When it comes to Firewall, System Center Endpoint Protection has no built-in firewall of its own; it mostly relies on Windows Firewall doing the job. Now, you might think the Windows Firewall is not good enough to protect your computers. With Windows XP, and even Windows 7, it is true that the firewall was maybe not top-notch and had room for improvement, but when Microsoft released the new platform Windows 8, and from there on up, it was a whole new matter. These systems included a brand-new Firewall with more advanced features, which has just kept improving as it has evolved.
That said, System Center Endpoint Protection has its own built-in features, like most of its competitors, for detecting and protecting against network exploits and massive attacks. This is important, as I often see customers running their Windows Server and workstations with the Windows Firewall switched OFF while in the Domain profile, and only switched ON with the Public Networks profile. Now, it's highly recommended by Microsoft and security specialists to have your Windows Firewall turned ON at all times on both workstations and servers, no matter how many firewalls you might have between your internal network and the Internet. Having it turned on will give you monitoring as well, and logging that might be useful so that you can pick up and detect network traffic on your servers that shouldn't actually be there. Using System Center Operation Manager or the cloud product, Operation Management Suite, as an example, you will be able to pick up that kind of information pretty easily if you're running with your Windows Firewall switched ON.
You can, of course, run another Firewall product on your workstations if you like. Just make the appropriate rule exception for System Center Configuration Manager Client and any other applications and management tools you might have.
Let's have a closer look at what we can do.
Group Policy Forcing Firewall settings are most commonly used as compared to OU or Security Groups. That is a simple and force full solution to make the Firewall configuration. Since 2012, you now have the ability to deploy this as a configuration as well. But why use this feature in System Center Configuration Manager?
Well, for one, it will give you the benefit of monitoring the results and more deployment flexibility within your organization. This means that you can deploy this Firewall configuration to any kind of targeted machine, as long as it has the Configuration Manager client installed and running. As mentioned earlier, Collections are based on many kinds of criteria such as, domains, computer model information, kind of role, IP subnet, naming, installed application information just to name a few. You might also catch some machines that someone has moved out of the OU where you specified the Group Policy that configures the Windows Firewall. Therefore, I would say that it is best to use both Group Policy and the Windows Firewall policy with System Center. But remember, Group Policy wins.
You might have Workgroup Clients or Servers in DMZ where this feature would be very handy to configure Windows Firewall via SCCM.
The basic tasks you can configure are as follows:
In the following screenshot, you can see the creation of a Windows Firewall Policy, and what configuration you can define, in the System Center Configuration Manager console:

Settings for creating a Firewall Policy
So, how this works is like this:
If you don't have a Group Policy that defines the Windows Firewall settings, the Endpoint Protection Windows Firewall Policy will be effective.
If you have a Group Policy as well as an Endpoint Protection Windows Firewall policy, then you can think of the policy shown in the preceding screenshot as a compliance baseline, where you will get a report back on what status the computers have regarding the settings you define.
You can find the Group Policy setting for this in Computer ConfigurationPoliciesAdministrative Templates..NetworkNetwork ConnectionsWindows Firewall.
This is shown in the following screenshot:

Group Policy settings for Windows Firewall
You can also use the Advanced Security settings that were released from Windows 2008 and Vista. This will give you a more granular control and give you the ability to control both inbound and outbound communication.
The settings are found in Windows Settings | Security Settings | Windows Firewall with Advanced Security:
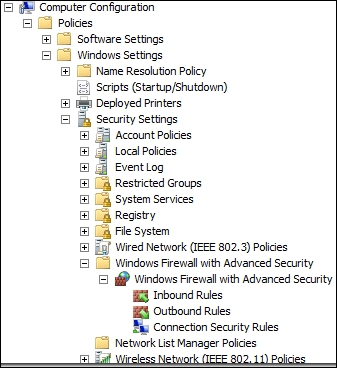
Group Policy for Windows Firewall with Advanced Security
After creating the Endpoint Protection Windows Firewall policy, deploying it to a collection of computers is a very common procedure in System Center Configuration Manager:
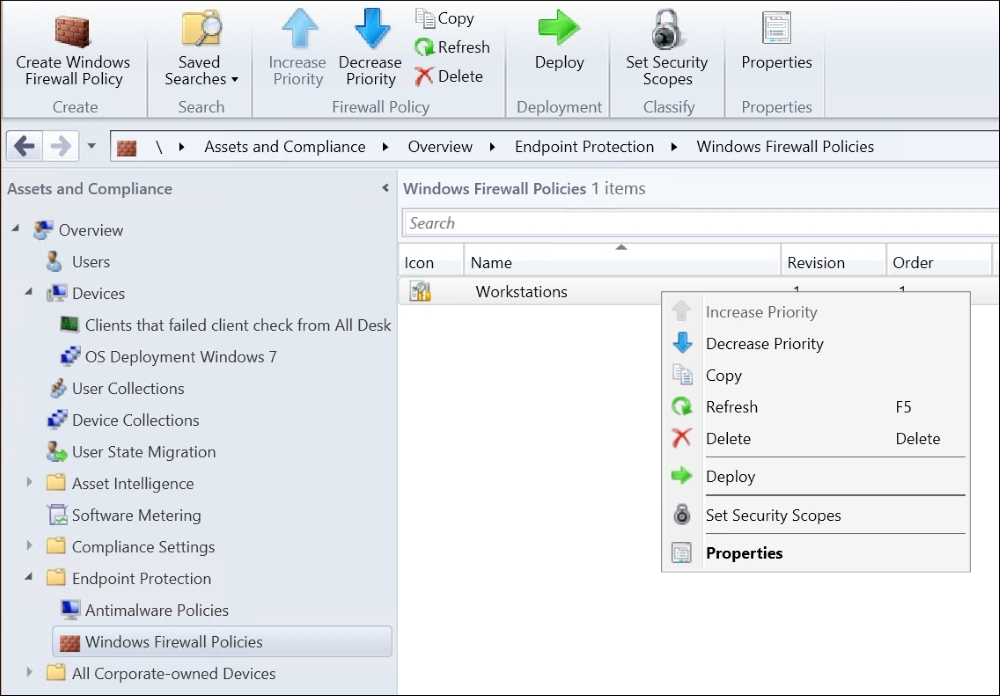
Workstations policy we created and the options present
The following screenshot shows the Deploy Windows Firewall Policy window, where you define how often the compliance baseline will be evaluated:
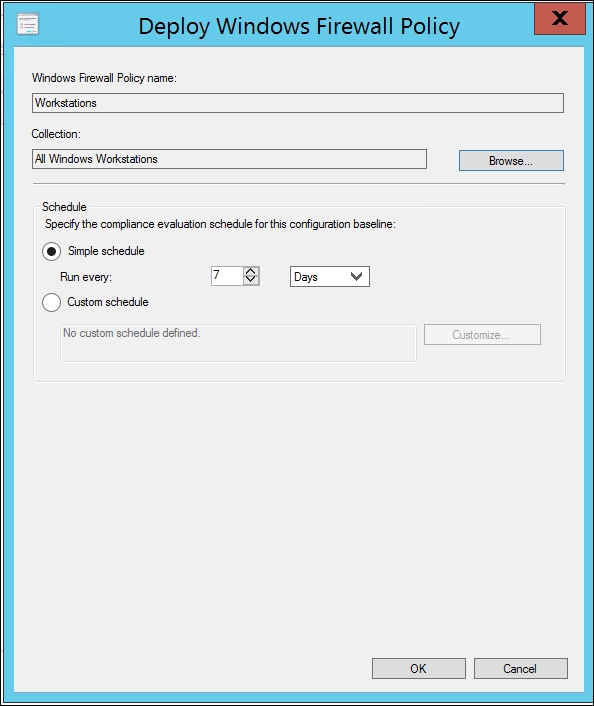
Default Simple schedule of the Compliance evaluation of the baseline
If we head on over to a computer that will receive this policy and perform a Machine Policy update on the Configuration Manager client, you can see that the policy has arrived as a configuration baseline. You can trigger the evaluation manually.
The following screenshot shows you the actions you have in the Configuration Manager application from the Control Panel in Windows:
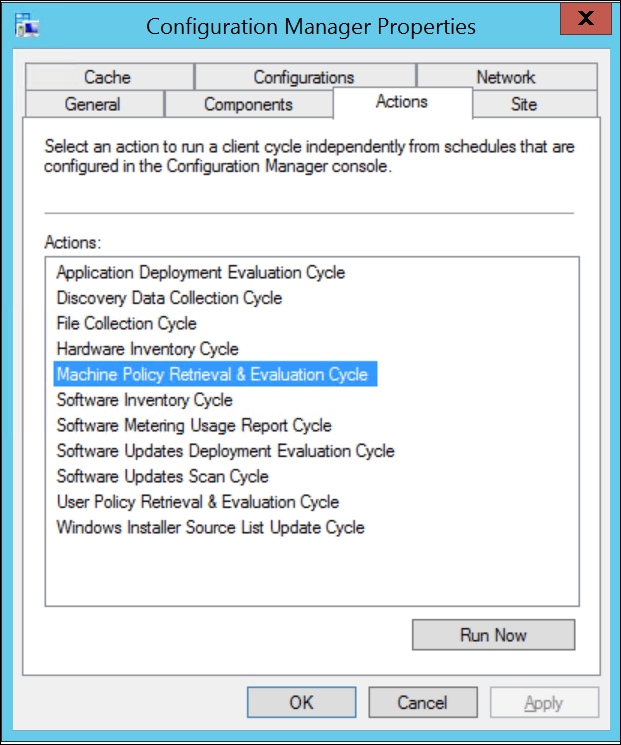
The following screenshot shows you that baselines are received in the Configuration Manager client, and that it is evaluated as Compliant:
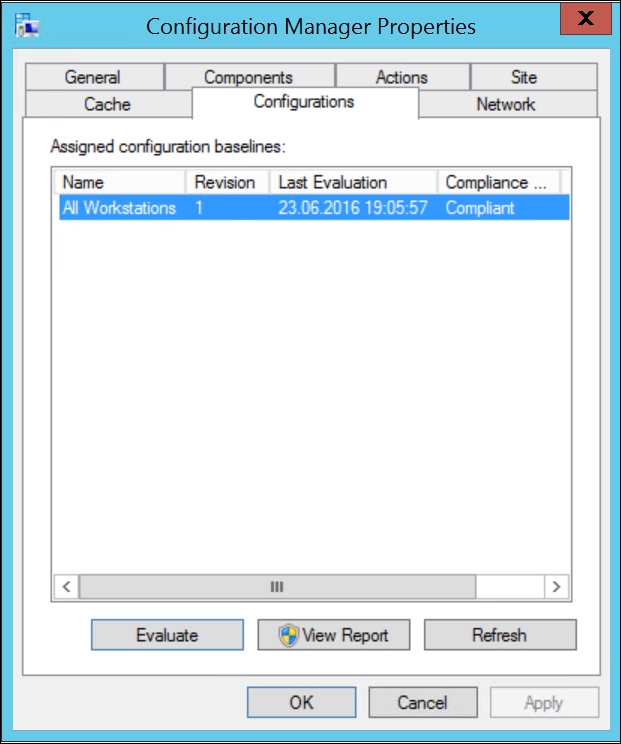
If you are local administrator, you get to see a report as well:

Compliance report from the Windows Firewall baseline
The Windows Firewall in Windows will show you a message that some settings are managed by your system administrator if you have either a Group Policy or Endpoint Protection Windows Firewall policy, as shown in the following screenshot:
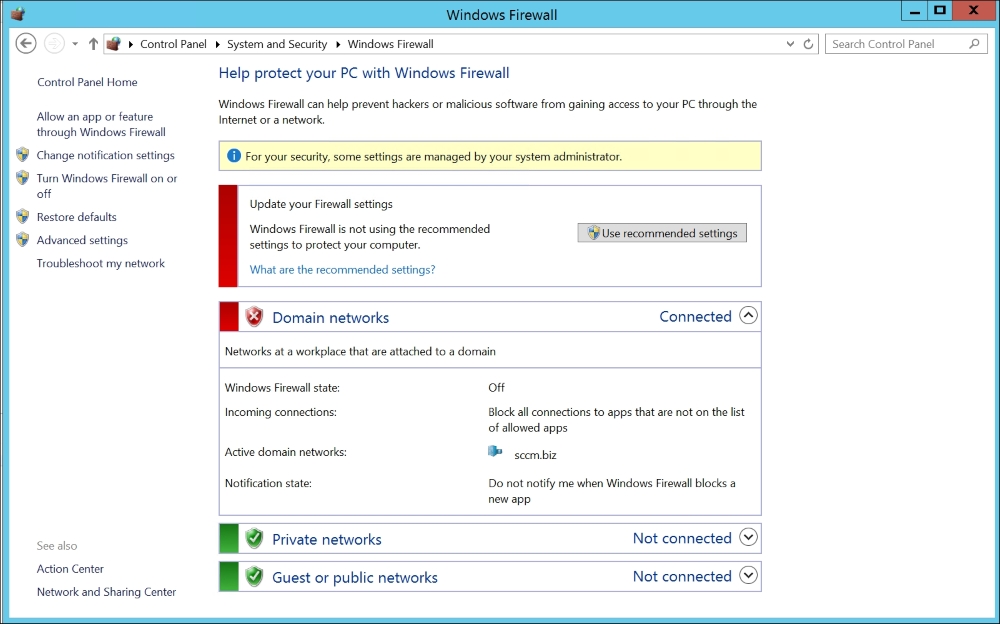
Settings being managed by your system administrator and the Firewall state
To monitor the compliance level and get more details on how the policy compliance is heading in your environment, you can go to the Monitoring | Overview | Deployments page and choose to view the rule you deployed. Remember that it may take a while until you get results back on this one, depending on your settings. Then you have to hit Run Summarization and Refresh to get an update in the view.
When you click on a Compliant listed, you will get more details on the status of the compliance as you can see on the picture following:

Deployment status in the Configuration Manager Console of the Windows Firewall setting that are deployed to the clients.
