How does Endpoint Protection handle different kinds of malware?
First, it's important that we understand and accept that the world is constantly changing. Everything is in flux and moving forward. With security, malware, and attacks, we have to be on a constant alert. Your security solution may be secure today, but not in a month or a year, meaning that it must be updated and kept under constant surveillance.
So the question that security admins are asking these days is, Are our computers safe and protected from malware and attacks? And what about Ransomware?
Well, unfortunately the protection isn't 100% Why? Simply because we cannot yet predict what new forms malware developers are heading towards. But antimalware products are getting pretty good at sensing harmful code. The newest and latest challenges many businesses are facing these days are Ransomware, the cryptolocker virus. System Center Endpoint Protection or Windows Defender will protect against some of these, but not all. Hopefully Microsoft will be able to fight back even against new variants of these kinds of malware.
That said, I'm not sure there is any antimalware product that will completely protect your computers from Ransom malware today. But there are few doing a better job than Endpoint Protection at the moment. This is something that everyone, I expect, is doing, constantly trying every day to improve their detection and defense.
Ransomware has been a huge problem over the last year now. Ransom malware starts off with a Trojan script that you get either by clicking on an attachment in an e-mail that looks trustworthy, as it appears to be an invoice or post-tracking receipt. You may also get it from a web site, but I believe e-mail has the largest impact, because it also looks like it's coming from someone you trust, or a mailing list you know.
If you don't have a very good antimalware solution for your e-mail this could easily slip through and begin its work without any warning. At this point, what it does is start scanning all your local disk drives, USB sticks, and network drives for all kinds of files. It looks especially for files that might be of great interest to you, such as documents, pictures, and data files. It then starts to rename and encrypt all the files. Then it pops up a message or alters your background picture to let you know that it has taken all your data files and encrypted them. From here on, your data files are taken hostage for money.
All you can do is to pay up or restore the files from a backup. But be sure to get rid of the malware first.
I recommend that you wipe the entire machine as you will never be 100% sure that the machine is completely clean from malware and backdoor software.
Just to give you a picture of what you might be facing, if your file system looks anything like the one shown here, you are probably infected and in deep trouble. My recommendation is to unplug the computer from your network at once.
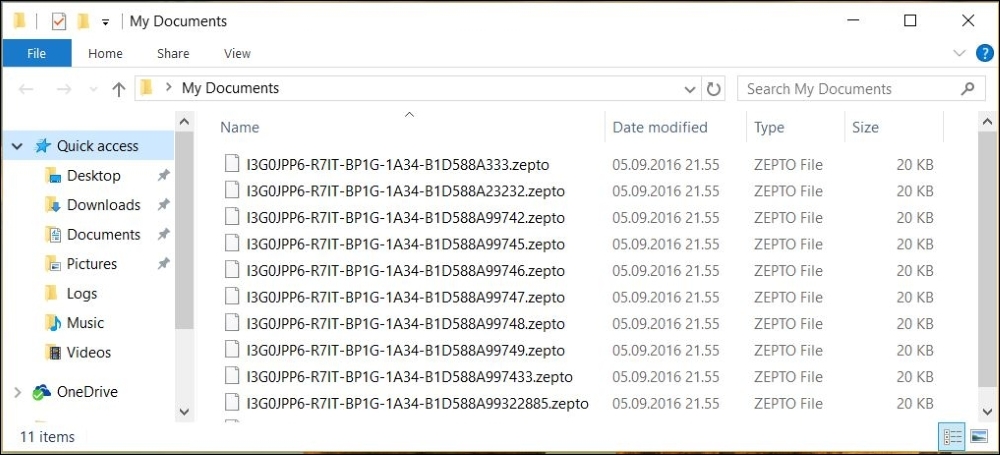
So, is there any way we can protect our computers from Ransom malware? Yes, you can improve your protection further.
First of all, the best way is to constantly learn and instruct your employees about the dangers, what they need to be aware of, and how to operate their machine in a safe way.
As an IT admin of your company you need to ensure you have a good Firewall solution, as well as a good Antimalware solution, for your computers and server. But make sure that you don't forget your antivirus/SPAM solution for E-mail scanning.
You can benefit greatly from utilizing Microsoft AppLocker, which will essentially lock down your computers so that they can only execute a certain set of programs that you have specified.
If you have System Center Configuration Manager (SCCM) established in your organization, there should be very little need for your users to be administrators on their computers. Otherwise, this is considered a huge security risk.
As an administrator, you should offer all the software applications needed in the self-service Application portal to the users. They will be able to install them without being administrators themselves, because SCCM will handle that part from the system account.
And if a program or script needs to be run from a user or from a admin user account then that is possible as well.
So I would recommend that you remove the local admin privileges, and don't deviate from that compliance lightly.
But what about Exploits? We will return to this in the last recipe in this chapter.
Sometimes malware manages to infect Windows in a way that makes it difficult to remove while running Windows in an aesthetically and functionally pleasing way. SCEP or Defender needs to scan Windows system files offline, meaning that it will have to reboot Windows in a secure boot with very limited services running and no startup applications.
With Windows 10 version 1607 and its built-in Defender, you have the ability to very easily do this in Settings | Update & Security | Windows Defender.
This is something every user can do, when needed or instructed to. So far there isn't a way for admins to trigger this from within the SCCM console. To do this you need to remote a Windows 10 machine; the computer will reboot automatically after it's finished scanning. Regarding older platforms, for now you have to either use Microsoft Diagnostics and Recovery Toolset (DaRT) to create a bootable flash disc or USB to boot the infected computer on, or you need to instruct Windows to run MSConfig.exe to tell it to boot into secure mode. You can also simply press F8 as Windows boots up.
But I would recommend having a DART boot medium available, and you might need to put some extra tools on it too. When Microsoft released version 1607, which they named the Anniversary Update, they significantly updated and improved Windows Defender to increase its defense against today's attacks and threats even more. Microsoft will continuously improve and update Windows Defender along with updates for Windows 10, so if you want to keep an optimum level of security, you need to keep your computers as up-to-date as possible. By creating a Windows 10 servicing plan or simply approving the upgrades of the platform, like in version 1607, and deploying that, you need to make sure that you have updated your WSUS with KB3095113 prior to your adding the category and product named Upgrades in your Software Update Point settings.
What about the different Windows 10 builds? Enterprises can choose between Current Branch for Business (CBB) or Long Term Servicing Branch (LTSB). One should really think this through. From a security perspective the recommendation I would give you is to plan and go for CBB, with LTSB as Plan B. What I mean by that is that LTSB should be used for client computers that have very little need to stay current with the latest releases, features, and updates. Those machines will probably just stay on the Local Area Network, and work very little on the Internet. They will most likely not be laptops traveling around and plugging in to all kinds of networks. Therefore, CBB will be the most secure platform release to stay on, but will require more rapid servicing and updates from the administrator.
Another rule of thumb is that, if you plan to deploy Microsoft Office to your machines, you most likely need the CBB version of Windows 10.
There are several huge components within Windows 10 that Microsoft constantly works to make more secure, while also working to improve their performance and usability. Its comprehensive threat resistance consists of a combination of Windows Firewall, Windows Defender, Device Guard, Microsoft Edge, SmartScreen, and Office ATP. Office Advanced Threat Protection (ATP) requires Enterprise E5 licensing.
SmartScreen actually blocks around 97% of all known threats trying to breach Internet Explorer and Microsoft Edge. Another thing to keep in mind when running SCEP or Windows Defender is that the interactive module for the Internet browser does not work on all kinds of system. Does my SCEP or Windows Defender scan downloads before they are run or not? It works very well with Internet Explorer and Microsoft Edge, of course, and also with Google Chrome, but it does not work in Mozilla Firefox. So if you're running Firefox in your organization, be aware of this issue.
Microsoft Edge is currently a less attractive target to attack with its available vulnerabilities than other well-known browsers.
That said, how do we handle malware?
From my experience, System Center Endpoint Protection and Windows Defender, in most cases, find malware on their own, and require very little work or attention from the administrator. It does not bother the user or the admin unnecessarily. This is great, as we don't want a lot of unnecessary warnings and alerts if it's considered not to be a great risk for the environment. As mentioned earlier in previous chapters, you can define on what level you want to be alerted in the Console and e-mail alerts.
Perhaps you do want to know about all the detected malware so that you can be very well informed about what's going on, and for peace of mind.
Often, however, administrators have several roles and responsibilities in the company, and they only want to be alerted about critical stuff. They don't want to be bothered otherwise.
Perhaps you might consider having different levels of alerts. For example, if Malware is found on certain servers such as Domain Controllers, Exchange Servers, and other important servers, you need to be aware of this, because then there might be someone who is operating a bit carelessly. I would strongly advise an admin to not use a Domain Admin's account, or an Administrator of the domain to not download content from the Internet or for that matter do any Internet browsing with a Domain Admins rights account. For security reasons, you should rename the Administrator default account for the domain. It is still possible to figure this out if you are clever, but it's slightly more hidden from potential attacks. The password should be strong, long, and difficult, and the account should not need to be used.
Large enterprises use delegation between Organizational Units (OU) and delegate needed rights to Admins. For Group Policy Management, you might want to look closer at Advanced Group Policy Management (AGMP) in the Microsoft Desktop Optimization Pack. You can refer to it in the following URL: https://technet.microsoft.com/en-us/windows/mdop.aspx.
With the AGMP you will gain more control and security with whatever changes are made in the Active Directory Group Policy. Admins that edit and create Group Policies need to check in the policy with their user, and policies can be rolled back with ease if something has gone wrong. You can have admins that approve it before it's applied, but the most important thing to remember is that it's all logged so you know what and whom to go and see. Another benefit is that the admx template content files are stored centrally and only need to be updated and added once.
But what can we do with malware that is found by System Center Endpoint Protection or Windows Defender?
If we first take a look at the Console in the Monitoring section, we can see what's found and how it's automatically handled.
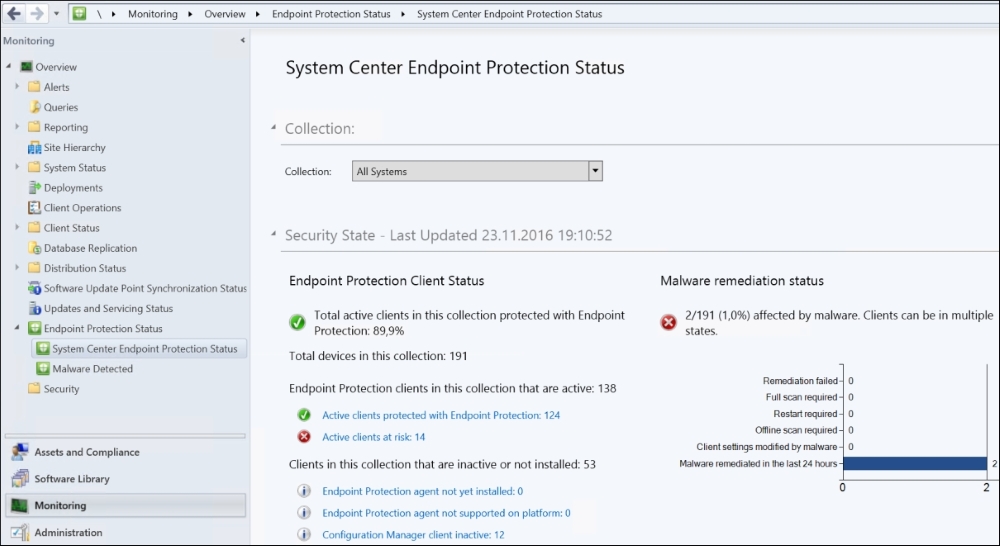
System Center Endpoint Protection status
As you see, to the right of the screenshot, we have Remediation failed, Offline scan required, and Client settings modified by malware. Those are areas we need to pay attention to. We don't want to see a lot of machines in those. But so far, over the past years and across different environments, I have not experienced many computers in these categories, and that is good. It means that SCEP and Defender are doing their job and protecting computers from being infected very well.
But the area on the left, Active clients at risk: .., is nearly never at a zero count. We have covered this topic in the previous chapter, and it is important for you to deal with.
A good rule many companies have implemented is that if they have a computer constantly infected with malware, they notify the user of it, and mostly, on 9 out of 10 occasions, they just reformat the disks and perform a fresh install. It's much less work to do this when you have a System Center Configuration Manager OS deployment in place.
Also on the same System Center Endpoint Protection Status page we can easily monitor the top 5 types of malware based on the number of computers that the malware is found on. This will give us good information about the most common types of malware our business computers are encountering right now. The following screenshot shows you an example of this:
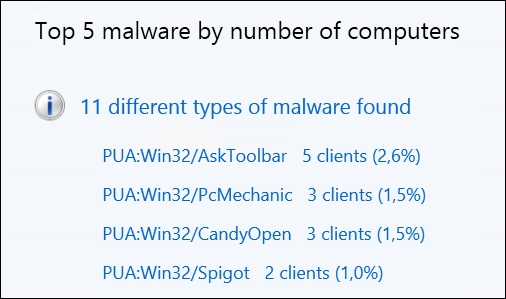
The Top 5 types of malware found
You can figure out the user that was involved in the malware infection from the SCCM console very easily. Usually the user also gets a heads-up in how to operate their machine more safely.
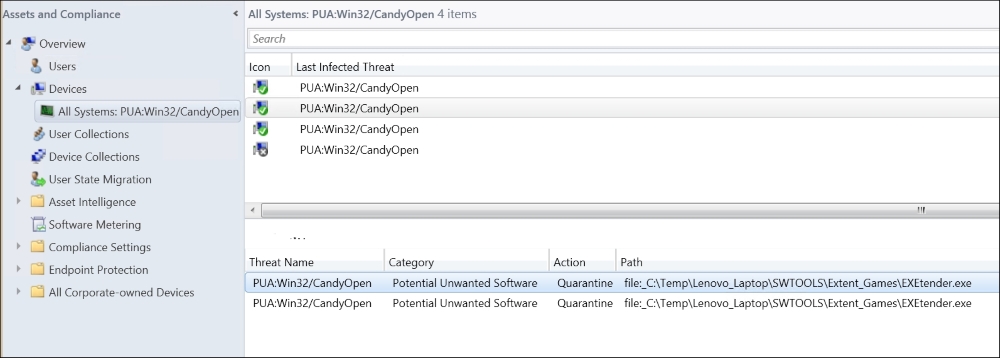
Malware information given in the SCCM Console
Another benefit of just wiping the local disks of the infected machines is that you never know for sure how deep the infection is and what else could be there, hidden.
A dangerous situation is where the Domain Admins log on to a machine that a user reports as having trouble. Perhaps it is running slowly, cannot log on correctly, has applications that keep crashing, or windows that pop up occasionally. Perhaps the user has also ignored malware information messages. The Domain Admins log on and this is where the malware snaps the login information and benefits from the Admins login credentials to spread itself among the infrastructure.
So, therefore it's important for you to gain as much information through the SCCM console as possible, and try to resolve the issue remotely, before you find the need to take physical action on the infected computer.
The actions you have available within the SCCM Console are a Full Scan, Quick Scan, or Download Definition for one machine or several machines.

Endpoint Protection actions you can set in action.
The action you will most likely be using is Full Scan, if you encounter a machine that is troublesome and repeatedly discover malware on it.
But as has been said, if it often or continually pops up malware warnings, you will probably want to wipe it and re-install Windows.
Users should be instructed to store important work on server locations so that nothing is lost if the machines are broken, stolen, or infected. To prevent your laptops as well as Workstations from being physically stolen and corporate data lost to criminals or industrial espionage, you might benefit from using Microsoft BitLocker. It's fast, safe, and easy to use. As you probably have seen as an SCCM admin, you can set it and enable it on appropriate computers with SCCM. But just to be clear, BitLocker does not protect your data from Malware, Ransomware, or any similar programs. It protects your data from being physically stolen if you should lose your computer or it is stolen. With BitLocker enabled, the data on the local hard drive is safe if someone should try to break into it and try to extract the data. You would need the pin code and password to enter a Windows OS that owns the Trusted Platform Module (TPM), which has the decryption key to open the files on the hard drive.
You might want to learn as much as possible about the malware in question. Now, you don't have to remember the correct name and Google it. All you have to do is hit the button; Microsoft has made this available for you within the SCCM Console.
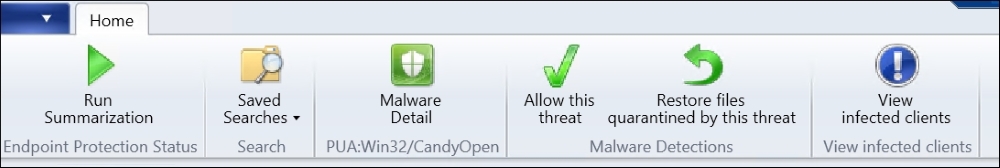
The previous screenshot shows you buttons and information available for you in the SCCM console when you click on a client machine.
When you hit the button named Malware Detail, you are automatically presented with a web browser that immediately takes you to the Malware Protection Center at Microsoft.
This will present information you need to know about the malware, and you can easily Google more information from there if needed.
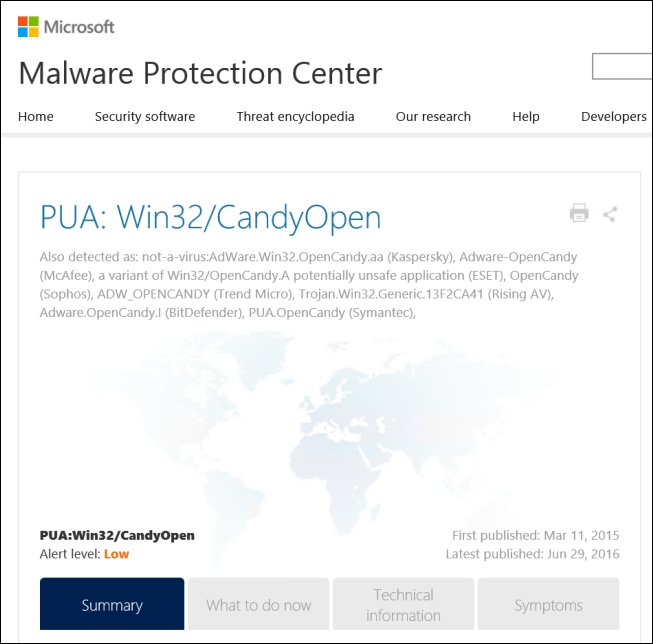
The preceding picture shows you the Malware Protection Center that the SCCM Console button Malware Detail presents to you. You might need further manual removal instructions if there are some infections that SCEP and Defender does not manage to remove by themselves.
But remember to try an offline scan as well. With the cloud feature enabled, you might see that it will be resolved later on, as Microsoft has treated this new malware in the cloud and the clients are downloading removal instructions for it.
If you manually want to submit a sample of some files that you want Microsoft to investigate, upload it at the Malware Protection Center page: https://www.microsoft.com/en-us/security/portal/submission/submit.aspx.

Malware Protection Center
