When should we use System Center as a definition source? Microsoft recommends using SCCM as your primary source for updates.
In this recipe we will cover how you can deploy the updates you need to keep Endpoint Protection updated.
First you need to ensure you have the categories correctly set in the SCCM site settings. These settings are forced back to WSUS. There are two categories you need to implement. They are:
System Center Endpoint Protection will get Definition Updates as well as Engine Updates based on these categories.
So just to be clear, engine updates for all Configmgr versions (2007, 1511, 1602, 1606, and so on) will always come under the name System Center 2012 Endpoint Protection.
Now this can be a bit confusing, the category for update settings under Sites is Forefront Endpoint Protection 2010; and engine updates that show up in the console are called Update for System Center Endpoint Protection 2012 Client, even though it's for Endpoint Protection 1511 or newer versions.
The SCEP product has been rebranded as System Center Endpoint Protection. We will go through all these settings with appropriate screenshots.
First we will configure the Software Update Point under Sites components.

Configure Site Components setting
The settings we can define in the Software Update Point component are Sync Settings, Classifications, Products, Sync Schedule, Supersedence Rules, and Languages.
Remember, the settings you define here will impact all Software Update Points within this site's hierarchy.
For the setting following I recommend you use the default setting unless you have specific needs. This will set the WSUS server to synchronize directly from Microsoft Update.

Sync Settings within Software Update Point Component
Regarding Classifications, I've selected the most commonly used. But you should choose those that fit your needs.
For Endpoint Protection you need to have Definition Updates and Critical Updates checked to get engine updates.
Tip
Notice that there is a new Classification called Upgrades. This is for new Windows 10 releases that upgrade the OS to new versions. Another tip here is to check that you have the necessary KB update on your WSUS server before you enable that checkmark. You also need to be using Windows Server 2012.
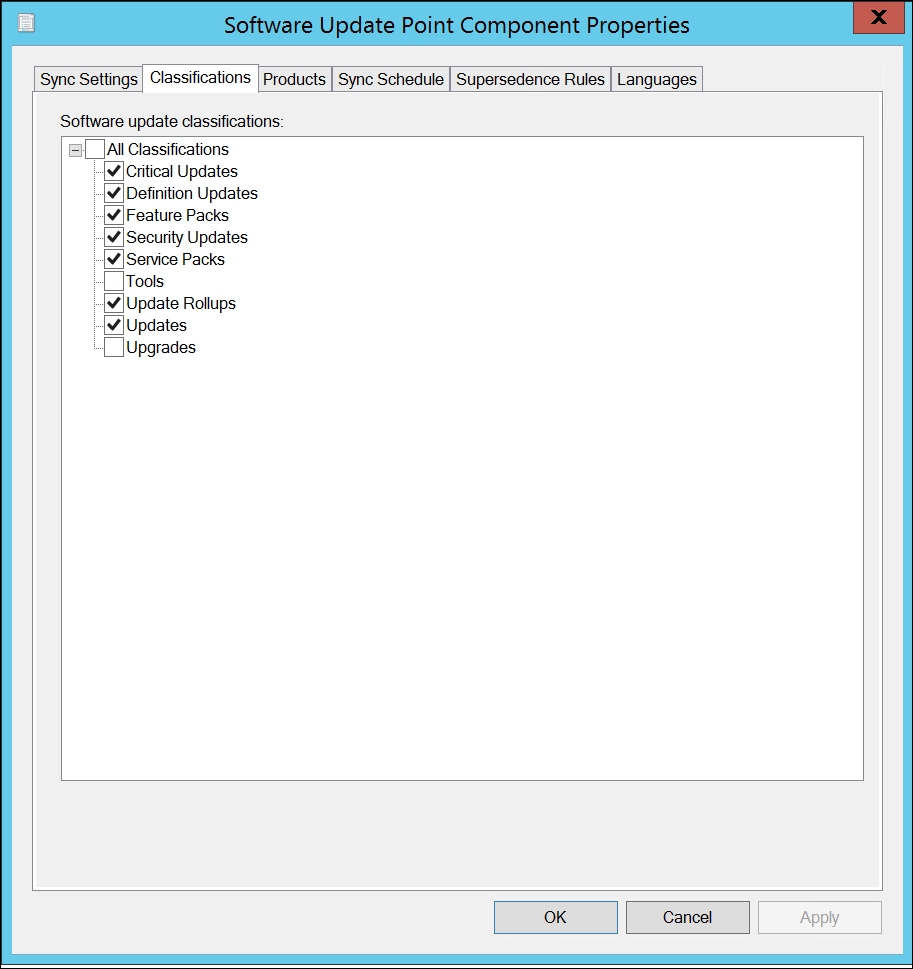
Classifications within the Software Update Point Component
We will define what actual products we want to have metadata about. This means that, when we checkmark products in this, it will not download hundreds of gigabytes of updates (it actually depends of the Automatic Deployment Rules). Taking into consideration that we have that under control, checking products here will make only those updates available for us in the console so that we can download and deploy them.
As mentioned earlier regarding Endpoint Protection, the first Products category we need is called Forefront Endpoint Protection 2010 as shown in the following screenshot:

Products page within the Software Update Point Component
If or when we need to support Windows 10 machines or Windows Server 2016, we need the product category named Windows Defender added to the standalone WSUS or Software Update Point. This will deliver definition updates for Windows Defender that come with Windows 10 and Windows Server 2016 that SCCM will take charge of.
Windows Defender Engine Updates come with Windows 10 updates.
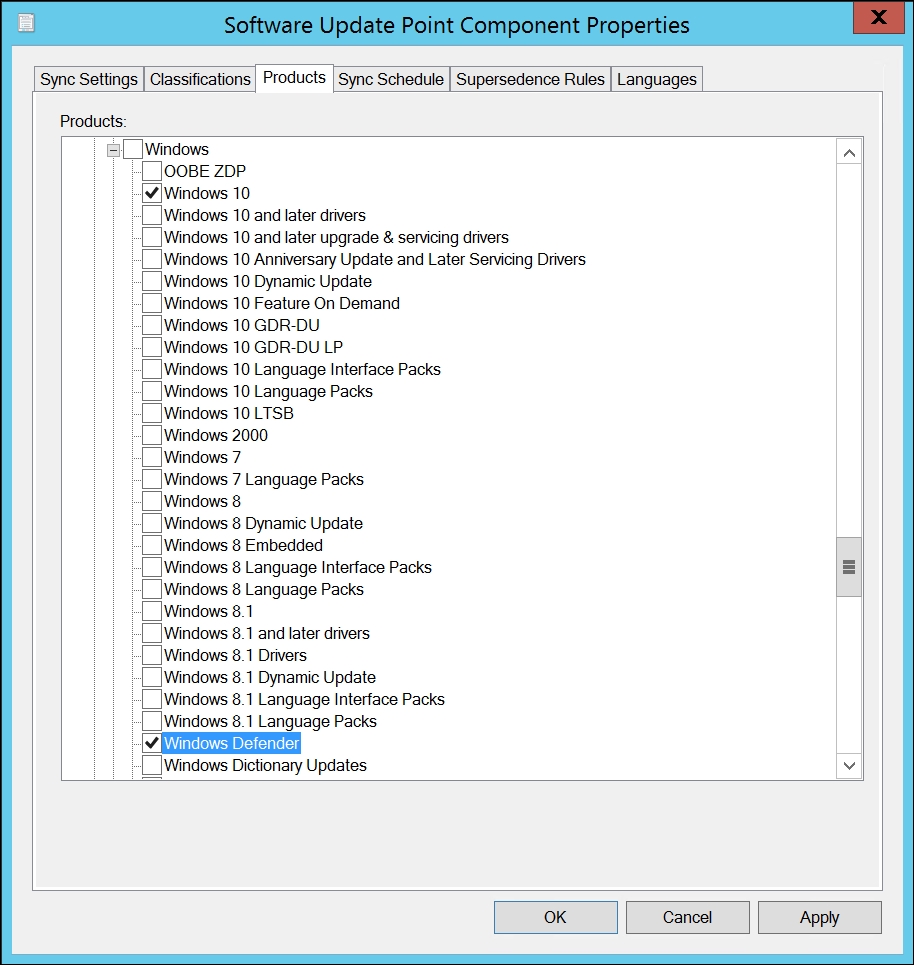
Windows Defender selection in Products
After we are done selecting Classifications and Products we need to define the Sync Schedule.
When we use Endpoint Protection we need to define a more intensive time schedule to ensure clients are as up-date as possible without stressing the infrastructure too much.
Endpoint Protection and Defender definition updates are released, at most, three times a day, and our server has to be told when to go and search for new content.
I recommend you set it to check at least every eight hours, which is usually sufficient. If you want a greater update frequency you can easily set it to every two or four hours instead. This depends on your environment and what business needs.
Remember to checkmark the Alert when synchronization fails on any site in the hierarchy as this is crucial information to know. You can also receive an email about this as we covered earlier.

Sync Schedule within the Software Update Point Component
Supersedence Rules are really more for other kinds of updates, and not Endpoint Protection.
Since Endpoint Protection uses delta files to keep new daily updates at a minimum, you will see updates quickly marked as superseded. You don't have to pay any attention to this: It's just the design and has nothing to do with the following Supersedence Rules setting, which will expire other superseded updates so they can easily be cleaned out.
There is also, from SCCM version 1511, an option to enable Run WSUS cleanup wizard. This will remove expired updates on the next Sync Schedule if the last cleanup is older that 30 days. Previously, you had to do this regularly yourself within the WSUS Console.

Supersedence Rules setting within the Software Update Point Component
The last step is Languages. I recommend keeping languages to a minimum so that Software Update metadata and downloads don't get too chunky.
Regarding Endpoint Protection, all you need check marked is English as shown in the following screenshot.
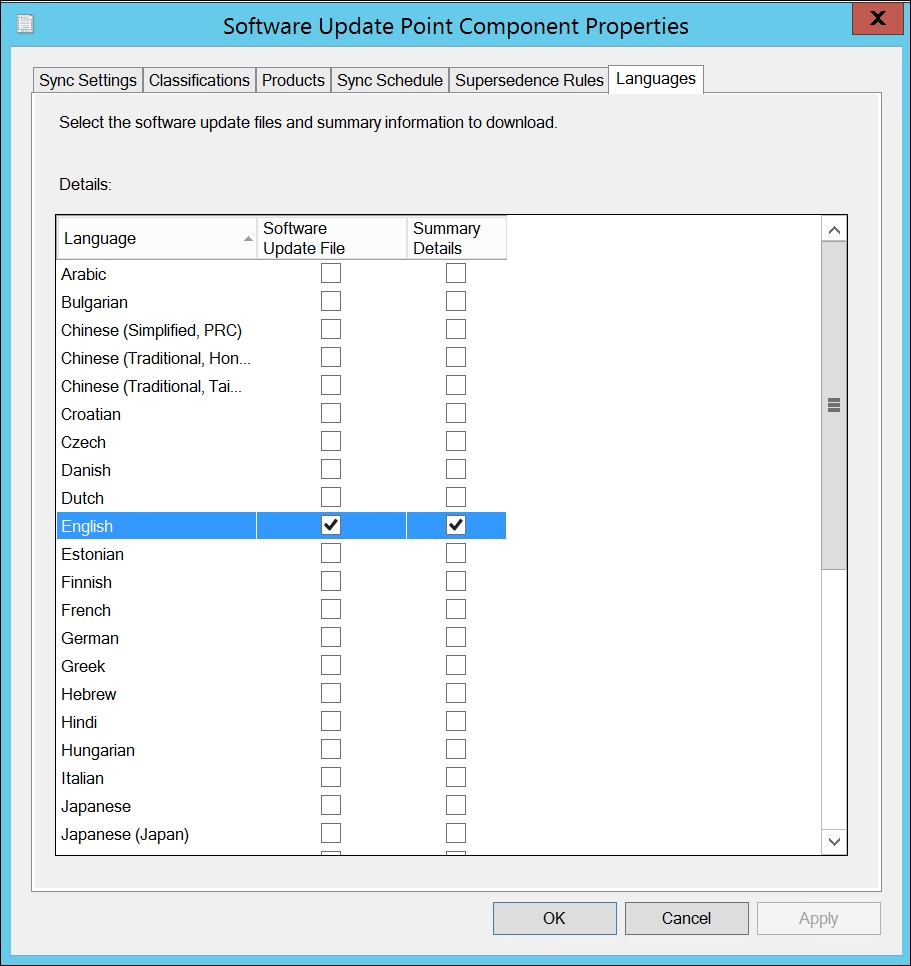
The products will now download on the next scheduled sync.
You can monitor this in the Console | Monitoring | Software Update Point Synchronization.
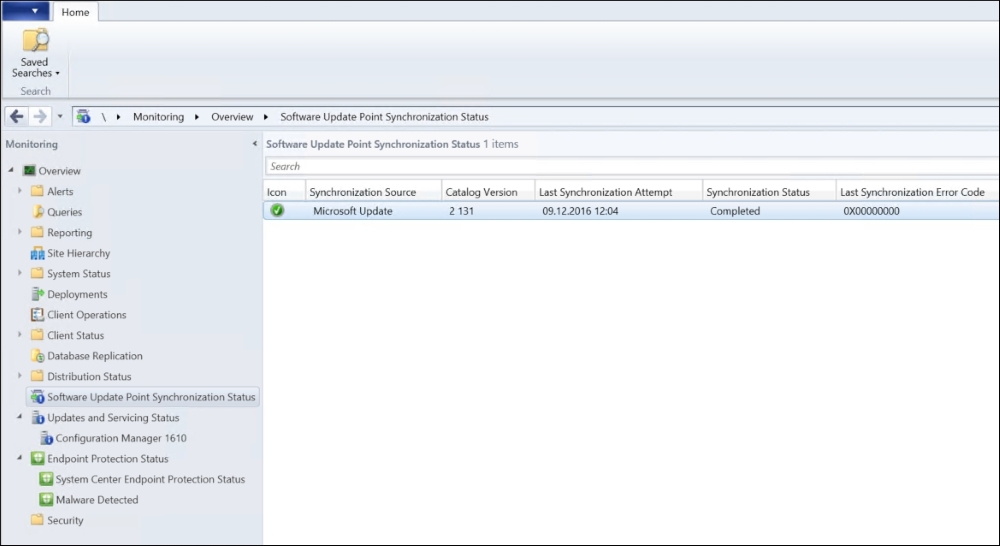
Software Update Point Synchronization status
You can also monitor the synchronization log file, which will give you more detailed information as follows:

When it's finished synchronizing you can verify the sync by searching and viewing updates in the Console by Criteria as shown following:
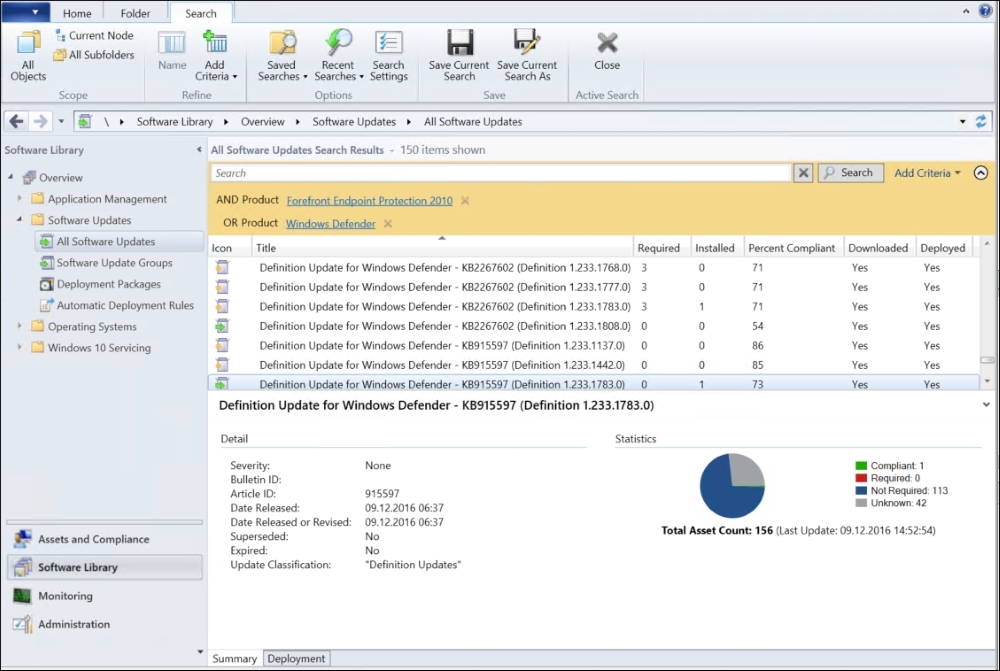
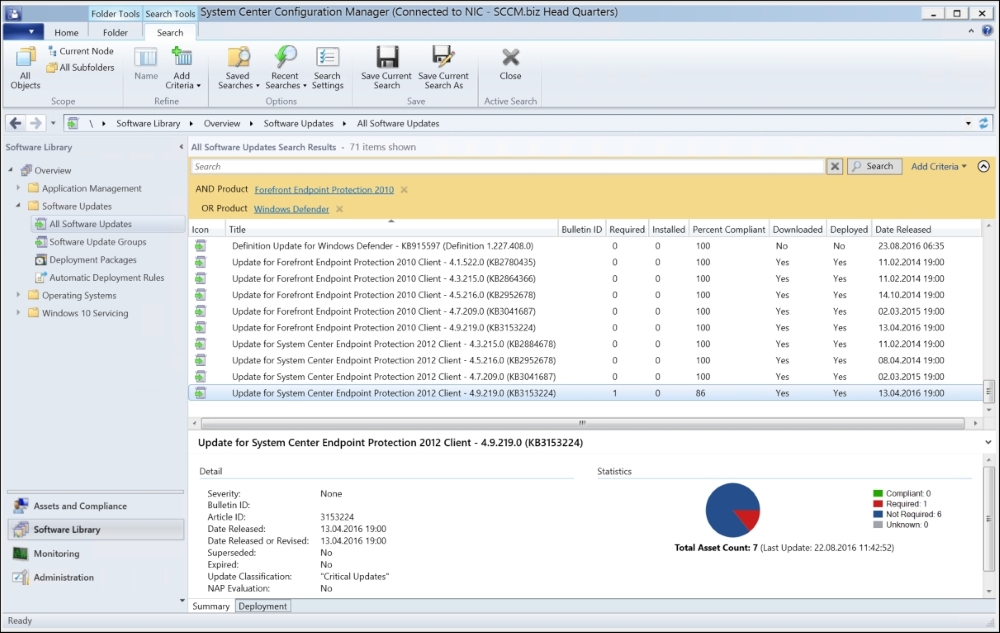
Now that we have verified that the Software Update Point settings are working as we wanted, we can go ahead and deploy the Endpoint Protection updates to the clients.
For that we use the Automatic Deployment Rules.

Automatic Deployment Rules in the SCCM Console
The easiest and fastest way to create an automatic deployment of Endpoint Protection and Windows Defender definition updates is to use the Template named Definition Updates as the picture following shows:
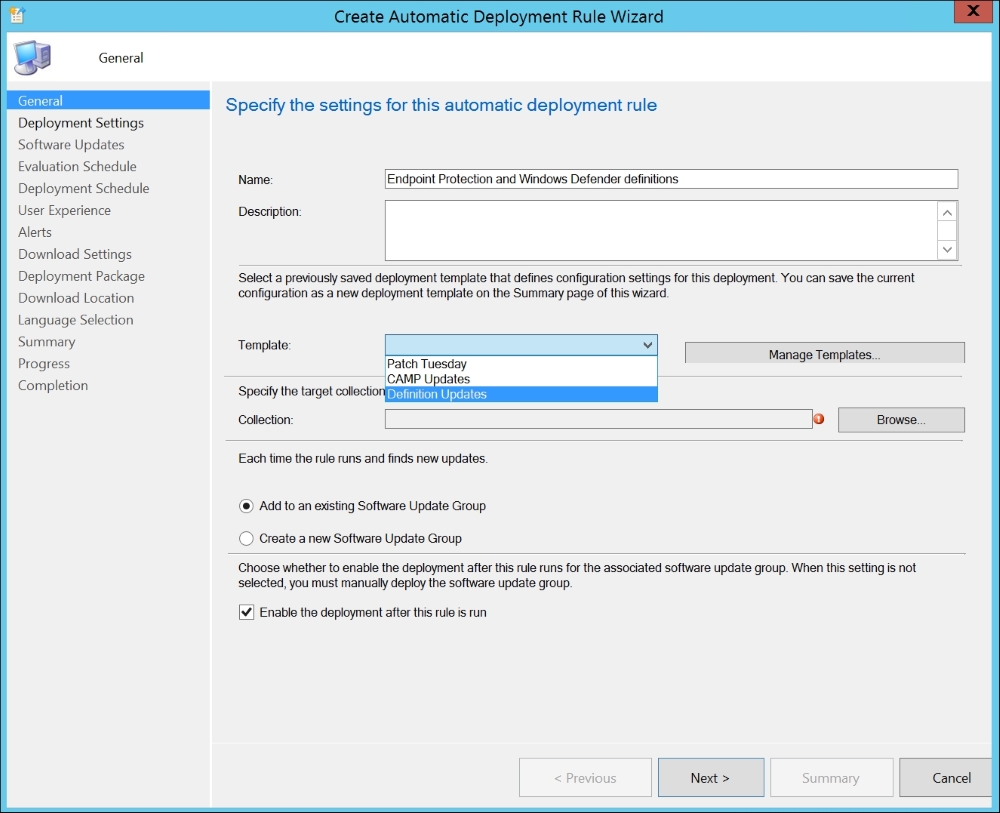
Automatic Deployment Rule Wizard

Product selection within the Automatic Deployment Rule Wizard
You can hit the Preview button to verify what you will get based on the settings you made.
Run the rule after any software update point synchronization is just fine, as we don't want any more delays.
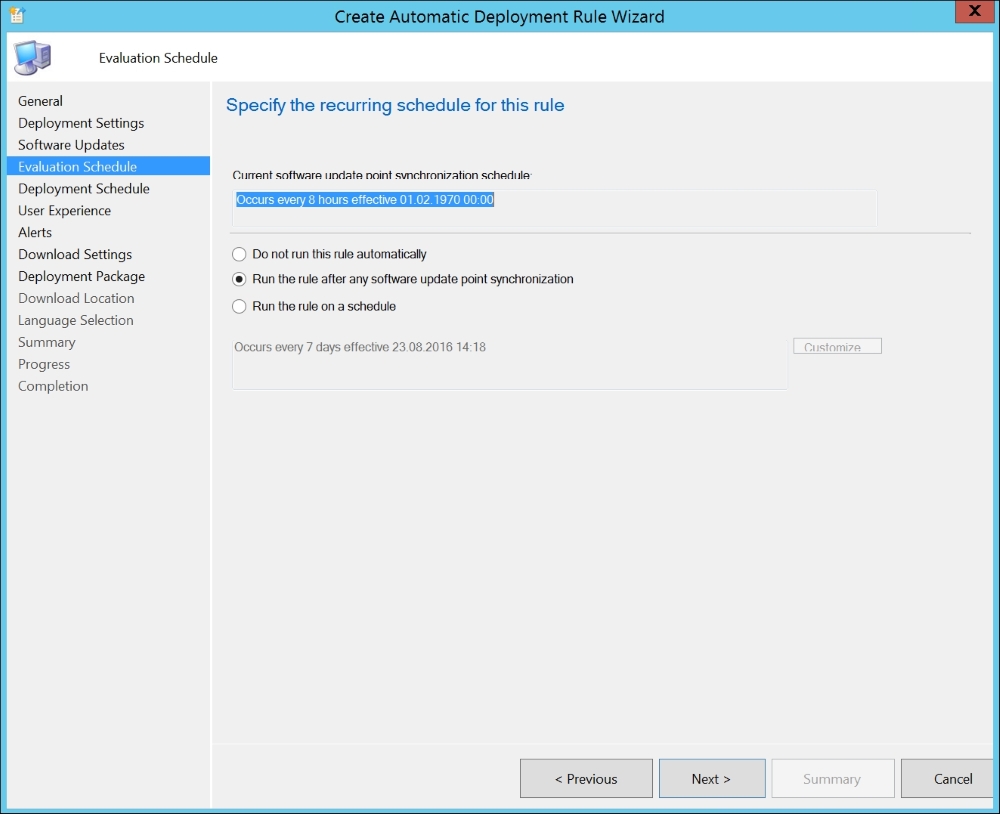
Recurring schedule setting
The default settings schedule for deployment is as follows.
The 1 Hours setting imposes a delay so that all distribution points in your hierarchy have time to get the update before any clients ask for it. Otherwise clients may start to download the update from the possible fallback location or primary site server.
If, however, you have a smaller environment with only one location, or a very high bandwidth connection to all distribution points, you can omit the 1 Hours delay.

Deployment Schedule setting for this rule
Hide in Software Center and all notifications is recommended as we don't usually want to bother users with this kind of information several times a day.
I also select Software Update Installation, in Deadline behavior, to allow updates outside any defined maintenance windows. This is important to remember as we don't want any delays for these important updates.

User Experience setting for this rule
I recommend you have a dedicated package for the Endpoint Protection Definition to keep it as small and tidy as possible since this is often updated.
Define it to replicate with high importance. When it comes to what collections you should deploy it to, that is up to you. I usually just deploy it to All Systems Collection to ensure no one is left out in the dark.
This will have no impact on systems that might not need this update if they have other Antimalware products.
There are exceptions to this: There might be situations when you have clients running another Antimalware product such as Symantec, which will automatically turn off and disable Windows Defender. You can get situations where Windows Updates want to install new definition updates for Defender, but this will fail because Symantec interferes with the process. This will result in a disturbing error message on Windows client machines.
If you are in a situation where you are in the process of replacing your antimalware product or you are running several products, you need to make some adjustments to both the Automatic Rules in Software Updates as well as WSUS.
Another drawback to be aware of is that the Compliance % report on the deployment job will have a lower score. However, I recommend you then use System Center Endpoint Protection Status view under the Monitoring tab in the console as shown following:

Definition Status of Endpoint Protection
