If you don't want to go as far as implementing AppLocker as described in the preceding recipe, there is another method that you can consider.
We will look into how to protect your computers with more tools than System Center Endpoint Protection will give you. We will be looking at scenarios for the Enhanced Mitigation Experience Toolkit (EMET).
Another possibility that we can investigate is simply blocking certain file extensions that all known cryptolocker and ransomware programs use, such as .locky, and .zepto. Later in this chapter I will show you how you can achieve this.
First, Exploits need some explaining.
These are vulnerability holes in software installed on computers. Malware can slip through the antimalware solution and then has the ability to take advantage of and use these vulnerabilities to exploit how the software works; it can then figure out a way to infect computers concealed from the antimalware software.
This is an increasingly common form of malware attack these days, and you need to know how to handle it and protect your computers in the best way you can.
We have all read or heard about security vulnerabilities with Java and Adobe Flashplayer, to mention the two most affected software programs.
Why are these more exposed than others? Is it because they are weak and poorly built? No. It's simply because those applications are, globally, the most installed software , and therefore they have a huge potential as a target. It is also a fact that these kinds of application are not updated frequently enough, and the attackers take advantage of this.
So, in other words, the best way to protect your computers from Exploits is to keep them updated as rapidly and frequently as you can, if possible, by simply keeping an eye out for when there are new versions available, and downloading and deploying them.
I would also recommend using the free System Center Update Publisher (SCUP), or another third-party product that can integrate into SCCM. These cost money, but will give you more important features as well. There are several good alternatives that will also give you a live heads-up about malware risks, such as Secunia Patch Management.
It's also important that you keep all your other Microsoft software up to date with WSUS or Software Update.
A good tip that you could do right now is to go to your console in SCCM and do a search in Software Updates for whatever product updates computers require but you haven't deployed. Do this now, and you might just be surprised to find out that you left out something in your Automatic Deployment Rules.
But what if we want to protect our workstation computers even more from Exploits? There is a Microsoft Toolkit named Microsoft Enhanced Mitigation Experience Toolkit (EMET). This is a supplemental security defense tool to protect potential vulnerable applications.
It's free and works on all supported Windows platforms, and Microsoft recommends it particularly for Enterprise customers to protect applications running on old platforms, such as Windows XP, as this Windows version has huge security deficiencies compared to the newer Operating Systems.
Another tip for you to keep in mind is that 64-bit versions of Windows are more secure than 32-bit ones; in fact, the EMET security features are more comprehensive and work better on a 64-bit platform as well. There is also the fact that many kinds of malware do not work so well with 64-bit, so my suggestion to you is that when your organization is doing an OS deployment to a new release, consider always making it 64-bit by checking all applications, printers, integrations, and hardware drivers. One other point is that 64-bit Windows requires at least one additional gigabyte of memory more than 32-bit versions.
The sad part when dealing with the OS upgrade is that you cannot upgrade from 32-bit to 64-bit; not even with the Windows 10 upgrade in place, which is simply a fantastic piece of work. You have to do a new fresh install. No other Windows upgrade has been more successful in my opinion. Now you can even upgrade Windows Server successfully. But I recommend that you do that with great care and with a full backup in advance.
EMET has been there for several years now, but maybe not everyone has heard about it. The current version uses no fewer than 12 mitigation techniques to detect and block Exploits, which will make it harder for attackers to find a way to infect your computers. Most of these techniques are very much involved in protecting memory from corruption, such as data execution prevention, mandatory address space randomization, and structured exception handling.
Note
You can download EMET from this link, and you can control and deploy Group Policy to handle the configuration in your Enterprise: https://www.microsoft.com/en-us/download/details.aspx?id=50766.
EMET User Guide: https://www.microsoft.com/en-us/download/details.aspx?id=50802.
The following screenshot shows you the options you have when installing EMET:
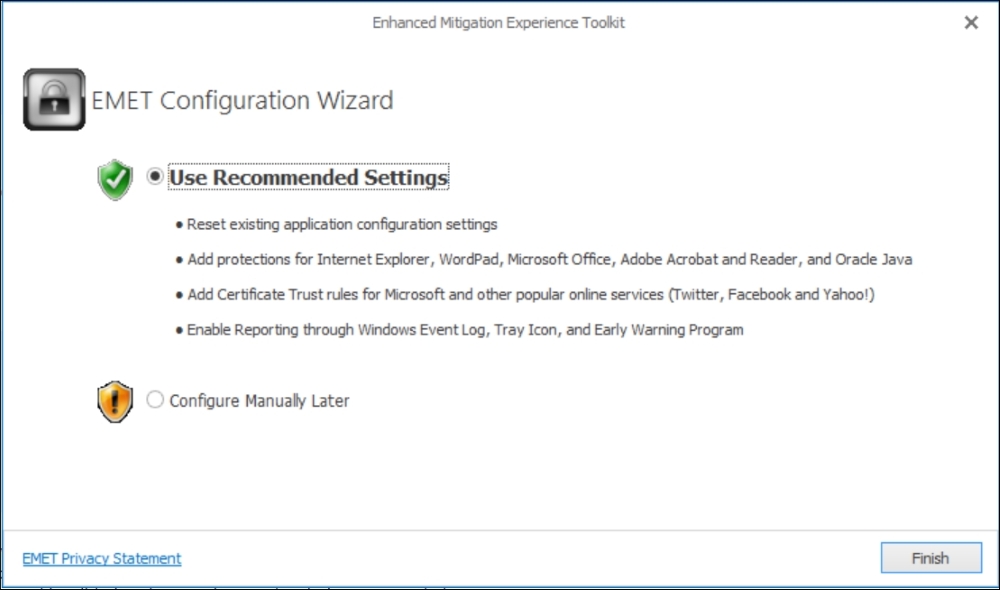
The following screenshot shows you the EMET GUI and the applications it has found installed on the computer:

If an application is being blocked by EMET for whatever security reason, the user will get a message box like the one following:

The following settings are the default EMET settings. Data Execution Prevention (DEP) is, as you can see, set to Application Opt In or Application Opt Out for maximum security. But be aware that this may prevent applications from working properly. I would recommend you try this with care and not on a mass scale. Leave it set to the default, or create opt-out rules for applications that will simply not work with EMET. Another great feature is Audit only, which will only log events, so you can monitor them better before starting to secure and block.
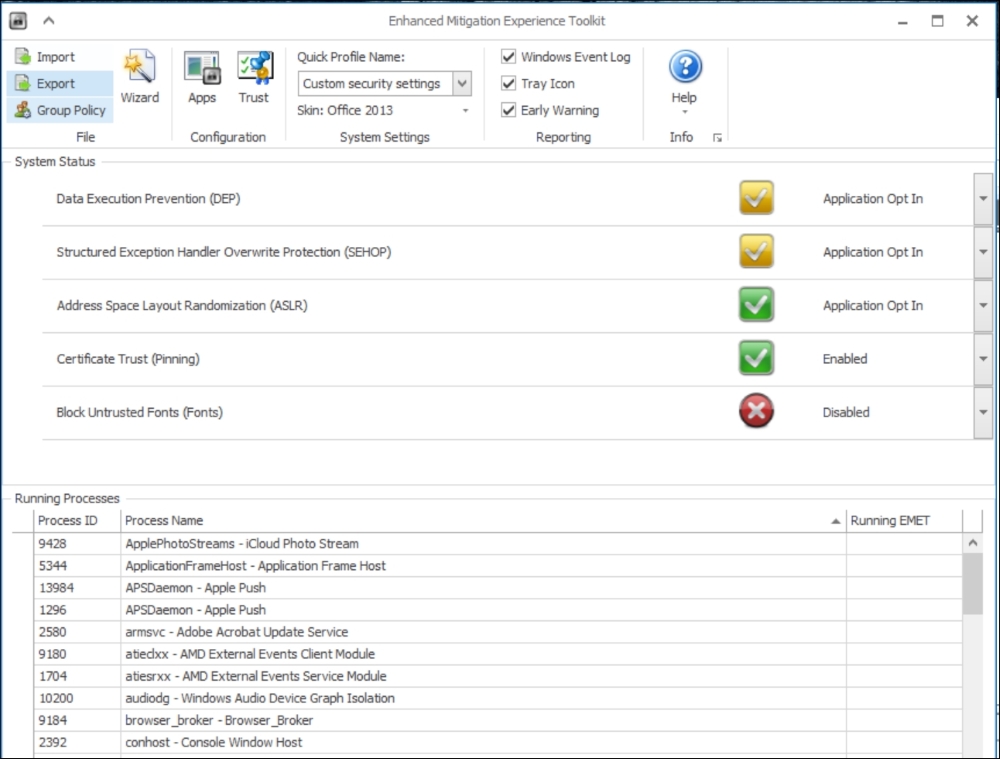
The preceding picture shows you the default settings for the EMET GUI. The events are logged by EMET to the application log in the Windows Event log.
With this you have the ability to monitor using System Center Operation Manager or another monitoring solution that connects to the Windows Event log.
Power BI is approaching the standards of SCCM, Intune, and Windows 10. It is really neat for the Administrators to put up on a big screen to give you important information specific to your environments and needs; it can clearly display, for example, the Windows Update status of my clients, or how my deployments are doing, or my antimalware status, or my current EMET attacks status, and so on.
This is the kind of information that is easy to forget about, given that you only look at it when something is wrong. But what if you could prevent huge faults, errors, outbreaks, and attacks by having a better monitoring solution or a good Power BI view to keep a daily eye on it all?
Would there be a risk if I look away from it for a while?
Well let's say you have a user who receives a suspicious e-mail; just by clicking once on the e-mail with the preview pane on the right, the computer gets infected with an Exploit malware. This could very well be a Ransom malware, encrypting all the user's data files.
If you are using BitLocker, be aware of this. When implementing EMET, you need to suspend BitLocker. There have been issues with this, so please follow the suggestions by running some PowerShell commands and then follow the further instructions shown in this article at Microsoft: https://support.microsoft.com/en-us/kb/2458544.
I think we will, in the near future, see that more and more apps will be running in virtualized environments, so that malware will not be able to cause so much harm to the environment and Operating System.
It is important to make clear that this solution will only block known file types. We know that Cryptolocker will try to rename the data files to a given file type name extension, for example .ZEPTO or .CRYPTO to mention a few.
So, it's vital that the Server will be updated with new file types in future. But by doing this right now could prevent your business data from being lost, and save yourself a lot of work.
The following PowerShell Script will work on Windows Server 2012 or newer versions. It will install the Windows feature named File Server Resource Manager if it's not already installed.
--------- $a = gwmi win32_logicaldisk -filter DriveType=3 | Select -ExpandProperty DeviceID install-windowsfeature -name FS-Resource-Manager -IncludeManagementTools Import-Module Servermanager New-FsrmFileGroup -name "CryptoWall" -IncludePattern @("*.ecc","*.ezz","*.exx","*.zzz","*.xyz","*.aaa","*.abc","*.ccc","*.vvv","*.xxx","*.ttt","*.micro","*.encrypted","*.locked","*.crypto","*._crypt","*.crinf","*.r5a","*.XRNT","*.XTBL","*.crypt","*.R16M01D05","*.pzdc","*.good","*.LOL!","*.OMG!","*.RDM","*.RRK","*.encryptedRSA","*.crjoker","*.EnCiPhErEd","*.LeChiffre","*.keybtc@inbox_com","*.0x0","*.bleep","*.1999","*.vault","*.HA3","*.toxcrypt","*.magic","*.SUPERCRYPT","*.CTBL","*.CTB2","*.locky","*.zepto") foreach ($i in $a){ $Notification = New-FsrmAction -Type Event -EventType Warning -Body "User [Source Io Owner] attempted to save [Source File Path] to [File Screen Path] on the [Server] server. This file is in the [Violated File Group] file group. This file could be a marker for malware infection, and should be investigated immediately." -RunlimitInterval 30 New-FsrmFileScreen -Path "$i" -Active: $true -IncludeGroup "CryptoWall" -Notification $Notification } $a = gwmi win32_logicaldisk -filter DriveType=3 | Select -ExpandProperty DeviceID install-windowsfeature -name FS-Resource-Manager -IncludeManagementTools Import-Module Servermanager ;New-FsrmFileGroup -name "CryptoWall" New-FsrmFileGroup -name "CryptoWall" -IncludePattern @("*.ecc","*.ezz","*.exx","*.zzz","*.xyz","*.aaa","*.abc","*.ccc","*.vvv","*.xxx","*.ttt","*.micro","*.encrypted","*.locked","*.crypto","*._crypt","*.crinf","*.r5a","*.XRNT","*.XTBL","*.crypt","*.R16M01D05","*.pzdc","*.good","*.LOL!","*.OMG!","*.RDM","*.RRK","*.encryptedRSA","*.crjoker","*.EnCiPhErEd","*.LeChiffre","*.keybtc@inbox_com","*.0x0","*.bleep","*.1999","*.vault","*.HA3","*.toxcrypt","*.magic","*.SUPERCRYPT","*.CTBL","*.CTB2","*.locky","*.zepto") foreach ($i in $a){ $Notification = New-FsrmAction -Type Event -EventType Warning -Body "User [Source Io Owner] attempted to save [Source File Path] to [File Screen Path] on the [Server] server. This file is in the [Violated File Group] file group. This file could be a marker for malware infection, and should be investigated immediately." -RunlimitInterval 30 New-FsrmFileScreen -Path "$i" -Active: $true -IncludeGroup "CryptoWall" -Notification $Notification } -------------
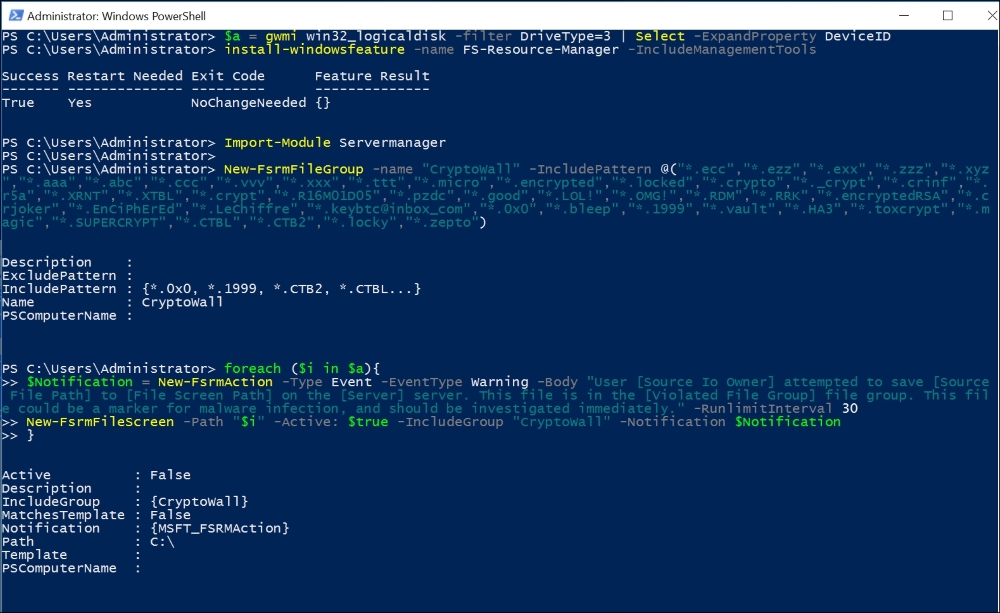
PowerShell Script after running successfully on a Windows Server 2016
Now we have managed to install the File Resource feature and defined the File Group rules with known Cryptolocker file types. No guarantees are given with this; you must ensure that the file types don't conflict with your environment and needs.

File Server Resource Manager with the new CryptoWall File Group created containing known file types.
As you can see from the script, we have only enabled Notification alerts if any of these file types are created on Drive C:.
You can view notifications in the Application log from within Windows Event Viewer.
So, we don't block anything yet.
The next step is to define a File Screen Template CryptoWall and, as you see in the following screenshot you need to define a File screen path to whichever folder or drive you want to block these file types on, and choose the CryptoWall template.
You can modify the preceding PowerShell Script if you want to automate this last part, and run it on several Windows Servers.
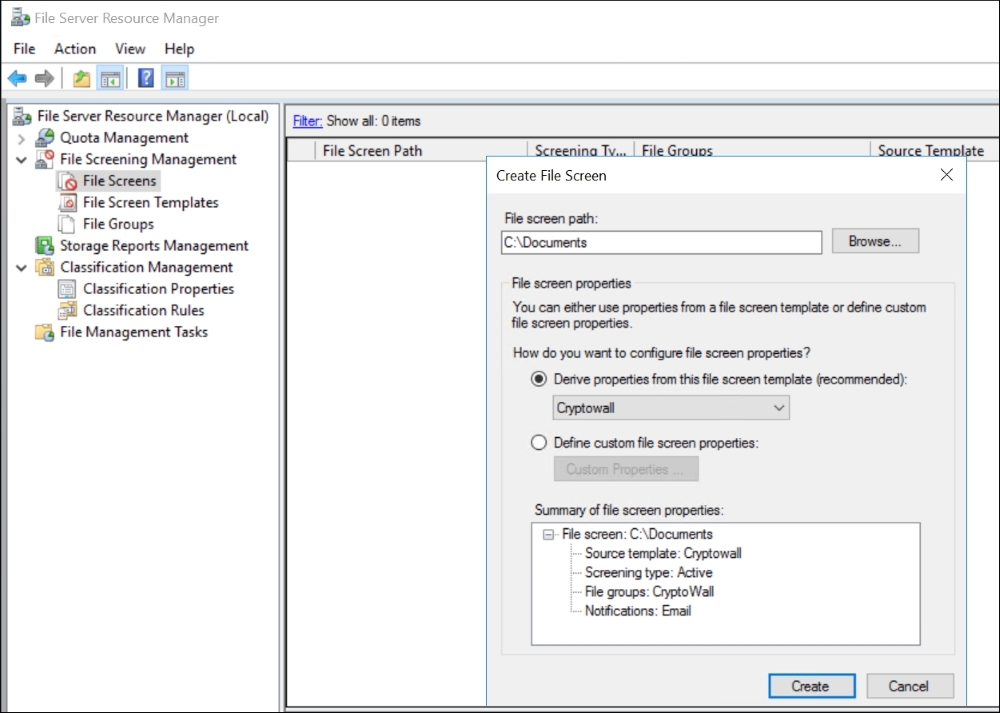
File Server Resource Manager with the creation of a File Screen rule
Another smart thing to do is to set up and configure Email alerts on this, so you know if there are any outbreaks or attempts. You configure this within the same console in the File Server Resource Manager.

When you try to create a file with any of those file type extensions, you should receive the previous message.
That's it!
