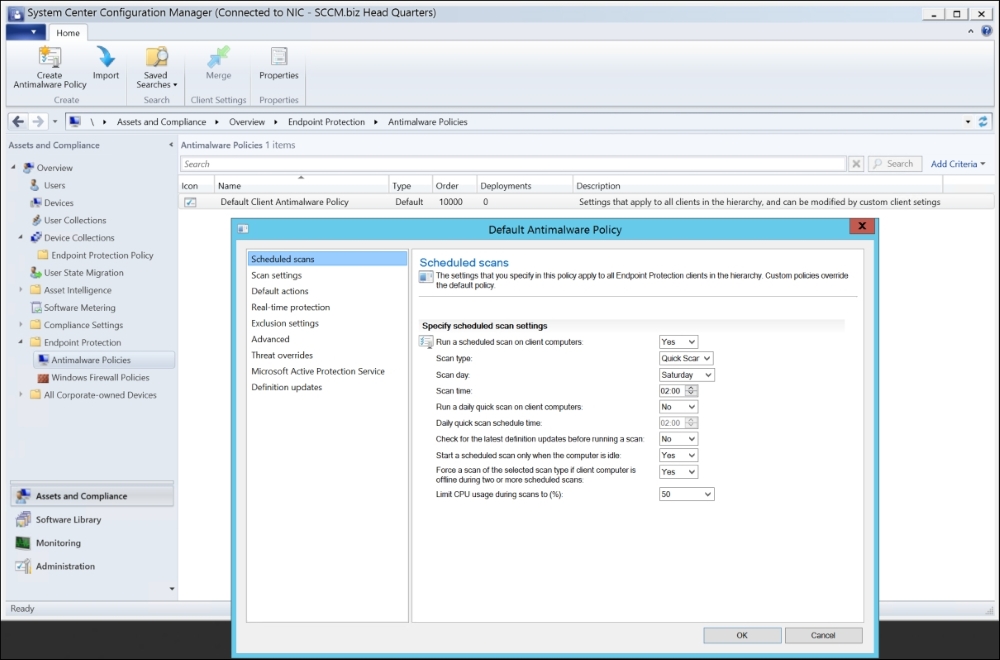
This is how your default antimalware policy in Endpoint Protection looks and will be applied to all your Configuration Manager clients that have the Endpoint Protection client installed and enabled.
I recommend that you don't make changes to this policy other than the definition updates shown in the following screenshot:
Default Antimalware Policy
You can see the Definition updates settings, in the Default Antimalware Policy, in the following screenshot.
I would recommend that you define in the Default Antimalware Policy what Update Sources order and configure settings that would suite most of your Endpoint Protection clients. That way, if the computer should not receive any other Custom defined policy for whatever reason, it will at least get definitions updates correctly, which is the most essential thing for it to work properly:

Update Sources order in the Default Antimalware Policy
The order shown in the preceding screenshot is the default order, and I've checked the updates from the Universal Naming Convention (UNC) file share as well. As described in Chapter 2, Configuring Endpoint Protection in Configuration Manager about Definition updates, you need to think this through and plan according to how Configuration Manager is installed, how its hierarchy is defined, and what your network looks like.
The default order is the recommended one, and I wouldn't change it if you don't have any special requirements. But you need to know that the clients won't be able to fetch any definition updates from WSUS if you have not entered the WSUS Console and set up Automatic Definition rule there. You should not make any other changes in the WSUS console.
However, you need to think this through. If you have 20,000 clients in an office located on the other side of the world communicating over a 2 Mb network link connection, you might not want them to fetch definition updates from the WSUS Server at your primary site headquarters just because something is wrong with the Configuration Manager distribution points.
I would also recommend keeping the last two options selected as well. These are the updates from Microsoft Malware Protection Center and UNC file shares, and they will kick in as a failsafe method for the Endpoint Protection clients to fetch the definitions updates if the Windows updates or Configuration Manage client should somehow cease to work or fail.
Keeping this order and all settings correct should ensure that all your clients should work as safely as possible.
Other antimalware that I've worked with doesn't have a good monitoring solution to detect if a client fails to respond and no longer applies updates. A worse case scenario would be to find out which machines do not have anti-malware product installed and why do they not have it.
It's important to know that if you have several policies deployed to the same targeted systems with the same specified settings, only the specified setting from policy with highest precedence will be applied, depending on the order.
Meaning policies do merge with precedence order in consideration. So, you can actually approach this in many ways depending on what suites your needs in the best way. Also, the fact that this works dynamically with constantly updated collections makes this highly unique compared to other similar products.
You can in fact have several policies like DNS, DHCP and Active Directory deployed to each collection and have several servers automatically queried based on what software application they have installed.
There is also another merge feature that will allow you to create a new custom policy based on the settings from two or more policies. Let's say you have DNS and DHCP roles on your domain controllers, which is very common in small- to medium-sized companies, you would want to import those three policies and merge them. This is done by selecting the policies and then selecting Merge from the menu:

Merging of three Antimalware policies.
You would then want to deploy the policy created to a collection containing all the Active Directory Domain Controller servers in your domain.
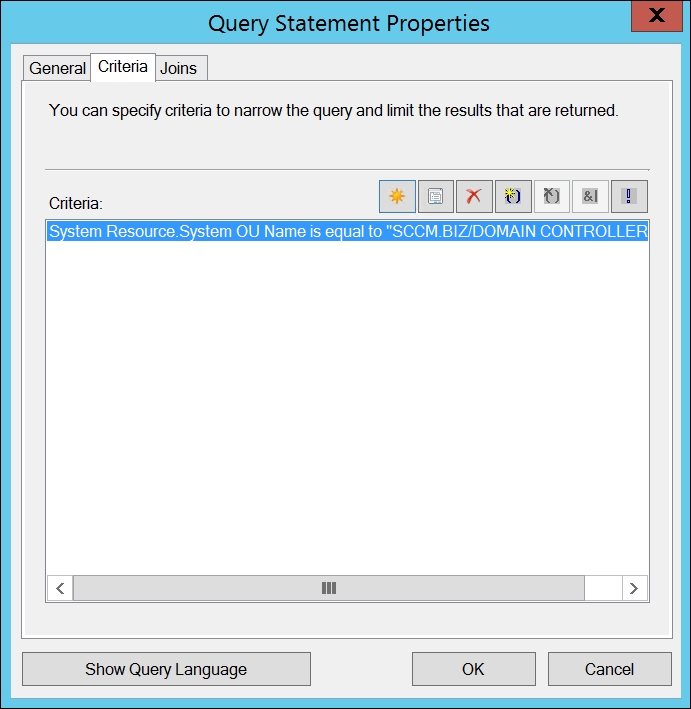
You could create a query on the collection like this to query the Organization Unit (OU), as shown in the following screenshot:

Querying of a Collection for Domain Controllers
For example, we have an Endpoint Protection Policy and we want to target all our Domain Controller servers with this policy. We also want all new Domain Controllers installed later to automatically get this policy as well. We can do this in different ways, but a quick and easy way to do it is to create a collection and query it to target systems that are in the Domain Controller Organization Unit within Active Directory and then target the policy to that OU. The collection will update itself hereafter based on the settings you apply. The default is every seven days, and if you want it updated as fast as possible, you check the incremental update option, which will kick in an update cycle every 10 minutes. Be aware, however, that this option should only be used on a maximum of 200 collections within the Configuration Manager hierarchy. A symptom that may easily occur if a larger number of collections is used is that the update fails, meaning that the content of the collections is not correct and may show as empty, or with a lack of consistency. I've seen this occur where there were around 500 collections with this feature enabled.
But going back to the Endpoint Protection policy, why do we need a dedicated configured policy for our Domain Controllers, Exchange Servers, SQL Servers, and so on? This is a very important question, and is very often overlooked or forgotten. You might not see any obvious symptoms, errors, or faults, but it is recommended by Microsoft that you configure antimalware exclusion settings regardless of what antimalware system you might be running. This is to ensure that nothing will hold, delay, or compromise the application or system running on that server or workstation. For example, on Domain Controllers, it's important that the System Volume (SYSVOL) folder structure is excluded to ensure that domain function and replication are fully functional and work as quickly and smoothly as they should. Different behavior may occur depending on the antimalware product, but I have seen replication issues, as well as slow replication, on servers that are running with real-time scanning on these folders.
It is important to exclude any databases from antimalware real-time scanning. Otherwise, failure, or at least slow database performance and high CPU usage, will occur:
Note
Now Microsoft has a guideline for what folders and processes that should be excluded: https://support.microsoft.com/en-us/kb/943556.
Collection Criteria of the Domain Controllers in Active Directory
It may also be wise to decrease the Schedule a full update on this collection to every day:

Collection update settings
After creating the collection, you will see the hourglass on the icon of the collection working for a few seconds while it's running the update. You can then hit the Refresh button and confirm that it contains what you want.
Then, you deploy the Endpoint Protection to that collection, and you're done, as shown in the following screenshot:
Antimalware policy ready deployment
Keep in mind that the Policy is not effective until its deployed to a targeted collection, and the computer or server has received the new policy. The Configuration Manager database usually needs a few seconds to process, as well. Now, this is one of the things that is essential to understand when working with Configuration Manager, that usually things needs a little bit a patience before it starts to work, because it's a large machinery and many parallel processes going on and they each have their schedule cycle to work with.
Collection choice you have when deploying the Policy
The settings will be applied to the clients on their next Machine Policy Retrieval & Evaluation Cycle. You can view the settings within the Endpoint Protection client GUI:

Actions you have available within the Configuration Manager Properties on the Client
Another way to make a collection is to make a query based on what application is installed on it. The following screenshot shows an example of a SQL 2012 Server query:
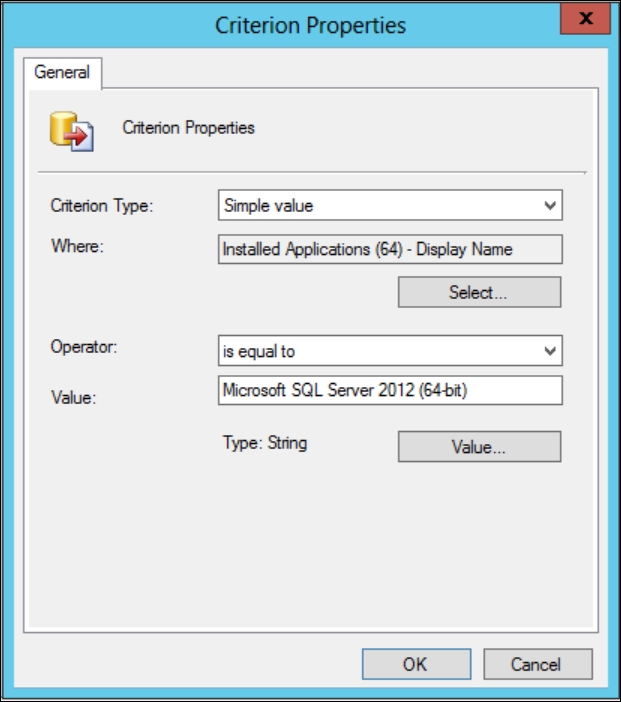
Collection query for Installed Applications Microsoft SQL Server 2012
Collections based on a query will automatically update themselves with new members as more systems with Configuration Manager clients are installed and inventoried.
You could, of course, just create a plain collection with no queries and add systems manually by right-clicking the collection and choosing Add Resources. That would be the easiest and quickest way, but requires a little maintenance. However, I would recommend that you do a little bit of work getting the queries right from the start as a good practice, this will ensure that every server, service or application will have its proper policy to work properly.
In the Introduction to this chapter, you read about the importance of exclusions, especially when it comes to servers, and applications running on servers, such as Active Directory, SQL, Exchange, and so on.
One of the advantages of Endpoint Protection is that it contains several ready-made policies from Microsoft, as shown in the following screenshot:

Import policies provided to you with Configuration Manager
When you click on Import while that you on the Antimalware Policies screen, you can import those xml files that are policies with settings defined by Microsoft best practice.
In the Archive folder, you will find more policies, as shown in the following screenshot:
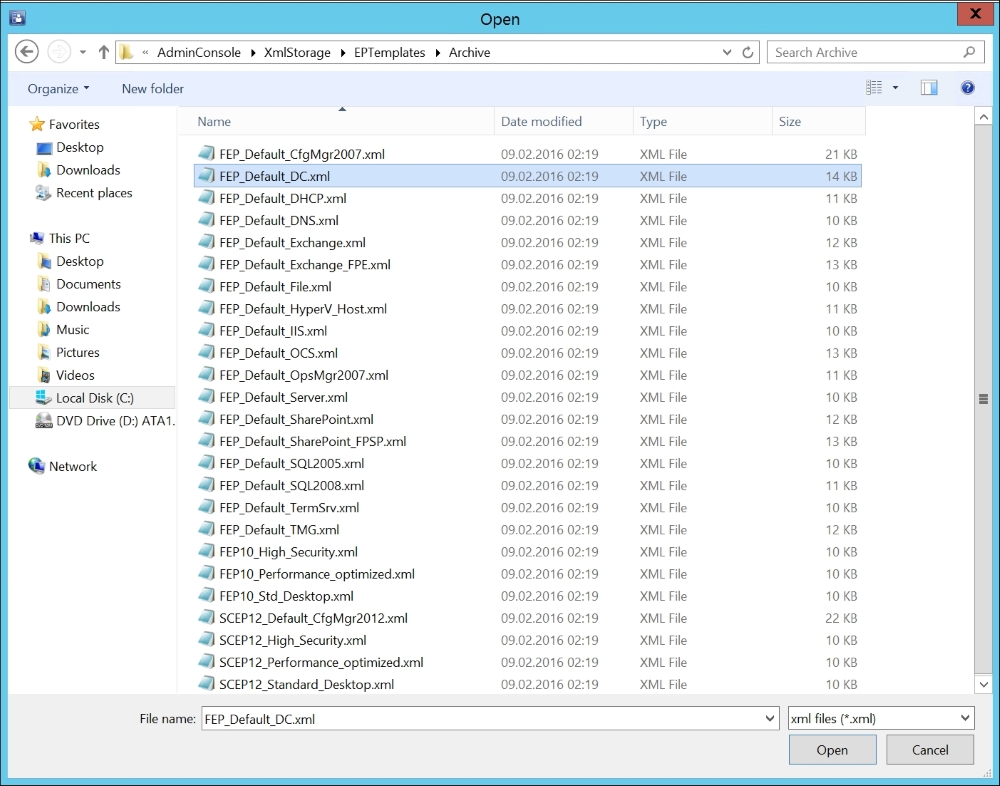
Several policies for the different Windows Server Roles or Applications.
For System Center Operation Manager 2007 and newer, you need to use the FEP_Default_OpsMgr2007.xml policy
For Window Server File Services, you need to use the FEP_Default_File.xml policy.
After importing your chosen policy, you can view the settings. You may find the essential settings in the exclusion section. There might be some settings on file system behavior for File Servers, and so on:

Exclusions the policy for Domain Controllers have
The preceding screenshot shows that the SYSVOL folder is excluded in the DC policy.
Process exclusions are shown in the following screenshot:

Processes excluded in the Domain Controllers policy
You will find similar exclusions in the other policies.
After updating your Configuration Manager Site to version 1602, you will get an improved Endpoint Protection that enables, by default, a new feature called Potentially Unwanted Applications.
This will perform a real-time scan on all .exe files that might have been modified and added such as toolbar, ad-ware, dialer, password stealers, and so on. This is a very new feature that will definitely have uses in every corporation.
The following screenshot shows you the default real-time protection. From version 1602 onward, you have the new Potential Unwanted Applications feature.

The following screenshot shows an example of what you might find being detected and quarantined:
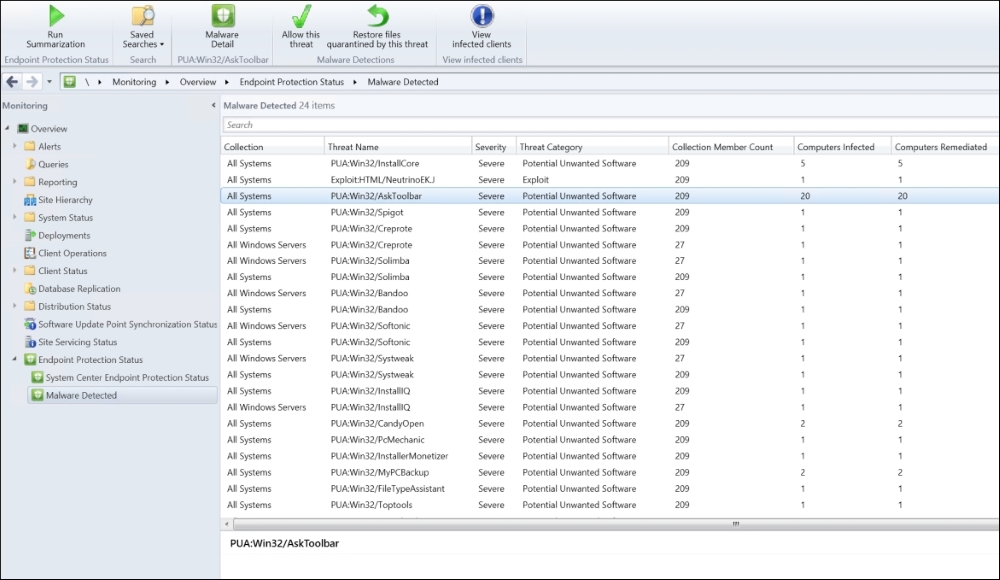
Malware detected in a production environment
